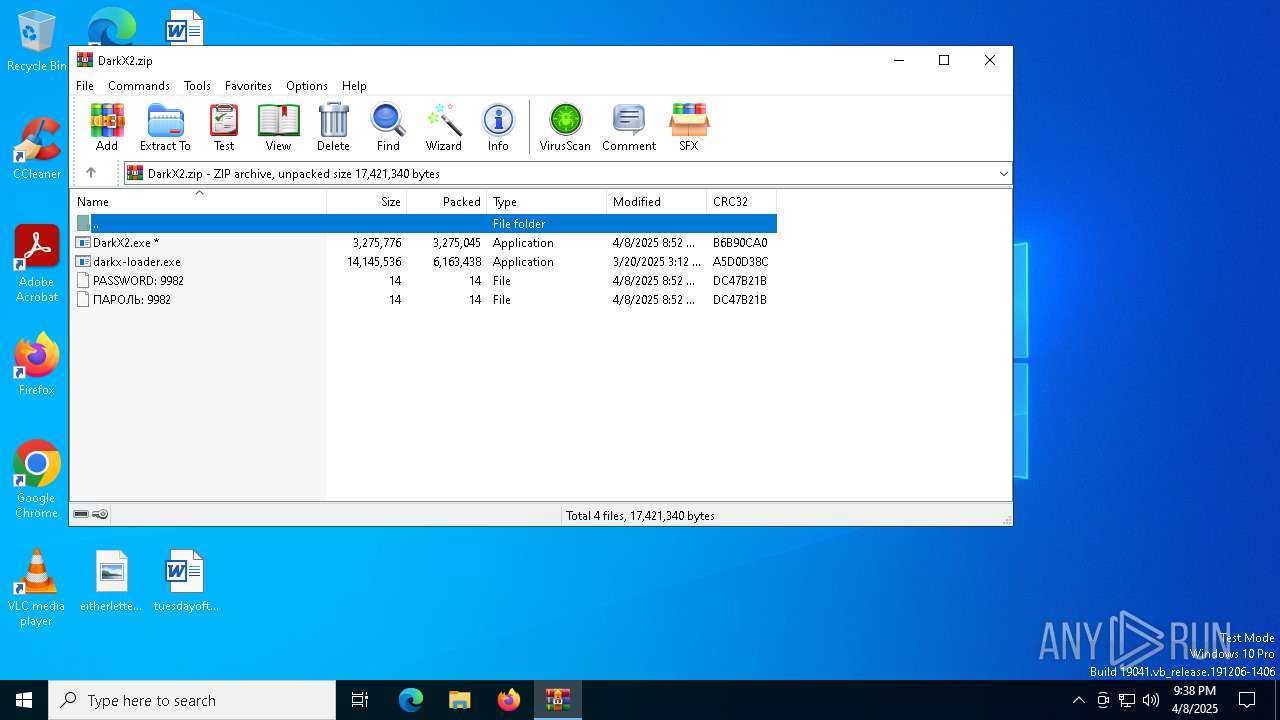
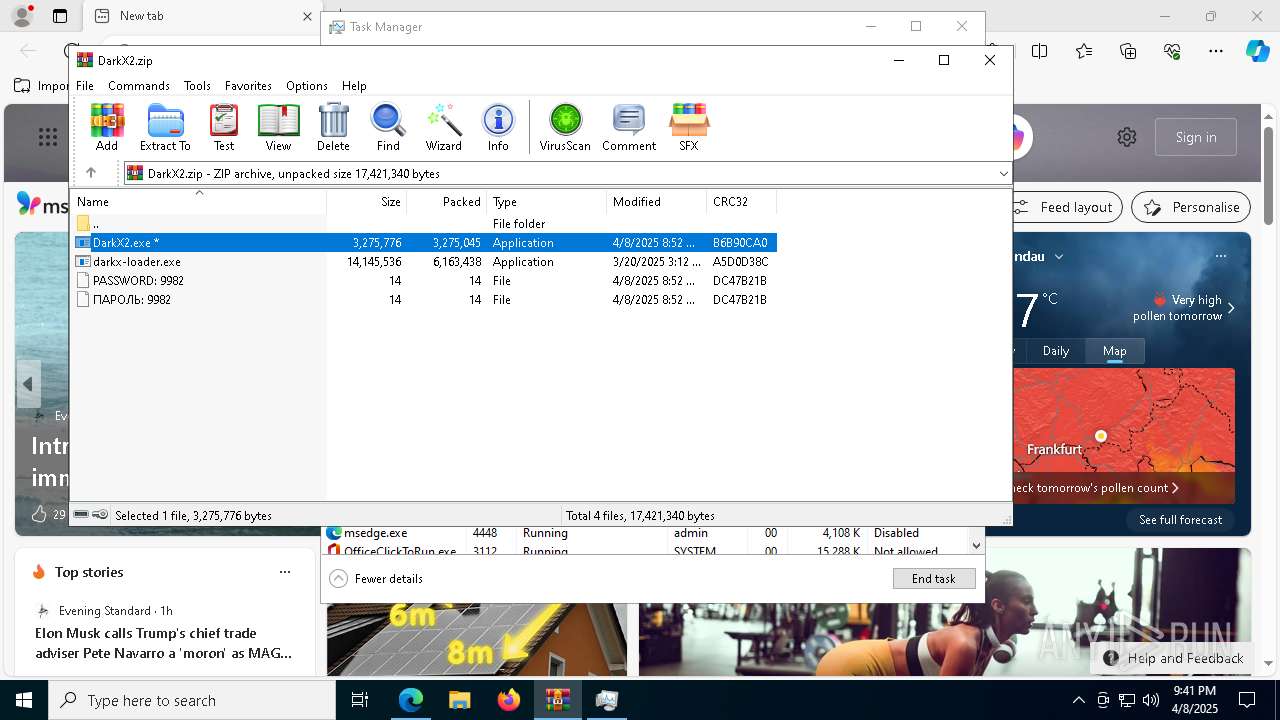
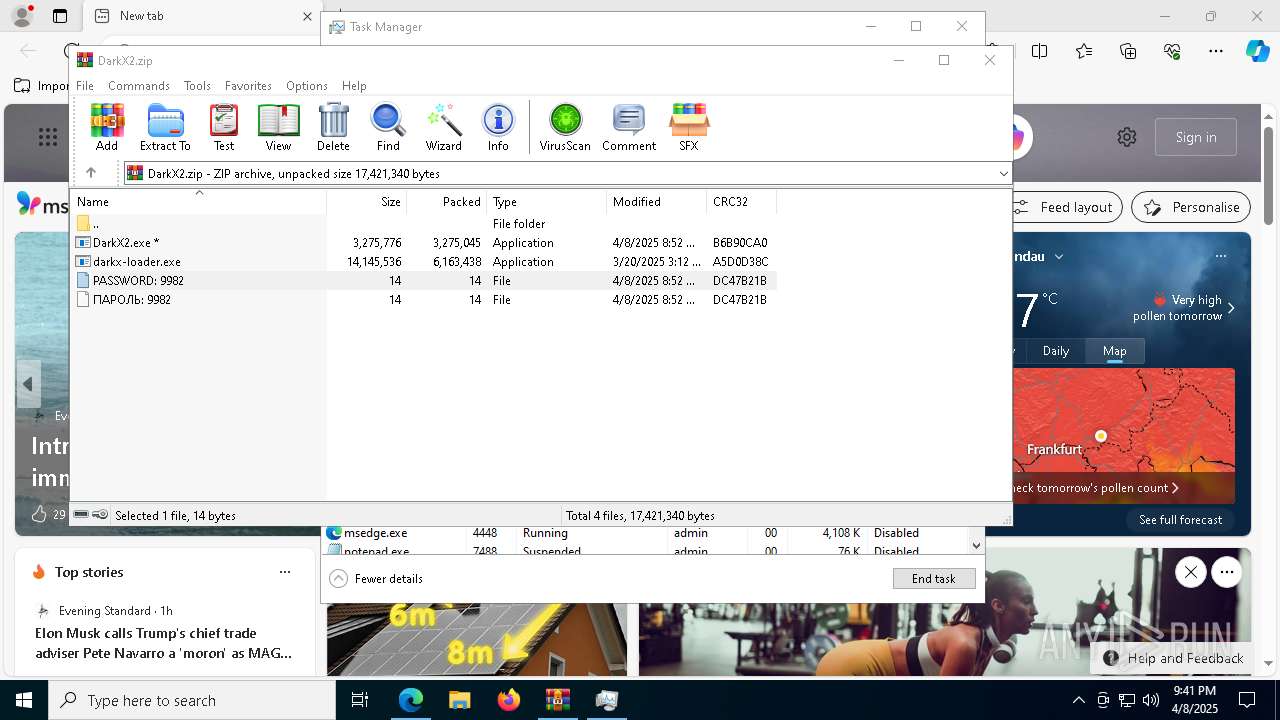
| File name: | DarkX2.zip |
| Full analysis: | https://app.any.run/tasks/14504709-632e-4e62-a7c0-da49dd274d1a |
| Verdict: | Malicious activity |
| Analysis date: | April 08, 2025, 21:38:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 8EF2838AE4FCF08159782EB2F261D2A7 |
| SHA1: | 09EB2C36741AA4037A9DD78639C9B6B4A3CB9494 |
| SHA256: | 353F0074FB11D0E209E051B186CBB677D5BAAFAADCC5D94E3667572F73DB24A2 |
| SSDEEP: | 98304:YRjOzq3idYNB1LGAH7eSdel/U+iqCgXs3ntpJYfdZQH4DkdwMcpl1aJ53MP4vvrT:1CgNHVs+MlEHJVOal/u |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for external IP
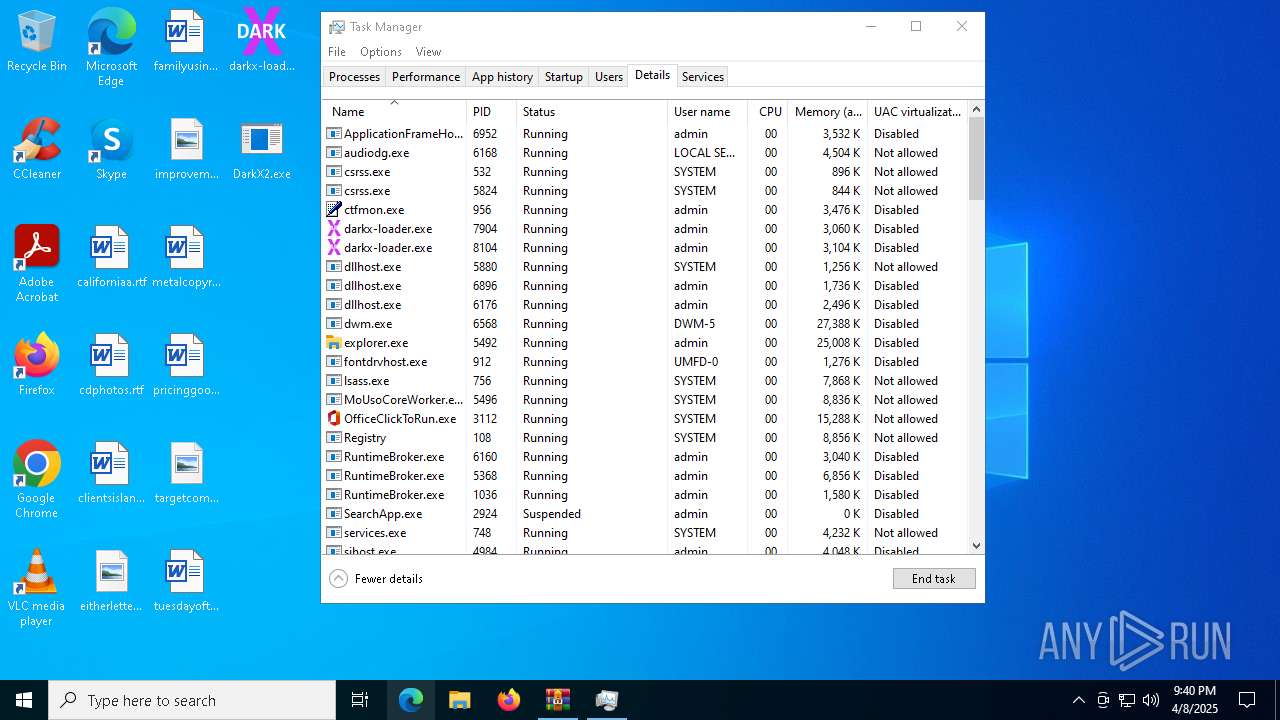
- svchost.exe (PID: 2196)
- darkx-loader.exe (PID: 7904)
- darkx-loader.exe (PID: 8104)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7292)
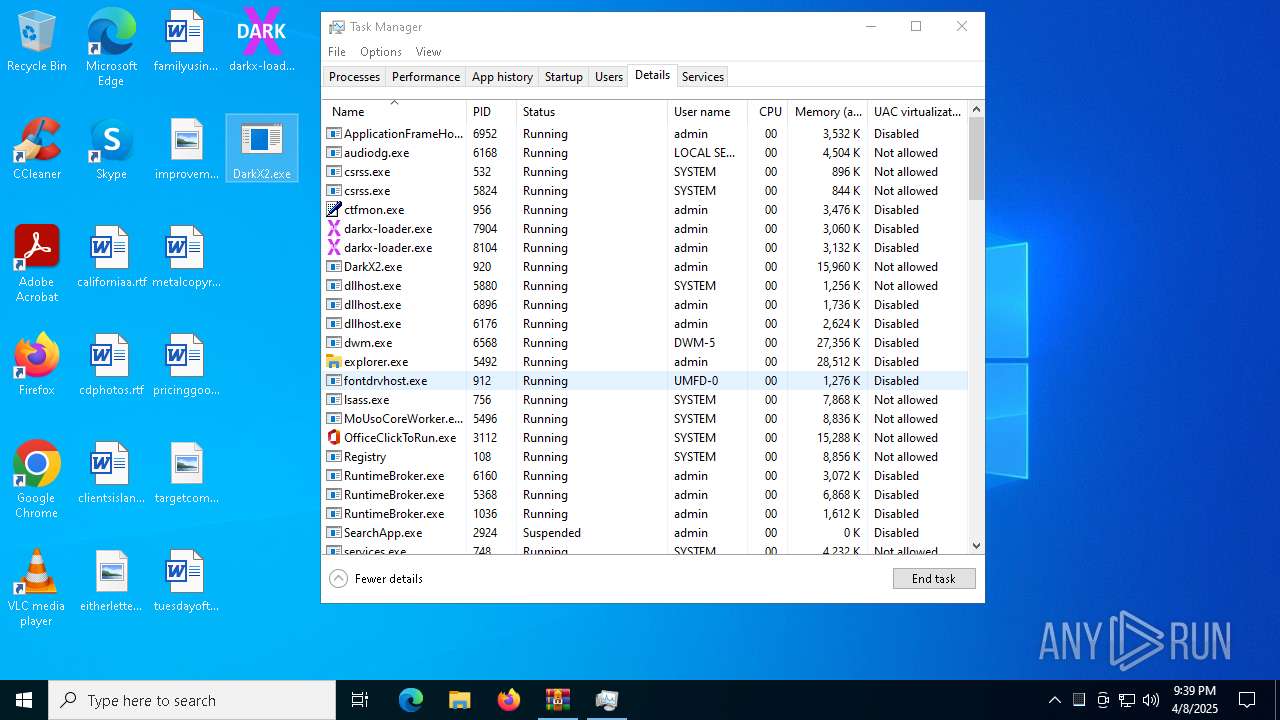
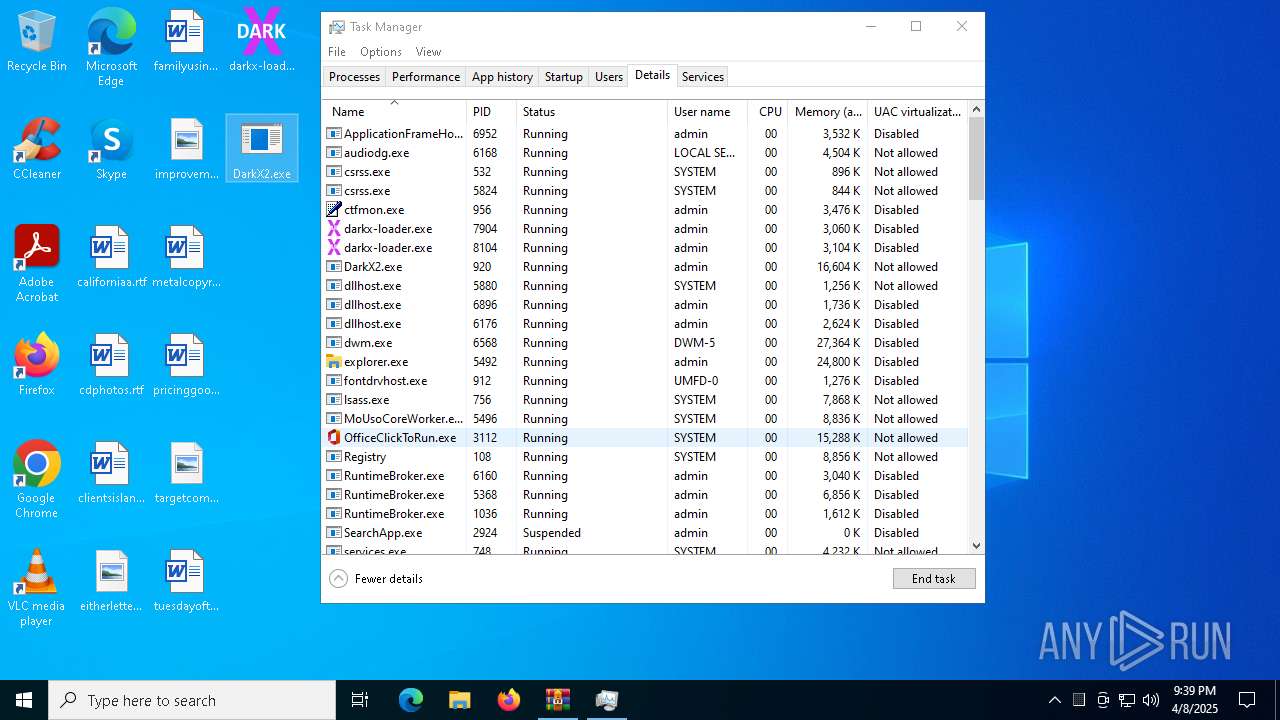
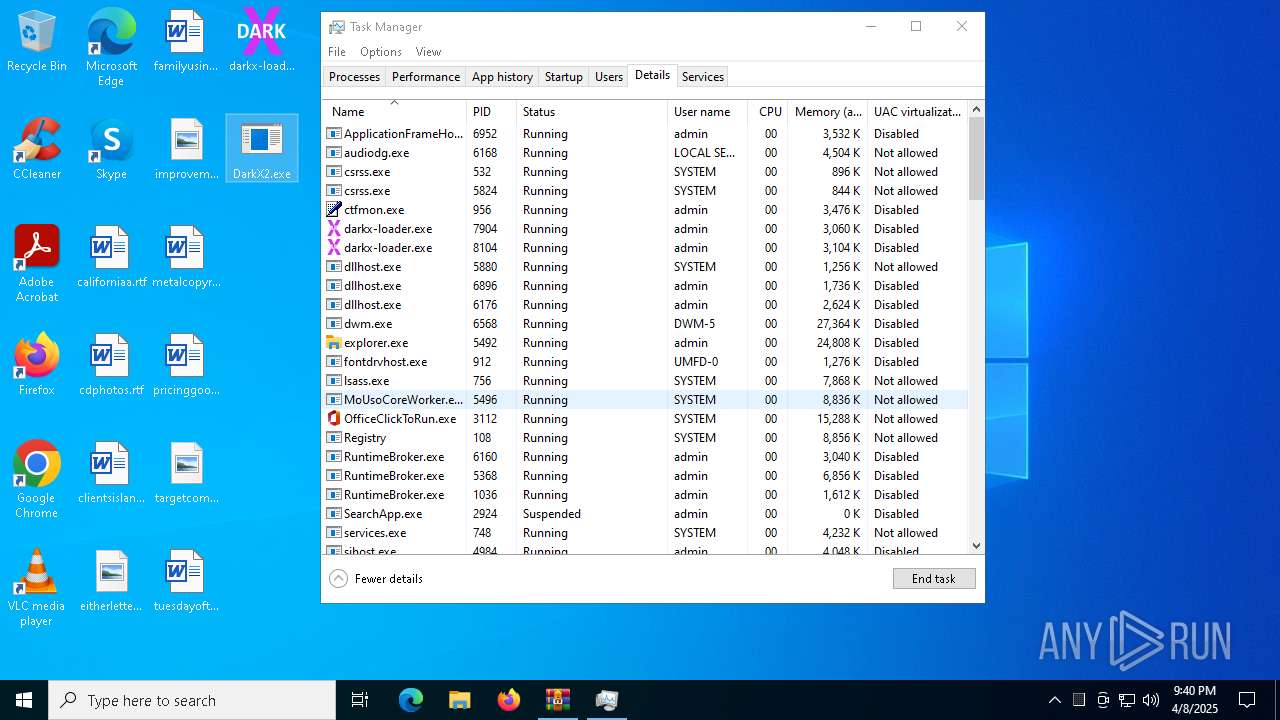
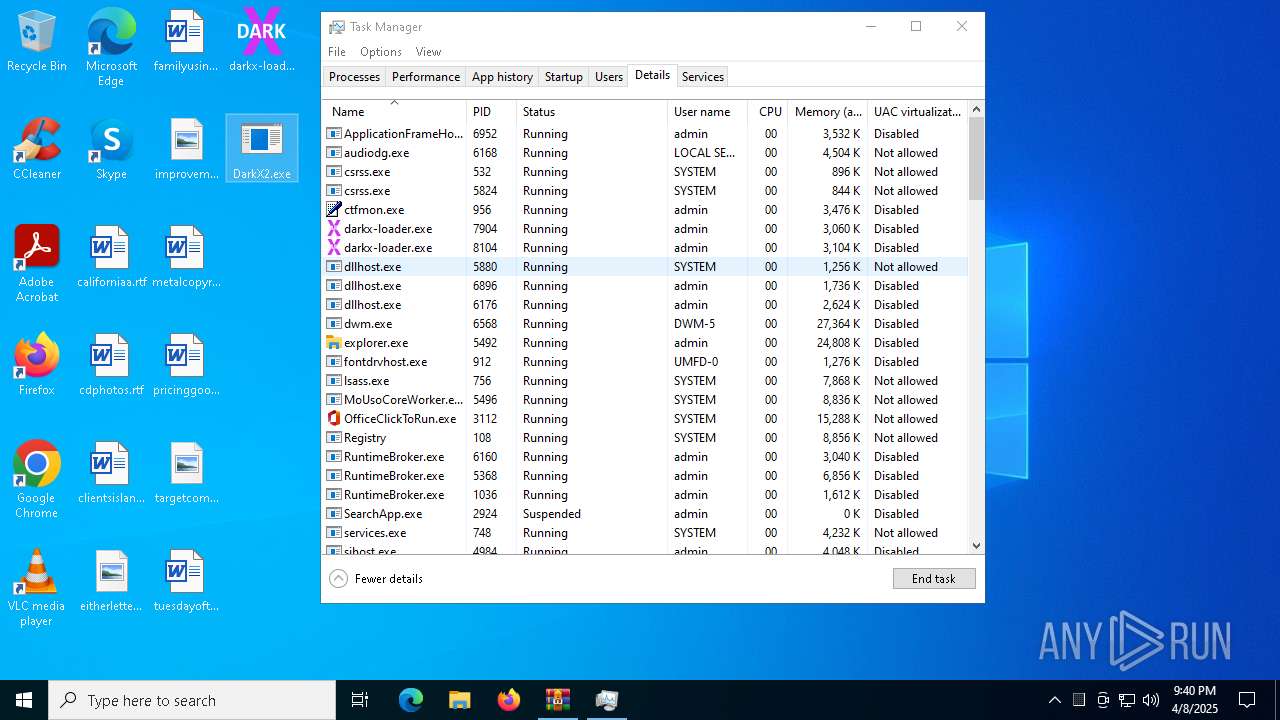
