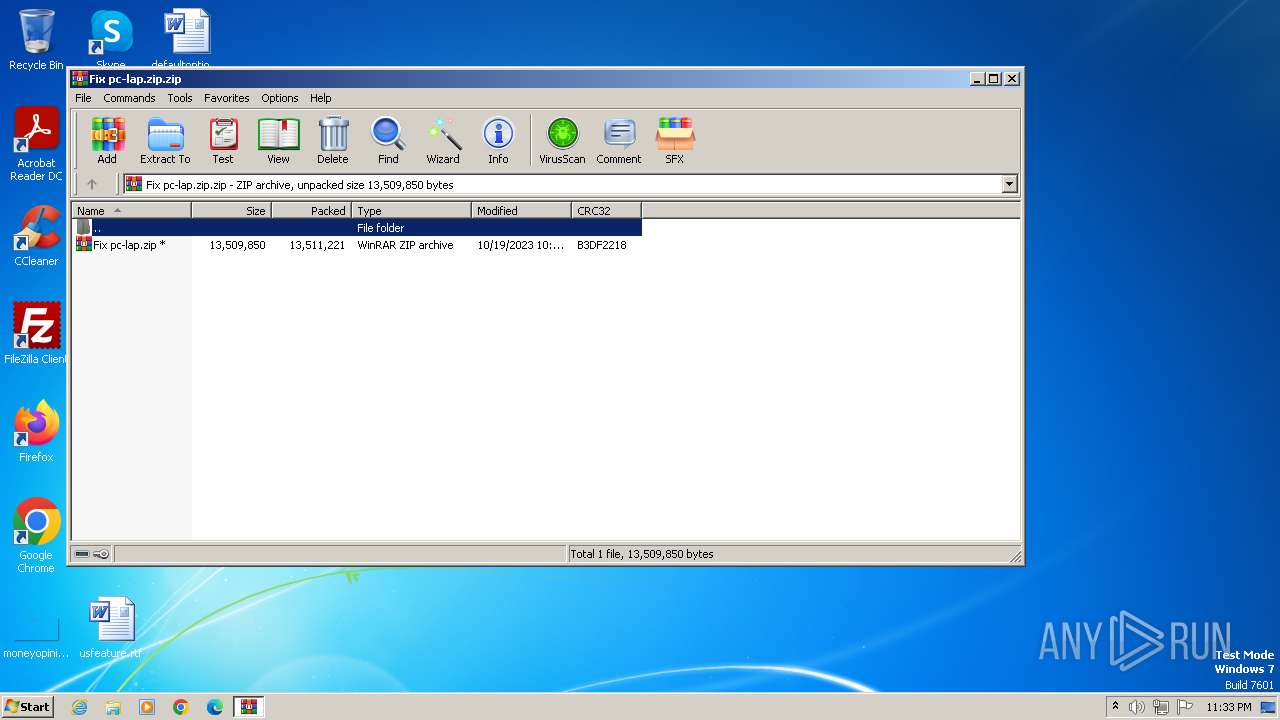
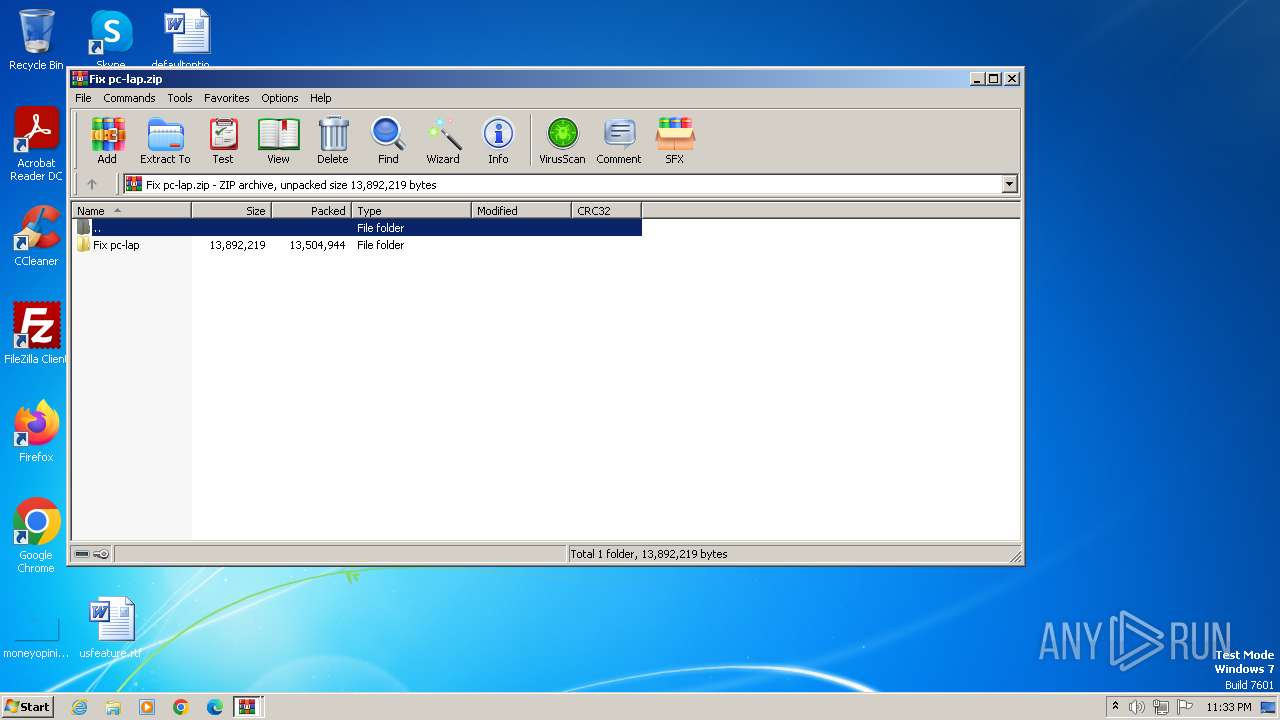
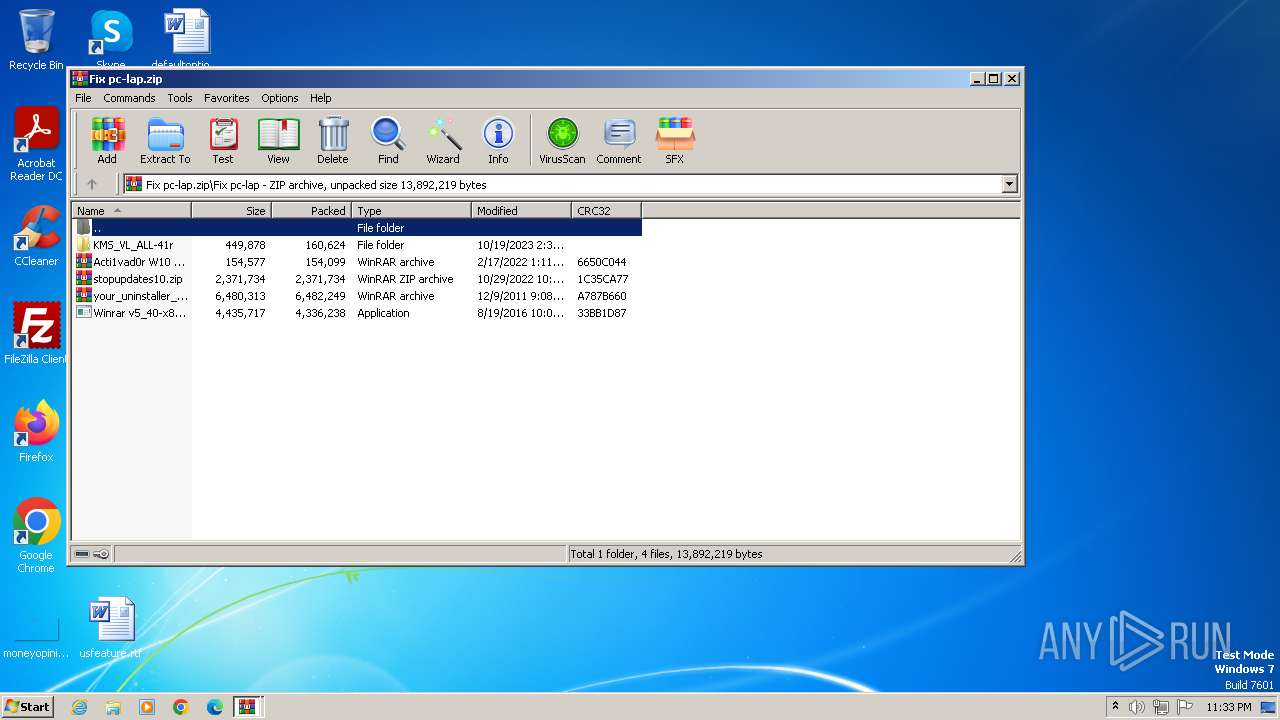
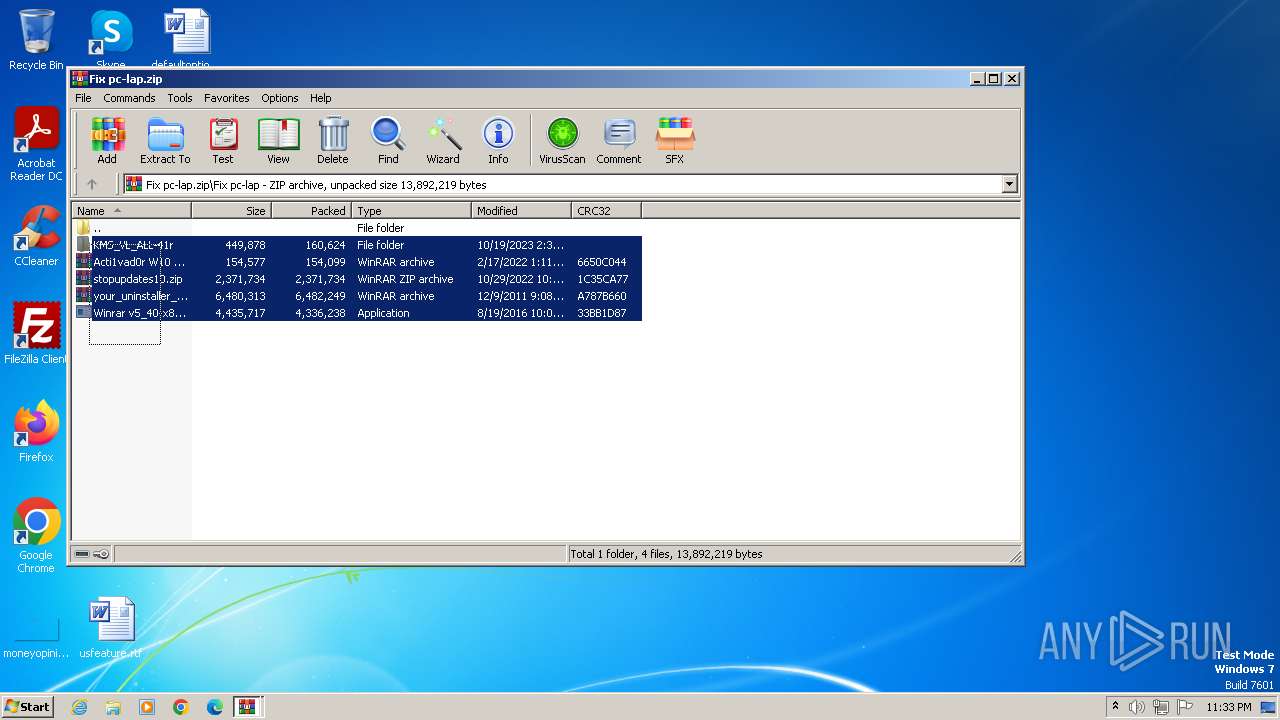
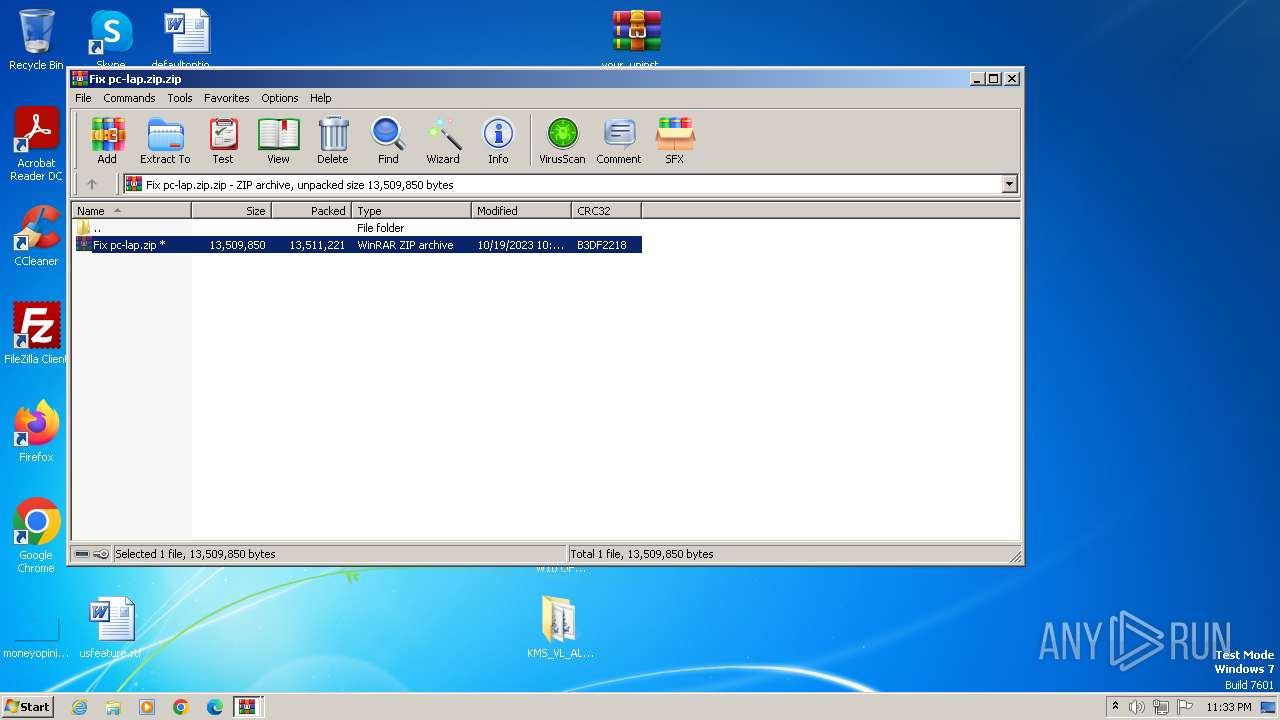
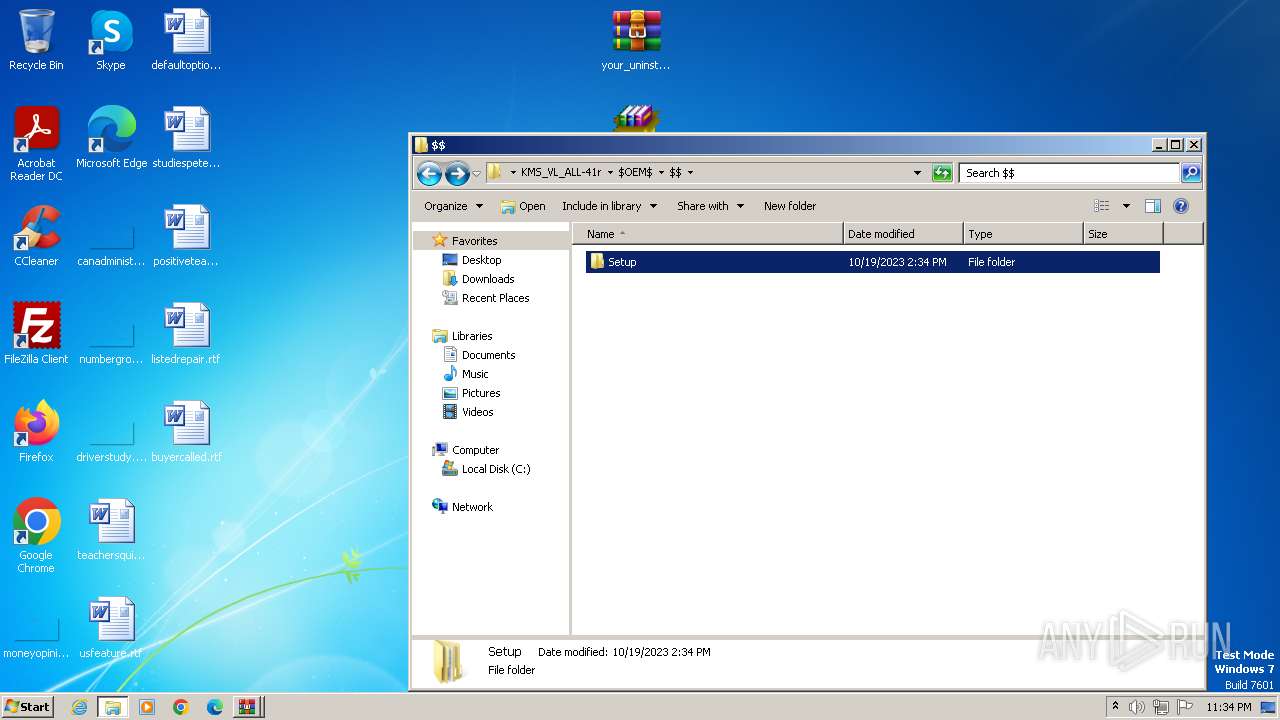
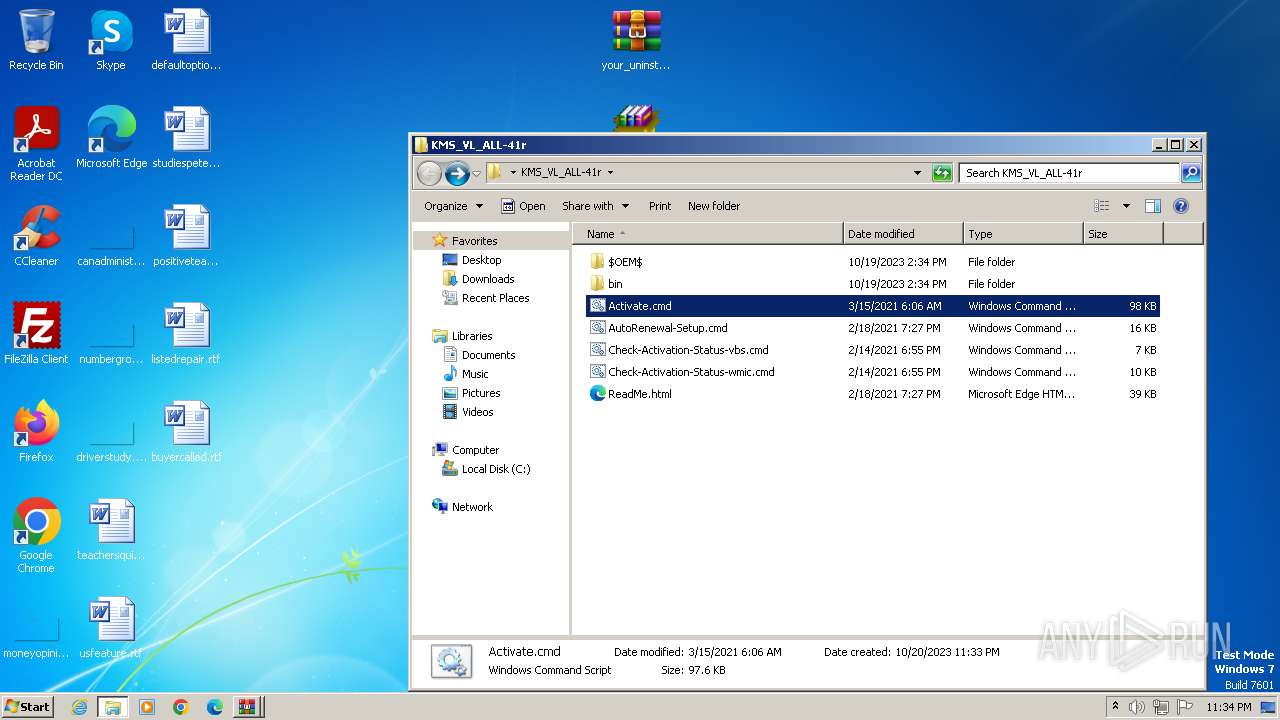
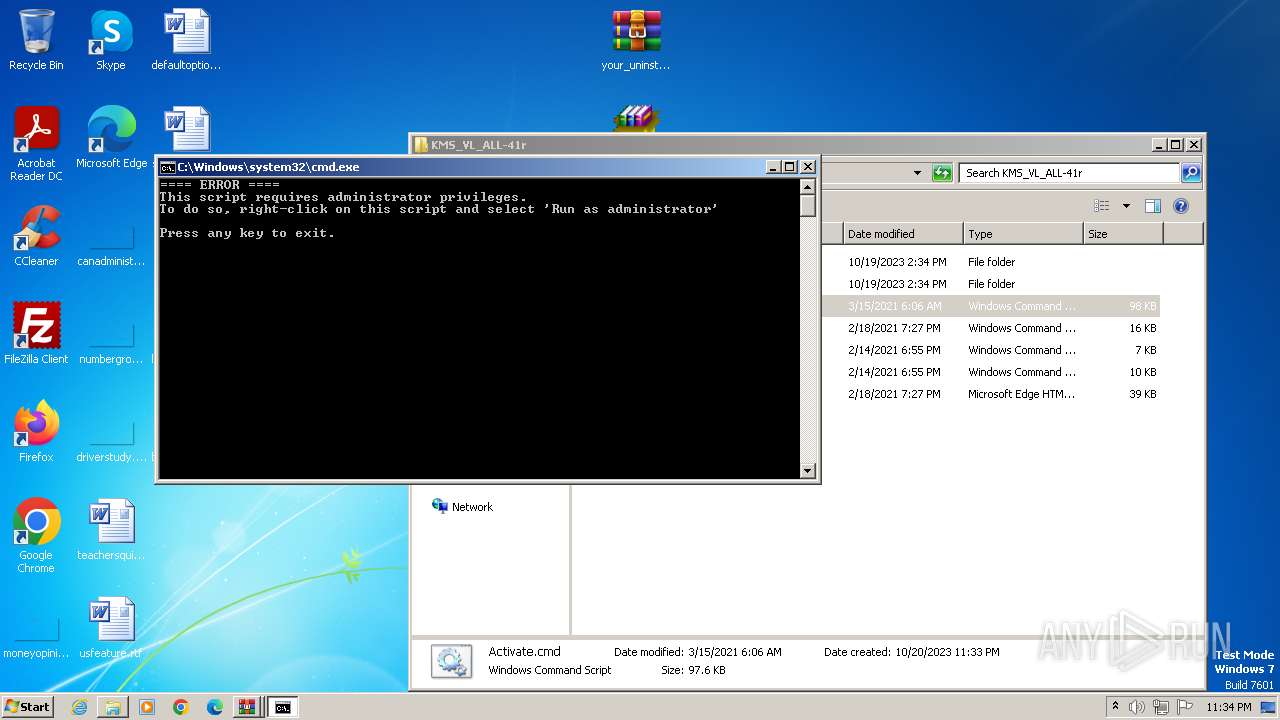
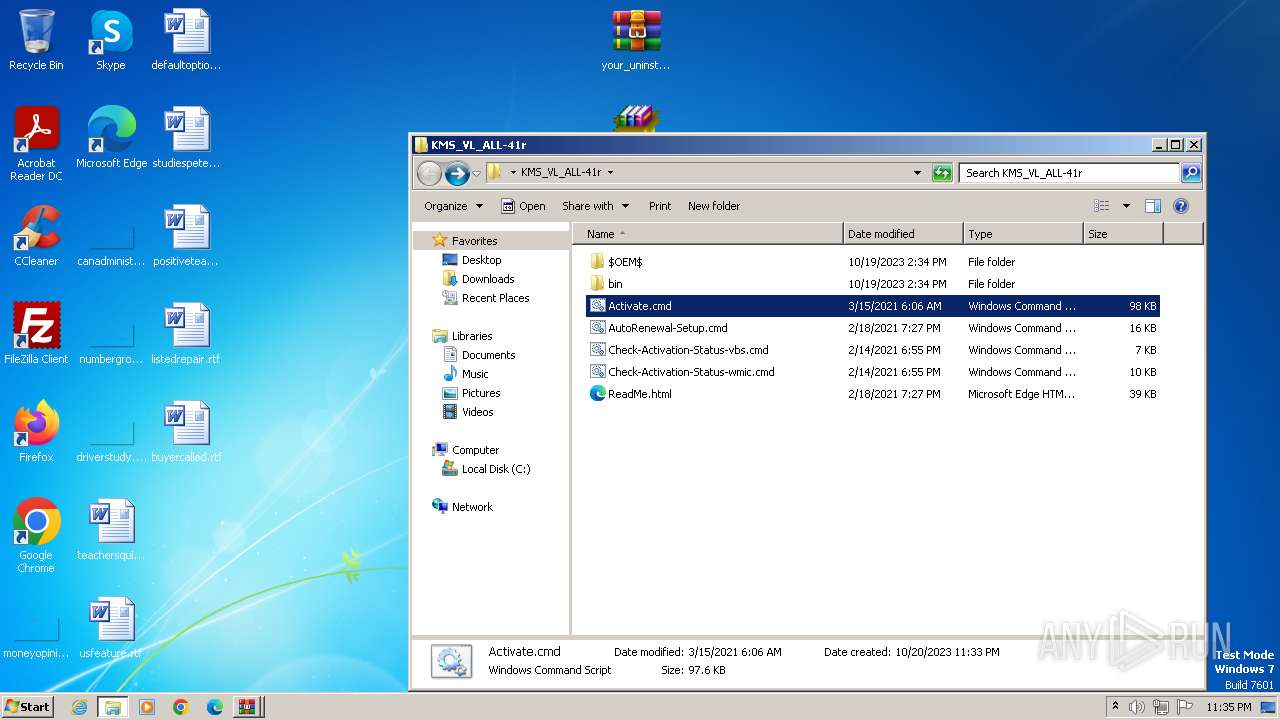
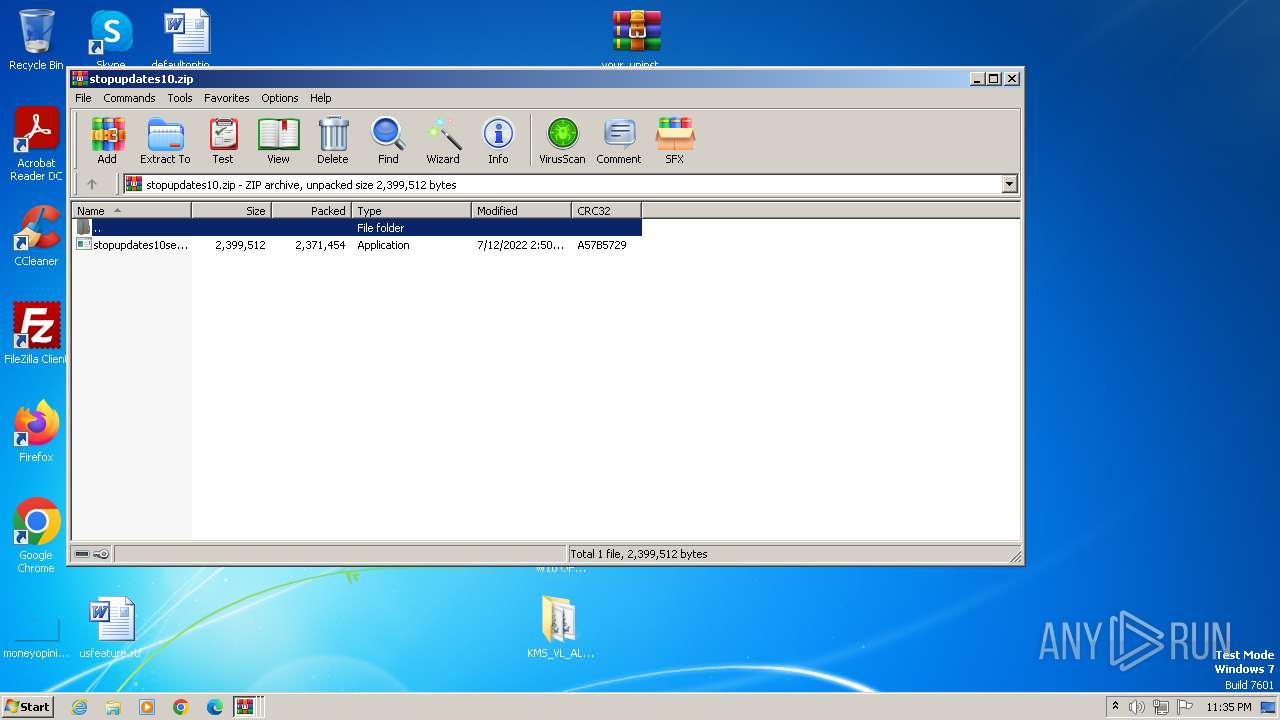
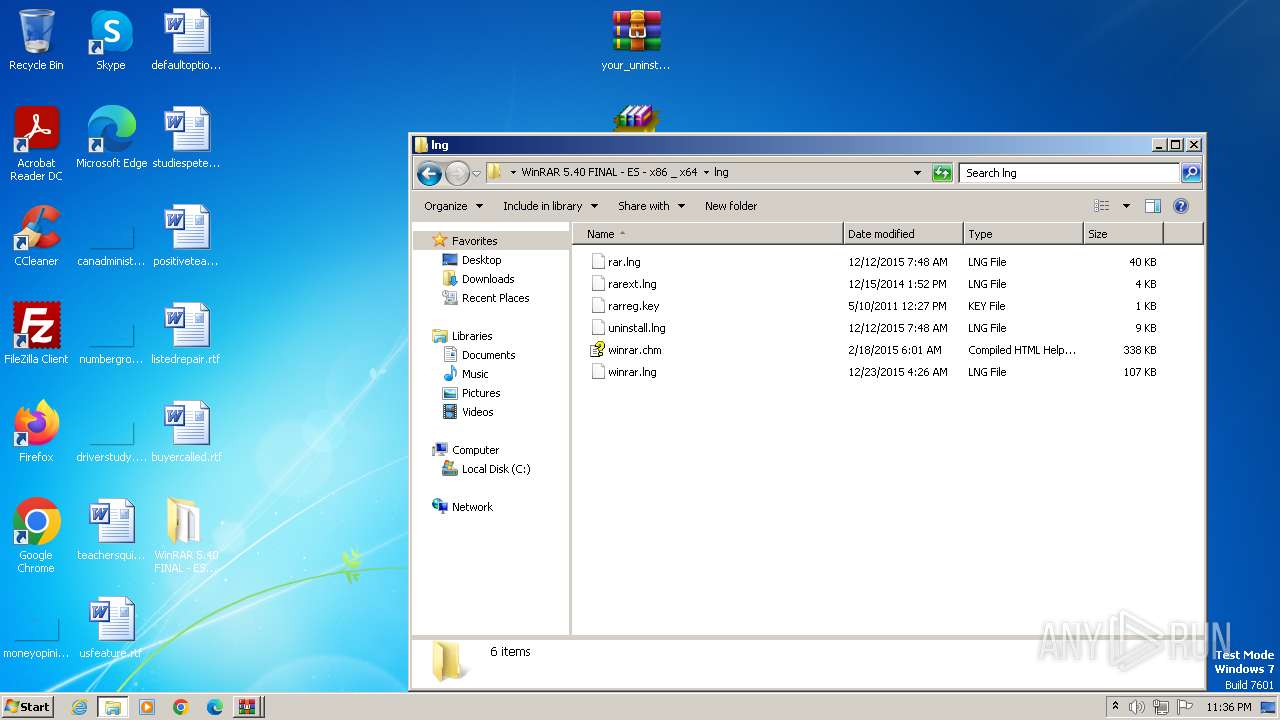
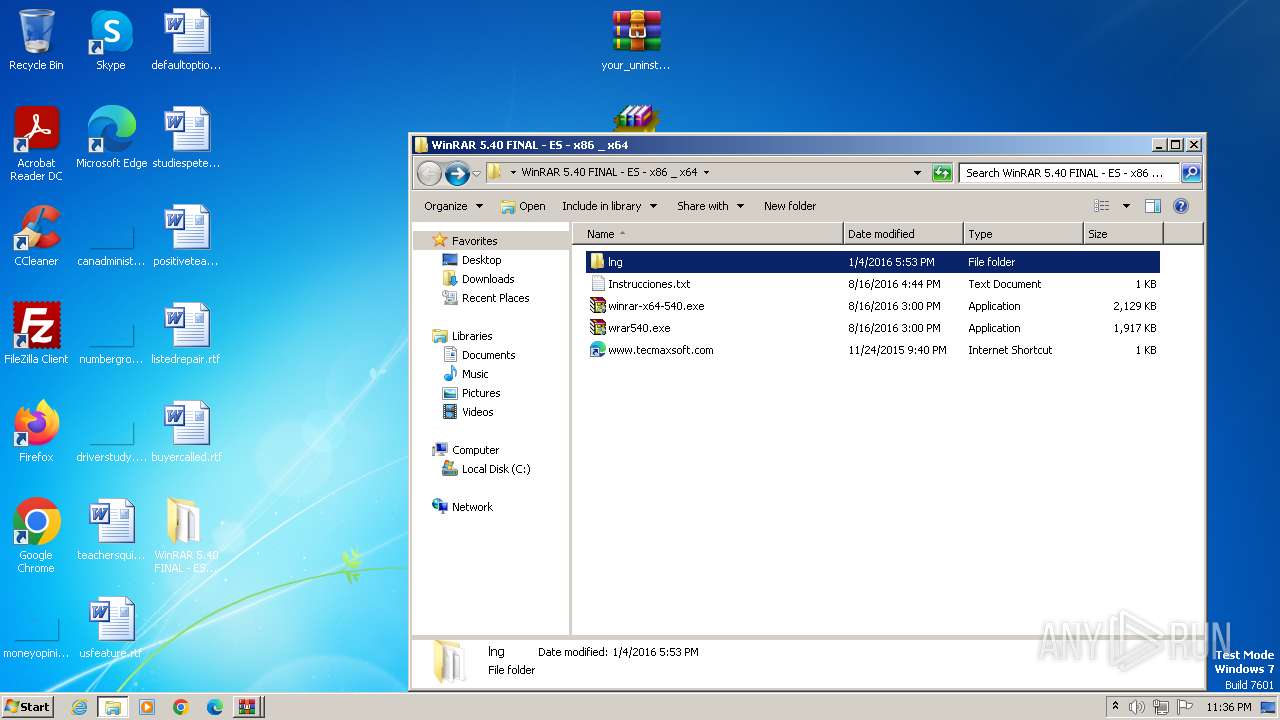
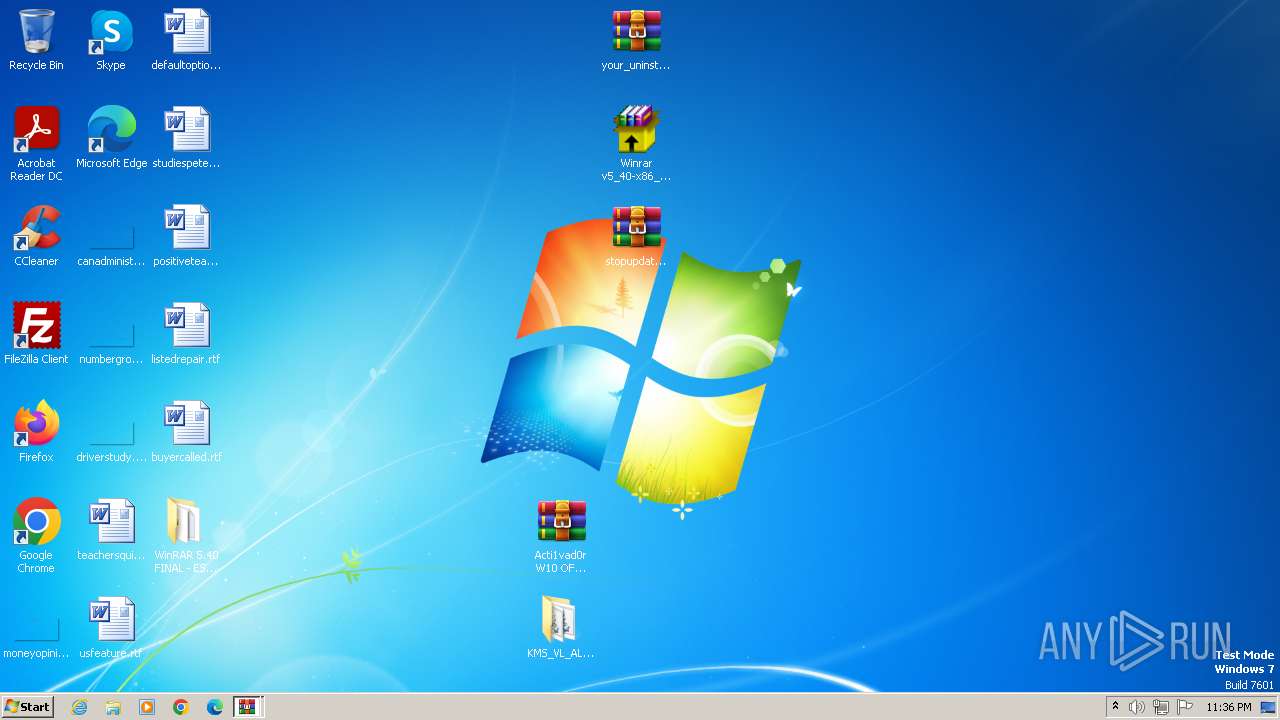
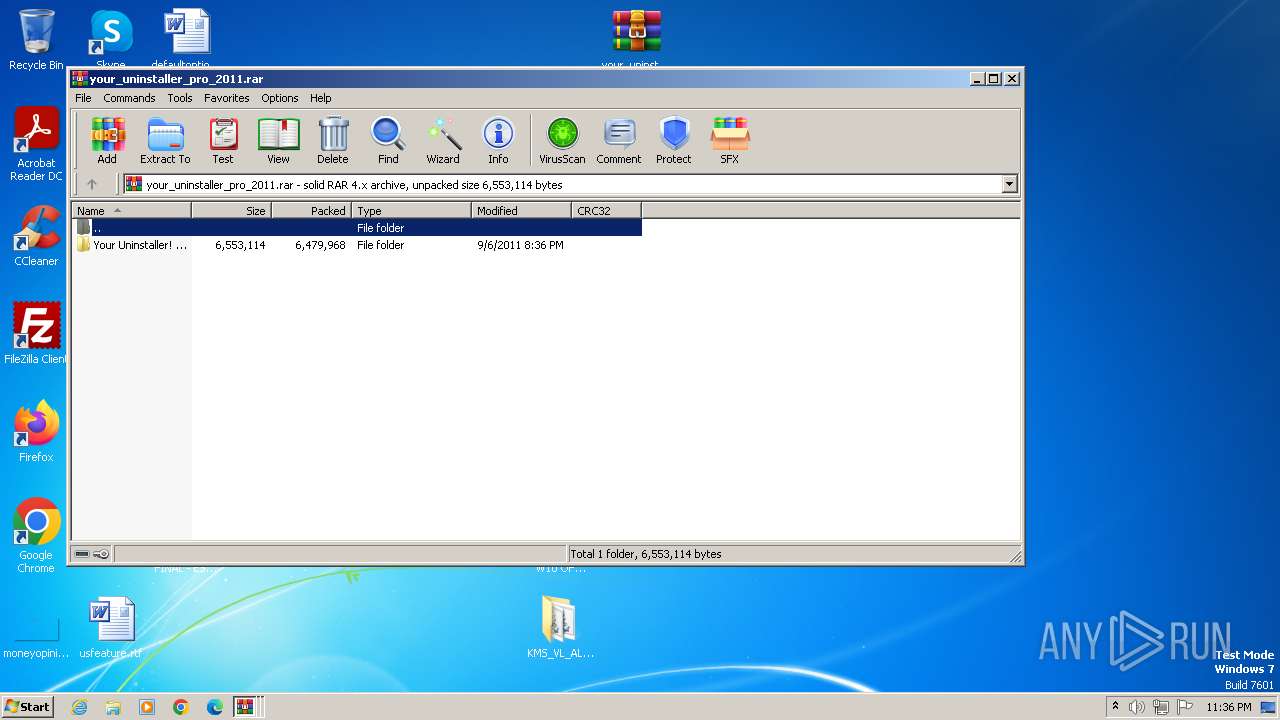
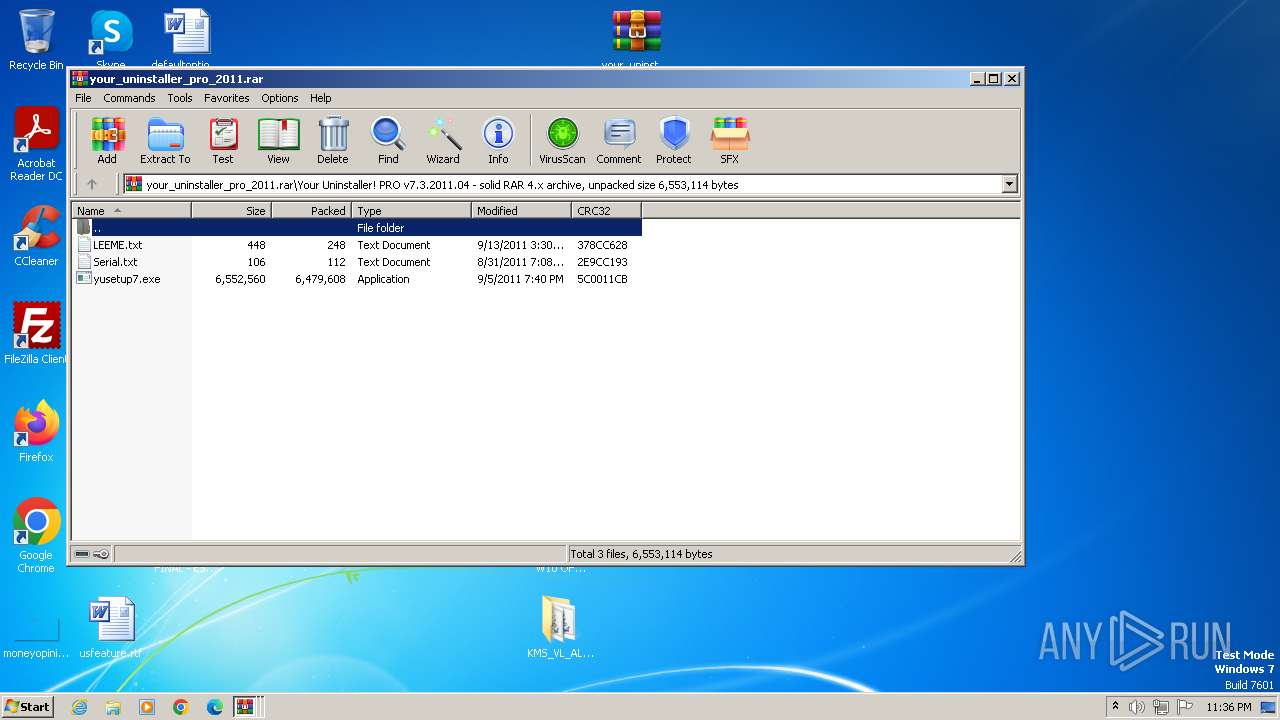
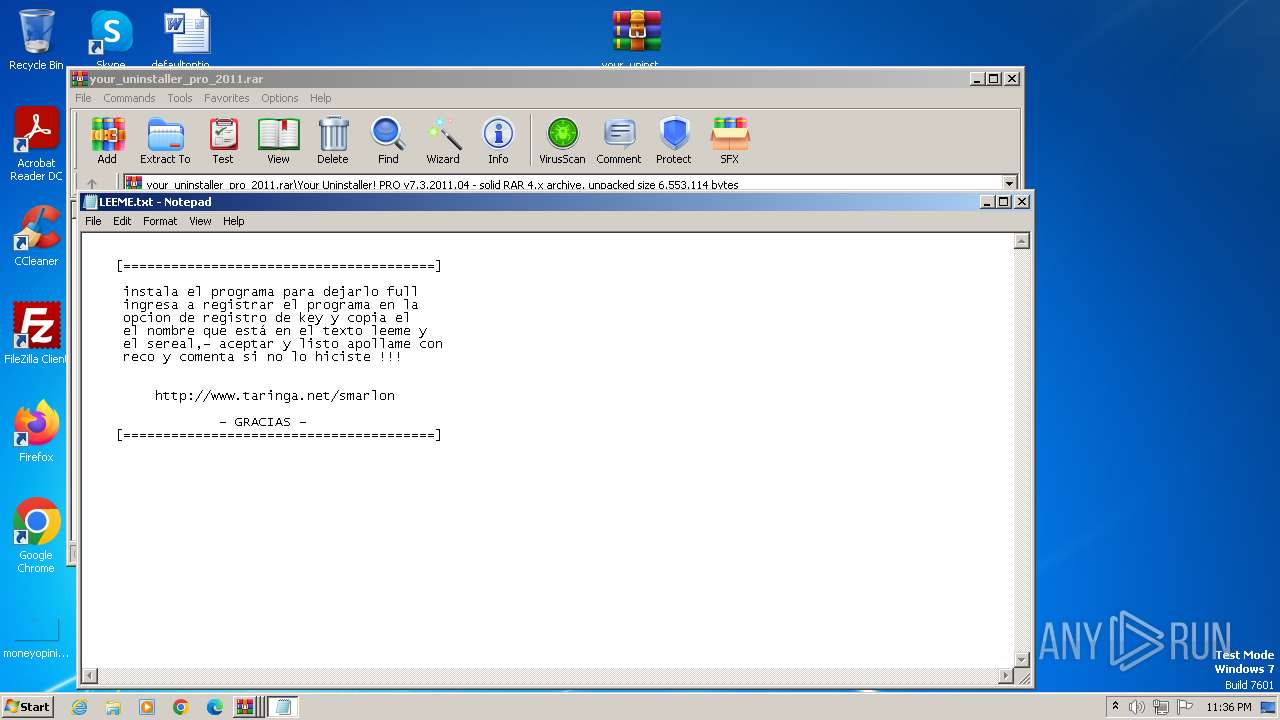
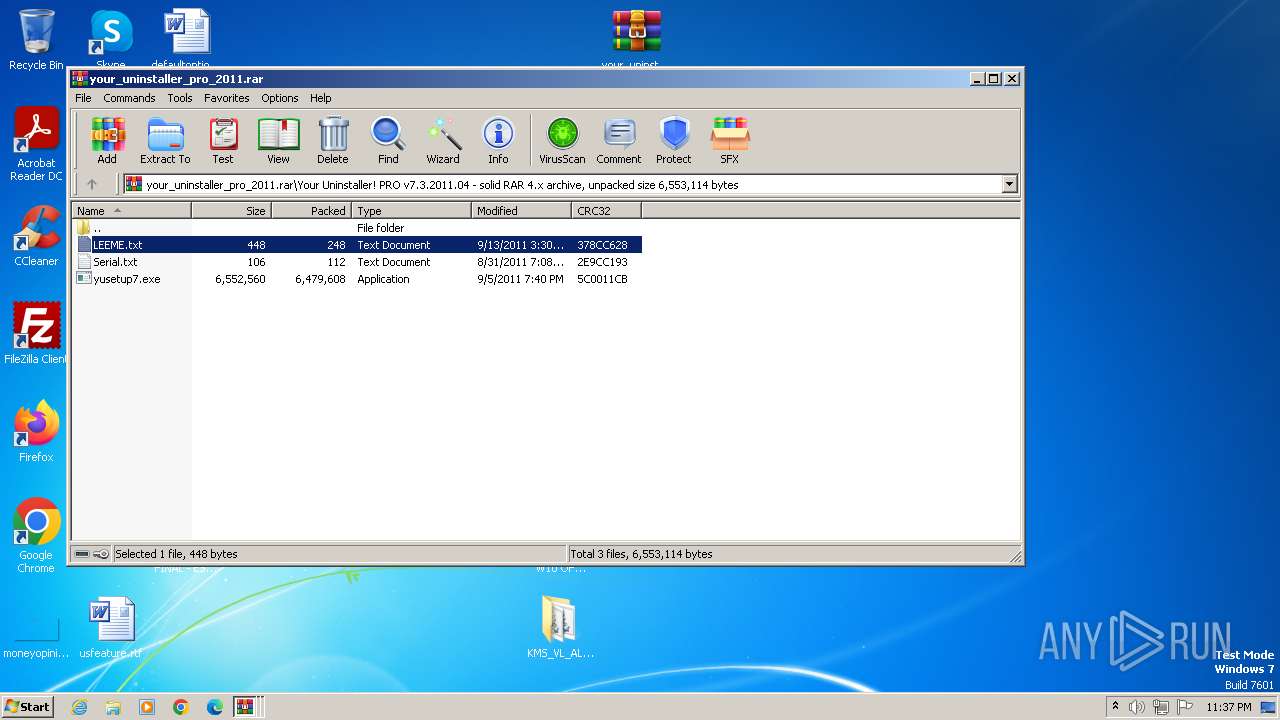
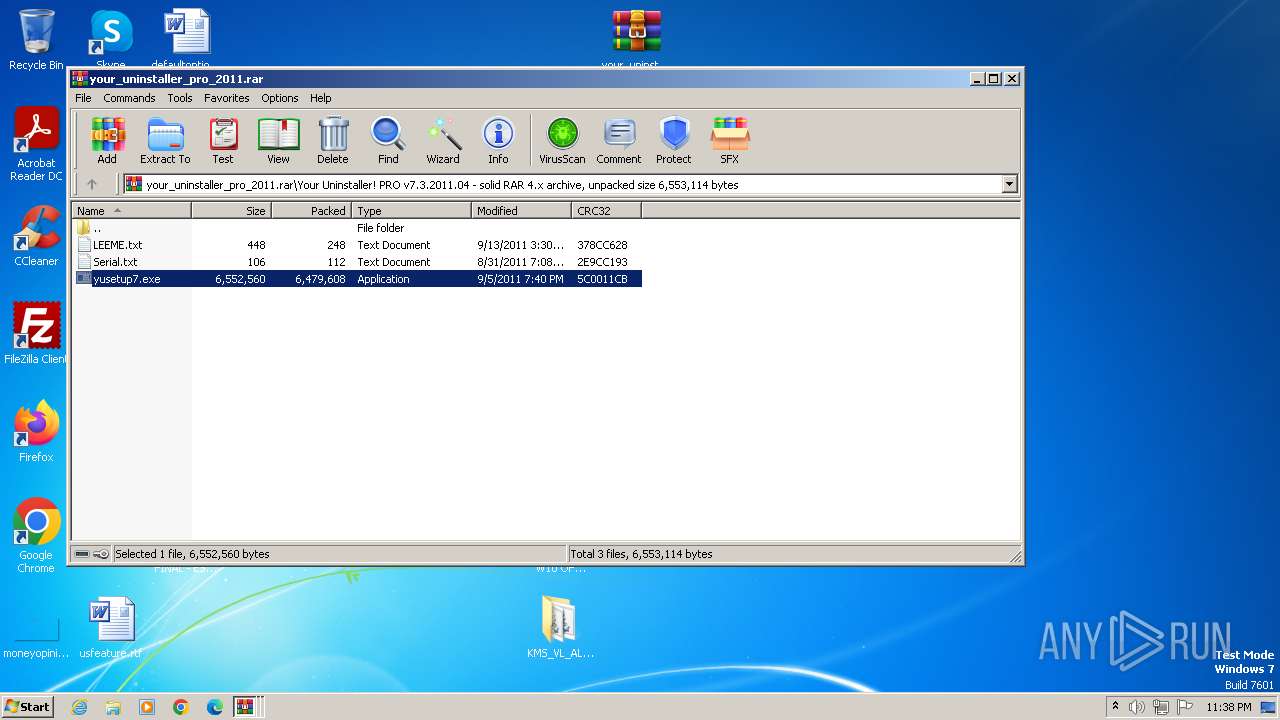
| File name: | Fix pc-lap.zip.zip |
| Full analysis: | https://app.any.run/tasks/775af82f-23c1-4f60-8de5-8ed4c2f04cb2 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2023, 22:33:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C01AA6D95CB41E05A8CF798E92EF181C |
| SHA1: | 276B0F08FA3DCFD56720FBACBDD0DD28C0A49BB1 |
| SHA256: | 348CB8392D41FE66A72482CA97AF770083888864BC592CDE9BA689F0D7ABDEA6 |
| SSDEEP: | 196608:WnfuVTP+abTGte15kRwCpXo/wQzHHJGqyp2W7hvdeQjF+JjywzFhv4kvFmzcQMFR:WnfuVTXAgSRZoTMF2WV1LjFaHYkIPt6x |
MALICIOUS
Application was dropped or rewritten from another process
- Winrar v5_40-x86_x64.exe (PID: 1176)
- yusetup7.exe (PID: 3664)
- yusetup7.exe (PID: 2540)
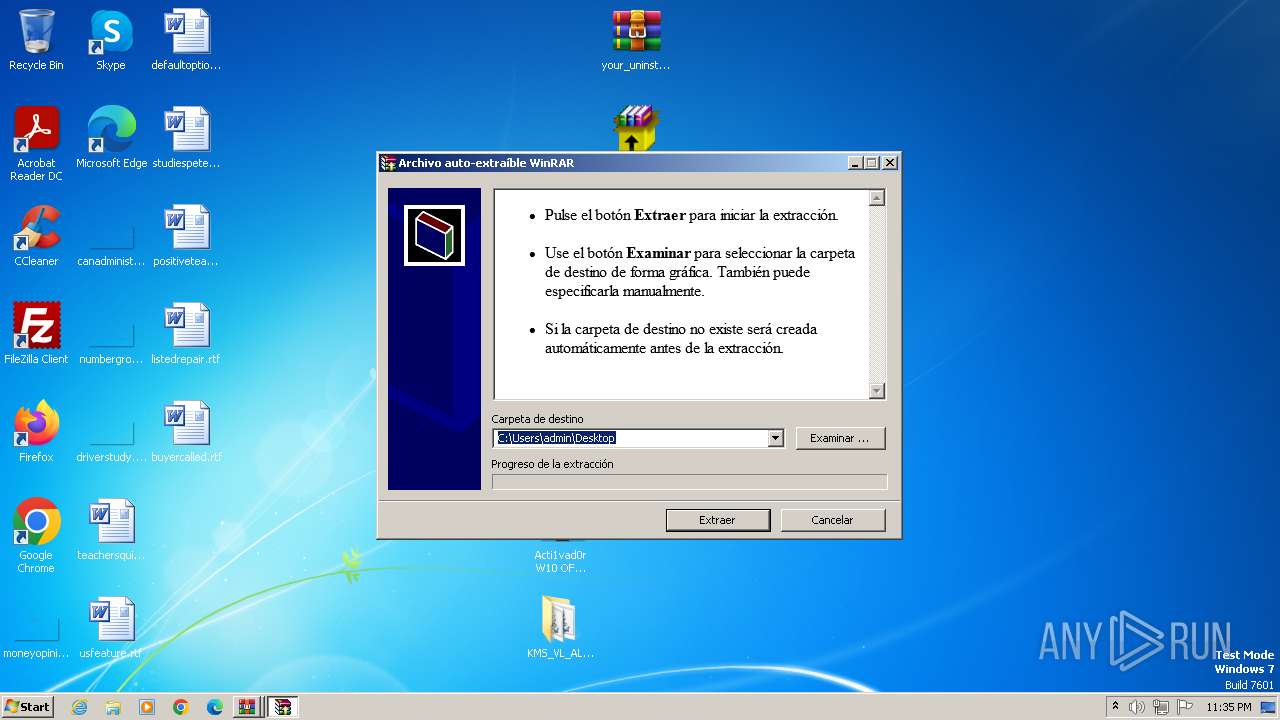
Drops the executable file immediately after the start
- yusetup7.exe (PID: 3664)
- Winrar v5_40-x86_x64.exe (PID: 1176)
- yusetup7.tmp (PID: 2888)
- yusetup7.exe (PID: 2540)
Loads dropped or rewritten executable
- yusetup7.tmp (PID: 2888)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2752)
- cmd.exe (PID: 3976)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3976)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3976)
Reads the Internet Settings
- Winrar v5_40-x86_x64.exe (PID: 1176)
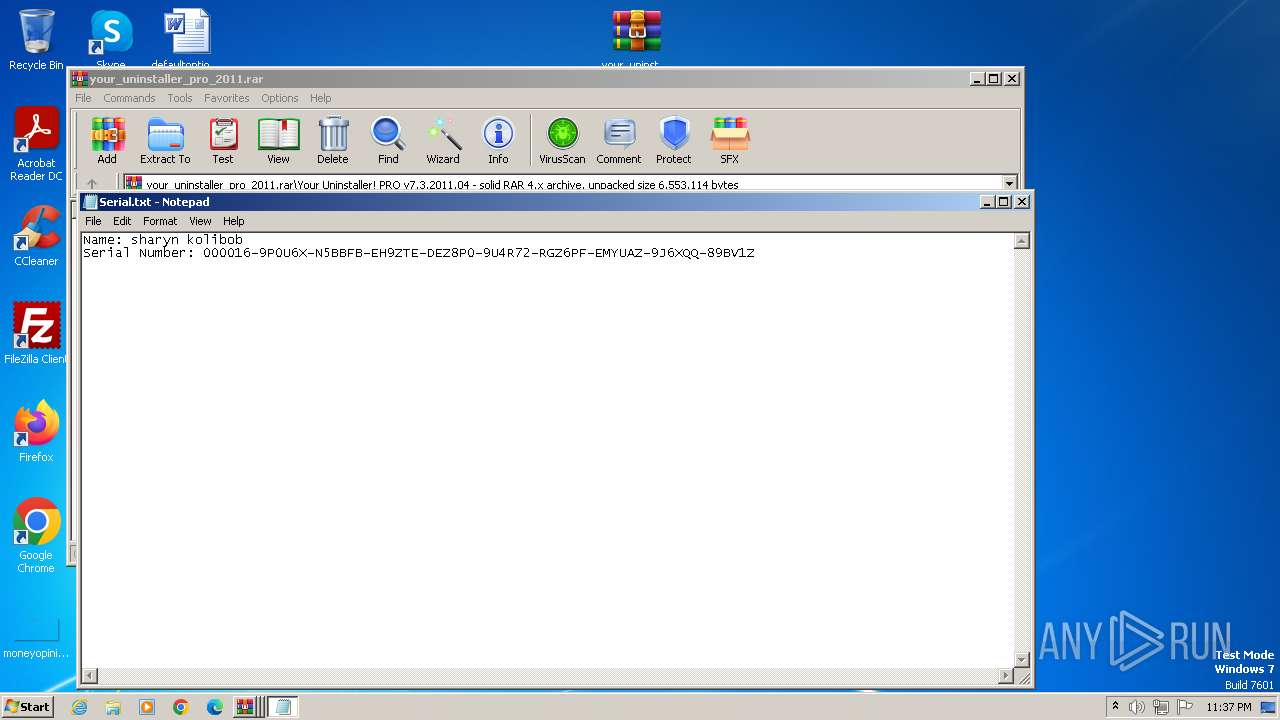
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2440)
Reads Microsoft Outlook installation path
- Winrar v5_40-x86_x64.exe (PID: 1176)
Reads Internet Explorer settings
- Winrar v5_40-x86_x64.exe (PID: 1176)
Reads the Windows owner or organization settings
- yusetup7.tmp (PID: 2888)
Process drops legitimate windows executable
- yusetup7.tmp (PID: 2888)
INFO
Manual execution by a user
- msedge.exe (PID: 2844)
- cmd.exe (PID: 3976)
- WinRAR.exe (PID: 3568)
- WinRAR.exe (PID: 3716)
- Winrar v5_40-x86_x64.exe (PID: 1176)
- notepad.exe (PID: 2568)
- WinRAR.exe (PID: 2440)
- wmpnscfg.exe (PID: 3416)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4060)
- WinRAR.exe (PID: 2440)
Application launched itself
- msedge.exe (PID: 2844)
Reads the computer name
- Winrar v5_40-x86_x64.exe (PID: 1176)
- yusetup7.tmp (PID: 3876)
- yusetup7.tmp (PID: 2888)
- cc.exe (PID: 2516)
- wmpnscfg.exe (PID: 3416)
Checks supported languages
- Winrar v5_40-x86_x64.exe (PID: 1176)
- yusetup7.exe (PID: 3664)
- yusetup7.tmp (PID: 3876)
- yusetup7.exe (PID: 2540)
- cc.exe (PID: 2516)
- wmpnscfg.exe (PID: 3416)
- yusetup7.tmp (PID: 2888)
Create files in a temporary directory
- yusetup7.exe (PID: 3664)
- yusetup7.exe (PID: 2540)
- yusetup7.tmp (PID: 2888)
Checks proxy server information
- Winrar v5_40-x86_x64.exe (PID: 1176)
Reads the machine GUID from the registry
- Winrar v5_40-x86_x64.exe (PID: 1176)
- wmpnscfg.exe (PID: 3416)
Application was dropped or rewritten from another process
- yusetup7.tmp (PID: 3876)
- cc.exe (PID: 2516)
- yusetup7.tmp (PID: 2888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Fix pc-lap.zip |
|---|---|
| ZipUncompressedSize: | 13509850 |
| ZipCompressedSize: | 13511221 |
| ZipCRC: | 0xb3df2218 |
| ZipModifyDate: | 2023:10:19 22:21:42 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
82
Monitored processes
35
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3576 --field-trial-handle=1296,i,14396177915336481163,17552431446446489026,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 820 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 1176 | "C:\Users\admin\Desktop\Winrar v5_40-x86_x64.exe" | C:\Users\admin\Desktop\Winrar v5_40-x86_x64.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1336 | cmd /v:on /c echo(^!param^! | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1188 --field-trial-handle=1296,i,14396177915336481163,17552431446446489026,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3592 --field-trial-handle=1296,i,14396177915336481163,17552431446446489026,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1740 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3640 --field-trial-handle=1296,i,14396177915336481163,17552431446446489026,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1840 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3532 --field-trial-handle=1296,i,14396177915336481163,17552431446446489026,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2196 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3840 --field-trial-handle=1296,i,14396177915336481163,17552431446446489026,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2212 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2440.41047\Serial.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 723
Read events
8 585
Write events
132
Delete events
6
Modification events
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
20
Suspicious files
68
Text files
61
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2752.20353\Fix pc-lap.zip | compressed | |
MD5:36460C8240DDACF944CA82C24159D1AB | SHA256:5F3E55C7B57B353B9C2C311339FDF616779ABC0D78D1D26441AF31175CBA5E9B | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\Acti1vad0r W10 OFFICE.rar | compressed | |
MD5:0CDA81B6DF6E2551FD023138B8128CD0 | SHA256:C8C3D16BC4ECB3E5A2E94FEAB4322FB5DF3530D58EE0BCC9F80EB772489A776A | |||
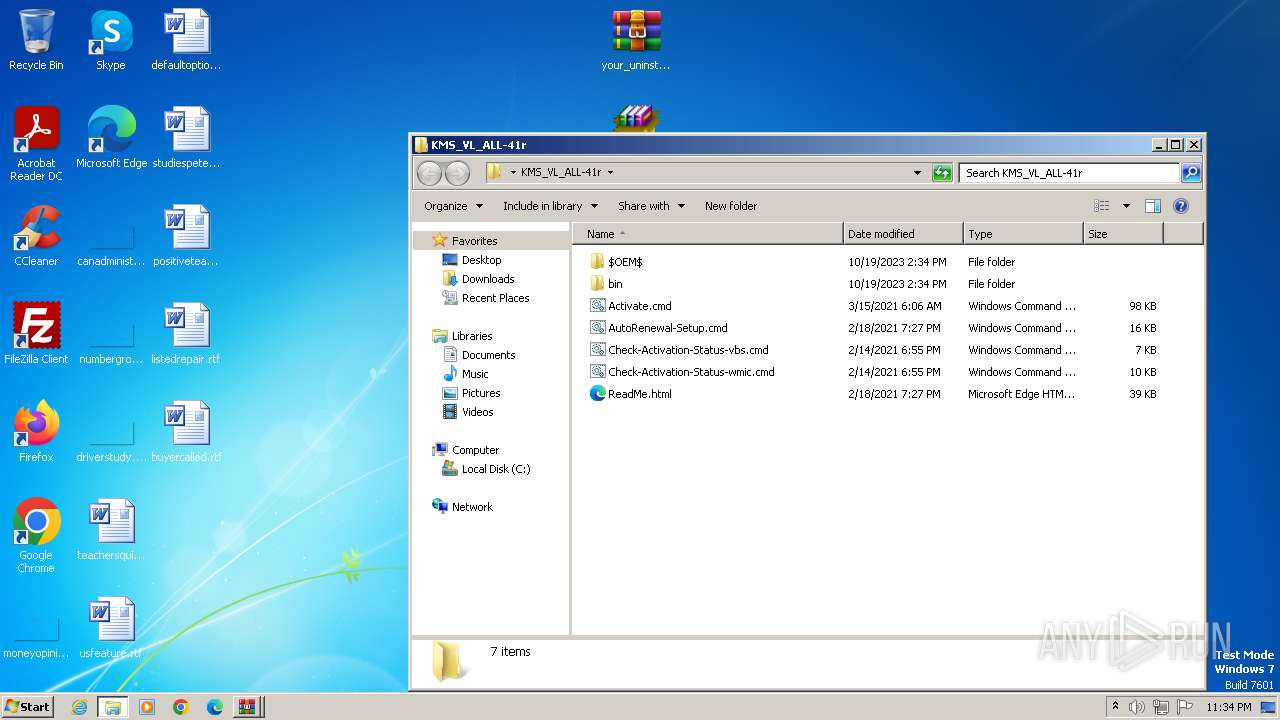
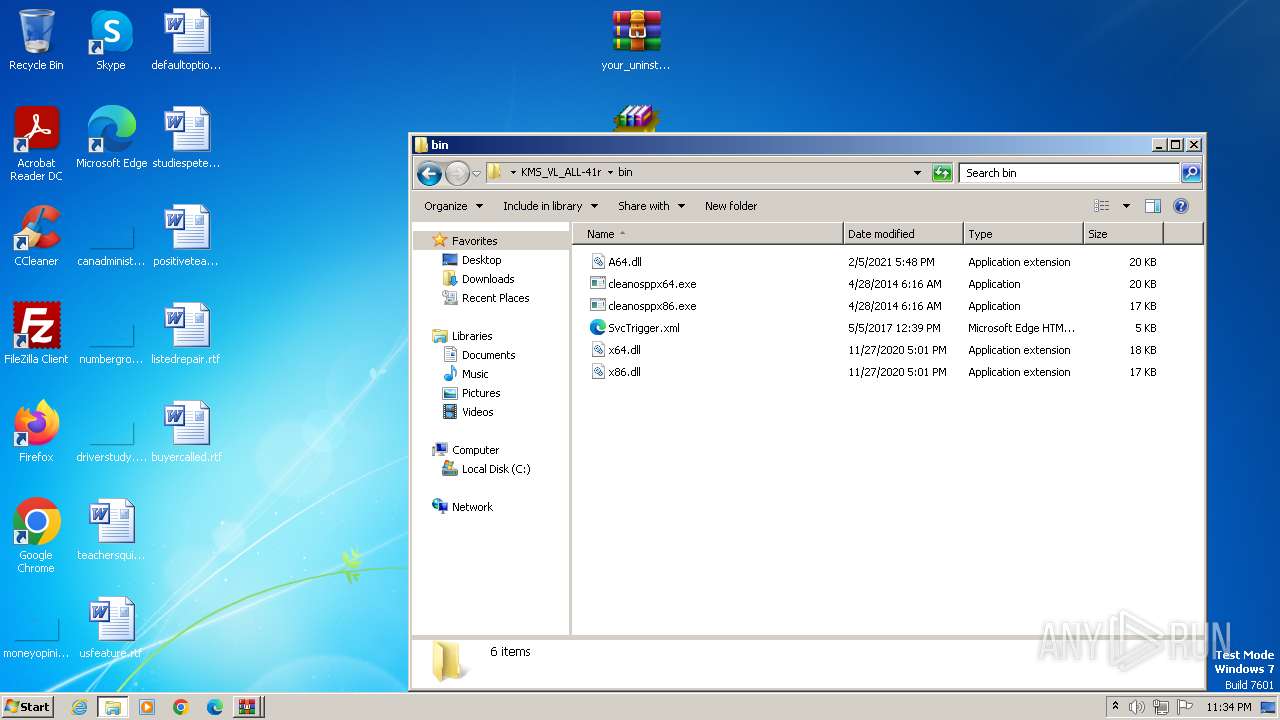
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\KMS_VL_ALL-41r\$OEM$\$\Setup\Scripts\bin\A64.dll | executable | |
MD5:92C55495ECDC742B434D6B28827873A3 | SHA256:719FC76A343B9F07A10CB61FF620E5C56A41CD8A9305C5573DA52560E2F7A9C5 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\your_uninstaller_pro_2011.rar | — | |
MD5:— | SHA256:— | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\KMS_VL_ALL-41r\$OEM$\$\Setup\Scripts\bin\cleanosppx86.exe | executable | |
MD5:5FD363D52D04AC200CD24F3BCC903200 | SHA256:3FDEFE2AD092A9A7FE0EDF0AC4DC2DE7E5B9CE6A0804F6511C06564194966CF9 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\KMS_VL_ALL-41r\$OEM$\$\Setup\Scripts\bin\x86.dll | executable | |
MD5:6453AFE61FCD25F72EFB86202365F84D | SHA256:499EAE9A096054DF68B9F2CFFF37FB0B9393FBDA085E05A01DC25BC5EE011020 | |||
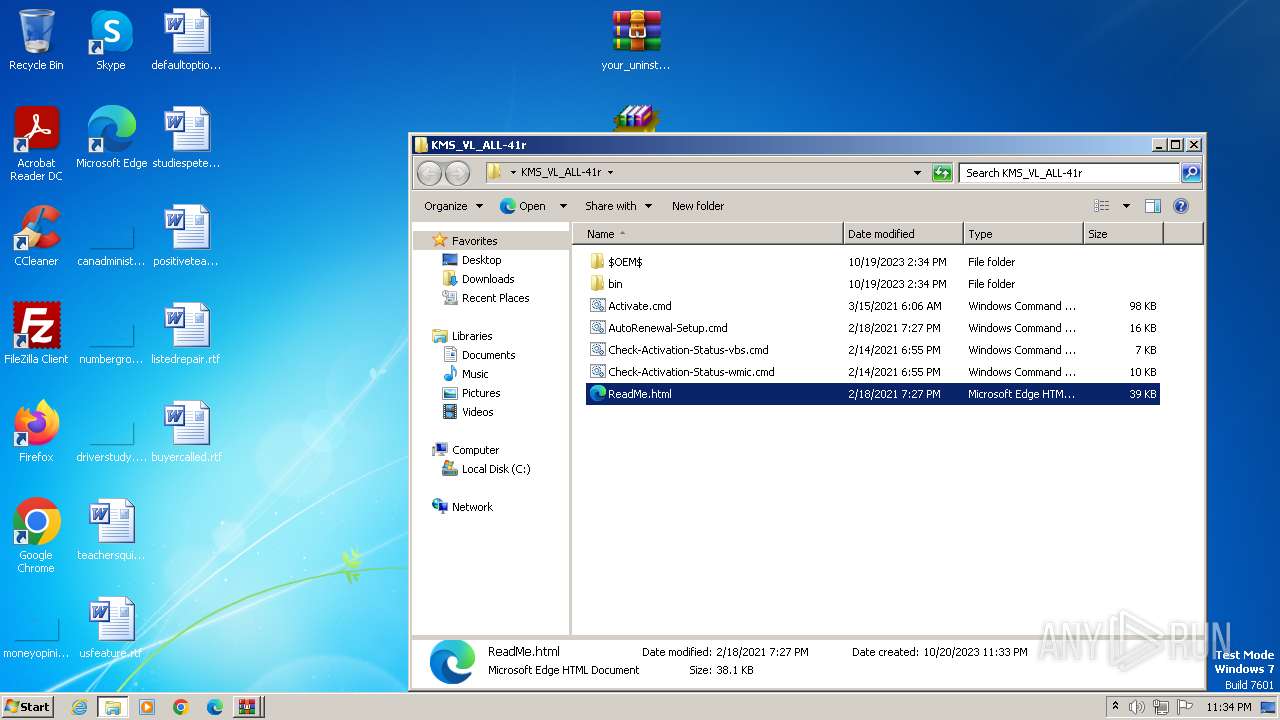
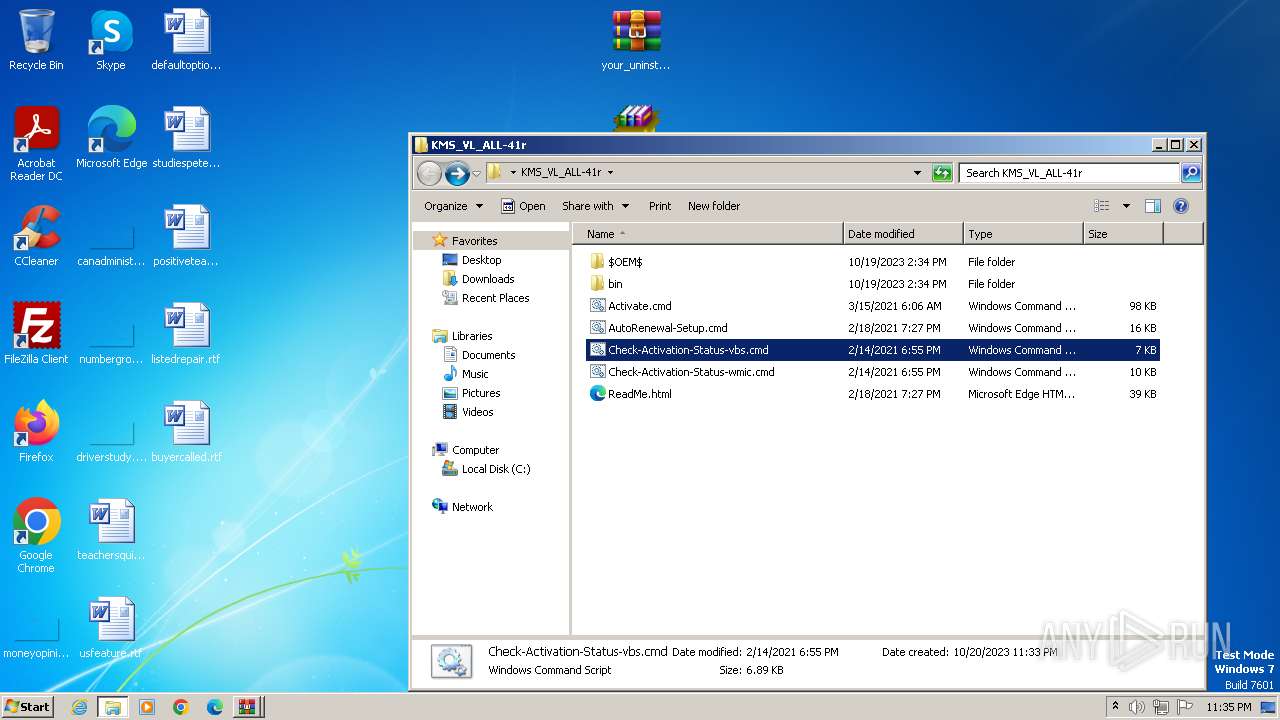
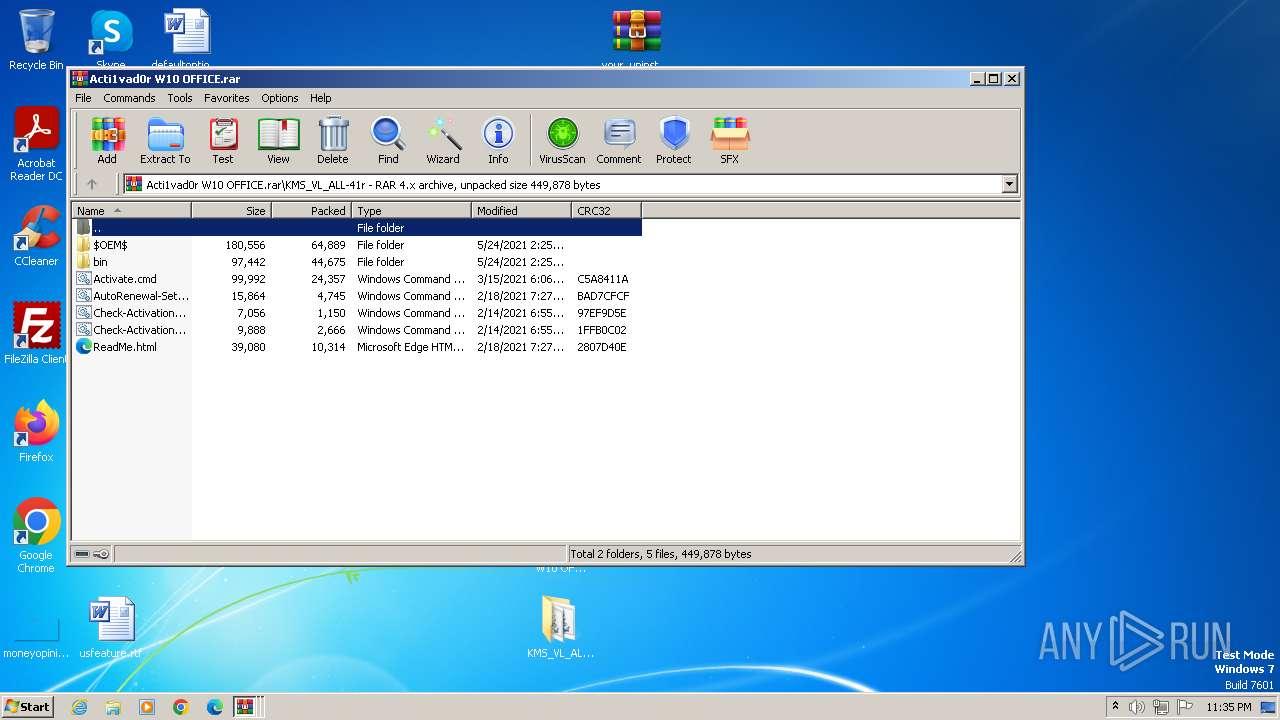
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\KMS_VL_ALL-41r\Check-Activation-Status-vbs.cmd | text | |
MD5:4D91E466DC03CFD8470A0D17407072E0 | SHA256:6385BEAE02565A8BDF16195B5630EC2A5C62F524F051C0E65E32924B60DBBACB | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\KMS_VL_ALL-41r\bin\cleanosppx64.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\KMS_VL_ALL-41r\bin\A64.dll | executable | |
MD5:92C55495ECDC742B434D6B28827873A3 | SHA256:719FC76A343B9F07A10CB61FF620E5C56A41CD8A9305C5573DA52560E2F7A9C5 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4060.21855\Fix pc-lap\KMS_VL_ALL-41r\bin\cleanosppx86.exe | executable | |
MD5:5FD363D52D04AC200CD24F3BCC903200 | SHA256:3FDEFE2AD092A9A7FE0EDF0AC4DC2DE7E5B9CE6A0804F6511C06564194966CF9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
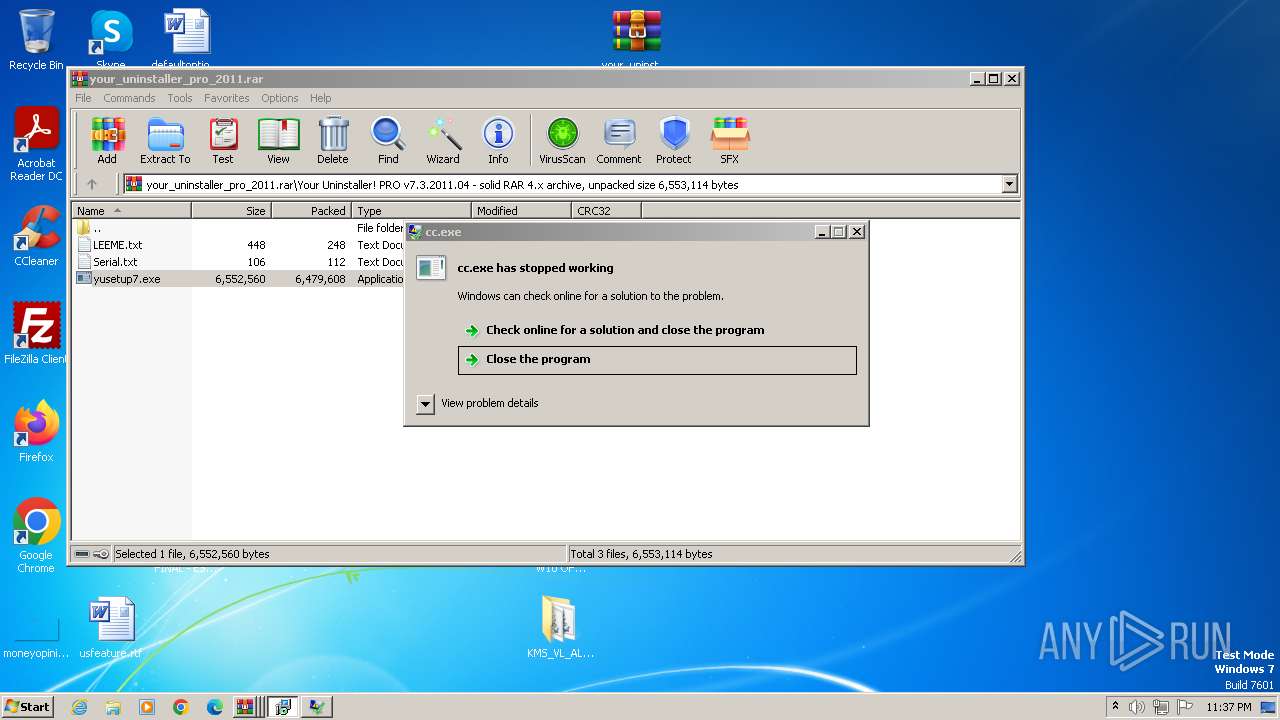
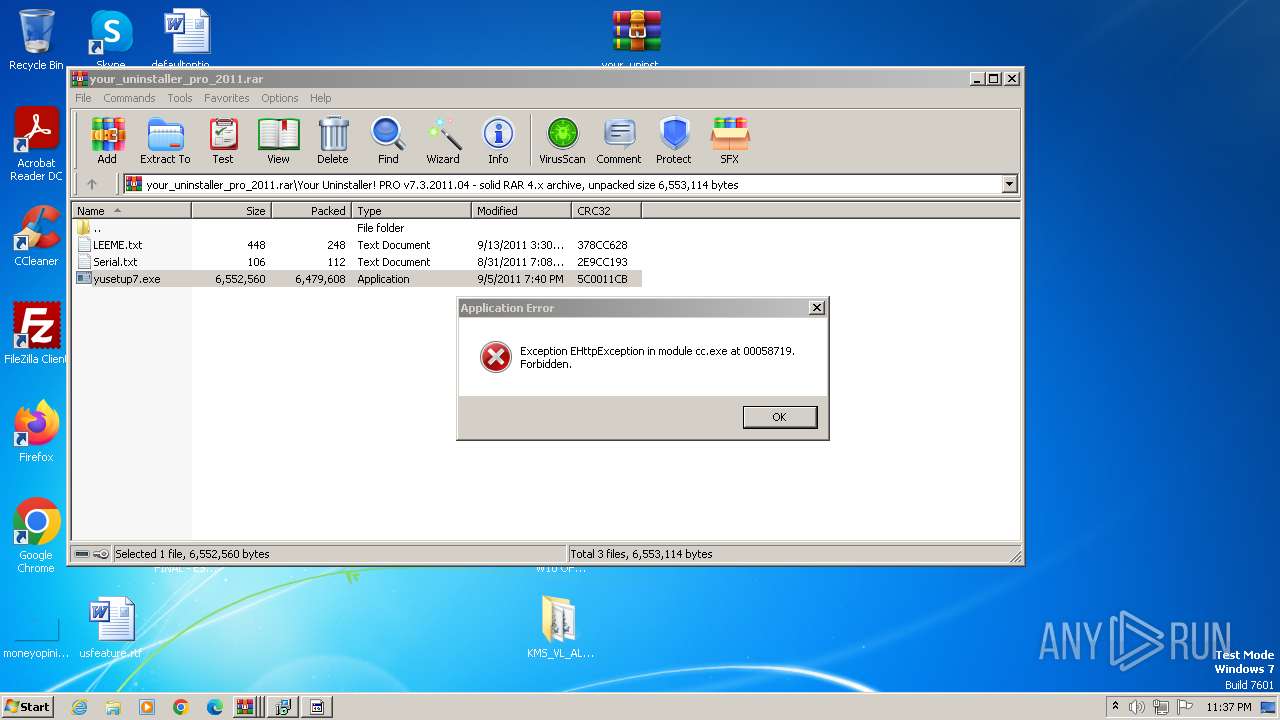
2516 | cc.exe | GET | 403 | 172.67.172.233:80 | http://www.ursoftware.com/sc/getcountry.php | unknown | text | 16 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3404 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2844 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3404 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3404 | msedge.exe | 13.107.21.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3404 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3404 | msedge.exe | 67.27.159.252:443 | msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com | LEVEL3 | US | unknown |
2844 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
3404 | msedge.exe | 40.74.98.195:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | JP | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |
www.ursoftware.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2516 | cc.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Mozilla/3.0 (compatible)) |