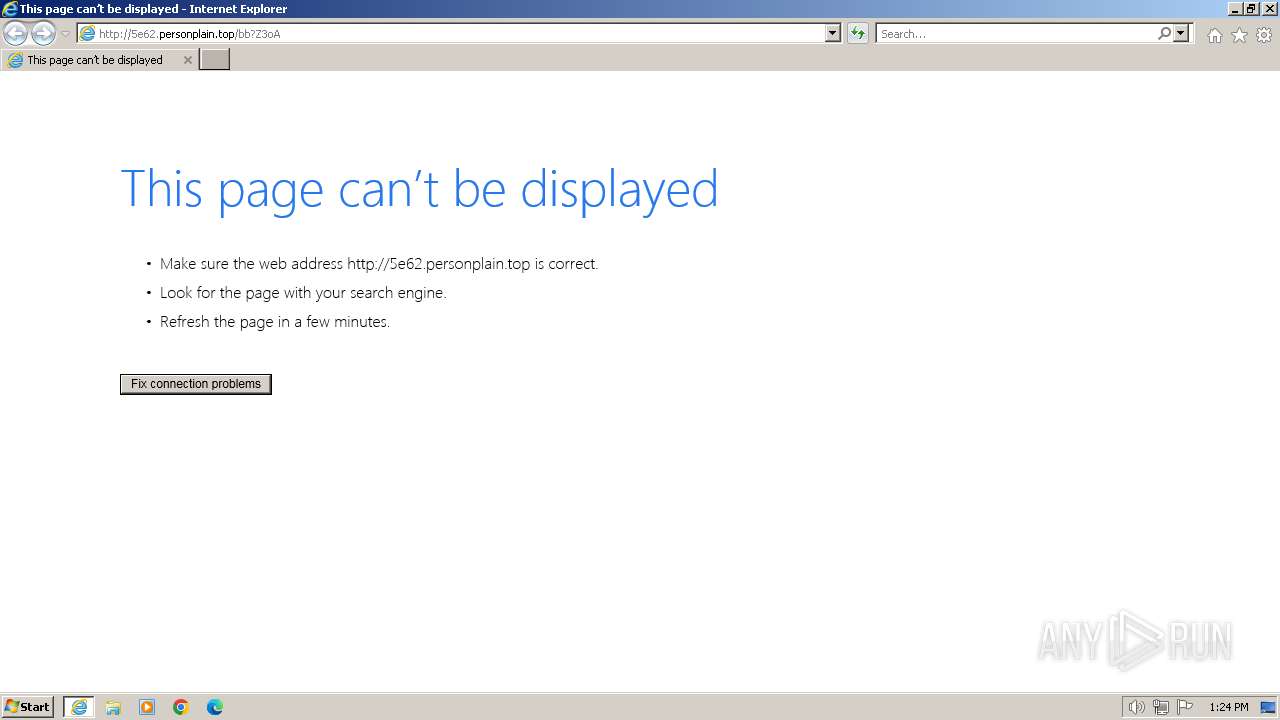
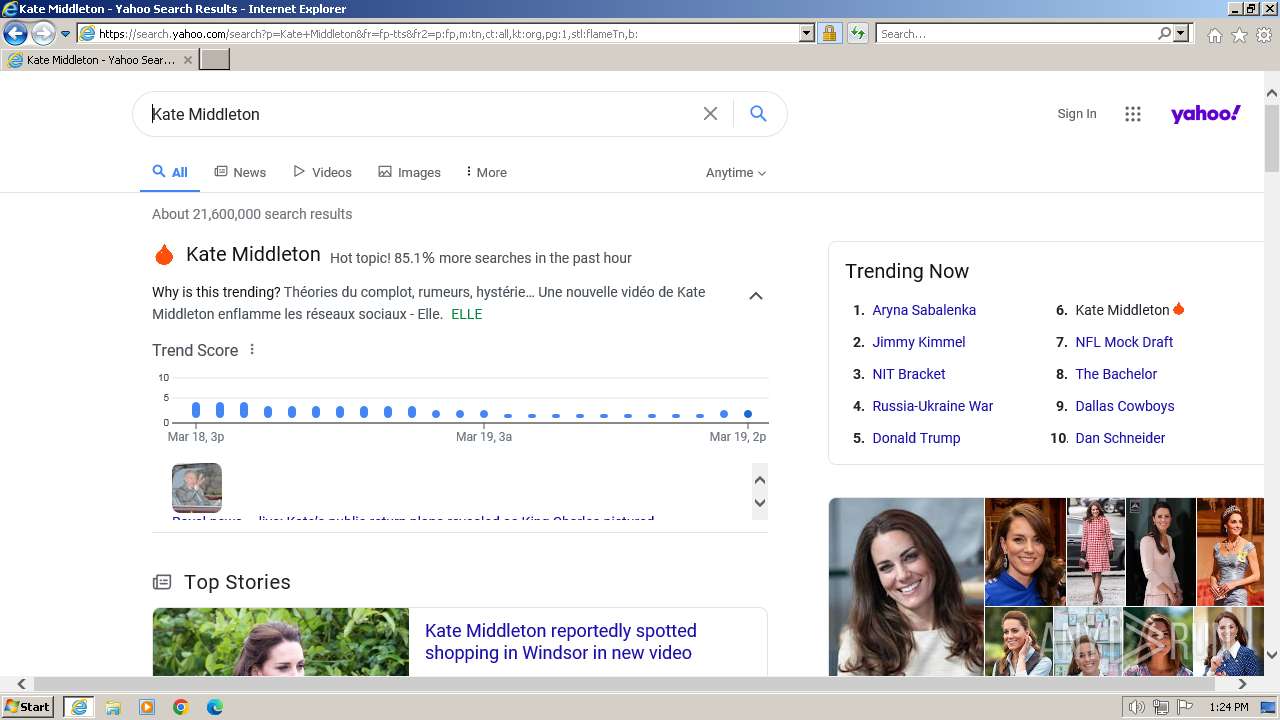
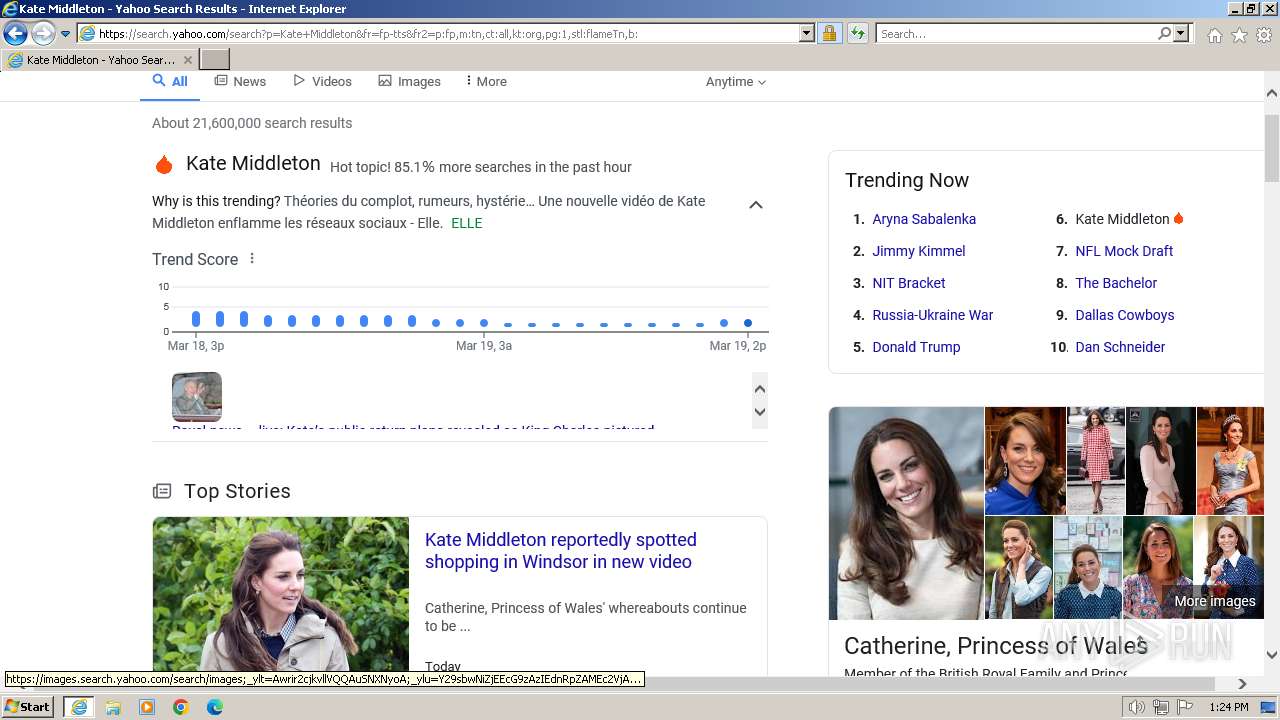
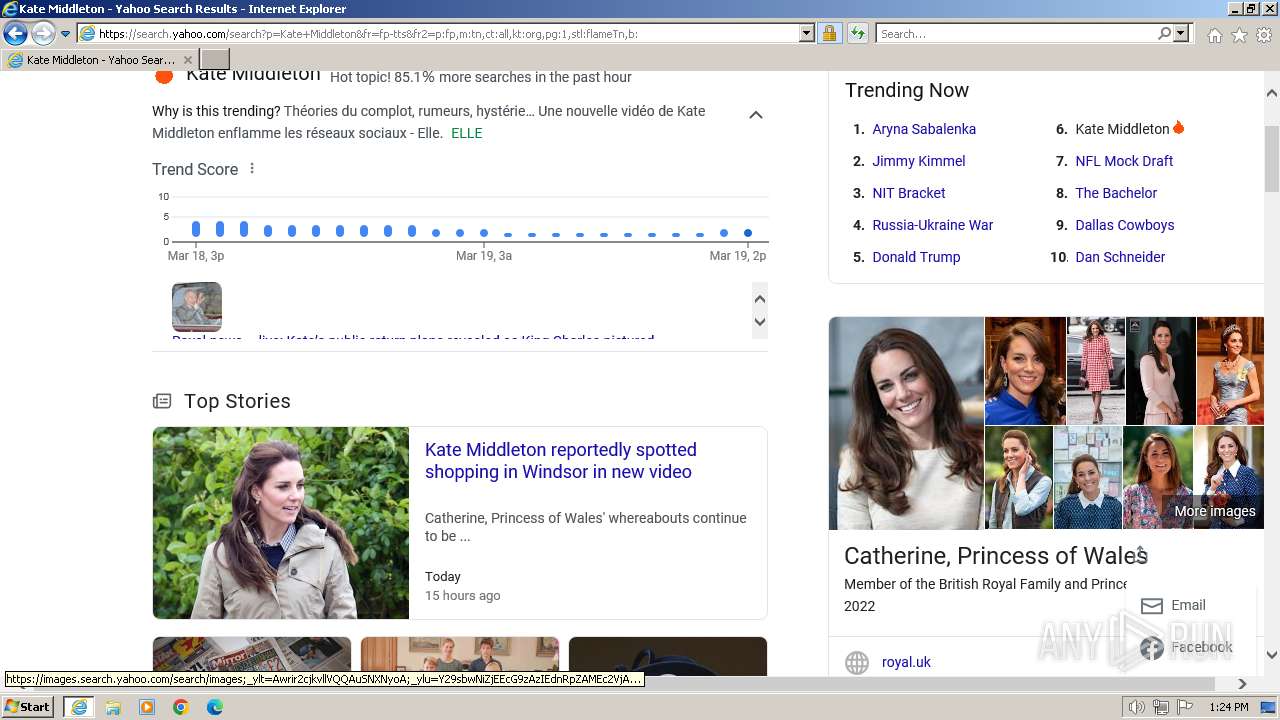
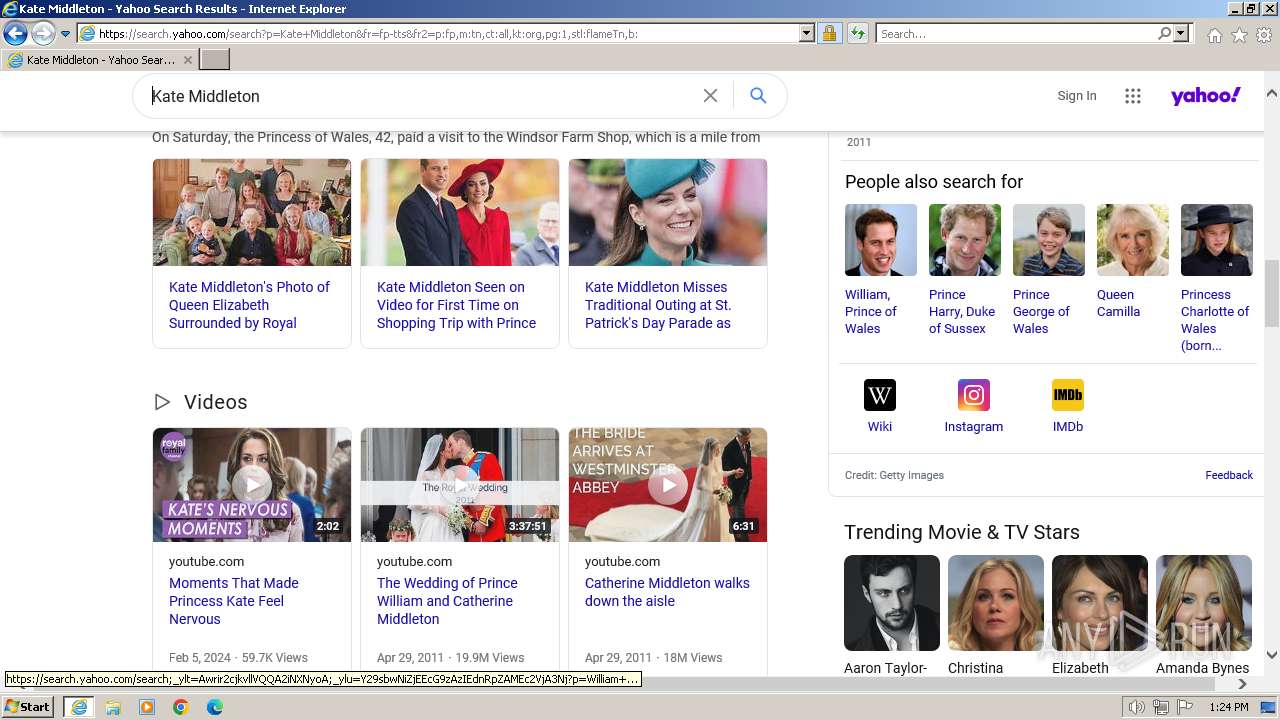
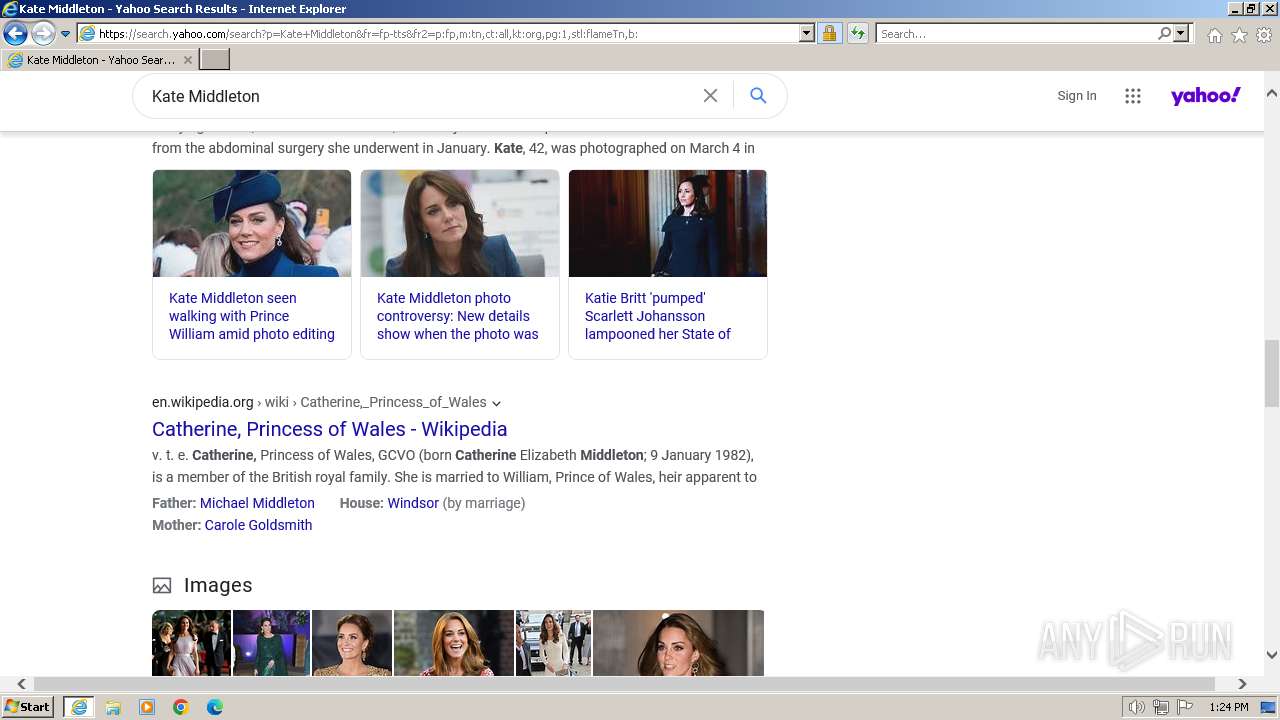
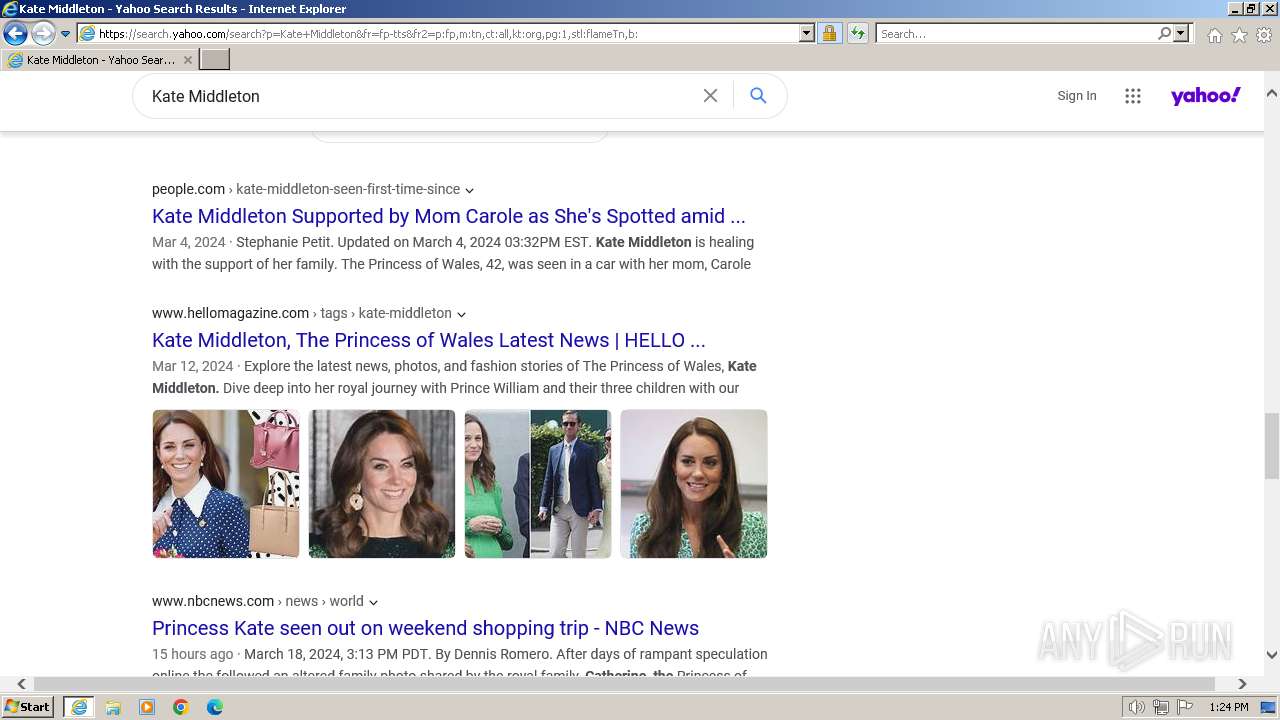
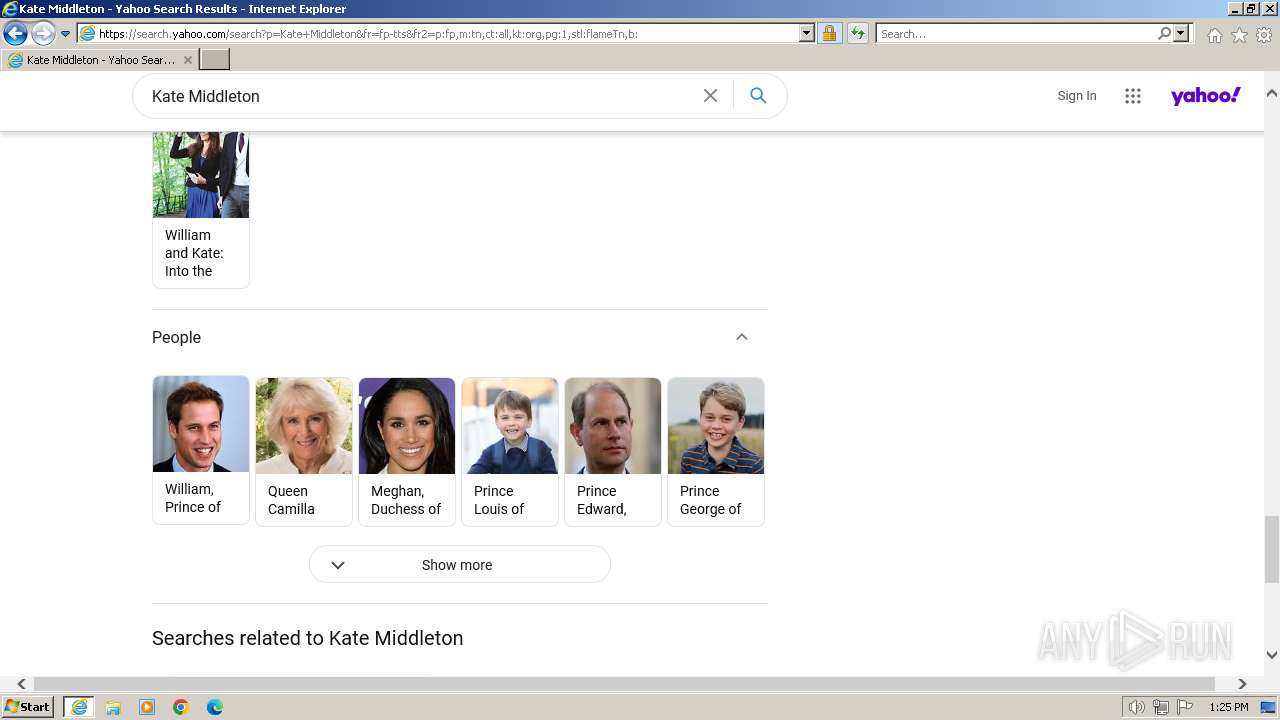
| URL: | http://5e62.personplain.top/bb?Z3oA |
| Full analysis: | https://app.any.run/tasks/f94bf79e-488b-48bb-b6c9-befe0d150c70 |
| Verdict: | Malicious activity |
| Analysis date: | March 19, 2024, 13:21:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 954D4D3B0B87511BAA02F84272F5868A |
| SHA1: | BE9734563D8B1DD59E564766FD662AC0578329F4 |
| SHA256: | 351D81F429F967A3B7490FCDA843F2EB898822D086396B63B984A89327B3B933 |
| SSDEEP: | 3:N1K0vqdtLL0cHSk:C0itLLuk |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads settings of System Certificates
- msdt.exe (PID: 1728)
Process drops legitimate windows executable