- DarkX2.exe (PID: 6032)
Possible usage of Discord/Telegram API has been detected (YARA)
- darkx-loader.exe (PID: 7904)
- darkx-loader.exe (PID: 8104)
There is functionality for taking screenshot (YARA)
- darkx-loader.exe (PID: 7904)
- darkx-loader.exe (PID: 8104)
Application launched itself
- DarkX2.exe (PID: 6032)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7292)
Checks supported languages
- darkx-loader.exe (PID: 7904)
- darkx-loader.exe (PID: 8104)
- DarkX2.exe (PID: 6032)
- DarkX2.exe (PID: 920)
- identity_helper.exe (PID: 7760)
Reads the computer name
- darkx-loader.exe (PID: 7904)
- darkx-loader.exe (PID: 8104)
- DarkX2.exe (PID: 6032)
- DarkX2.exe (PID: 920)
- identity_helper.exe (PID: 7760)
Checks proxy server information
- darkx-loader.exe (PID: 7904)
- darkx-loader.exe (PID: 8104)
- slui.exe (PID: 2140)
Attempting to use instant messaging service
- svchost.exe (PID: 2196)
Reads the software policy settings
- darkx-loader.exe (PID: 7904)
- darkx-loader.exe (PID: 8104)
- slui.exe (PID: 7500)
- slui.exe (PID: 2140)
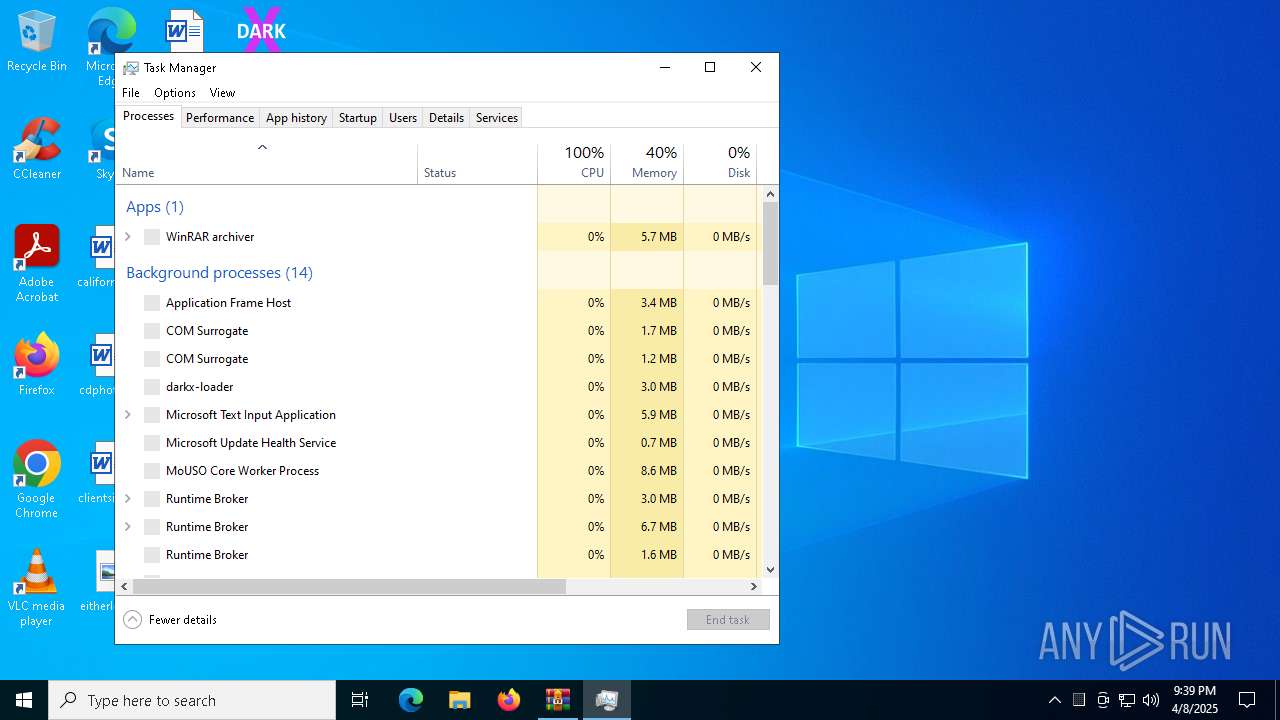
Manual execution by a user
- darkx-loader.exe (PID: 8104)
- Taskmgr.exe (PID: 5156)
- Taskmgr.exe (PID: 7172)
- DarkX2.exe (PID: 6032)
- msedge.exe (PID: 2108)
Application based on Rust
- darkx-loader.exe (PID: 7904)
- darkx-loader.exe (PID: 8104)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 5156)
- WWAHost.exe (PID: 3396)
- OpenWith.exe (PID: 7236)
- notepad.exe (PID: 7488)
Reads the machine GUID from the registry
- DarkX2.exe (PID: 6032)
- DarkX2.exe (PID: 920)
Process checks computer location settings
- DarkX2.exe (PID: 6032)
Creates files or folders in the user directory
- WWAHost.exe (PID: 3396)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7236)
Application launched itself
- msedge.exe (PID: 2108)
Reads Environment values
- identity_helper.exe (PID: 7760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7904) darkx-loader.exe
Discord-Webhook-Tokens (1)1267155916109779137/csIK61NTG4-ssAPfbfbDCXNkwA88DElPSHBGSBAAcSBIrrkt30WqcPCr1Ou1grUIH3gc
Discord-Info-Links
1267155916109779137/csIK61NTG4-ssAPfbfbDCXNkwA88DElPSHBGSBAAcSBIrrkt30WqcPCr1Ou1grUIH3gc
Get Webhook Infohttps://discord.com/api/webhooks/1267155916109779137/csIK61NTG4-ssAPfbfbDCXNkwA88DElPSHBGSBAAcSBIrrkt30WqcPCr1Ou1grUIH3gc
(PID) Process(8104) darkx-loader.exe
Discord-Webhook-Tokens (1)1267155916109779137/csIK61NTG4-ssAPfbfbDCXNkwA88DElPSHBGSBAAcSBIrrkt30WqcPCr1Ou1grUIH3gc
Discord-Info-Links
1267155916109779137/csIK61NTG4-ssAPfbfbDCXNkwA88DElPSHBGSBAAcSBIrrkt30WqcPCr1Ou1grUIH3gc
Get Webhook Infohttps://discord.com/api/webhooks/1267155916109779137/csIK61NTG4-ssAPfbfbDCXNkwA88DElPSHBGSBAAcSBIrrkt30WqcPCr1Ou1grUIH3gc
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:08 23:52:38 |
| ZipCRC: | 0xdc47b21b |
| ZipCompressedSize: | 14 |
| ZipUncompressedSize: | 14 |
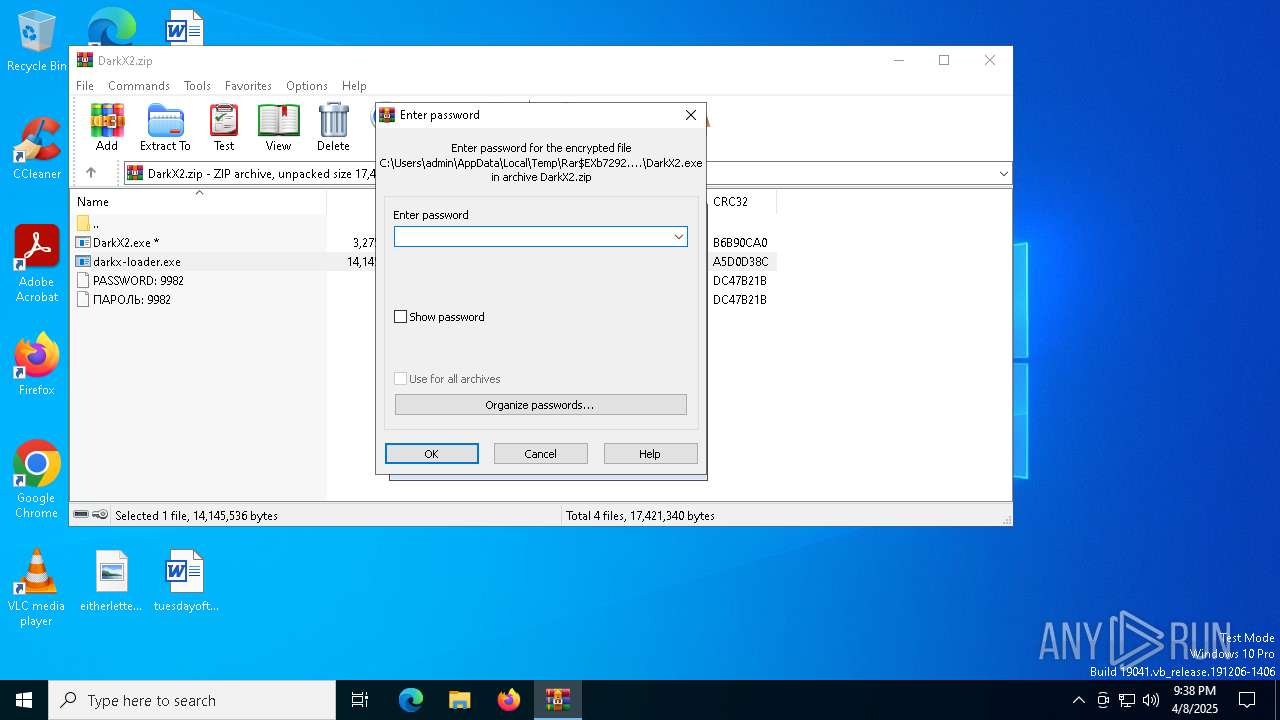
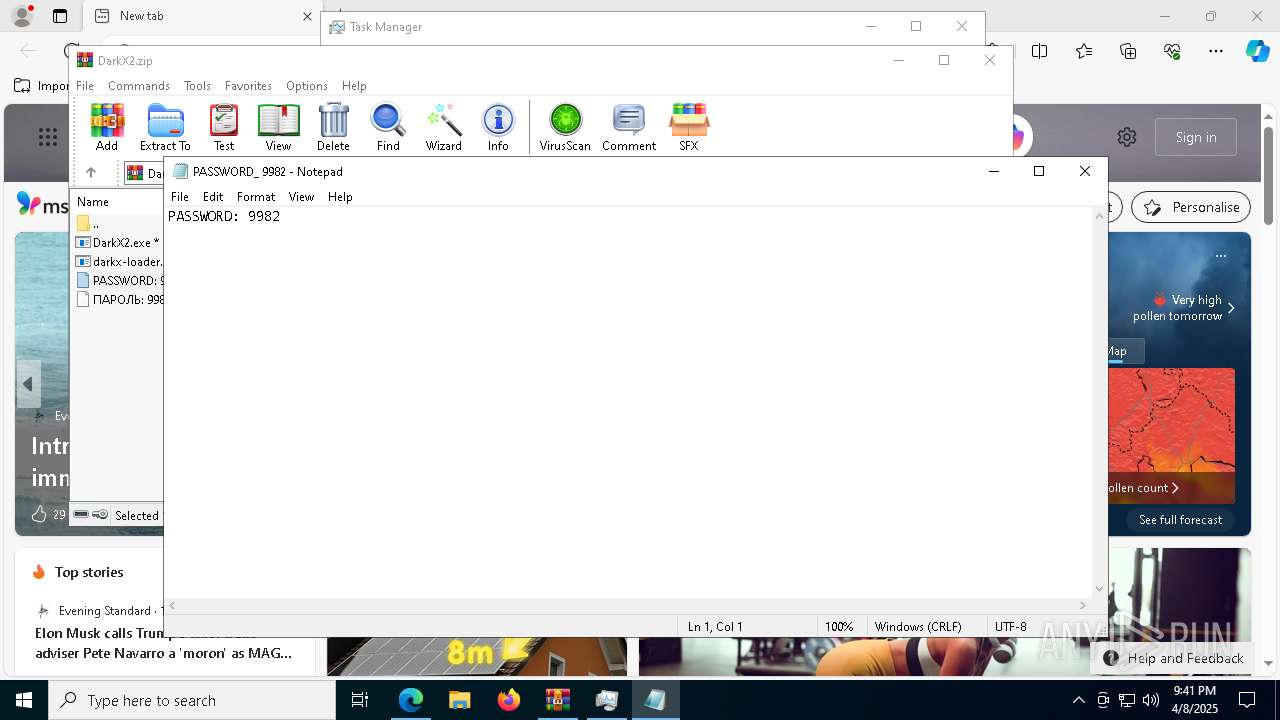
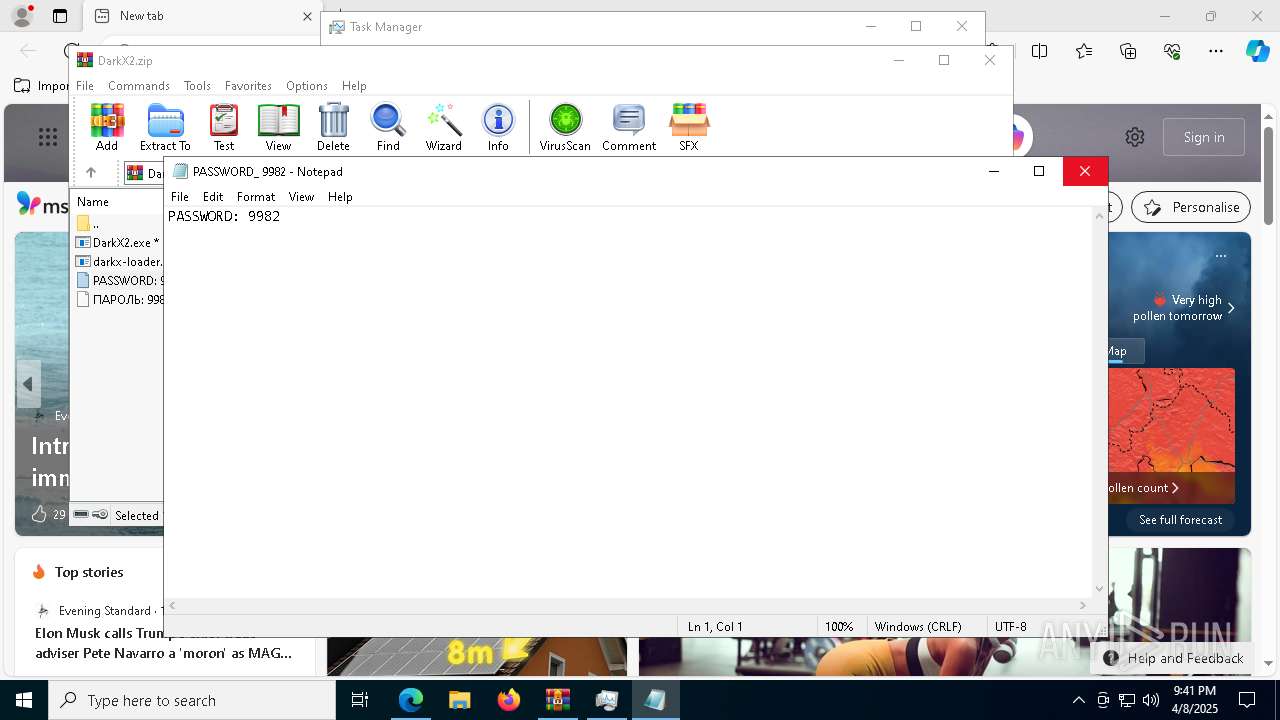
| ZipFileName: | PASSWORD: 9982 |
Total processes
175
Monitored processes
41
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Users\admin\Desktop\DarkX2.exe" | C:\Users\admin\Desktop\DarkX2.exe | DarkX2.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2108 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2140 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6148 --field-trial-handle=2468,i,16593990781958574106,9144267918493322739,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2416 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5052 --field-trial-handle=2468,i,16593990781958574106,9144267918493322739,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3140 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6556 --field-trial-handle=2468,i,16593990781958574106,9144267918493322739,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3396 | "C:\WINDOWS\system32\wwahost.exe" -ServerName:App.wwa | C:\Windows\System32\WWAHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft WWA Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=6392 --field-trial-handle=2468,i,16593990781958574106,9144267918493322739,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3956 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4092 --field-trial-handle=2468,i,16593990781958574106,9144267918493322739,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
14 472
Read events
14 397
Write events
43
Delete events
32
Modification events
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DarkX2.zip | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7292) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
Executable files
37
Suspicious files
569
Text files
93
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF12556b.TMP | — | |
MD5:— | SHA256:— | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF12556b.TMP | — | |
MD5:— | SHA256:— | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF12556b.TMP | — | |
MD5:— | SHA256:— | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF12557b.TMP | — | |
MD5:— | SHA256:— | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:6971E42ED64D2BE125547F021EB852B1 | SHA256:B46CFDC4106DF566F71AA34D6F10B53767C561DFD17DD07A5930A18E67BB344B | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:1E9E15EF6E531C4557100F20C9C76F01 | SHA256:46CB063CC268B69B172660F166C4394D5B4EDD802388B3EC16766DEBDB9F86C3 | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF12559a.TMP | — | |
MD5:— | SHA256:— | |||
| 2108 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
162
DNS requests
104
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7904 | darkx-loader.exe | GET | 200 | 208.95.112.1:80 | http://208.95.112.1:80/json/ | unknown | — | — | unknown |
8104 | darkx-loader.exe | GET | 200 | 208.95.112.1:80 | http://208.95.112.1:80/json/ | unknown | — | — | unknown |
4112 | svchost.exe | HEAD | 200 | 151.101.206.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/b649b6c2-4484-495a-96f2-2fd1ee2b66ca?P1=1744554828&P2=404&P3=2&P4=ippr0BBDwA%2f0YeFQxVKJ6YY6a7U4IVdMFBYbAfYR0Iw5pGS0vtTIP%2bp1ircU2P6W%2fp2%2f9MpJSGAesKVLf%2bnmYw%3d%3d | unknown | — | — | whitelisted |
4112 | svchost.exe | GET | 206 | 151.101.206.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/b649b6c2-4484-495a-96f2-2fd1ee2b66ca?P1=1744554828&P2=404&P3=2&P4=ippr0BBDwA%2f0YeFQxVKJ6YY6a7U4IVdMFBYbAfYR0Iw5pGS0vtTIP%2bp1ircU2P6W%2fp2%2f9MpJSGAesKVLf%2bnmYw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7904 | darkx-loader.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
7904 | darkx-loader.exe | 162.159.136.232:443 | discord.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ip-api.com |
| whitelisted |
discord.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
dns.google |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
7904 | darkx-loader.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
7904 | darkx-loader.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
7904 | darkx-loader.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
8104 | darkx-loader.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
8104 | darkx-loader.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
8104 | darkx-loader.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |