| File name: | 7782096160.zip |
| Full analysis: | https://app.any.run/tasks/dc8be754-d94c-41e3-abd3-cc4c5fdf6bb5 |
| Verdict: | Malicious activity |
| Analysis date: | July 27, 2022, 17:22:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 156450C1E5192AE977B2070DDC13A495 |
| SHA1: | 0FA8AB23F9092422A0DB2DE6003C1175CE36B9BA |
| SHA256: | 34909DA23372C6134449E94F64273ABEADD069F2EB5F791BCAD65A8BBA8A7AF8 |
| SSDEEP: | 24576:geiwuyAi55TGDr2CaAfbmYKyt6yavIY4nfKW2YvAYzEeTjO1TcSxPvwRkKNOWXFa:BF5NGXNaObvKm6c4YRjOY6KAIS/V |
MALICIOUS
Drops executable file immediately after starts
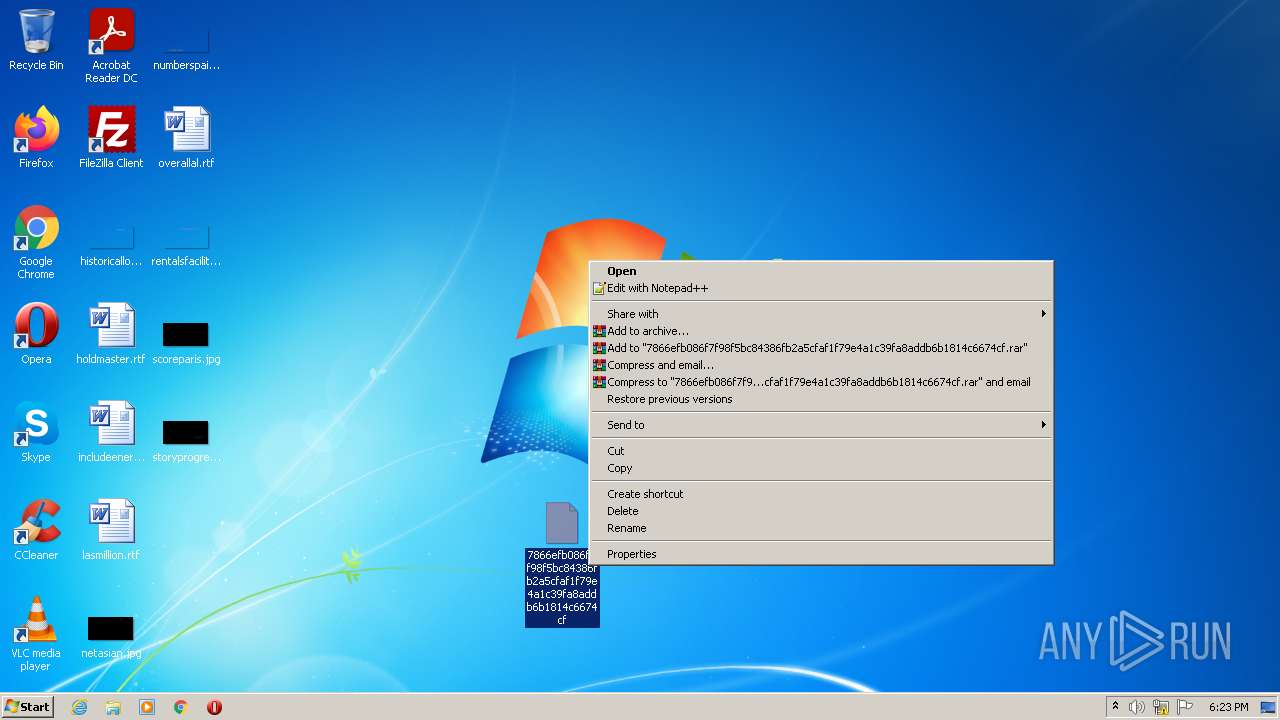
- WinRAR.exe (PID: 3948)
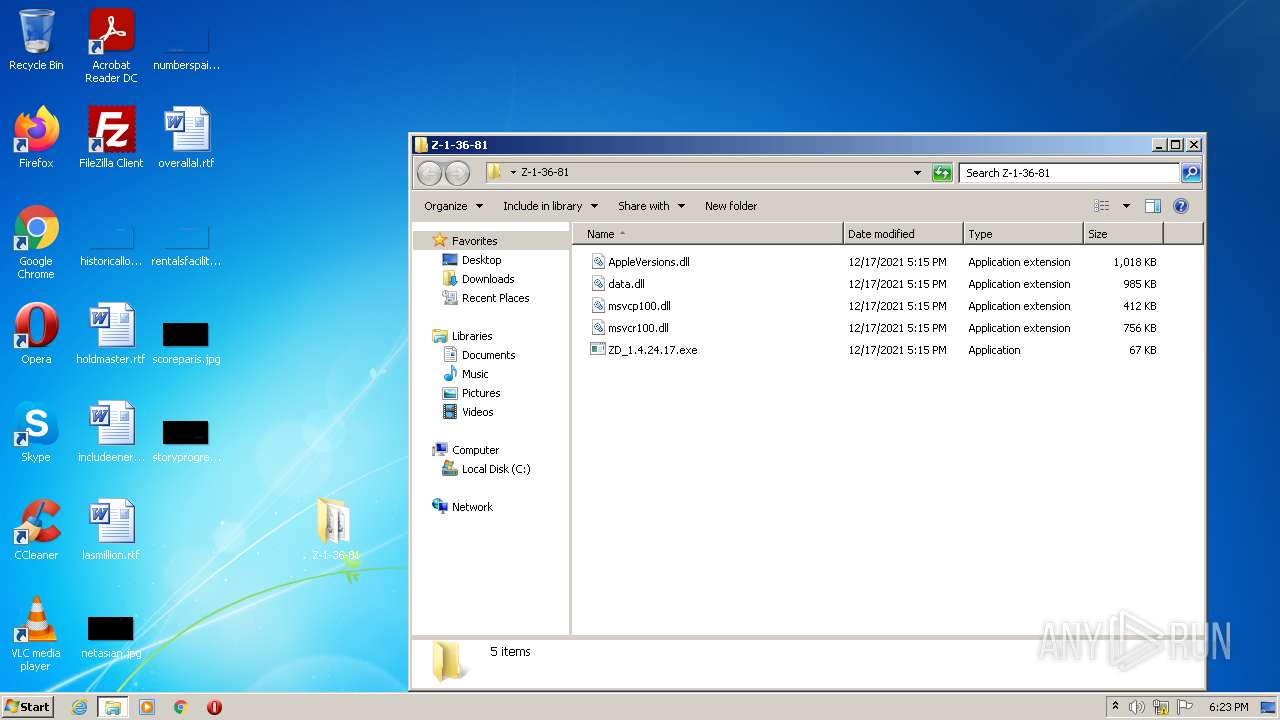
- ZD_1.4.24.17.exe (PID: 3720)
Application was dropped or rewritten from another process
- ZD_1.4.24.17.exe (PID: 3720)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1448)
- ZD_1.4.24.17.exe (PID: 3720)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3104)
- WinRAR.exe (PID: 3948)
- ZD_1.4.24.17.exe (PID: 3720)
Checks supported languages
- WinRAR.exe (PID: 3104)
- ZD_1.4.24.17.exe (PID: 3720)
- WinRAR.exe (PID: 3948)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3948)
- ZD_1.4.24.17.exe (PID: 3720)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3948)
INFO
Manual execution by user
- ZD_1.4.24.17.exe (PID: 3720)
- WinRAR.exe (PID: 3948)
Checks Windows Trust Settings
- ZD_1.4.24.17.exe (PID: 3720)
Reads settings of System Certificates
- ZD_1.4.24.17.exe (PID: 3720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | 7866efb086f7f98f5bc84386fb2a5cfaf1f79e4a1c39fa8addb6b1814c6674cf |
|---|---|
| ZipUncompressedSize: | 1938075 |
| ZipCompressedSize: | 1938548 |
| ZipCRC: | 0x235d0905 |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
40
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1448 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3104 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\7782096160.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
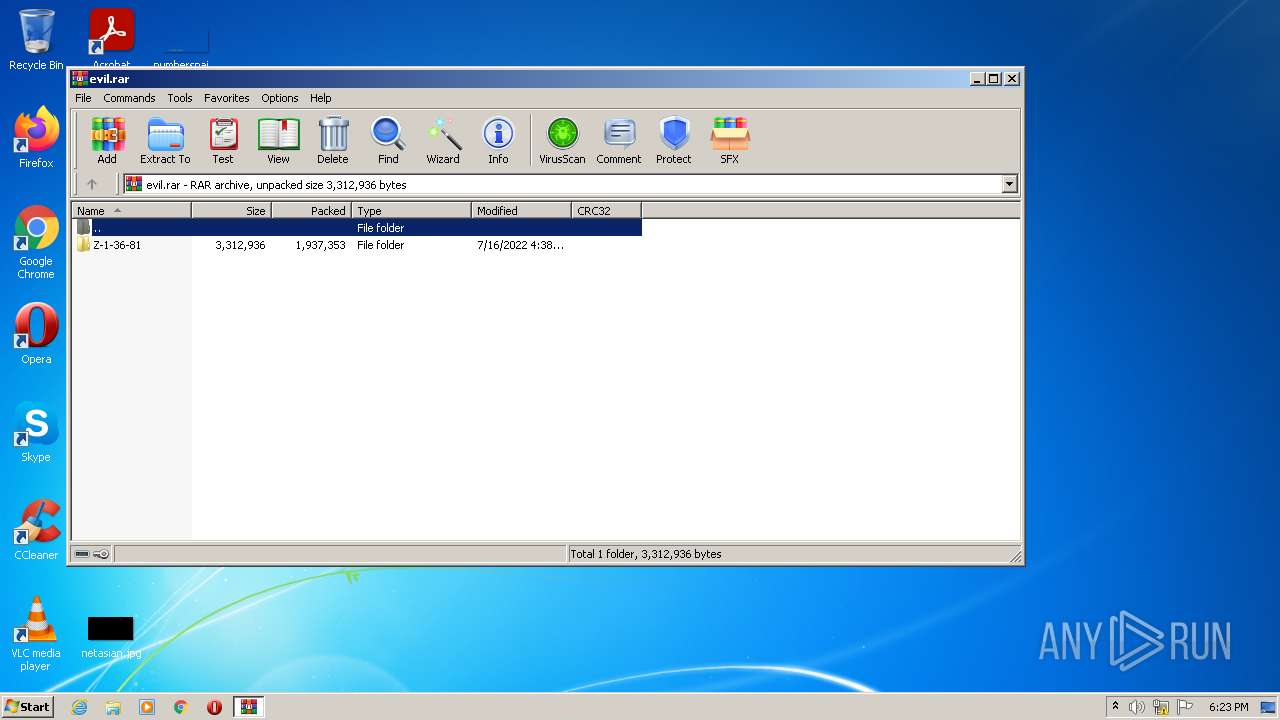
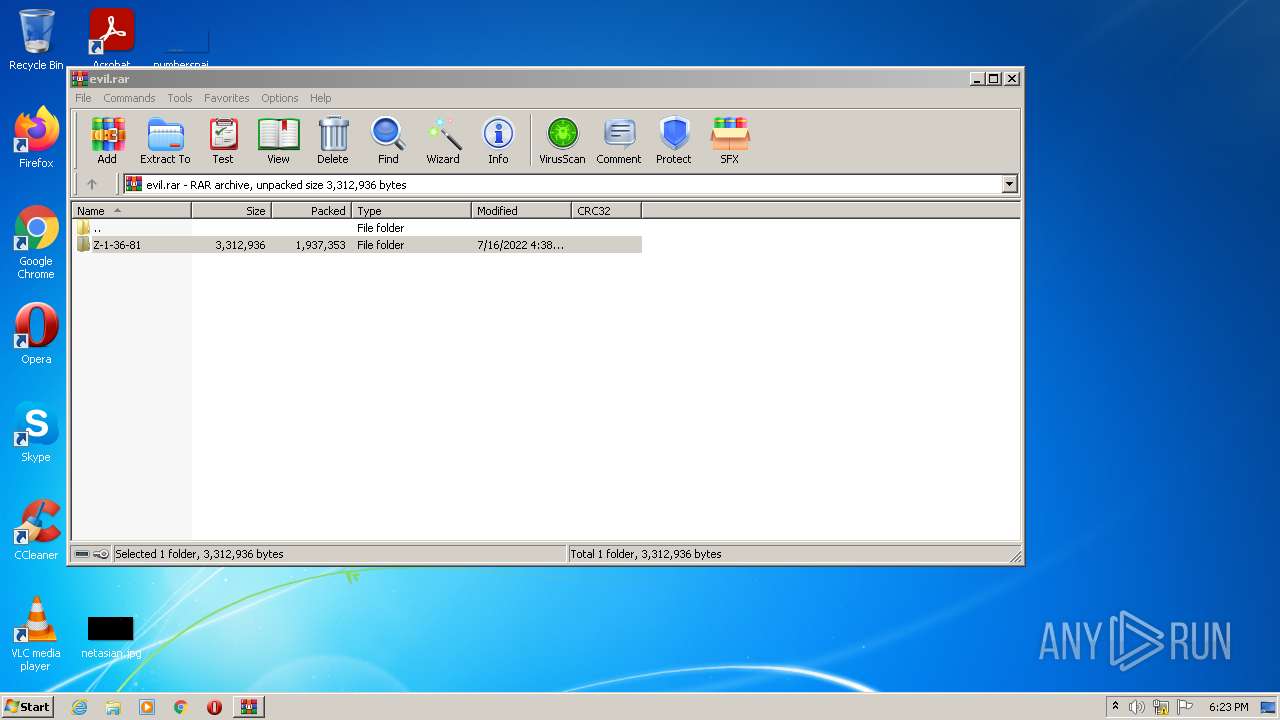
| 3720 | "C:\Users\admin\Desktop\Z-1-36-81\ZD_1.4.24.17.exe" | C:\Users\admin\Desktop\Z-1-36-81\ZD_1.4.24.17.exe | Explorer.EXE | ||||||||||||
User: admin Company: Apple Inc. Integrity Level: MEDIUM Description: Apple Push Exit code: 151 Version: 2.7.22.21 Modules
| |||||||||||||||
| 3948 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\evil.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 829
Read events
6 751
Write events
78
Delete events
0
Modification events
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\7782096160.zip | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
6
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3720 | ZD_1.4.24.17.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3720 | ZD_1.4.24.17.exe | C:\Users\admin\AppData\Local\Temp\CabD5C2.tmp | compressed | |
MD5:— | SHA256:— | |||
| 3720 | ZD_1.4.24.17.exe | C:\Users\admin\AppData\Local\Temp\TarD5C3.tmp | cat | |
MD5:— | SHA256:— | |||
| 3720 | ZD_1.4.24.17.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 3720 | ZD_1.4.24.17.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\data[1].bin | binary | |
MD5:— | SHA256:— | |||
| 3104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3104.23023\7866efb086f7f98f5bc84386fb2a5cfaf1f79e4a1c39fa8addb6b1814c6674cf | compressed | |
MD5:A05144D7254B419D3A09787E280B4BE3 | SHA256:7866EFB086F7F98F5BC84386FB2A5CFAF1F79E4A1C39FA8ADDB6B1814C6674CF | |||
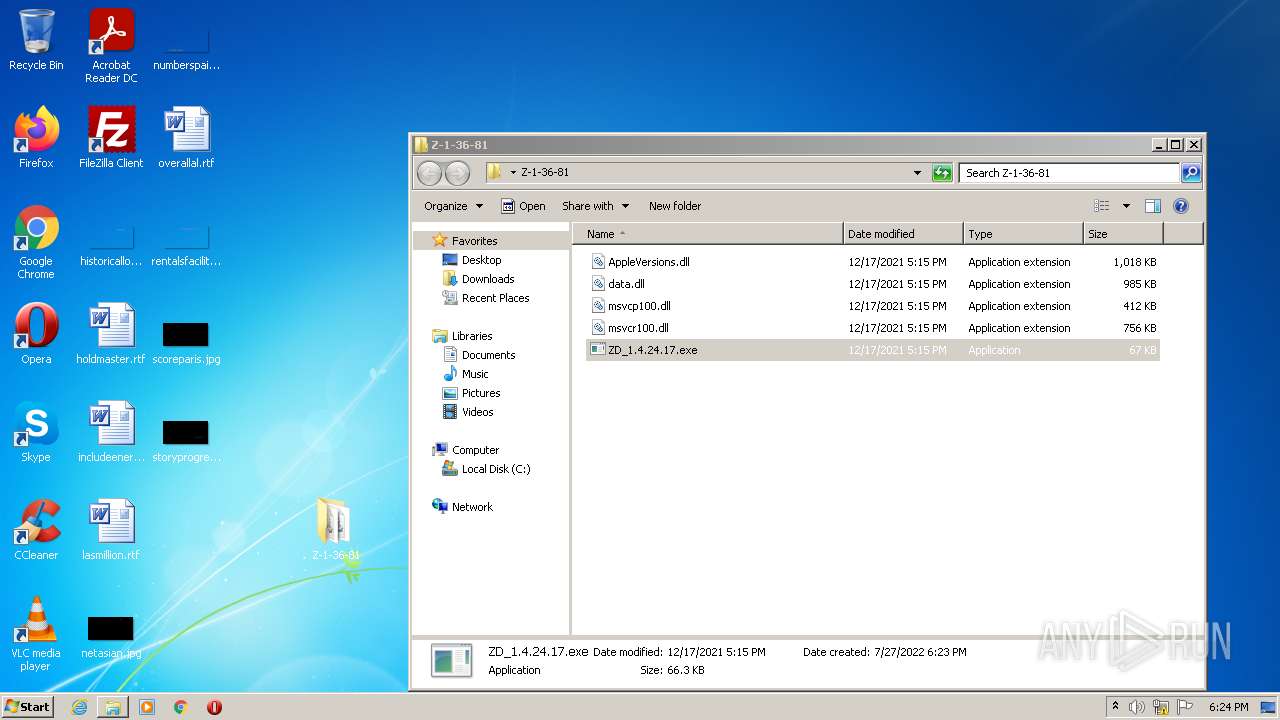
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.24368\Z-1-36-81\AppleVersions.dll | executable | |
MD5:E0E4B11A823B9CCF83EF71764AC31762 | SHA256:103DA5CEE32496CED042A4C6D63ABDBFECDFB208A482156B6F099F622647D648 | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.24368\Z-1-36-81\msvcr100.dll | executable | |
MD5:0E37FBFA79D349D672456923EC5FBBE3 | SHA256:8793353461826FBD48F25EA8B835BE204B758CE7510DB2AF631B28850355BD18 | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.24368\Z-1-36-81\ZD_1.4.24.17.exe | executable | |
MD5:A72E79B12016B789F796BA267CCA05A9 | SHA256:FC45EB5C9D3F89CB059212E00512EC0E6C47C1BDF12842256CEDA5D4F1371BD5 | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3948.24368\Z-1-36-81\data.dll | executable | |
MD5:45DDDC18557B63C288E8D3AEBE17C8FA | SHA256:6A11E460BD2F9FC29EC518F29A5854C8A79033A48CC432FF6E4679E251883808 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3720 | ZD_1.4.24.17.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?906f3a577fcf0f41 | US | compressed | 60.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3720 | ZD_1.4.24.17.exe | 23.216.77.80:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
3720 | ZD_1.4.24.17.exe | 185.225.17.239:443 | rqmetrixb.info | — | — | malicious |
3720 | ZD_1.4.24.17.exe | 185.225.17.249:443 | rqmetrixd.info | — | — | suspicious |
3720 | ZD_1.4.24.17.exe | 185.225.17.235:443 | rqmetrixa.info | — | — | malicious |
3720 | ZD_1.4.24.17.exe | 185.225.17.243:443 | rqmetrixc.info | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rqmetrixb.info |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
rqmetrixa.info |
| unknown |
rqmetrixc.info |
| unknown |
rqmetrixd.info |
| unknown |
33f47123e8cfce07f3ba4d073238576c.rqmetrixsdn.info |
| unknown |