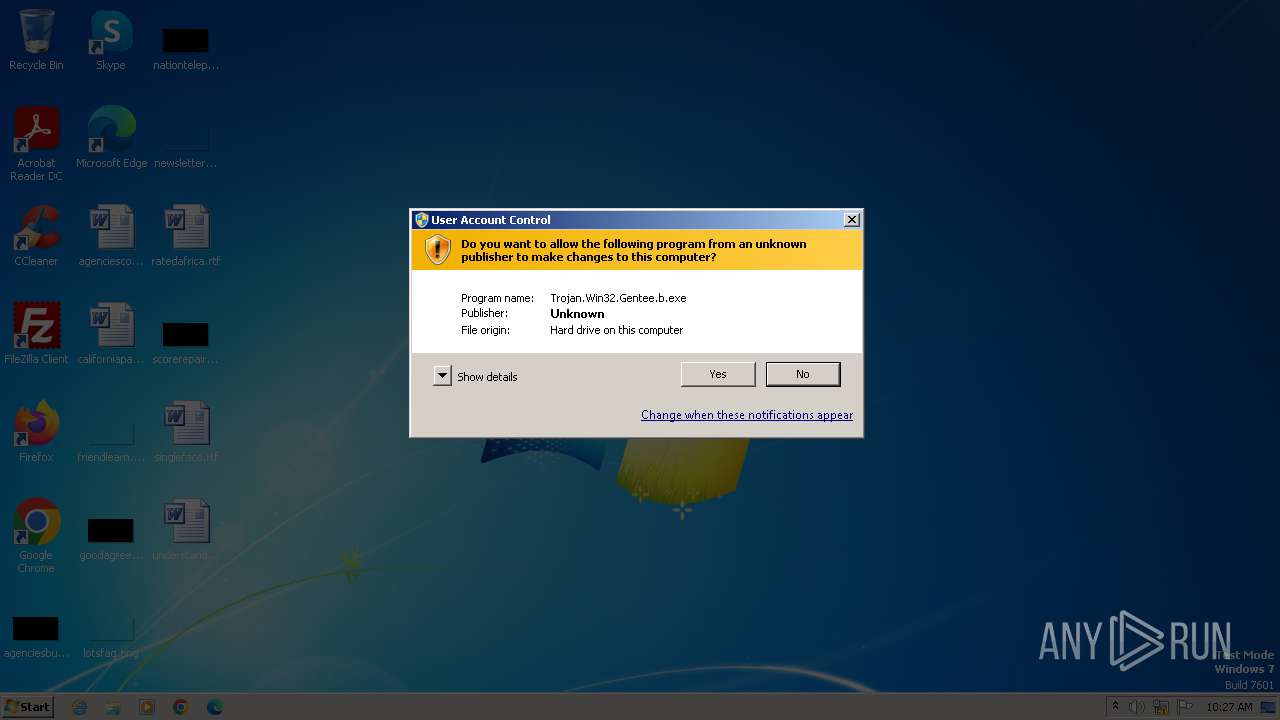
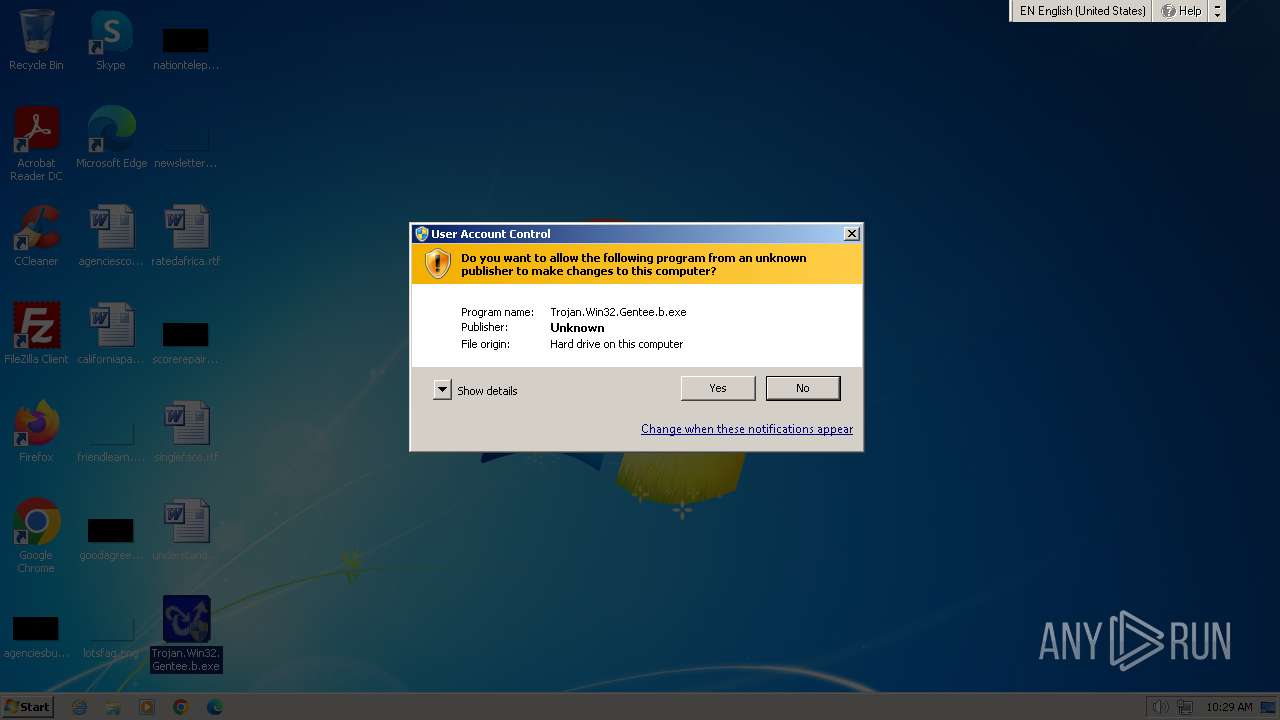
| File name: | Trojan.Win32.Gentee.b |
| Full analysis: | https://app.any.run/tasks/c92fe994-7a98-47a0-a671-ca33529e69be |
| Verdict: | Malicious activity |
| Analysis date: | November 25, 2024, 10:27:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 86E63BB63F3BAF48AD3BF24C3F5B7E40 |
| SHA1: | 70C89810AAA341125859444F57C6DD2480AE377D |
| SHA256: | 3512173E7B8B6579301463C687198ED83D8357A28E0FCF3E7F689D2C3ABA735E |
| SSDEEP: | 3072:4tkqwVQYGbAjv1+UVfBTPxGR0DKrhfGStDFsj:4j8MbAjtpVB0RUCfnDqj |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process executes via Task Scheduler
- sipnotify.exe (PID: 1580)
- ctfmon.exe (PID: 1416)
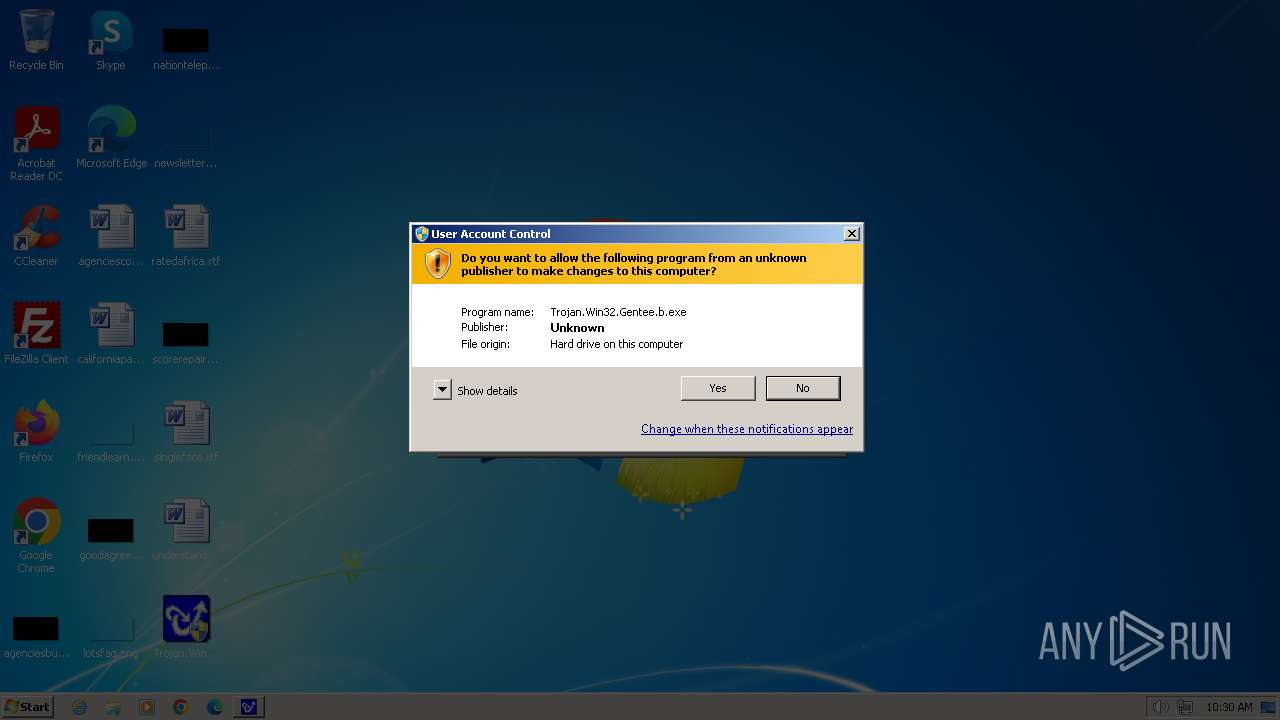
Executable content was dropped or overwritten
- Trojan.Win32.Gentee.b.exe (PID: 1776)
- Trojan.Win32.Gentee.b.exe (PID: 2728)
INFO
Create files in a temporary directory
- Trojan.Win32.Gentee.b.exe (PID: 1776)
