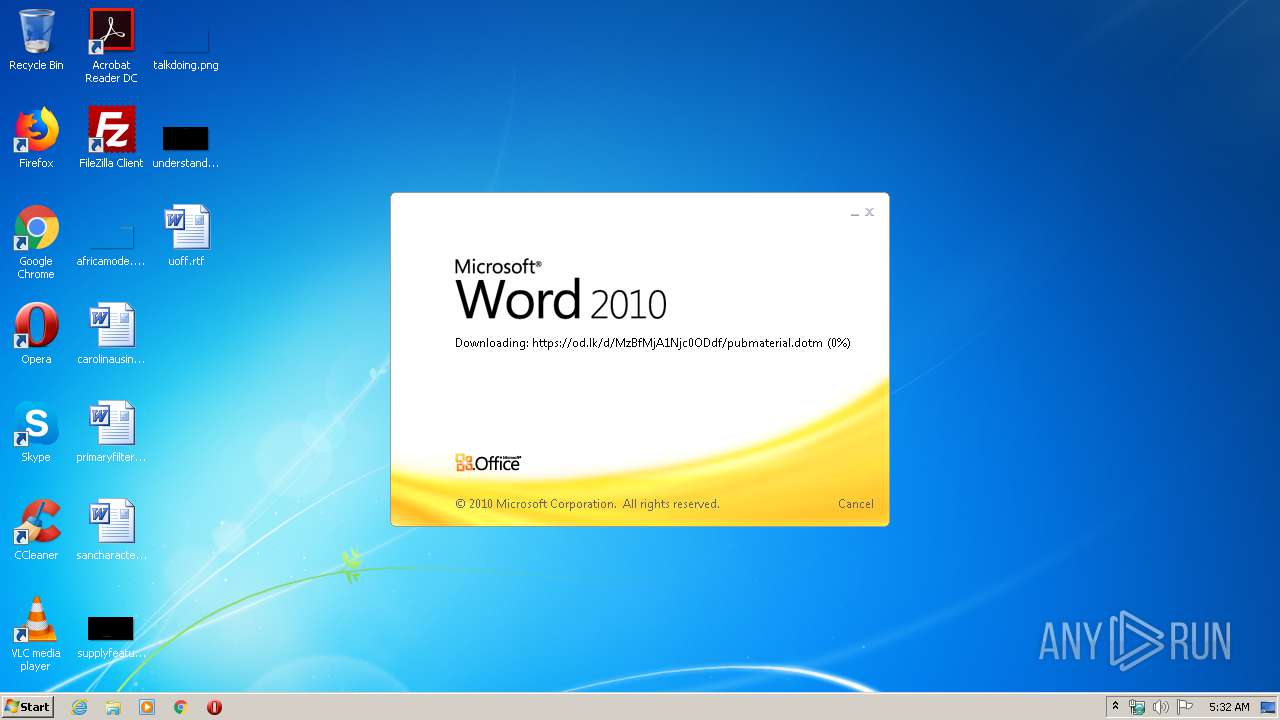
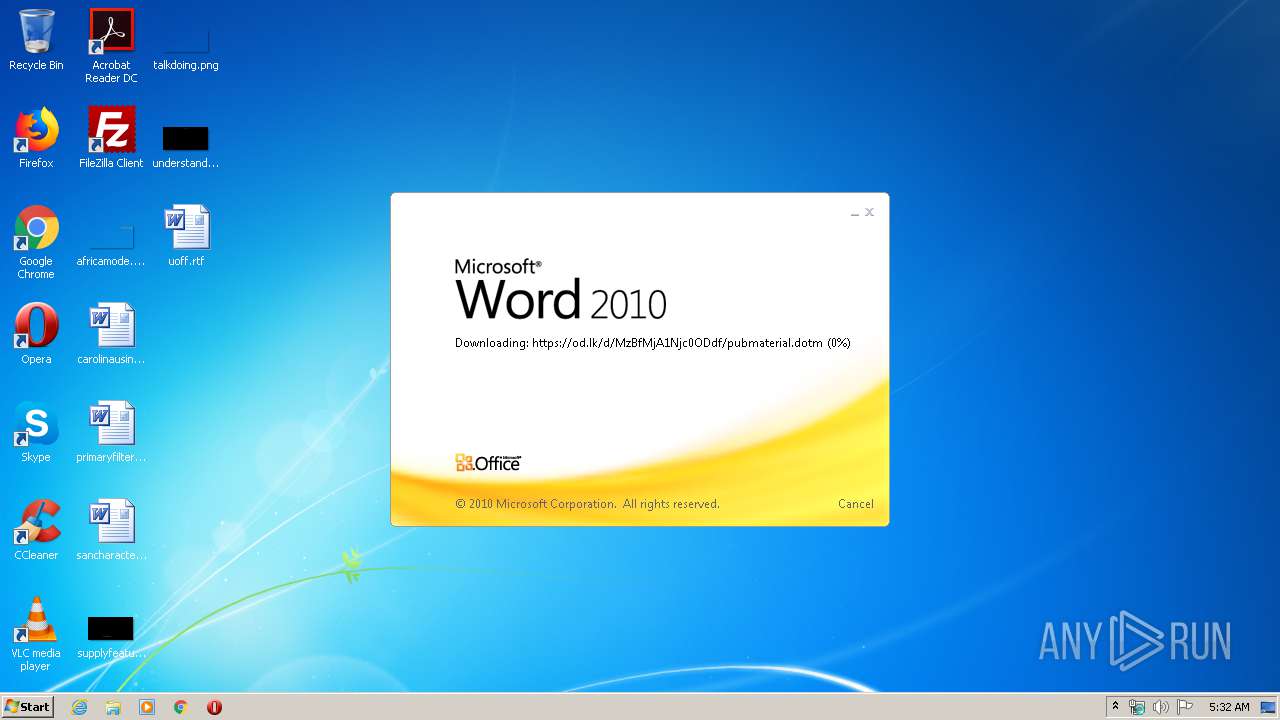
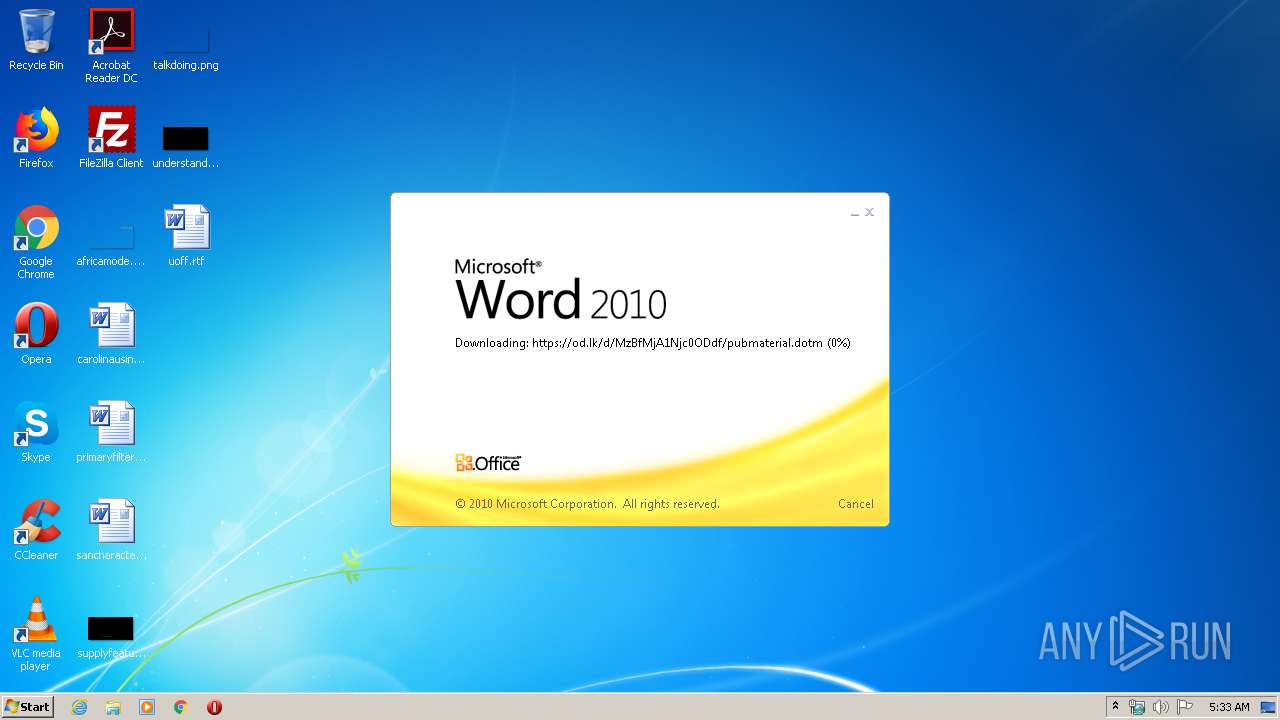
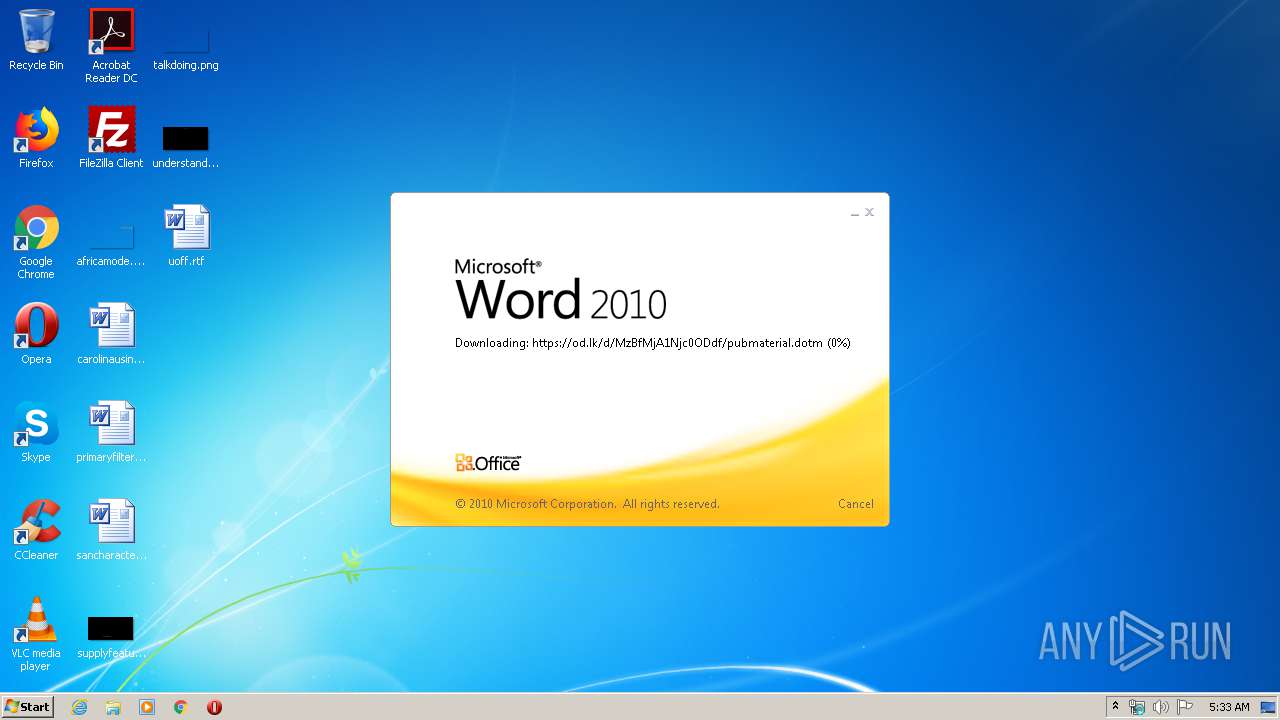
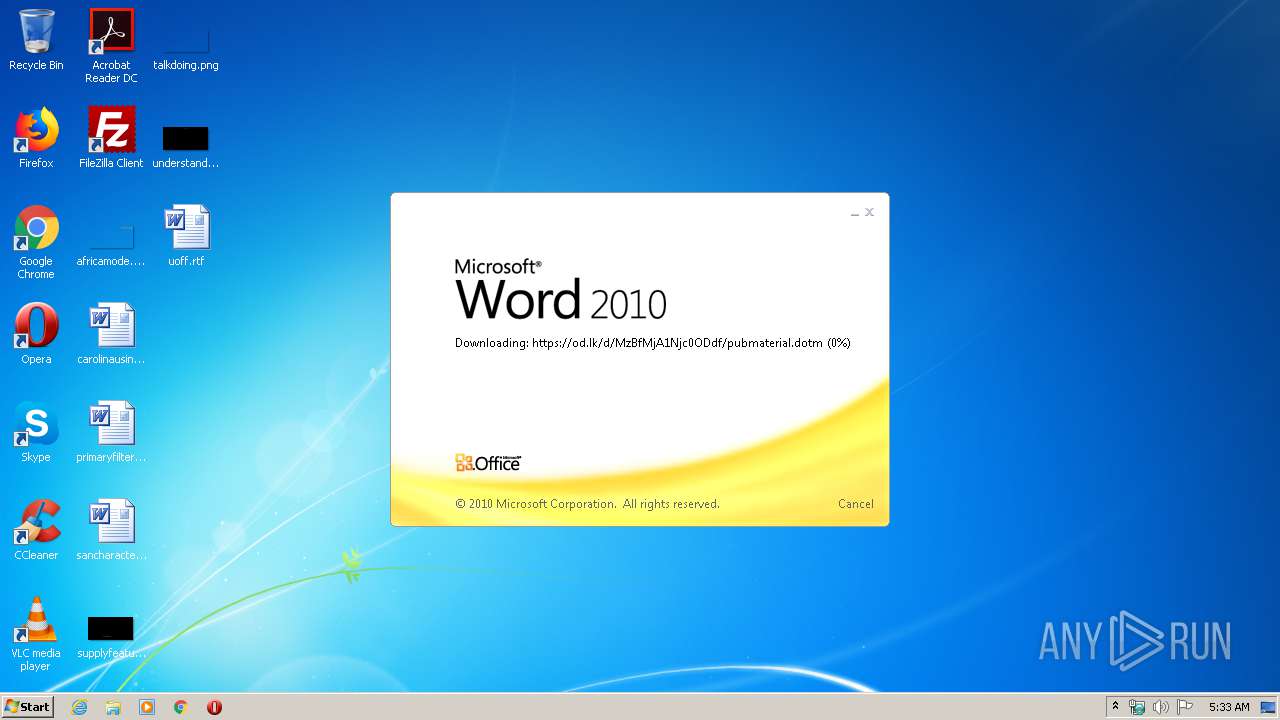
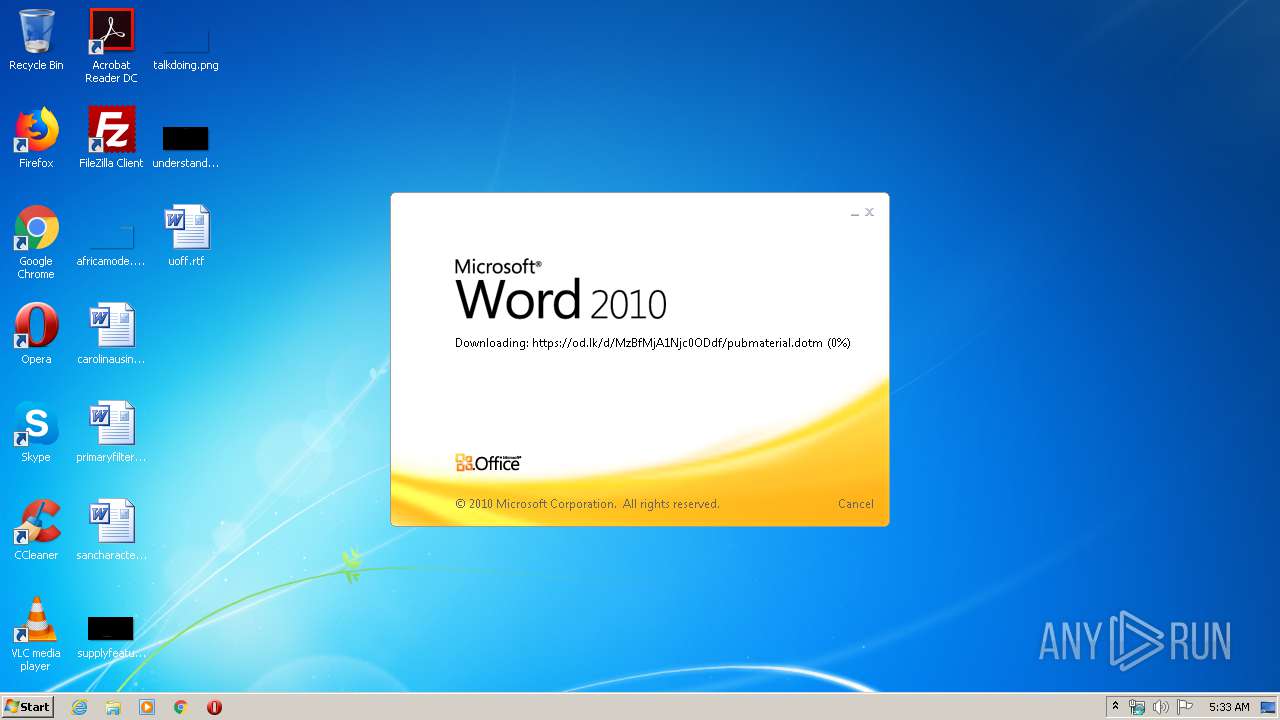
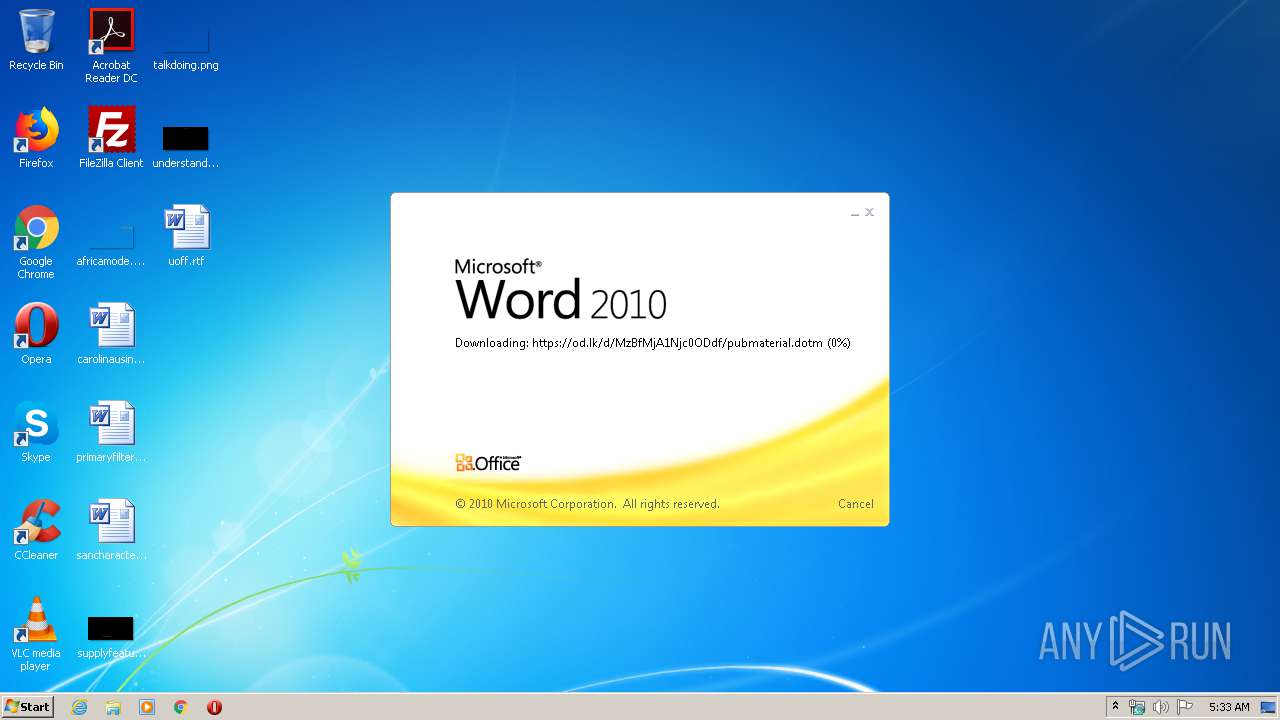
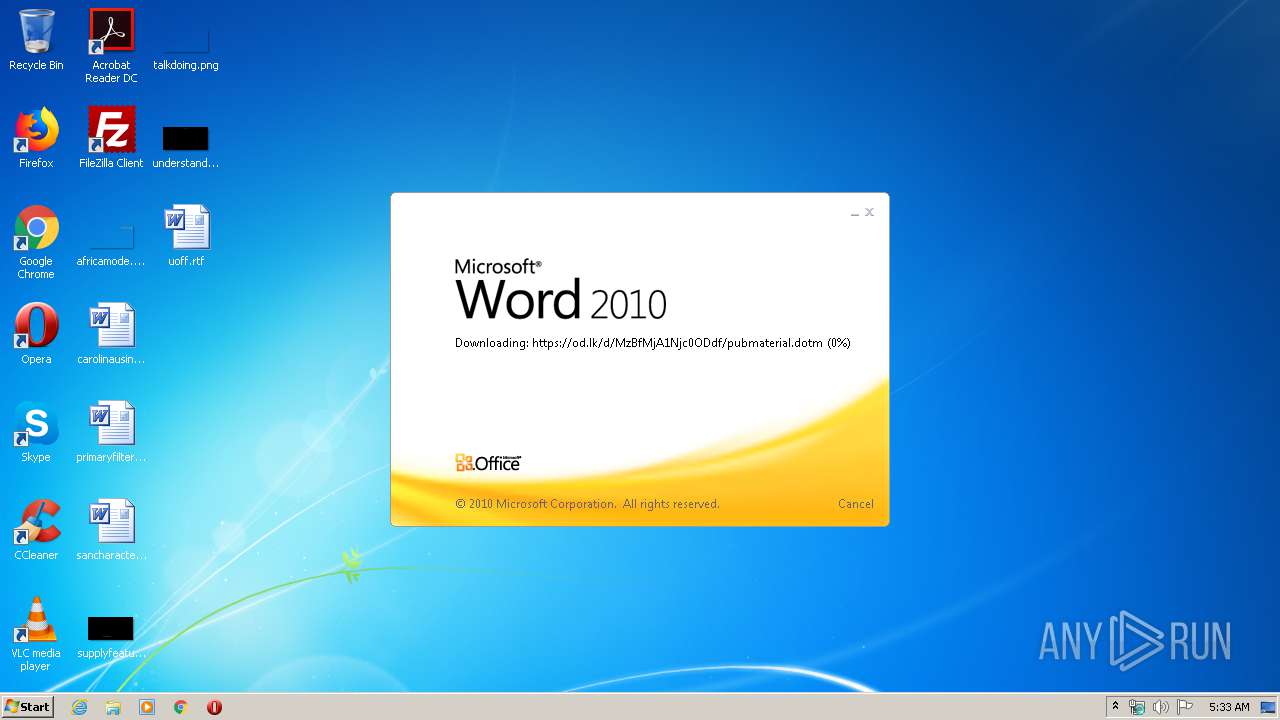
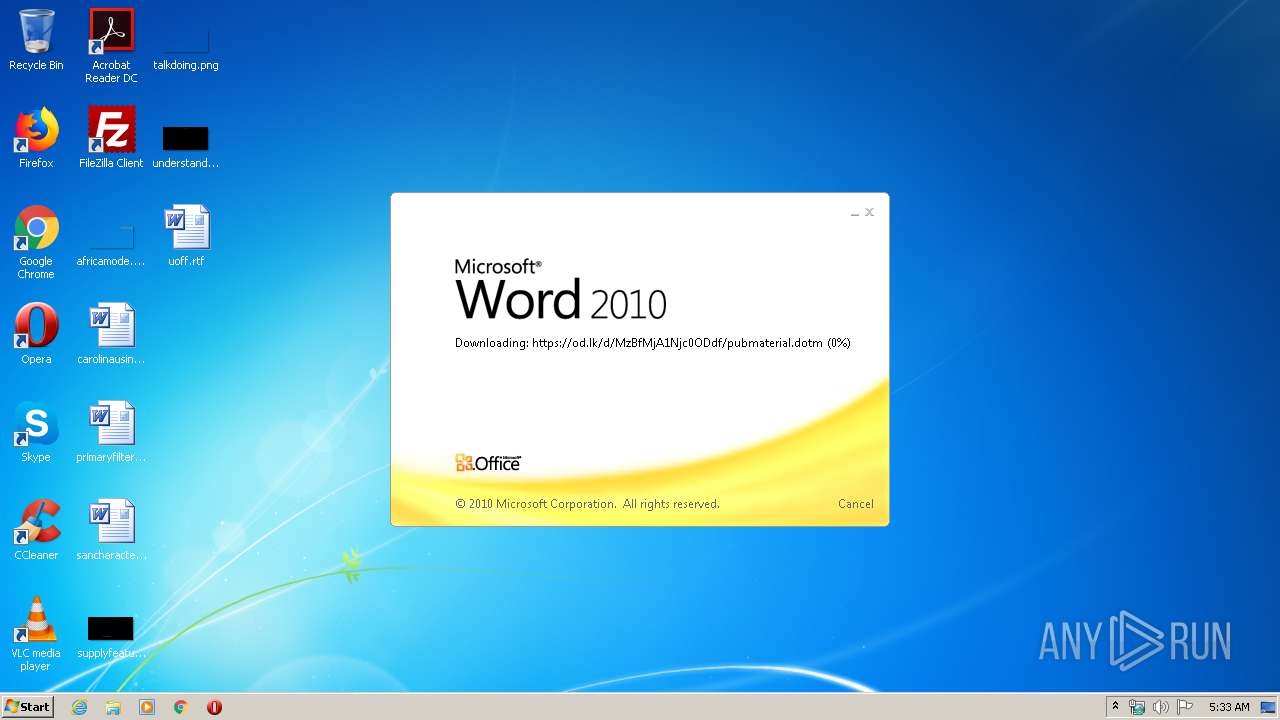
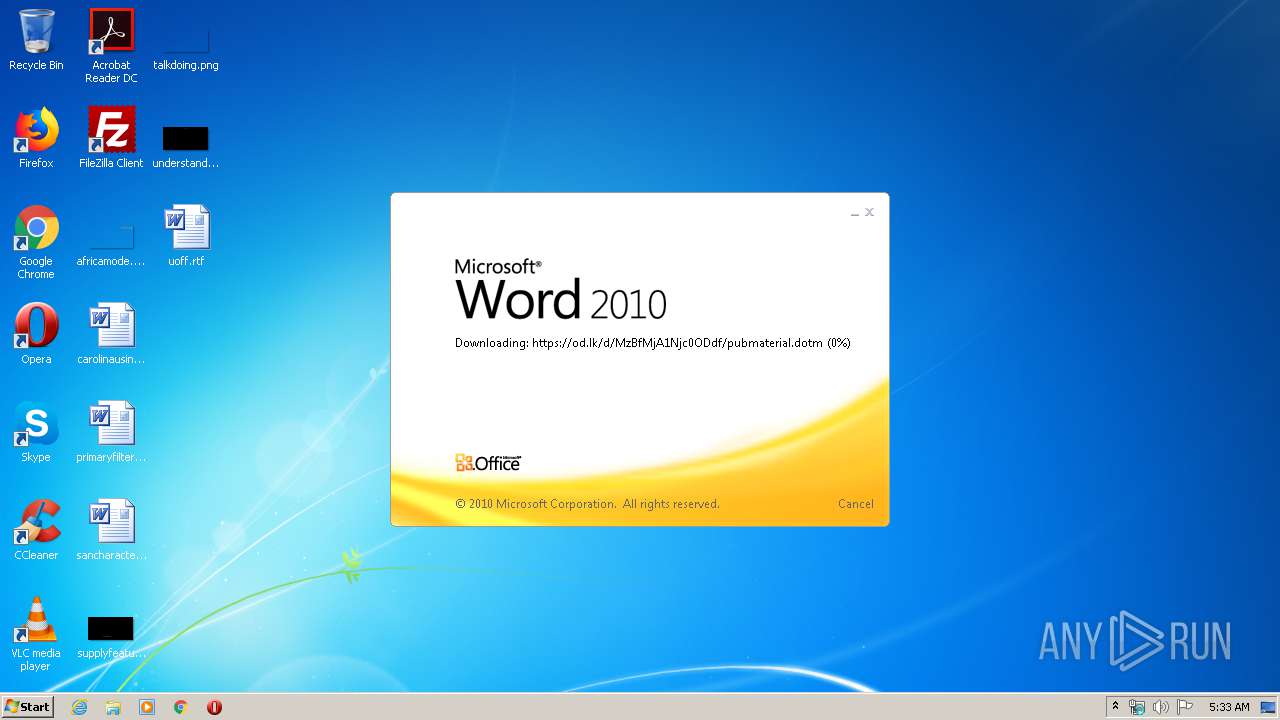
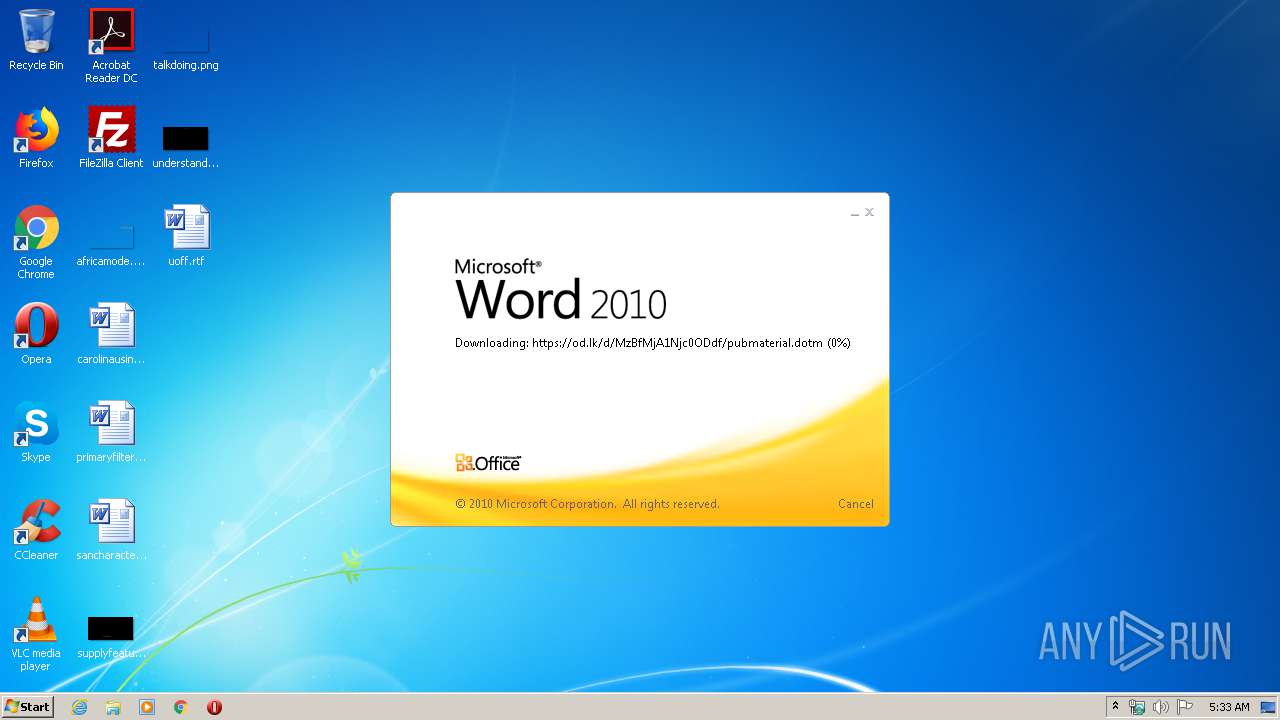
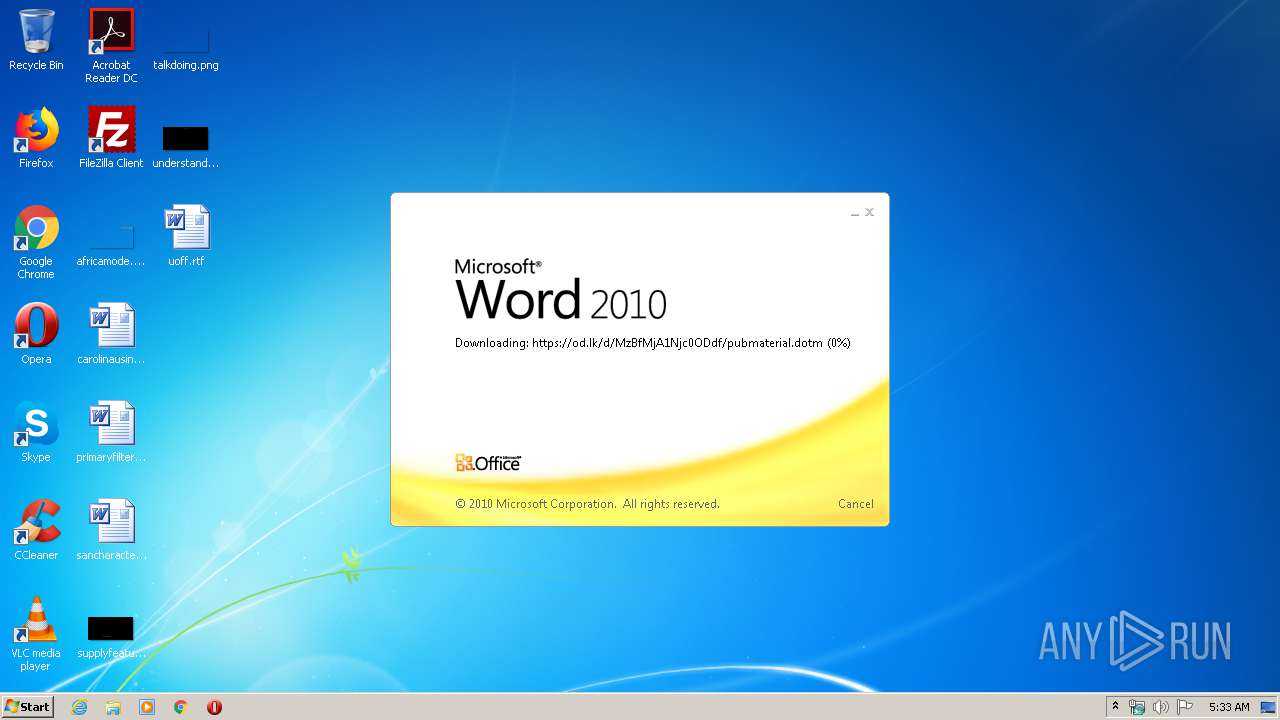
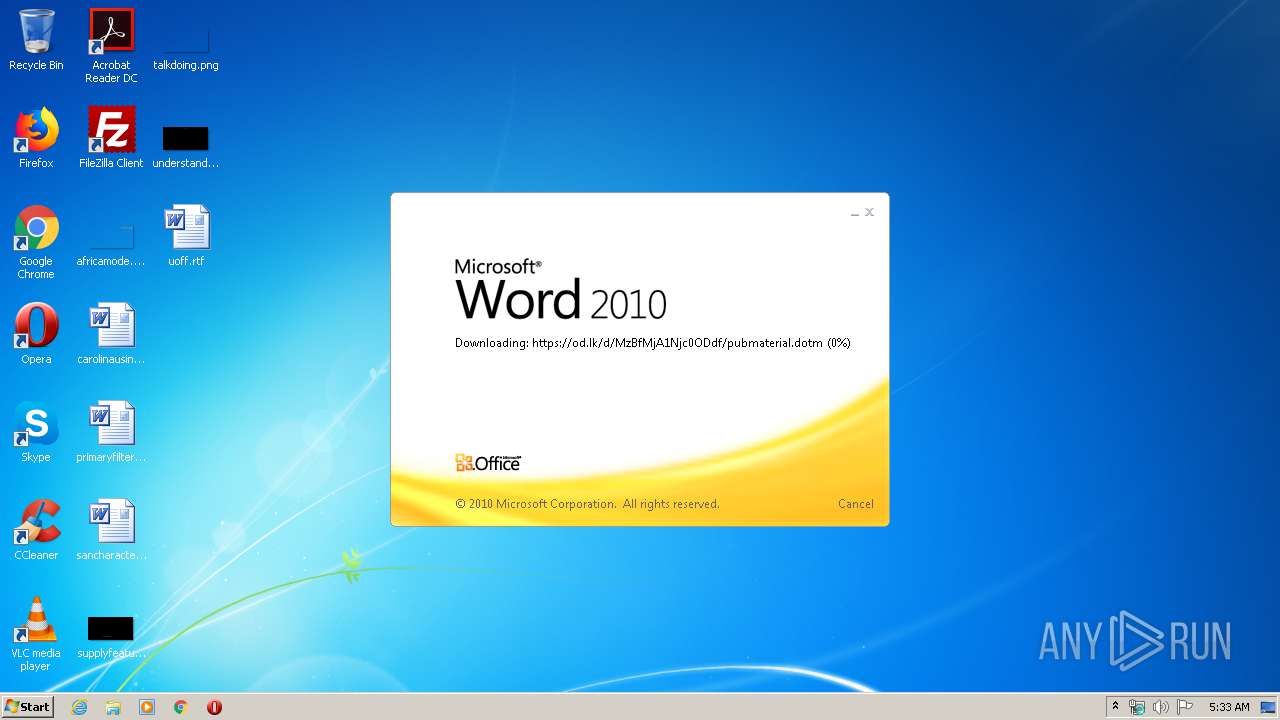
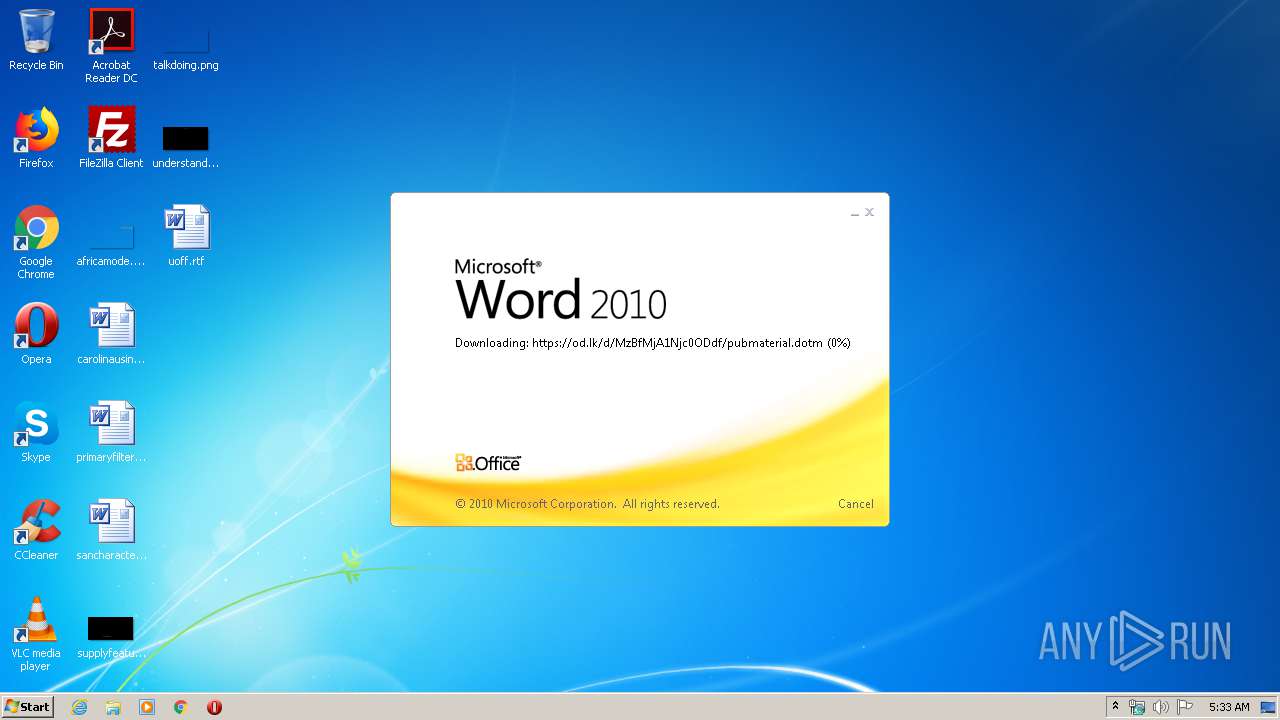
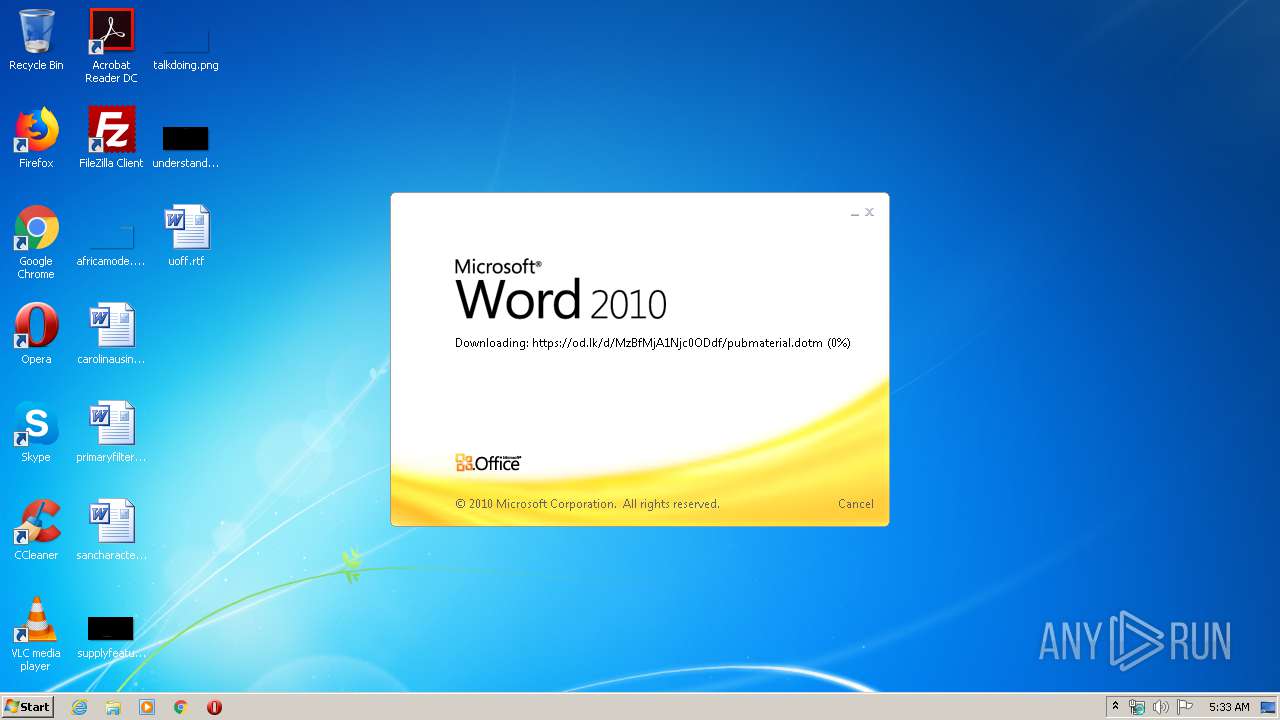
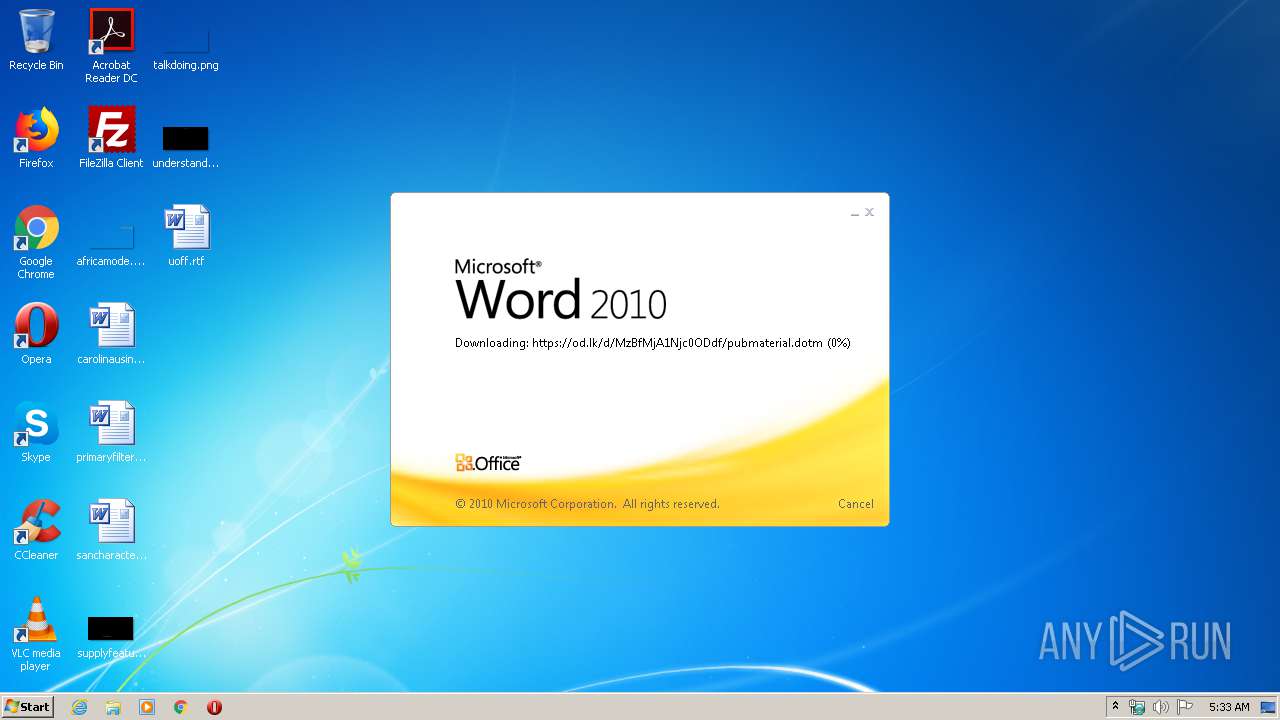
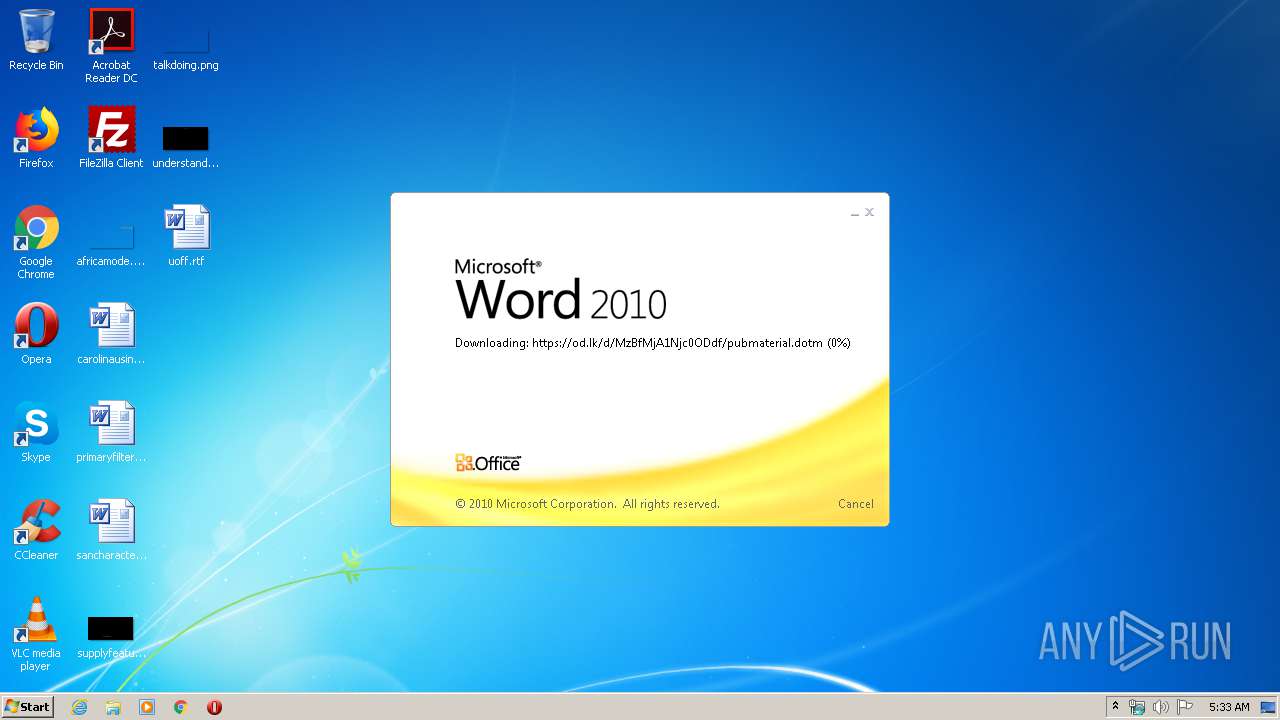
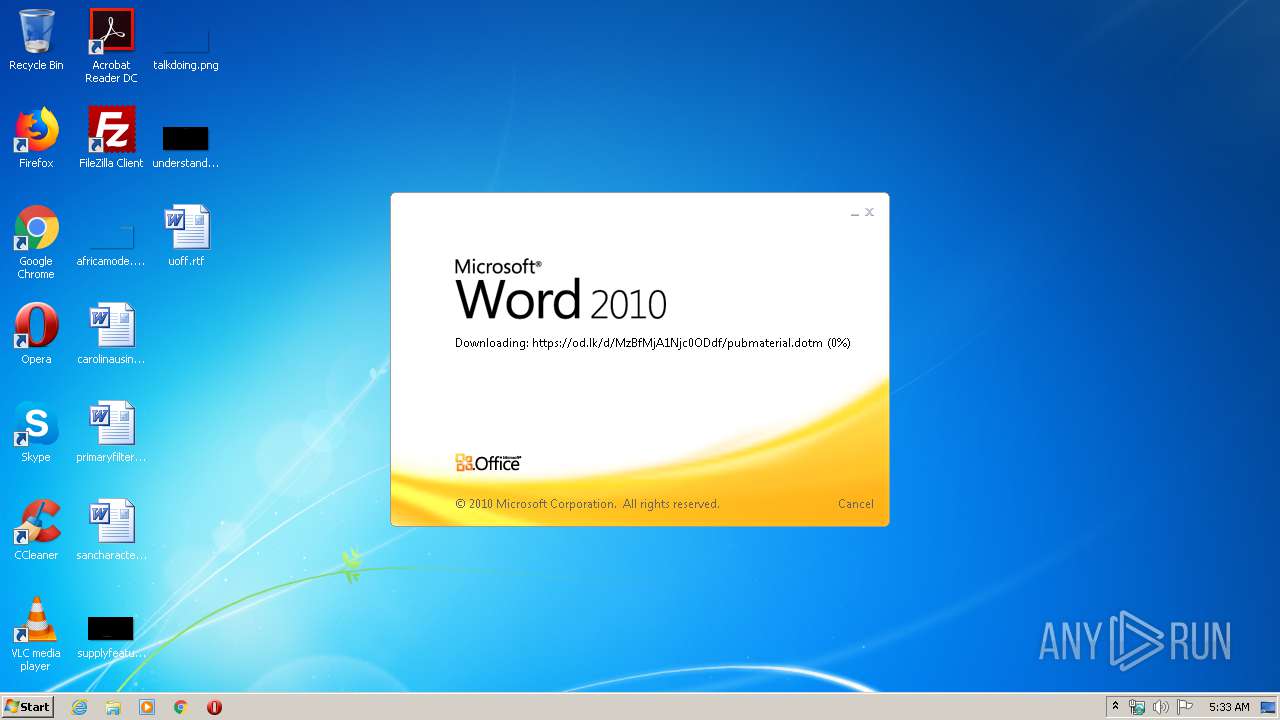
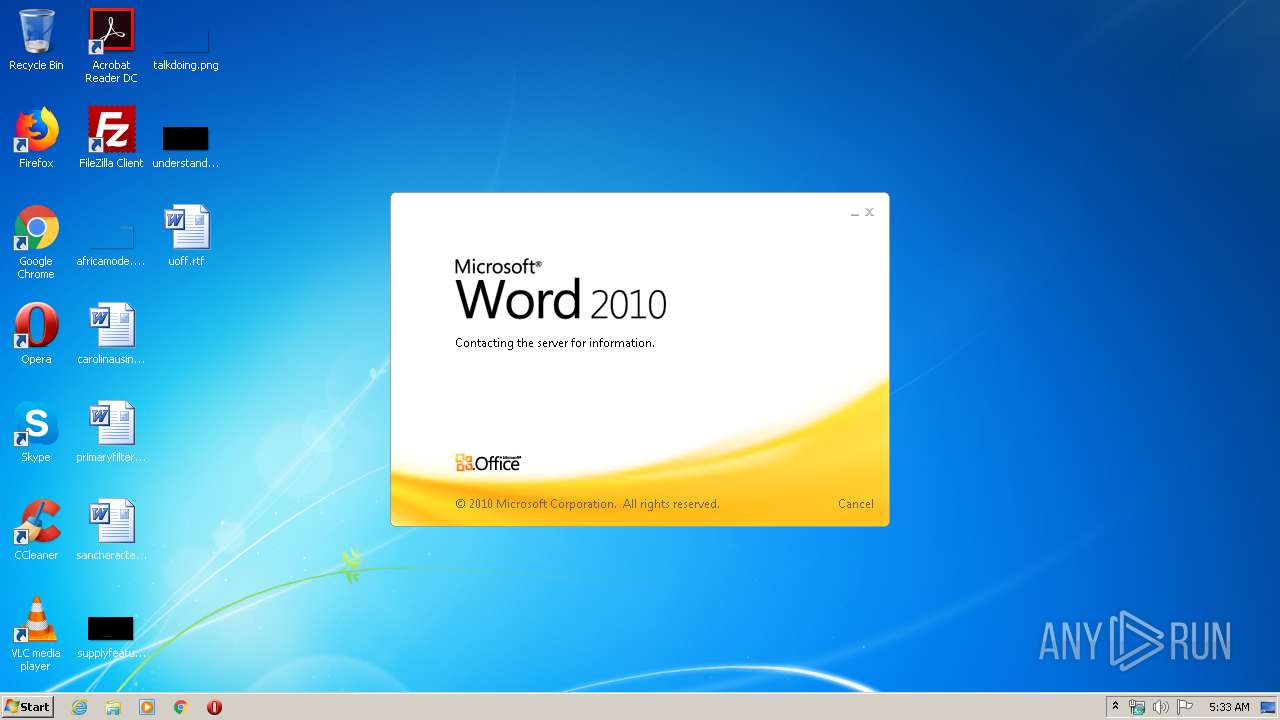
| File name: | 34b4546e3468238702df24794e598add494beaeacf95df10af54d88b3d241e8a.docx |
| Full analysis: | https://app.any.run/tasks/51a1296a-3a1a-4e47-9e59-27939f110b12 |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2020, 04:32:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 4C239A926676087E31D82E79E838CED1 |
| SHA1: | 2BEF437C6E7ED3C438D23E6CAC0A7FFB9D2F3E26 |
| SHA256: | 34B4546E3468238702DF24794E598ADD494BEAEACF95DF10AF54D88B3D241E8A |
| SSDEEP: | 6144:3fjyOrms2uRrXcuihuSKicuihuSKFhV/YbC:2OrGEcuiVKicuiVKFHAbC |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 1916)
Loads dropped or rewritten executable
- WINWORD.EXE (PID: 1916)
- rundll32.exe (PID: 604)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1916)
Writes to a start menu file
- WINWORD.EXE (PID: 1916)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- WINWORD.EXE (PID: 1916)
Executed via COM
- WINWORD.EXE (PID: 2684)
INFO
Reads Internet Cache Settings
- WINWORD.EXE (PID: 1916)
Creates files in the user directory
- WINWORD.EXE (PID: 1916)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1916)
- WINWORD.EXE (PID: 2684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xca98e698 |
| ZipCompressedSize: | 475 |
| ZipUncompressedSize: | 2994 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | JangSY |
|---|
XML
| LastModifiedBy: | user |
|---|---|
| RevisionNumber: | 1 |
| CreateDate: | 2020:04:06 08:47:00Z |
| ModifyDate: | 2020:04:06 08:49:00Z |
| Template: | ApothecaryLetter.dotx |
| TotalEditTime: | 2 minutes |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | C:\Windows\System32\rundll32.exe "C:\Users\admin\AppData\Local\Microsoft\OneNote\onenote.db", CMS_ContentInfo S-6-38-4412-76700627-315277-3247 0 0 18 1 | C:\Windows\System32\rundll32.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
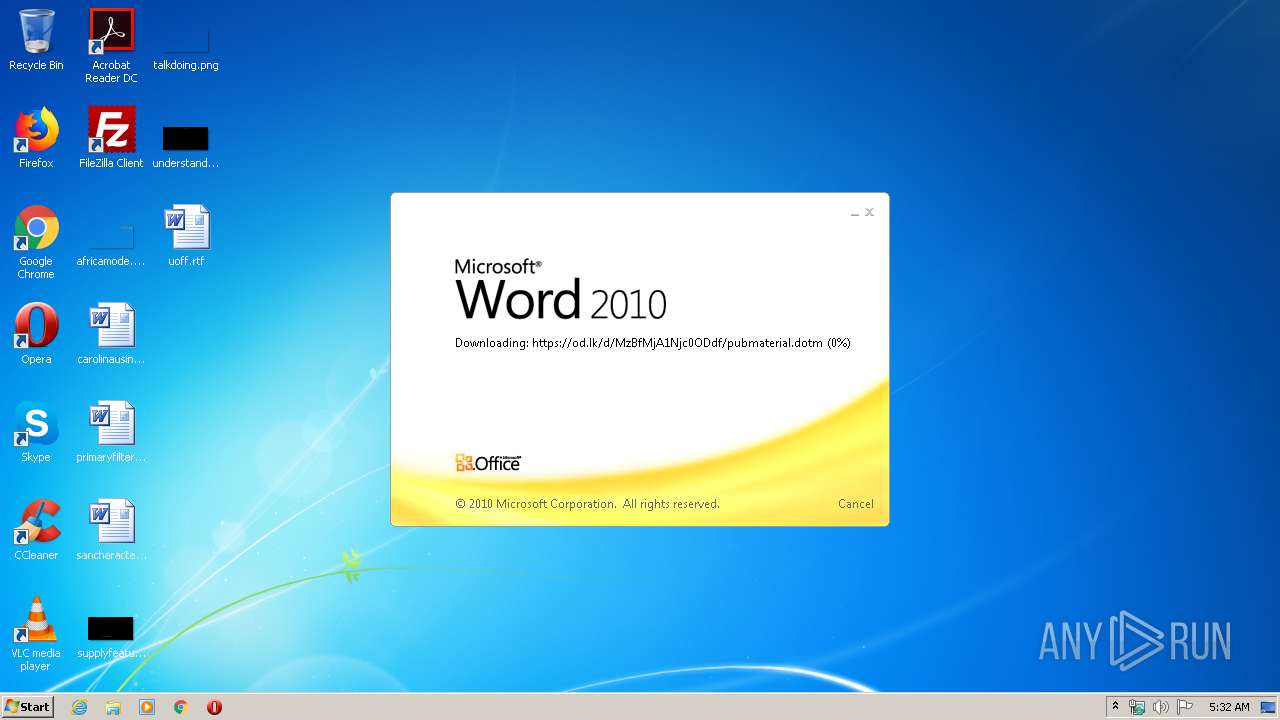
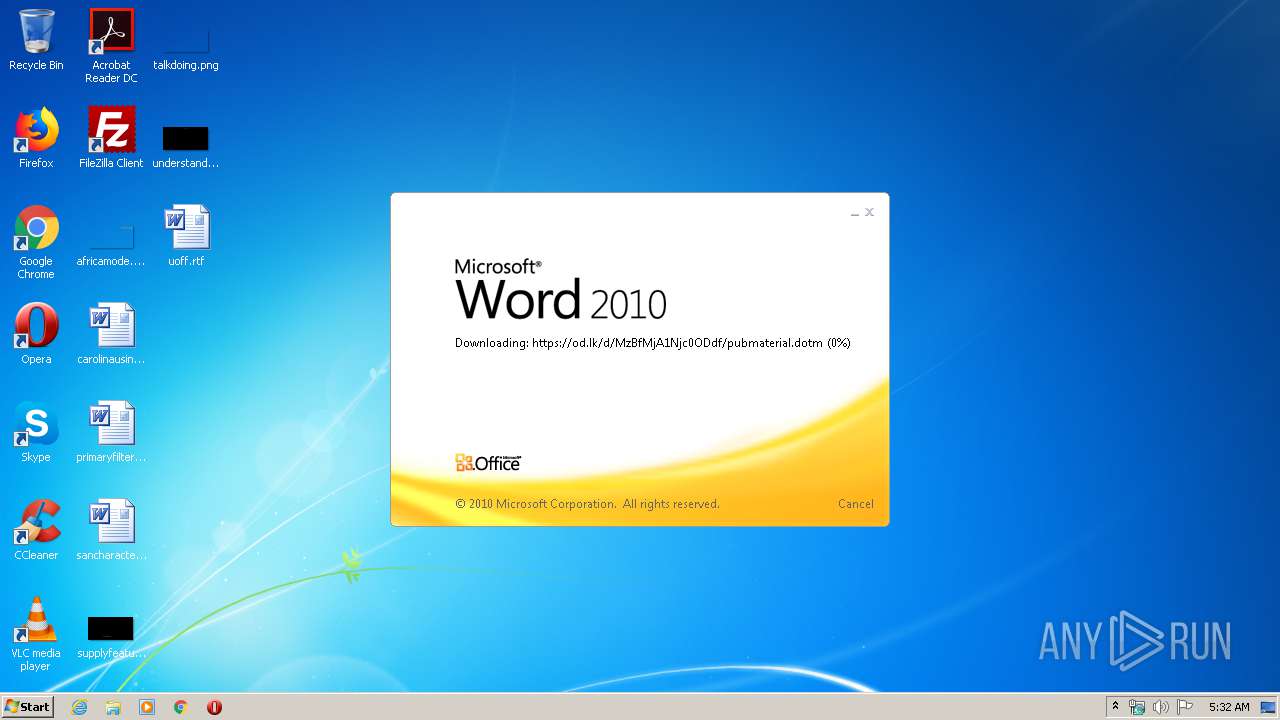
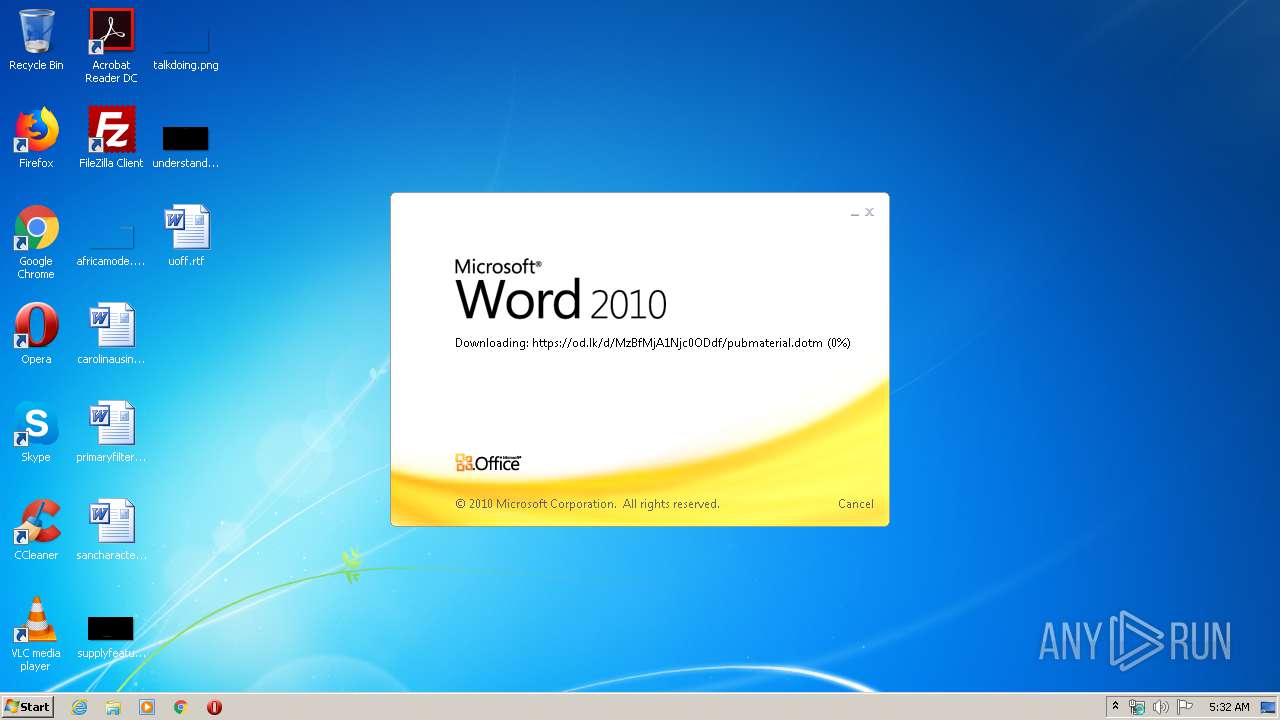
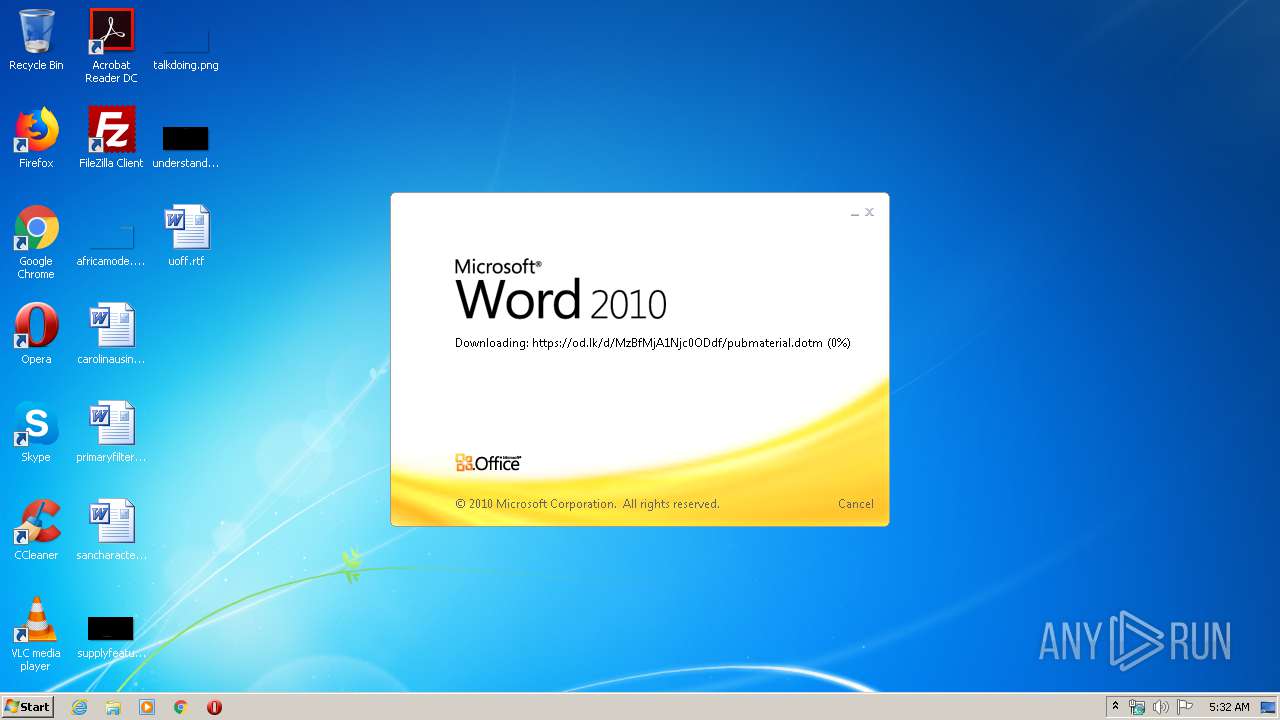
| 1916 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\34b4546e3468238702df24794e598add494beaeacf95df10af54d88b3d241e8a.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2684 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Automation -Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 890
Read events
1 695
Write events
1 074
Delete events
121
Modification events
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 4`5 |
Value: 346035007C070000010000000000000000000000 | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1916) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
35
Text files
5
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE0B4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\msoE5F4.tmp | — | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CabEA5A.tmp | — | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\TarEA5B.tmp | — | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{D4470957-BE97-4865-B9C8-E3C11903BB30} | — | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{0B39A297-E0FC-4489-8D12-02D0D78113E8} | — | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BC2602F5489CFE3E69F81C6328A4C17C_849A9AE095E451B9FFDF6A58F3A98E26 | der | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36CA4384028663214208D6897AE982DE_B5853EDE1BA77A3004D18C9D4909D359 | binary | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1916 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BC2602F5489CFE3E69F81C6328A4C17C_849A9AE095E451B9FFDF6A58F3A98E26 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1916 | WINWORD.EXE | GET | 200 | 192.124.249.22:80 | http://ocsp.starfieldtech.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBT1ZqtwV0O1KcYi0gdzcFkHM%2BuArAQUJUWBaFAmOD07LSy%2BzWrZtj2zZmMCCQC99IvcVldvMQ%3D%3D | US | der | 1.80 Kb | whitelisted |
1916 | WINWORD.EXE | GET | 200 | 192.124.249.22:80 | http://ocsp.starfieldtech.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCAzkUhA%3D%3D | US | der | 1.70 Kb | whitelisted |
1916 | WINWORD.EXE | GET | 200 | 192.124.249.22:80 | http://ocsp.starfieldtech.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQUwPiEZQ6%2FsVZNPaFToNfxx8ZwqAQUfAwyH6fZMH%2FEfWijYqihzqsHWycCAQc%3D | US | der | 1.74 Kb | whitelisted |
1916 | WINWORD.EXE | GET | 200 | 192.124.249.22:80 | http://ocsp.starfieldtech.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBT1ZqtwV0O1KcYi0gdzcFkHM%2BuArAQUJUWBaFAmOD07LSy%2BzWrZtj2zZmMCCQC9vPUDVXnWRA%3D%3D | US | der | 1.80 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1916 | WINWORD.EXE | 192.124.249.22:80 | ocsp.starfieldtech.com | Sucuri | US | suspicious |
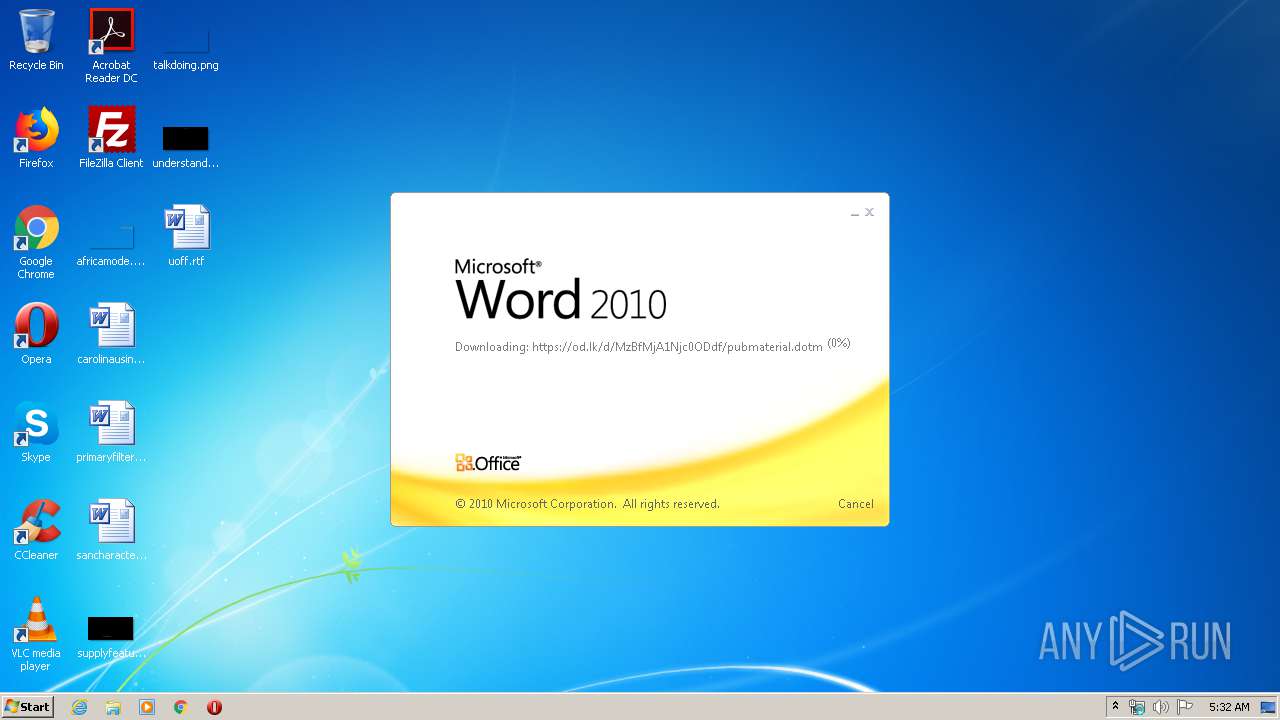
824 | svchost.exe | 38.108.185.79:443 | od.lk | Cogent Communications | US | unknown |
824 | svchost.exe | 38.108.185.115:443 | od.lk | Cogent Communications | US | suspicious |
604 | rundll32.exe | 192.169.250.185:443 | www.elite4print.com | GoDaddy.com, LLC | US | suspicious |
1916 | WINWORD.EXE | 38.108.185.70:443 | web.opendrive.com | Cogent Communications | US | unknown |
1916 | WINWORD.EXE | 38.108.185.79:443 | od.lk | Cogent Communications | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
od.lk |
| shared |
ocsp.starfieldtech.com |
| whitelisted |
dns.msftncsi.com |
| shared |
web.opendrive.com |
| suspicious |
www.elite4print.com |
| suspicious |