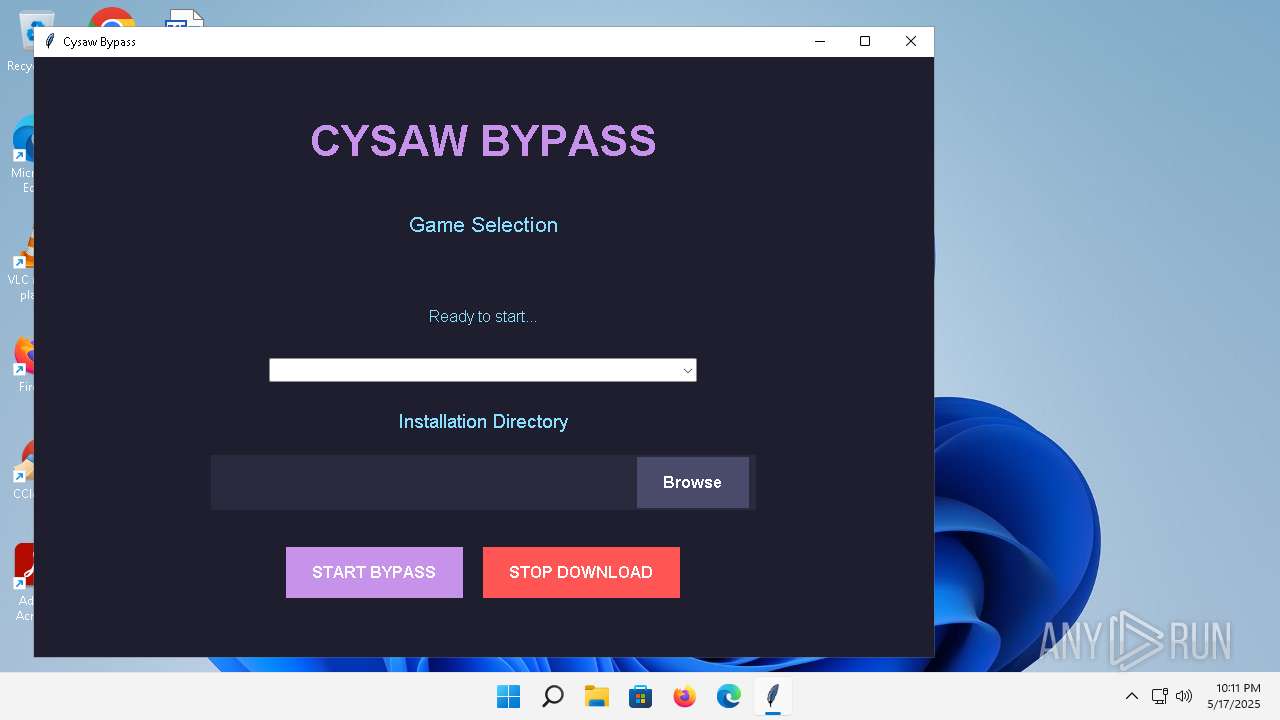
| File name: | Cy.exe |
| Full analysis: | https://app.any.run/tasks/807e44ea-b196-4f05-8890-c9d17f72655d |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 22:10:16 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | DBD549F0C2EF8118691EBC93564E5342 |
| SHA1: | EBE6AEA4A583E4F9D279320BB72339A030395A9A |
| SHA256: | 34F2A930321BAAD911C7E129B394FBAC00CE9CD6C907F5EB394281DE1F4D6BA9 |
| SSDEEP: | 98304:ECYzBbltevzm0a7MC2xumzy722pACb9RvOYVAYwVf9TtYw9pk9dbXtpEKLuIgqNT:g7I4zdEEZ5KAOnrR5r559 |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- Cy.exe (PID: 5740)
Executable content was dropped or overwritten
- Cy.exe (PID: 5740)
Process drops legitimate windows executable
- Cy.exe (PID: 5740)
Process drops python dynamic module
- Cy.exe (PID: 5740)
There is functionality for taking screenshot (YARA)
- Cy.exe (PID: 5740)
- Cy.exe (PID: 2996)
Application launched itself
- Cy.exe (PID: 5740)
Loads Python modules
- Cy.exe (PID: 2996)
Reads the Internet Settings
- Cy.exe (PID: 2996)
INFO
Checks supported languages
- Cy.exe (PID: 5740)
- Cy.exe (PID: 2996)
Reads the computer name
- Cy.exe (PID: 5740)
- Cy.exe (PID: 2996)
The sample compiled with english language support
- Cy.exe (PID: 5740)
Create files in a temporary directory
- Cy.exe (PID: 5740)
PyInstaller has been detected (YARA)
- Cy.exe (PID: 5740)
- Cy.exe (PID: 2996)
Checks proxy server information
- Cy.exe (PID: 2996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:18 11:40:20+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 173568 |
| InitializedDataSize: | 155648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce30 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
101
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1664 | C:\Windows\system32\svchost.exe -k NetworkService -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2996 | "C:\Users\admin\Desktop\Cy.exe" | C:\Users\admin\Desktop\Cy.exe | — | Cy.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5740 | "C:\Users\admin\Desktop\Cy.exe" | C:\Users\admin\Desktop\Cy.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
873
Read events
873
Write events
0
Delete events
0
Modification events
Executable files
25
Suspicious files
5
Text files
935
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_decimal.pyd | executable | |
MD5:C88282908BA54510EDA3887C488198EB | SHA256:980A63F2B39CF16910F44384398E25F24482346A482ADDB00DE42555B17D4278 | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_tcl_data\encoding\ascii.enc | text | |
MD5:9E3A454FA480E9A99D2D5ACDAA775233 | SHA256:FB87BF197F4F485B08EA81F7534BC07D9C3A538D022424BE11011A1FE3C413FD | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_tcl_data\encoding\cp1251.enc | text | |
MD5:83DAF47FD1F87B7B1E9E086F14C39E5B | SHA256:0AA66DFF8A7AE570FEE83A803F8F5391D9F0C9BD6311796592D9B6E8E36BE6FC | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_bz2.pyd | executable | |
MD5:AA1083BDE6D21CABFC630A18F51B1926 | SHA256:00B8CA9A338D2B47285C9E56D6D893DB2A999B47216756F18439997FB80A56E3 | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_ssl.pyd | executable | |
MD5:0F02ECCD7933B7A7C2BDEDCA2A72AAB6 | SHA256:BA5388D6A6557D431E086734A3323621DC447F63BA299B0A815E5837CF869678 | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_tcl_data\encoding\cp1252.enc | text | |
MD5:E9117326C06FEE02C478027CB625C7D8 | SHA256:741859CF238C3A63BBB20EC6ED51E46451372BB221CFFF438297D261D0561C2E | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_ctypes.pyd | executable | |
MD5:565D011CE1CEE4D48E722C7421300090 | SHA256:C148292328F0AAB7863AF82F54F613961E7CB95B7215F7A81CAFAF45BD4C42B7 | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_asyncio.pyd | executable | |
MD5:07A6E6DCC30E1C4C7E0CDC41A457A887 | SHA256:746BC8FA88282AFE19DC60E426CC0A75BEA3BD137CCA06A0B57A30BD31459403 | |||
| 5740 | Cy.exe | C:\Users\admin\AppData\Local\Temp\_MEI57402\_queue.pyd | executable | |
MD5:7F52EF40B083F34FD5E723E97B13382F | SHA256:3F8E7E6AA13B417ACC78B63434FB1144E6319A010A9FC376C54D6E69B638FE4C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
15
DNS requests
10
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.110.147:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2412 | MoUsoCoreWorker.exe | GET | 200 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d3763667235d4d4f | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?15be5abb986864ed | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3e4d47703098faed | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?4c1c53e3976db8c9 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e8295883656f7dad | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 88.221.110.147:80 | — | Akamai International B.V. | DE | unknown |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2412 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2412 | MoUsoCoreWorker.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3640 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1396 | smartscreen.exe | 20.56.187.20:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2984 | svchost.exe | 23.197.142.186:443 | fs.microsoft.com | Akamai International B.V. | US | whitelisted |
2768 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2988 | OfficeClickToRun.exe | 20.42.65.85:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
cysaw.top |
| unknown |
fs.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
1664 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |