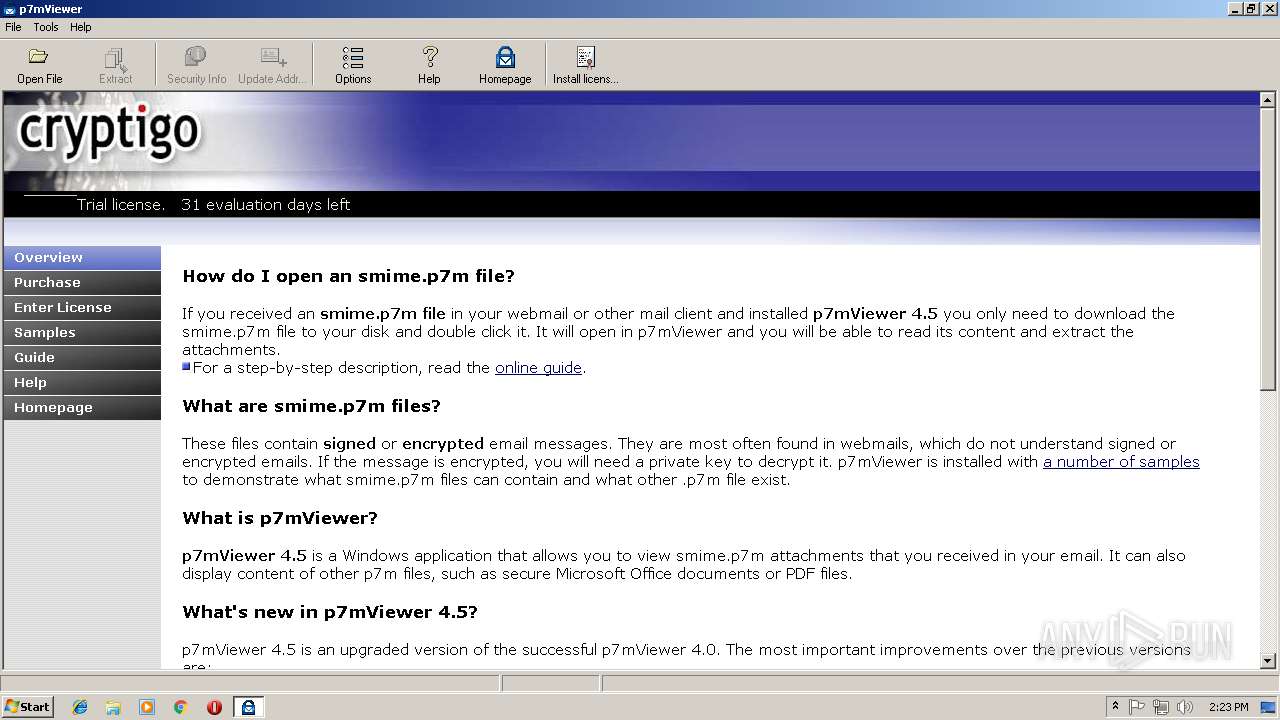
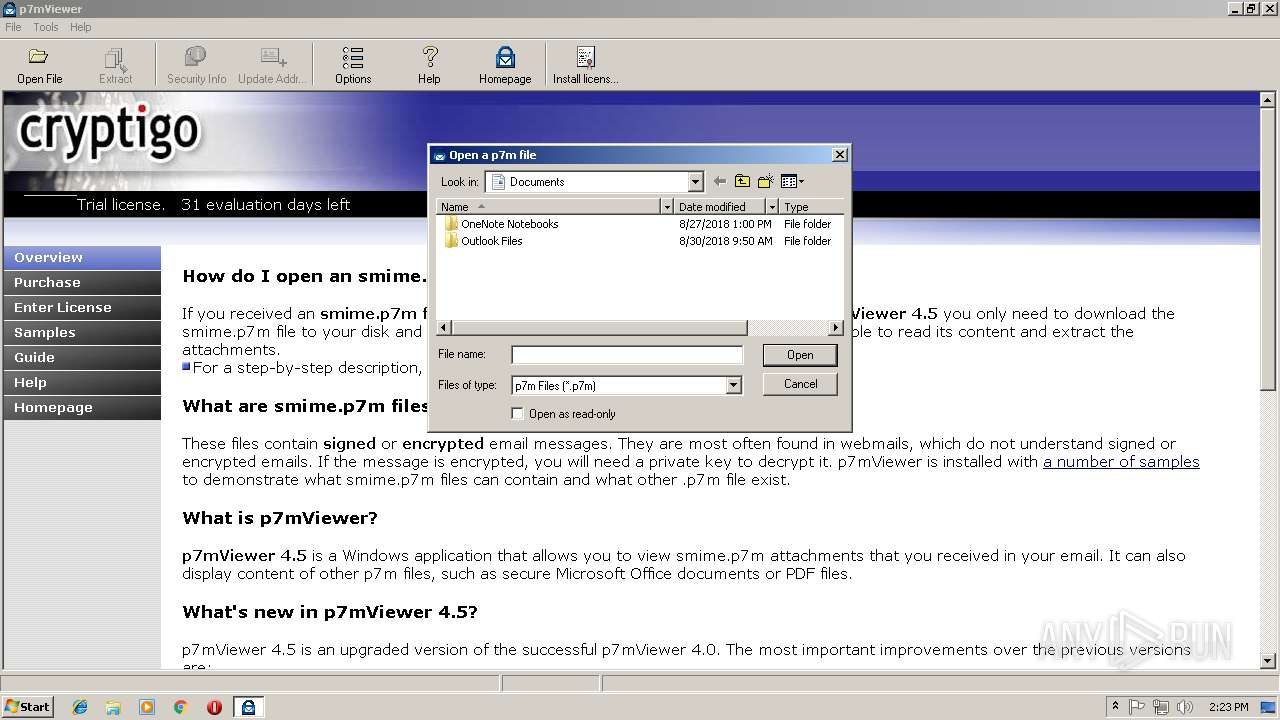
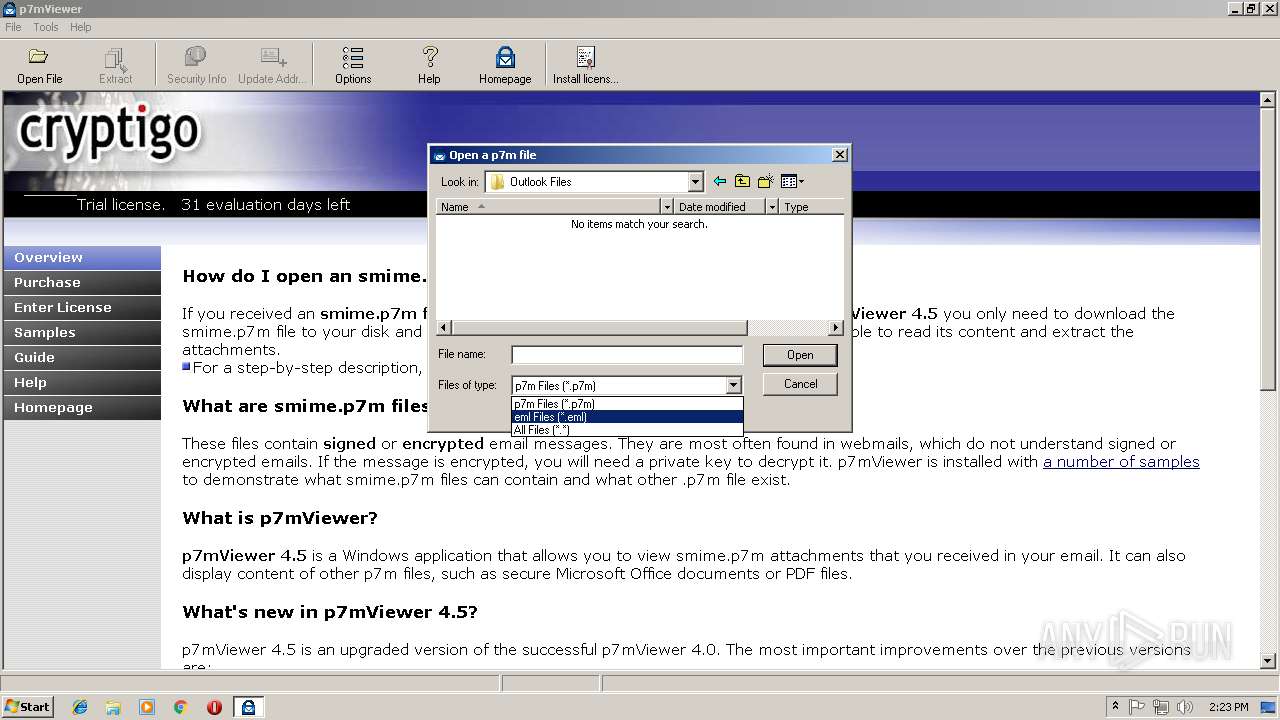
| download: | p7vSetup.exe |
| Full analysis: | https://app.any.run/tasks/01fb2c95-f2bf-4b49-8b76-9c88d8923c53 |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2018, 13:20:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C72B198119505DCE4F1D5F41C344F505 |
| SHA1: | 5EA2BAB64073D5637F30FDC417775F2D0B3D6A34 |
| SHA256: | 354525A06614991765918151766D5A69AD363B6FD04C9F9B3D702E7B488A1979 |
| SSDEEP: | 49152:l/Pm552DbVlYh7u2ol/i9GZjhDxaxAnav3BeiiHFZXzMLMUhyLlp2KJa3/KKV:Rg52tuHCq90NqfBUHNUhyaL3Cm |
MALICIOUS
Loads dropped or rewritten executable
- p7vSetup.exe (PID: 3164)
Application was dropped or rewritten from another process
- p7mViewer.exe (PID: 3348)
- p7mViewer.exe (PID: 4008)
SUSPICIOUS
Executable content was dropped or overwritten
- p7vSetup.exe (PID: 3164)
Creates files in the program directory
- p7vSetup.exe (PID: 3164)
Creates COM task schedule object
- p7vSetup.exe (PID: 3164)
Modifies the open verb of a shell class
- p7mViewer.exe (PID: 3348)
Reads internet explorer settings
- p7mViewer.exe (PID: 4008)
Reads Internet Cache Settings
- p7mViewer.exe (PID: 4008)
Creates files in the user directory
- p7mViewer.exe (PID: 4008)
INFO
Dropped object may contain Bitcoin addresses
- p7vSetup.exe (PID: 3164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (33) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (23.9) |
| .exe | | | Win64 Executable (generic) (21.2) |
| .scr | | | Windows screen saver (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2004:02:12 21:19:14+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 156672 |
| InitializedDataSize: | 359424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x24d1a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 12-Feb-2004 20:19:14 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 12-Feb-2004 20:19:14 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000262D5 | 0x00026400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59877 |
.rdata | 0x00028000 | 0x000021F8 | 0x00002200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.76488 |
.data | 0x0002B000 | 0x00054818 | 0x00003200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.49681 |
.rsrc | 0x00080000 | 0x00000FB0 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.30928 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.89965 | 696 | UNKNOWN | Finnish - Finland | RT_MANIFEST |
2 | 2.59572 | 308 | UNKNOWN | Finnish - Finland | RT_CURSOR |
18 | 3.20217 | 240 | UNKNOWN | Finnish - Finland | RT_DIALOG |
101 | 2.16096 | 20 | UNKNOWN | Finnish - Finland | RT_GROUP_ICON |
114 | 3.41672 | 480 | UNKNOWN | Finnish - Finland | RT_DIALOG |
127 | 3.4905 | 468 | UNKNOWN | Finnish - Finland | RT_BITMAP |
138 | 2.69978 | 166 | UNKNOWN | Finnish - Finland | RT_DIALOG |
152 | 1.91924 | 20 | UNKNOWN | Finnish - Finland | RT_GROUP_CURSOR |
154 | 3.02015 | 182 | UNKNOWN | Finnish - Finland | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
WINMM.dll |
comdlg32.dll |
Total processes
40
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | "C:\Users\admin\AppData\Local\Temp\p7vSetup.exe" | C:\Users\admin\AppData\Local\Temp\p7vSetup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3164 | "C:\Users\admin\AppData\Local\Temp\p7vSetup.exe" | C:\Users\admin\AppData\Local\Temp\p7vSetup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
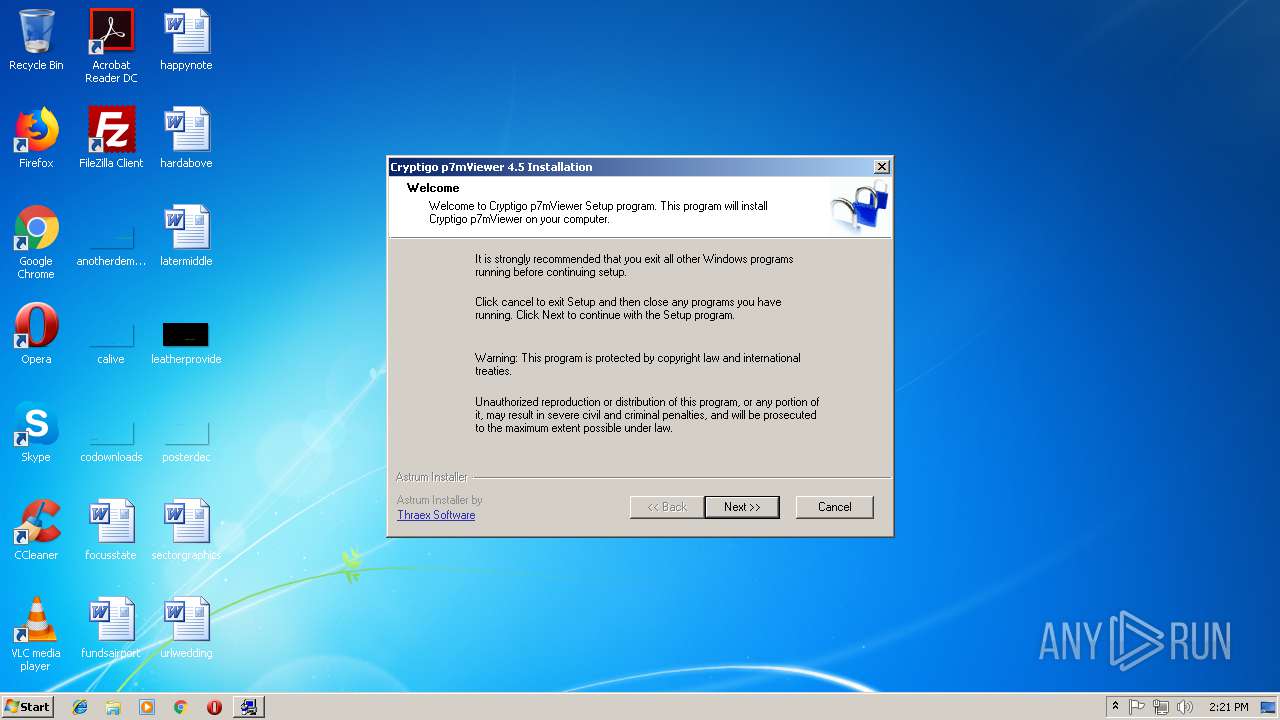
| 3348 | "C:\Program Files\Cryptigo\p7mViewer\p7mViewer.exe" -Install | C:\Program Files\Cryptigo\p7mViewer\p7mViewer.exe | — | p7vSetup.exe | |||||||||||
User: admin Company: Cryptigo Integrity Level: HIGH Description: p7mViewer Exit code: 0 Version: 4.6.16.1286 Modules
| |||||||||||||||
| 4008 | "C:\Program Files\Cryptigo\p7mViewer\p7mViewer.exe " | C:\Program Files\Cryptigo\p7mViewer\p7mViewer.exe | — | p7vSetup.exe | |||||||||||
User: admin Company: Cryptigo Integrity Level: HIGH Description: p7mViewer Exit code: 0 Version: 4.6.16.1286 Modules
| |||||||||||||||
Total events
955
Read events
758
Write events
196
Delete events
1
Modification events
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\p7mViewer.exe |
| Operation: | write | Name: | |
Value: | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\p7mViewer.exe\install |
| Operation: | write | Name: | Directory |
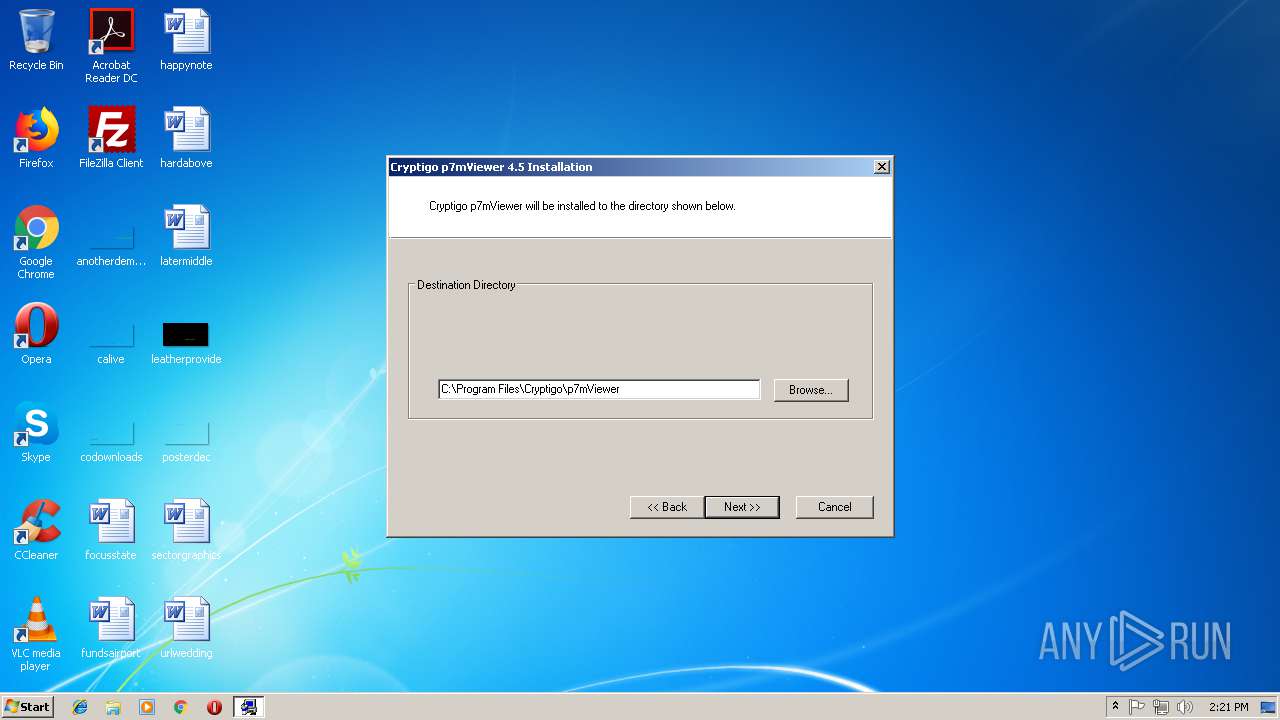
Value: C:\Program Files\Cryptigo\p7mViewer | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\p7mViewer.exe\install |
| Operation: | write | Name: | Version |
Value: 4.5 | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\p7mViewer.exe\install |
| Operation: | write | Name: | Uninstaller |
Value: C:\Program Files\Cryptigo\p7mViewer\Uninstall.exe | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Program Files\Cryptigo\p7mViewer\CryptigoUtils.ocx |
Value: 1 | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E4EC6663-E433-4C76-AA4A-7643CC487513} |
| Operation: | write | Name: | |
Value: Shell.Utils | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E4EC6663-E433-4C76-AA4A-7643CC487513}\InprocServer32 |
| Operation: | write | Name: | |
Value: %SystemRoot%\system32\shell32.dll | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E4EC6663-E433-4C76-AA4A-7643CC487513}\ProgId |
| Operation: | write | Name: | |
Value: Shell.Utils | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E4EC6663-E433-4C76-AA4A-7643CC487513}\TypeLib |
| Operation: | write | Name: | |
Value: {1B8E5FE3-6A3C-4CD2-BF40-569170474137} | |||
| (PID) Process: | (3164) p7vSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E4EC6663-E433-4C76-AA4A-7643CC487513}\Version |
| Operation: | write | Name: | |
Value: 1.0 | |||
Executable files
7
Suspicious files
11
Text files
15
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3164 | p7vSetup.exe | C:\Users\admin\AppData\Local\Temp\aiw1094593.bmp | image | |
MD5:E765FF8C8C4F07FC1565539B7A0D9EA8 | SHA256:2A70254F17EF98B982174BD93E18B37894482B04693AB09E8A70D052337E8651 | |||
| 3164 | p7vSetup.exe | C:\Program Files\Cryptigo\p7mViewer\P7MVIEWER.HLP | hlp | |
MD5:257535FFB87B245AF77EA96FE90EDC4D | SHA256:21CA92438F179934763AB96EDC1116B71FEC5FBAC33AE75899B20F23BFAFCA76 | |||
| 3164 | p7vSetup.exe | C:\Users\admin\AppData\Local\Temp\aiw1094609.EXE | executable | |
MD5:18A2BDA5D762290BCE8AFE9FB872B8EA | SHA256:9635627365AF54A4348EC379E1D6C0098CEA2554A93F7A3EF5398F72C4E6E1DE | |||
| 3164 | p7vSetup.exe | C:\Users\admin\AppData\Local\Temp\aaiw1094595.bmp | image | |
MD5:ADF651467B764A4E25813C0DE709AD63 | SHA256:04A2DFE644293C0F8AC9ABC8F71411112EED097D798EAB2AB8E24619FD19C263 | |||
| 3164 | p7vSetup.exe | C:\Users\admin\AppData\Local\Temp\aiw1094609.DLL | executable | |
MD5:4E97C7B658113BE24E839EE5D798C1F0 | SHA256:C10E132B5A0430F7034F89EDA86D9A8E2E506297E1DB01AEFDF4070E6F4C8903 | |||
| 3164 | p7vSetup.exe | C:\Program Files\Cryptigo\p7mViewer\smime\scenarios\B1-EXTRACTTO-Extract to folder ${EXTRACTFILENAME}.pvc | xml | |
MD5:D289E1BBE82B1A3AE53406C7B1CAA44A | SHA256:E794D6D428021A8DC74206516EF668A008B4CCD3DF824D10133C2C9B0FC0278F | |||
| 3164 | p7vSetup.exe | C:\Program Files\Cryptigo\p7mViewer\p7mViewer.exe | executable | |
MD5:45419E9286D8BE96F10F74B41083820D | SHA256:45C856B1C81CF1BC0D8476067E0F733BE034103967ED4F35FFC0776987F24B6E | |||
| 3164 | p7vSetup.exe | C:\Program Files\Cryptigo\p7mViewer\smime\scenarios\A1-OPEN-View.pvc | xml | |
MD5:06D4F466EA296E92B29575D2278367D1 | SHA256:F4A3EEBB4D4BED9766B70F42E0D0FD7E8A99F6EC440A8C34717CAD5272DBBDEA | |||
| 3164 | p7vSetup.exe | C:\Program Files\Cryptigo\p7mViewer\smime\scenarios\B3-EXTRACTTO-Extract to selected folder${EFS}.pvc | xml | |
MD5:050C2124DFC82978DF721795A53E6B66 | SHA256:385FE05C3867B3826AD883CF2DA6D4F5CD20EA1B532F4DD0F6769339D60A5AAC | |||
| 3164 | p7vSetup.exe | C:\Program Files\Cryptigo\p7mViewer\smime\scenarios\C1-CONFIGURE-Configure....pvc | xml | |
MD5:091EF7849A21DE3ADE372957EE37F7F3 | SHA256:CB99C788BA9B31B976912AEF7C996535EFE48CADD216E62715A0D44CB209C7F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report