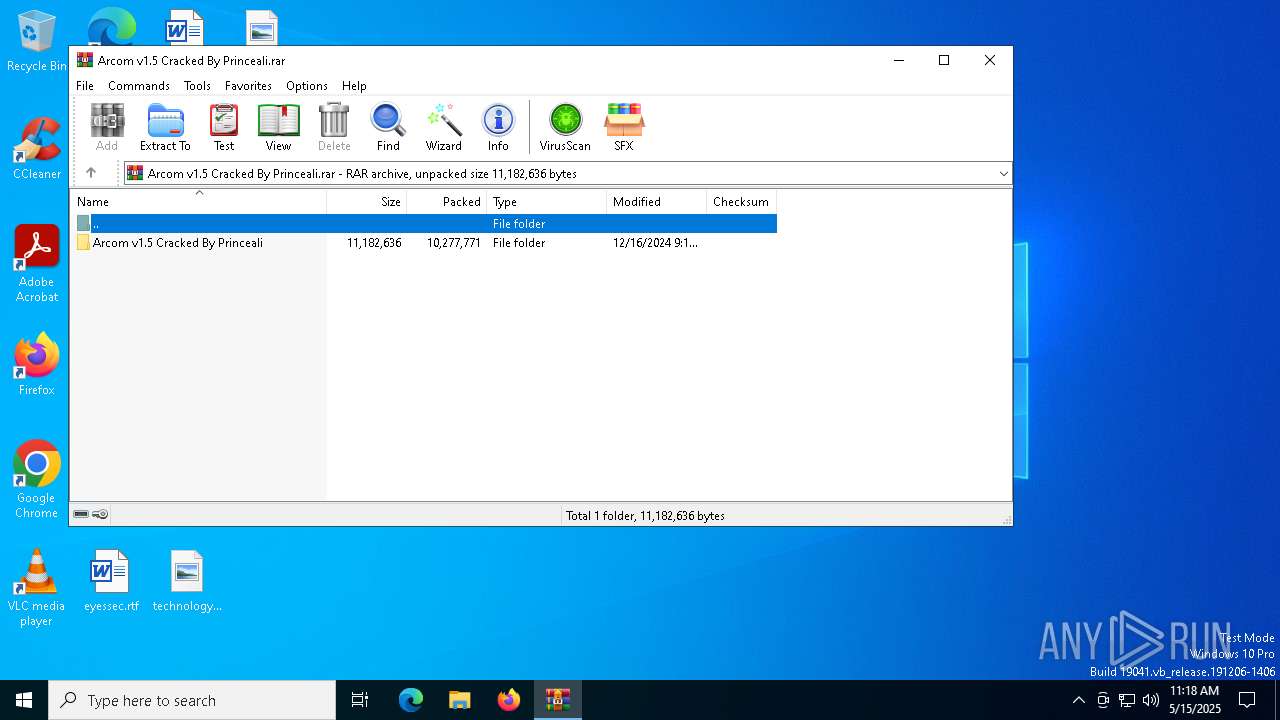
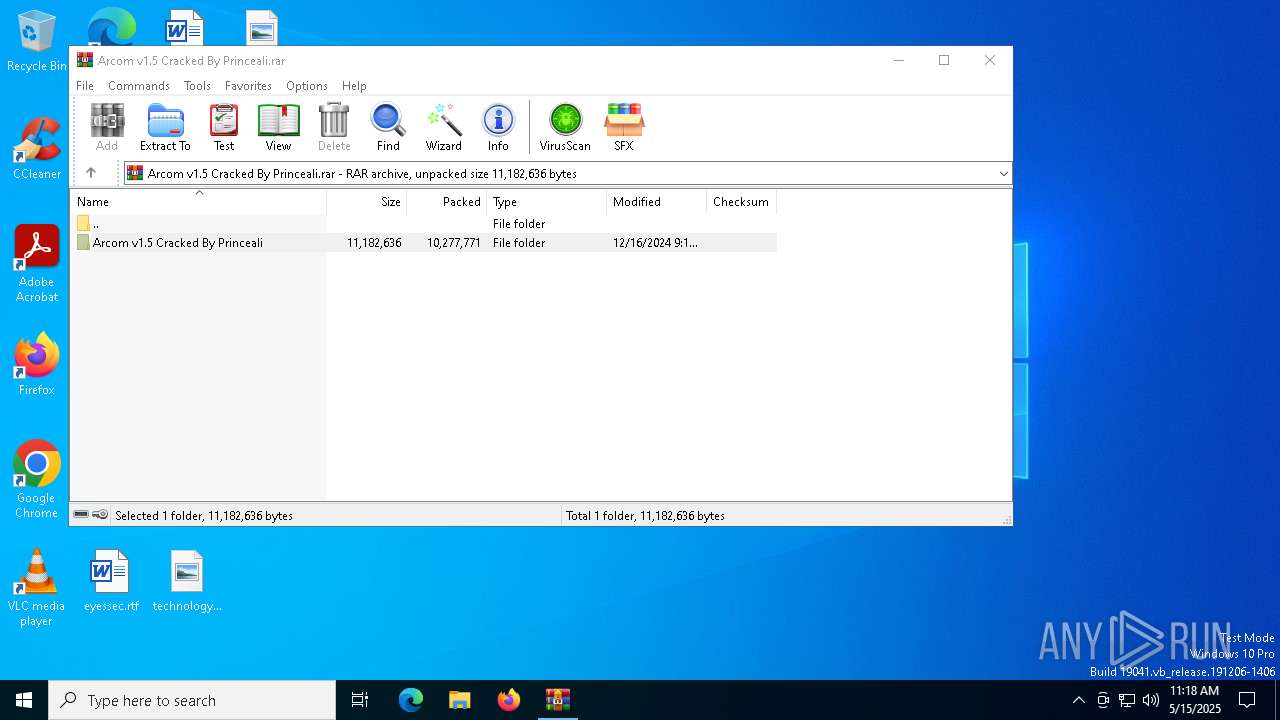
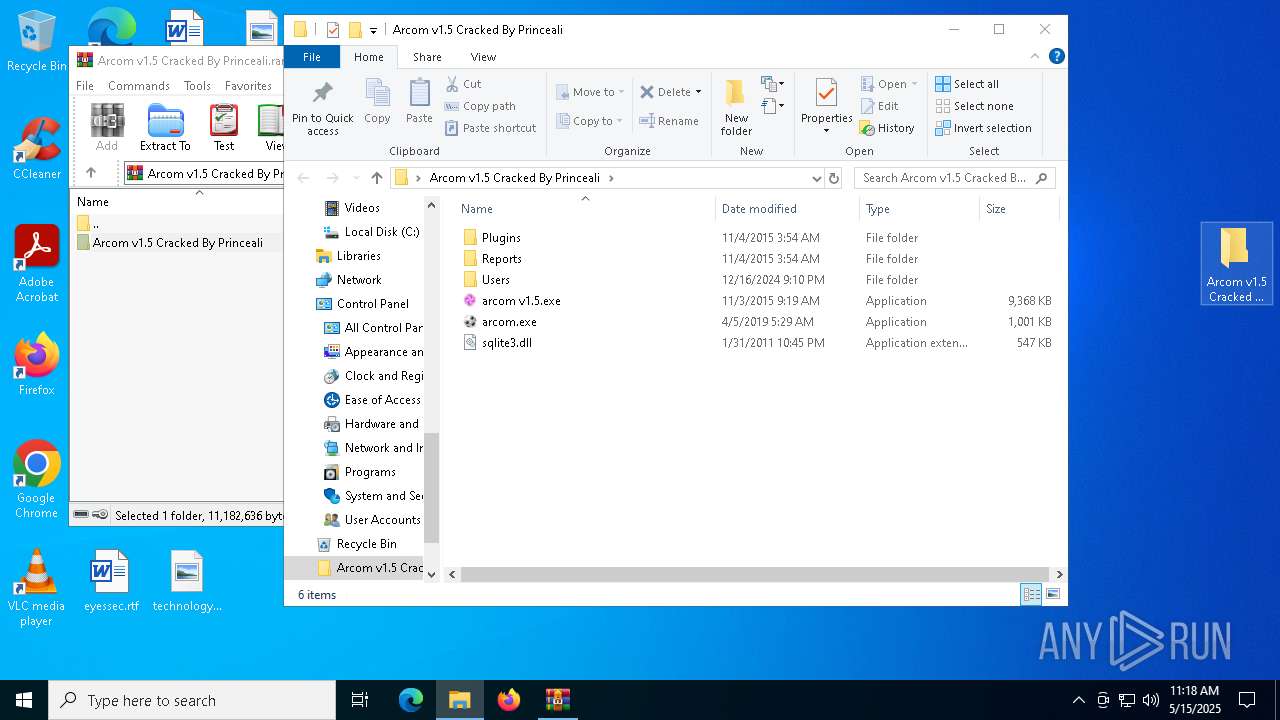
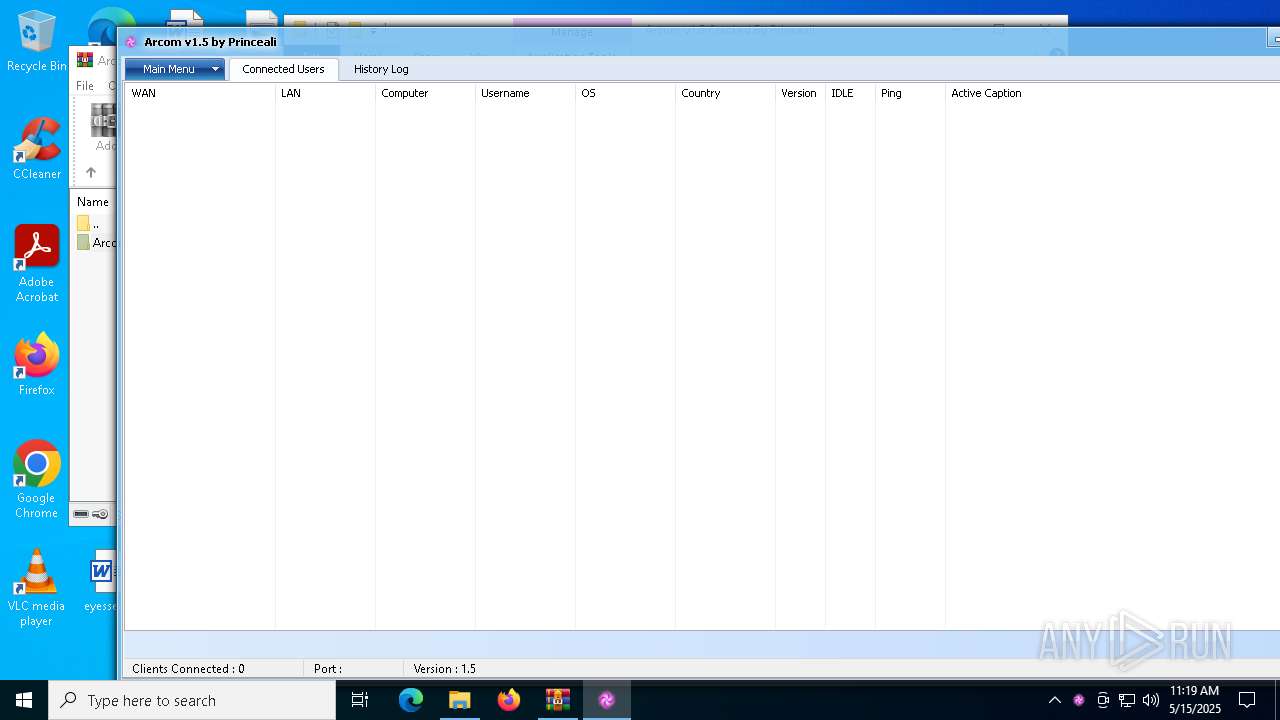
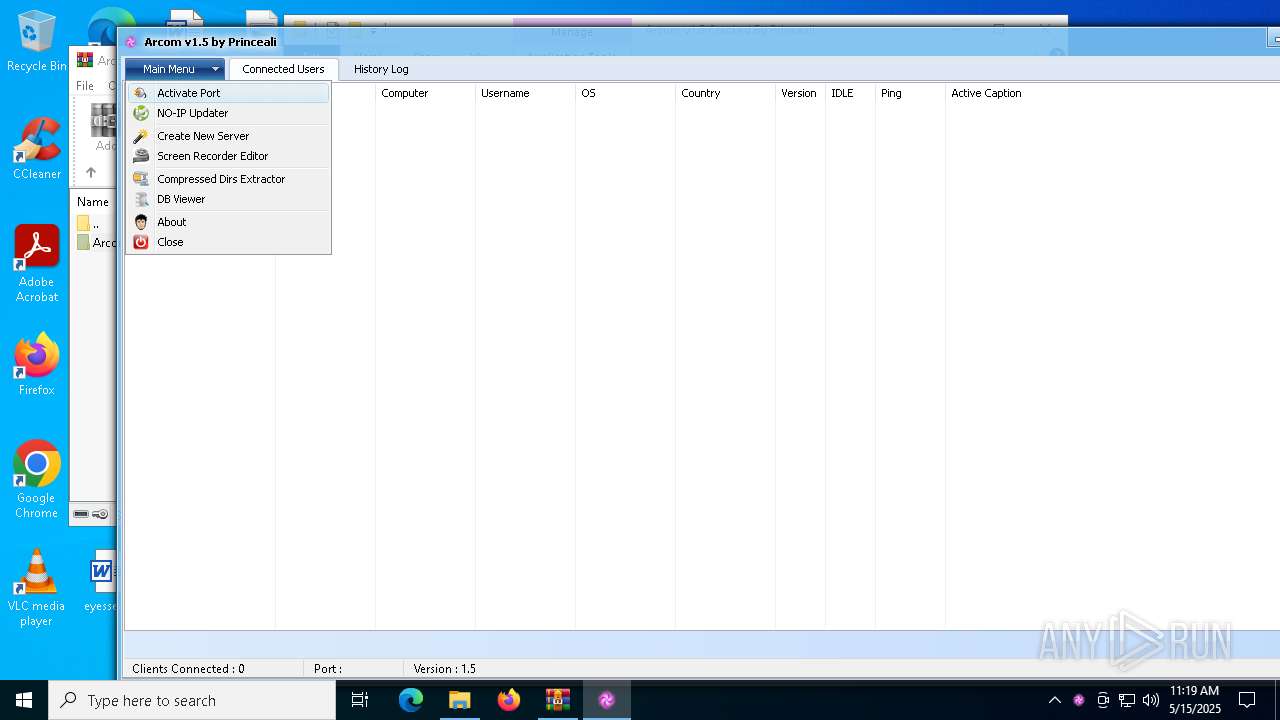
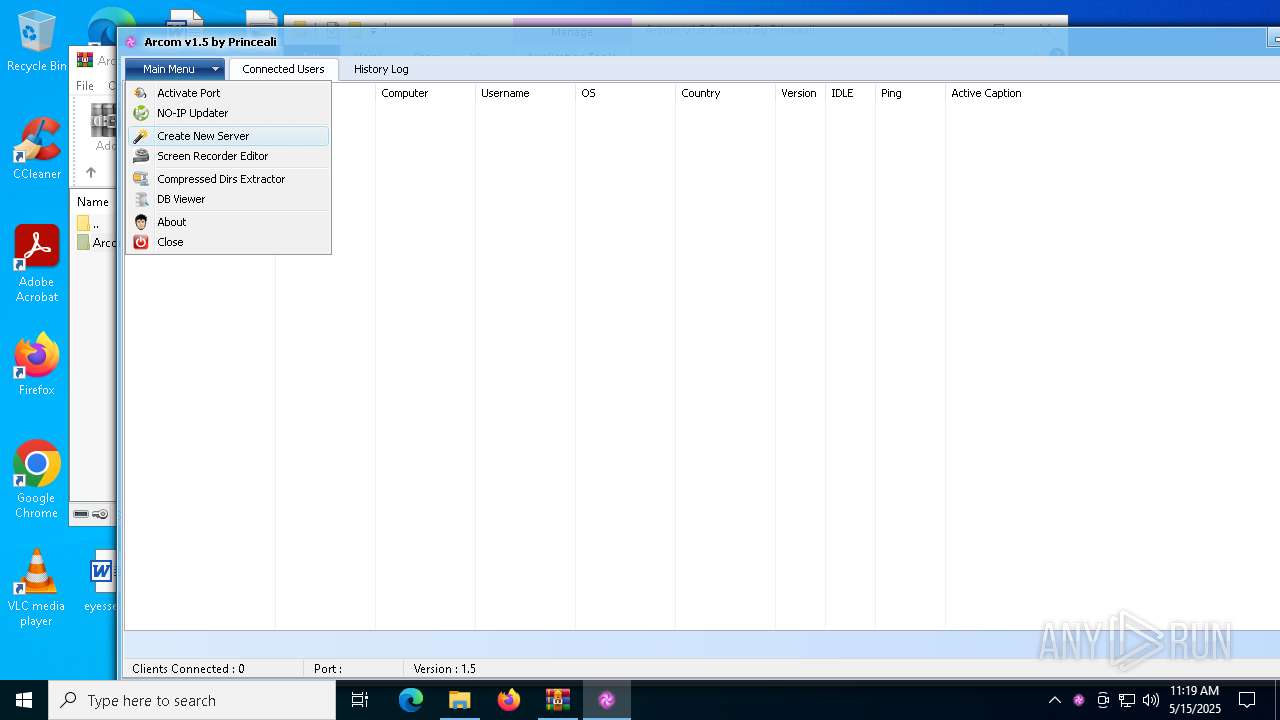
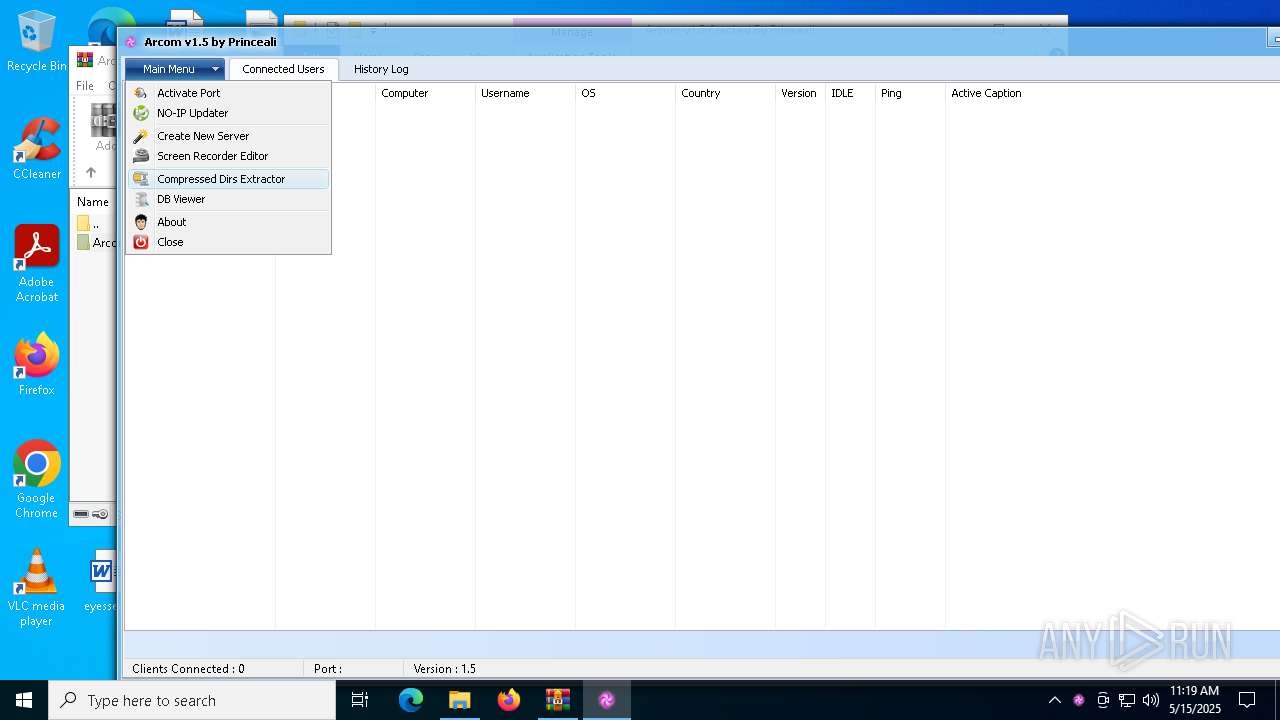
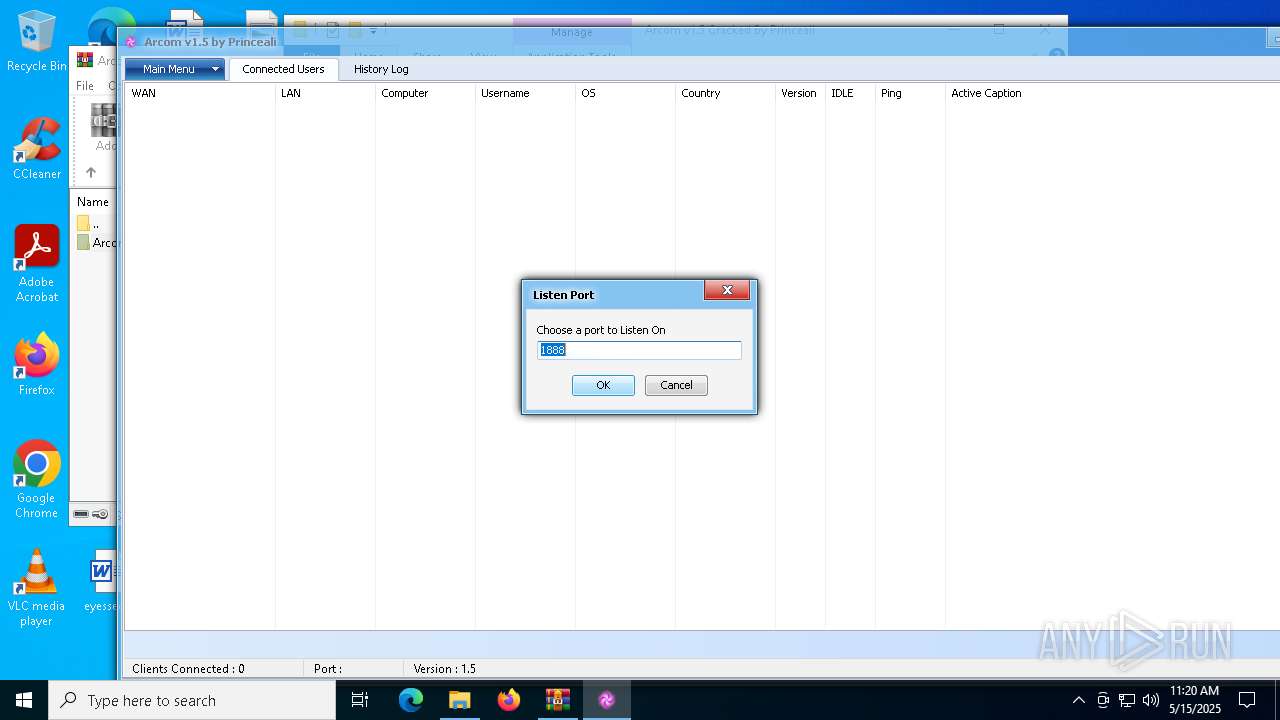
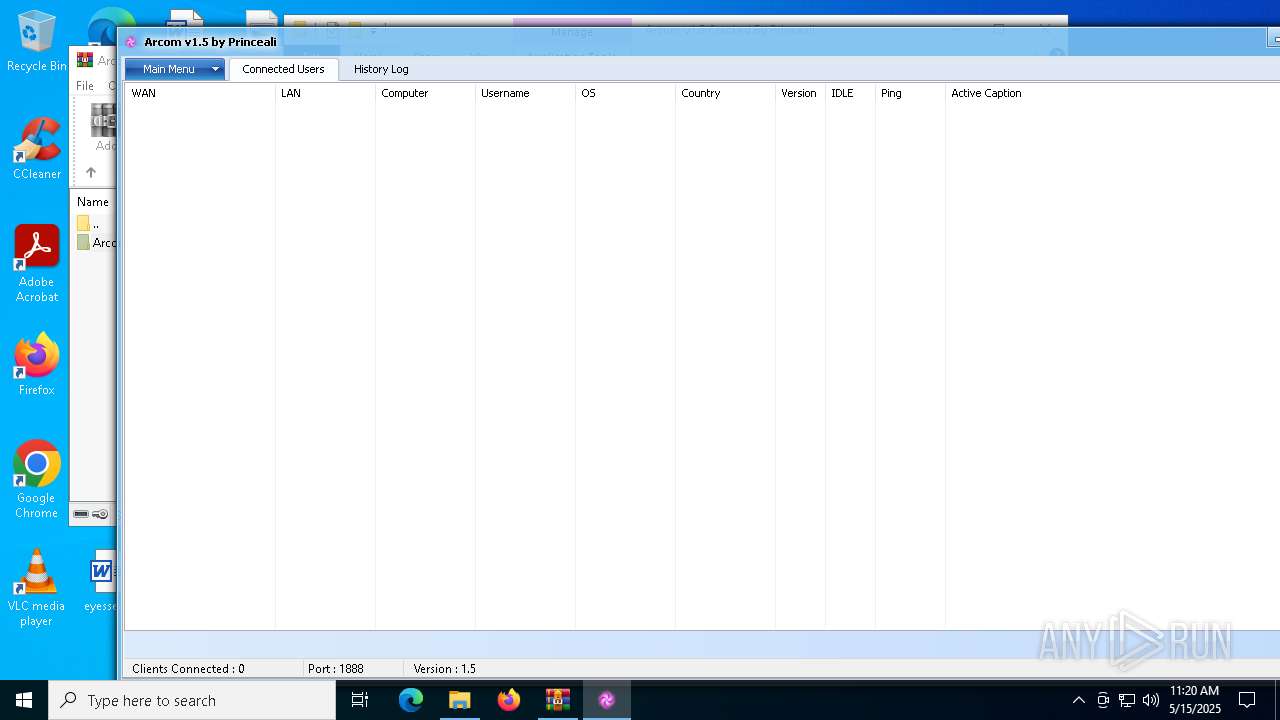
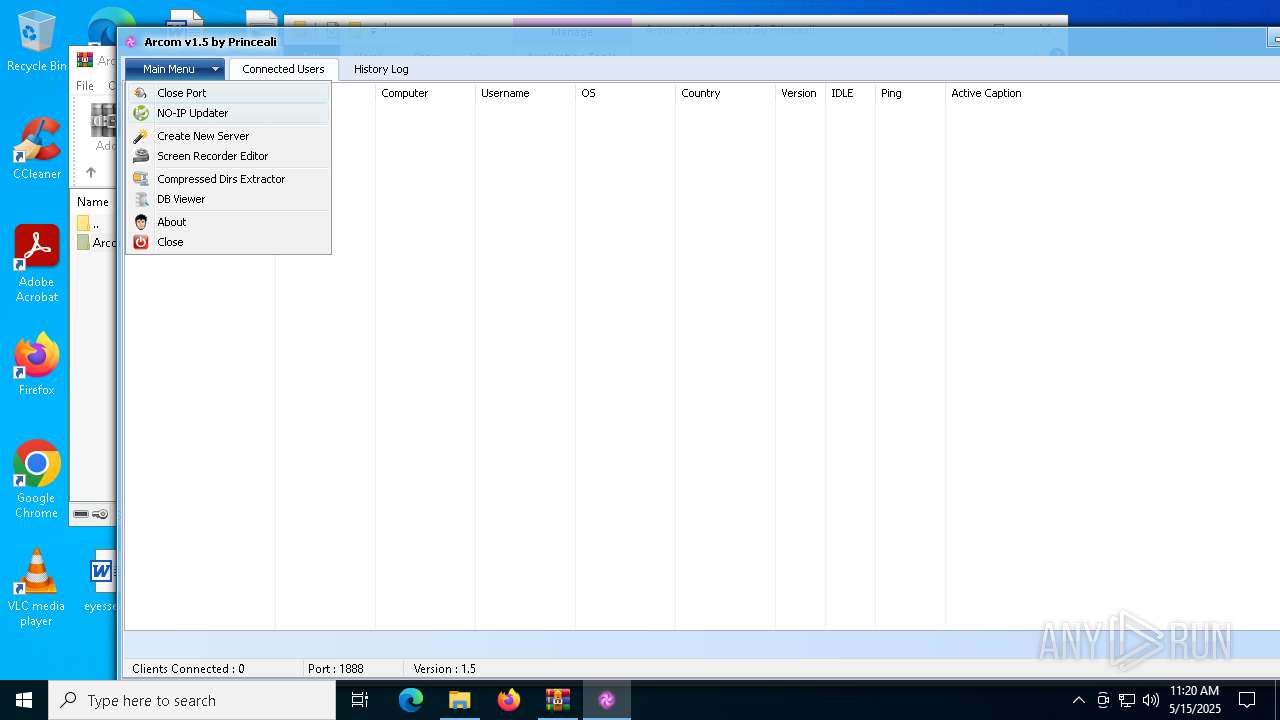
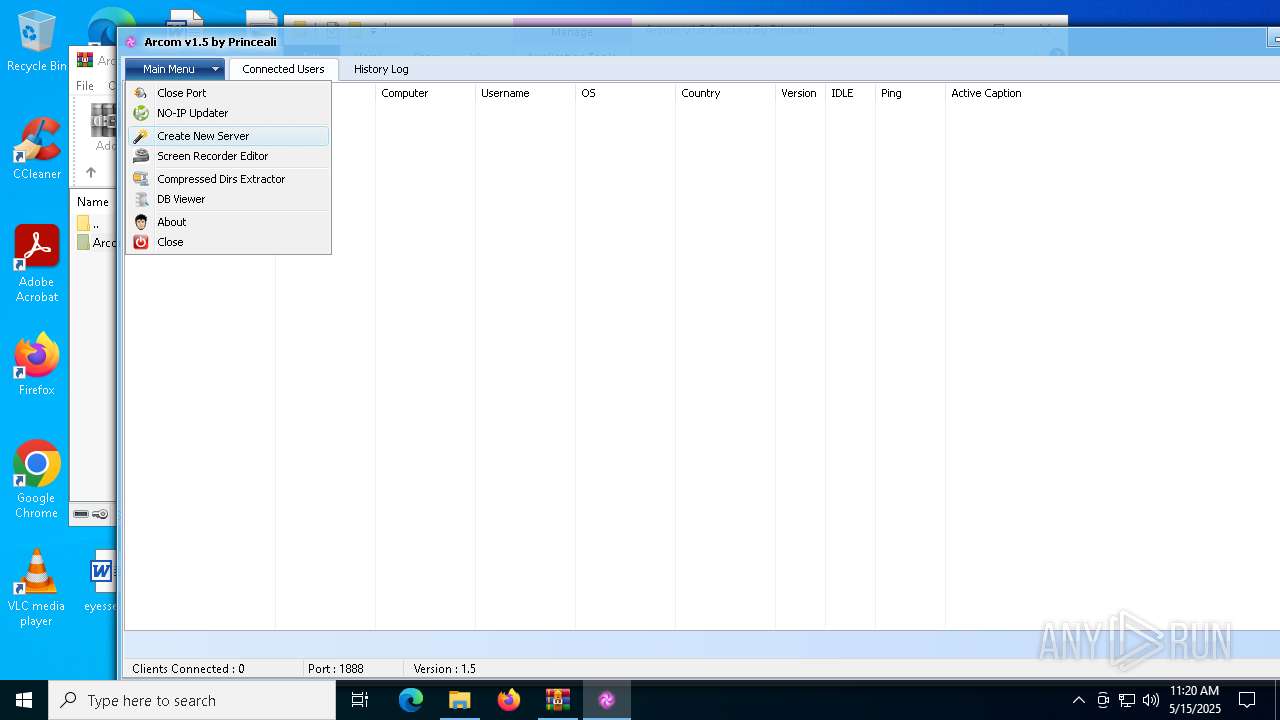
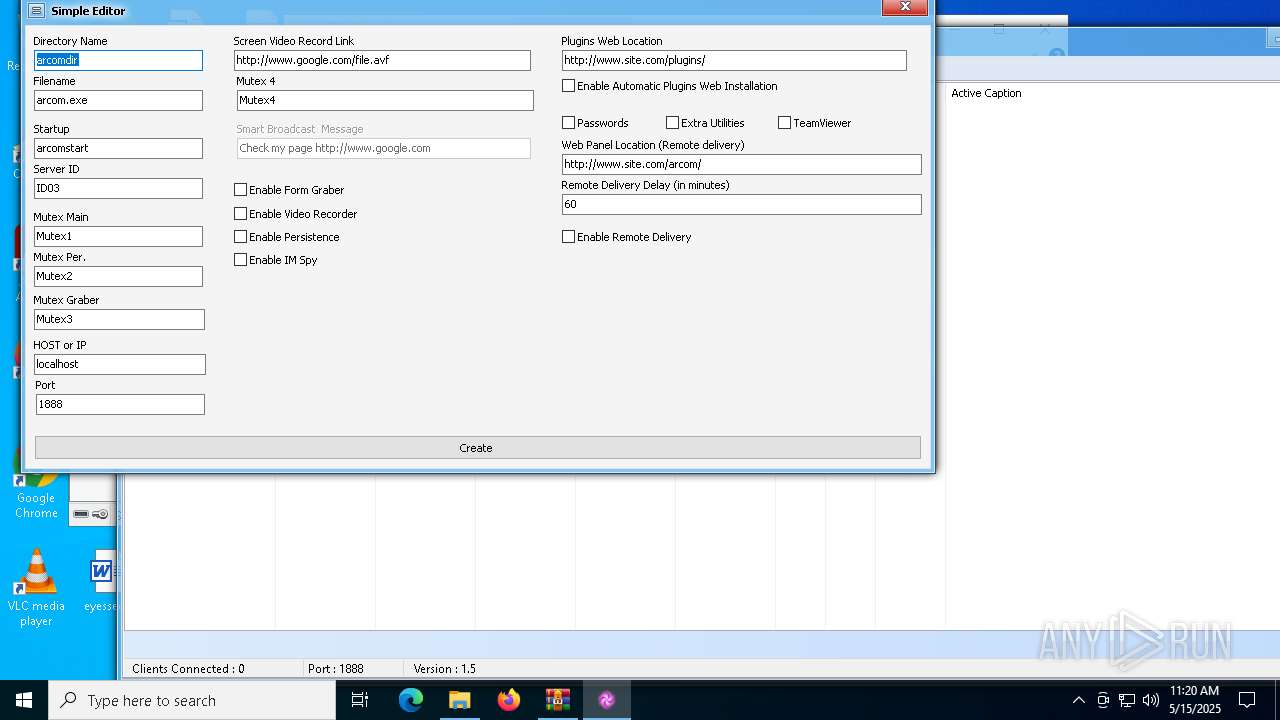
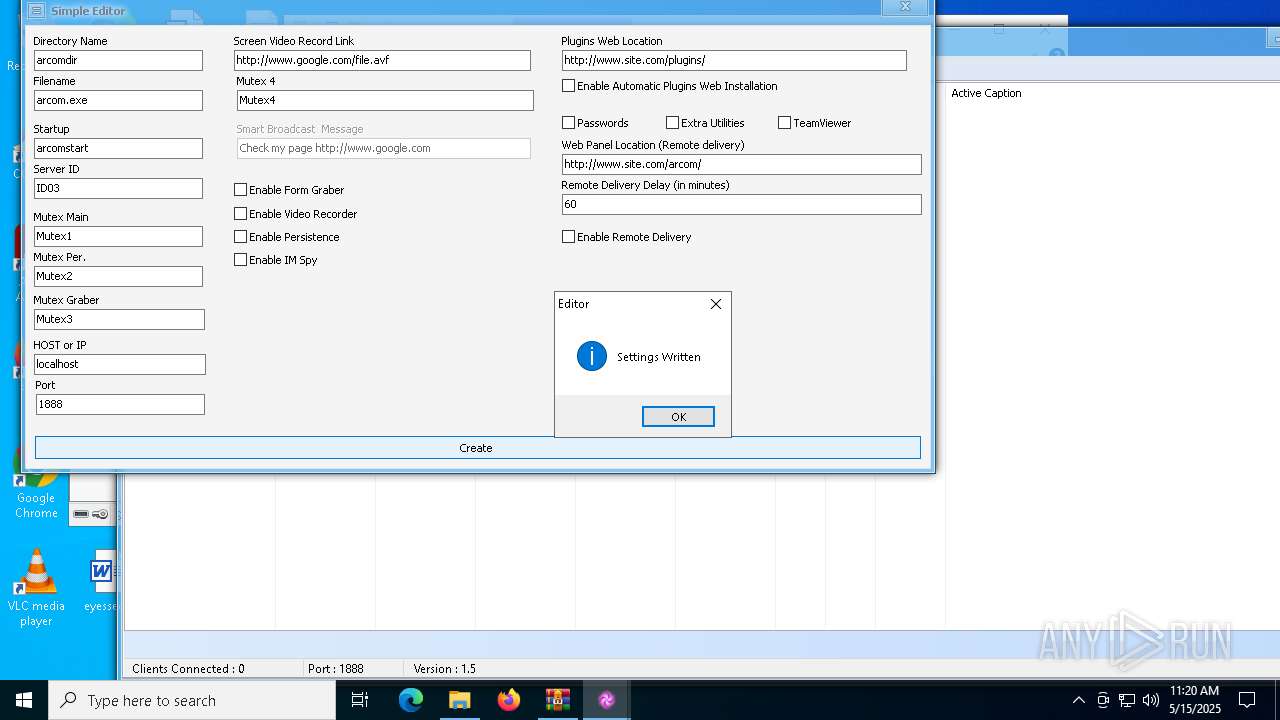
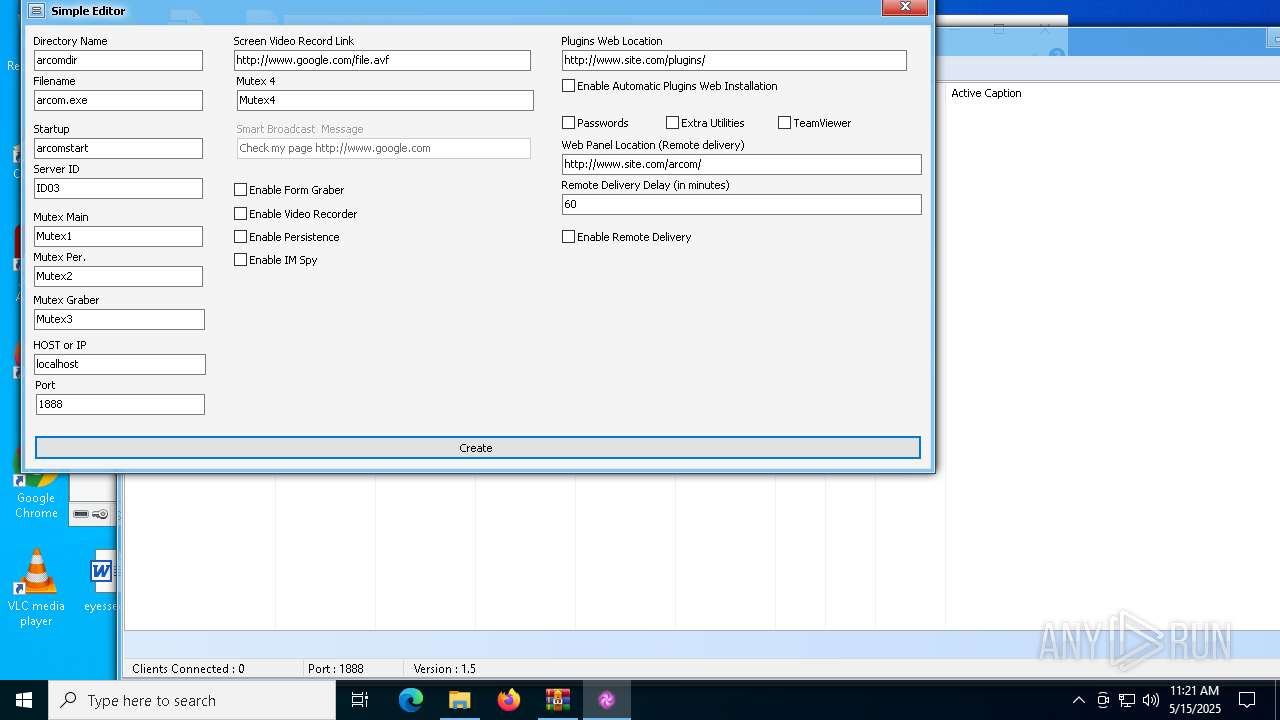
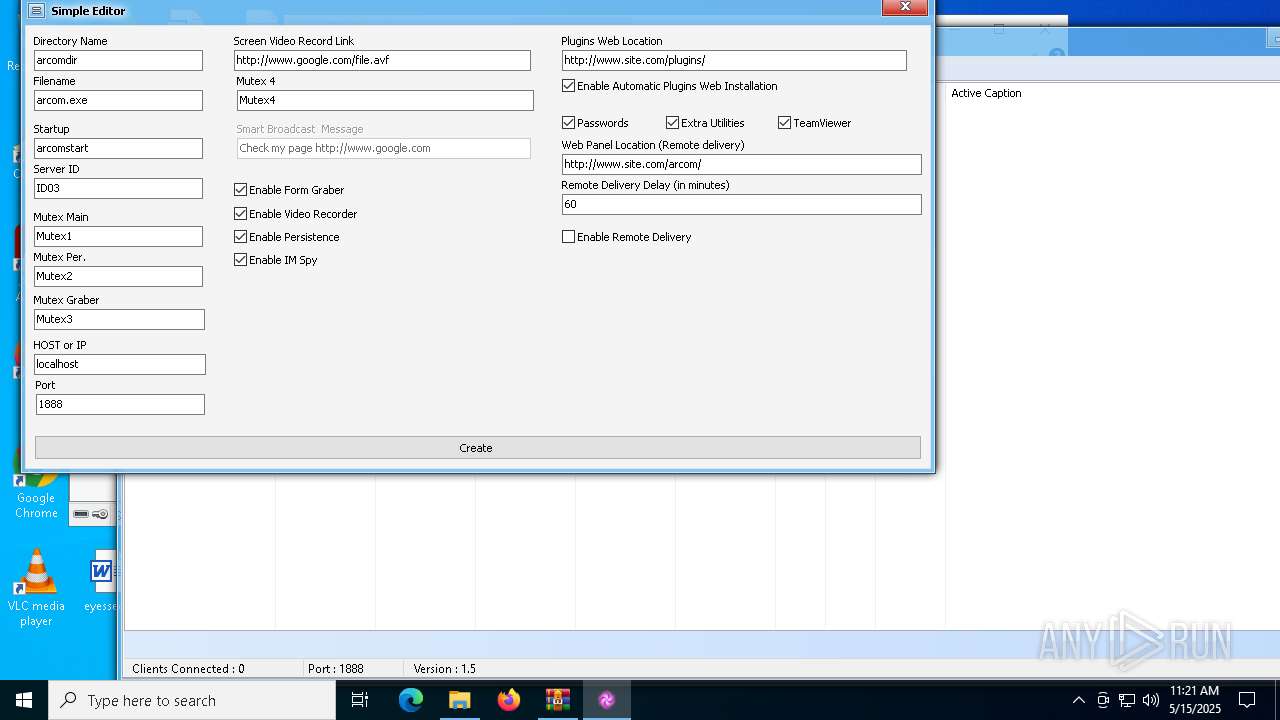
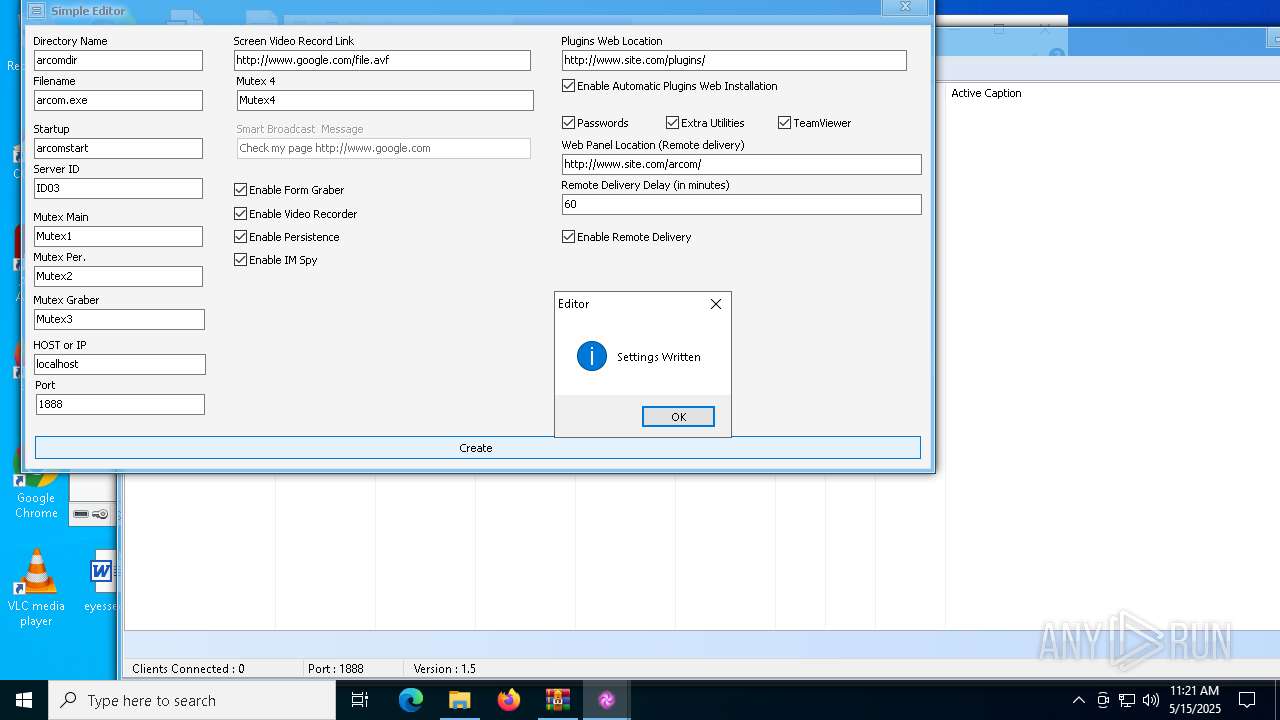
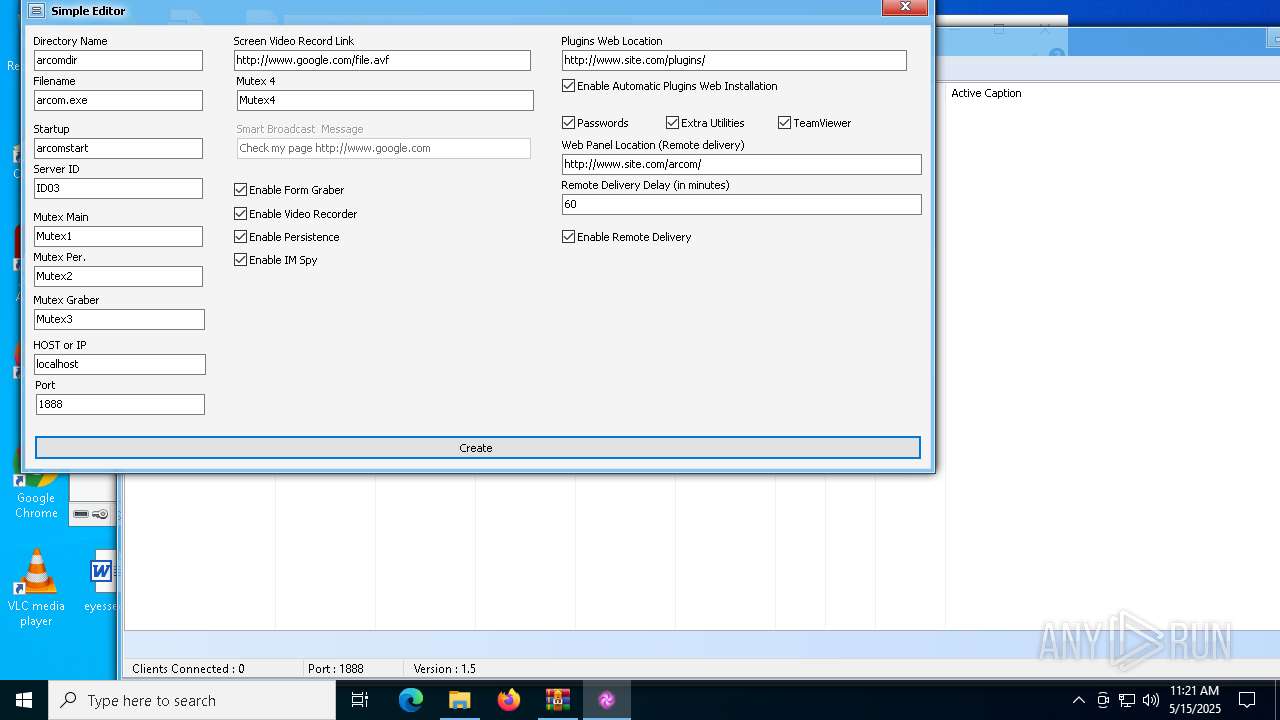
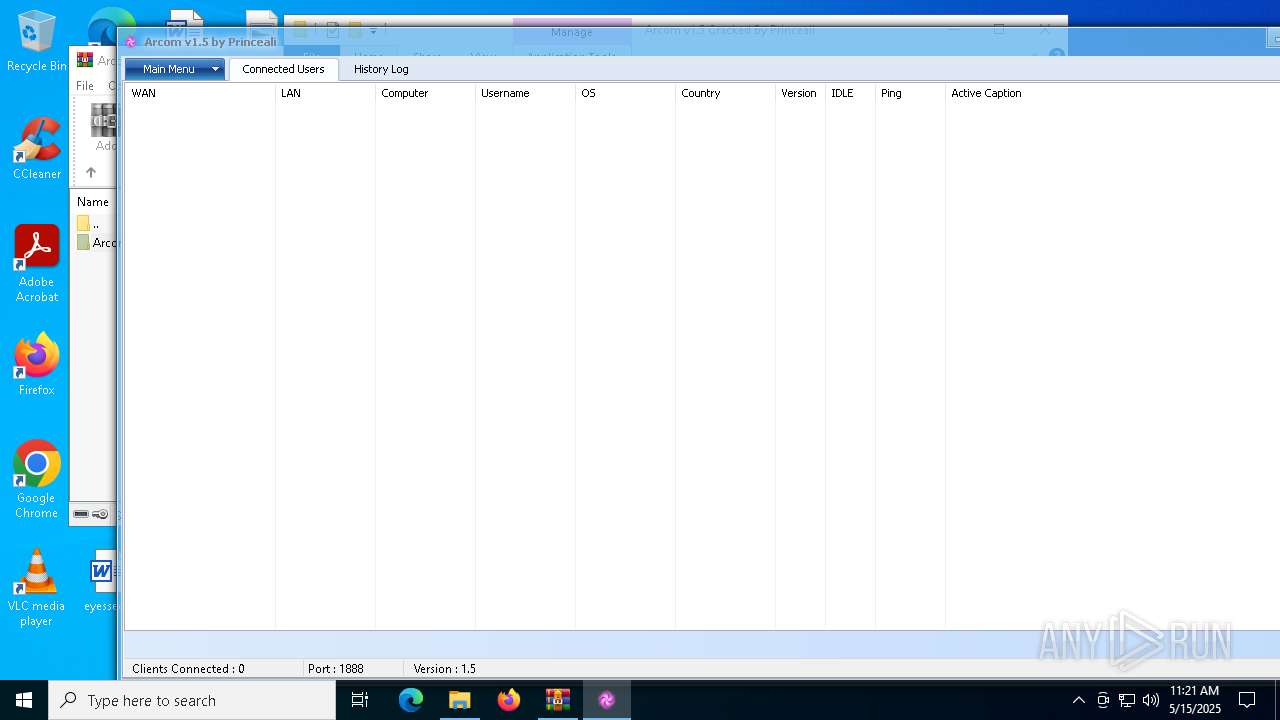
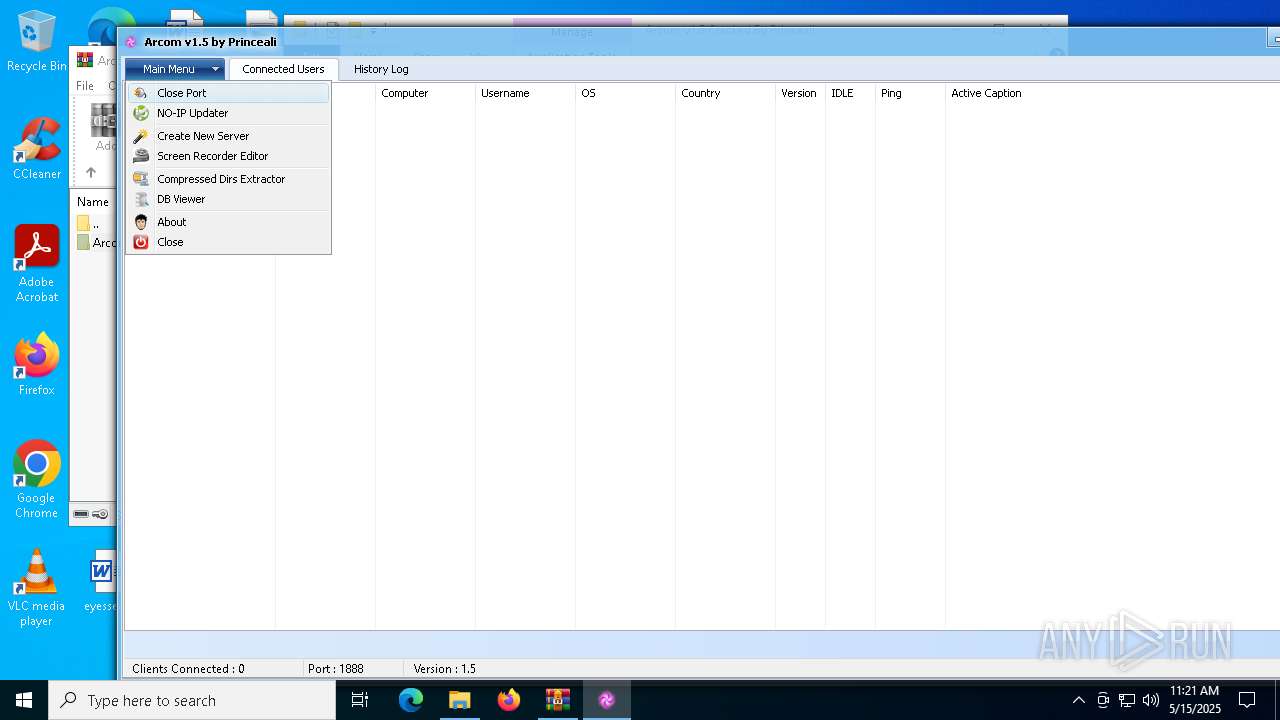
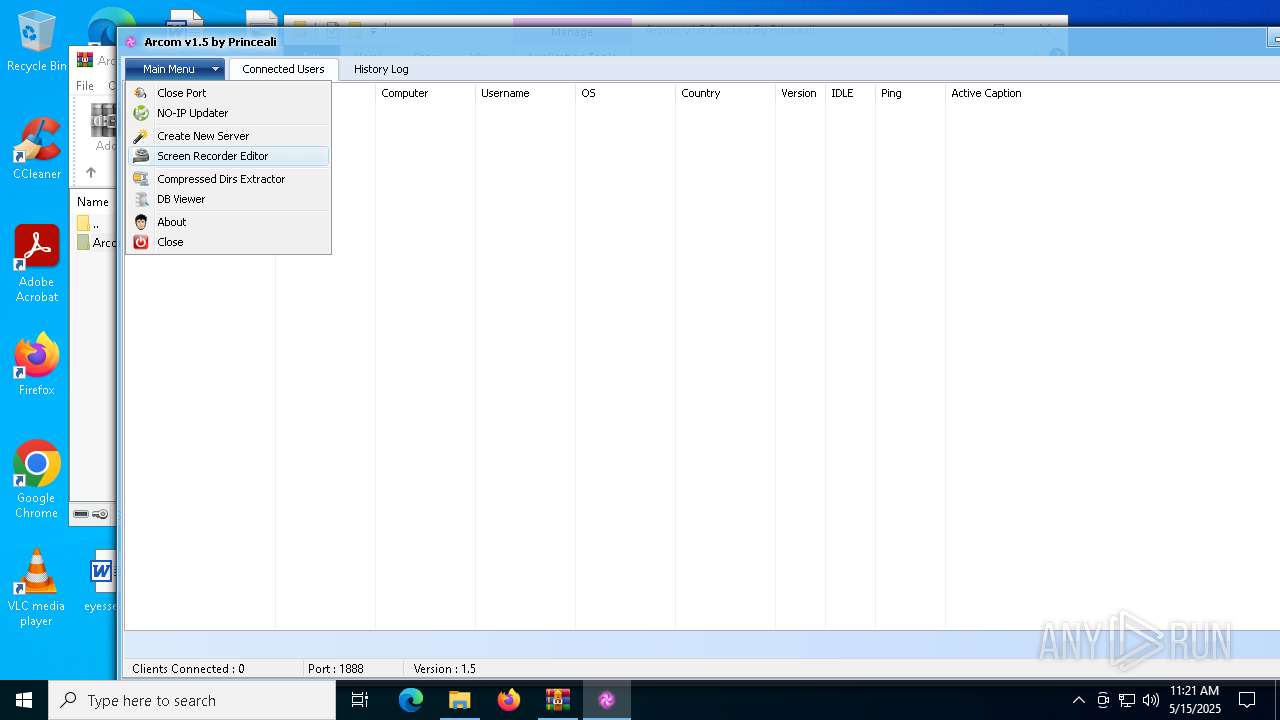
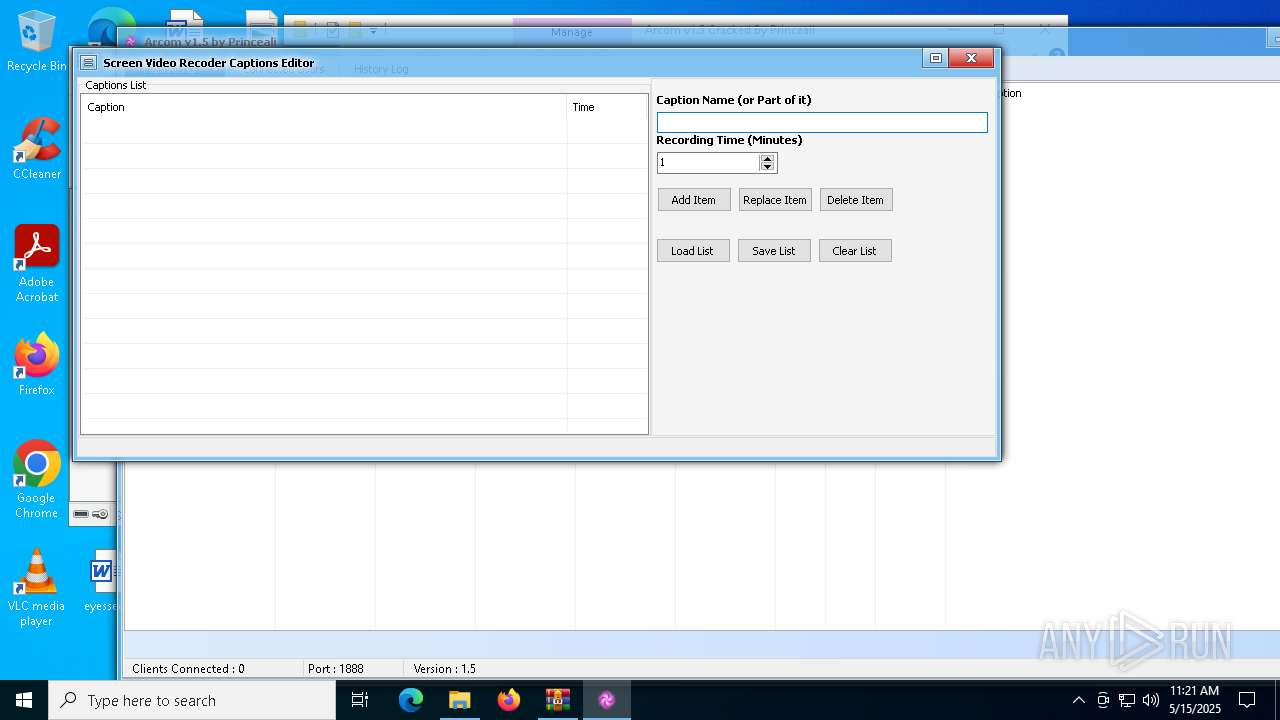
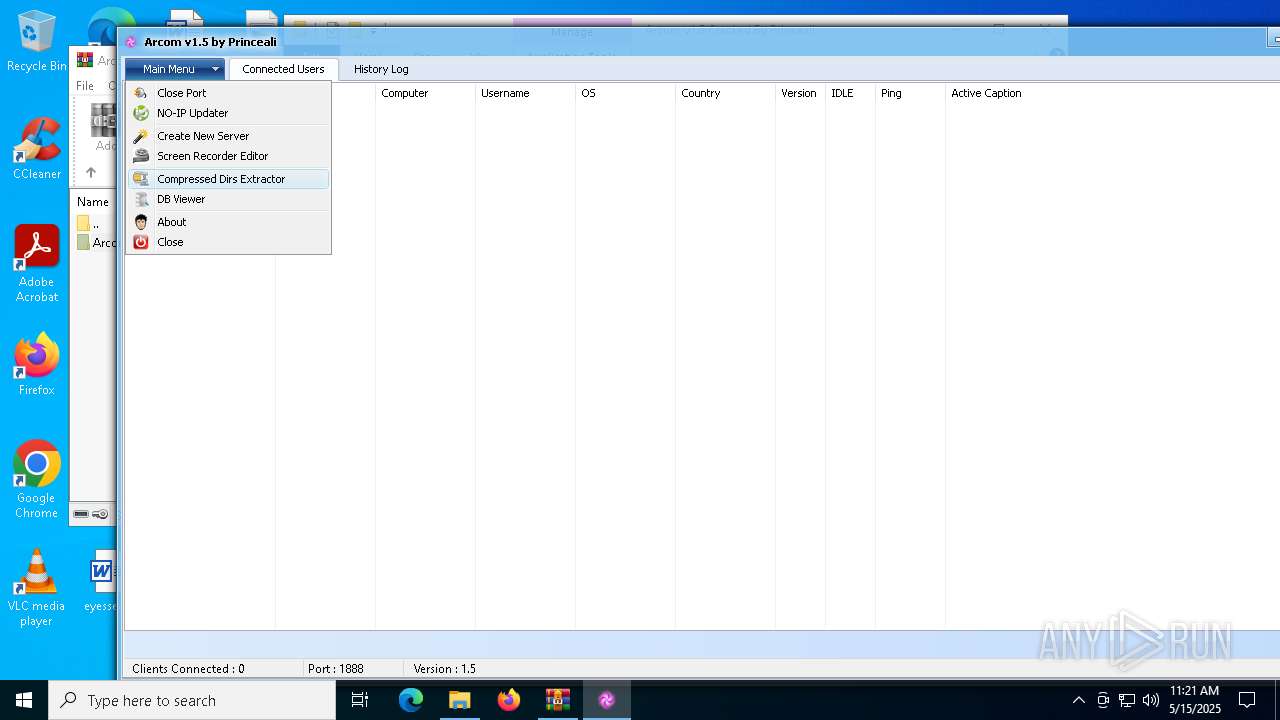
| File name: | Arcom v1.5 Cracked By Princeali.rar |
| Full analysis: | https://app.any.run/tasks/9268a07f-ebab-4ce2-b0e7-e1fcc88db999 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 11:18:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 8D206CF1B6D494B0EEF6292D8CAF5BD1 |
| SHA1: | 8F8912FE214FEAC2ACD0AE2C5D52CA2773B26CAD |
| SHA256: | 350A8E87CC064F23F8B9D180BE3944F3F7B4E23F17ABB3C73976515B65050EF3 |
| SSDEEP: | 98304:sI3SO6UG0rjLBumw25fynb+RNokRLPM+NO9LIh4gnoVo2X1FYpAh42B1aqwsBhMZ:ZoTAYP0IwplXKLn2B8+ |
MALICIOUS
Executing a file with an untrusted certificate
- arcom.exe (PID: 5384)
SUSPICIOUS
Reads security settings of Internet Explorer
- arcom v1.5.exe (PID: 6048)
There is functionality for VM detection VirtualBox (YARA)
- arcom v1.5.exe (PID: 6048)
There is functionality for taking screenshot (YARA)
- arcom v1.5.exe (PID: 6048)
There is functionality for communication over UDP network (YARA)
- arcom v1.5.exe (PID: 6048)
INFO
Checks supported languages
- arcom v1.5.exe (PID: 6048)
- arcom.exe (PID: 5384)
Manual execution by a user
- arcom v1.5.exe (PID: 6048)
- arcom.exe (PID: 5384)
The sample compiled with english language support
- WinRAR.exe (PID: 4428)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4428)
Reads the computer name
- arcom v1.5.exe (PID: 6048)
Themida protector has been detected
- arcom v1.5.exe (PID: 6048)
Enigma protector has been detected
- arcom v1.5.exe (PID: 6048)
Creates files or folders in the user directory
- arcom.exe (PID: 5384)
Compiled with Borland Delphi (YARA)
- arcom v1.5.exe (PID: 6048)
- slui.exe (PID: 5048)
Checks proxy server information
- slui.exe (PID: 5048)
Reads the software policy settings
- slui.exe (PID: 5048)
Create files in a temporary directory
- arcom v1.5.exe (PID: 6048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 9330777 |
| UncompressedSize: | 9592320 |
| OperatingSystem: | Win32 |
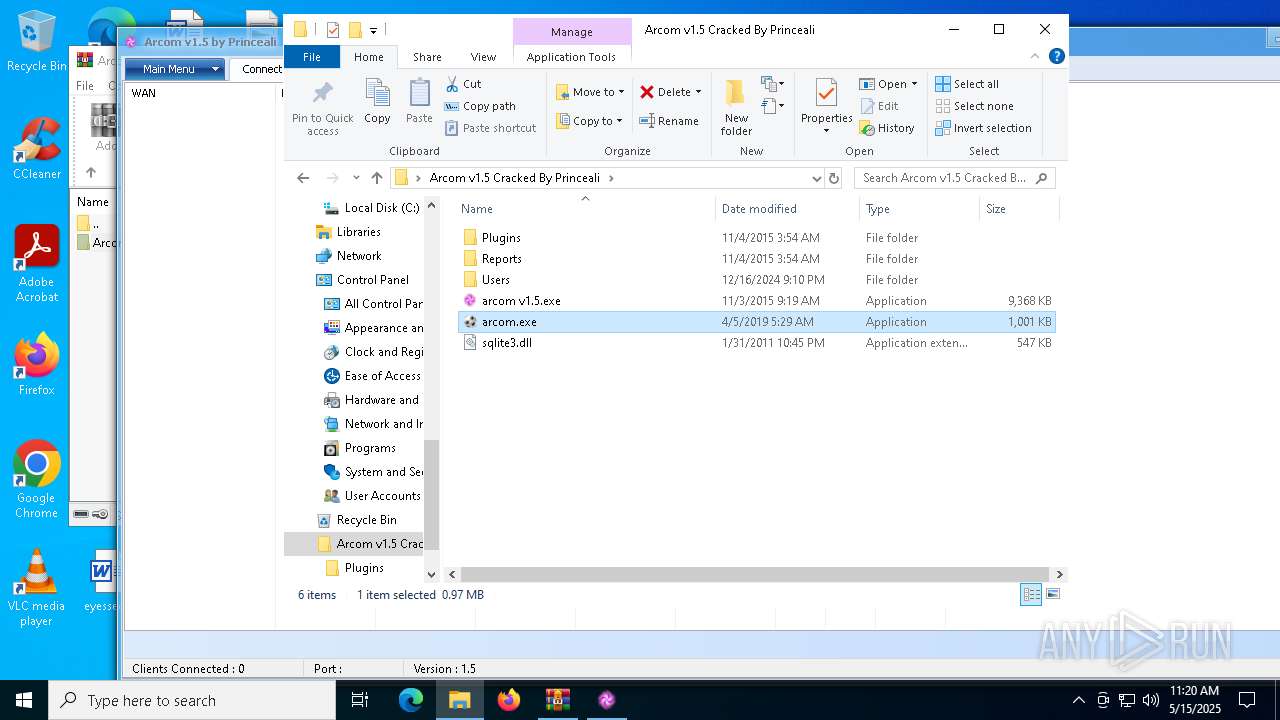
| ArchivedFileName: | Arcom v1.5 Cracked By Princeali/arcom v1.5.exe |
Total processes
133
Monitored processes
6
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2980 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | arcom.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 4428 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Arcom v1.5 Cracked By Princeali.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4488 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5048 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5384 | "C:\Users\admin\Desktop\Arcom v1.5 Cracked By Princeali\arcom.exe" | C:\Users\admin\Desktop\Arcom v1.5 Cracked By Princeali\arcom.exe | explorer.exe | ||||||||||||
User: admin Company: Mirage International Integrity Level: HIGH Description: Mirage Protection Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6048 | "C:\Users\admin\Desktop\Arcom v1.5 Cracked By Princeali\arcom v1.5.exe" | C:\Users\admin\Desktop\Arcom v1.5 Cracked By Princeali\arcom v1.5.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 768
Read events
4 759
Write events
9
Delete events
0
Modification events
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Arcom v1.5 Cracked By Princeali.rar | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5384) arcom.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft |
| Operation: | write | Name: | 2980 |
Value: b2L8MhrkN2aMaxcA1hT6Tq4anp5Cuyz0LGjsYE1dqLCFX+M/dplXp8PIQqYv5sKbsP68HenNl1jM1Iu8yFROzdIDmGuyuFeLdiTuCfnJ3tRhNgU7v6PIYIffCDqJH9VmDA9O6XETk/ys8uvKner9GfkyixS0m7U1Fw/CYZ8M5vUJqr1h5R1uHOrRXYN3/zJxu0w4qlABvMNzQlIdMLeOujaqSDbkBTHhS1wNsXkSi8xmUz7JdqFwyHBTU7eTTSGjbhU8VVbi8LRqjMcyaAoUZwM4yiCH1r83ijBBzsWydcO4b74A2PhEkhJS4Shmqps5zNQfEfVxohlmSQQK6EiOPpdF12RAAbzUpgWBLFcJ6s1Ek3T8IIvdVpd6Yw8tzqbTTNpBbnQgpGdXTOlcSxX/3w== | |||
Executable files
3
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.23367\Arcom v1.5 Cracked By Princeali\arcom.exe | executable | |
MD5:05BBEC1886EF8BAB08E71166DE86AA1F | SHA256:FA53E96BD15D8B7CBC4FB35524646DBCF71BED03135AA6F76298B4339E8135F0 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.23367\Arcom v1.5 Cracked By Princeali\Users\info.db | binary | |
MD5:8753A4F57371CB97D8AEAAC999E27B2D | SHA256:4AE097975AFFC71682025CCFE0216B92851F4A3C35E8AE39E85EEB06B4182258 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.23367\Arcom v1.5 Cracked By Princeali\arcom v1.5.exe | executable | |
MD5:038B364A67160D5CA993CBE3B5D706ED | SHA256:03C1EDAB490344D062FAA9049BCCB952883CD79C17F16F0C9FDD0BD2A4DAB831 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.23367\Arcom v1.5 Cracked By Princeali\Users\connections.db | binary | |
MD5:08F83F450C022BF8466BD40F5ADA16B1 | SHA256:C01DDB6BA3F11FB59004642848E1B93A708336A08EA8E3BF62146A5A3E3B6A75 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.23367\Arcom v1.5 Cracked By Princeali\Users\client.db | binary | |
MD5:FE53710138FC4216187FD108528202A5 | SHA256:D9DA4CC2BA40809FCCEA63860DB1A2D5514A2119BF7E21D902BD3021D0F98184 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.23367\Arcom v1.5 Cracked By Princeali\sqlite3.dll | executable | |
MD5:B2232D645FAD62FD49D7D3EFCB7B5FB4 | SHA256:E21C530B616C6B0E4AC7A42731DB1F289CE686D871977FBC2F4DAEBCC48A76B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1328 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1328 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.19.11.105:80 | — | Elisa Oyj | NL | unknown |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1328 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1328 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1328 | SIHClient.exe | 20.3.187.198:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |