| File name: | program.exe |
| Full analysis: | https://app.any.run/tasks/6573b4cd-8328-4e74-9590-51b2983eedad |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2024, 08:24:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, PECompact2 compressed, 2 sections |
| MD5: | B18CA9C57E8DD3B1298296AEE0016B63 |
| SHA1: | 1FB7EA70AAE6CF869F348FB1DC610ACDB3AD18DA |
| SHA256: | 34ED049A431884739C3F04B135B0734C0C4EF34121DB5ABF8187062984141AFB |
| SSDEEP: | 1536:qmr1zQ09GiNb9Ltrja6Amr1zQjZv7O8IQq:qmrhQaNb9Lt66AmrhQjZiAq |
MALICIOUS
No malicious indicators.SUSPICIOUS
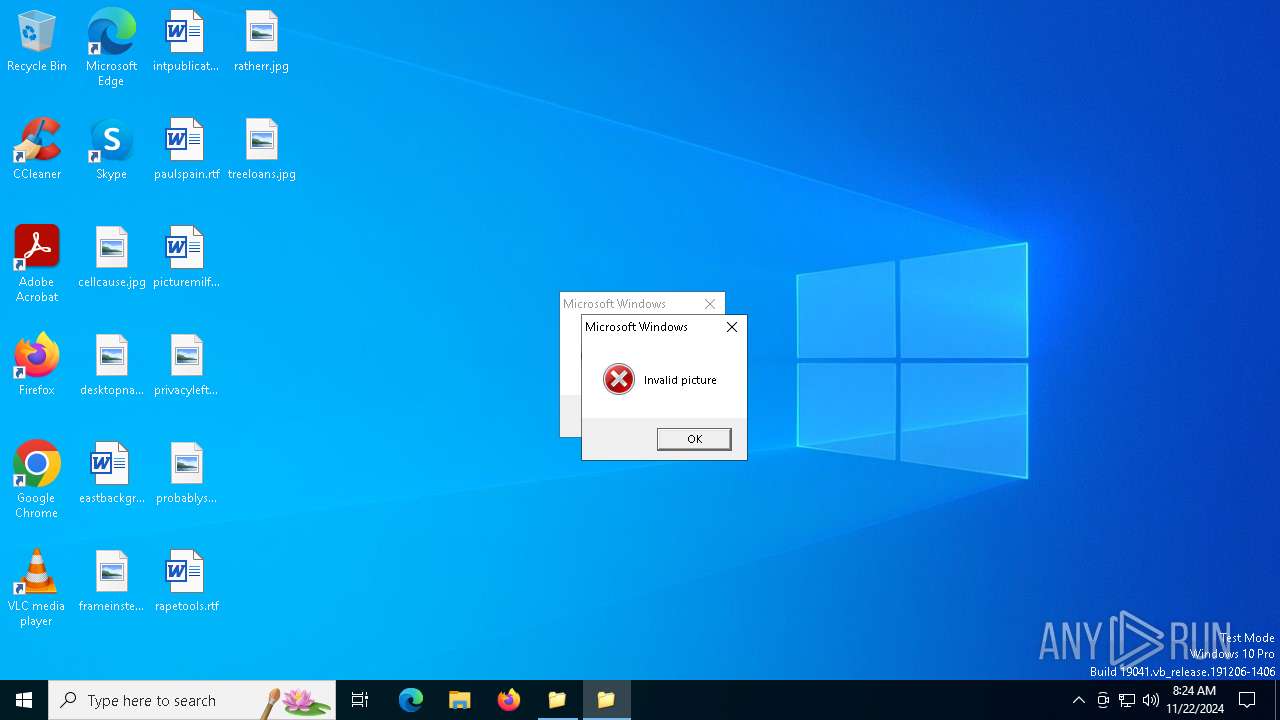
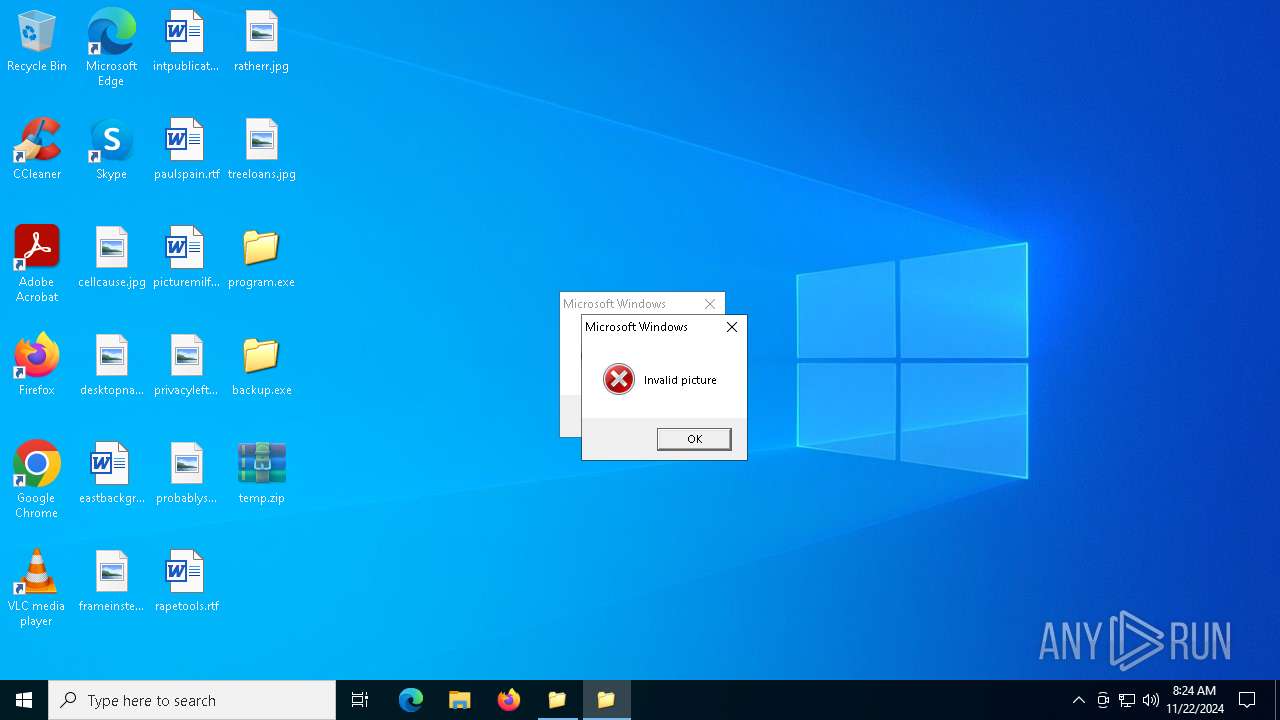
Starts itself from another location
- program.exe (PID: 1668)
- backup.exe (PID: 2076)
- backup.exe (PID: 3928)
- backup.exe (PID: 1796)
- backup.exe (PID: 5660)
- backup.exe (PID: 748)
- backup.exe (PID: 3732)
- backup.exe (PID: 8)
- backup.exe (PID: 4652)
- backup.exe (PID: 2008)
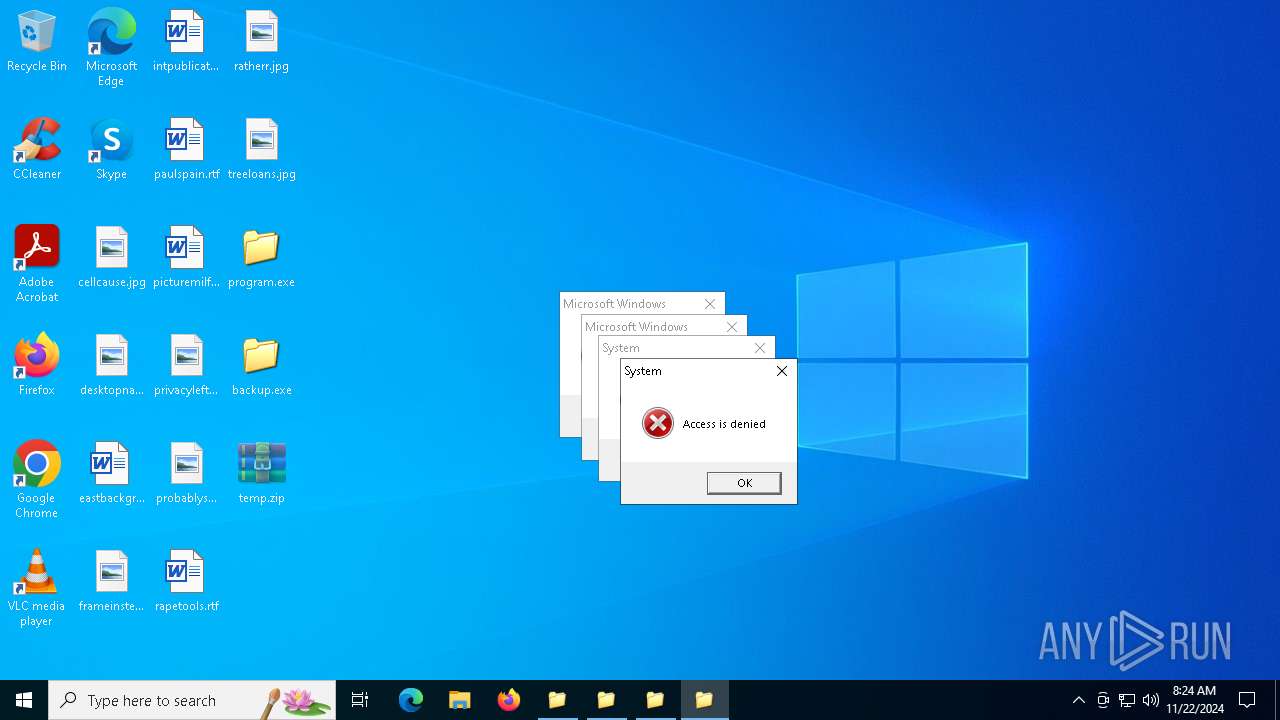
Executable content was dropped or overwritten
- backup.exe (PID: 3928)
- backup.exe (PID: 1796)
- program.exe (PID: 1668)
- backup.exe (PID: 2076)
- backup.exe (PID: 5660)
- backup.exe (PID: 8)
- backup.exe (PID: 748)
- backup.exe (PID: 3732)
- backup.exe (PID: 4652)
- backup.exe (PID: 2008)
- program.exe (PID: 3640)
INFO
Create files in a temporary directory
- program.exe (PID: 1668)
Checks supported languages
- program.exe (PID: 1668)
Reads the computer name
- program.exe (PID: 1668)
Manual execution by a user
- program.exe (PID: 3640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:01:06 03:24:42+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 45056 |
| InitializedDataSize: | 28672 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1134 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.50 |
| ProductVersionNumber: | 1.0.0.50 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Microsoft Windows |
| FileVersion: | 1.00.0050 |
| ProductVersion: | 1.00.0050 |
| InternalName: | music |
| OriginalFileName: | music.exe |
Total processes
143
Monitored processes
20
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | C:\Users\admin\AppData\Local\Temp\Diagnostics\backup.exe C:\Users\admin\AppData\Local\Temp\Diagnostics\ | C:\Users\admin\AppData\Local\Temp\Diagnostics\backup.exe | program.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 644 | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\backup.exe C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\ | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\backup.exe | — | backup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 720 | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\Acrobat\DC\backup.exe C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\Acrobat\DC\ | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\Acrobat\DC\backup.exe | — | backup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 748 | C:\Users\admin\AppData\Local\Temp\acrord32_super_sbx\backup.exe C:\Users\admin\AppData\Local\Temp\acrord32_super_sbx\ | C:\Users\admin\AppData\Local\Temp\acrord32_super_sbx\backup.exe | program.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1668 | "C:\Users\admin\AppData\Local\Temp\program.exe" | C:\Users\admin\AppData\Local\Temp\program.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1796 | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\Acrobat\backup.exe C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\Acrobat\ | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\Acrobat\backup.exe | backup.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1796 | "C:\Users\admin\AppData\Local\Temp\Rar$DRa988.30171\10x64\System Restore.exe" C:\Users\admin\AppData\Local\Temp\Rar$DRa988.30171\10x64\ | C:\Users\admin\AppData\Local\Temp\Rar$DRa988.30171\10x64\System Restore.exe | — | backup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2008 | C:\Users\admin\AppData\Local\Temp\Rar$DRa988.30171\backup.exe C:\Users\admin\AppData\Local\Temp\Rar$DRa988.30171\ | C:\Users\admin\AppData\Local\Temp\Rar$DRa988.30171\backup.exe | program.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2076 | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\backup.exe C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\ | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\backup.exe | backup.