Manual execution by a user
- IMEKLMG.EXE (PID: 2072)
- Trojan.Win32.Gentee.b.exe (PID: 2280)
- IMEKLMG.EXE (PID: 2080)
- wmpnscfg.exe (PID: 2432)
- Trojan.Win32.Gentee.b.exe (PID: 2728)
- Trojan.Win32.Gentee.b.exe (PID: 2764)
- wmpnscfg.exe (PID: 2408)
- wmpnscfg.exe (PID: 3040)
- Trojan.Win32.Gentee.b.exe (PID: 2980)
Checks supported languages
- Trojan.Win32.Gentee.b.exe (PID: 1776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.3) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2002:02:27 09:51:35+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 3 |
| CodeSize: | 2560 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1001 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
99
Monitored processes
13
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1416 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1580 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1776 | "C:\Users\admin\Desktop\Trojan.Win32.Gentee.b.exe" | C:\Users\admin\Desktop\Trojan.Win32.Gentee.b.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\Desktop\Trojan.Win32.Gentee.b.exe" | C:\Users\admin\Desktop\Trojan.Win32.Gentee.b.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2080 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2280 | "C:\Users\admin\Desktop\Trojan.Win32.Gentee.b.exe" | C:\Users\admin\Desktop\Trojan.Win32.Gentee.b.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\Desktop\Trojan.Win32.Gentee.b.exe" | C:\Users\admin\Desktop\Trojan.Win32.Gentee.b.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
3 847
Read events
3 830
Write events
16
Delete events
1
Modification events
| (PID) Process: | (2072) IMEKLMG.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEJP\14.0 |
| Operation: | write | Name: | SetPreload |
Value: 1 | |||
| (PID) Process: | (2080) IMEKLMG.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEKR\14.0 |
| Operation: | write | Name: | SetPreload |
Value: 1 | |||
