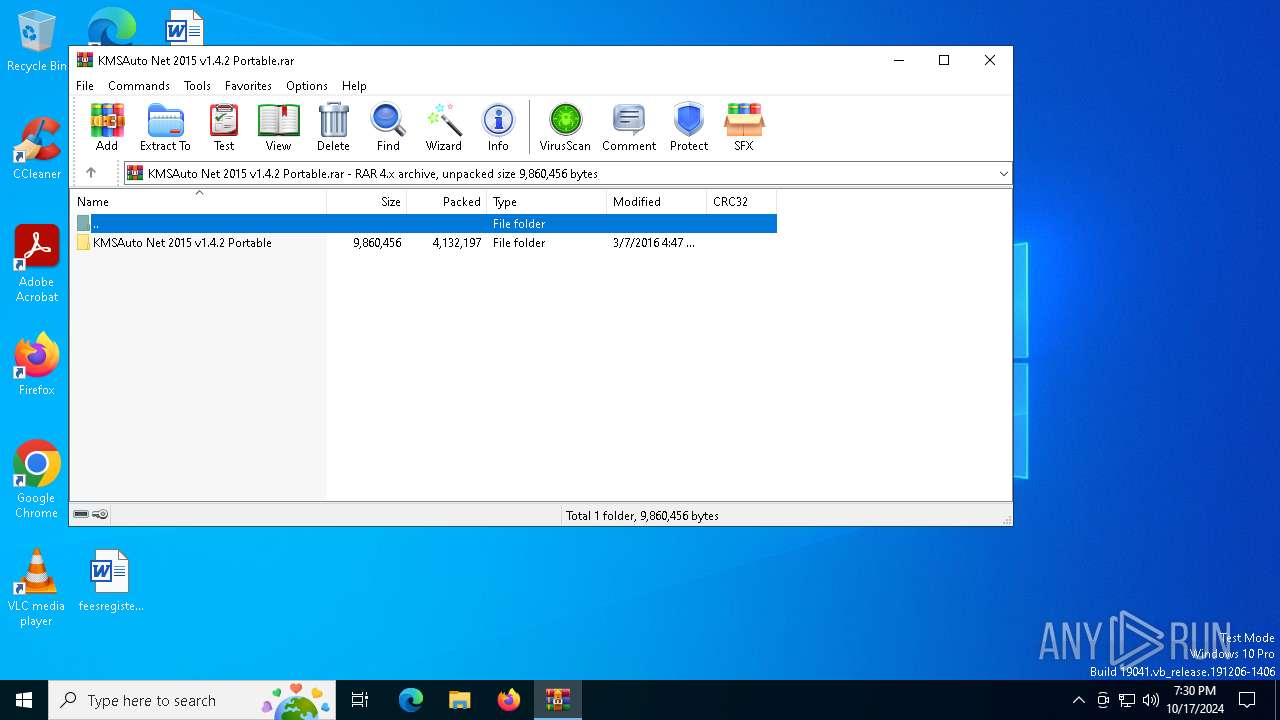
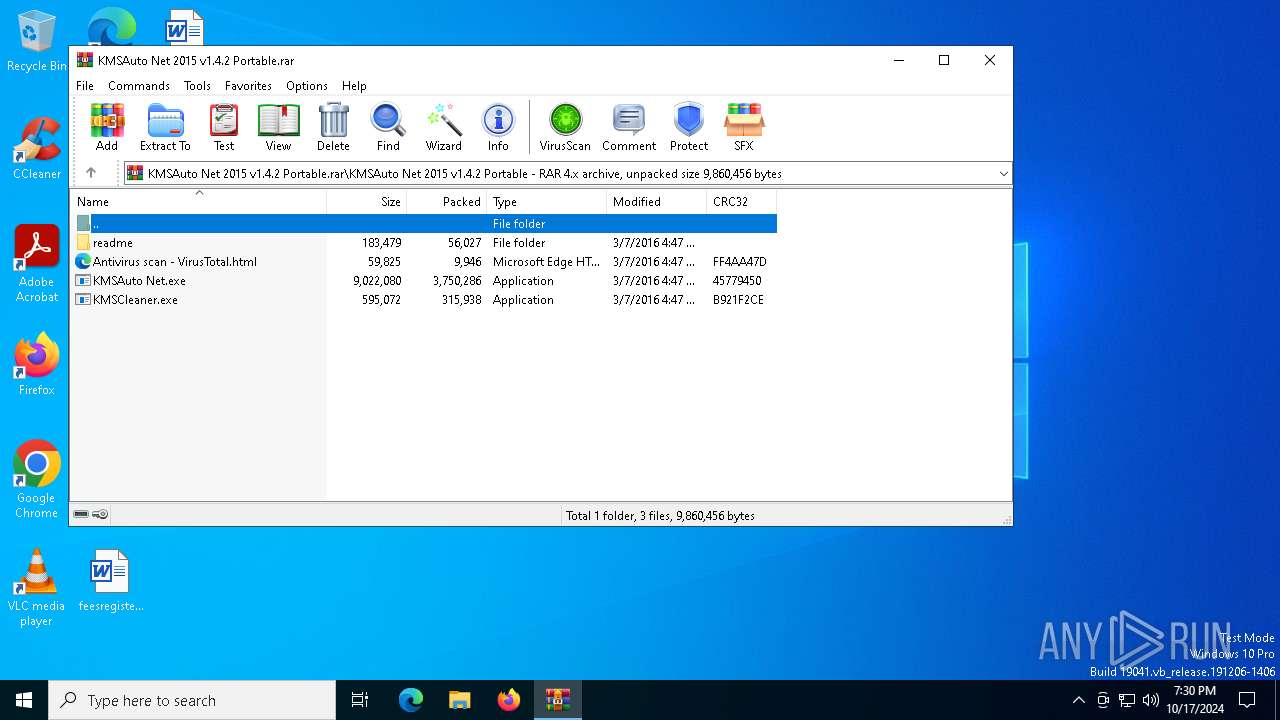
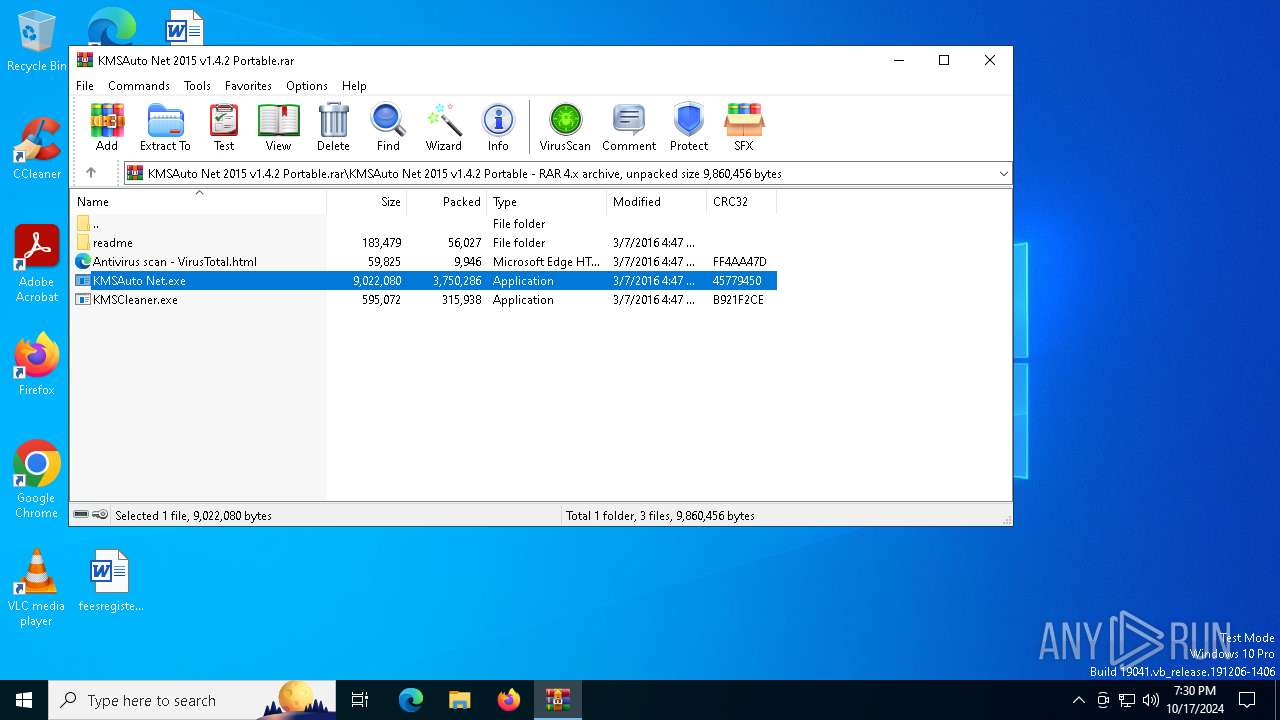
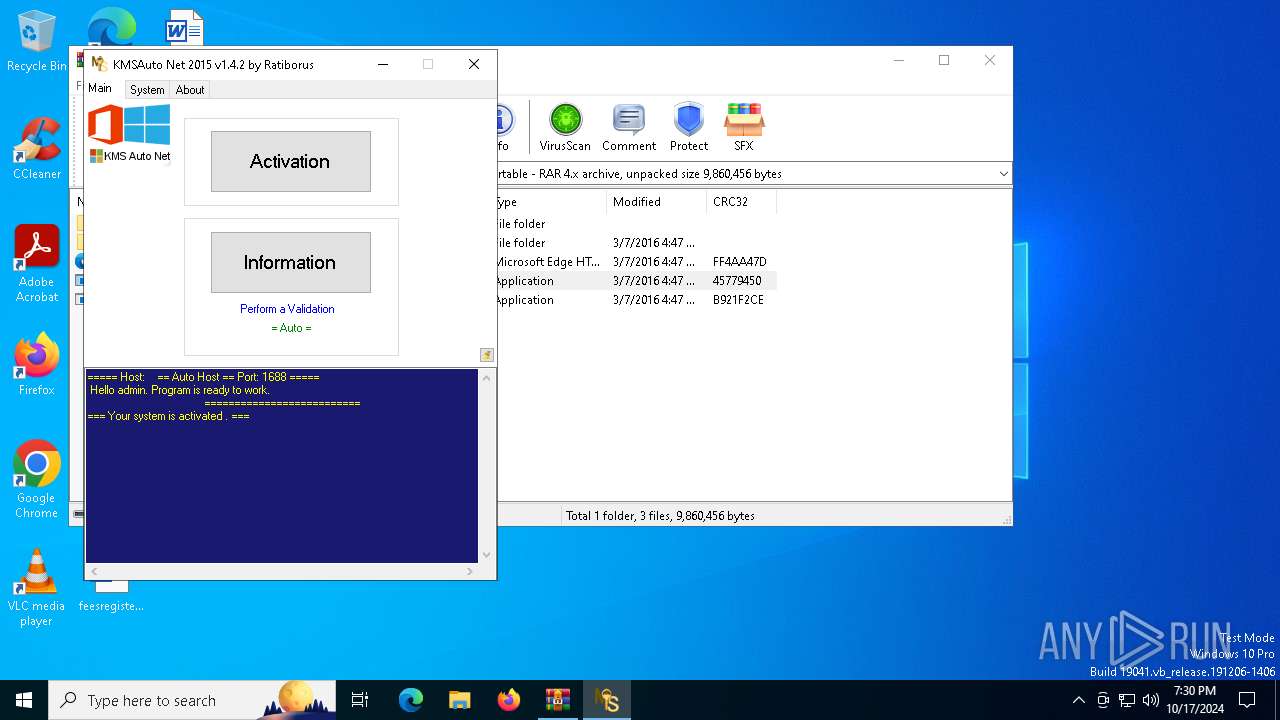
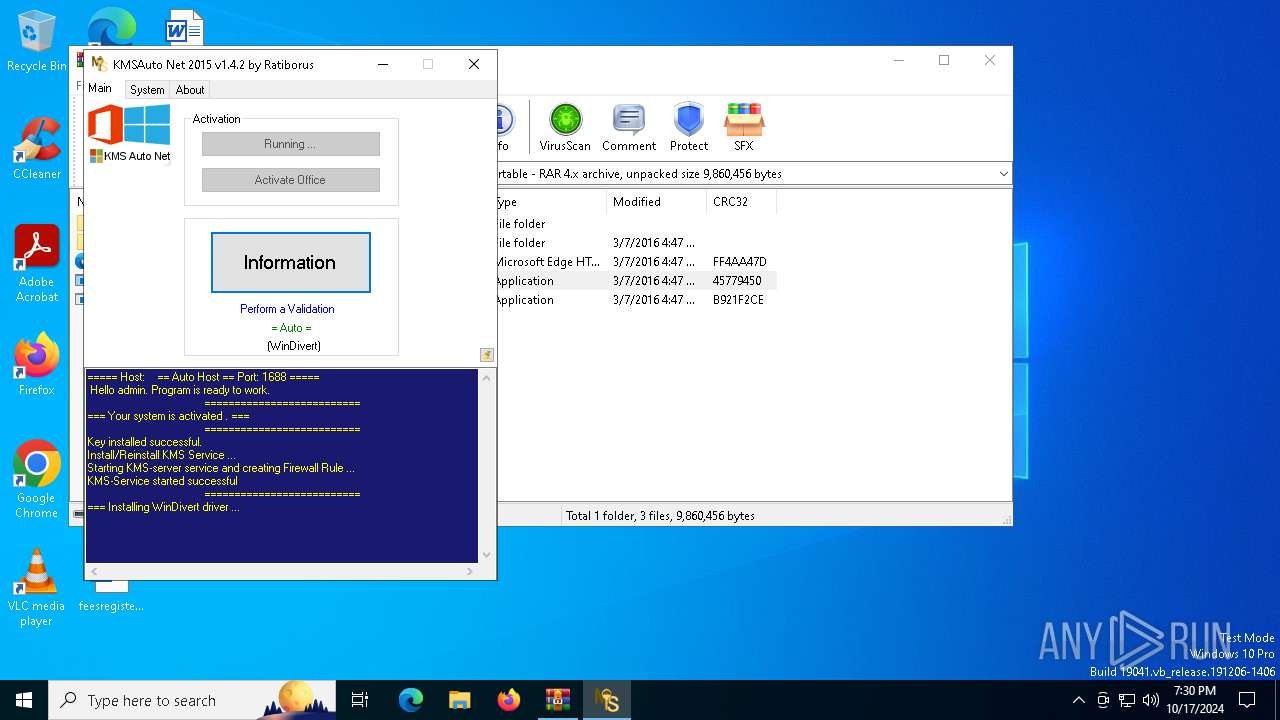
| File name: | KMSAuto Net 2015 v1.4.2 Portable.rar |
| Full analysis: | https://app.any.run/tasks/92bd013e-f740-4cce-a708-a0bfe0adf4c7 |
| Verdict: | Malicious activity |
| Analysis date: | October 17, 2024, 19:30:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 4119E2BF46DD5FB330D75CF24178D29E |
| SHA1: | CF82AF51F2775DF05BFD6B2A60AB9F0E128306C2 |
| SHA256: | 352F6B951561FBDCDD7E944FBBF9464107002BF5BA22DF6462BD964C44D060C0 |
| SSDEEP: | 98304:tDd6slZlnveKWXgYjynYVKXGQUva5SlKbH28fNXTRlsKkgnBGh859yDj4sWqRp5/:eBO4 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4072)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 6348)
Executable content was dropped or overwritten
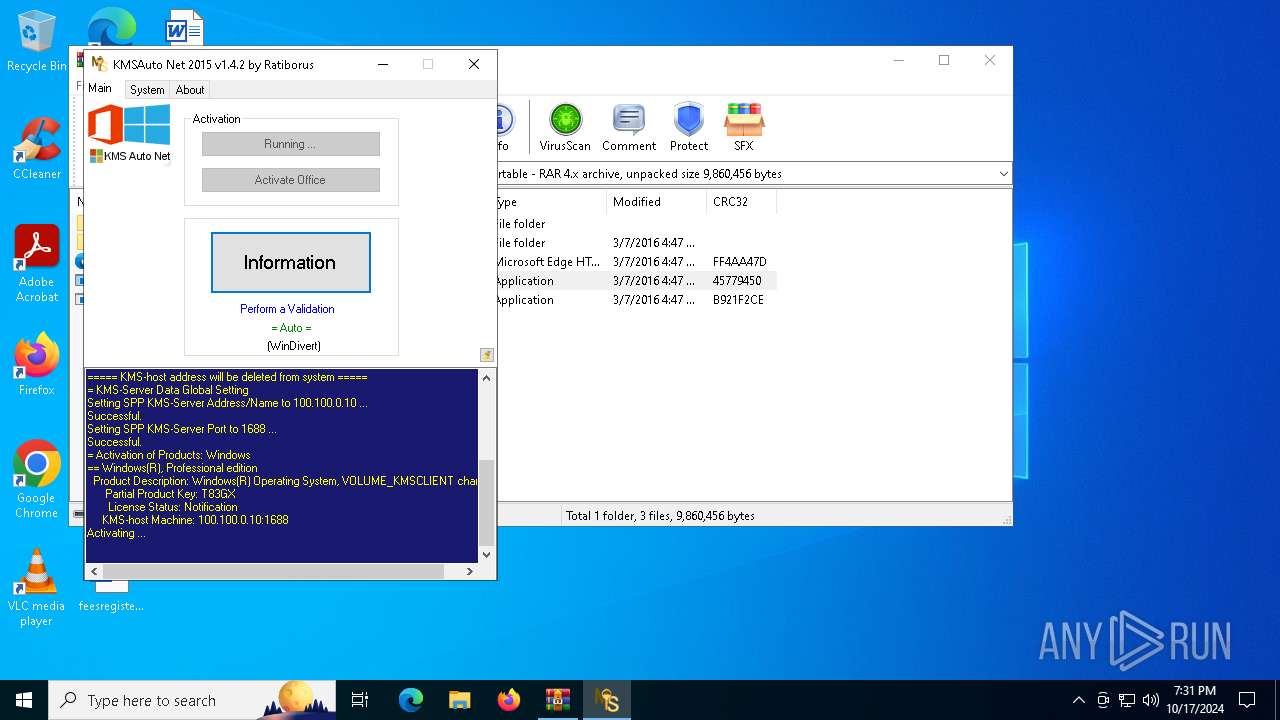
- KMSAuto Net.exe (PID: 4224)
- wzt.dat (PID: 5084)
- bin.dat (PID: 1204)
- AESDecoder.exe (PID: 6100)
- bin_x64.dat (PID: 6864)
The process executes VB scripts
- KMSAuto Net.exe (PID: 4224)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 4224)
- cmd.exe (PID: 6348)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 4224)
Starts application with an unusual extension
- cmd.exe (PID: 4348)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 6940)
Process drops legitimate windows executable
- wzt.dat (PID: 5084)
- bin_x64.dat (PID: 6864)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 4224)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 4224)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 7948)
Executes as Windows Service
- KMSSS.exe (PID: 1204)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 3860)
Uses REG/REGEDIT.EXE to modify registry
- KMSAuto Net.exe (PID: 4224)
- cmd.exe (PID: 7432)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 8036)
Drops a system driver (possible attempt to evade defenses)
- bin_x64.dat (PID: 6864)
INFO
Creates a new folder
- cmd.exe (PID: 5084)
- cmd.exe (PID: 7120)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4072)
Adds a route via ROUTE.EXE
- ROUTE.EXE (PID: 5508)
Deletes a route via ROUTE.EXE
- ROUTE.EXE (PID: 8004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 10037 |
|---|---|
| UncompressedSize: | 59825 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2016:03:07 16:47:12 |
| PackingMethod: | Normal |
| ArchivedFileName: | KMSAuto Net 2015 v1.4.2 Portable\Antivirus scan - VirusTotal.html |
Total processes
239
Monitored processes
99
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | C:\WINDOWS\Sysnative\Netsh Advfirewall Firewall delete rule name="0pen Port KMS" protocol=TCP | C:\Windows\System32\netsh.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | C:\WINDOWS\Sysnative\cmd.exe /D /c certmgr.exe -add wzt.cer -n wzt -s -r localMachine TRUSTEDPUBLISHER | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\WINDOWS\Sysnative\cmd.exe" /c rd "C:\ProgramData\KMSAuto\wzt" /S /Q | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1172 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | bin.dat -y -pkmsauto | C:\ProgramData\KMSAuto\bin.dat | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 15.09 beta Modules
| |||||||||||||||
| 1204 | "C:\ProgramData\KMSAuto\bin\KMSSS.exe" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -AI 43200 -RI 43200 KillProcessOnPort -Log -IP | C:\ProgramData\KMSAuto\bin\KMSSS.exe | — | services.exe | |||||||||||
User: SYSTEM Company: MDL Forum, mod by Ratiborus Integrity Level: SYSTEM Description: KMS Server Emulator Service (XP) Exit code: 0 Version: 1.2.1.0 Modules
| |||||||||||||||
| 1332 | C:\WINDOWS\Sysnative\cmd.exe /D /c del /F /Q "AESDecoder.exe" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 975
Read events
7 958
Write events
13
Delete events
4
Modification events
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAuto Net 2015 v1.4.2 Portable.rar | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1884) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | F81F111D0E5AB58D396F7BF525577FD30FDC95AA |
Value: | |||
| (PID) Process: | (1884) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\F81F111D0E5AB58D396F7BF525577FD30FDC95AA |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000F81F111D0E5AB58D396F7BF525577FD30FDC95AA2000000001000000E8010000308201E43082014DA003020102021008A8E826950F1A9940262589FCAF0B8F300D06092A864886F70D0101040500300E310C300A06035504031303575A54301E170D3135313130383038313534395A170D3339313233313233353935395A300E310C300A06035504031303575A5430819F300D06092A864886F70D010101050003818D0030818902818100A3B38E6E8CD01F282D0872986D29BF5F0EAAD61A32C045D9B23DB1C221C3679770C401DE98695E88CAD621B319730DCABEDF4C4709EEBE8126DD567A9AB387DAB7EA13B3665166464D1B8EFFFED8BC4225515A9AAA170E595EB348A496309110C8EB66D0490F113A3C79A508058448B0398BE6F9D34F84C60E694C472C72F9B70203010001A3433041303F0603551D01043830368010E4E11038D29FC50F20A0C1914BBEFF0BA110300E310C300A06035504031303575A54821008A8E826950F1A9940262589FCAF0B8F300D06092A864886F70D01010405000381810054C251E1B9CDCA11ADE10887278347C178233BFFB85A6D692CA235D68AFE76D59F2113E7C3016AC0347E7131D590047A877083536F61D90FCB2BF95856952ABD4F63DACCFCCC840950667CC68F7513F8AE72DC7676E94B61FA169158457EA2B8531A593671E79D886743E24EDDF7141E0443E22F1F6B16B0A76D720466E4B8E8 | |||
| (PID) Process: | (6772) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates |
| Operation: | delete value | Name: | F81F111D0E5AB58D396F7BF525577FD30FDC95AA |
Value: | |||
| (PID) Process: | (6772) certmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\F81F111D0E5AB58D396F7BF525577FD30FDC95AA |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000F81F111D0E5AB58D396F7BF525577FD30FDC95AA2000000001000000E8010000308201E43082014DA003020102021008A8E826950F1A9940262589FCAF0B8F300D06092A864886F70D0101040500300E310C300A06035504031303575A54301E170D3135313130383038313534395A170D3339313233313233353935395A300E310C300A06035504031303575A5430819F300D06092A864886F70D010101050003818D0030818902818100A3B38E6E8CD01F282D0872986D29BF5F0EAAD61A32C045D9B23DB1C221C3679770C401DE98695E88CAD621B319730DCABEDF4C4709EEBE8126DD567A9AB387DAB7EA13B3665166464D1B8EFFFED8BC4225515A9AAA170E595EB348A496309110C8EB66D0490F113A3C79A508058448B0398BE6F9D34F84C60E694C472C72F9B70203010001A3433041303F0603551D01043830368010E4E11038D29FC50F20A0C1914BBEFF0BA110300E310C300A06035504031303575A54821008A8E826950F1A9940262589FCAF0B8F300D06092A864886F70D01010405000381810054C251E1B9CDCA11ADE10887278347C178233BFFB85A6D692CA235D68AFE76D59F2113E7C3016AC0347E7131D590047A877083536F61D90FCB2BF95856952ABD4F63DACCFCCC840950667CC68F7513F8AE72DC7676E94B61FA169158457EA2B8531A593671E79D886743E24EDDF7141E0443E22F1F6B16B0A76D720466E4B8E8 | |||
Executable files
20
Suspicious files
11
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\KMSAuto Net.exe | executable | |
MD5:311F3BAA9BFA5B2364FEA8B254D15EB9 | SHA256:BEA219F0F08ED083677A0B869E658BA09785F470668EADC659DB2885FA89F3B9 | |||
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\KMSCleaner.exe | executable | |
MD5:13EA767A7BA607744EBEA7409B9F8649 | SHA256:A6E2CDC0E9426D50BD72D866BFC80E0FBA941EFB3AE6D1C564D409F57D1EB117 | |||
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\readme\readme_cn.txt | text | |
MD5:96696900C004588220E720565711EA23 | SHA256:E6B15F6F0E3B2108127B0FE21D52D63159F8414E764740DB6CED08F49CFE556F | |||
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\Antivirus scan - VirusTotal.html | binary | |
MD5:1B0EEBA9D8AFBC767635AC3636D1D833 | SHA256:06A6AA7E6E472CB898413F1B75CFCAD9F92C94E858200E51BB8BF519E148ABBF | |||
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\readme\readme_es.txt | text | |
MD5:669A4A375AF88A440520AD2554ED8D90 | SHA256:A753957192D3E91CA30C2B788B96AE95CD323239BAF4745040C45C3F1BC64024 | |||
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\readme\readme_en.txt | text | |
MD5:CC3B6A890378A4543FB955C1CB943106 | SHA256:BA0F59DAACFADF37D1BBE7293DAE505753B0939DDF3444D64D995AED110EB6FA | |||
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\readme\readme_kms.txt | text | |
MD5:922BFF8450A1F9E5FEF2D130D50F980A | SHA256:D637E76FCED201C2C88CDBF515E8FED0EFD9C12B477776B322164093B02D532B | |||
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\readme\readme_fr.txt | text | |
MD5:2E51FA6A866F4E60FD00B4873172D5F4 | SHA256:C9BEFA23DD0EA4CA56F4C6CC78DC3078B8AD57E61B586C033BA34FDBFBC1F4A4 | |||
| 4072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.24833\KMSAuto Net 2015 v1.4.2 Portable\readme\readme_ru.txt | text | |
MD5:F1E7B5B15040A9E6F576036B3525239F | SHA256:B48F386F8D650ACA34F125669B1EAECD19E505E68C9A6FE7D956F762CA10A251 | |||
| 4224 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\wzt.dat | executable | |
MD5:B41540F62BDE758F2FBB8BD9372CC417 | SHA256:21B5828E9B324690B1AF6352B44C4F668621EE659AB22D525D9AD175F652CB8C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
67
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6384 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6360 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6360 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2376 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6384 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
Process | Message |
|---|---|
FakeClient.exe | WdfCoInstaller: [10/17/2024 19:30.58.266] ReadComponents: WdfSection for Driver Service windivert using KMDF lib version Major 0x1, minor 0x9
|
FakeClient.exe | WdfCoInstaller: [10/17/2024 19:30.58.282] BootApplication: could not open service windivert, error error(1060) The specified service does not exist as an installed service.
|
FakeClient.exe | WdfCoInstaller: [10/17/2024 19:30.58.282] BootApplication: GetStartType error error(87) The parameter is incorrect.
Driver Service name windivert
|