- msdt.exe (PID: 1728)
Reads the Internet Settings
- sdiagnhost.exe (PID: 3556)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3028)
Reads the computer name
- wmpnscfg.exe (PID: 3028)
Application launched itself
- iexplore.exe (PID: 3936)
Manual execution by a user
- wmpnscfg.exe (PID: 3028)
Reads security settings of Internet Explorer
- msdt.exe (PID: 1728)
- sdiagnhost.exe (PID: 3556)
Create files in a temporary directory
- msdt.exe (PID: 1728)
Reads the software policy settings
- msdt.exe (PID: 1728)
Creates files or folders in the user directory
- msdt.exe (PID: 1728)
Drops the executable file immediately after the start
- msdt.exe (PID: 1728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1728 | -modal 1114548 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF8F60.tmp -ep NetworkDiagnosticsWeb | C:\Windows\System32\msdt.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 4294967295 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2572 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3936 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3028 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3556 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3936 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://5e62.personplain.top/bb?Z3oA" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
22 451
Read events
22 155
Write events
176
Delete events
120
Modification events
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31095296 | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31095296 | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
24
Text files
216
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3936 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\E6TM8IQ3.txt | text | |
MD5:474242D9B1896790A829B0BB2F953CDF | SHA256:576823C42BCBD7F20B5A43589C42D9564D99D7CEFC14F6050EF7B3941A68C306 | |||
| 3936 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bb[1].htm | html | |
MD5:3D59F0C7B15E7AB286503B5AF634C05F | SHA256:34716FA99018BDBDE7541EA6A58BFE5915D95EA2C106A6E725736DC757AE06BF | |||
| 3936 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\HOY1MYHR.txt | text | |
MD5:2E6879A50E2667F5989636B4FED631A6 | SHA256:E09660BBBA8817A3324C61AD54B7FF894BBA4701A81A5EB284B8E8255A3AB291 | |||
| 3936 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\QQ57SQG0.txt | text | |
MD5:05A0BC36260E559596982B8005443299 | SHA256:C75976EEC19889AFFD6E6250CAF8813C6DE378E29F4AFEF9BF22DAE53EDBD9D2 | |||
| 3936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:BBED5F0EA1A6D0BEE446D00176006812 | SHA256:79ADA8ACABC9BFDFA911DAD118CBA0DE3035AC783D86FB2BDF857413A88E7413 | |||
| 3936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9D6B3FE9E6E4067193F477ABAD990106 | der | |
MD5:EA8332102F630F9C1236CF0851266A45 | SHA256:4541D9339AB605B941805E151345FBC0CA514266FAD7D4AD0A32001124624A02 | |||
| 3936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8A7891822FCFF127E4EADADE9757112B | binary | |
MD5:3C9E30C72D2FC8E05C8132245A983F70 | SHA256:4E084F14923CA24222A4E20AAE3D84323F714F36AE2565EEF4D8D0E49B7E9F3F | |||
| 3936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9D6B3FE9E6E4067193F477ABAD990106 | binary | |
MD5:7AF3E9572987BD031276214CBD258137 | SHA256:10B4F689DAABBC0A373FA2C82548D21FFCBCE3CC39051176ACDD7E31588ECF2E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
129
DNS requests
41
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2572 | iexplore.exe | GET | 301 | 81.94.156.136:80 | http://5e62.personplain.top/bb?Z3oA | unknown | html | 330 b | unknown |
3936 | iexplore.exe | GET | 304 | 23.216.77.75:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bdc5ae628aaf0bd4 | unknown | — | — | unknown |
2572 | iexplore.exe | GET | 301 | 81.94.156.136:80 | http://5e62.personplain.top/bb/?Z3oA | unknown | html | 330 b | unknown |
3936 | iexplore.exe | GET | 304 | 23.216.77.75:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d416ea50f343b89b | unknown | — | — | unknown |
3936 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootG2.crl | unknown | binary | 1.14 Kb | unknown |
3936 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootG3.crl | unknown | binary | 863 b | unknown |
1080 | svchost.exe | GET | 200 | 23.53.40.82:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d24e253035548135 | unknown | compressed | 67.5 Kb | unknown |
2572 | iexplore.exe | GET | 301 | 81.94.156.136:80 | http://5e62.personplain.top/bb/?Z3oA | unknown | — | — | unknown |
2572 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | unknown | binary | 471 b | unknown |
2572 | iexplore.exe | GET | 301 | 81.94.156.136:80 | http://5e62.personplain.top/bb/?Z3oA | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2572 | iexplore.exe | 81.94.156.136:80 | 5e62.personplain.top | OOO WestCall Ltd. | RU | unknown |
3936 | iexplore.exe | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3936 | iexplore.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3936 | iexplore.exe | 23.216.77.45:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3936 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3936 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3936 | iexplore.exe | 104.126.37.161:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
5e62.personplain.top |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dns.msftncsi.com |
| shared |
crl3.digicert.com |
| whitelisted |
yahoo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2572 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2572 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2572 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |