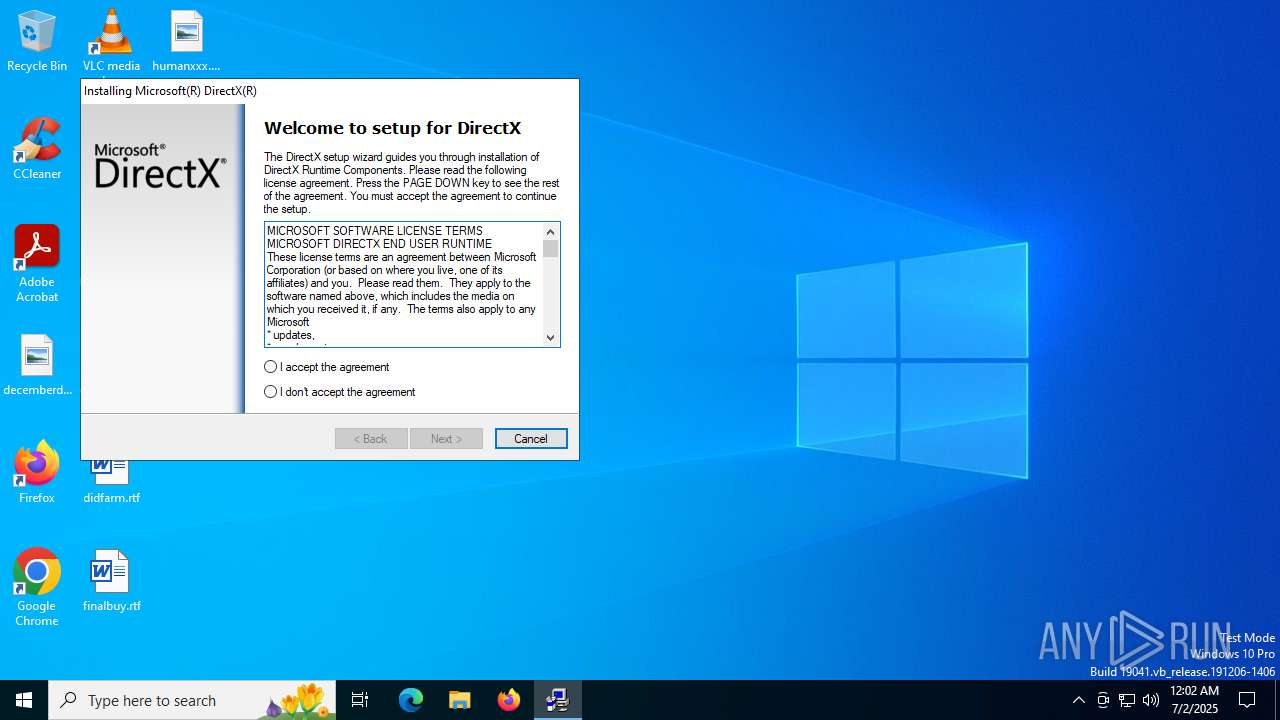
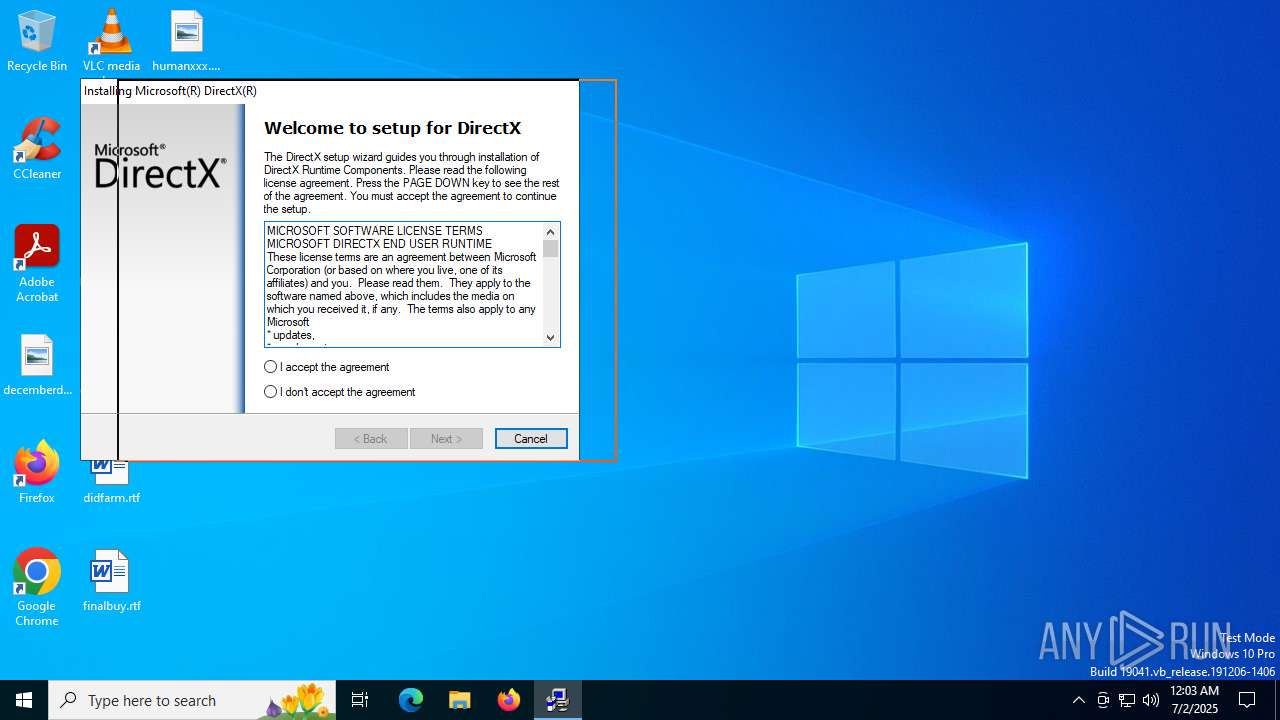
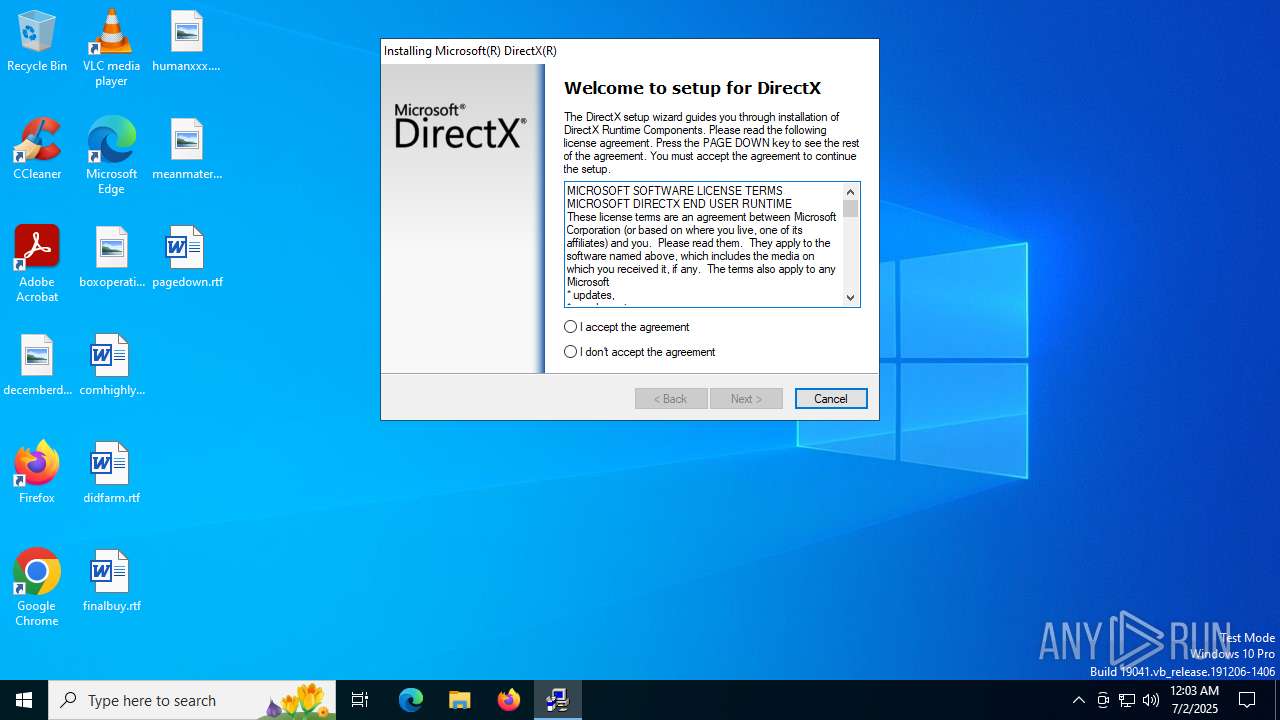
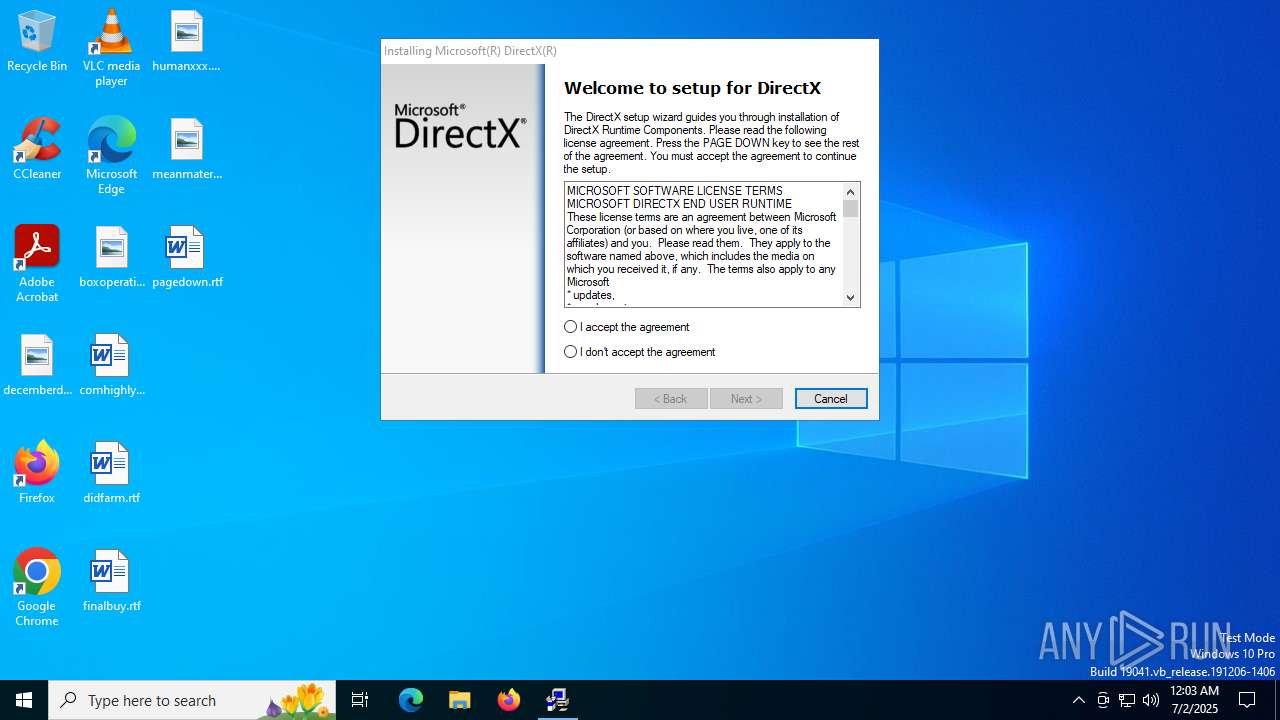
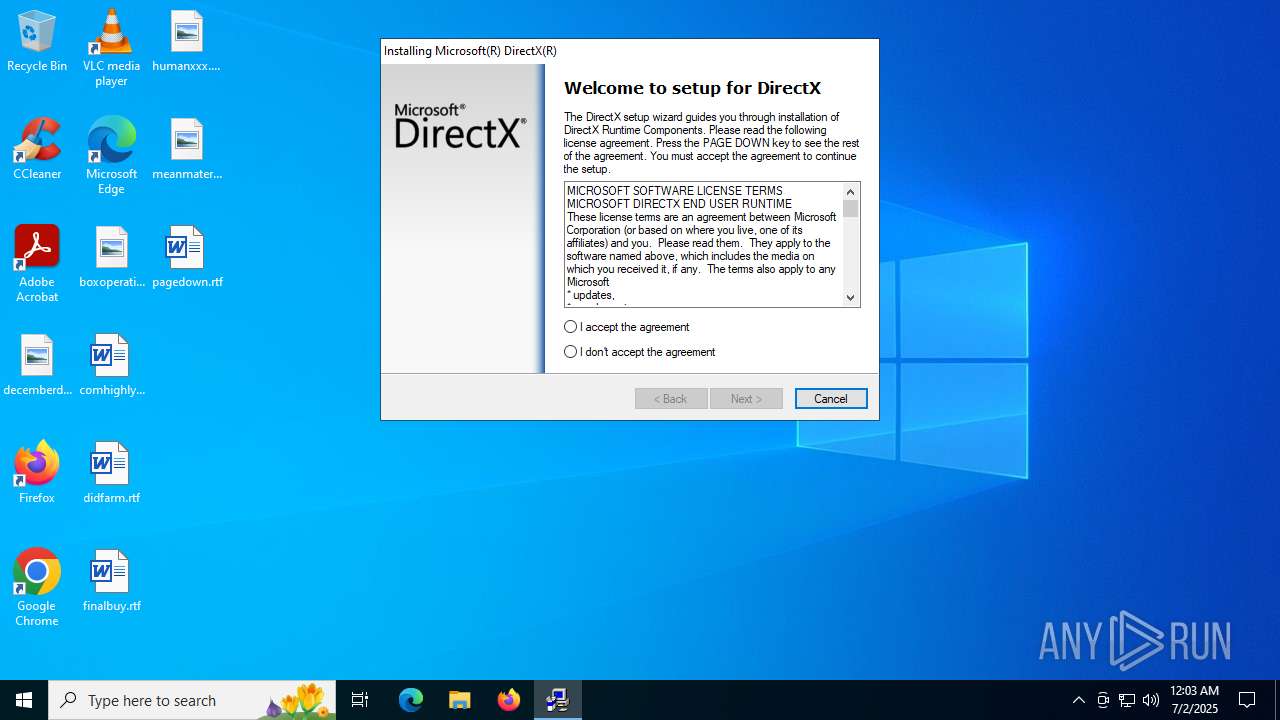
| File name: | dxwebsetup.exe |
| Full analysis: | https://app.any.run/tasks/356dacc6-fd2a-4868-95c6-5c6d24dee6b6 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 00:02:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, MS CAB-Installer self-extracting archive, 3 sections |
| MD5: | BCBB7C0CD9696068988953990EC5BD11 |
| SHA1: | 3C8243734CF43DD7BB2332BA05B58CCACFA4377C |
| SHA256: | 34F64699D4830145CAE69BD40115B1F326E70FC6A98456CB3DF996D947DDDCA4 |
| SSDEEP: | 6144:3WK8fc2liXmrLxcdRDLiH1vVRGVOhMp421/7YQ43:mcvgLARDI1KIOzOR3 |
MALICIOUS
Executing a file with an untrusted certificate
- dxwebsetup.exe (PID: 7104)
- dxwebsetup.exe (PID: 2536)
Changes the autorun value in the registry
- dxwebsetup.exe (PID: 7104)
SUSPICIOUS
Executable content was dropped or overwritten
- dxwebsetup.exe (PID: 7104)
- dxwsetup.exe (PID: 6648)
Starts a Microsoft application from unusual location
- dxwebsetup.exe (PID: 7104)
- dxwebsetup.exe (PID: 2536)
- dxwsetup.exe (PID: 6648)
Process drops legitimate windows executable
- dxwebsetup.exe (PID: 7104)
- dxwsetup.exe (PID: 6648)
INFO
Checks supported languages
- dxwebsetup.exe (PID: 7104)
- dxwsetup.exe (PID: 6648)
The sample compiled with english language support
- dxwebsetup.exe (PID: 7104)
- dxwsetup.exe (PID: 6648)
Create files in a temporary directory
- dxwebsetup.exe (PID: 7104)
Reads the computer name
- dxwsetup.exe (PID: 6648)
Launching a file from a Registry key
- dxwebsetup.exe (PID: 7104)
Manual execution by a user
- rundll32.exe (PID: 5960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2001:08:18 01:42:57+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7 |
| CodeSize: | 34816 |
| InitializedDataSize: | 250368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5a5e |
| OSVersion: | 5.1 |
| ImageVersion: | 5.1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.2600.0 |
| ProductVersionNumber: | 6.0.2600.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | DirectX 9.0 Web setup |
| FileVersion: | 9.29.1974.0 |
| InternalName: | DXWebSetup |
| LegalCopyright: | Copyright (c) Microsoft Corporation. All rights reserved. |
| OriginalFileName: | dxwebsetup.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 9.29.1974.0 |
Total processes
142
Monitored processes
5
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1732 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2536 | "C:\Users\admin\AppData\Local\Temp\dxwebsetup.exe" | C:\Users\admin\AppData\Local\Temp\dxwebsetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DirectX 9.0 Web setup Exit code: 3221226540 Version: 9.29.1974.0 Modules
| |||||||||||||||
| 5960 | rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6648 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | dxwebsetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DirectX Setup Exit code: 2852126720 Version: 4.9.0.0904 Modules
| |||||||||||||||
| 7104 | "C:\Users\admin\AppData\Local\Temp\dxwebsetup.exe" | C:\Users\admin\AppData\Local\Temp\dxwebsetup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DirectX 9.0 Web setup Exit code: 2852126720 Version: 9.29.1974.0 Modules
| |||||||||||||||
Total events
310
Read events
308
Write events
1
Delete events
1
Modification events
| (PID) Process: | (7104) dxwebsetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
| (PID) Process: | (7104) dxwebsetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
Executable files
9
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7104 | dxwebsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dsetup32.dll | executable | |
MD5:A5412A144F63D639B47FCC1BA68CB029 | SHA256:8A011DA043A4B81E2B3D41A332E0FF23A65D546BD7636E8BC74885E8746927D6 | |||
| 7104 | dxwebsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.inf | ini | |
MD5:AD8982EAA02C7AD4D7CDCBC248CAA941 | SHA256:D63C35E9B43EB0F28FFC28F61C9C9A306DA9C9DE3386770A7EB19FAA44DBFC00 | |||
| 6648 | dxwsetup.exe | C:\Windows\Logs\DirectX.log | text | |
MD5:58A2043DE1880246A76501168887C596 | SHA256:93C662B3278F721E73502E5C131901472CC5A9F0B7DFE10CA7312F58288046A2 | |||
| 7104 | dxwebsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | executable | |
MD5:AC3A5F7BE8CD13A863B50AB5FE00B71C | SHA256:8F5E89298E3DC2E22D47515900C37CCA4EE121C5BA06A6D962D40AD6E1A595DA | |||
| 6648 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\SET53AF.tmp | executable | |
MD5:A5412A144F63D639B47FCC1BA68CB029 | SHA256:8A011DA043A4B81E2B3D41A332E0FF23A65D546BD7636E8BC74885E8746927D6 | |||
| 6648 | dxwsetup.exe | C:\Windows\security\logs\scecomp.log | text | |
MD5:217337C0542FC0EA0886D819E4B839BF | SHA256:D582FA6A9714229D7032CA984E8A690A4318C60A9E7403E74A4463AB246F06C4 | |||
| 6648 | dxwsetup.exe | C:\Windows\Temp\OLDE197.tmp | executable | |
MD5:A5412A144F63D639B47FCC1BA68CB029 | SHA256:8A011DA043A4B81E2B3D41A332E0FF23A65D546BD7636E8BC74885E8746927D6 | |||
| 6648 | dxwsetup.exe | C:\Windows\Temp\OLDE186.tmp | executable | |
MD5:984CAD22FA542A08C5D22941B888D8DC | SHA256:57BC22850BB8E0BCC511A9B54CD3DA18EEC61F3088940C07D63B9B74E7FE2308 | |||
| 6648 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\dsetup.dll | executable | |
MD5:984CAD22FA542A08C5D22941B888D8DC | SHA256:57BC22850BB8E0BCC511A9B54CD3DA18EEC61F3088940C07D63B9B74E7FE2308 | |||
| 6648 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\SET4ECC.tmp | executable | |
MD5:984CAD22FA542A08C5D22941B888D8DC | SHA256:57BC22850BB8E0BCC511A9B54CD3DA18EEC61F3088940C07D63B9B74E7FE2308 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.18.121.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 104.123.41.162:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7020 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4860 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.18.121.147:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
1268 | svchost.exe | 104.123.41.162:80 | www.microsoft.com | AKAMAI-AS | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7020 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
ln-ring.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
Process | Message |
|---|---|
dxwsetup.exe | DLL_PROCESS_ATTACH |
dxwsetup.exe | Invalid parameter passed to C runtime function.
|
dxwsetup.exe | DLL_PROCESS_DETACH |
dxwsetup.exe | Invalid parameter passed to C runtime function.
|
dxwsetup.exe | DLL_PROCESS_DETACH |
dxwsetup.exe | DLL_PROCESS_ATTACH |