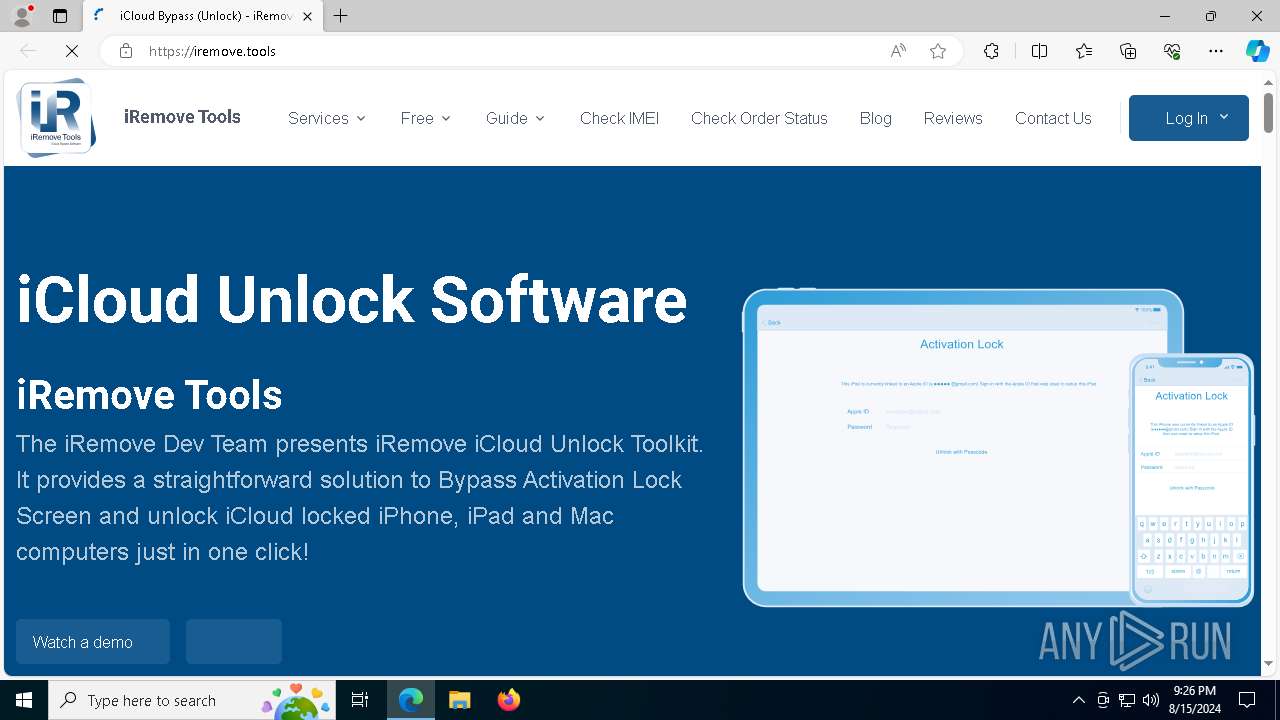
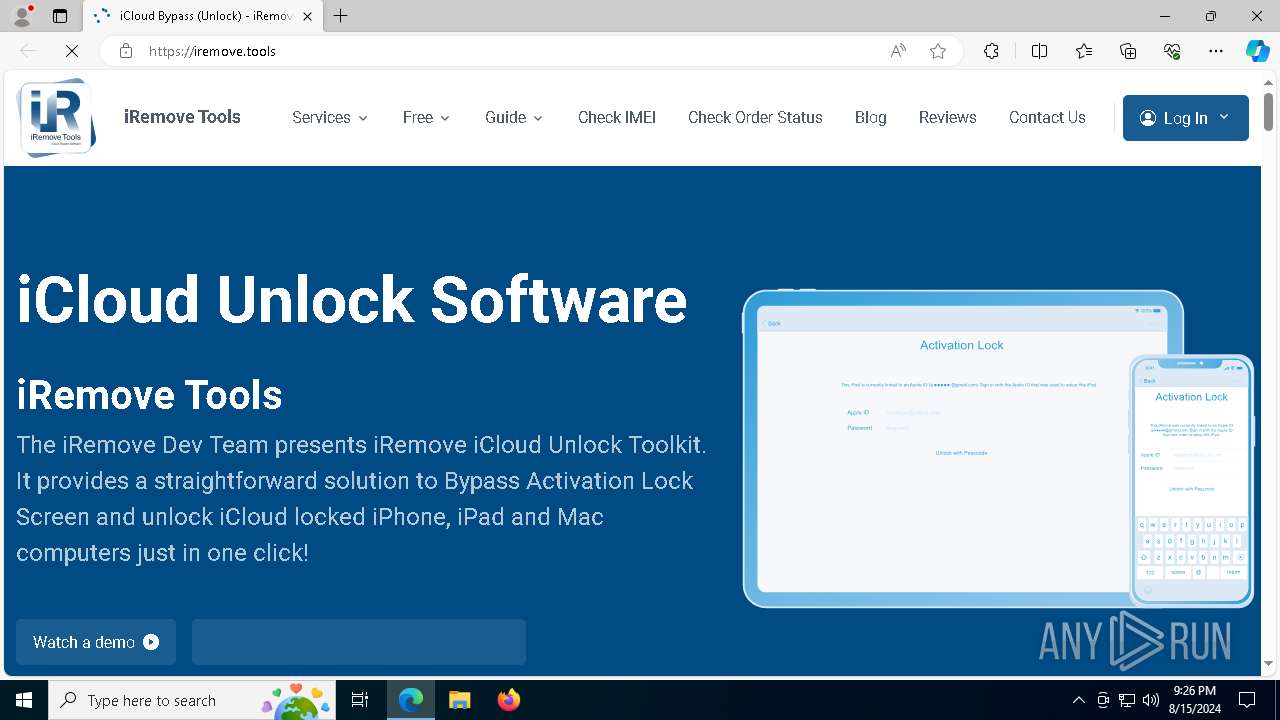
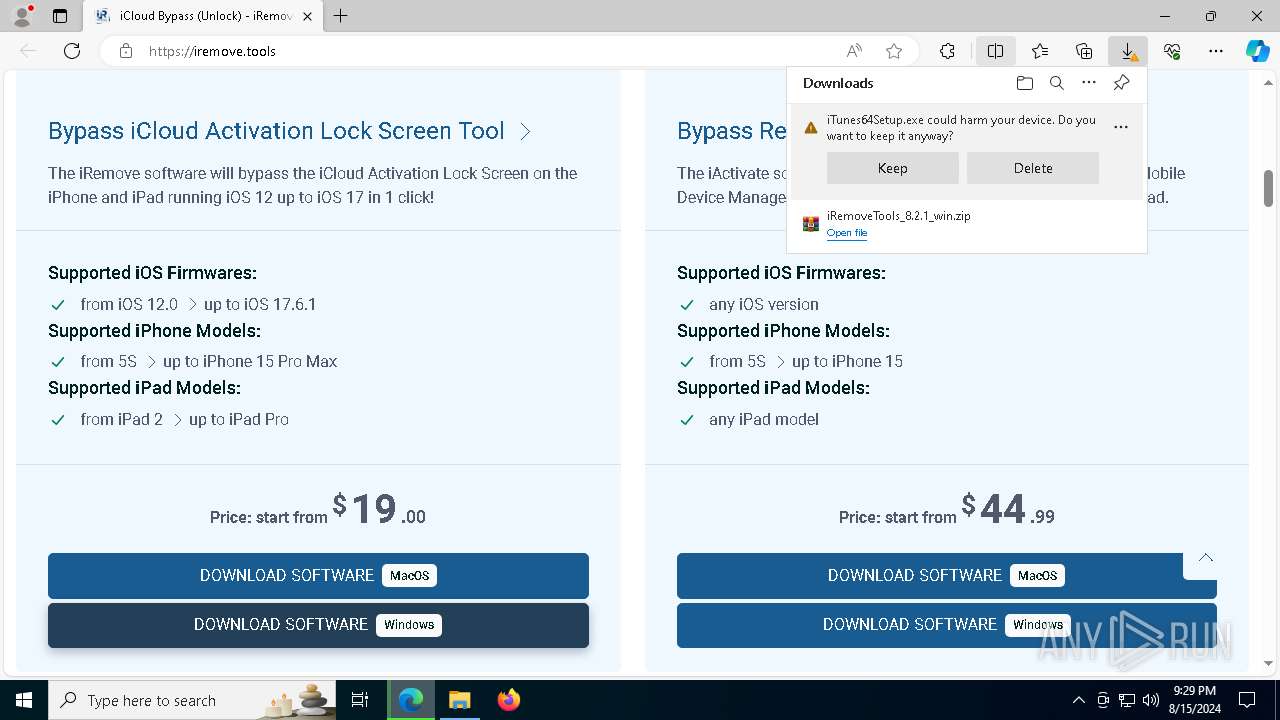
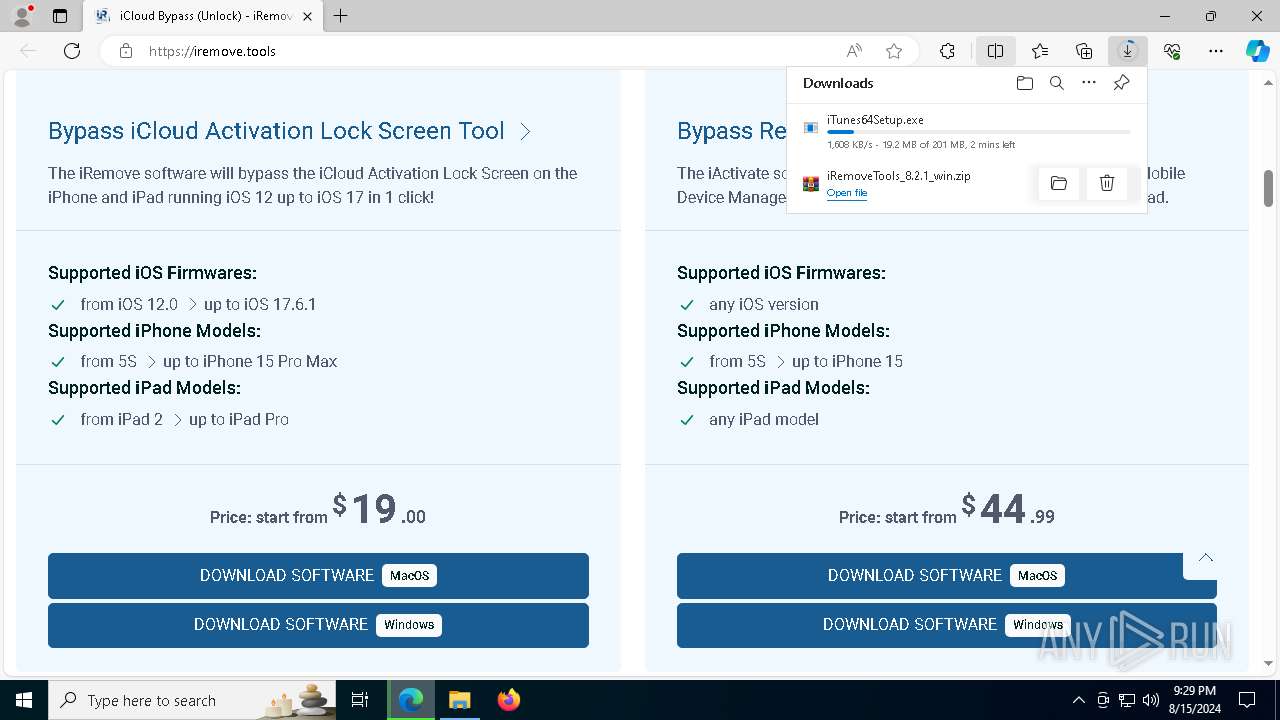
| URL: | https://iremove.tools/ |
| Full analysis: | https://app.any.run/tasks/8a804c78-c2ff-4f8a-8dcf-6506156a5f80 |
| Verdict: | Malicious activity |
| Analysis date: | August 15, 2024, 21:26:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 6DB1BE81E658B3C76CABD3BEE9AFD037 |
| SHA1: | 944179D78E750B1A17FC3F3327EFB0460D5E38C9 |
| SHA256: | 351D0295302B725AD3E72D0EBE4FBC7033C8F2A84B1345A1D6A1CD078F79EA37 |
| SSDEEP: | 3:N85IIa:2Ba |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- iRemove Tools.exe (PID: 7872)
- iRemove Tools.exe (PID: 4644)
- MSIB706.tmp (PID: 6212)
- msiexec.exe (PID: 8152)
- iRemove Tools.exe (PID: 1680)
Checks Windows Trust Settings
- iRemove Tools.exe (PID: 7872)
- msiexec.exe (PID: 7976)
- iRemove Tools.exe (PID: 4644)
- iRemove Tools.exe (PID: 1680)
Executable content was dropped or overwritten
- iRemove Tools.exe (PID: 7872)
- iRemove Tools.exe (PID: 4644)
- iRemove Tools.exe (PID: 1680)
- drvinst.exe (PID: 3104)
Drops the executable file immediately after the start
- iRemove Tools.exe (PID: 7872)
- msiexec.exe (PID: 8152)
- iRemove Tools.exe (PID: 4644)
- msiexec.exe (PID: 7976)
- msiexec.exe (PID: 7496)
- iRemove Tools.exe (PID: 1680)
- drvinst.exe (PID: 3104)
Process drops legitimate windows executable
- iRemove Tools.exe (PID: 7872)
- msiexec.exe (PID: 8152)
- iRemove Tools.exe (PID: 4644)
- msiexec.exe (PID: 7496)
- msiexec.exe (PID: 7976)
The process drops C-runtime libraries
- msiexec.exe (PID: 8152)
- msiexec.exe (PID: 7496)
- msiexec.exe (PID: 7976)
Reads Internet Explorer settings
- iRemove Tools.exe (PID: 7872)
Application launched itself
- iRemove Tools.exe (PID: 7872)
- cmd.exe (PID: 2572)
- cmd.exe (PID: 876)
Reads the date of Windows installation
- iRemove Tools.exe (PID: 7872)
- MSIB706.tmp (PID: 6212)
- msiexec.exe (PID: 8152)
Reads the Windows owner or organization settings
- iRemove Tools.exe (PID: 7872)
- iRemove Tools.exe (PID: 4644)
- msiexec.exe (PID: 7976)
Executes as Windows Service
- VSSVC.exe (PID: 2464)
Adds/modifies Windows certificates
- certutil.exe (PID: 7312)
- msiexec.exe (PID: 7976)
The process creates files with name similar to system file names
- msiexec.exe (PID: 7976)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 7976)
- drvinst.exe (PID: 3104)
- iRemove Tools.exe (PID: 1680)
Reads the BIOS version
- iRemove Tools.exe (PID: 1680)
Executing commands from a ".bat" file
- iRemove Tools.exe (PID: 7872)
- cmd.exe (PID: 2572)
- cmd.exe (PID: 876)
Starts CMD.EXE for commands execution
- iRemove Tools.exe (PID: 7872)
- cmd.exe (PID: 876)
- cmd.exe (PID: 2572)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2572)
- cmd.exe (PID: 876)
Creates files in the driver directory
- drvinst.exe (PID: 3104)
INFO
Creates files or folders in the user directory
- iRemove Tools.exe (PID: 7872)
- iRemove Tools.exe (PID: 1680)
Reads Environment values
- identity_helper.exe (PID: 7208)
- iRemove Tools.exe (PID: 7872)
- msiexec.exe (PID: 8152)
- iRemove Tools.exe (PID: 4644)
- msiexec.exe (PID: 7496)
- iRemove Tools.exe (PID: 1680)
The process uses the downloaded file
- WinRAR.exe (PID: 1248)
- msedge.exe (PID: 6192)
Reads the computer name
- identity_helper.exe (PID: 7208)
- iRemove Tools.exe (PID: 7872)
- msiexec.exe (PID: 7976)
- msiexec.exe (PID: 8152)
- iRemove Tools.exe (PID: 4644)
- msiexec.exe (PID: 7496)
- MSIB706.tmp (PID: 6212)
- msiexec.exe (PID: 5140)
- iRemove Tools.exe (PID: 1680)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6396)
Manual execution by a user
- WinRAR.exe (PID: 1248)
- iRemove Tools.exe (PID: 7872)
Checks supported languages
- identity_helper.exe (PID: 7208)
- iRemove Tools.exe (PID: 7872)
- msiexec.exe (PID: 7976)
- msiexec.exe (PID: 8152)
- iRemove Tools.exe (PID: 4644)
- msiexec.exe (PID: 7496)
- MSIB706.tmp (PID: 6212)
- msiexec.exe (PID: 5140)
- iRemove Tools.exe (PID: 1680)
- drvinst.exe (PID: 3104)
Reads the software policy settings
- iRemove Tools.exe (PID: 7872)
- iRemove Tools.exe (PID: 4644)
- msiexec.exe (PID: 7976)
- iRemove Tools.exe (PID: 1680)
- drvinst.exe (PID: 3104)
Reads the machine GUID from the registry
- iRemove Tools.exe (PID: 7872)
- msiexec.exe (PID: 7976)
- iRemove Tools.exe (PID: 4644)
- iRemove Tools.exe (PID: 1680)
- drvinst.exe (PID: 3104)
Create files in a temporary directory
- iRemove Tools.exe (PID: 7872)
- msiexec.exe (PID: 8152)
- iRemove Tools.exe (PID: 4644)
- msiexec.exe (PID: 7496)
- iRemove Tools.exe (PID: 1680)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8152)
- msiexec.exe (PID: 7976)
- msiexec.exe (PID: 7496)
- msedge.exe (PID: 6396)
Process checks computer location settings
- iRemove Tools.exe (PID: 7872)
- MSIB706.tmp (PID: 6212)
- msiexec.exe (PID: 8152)
Application launched itself
- msedge.exe (PID: 6396)
Starts application with an unusual extension
- msiexec.exe (PID: 7976)
Creates a software uninstall entry
- msiexec.exe (PID: 7976)
Process checks whether UAC notifications are on
- iRemove Tools.exe (PID: 1680)
Checks proxy server information
- iRemove Tools.exe (PID: 1680)
Reads product name
- iRemove Tools.exe (PID: 1680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
225
Monitored processes
82
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\EXEE882.bat" " | C:\Windows\SysWOW64\cmd.exe | — | iRemove Tools.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4416 --field-trial-handle=2332,i,18041676812586620162,13296417863087059714,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\system32\cmd.exe /S /D /c" cls" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | C:\WINDOWS\System32\attrib.exe -r "\\?\C:\Users\admin\AppData\Roaming\IREMOV~1\IREMOV~1.1\install\IREMOV~1.MSI" | C:\Windows\SysWOW64\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\iRemoveTools_8.2.1_win.zip" C:\Users\admin\Downloads\iRemoveTools_8.2.1_win\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1372 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6696 --field-trial-handle=2332,i,18041676812586620162,13296417863087059714,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1656 | C:\WINDOWS\system32\cmd.exe /S /D /c" cls" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1680 | "C:\Program Files (x86)\iRemoveTools\iRemove Tools\iRemove Tools.exe" | C:\Program Files (x86)\iRemoveTools\iRemove Tools\iRemove Tools.exe | msiexec.exe | ||||||||||||
User: admin Company: iRemove Tools Integrity Level: HIGH Description: iRemove Tools Exit code: 0 Version: 8.2.1 Modules
| |||||||||||||||
| 2400 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=6768 --field-trial-handle=2332,i,18041676812586620162,13296417863087059714,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
41 256
Read events
40 522
Write events
702
Delete events
32
Modification events
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6396) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
188
Suspicious files
336
Text files
135
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe55ec.TMP | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFe55fb.TMP | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFe55fb.TMP | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFe55fb.TMP | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe55fb.TMP | — | |
MD5:— | SHA256:— | |||
| 6396 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
176
DNS requests
197
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4344 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4344 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7784 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7740 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5656 | svchost.exe | HEAD | 200 | 217.20.57.35:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724202964&P2=404&P3=2&P4=E6oHnDktvZidM739Ge0CbEzCF3IF9EoIhHam9j8sTQ%2fAhCmotmq8BXa7sHrALVSod7LsX2BnnRQhwlbZ8WmvNA%3d%3d | unknown | — | — | whitelisted |
5656 | svchost.exe | GET | 206 | 217.20.57.35:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724202964&P2=404&P3=2&P4=E6oHnDktvZidM739Ge0CbEzCF3IF9EoIhHam9j8sTQ%2fAhCmotmq8BXa7sHrALVSod7LsX2BnnRQhwlbZ8WmvNA%3d%3d | unknown | — | — | whitelisted |
5656 | svchost.exe | GET | 206 | 217.20.57.35:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724202964&P2=404&P3=2&P4=E6oHnDktvZidM739Ge0CbEzCF3IF9EoIhHam9j8sTQ%2fAhCmotmq8BXa7sHrALVSod7LsX2BnnRQhwlbZ8WmvNA%3d%3d | unknown | — | — | whitelisted |
5656 | svchost.exe | GET | 206 | 217.20.57.35:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724202964&P2=404&P3=2&P4=E6oHnDktvZidM739Ge0CbEzCF3IF9EoIhHam9j8sTQ%2fAhCmotmq8BXa7sHrALVSod7LsX2BnnRQhwlbZ8WmvNA%3d%3d | unknown | — | — | whitelisted |
5656 | svchost.exe | GET | 206 | 217.20.57.35:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724202964&P2=404&P3=2&P4=E6oHnDktvZidM739Ge0CbEzCF3IF9EoIhHam9j8sTQ%2fAhCmotmq8BXa7sHrALVSod7LsX2BnnRQhwlbZ8WmvNA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4936 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3720 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6728 | msedge.exe | 188.114.96.3:443 | iremove.tools | — | — | unknown |
6396 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6728 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6728 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6728 | msedge.exe | 151.101.129.229:443 | cdn.jsdelivr.net | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
iremove.tools |
| unknown |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |