| File name: | RFP_AllianxMexico_2022.doc |
| Full analysis: | https://app.any.run/tasks/05f14cf5-7297-4f7b-8a96-37ad859ab8c2 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 22:40:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Keywords: 16, Comments: 4, Thumbnail: 2362, 0x17: 1048576CDFV2 Microsoft Word |
| MD5: | B371E1C2CA2E5718E151760BC4664366 |
| SHA1: | 73457D23E5235DF0FCFBF6547AAF26CCCC765011 |
| SHA256: | 3542078FD524E3CB141D5BEBF96AEA73467505A07AE72FC58395AFA14F22E8A3 |
| SSDEEP: | 24576:/HS4AwARd+X+i4Ht5O9SD++vxRC05yU3LahYcVy7eK+OuQAoKsn7uqb/H:fRyCpG/ |
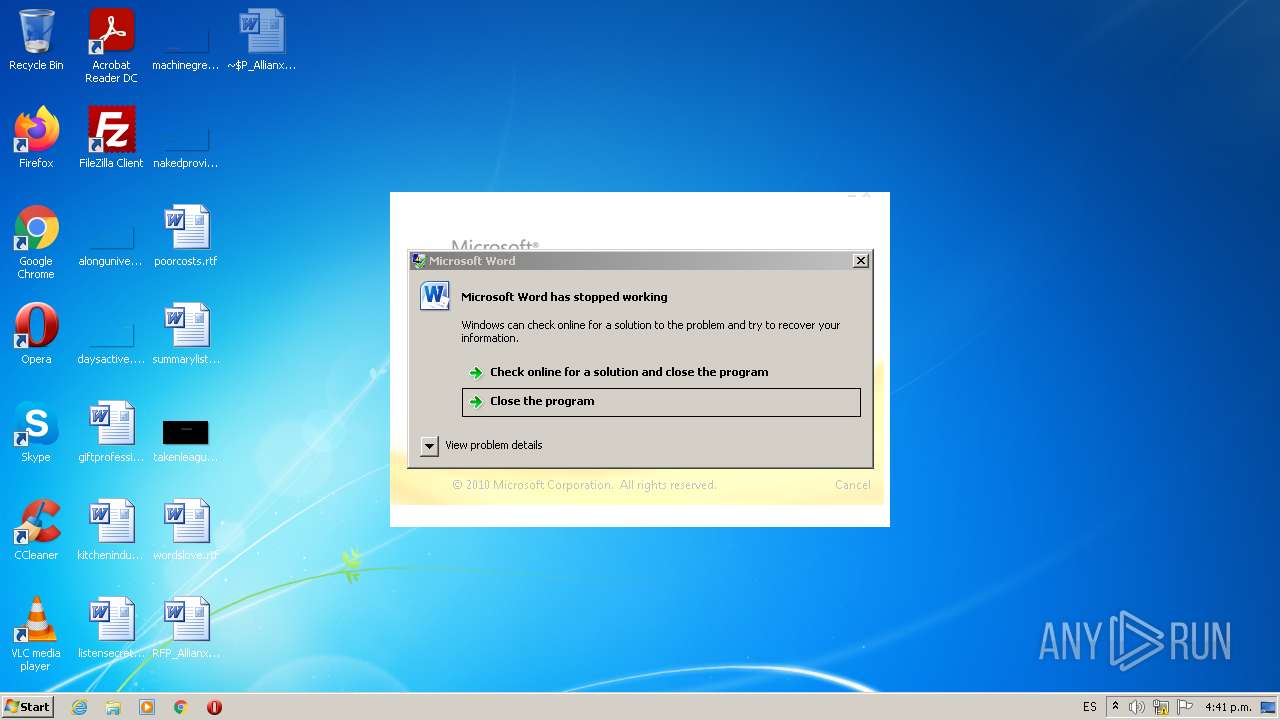
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 392)
SUSPICIOUS
Checks supported languages
- DW20.EXE (PID: 3832)
Reads default file associations for system extensions
- WINWORD.EXE (PID: 392)
INFO
Checks supported languages
- WINWORD.EXE (PID: 392)
- dwwin.exe (PID: 3272)
Reads the computer name
- WINWORD.EXE (PID: 392)
- dwwin.exe (PID: 3272)
Creates files in the user directory
- WINWORD.EXE (PID: 392)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| HeadingPairs: |
|
|---|---|
| TitleOfParts: | - |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 16 |
| CharCountWithSpaces: | 2362 |
| Paragraphs: | 4 |
| Lines: | 16 |
| Company: | - |
| CodePage: | Windows Latin 1 (Western European) |
| CompObjUserType: | Documento de Microsoft Word 97-2003 |
| CompObjUserTypeLen: | 36 |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\RFP_AllianxMexico_2022.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3272 | C:\Windows\system32\dwwin.exe -x -s 1420 | C:\Windows\system32\dwwin.exe | — | DW20.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Watson Client Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3832 | "C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE" -x -s 1420 | C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Application Error Reporting Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
Total events
1 378
Read events
1 262
Write events
80
Delete events
36
Modification events
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | cy< |
Value: 63793C0088010000010000000000000000000000 | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (392) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
2
Text files
1
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 392 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1B4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3272 | dwwin.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_WINWORD.EXE_5925cffacf343a3c93e92254daaac1d4b3aeb_0cdf08ba\Report.wer | — | |
MD5:— | SHA256:— | |||
| 392 | WINWORD.EXE | C:\Users\admin\Desktop\~$P_AllianxMexico_2022.doc | pgc | |
MD5:— | SHA256:— | |||
| 392 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 392 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\RFP_AllianxMexico_2022.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 392 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\1313828.cvr | sqm | |
MD5:— | SHA256:— | |||
| 392 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{7284319B-1821-42F1-9C1E-DF2052B1CF57}.tmp | binary | |
MD5:— | SHA256:— | |||
| 392 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
| 392 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{B8017934-9CB0-44A3-B49C-7F140DAAD751}.tmp | smt | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 392 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF4430F24A7BB01772.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report