| (PID) Process: | (1416) ctfmon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | internat.exe |
Value: | |||
| (PID) Process: | (1580) sipnotify.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
220
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
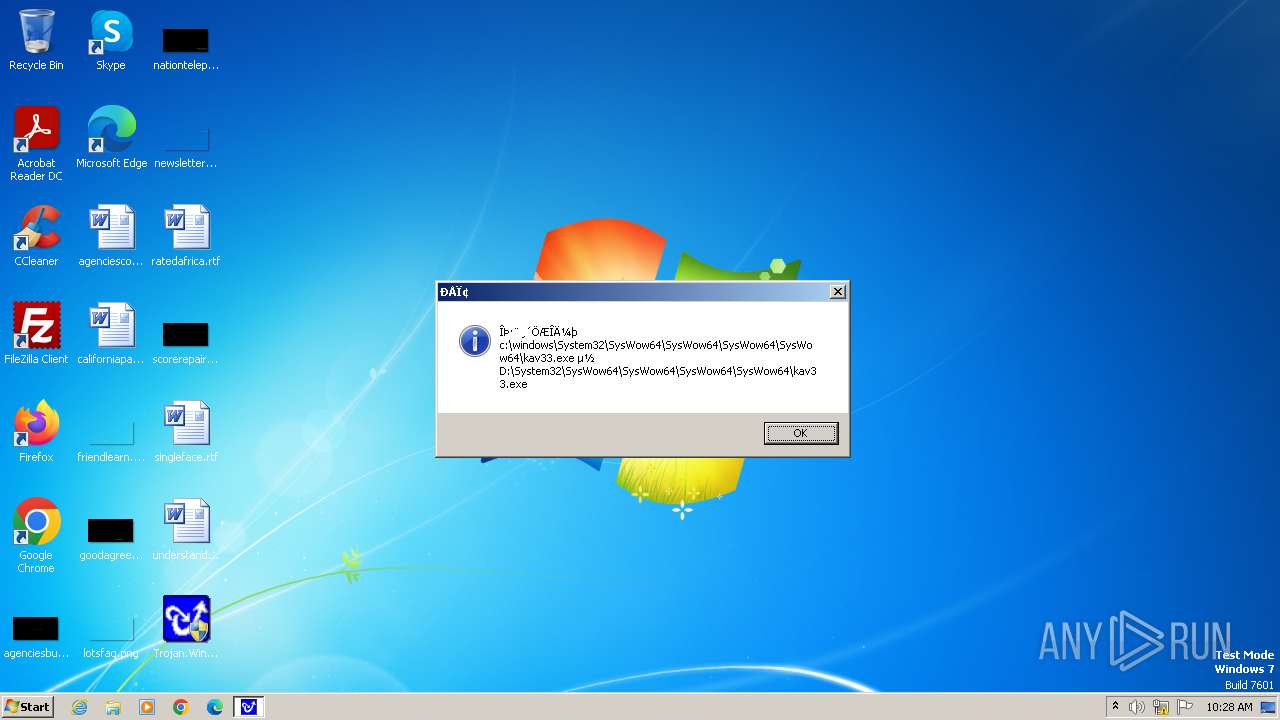
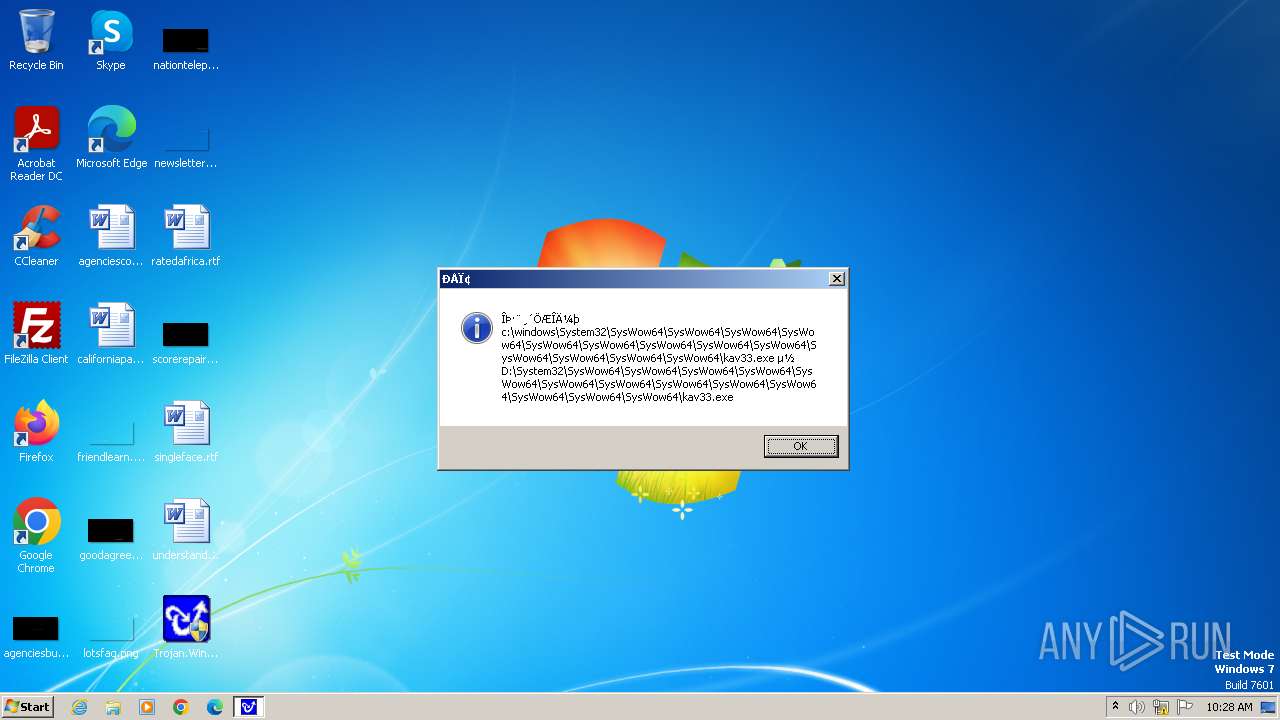
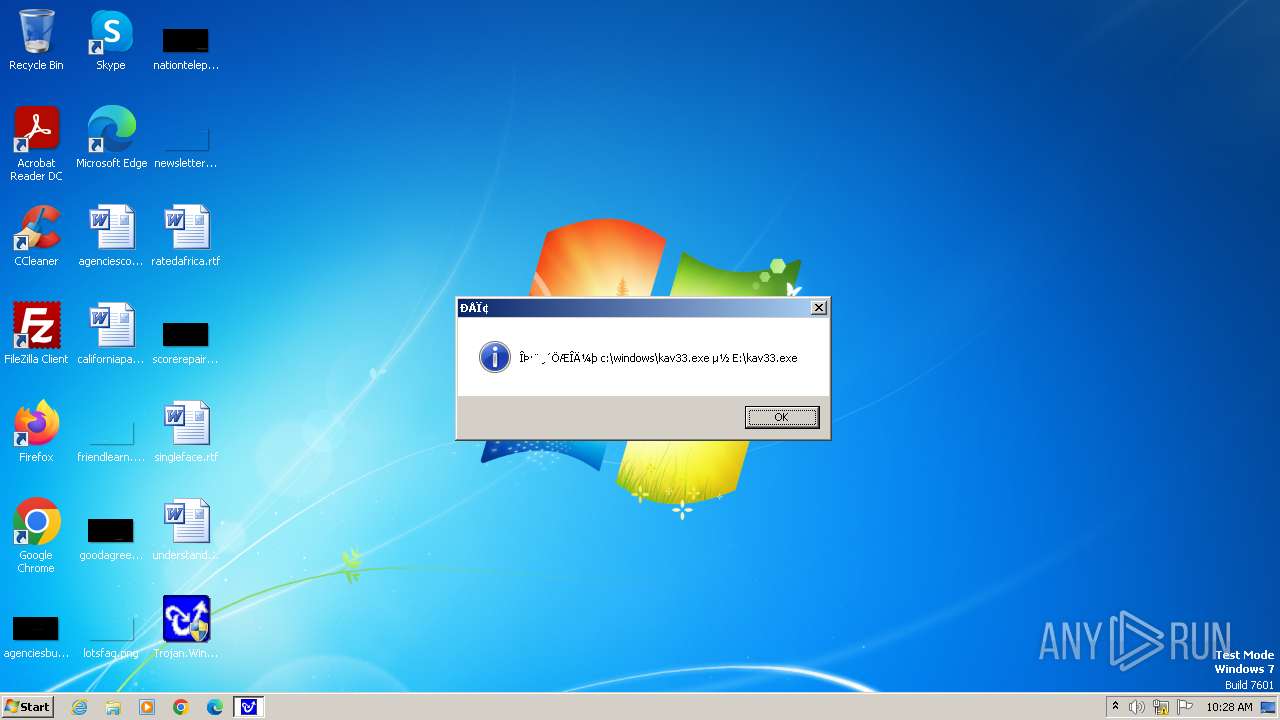
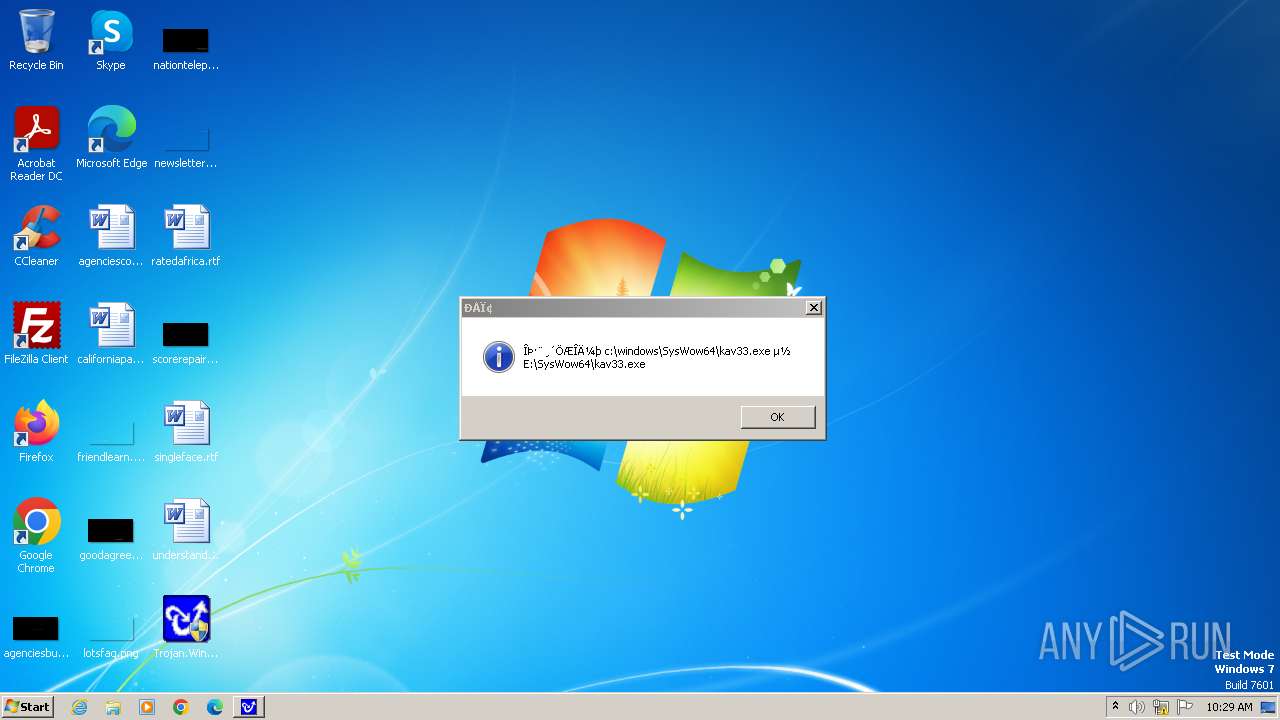
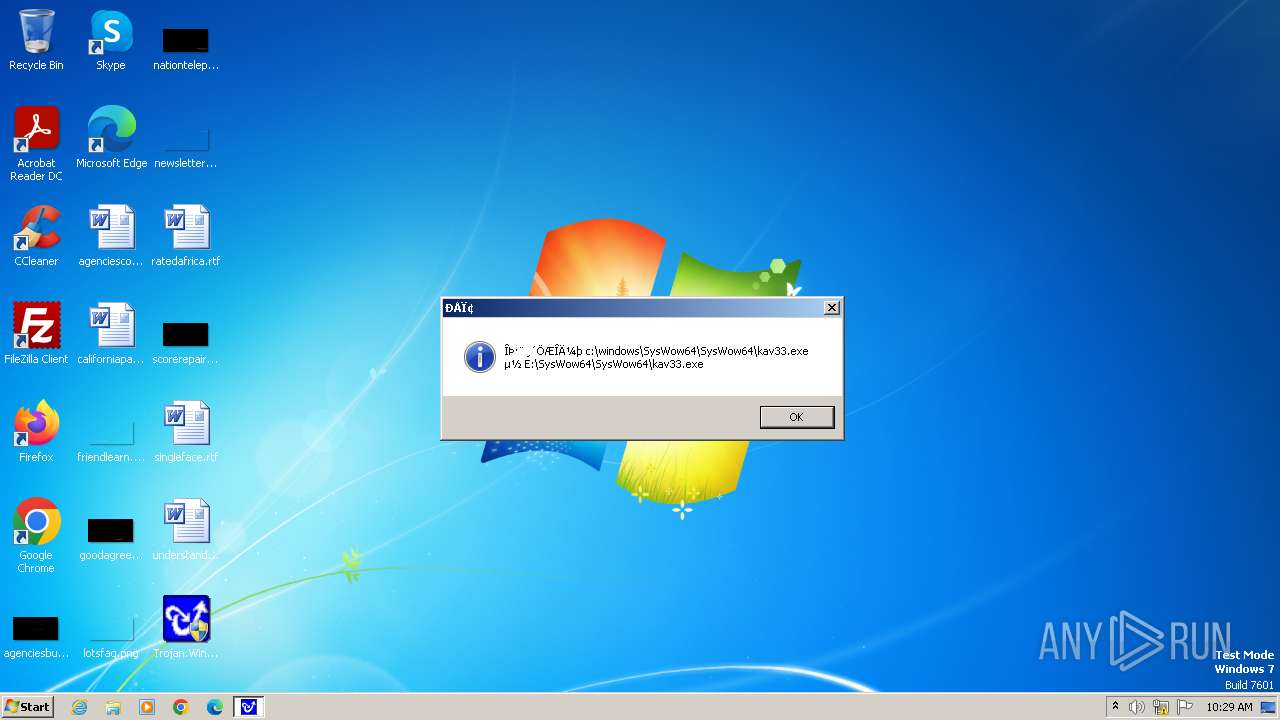
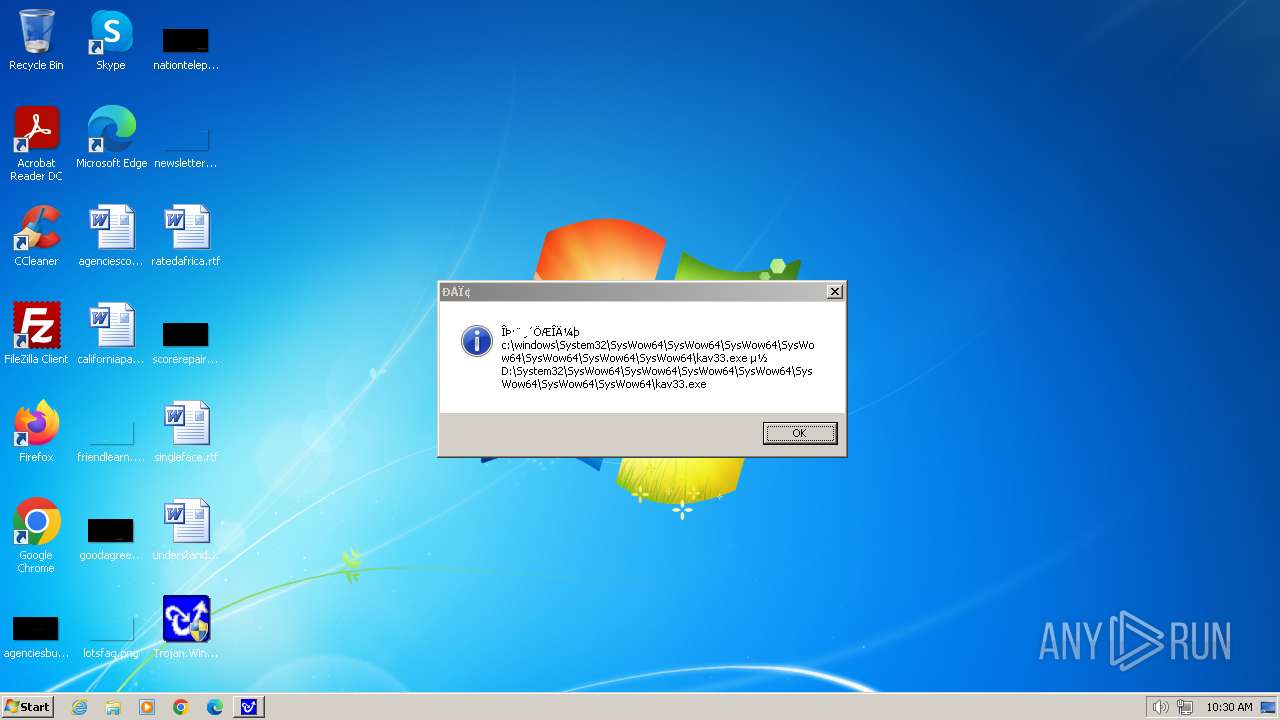
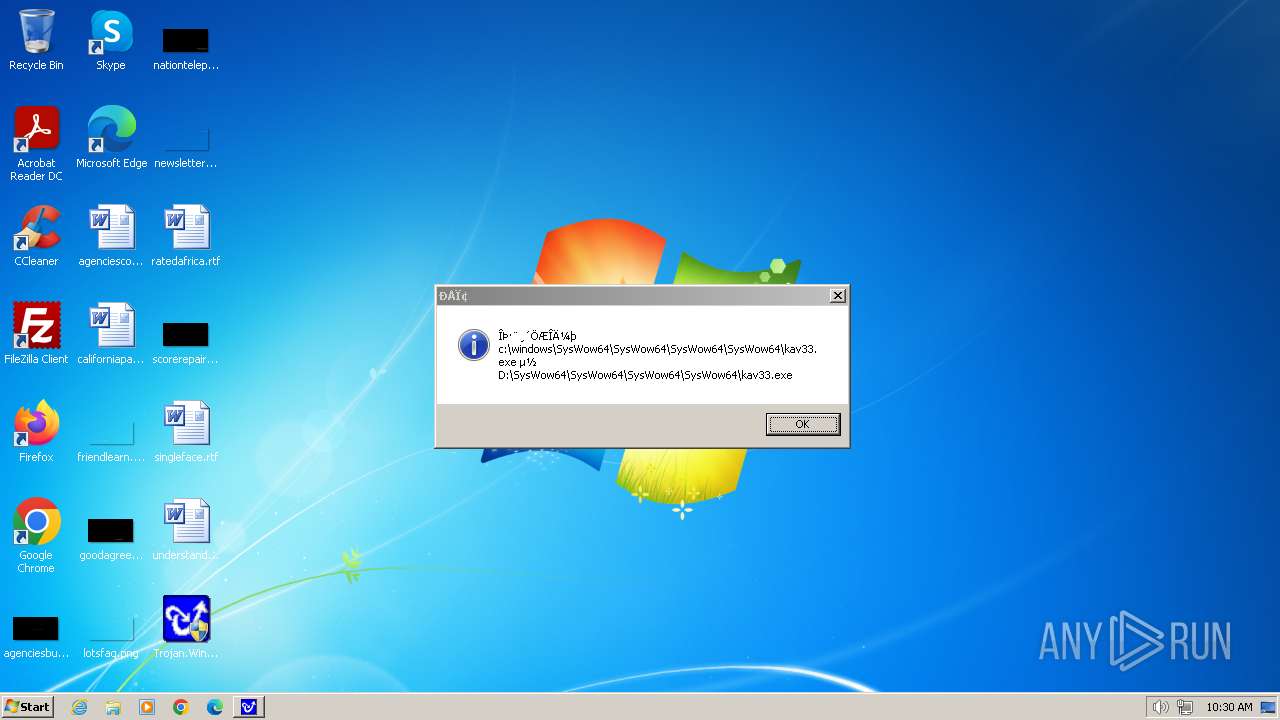
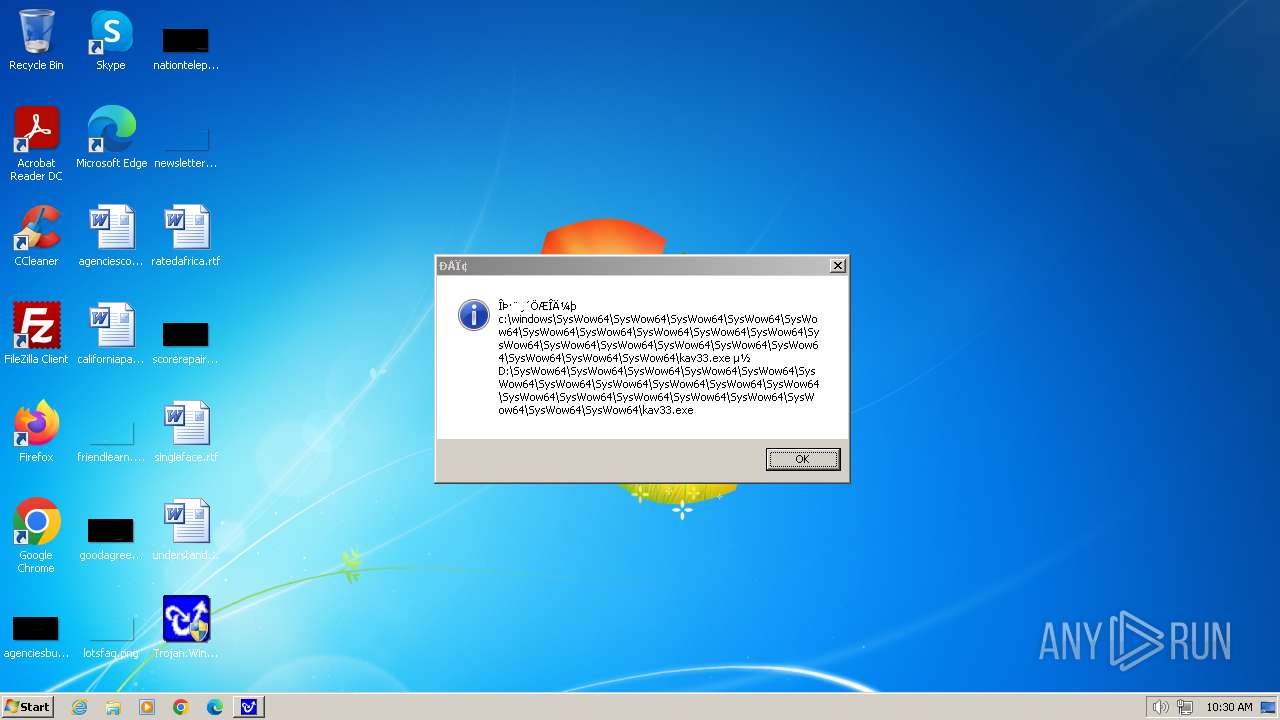
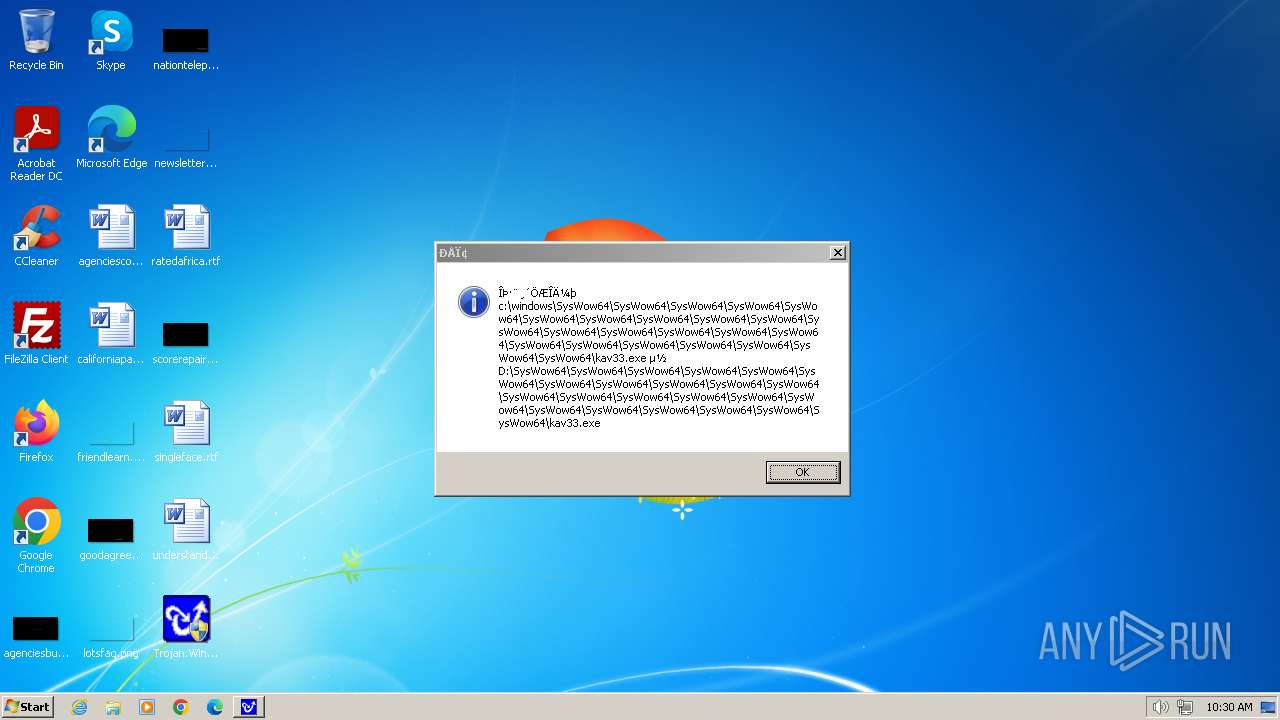
| 1776 | Trojan.Win32.Gentee.b.exe | C:\WINNT\kav33.exe | executable | |
MD5:BA19983D172B47B9696DE895750A2C36 | SHA256:3358C5764DE72D5B42BB02ED0012F7B4DB1DCD7A1941E2BF4739D75D44D32D31 | |||
| 1776 | Trojan.Win32.Gentee.b.exe | C:\Windows\x.BMP | image | |
MD5:FEFE6C910491ACD79069387C1140A0EF | SHA256:FAC51FF1686AC0D4B9C7EEFB3202F37C3596CBB3060102B0DCAEECC313923E89 | |||
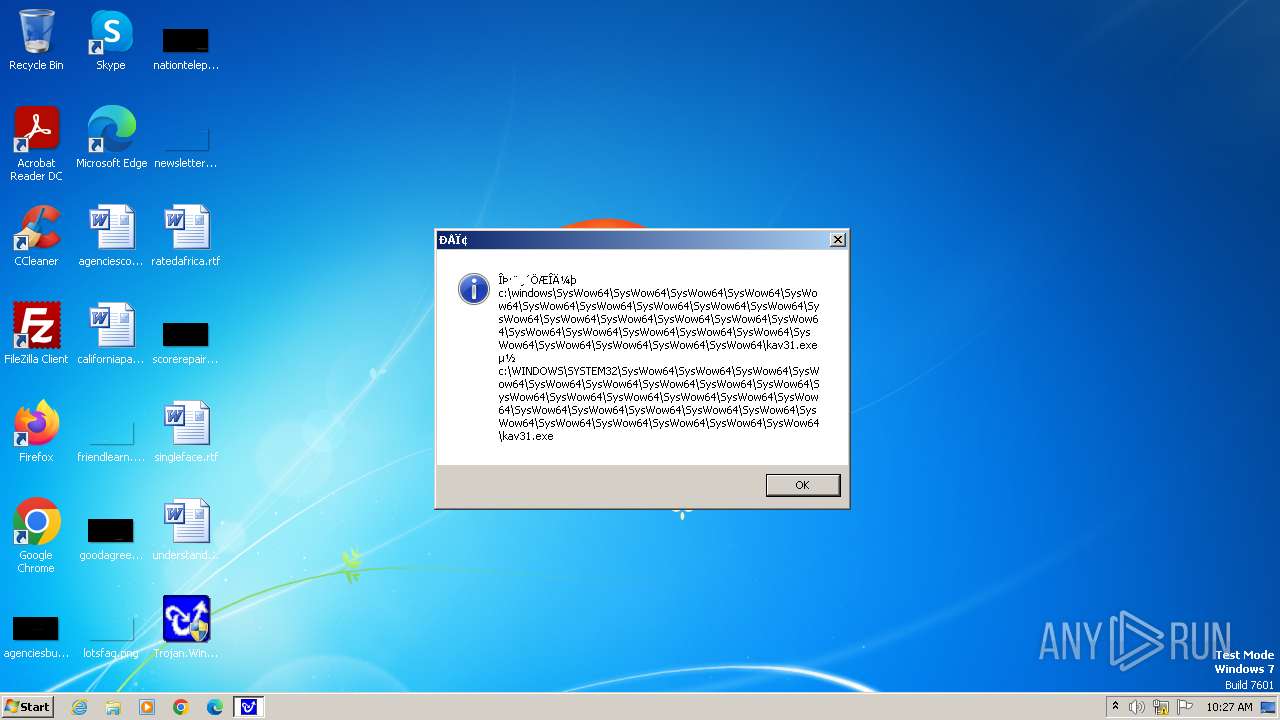
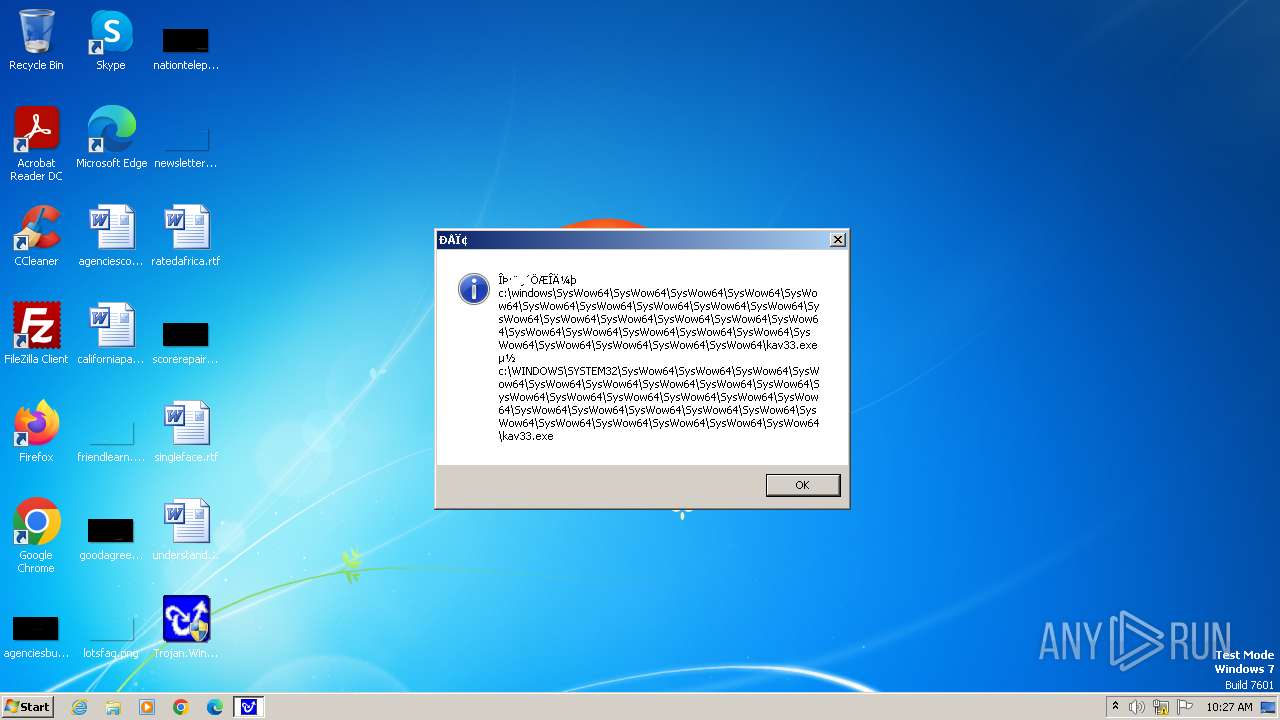
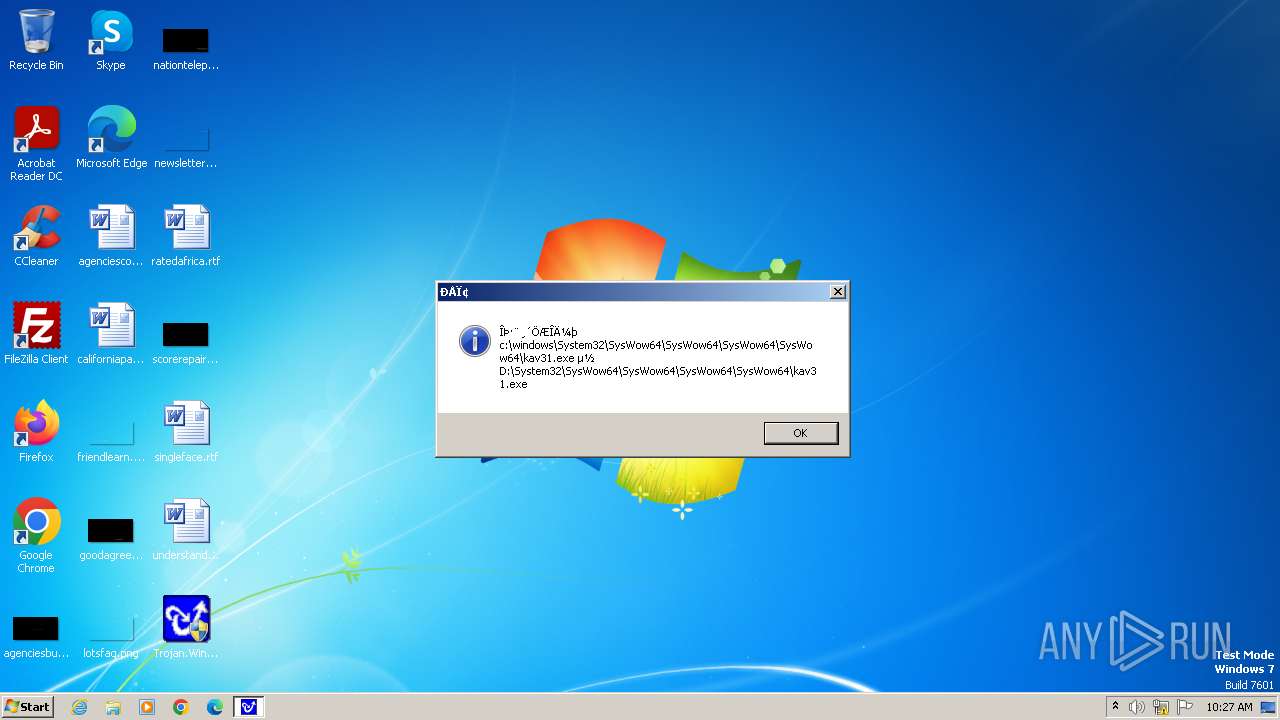
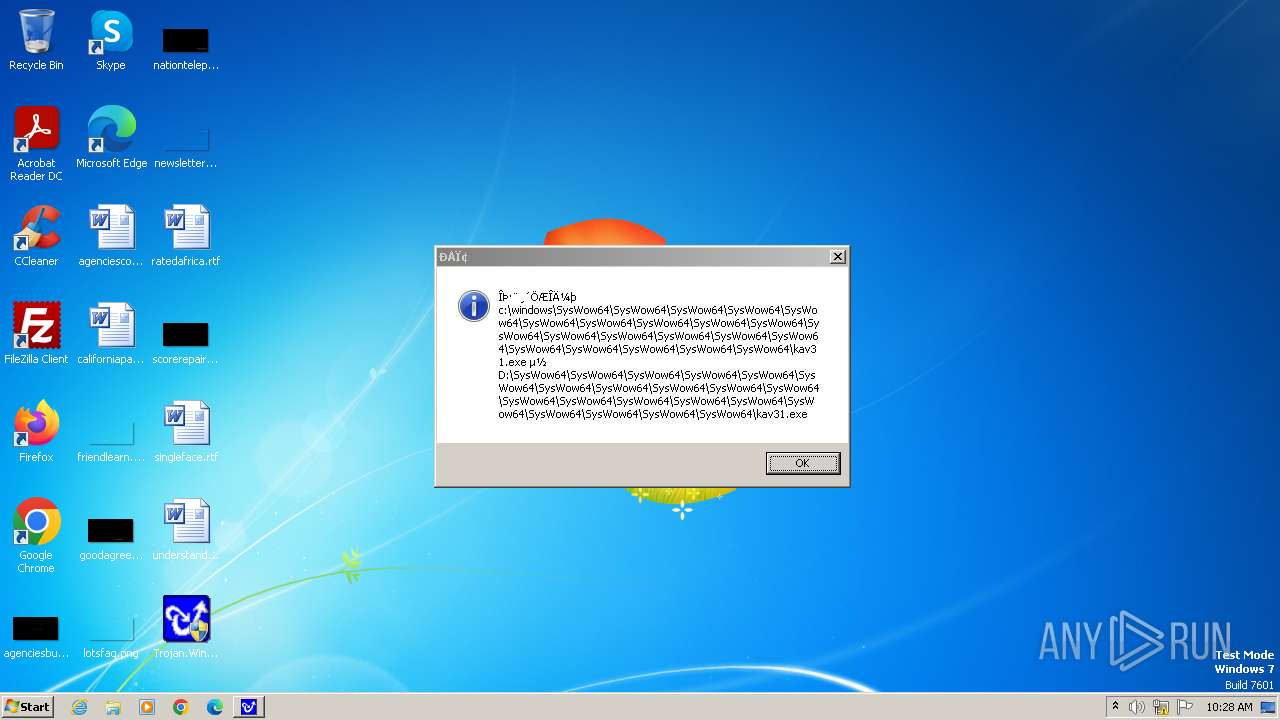
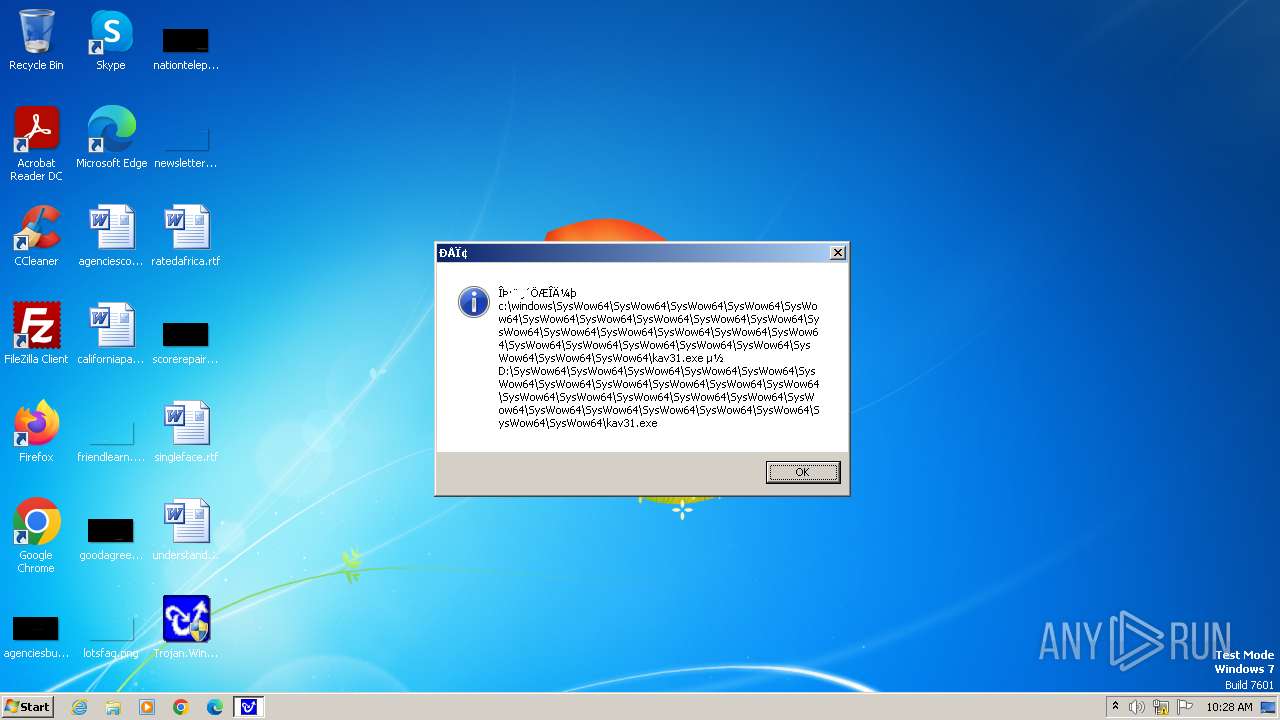
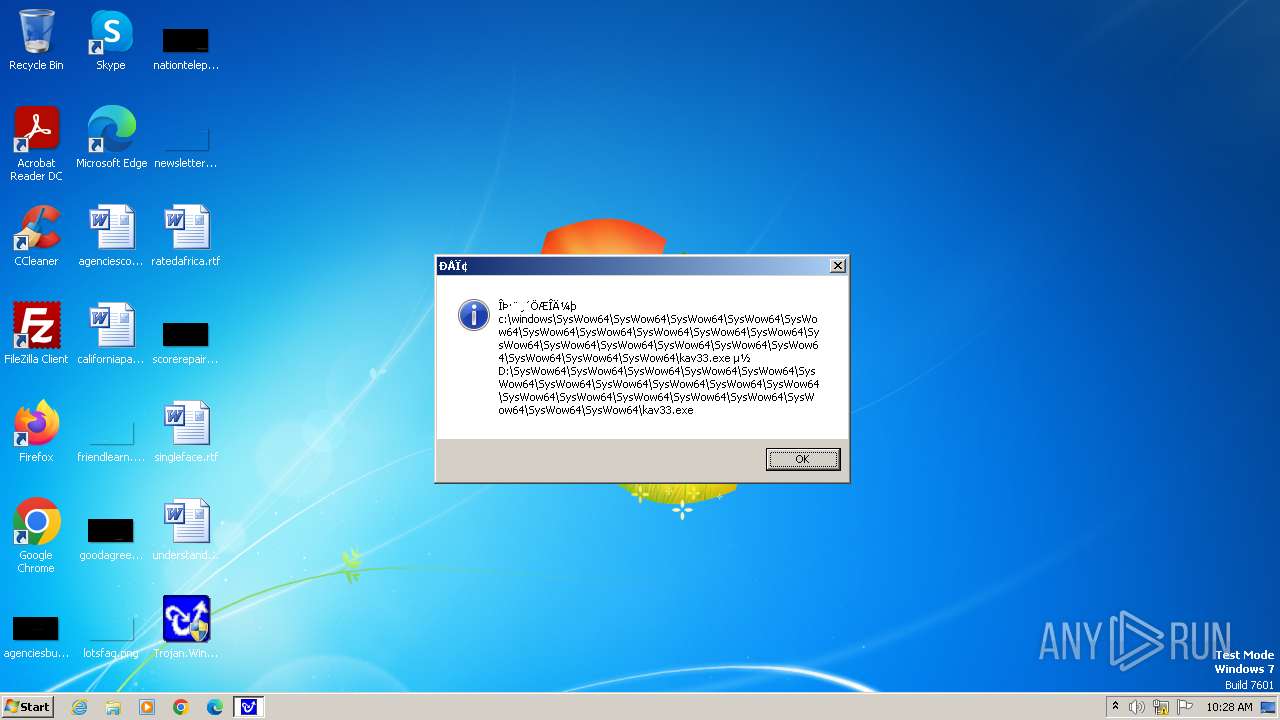
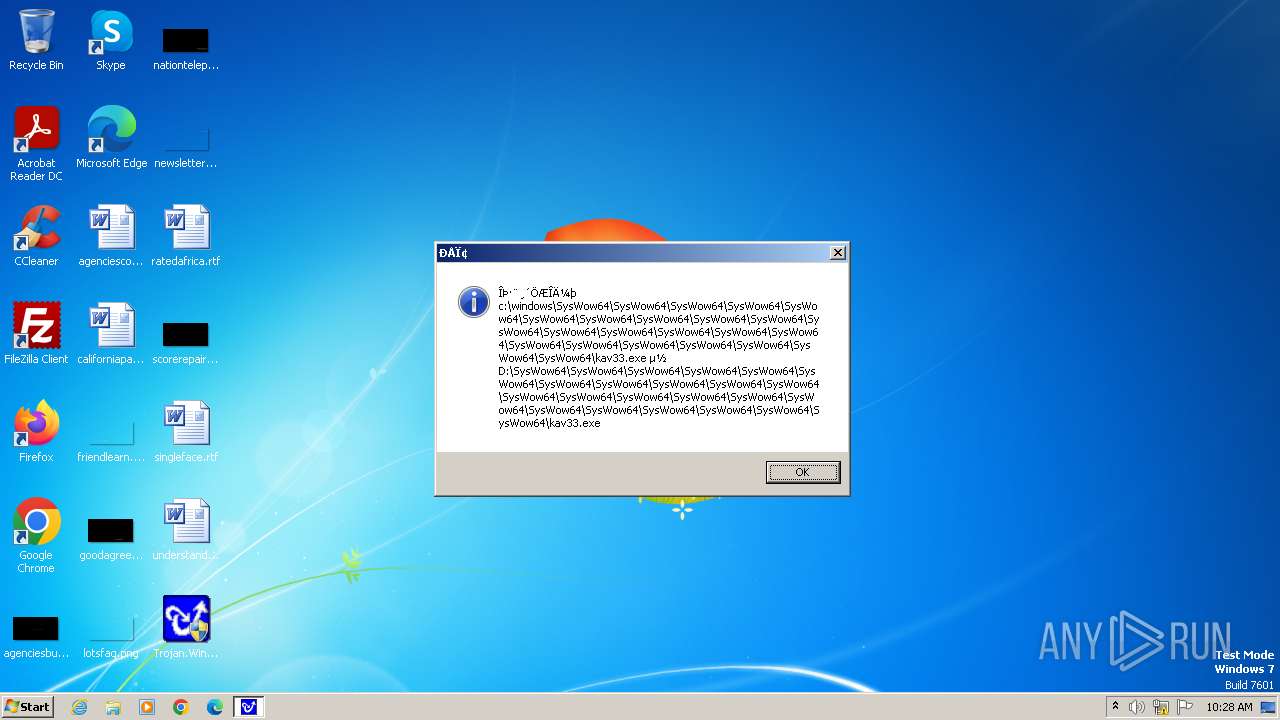
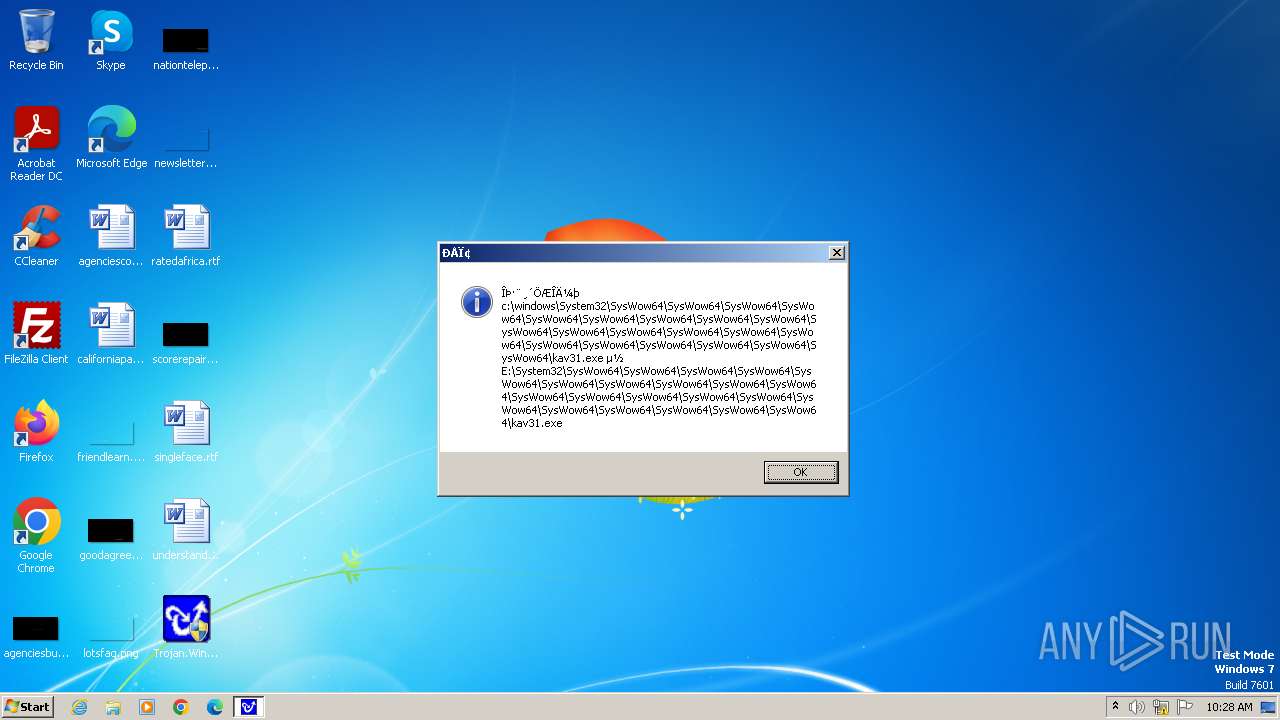
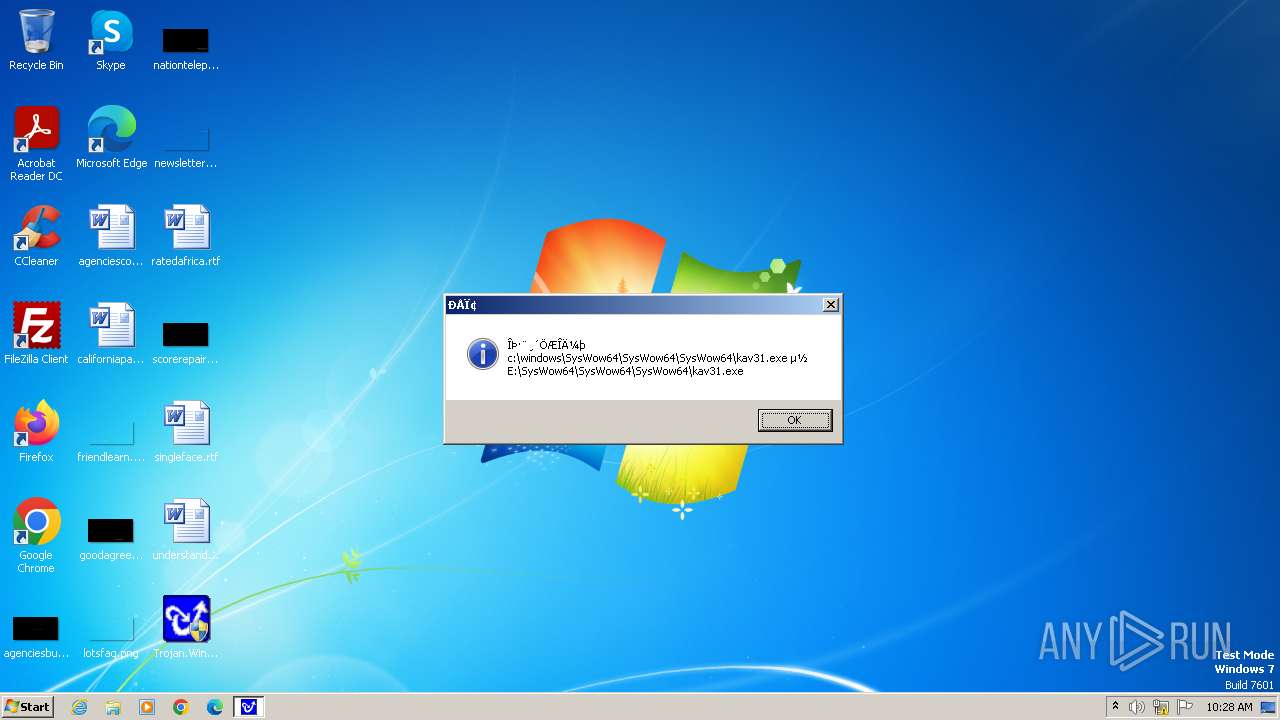
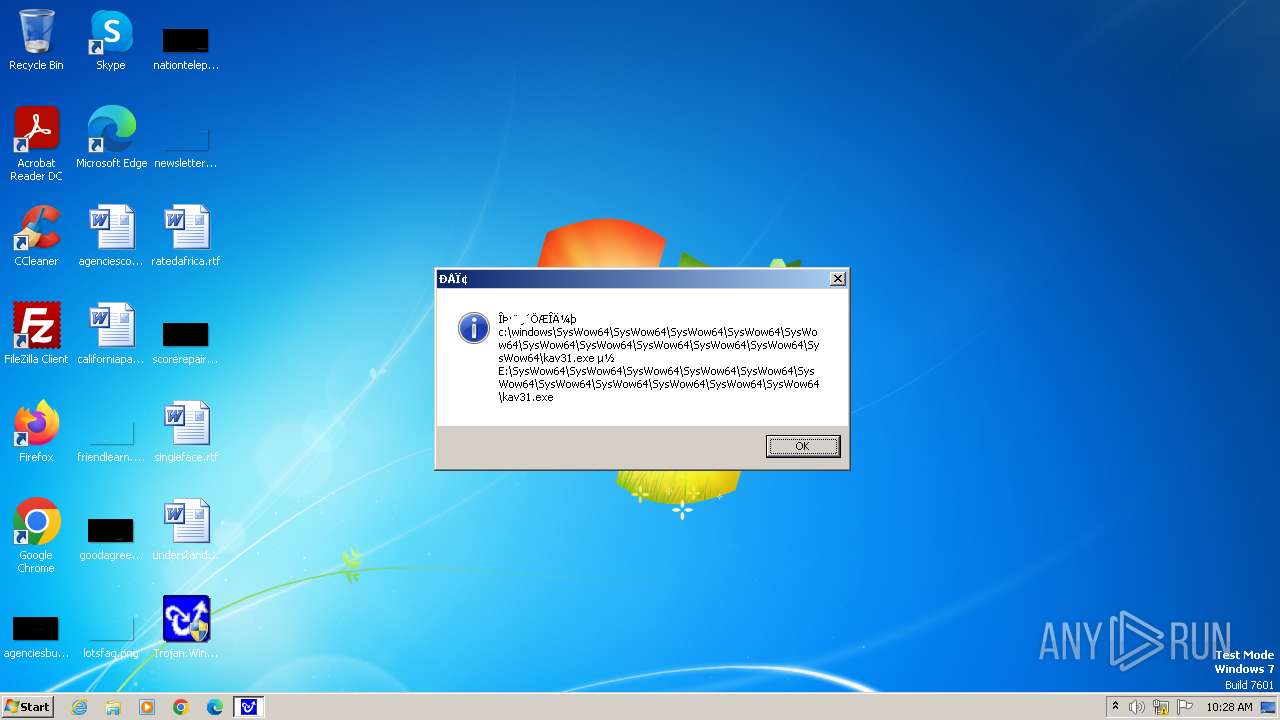
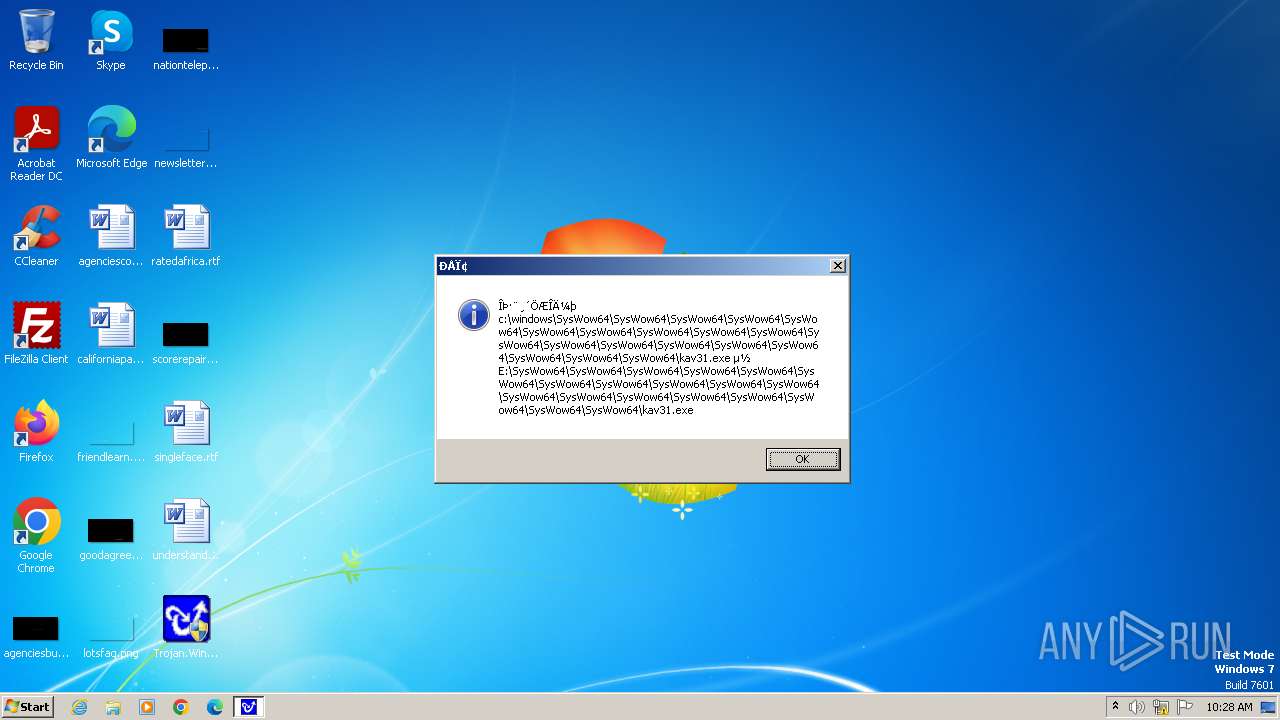
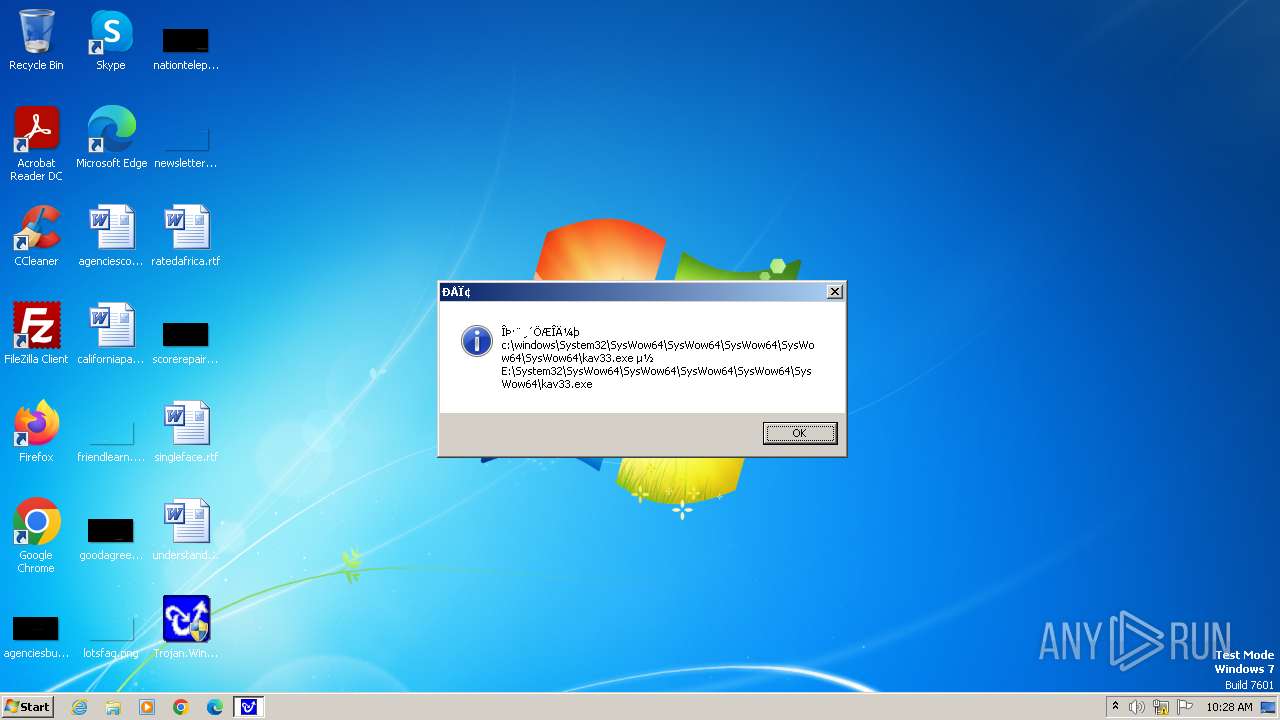
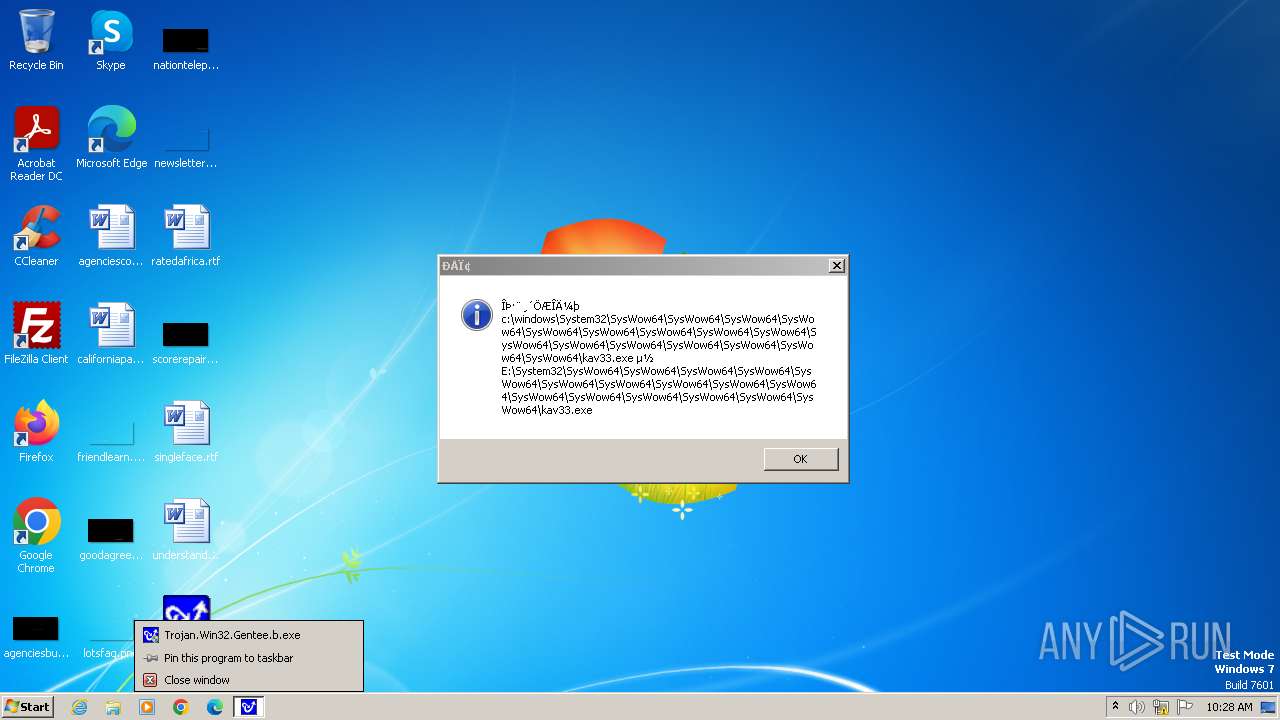
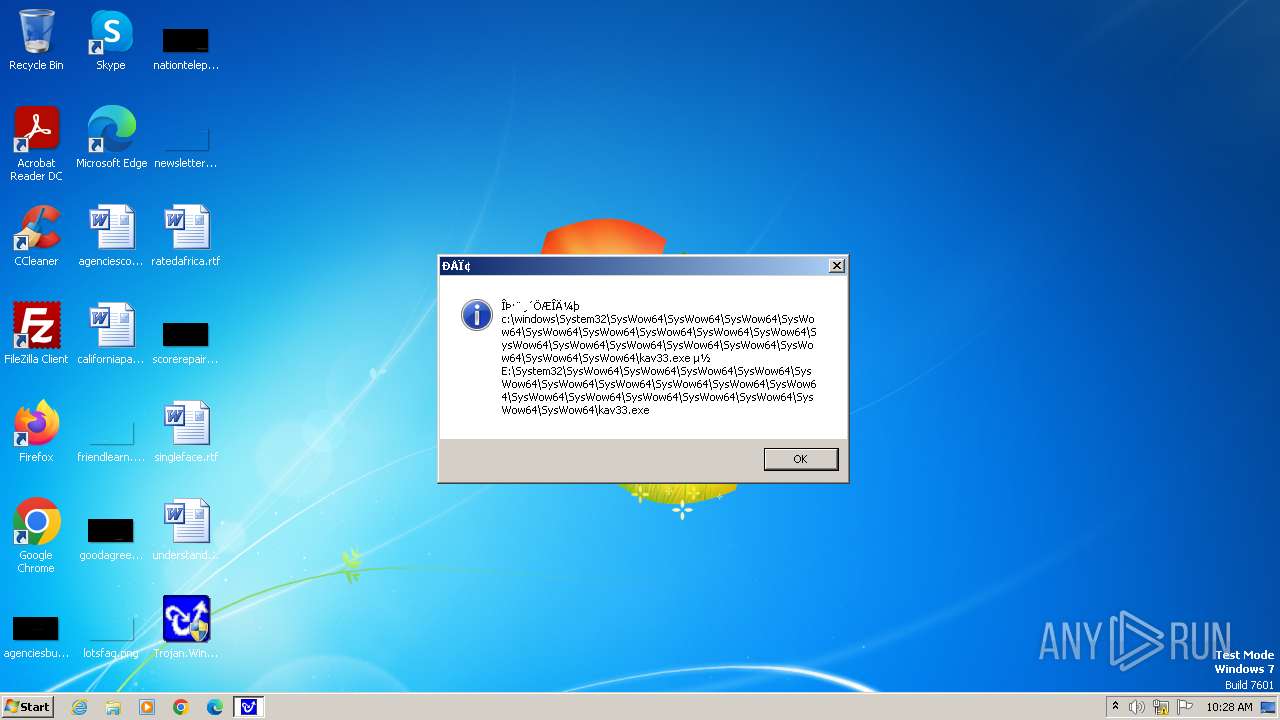
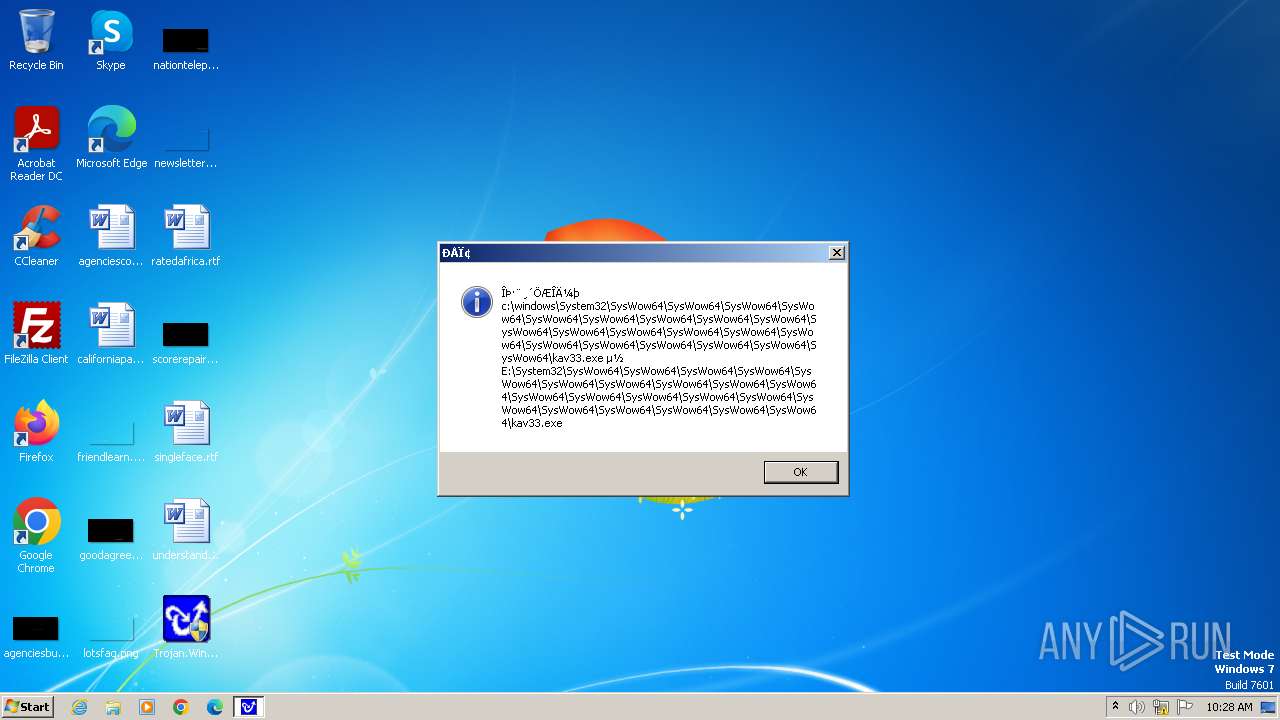
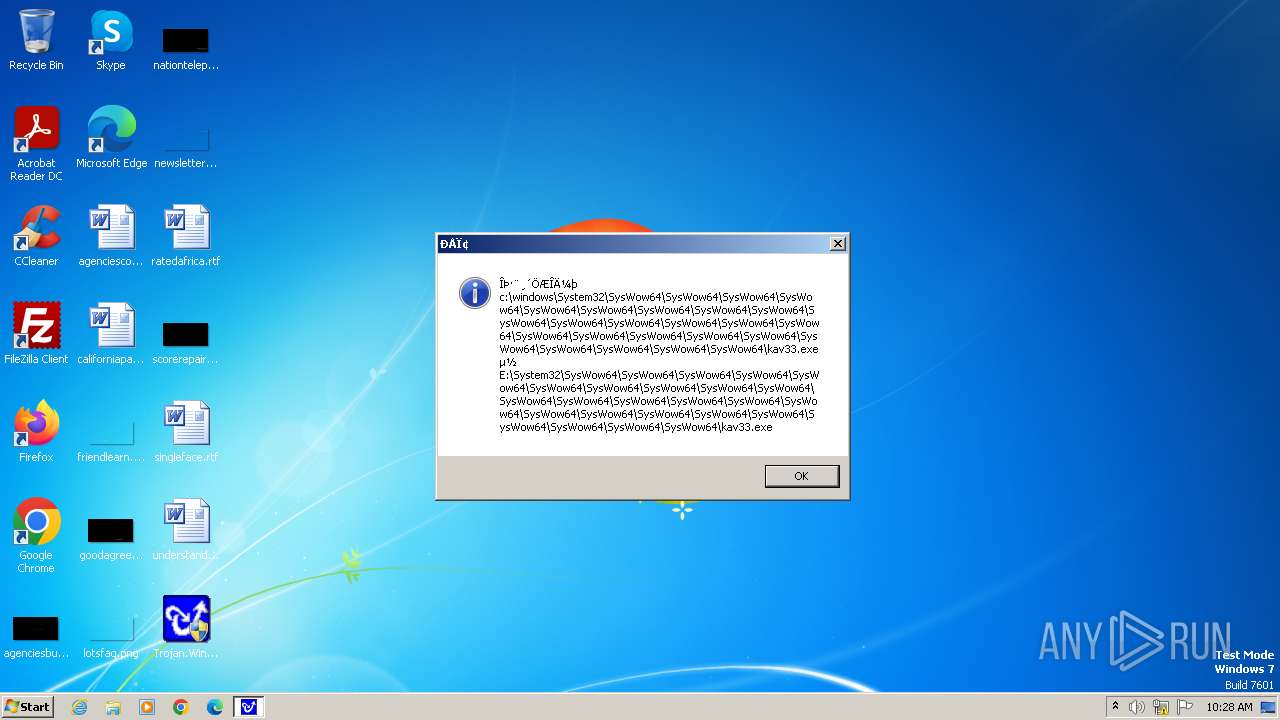
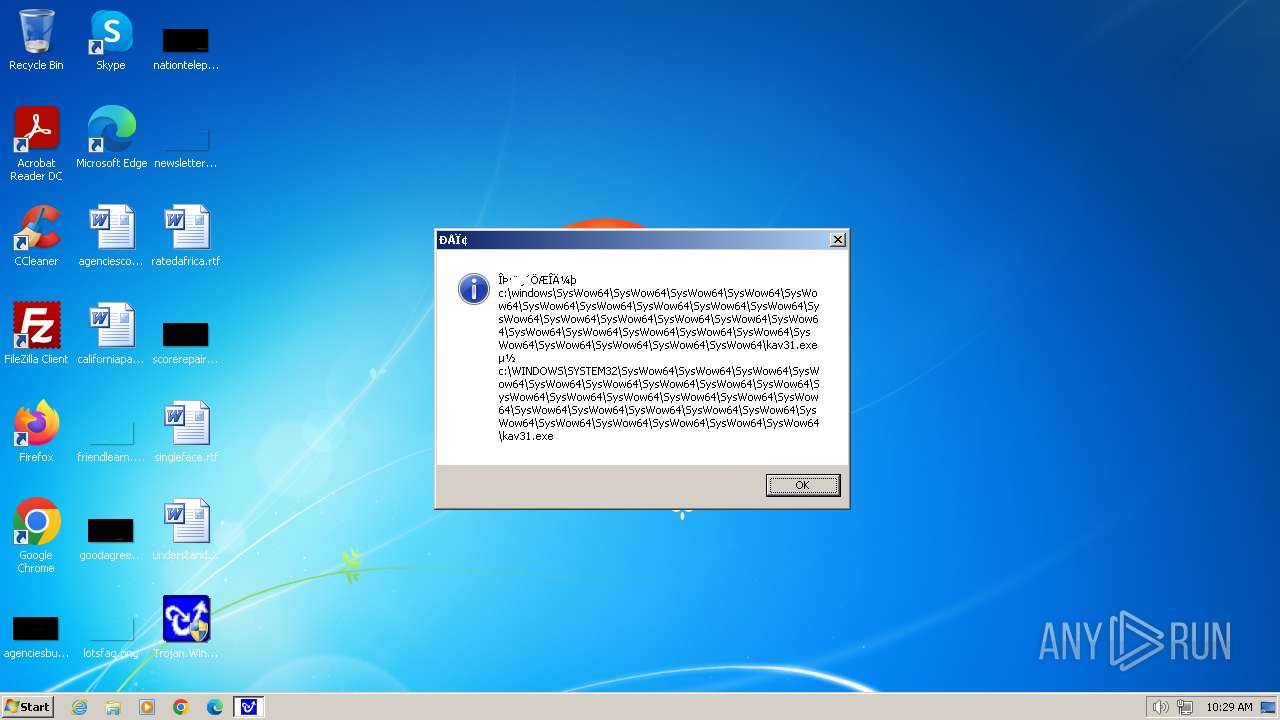
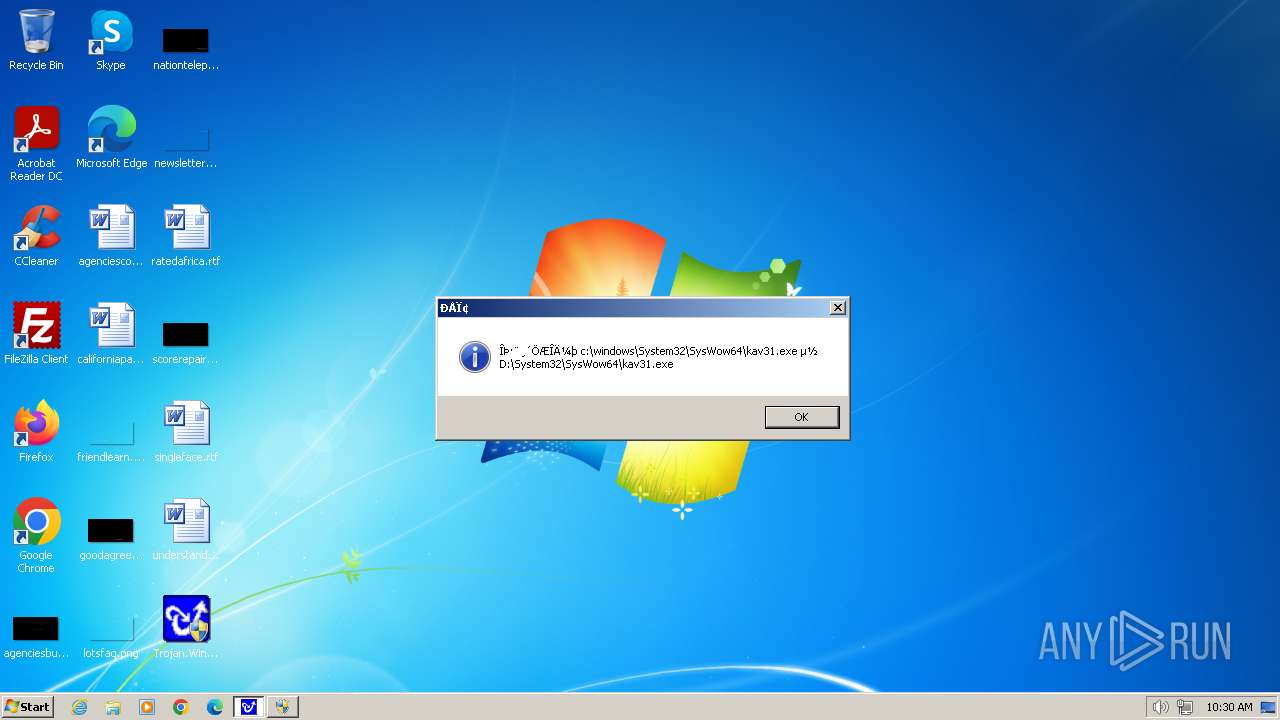
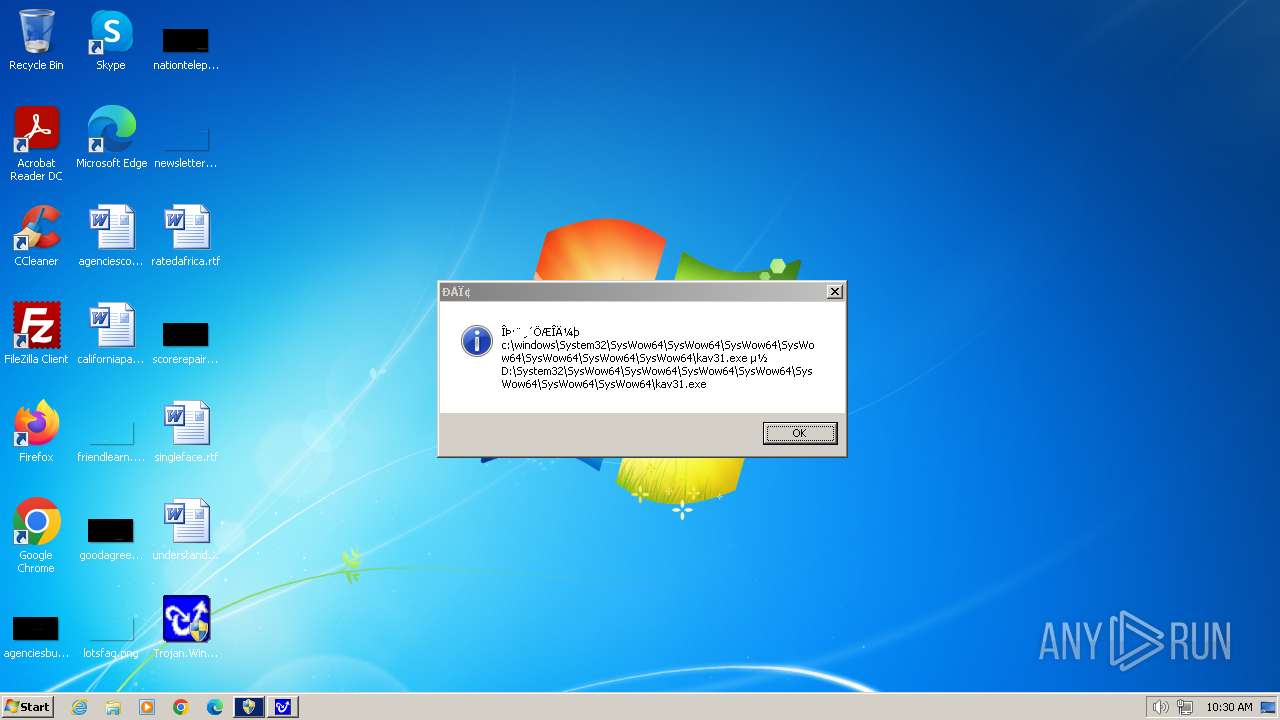
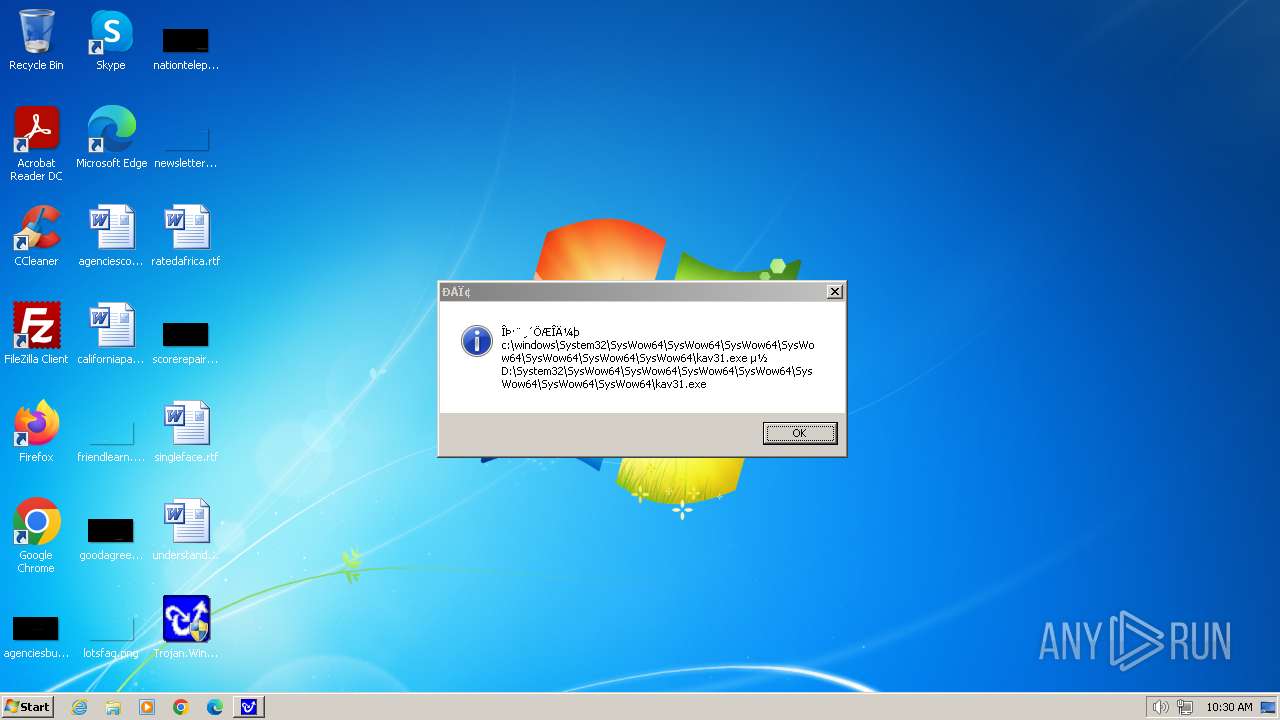
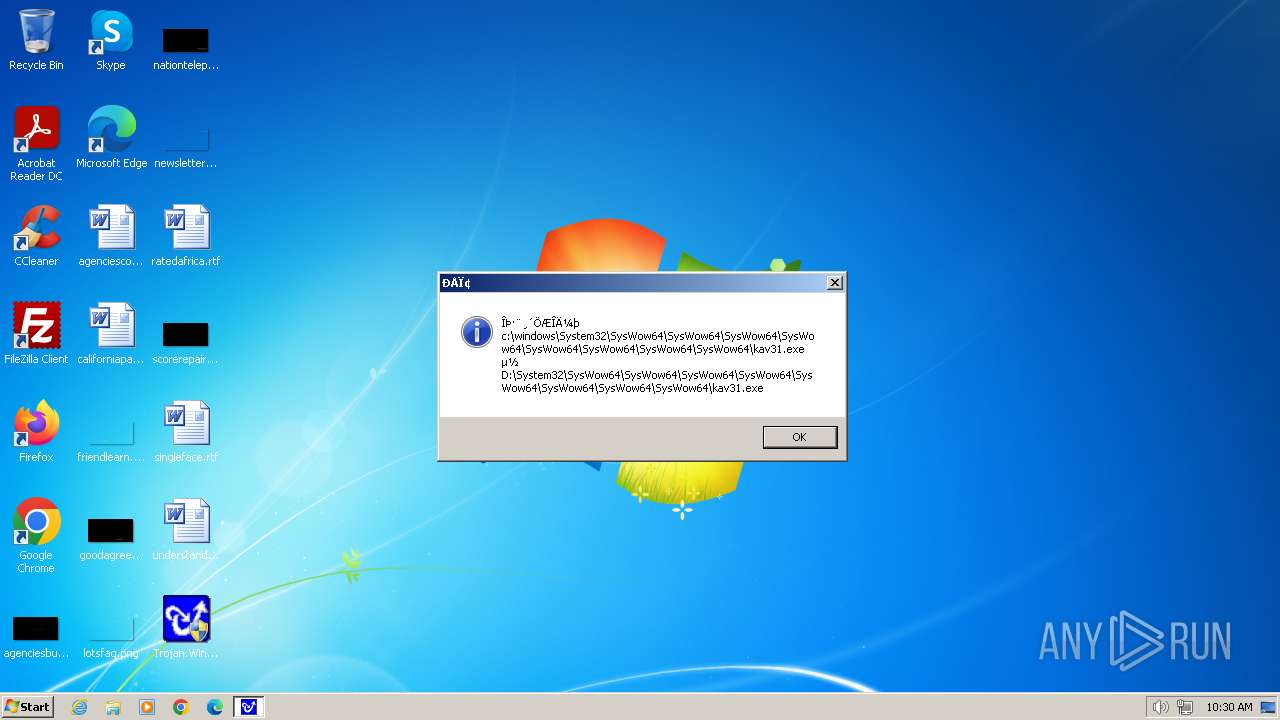
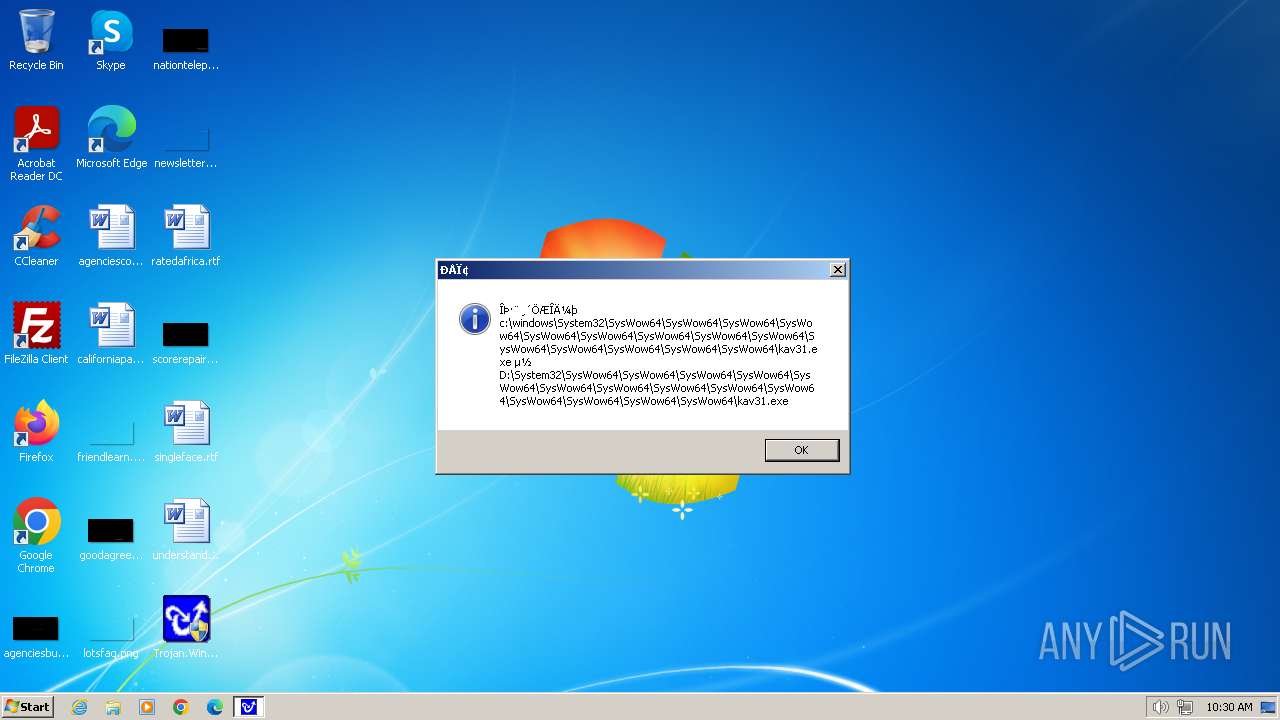
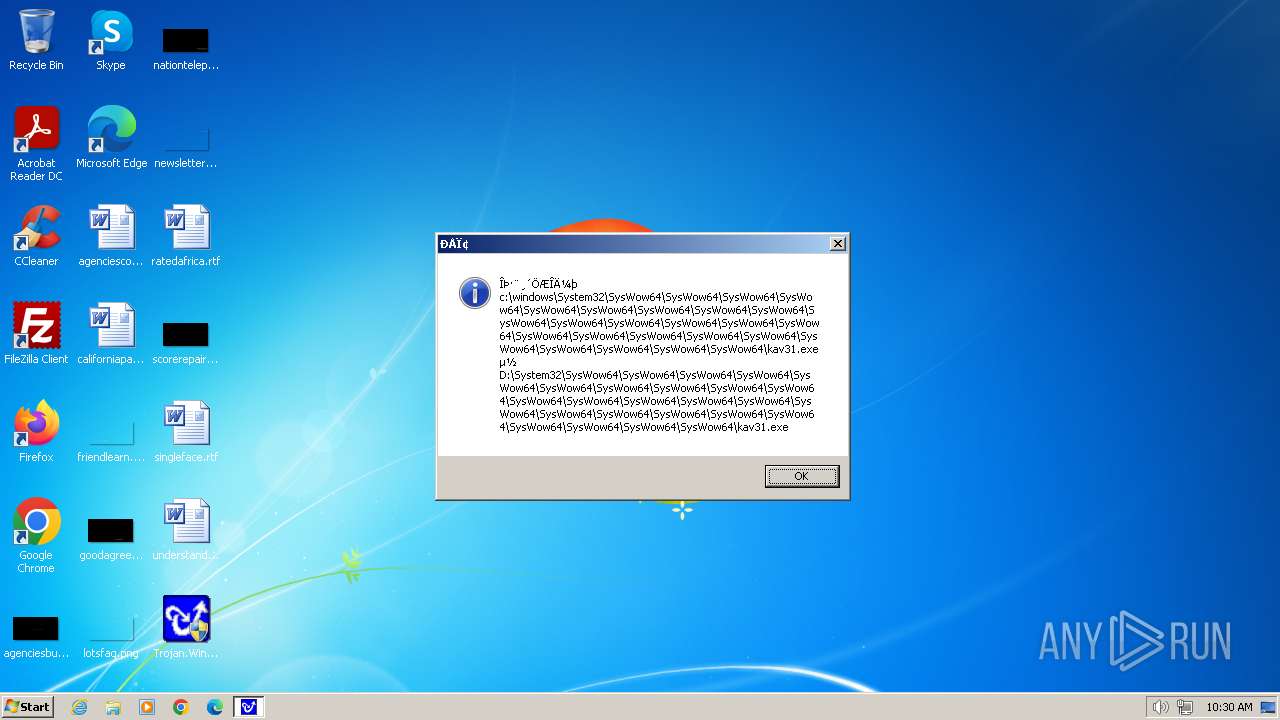
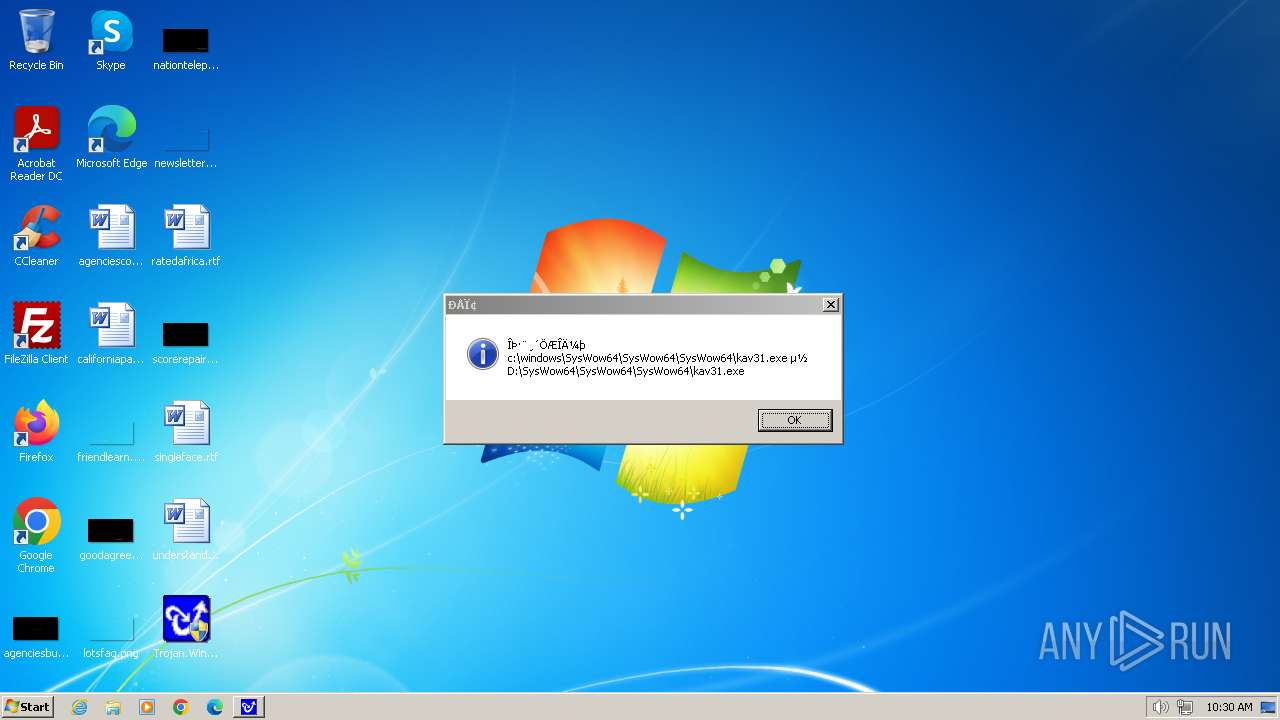
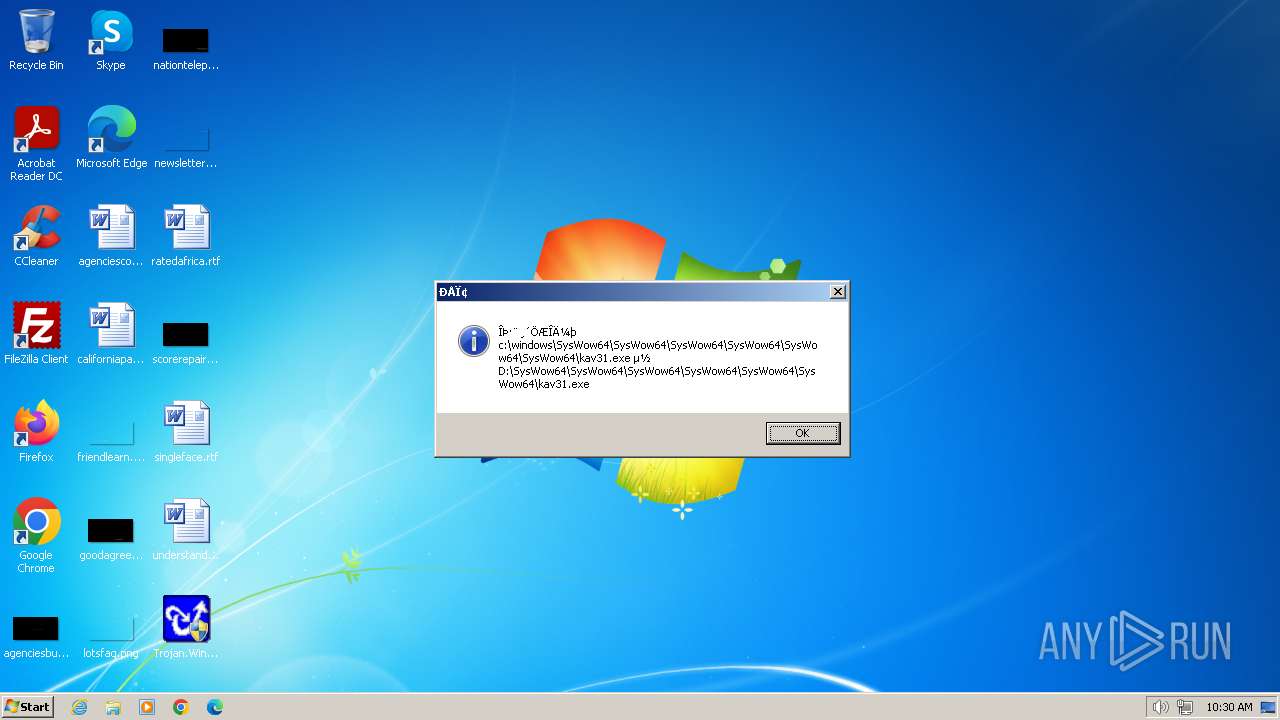
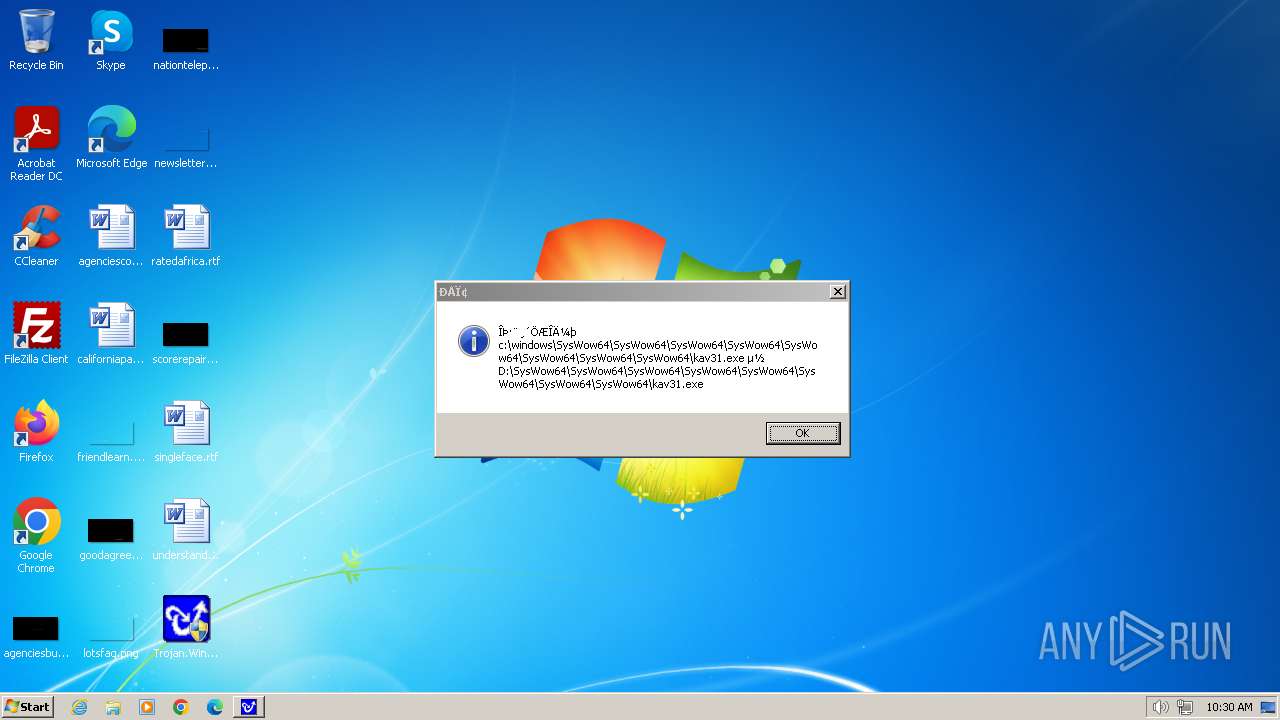
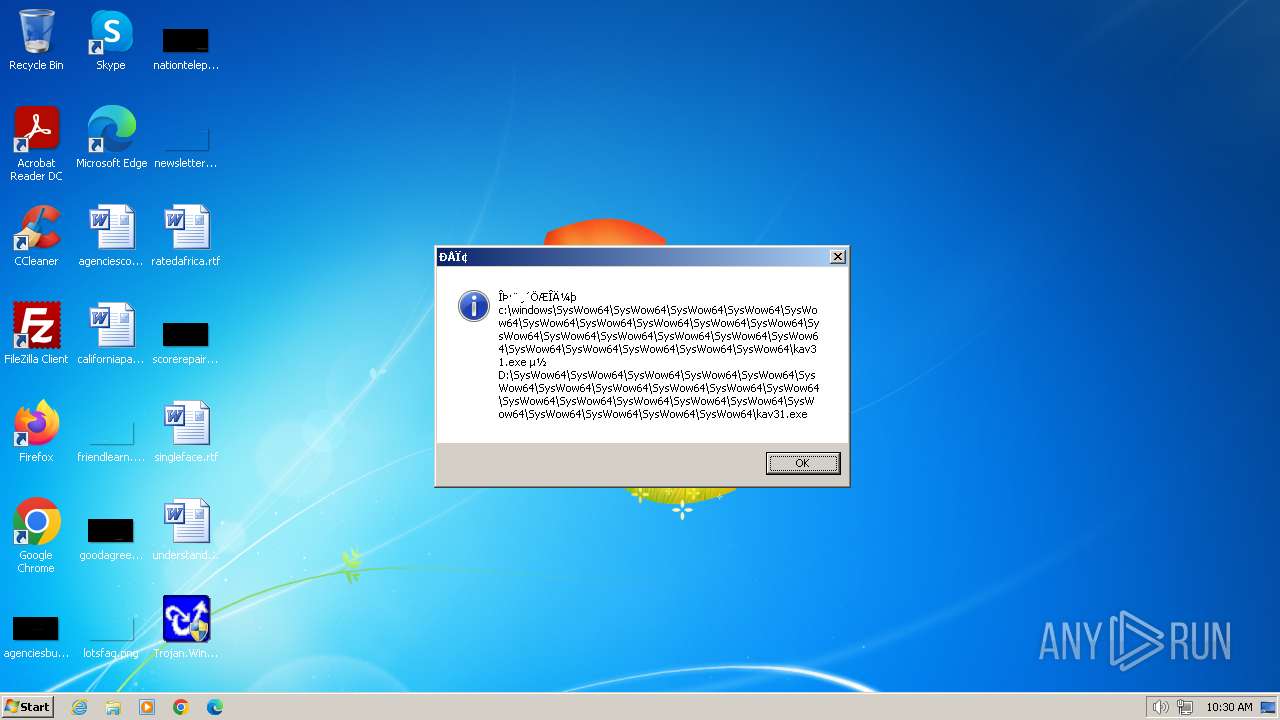
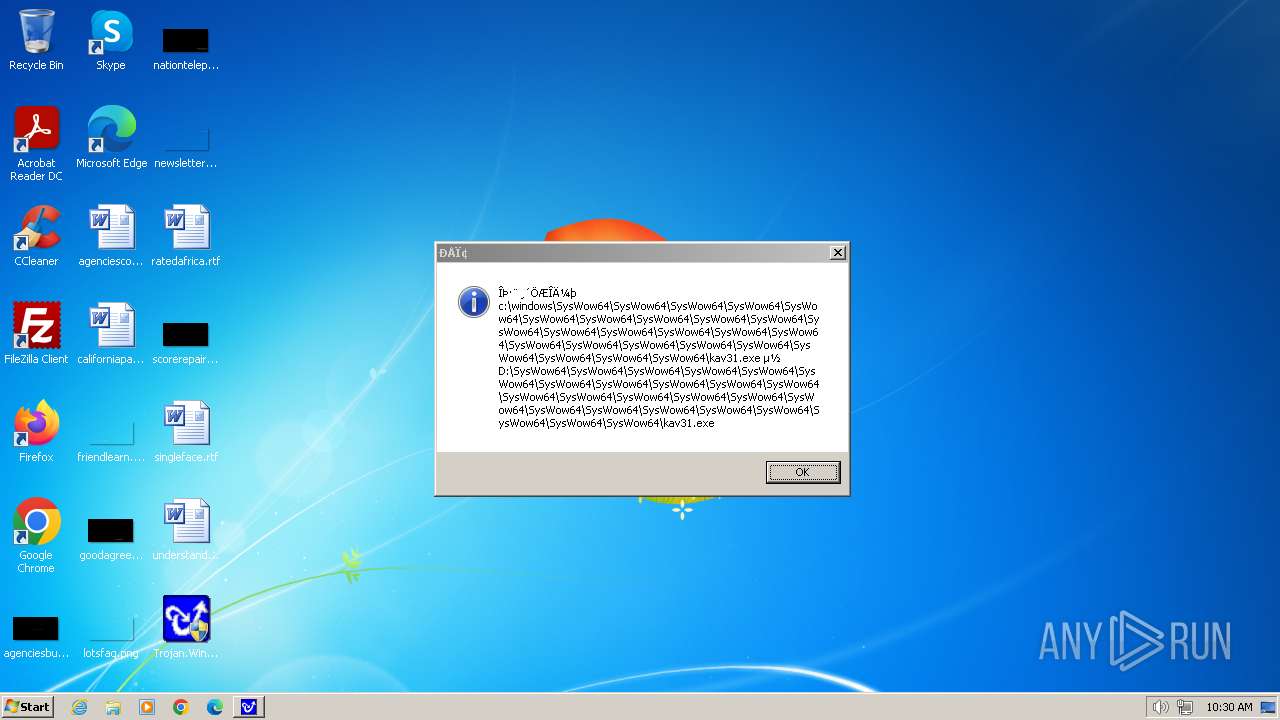
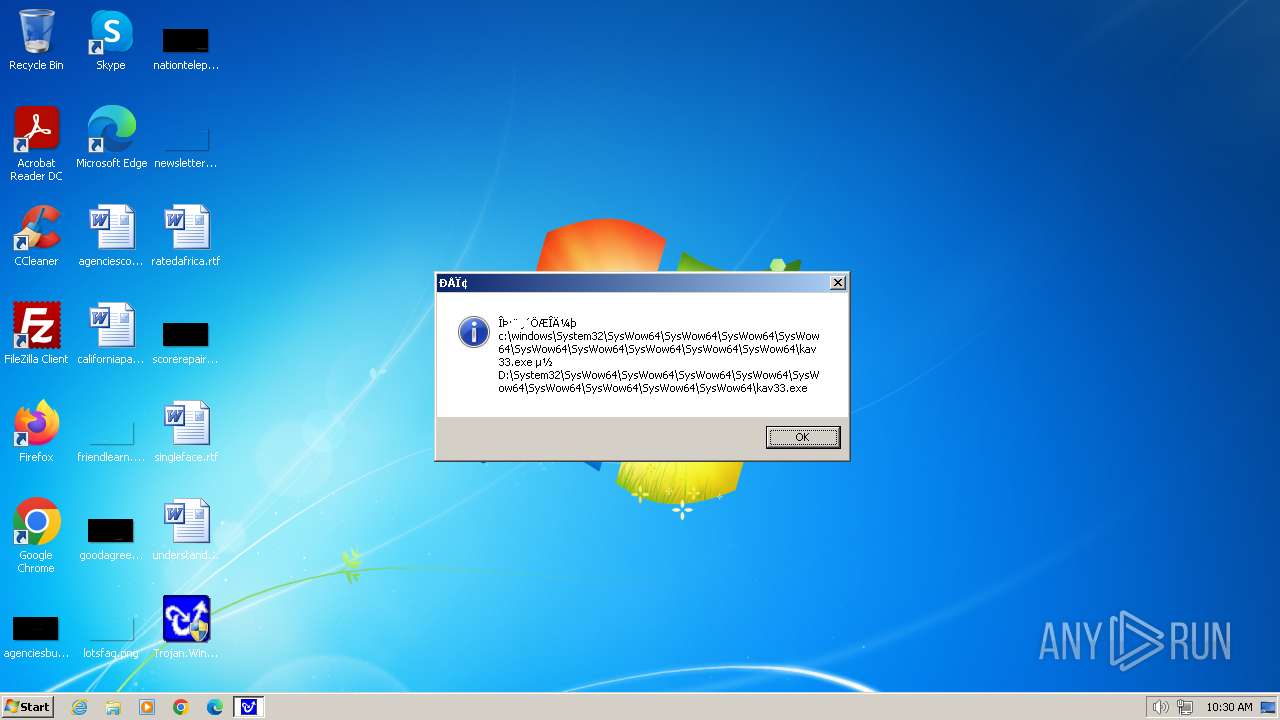
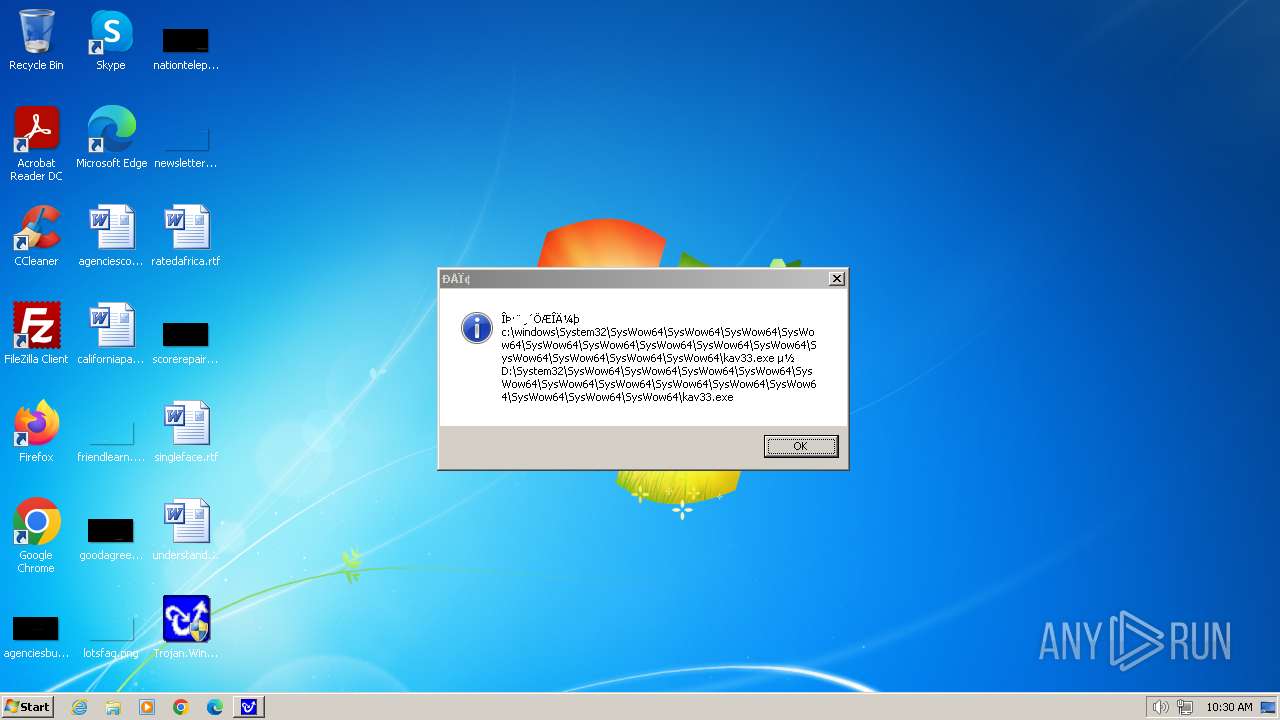
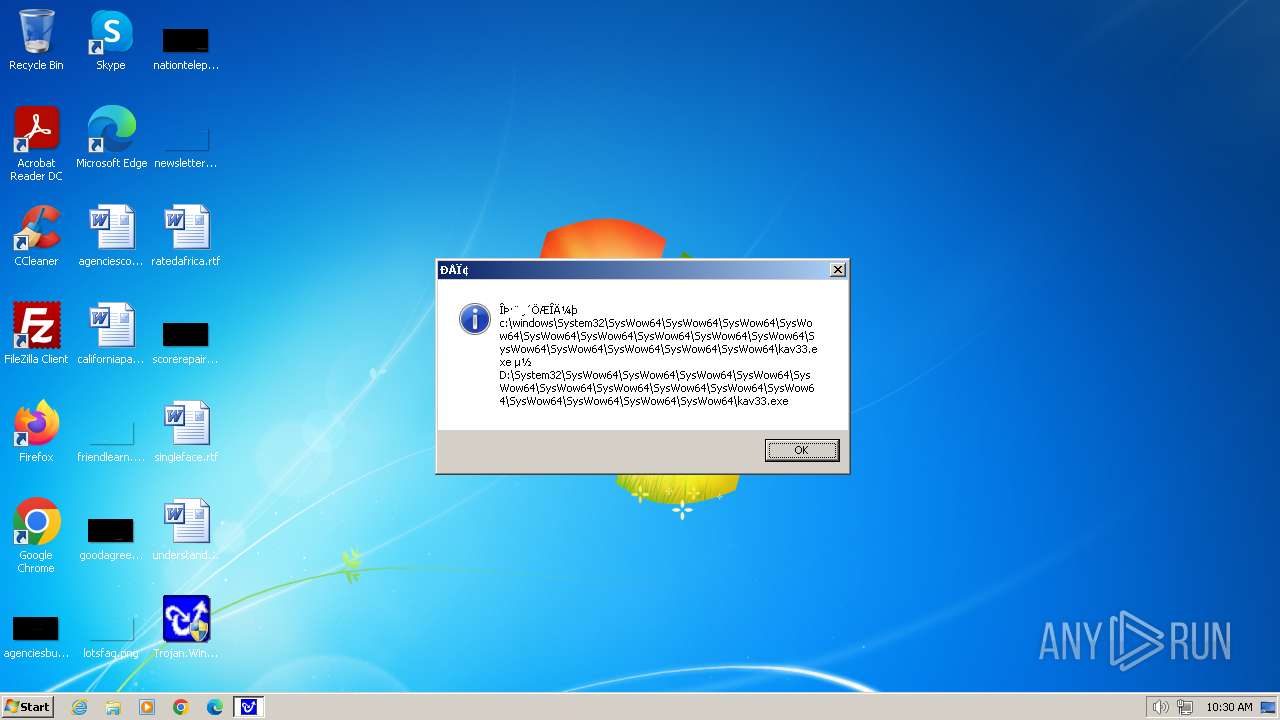
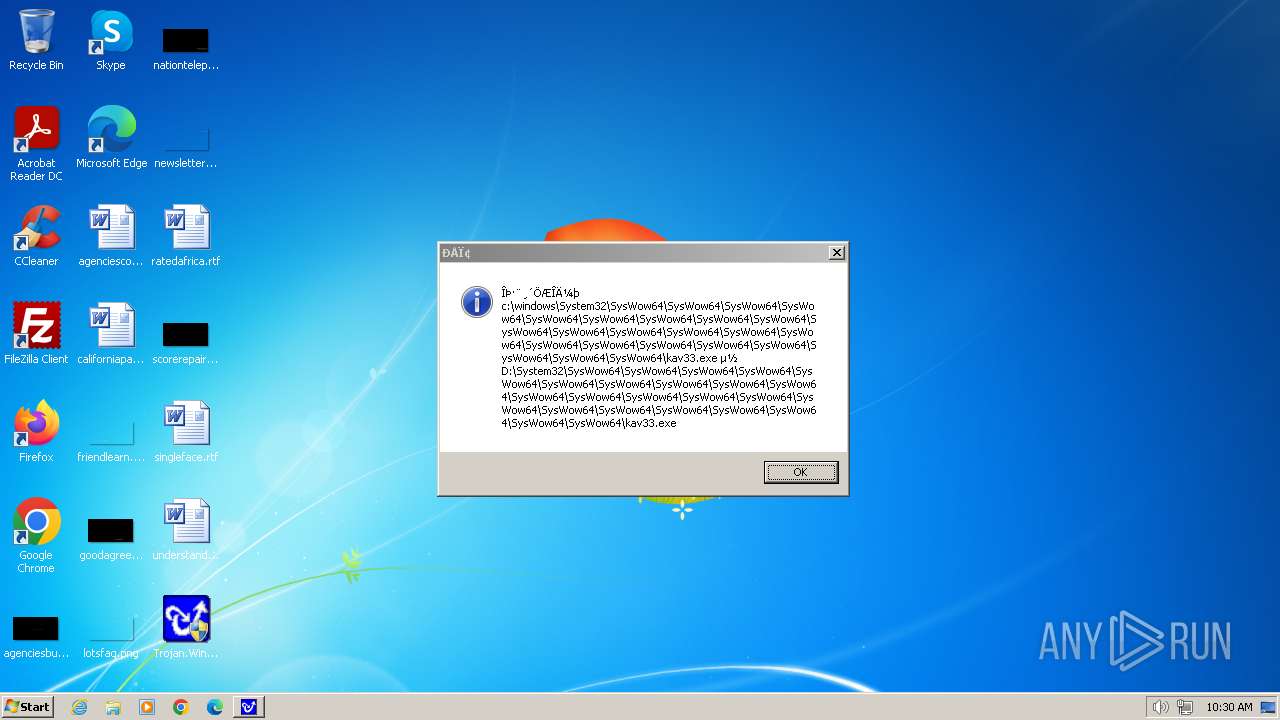
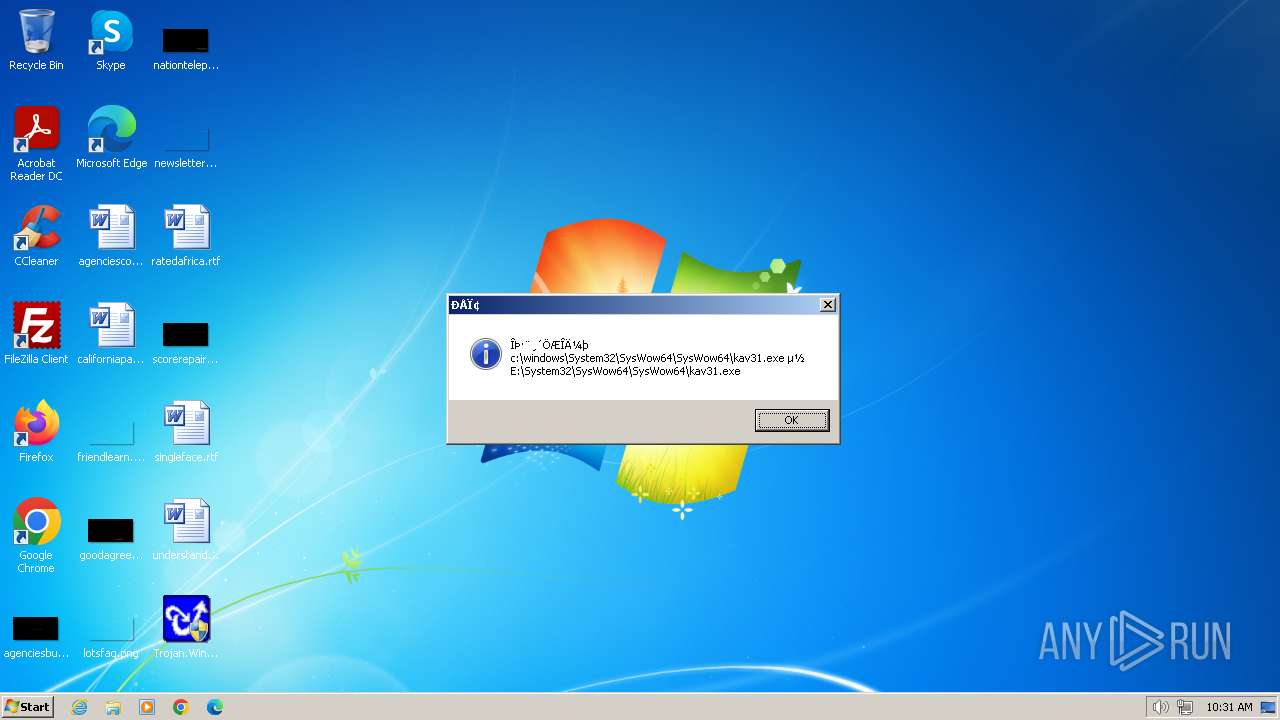
| 1776 | Trojan.Win32.Gentee.b.exe | C:\Windows\System32\SysWow64\SysWow64\SysWow64\SysWow64\kav31.exe | executable | |
MD5:A24BAF845C8F84CEB1D9D6CB7363E99D | SHA256:0E190F4767B0B6552B5261501428274DDD7A9EF38399E6476F6E8BECC094C7D3 | |||
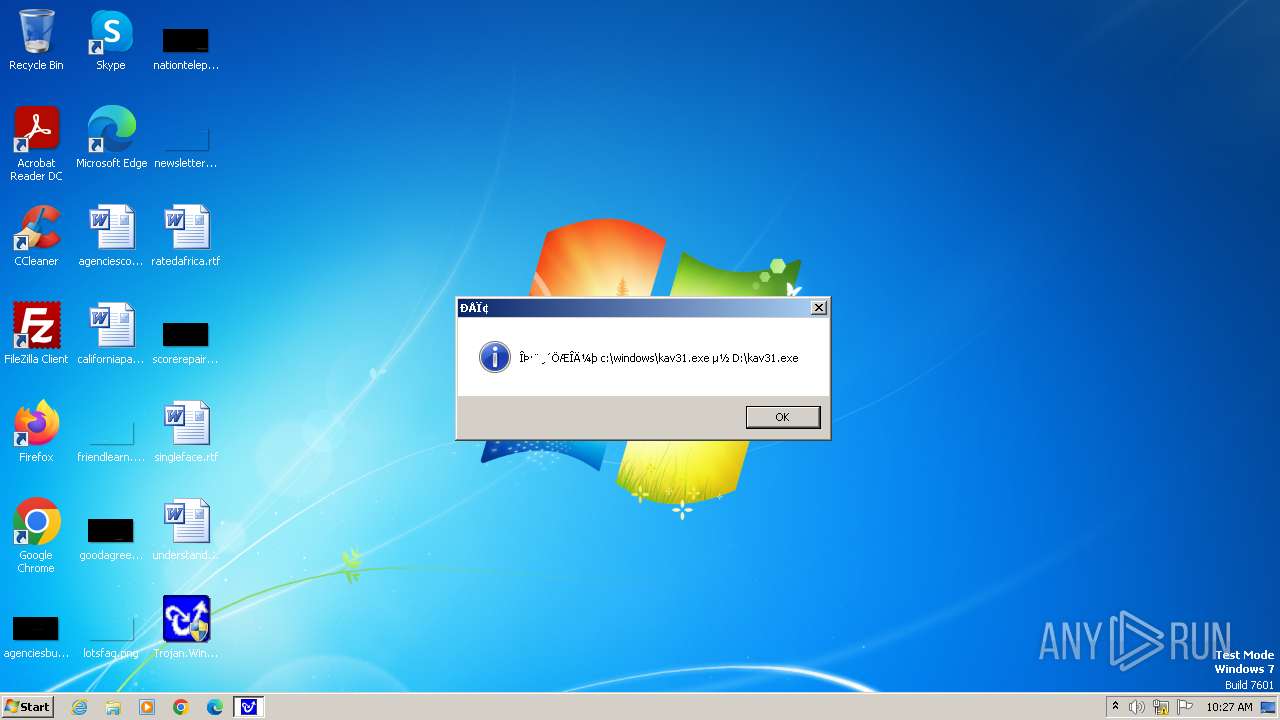
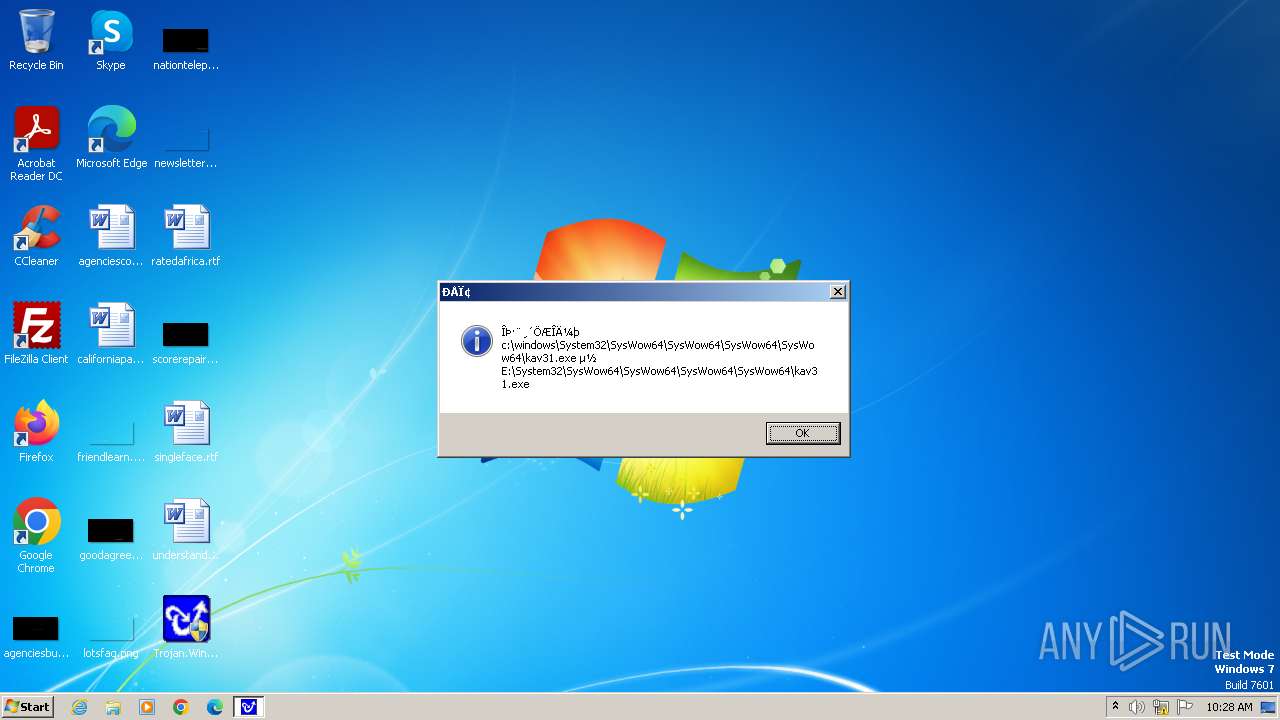
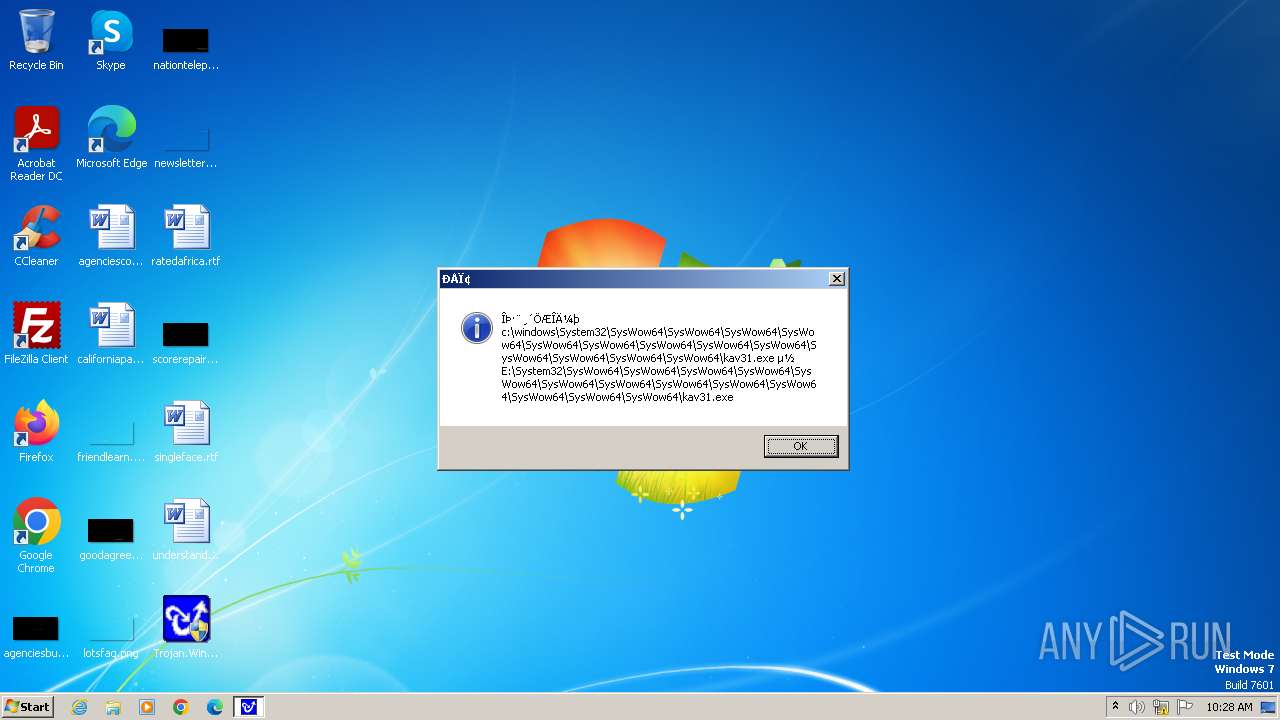
| 1776 | Trojan.Win32.Gentee.b.exe | C:\Windows\System32\kav31.exe | executable | |
MD5:A24BAF845C8F84CEB1D9D6CB7363E99D | SHA256:0E190F4767B0B6552B5261501428274DDD7A9EF38399E6476F6E8BECC094C7D3 | |||
| 1776 | Trojan.Win32.Gentee.b.exe | C:\Windows\System32\SysWow64\SysWow64\SysWow64\kav31.exe | executable | |
MD5:A24BAF845C8F84CEB1D9D6CB7363E99D | SHA256:0E190F4767B0B6552B5261501428274DDD7A9EF38399E6476F6E8BECC094C7D3 | |||
| 1776 | Trojan.Win32.Gentee.b.exe | C:\WINNT\kav31.exe | executable | |
MD5:A24BAF845C8F84CEB1D9D6CB7363E99D | SHA256:0E190F4767B0B6552B5261501428274DDD7A9EF38399E6476F6E8BECC094C7D3 | |||
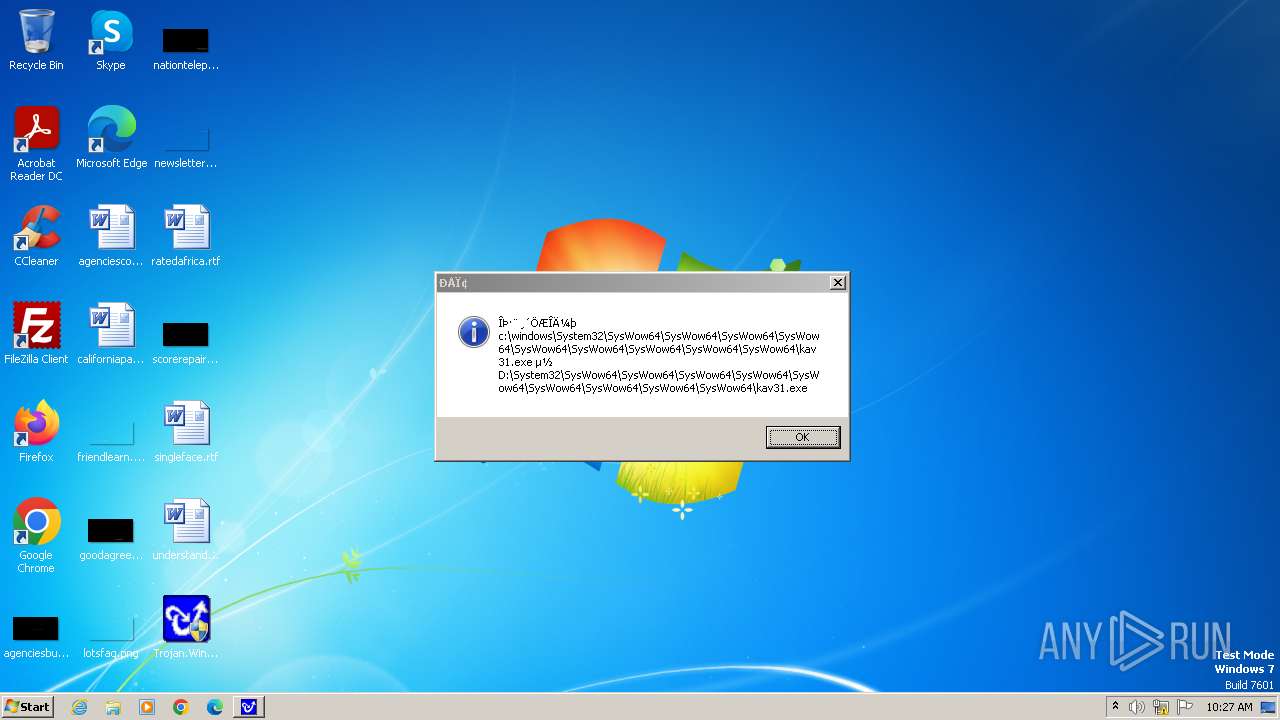
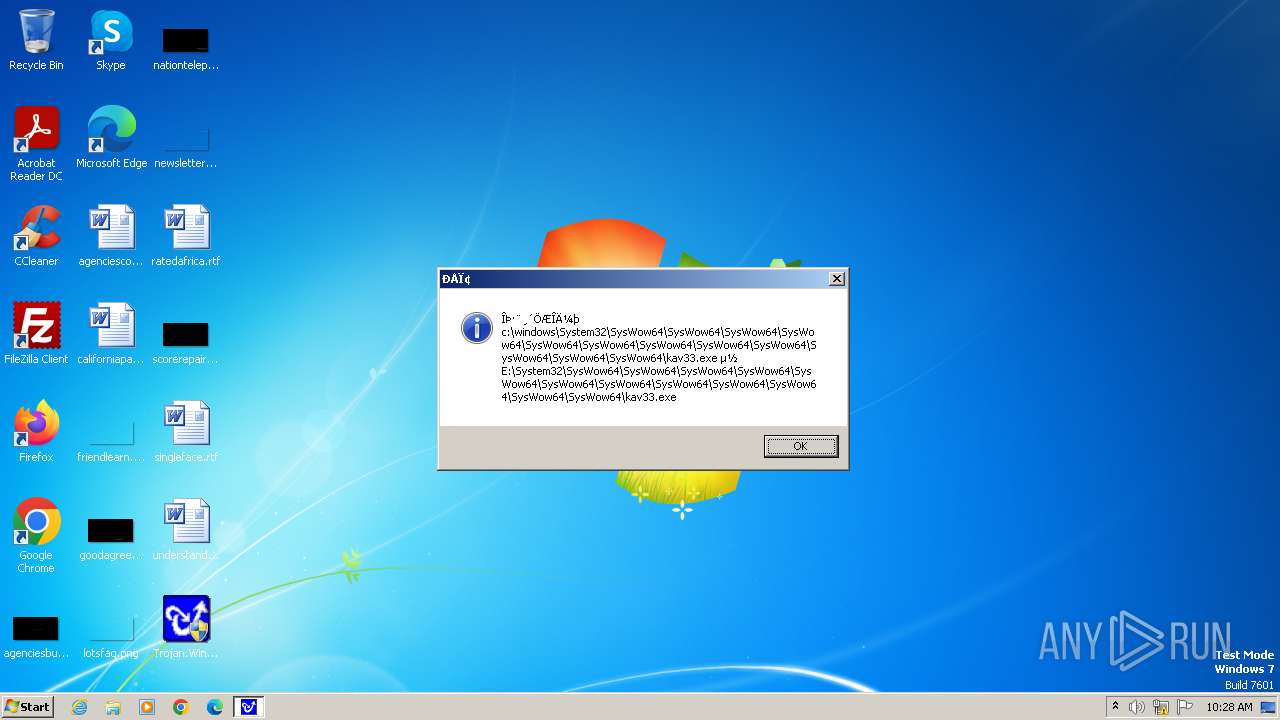
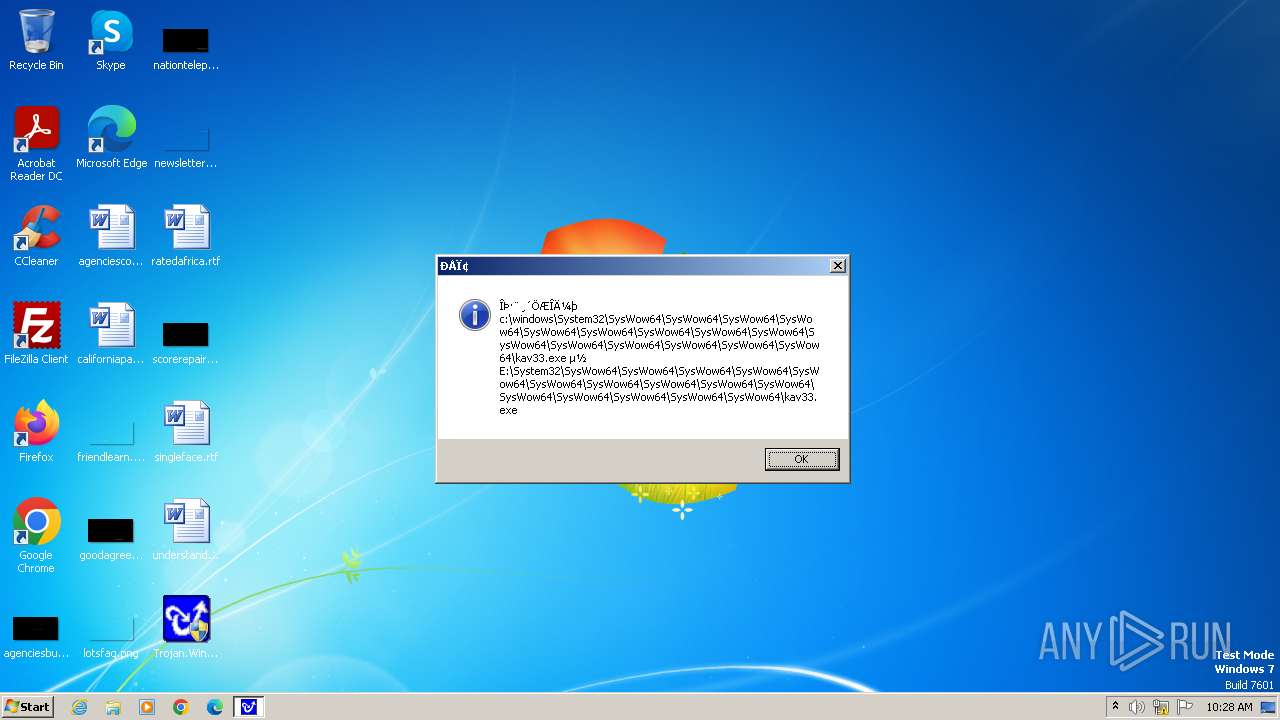
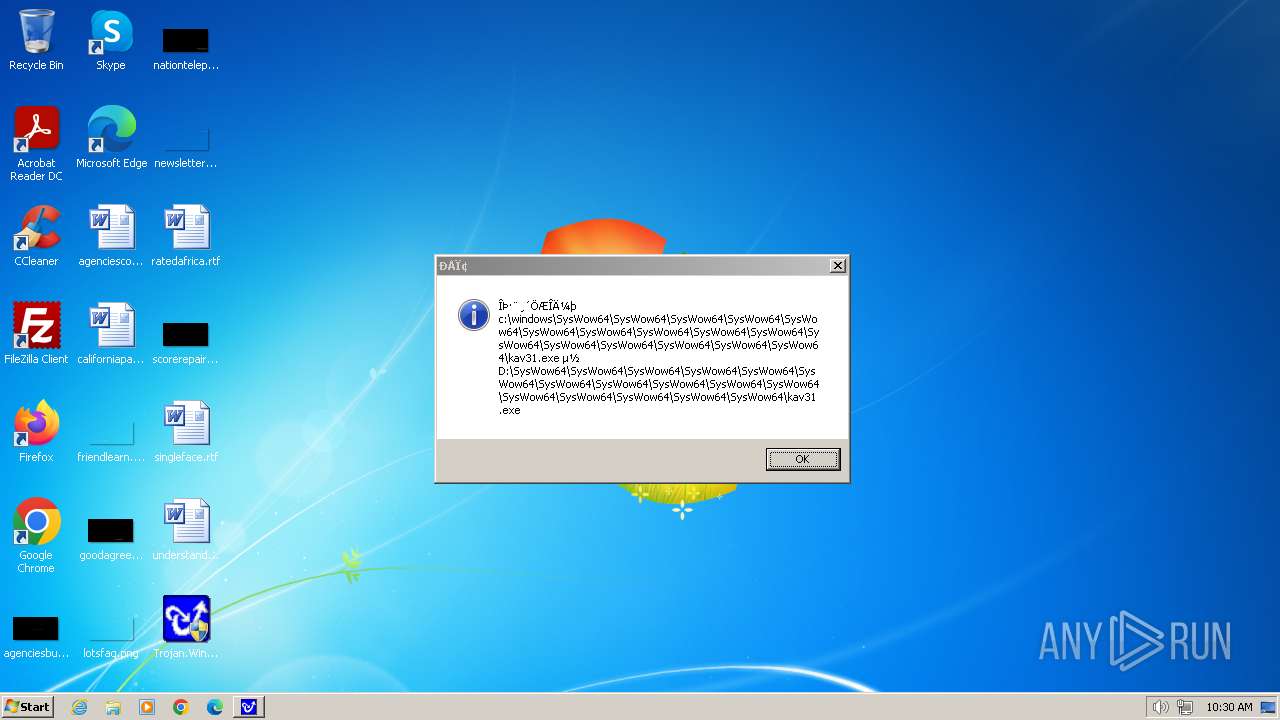
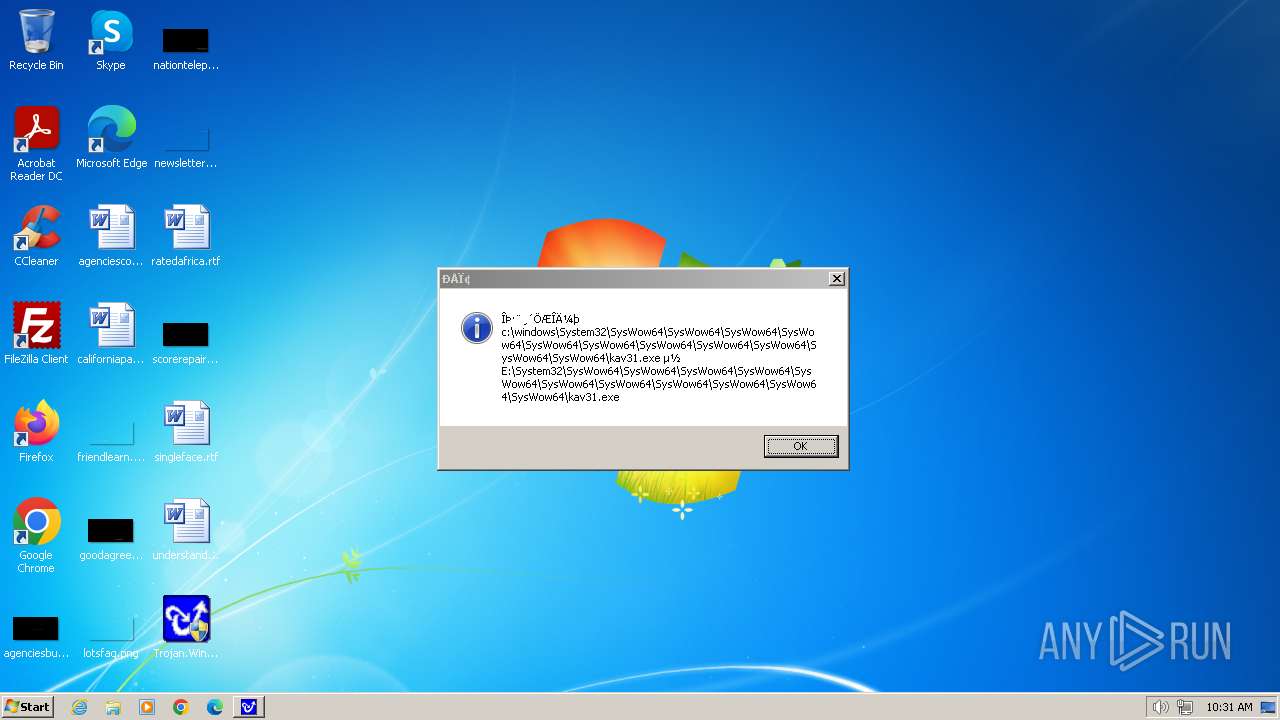
| 1776 | Trojan.Win32.Gentee.b.exe | C:\Windows\System32\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\kav31.exe | executable | |
MD5:A24BAF845C8F84CEB1D9D6CB7363E99D | SHA256:0E190F4767B0B6552B5261501428274DDD7A9EF38399E6476F6E8BECC094C7D3 | |||
| 1776 | Trojan.Win32.Gentee.b.exe | C:\Windows\System32\SysWow64\kav31.exe | executable | |
MD5:A24BAF845C8F84CEB1D9D6CB7363E99D | SHA256:0E190F4767B0B6552B5261501428274DDD7A9EF38399E6476F6E8BECC094C7D3 | |||
| 1776 | Trojan.Win32.Gentee.b.exe | C:\Windows\kav32.exe | executable | |
MD5:818E24366BFAC904FE06925BC90334BE | SHA256:3F96BA63285220B7881365467BE21AE1FDE147A0EC09B89A5FB2CA4E24D0066B | |||
| 1776 | Trojan.Win32.Gentee.b.exe | C:\Windows\System32\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\SysWow64\kav31.exe | executable | |
MD5:A24BAF845C8F84CEB1D9D6CB7363E99D | SHA256:0E190F4767B0B6552B5261501428274DDD7A9EF38399E6476F6E8BECC094C7D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
14
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1580 | sipnotify.exe | HEAD | 200 | 23.197.138.118:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133770041807960000 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1092 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
1580 | sipnotify.exe | 23.197.138.118:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |