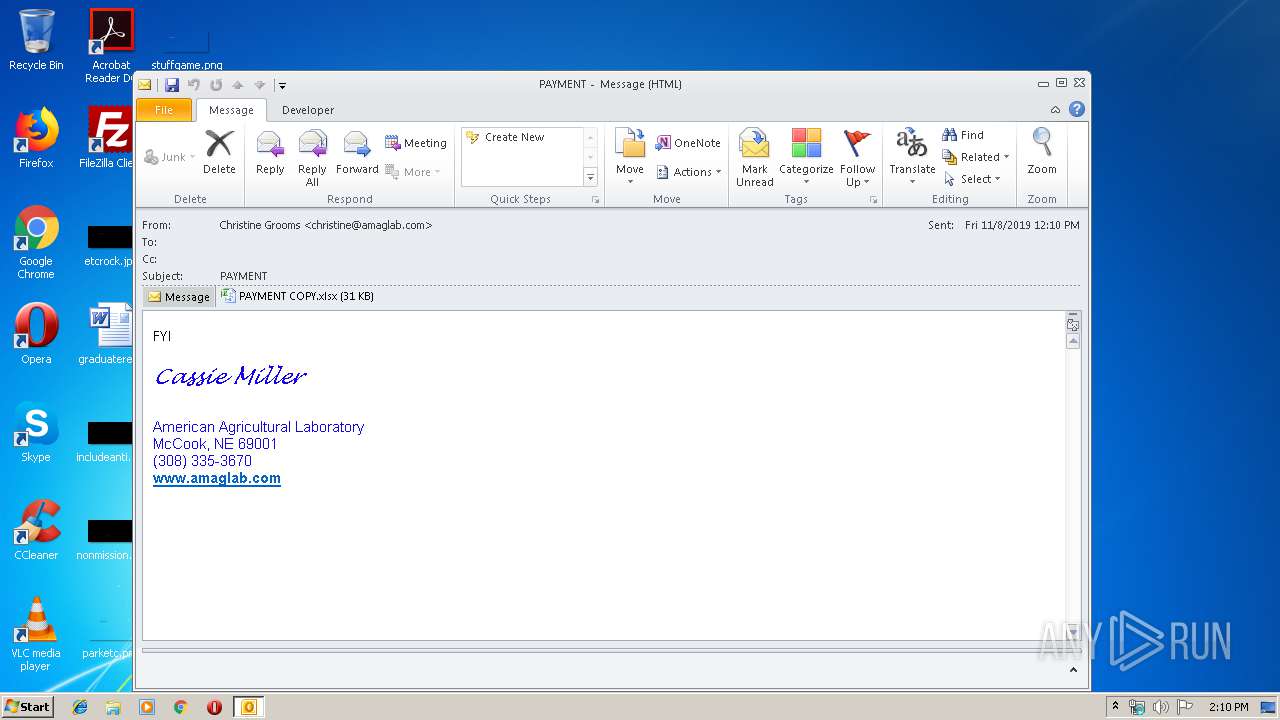
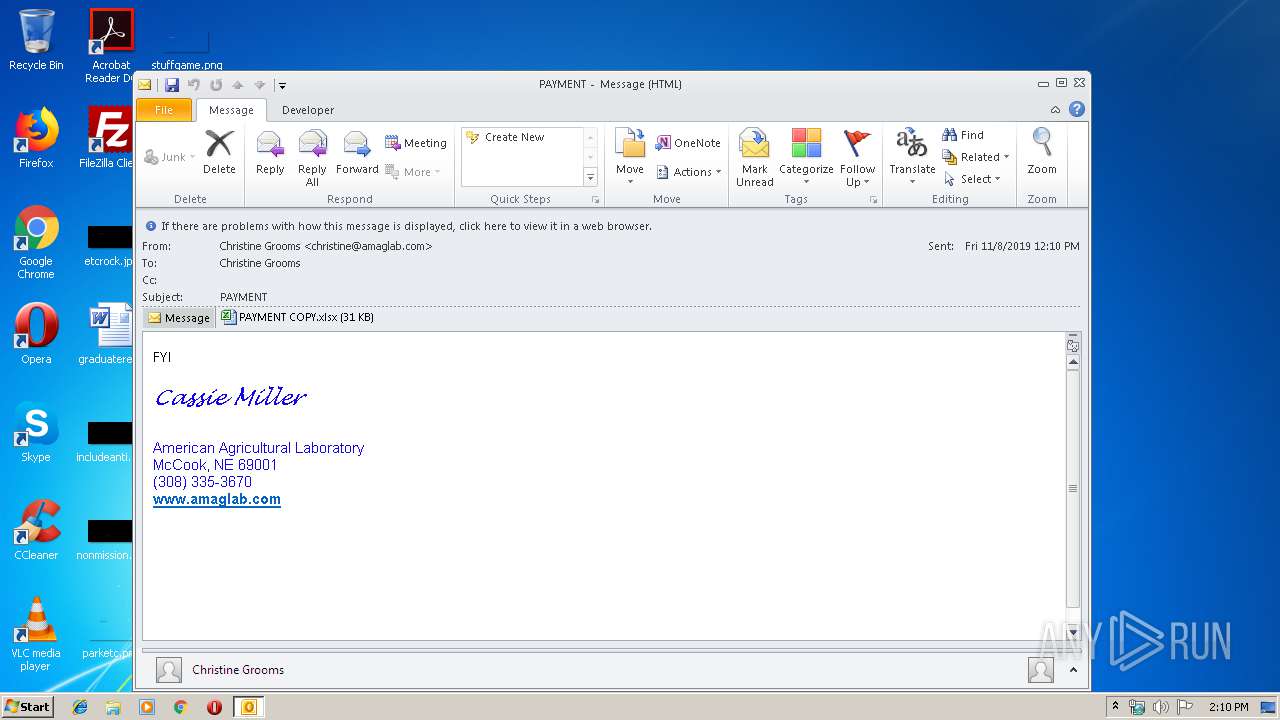
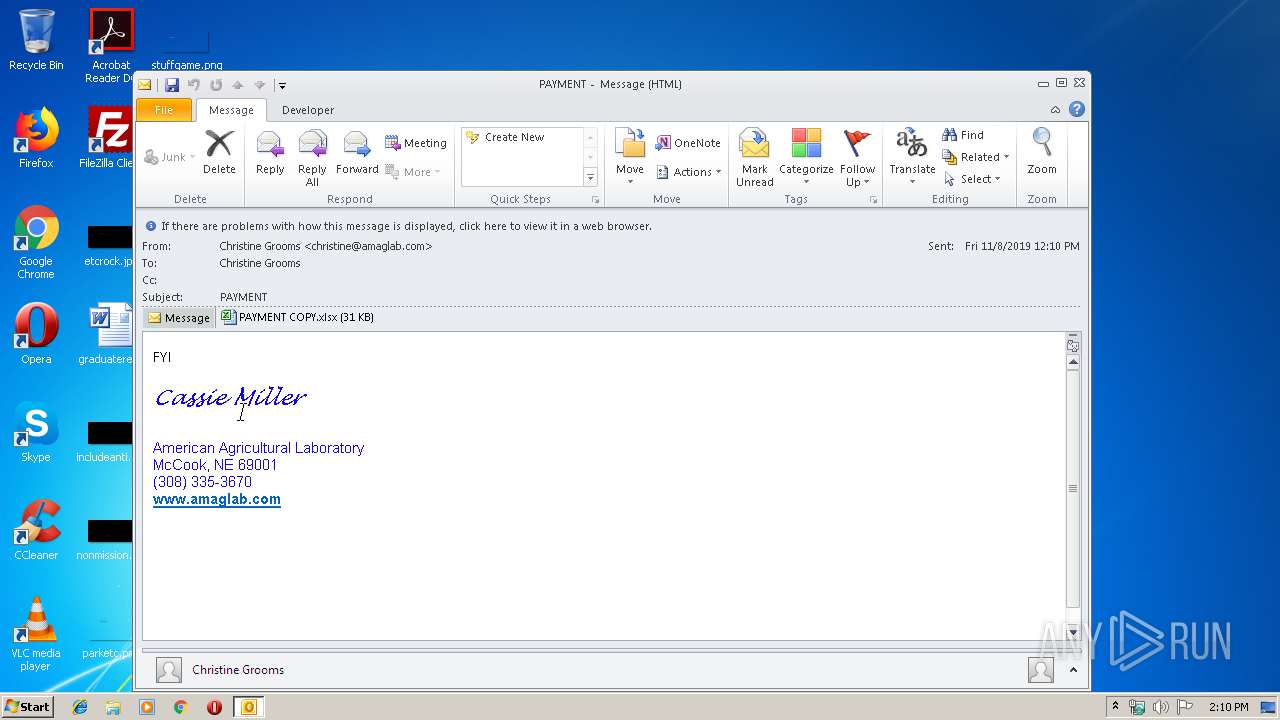
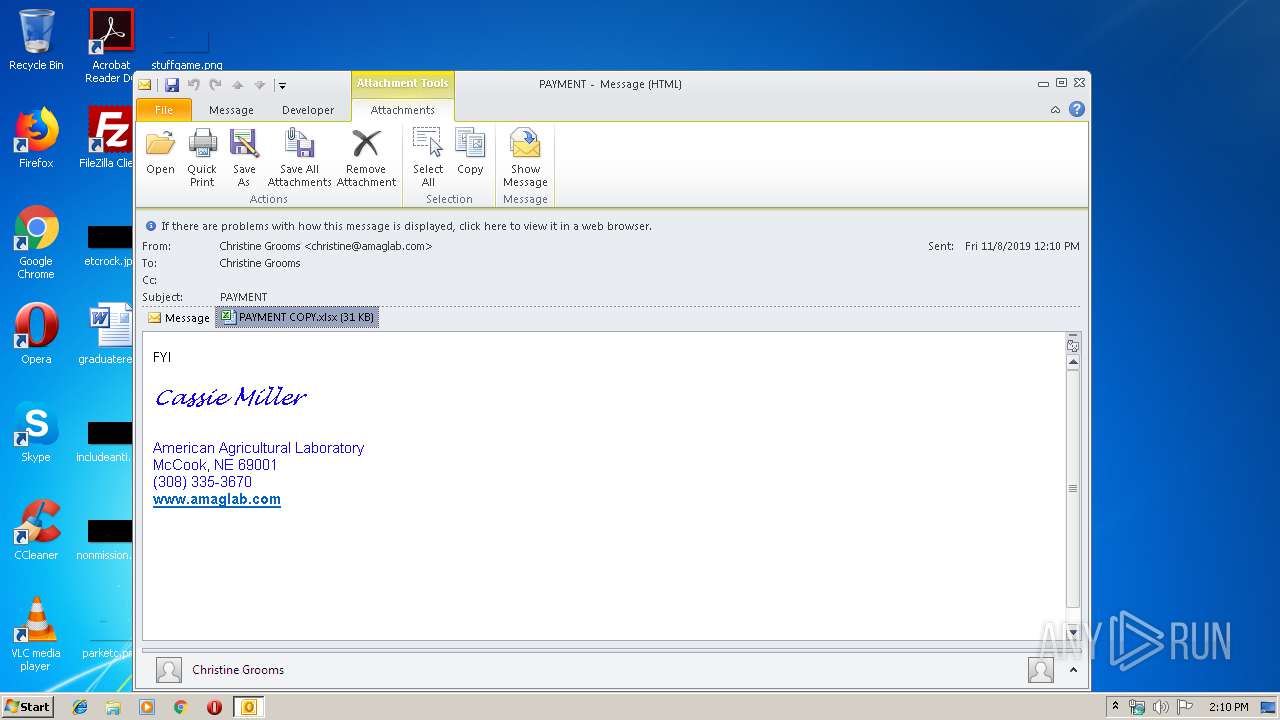
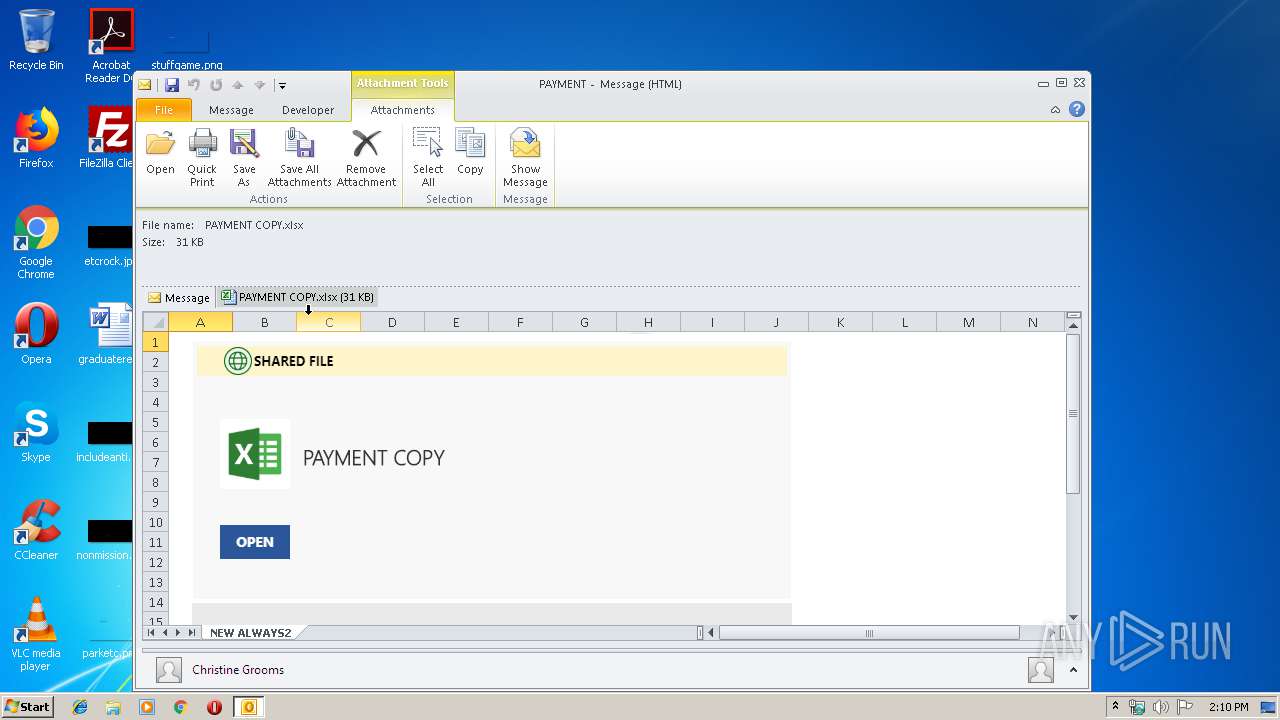
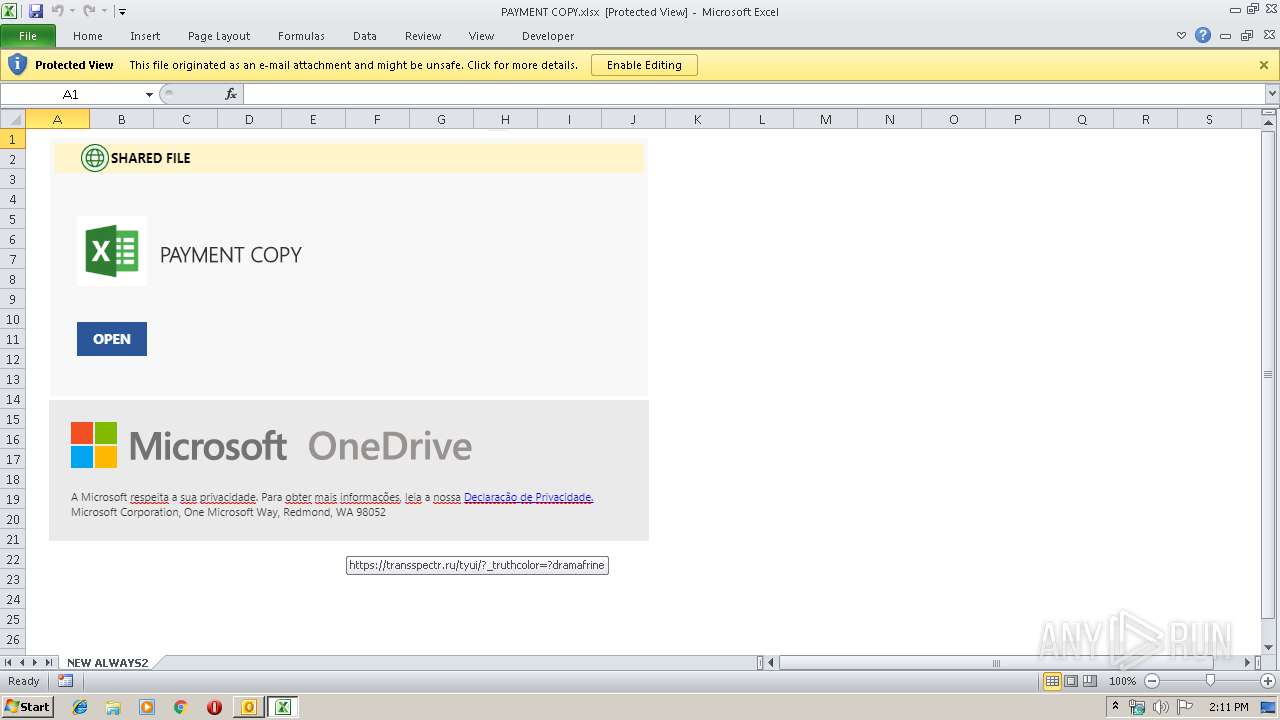
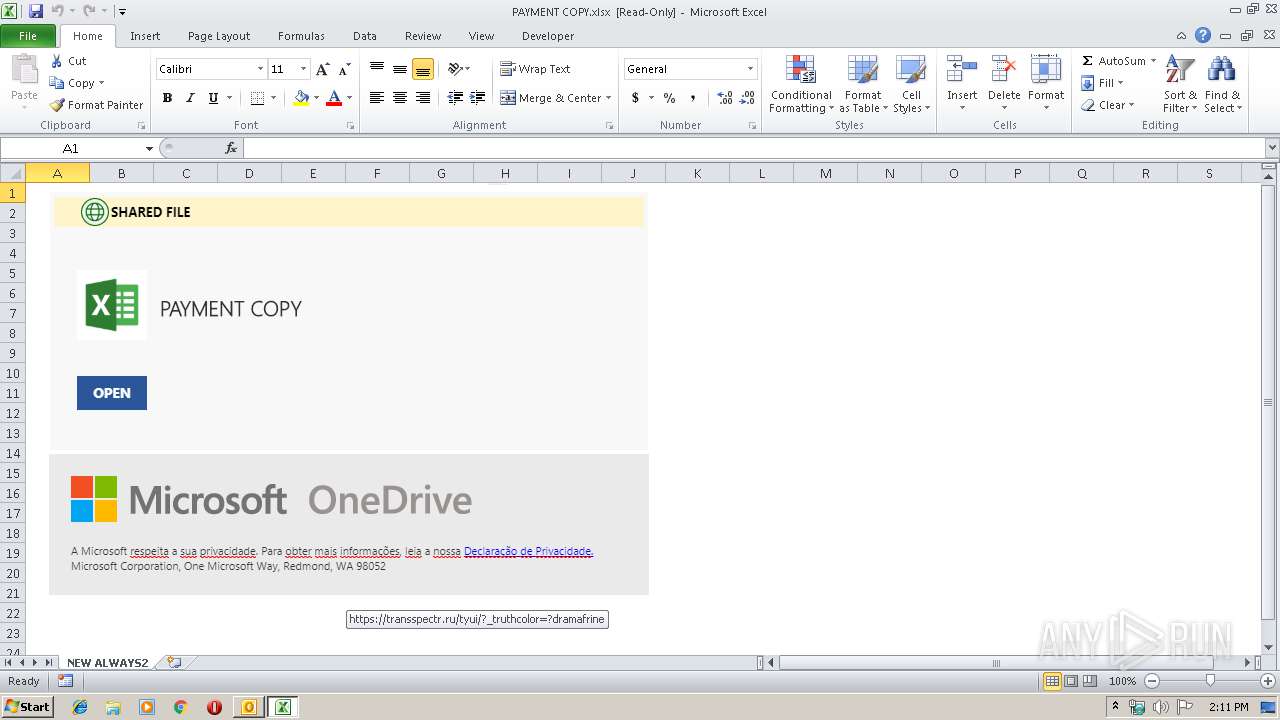
| File name: | PAYMENT.eml |
| Full analysis: | https://app.any.run/tasks/de85ed86-155f-4f0b-bc9e-002d25ce76e8 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 14:10:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 509B153C4805A16CB1029B332280700F |
| SHA1: | 2C1369EC595D3DF5E88FB99536B921F05893D7BD |
| SHA256: | 34F342B64C44D4ABA35A7E666AEDA054EC64AD4837A35C5B7B4EBA2CA9F7BF73 |
| SSDEEP: | 768:YPYxuH8YNGP1n/uroLqxzPNcVX7BLQJvGuiM9ldCc3otwDAu1lUXz+6:fkDN41YomgJsGulvfAMOXp |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 3180)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3180)
Writes to a desktop.ini file (may be used to cloak folders)
- EXCEL.EXE (PID: 1536)
- EXCEL.EXE (PID: 3960)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 3180)
- EXCEL.EXE (PID: 4056)
Application launched itself
- EXCEL.EXE (PID: 4056)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1536)
- EXCEL.EXE (PID: 4056)
- EXCEL.EXE (PID: 3960)
- OUTLOOK.EXE (PID: 3180)
Creates files in the user directory
- EXCEL.EXE (PID: 4056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
40
Monitored processes
4
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1536 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3180 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\PAYMENT.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3960 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 4056 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 783
Read events
2 148
Write events
597
Delete events
38
Modification events
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1332215988 | |||
| (PID) Process: | (3180) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
0
Suspicious files
6
Text files
45
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA7D3.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\W39QQAW9\PAYMENT COPY (2).xlsx\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\OICE_372D60CB-0742-40A9-ACC3-0857D5A84B46.0\AA0C8F96.xlsx\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\OICE_372D60CB-0742-40A9-ACC3-0857D5A84B46.0\AA0C8F96.xlsx | document | |
MD5:— | SHA256:— | |||
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_B7DBCFFFD09438419D5C3E42CE44B7F2.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_5C09F2CC5B437949912040B4AA43E88B.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 3180 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\W39QQAW9\PAYMENT COPY.xlsx | document | |
MD5:— | SHA256:— | |||
| 4056 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR68D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
19
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3180 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
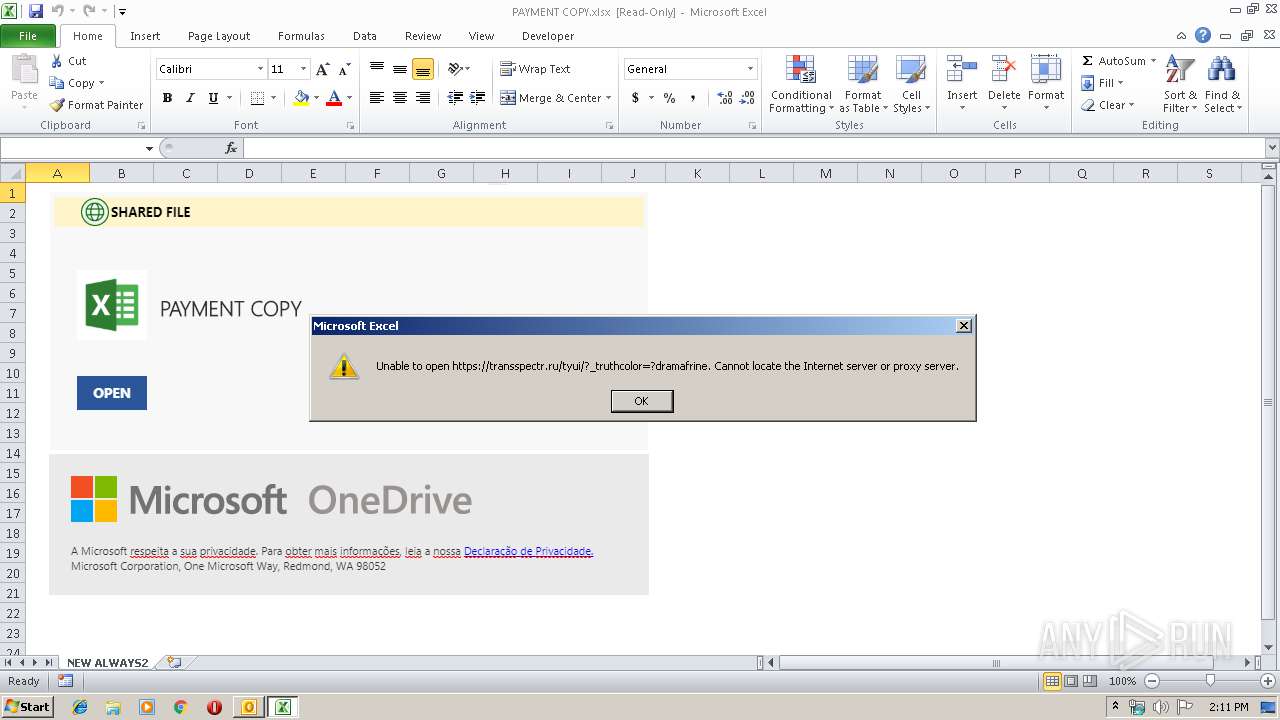
transspectr.ru |
| suspicious |