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2436 | C:\Users\admin\AppData\Local\Temp\acrord32_super_sbx\Adobe\Acrobat\DC\SearchEmbdIndex\backup.exe C:\Users\admin\AppData\Local\Temp\acrord32_super_sbx\Adobe\Acrobat\DC\SearchEmbdIndex\ | C:\Users\admin\AppData\Local\Temp\acrord32_super_sbx\Adobe\Acrobat\DC\SearchEmbdIndex\backup.exe | — | backup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
842
Read events
788
Write events
36
Delete events
18
Modification events
| (PID) Process: | (1668) program.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoFolderOptions |
Value: 1 | |||
| (PID) Process: | (1668) program.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
| (PID) Process: | (1668) program.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Streams |
| Operation: | delete value | Name: | Settings |
Value: | |||
| (PID) Process: | (4060) backup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoFolderOptions |
Value: 1 | |||
| (PID) Process: | (4060) backup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
| (PID) Process: | (4060) backup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Streams |
| Operation: | delete value | Name: | Settings |
Value: | |||
| (PID) Process: | (3928) backup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoFolderOptions |
Value: 1 | |||
| (PID) Process: | (3928) backup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
| (PID) Process: | (3928) backup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Streams |
| Operation: | delete value | Name: | Settings |
Value: | |||
| (PID) Process: | (2076) backup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoFolderOptions |
Value: 1 | |||
Executable files
20
Suspicious files
29
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1668 | program.exe | C:\Users\admin\AppData\Local\Temp\backup.exe | executable | |
MD5:DC3BAA3A9824FEA598735F0426BEA7F2 | SHA256:0366ADBD1B7DA630F26FFC221B21C4216169E116D8D86FB28B2A655F388D097D | |||
| 1796 | backup.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\Adobe\Acrobat\DC\backup.exe | executable | |
MD5:3AFEDC20630AED4FD682522F4E27A247 | SHA256:1D604FDF33EF27A3BD90F729907B27C7C3F2054261C24D038FB355A9210C0FD5 | |||
| 748 | backup.exe | C:\Users\admin\AppData\Local\Temp\acrord32_super_sbx\Adobe\backup.exe | executable | |
MD5:7E4F5A6B39B10A31D80AC8F072C4FC57 | SHA256:6FCCF162DE07C710FB05808A82DFDC9949EBCC8804DED8FCC6F8C3DB9EE712C5 | |||
| 1668 | program.exe | C:\Users\admin\AppData\Local\Temp\acrocef_low\backup.exe | executable | |
MD5:80C0D26A69A4A752496E194C2DAF6060 | SHA256:E631A2F643D64A8A4AC68243950D3A1B9589070DA1F398D1041484B18383557B | |||
| 1668 | program.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\backup.exe | executable | |
MD5:DC3BAA3A9824FEA598735F0426BEA7F2 | SHA256:0366ADBD1B7DA630F26FFC221B21C4216169E116D8D86FB28B2A655F388D097D | |||
| 3928 | backup.exe | C:\Users\admin\AppData\Local\Temp\~DF4034554684B31CD3.TMP | binary | |
MD5:A2451AC51781BDB840208F3E2E1D7C46 | SHA256:BE2F22C484CDBE6B76F904D4C495F9C9FAF7044E0303CC6EF7897B5BC3D91EA1 | |||
| 3732 | backup.exe | C:\Users\admin\AppData\Local\Temp\acrord32_super_sbx\Adobe\Acrobat\backup.exe | executable | |
MD5:6FDABD64818896E6517268767AF032EF | SHA256:E9C188BB795C31A127BD23693864870B675B57C441DA80C173DB3F3A81B5AC76 | |||
| 2076 | backup.exe | C:\Users\admin\AppData\Local\Temp\~DF2DBF7A207C832226.TMP | binary | |
MD5:2606A0DFF12C96FE8EA6B4CC2C59DAD7 | SHA256:70BADD76579BF344CD7FB31F097C0E49D090E00532DC26BCA29A48AA411CAD79 | |||
| 5660 | backup.exe | C:\Users\admin\AppData\Local\Temp\~DFD38824E3721D5E19.TMP | binary | |
MD5:5B02CDB61A35B1F4094BF56009C5DEB2 | SHA256:1B4D8B1A4B78FA4C4701C5A2EF9B4C0AF7101B03CEEFF186269697071DDB507F | |||
| 720 | backup.exe | C:\Users\admin\AppData\Local\Temp\~DFD59B62B05BDB6C49.TMP | binary | |
MD5:40E6700615A04581F77E2D20281FA172 | SHA256:762406FE1382680DF35B266CFDA07342BD545A6A8535CCF9897C47FEF7467A2A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4932 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6324 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6324 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2972 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2480 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4932 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.11:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |