| File name: | setup-vghd_zbmu3afflckhq.exe |
| Full analysis: | https://app.any.run/tasks/8fba7774-829d-4419-899d-858a8f526863 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 18:44:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive, 8 sections |
| MD5: | EC6CF82D0DB1436C0F924FAF125626DB |
| SHA1: | E13A86E7D768B62E5D02C375924348D920DED28B |
| SHA256: | 348C7E64C03E774A23107664123845B4D0C58704A4BB3AFF8F013D0592C38AB9 |
| SSDEEP: | 196608:fKPaV9FHLuMB3MyWQnJ1QfixFQZy1M/uv+AAeyVI:f2a1CMB+QnJqfix2yC6+AA4 |
MALICIOUS
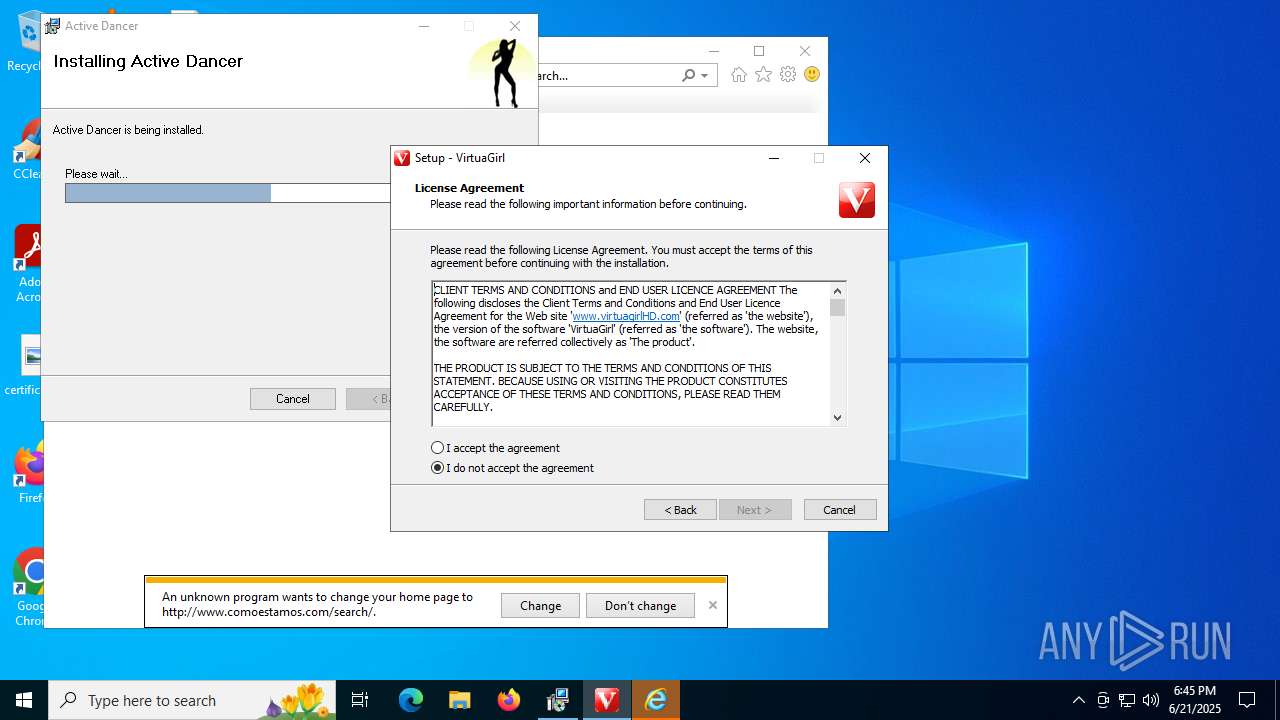
Executing a file with an untrusted certificate
- setup-vgirl-us_6aaQdW85sAW.exe (PID: 2276)
Create files in the Startup directory
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
SUSPICIOUS
Reads security settings of Internet Explorer
- setup-vghd_zbmu3afflckhq.exe (PID: 2228)
- setup.exe (PID: 6636)
- MSIBF2B.tmp (PID: 416)
- vghd.exe (PID: 7528)
Executable content was dropped or overwritten
- setup-vghd_zbmu3afflckhq.exe (PID: 2228)
- MSIBDC3.tmp (PID: 3108)
- MSIBDC3.tmp (PID: 5244)
- MSIBF2B.tmp (PID: 416)
- setup-vgirl-us_6aaQdW85sAW.exe (PID: 2276)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Executes as Windows Service
- VSSVC.exe (PID: 4032)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6292)
- MSIBDC3.tmp (PID: 3108)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Changes the title of the Internet Explorer window
- MSIBDC3.tmp (PID: 3108)
- iexplore.exe (PID: 6148)
Process drops legitimate windows executable
- MSIBDC3.tmp (PID: 3108)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Changes the Home page of Internet Explorer
- MSIBDC3.tmp (PID: 3108)
Creates/Modifies COM task schedule object
- MSIBF2B.tmp (PID: 416)
Creates a software uninstall entry
- MSIBF2B.tmp (PID: 416)
The process drops C-runtime libraries
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Potential Corporate Privacy Violation
- iexplore.exe (PID: 504)
- VirtuaGirl_Downloader.exe (PID: 7568)
Reads the BIOS version
- vghd.exe (PID: 7528)
INFO
Create files in a temporary directory
- setup-vghd_zbmu3afflckhq.exe (PID: 2228)
- setup.exe (PID: 6636)
- MSIBDC3.tmp (PID: 5244)
- MSIBDC3.tmp (PID: 3108)
- setup-vgirl-us_6aaQdW85sAW.exe (PID: 2276)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Creates files or folders in the user directory
- setup-vghd_zbmu3afflckhq.exe (PID: 2228)
- msiexec.exe (PID: 6292)
- MSIBDC3.tmp (PID: 3108)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
- vghd.exe (PID: 7528)
- VirtuaGirl_Downloader.exe (PID: 7568)
Reads the computer name
- setup-vghd_zbmu3afflckhq.exe (PID: 2228)
- setup.exe (PID: 6636)
- msiexec.exe (PID: 6292)
- MSIBDC3.tmp (PID: 3108)
- MSIBF2B.tmp (PID: 416)
- RunFromToolbar.exe (PID: 7140)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
- ielowutil.exe (PID: 7116)
- identity_helper.exe (PID: 7972)
- VirtuaGirl_Downloader.exe (PID: 7568)
- vghd.exe (PID: 7528)
Checks supported languages
- setup-vghd_zbmu3afflckhq.exe (PID: 2228)
- setup.exe (PID: 6636)
- msiexec.exe (PID: 6292)
- MSIBDC3.tmp (PID: 5244)
- MSIBDC3.tmp (PID: 3108)
- MSIBF2B.tmp (PID: 416)
- setup-vgirl-us_6aaQdW85sAW.exe (PID: 2276)
- ielowutil.exe (PID: 7116)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
- RunFromToolbar.exe (PID: 7140)
- identity_helper.exe (PID: 7972)
- vghd.exe (PID: 7528)
- VirtuaGirl_Downloader.exe (PID: 7568)
The sample compiled with english language support
- setup-vghd_zbmu3afflckhq.exe (PID: 2228)
- MSIBDC3.tmp (PID: 3108)
- MSIBF2B.tmp (PID: 416)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Process checks computer location settings
- setup-vghd_zbmu3afflckhq.exe (PID: 2228)
- setup.exe (PID: 6636)
Manages system restore points
- SrTasks.exe (PID: 4576)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6292)
Starts application with an unusual extension
- msiexec.exe (PID: 6292)
Creates files in the program directory
- MSIBF2B.tmp (PID: 416)
Creates a software uninstall entry
- MSIBDC3.tmp (PID: 3108)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
- msiexec.exe (PID: 6292)
Application launched itself
- msedge.exe (PID: 3108)
- msedge.exe (PID: 7060)
Manual execution by a user
- msedge.exe (PID: 3108)
Detects InnoSetup installer (YARA)
- setup-vgirl-us_6aaQdW85sAW.exe (PID: 2276)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Compiled with Borland Delphi (YARA)
- setup-vgirl-us_6aaQdW85sAW.exe (PID: 2276)
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Launching a file from the Startup directory
- setup-vgirl-us_6aaQdW85sAW.tmp (PID: 2032)
Reads Environment values
- identity_helper.exe (PID: 7972)
Checks proxy server information
- slui.exe (PID: 7724)
Reads the software policy settings
- slui.exe (PID: 7724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 9216 |
| InitializedDataSize: | 186368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3274 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.7.0 |
| ProductVersionNumber: | 5.0.7.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
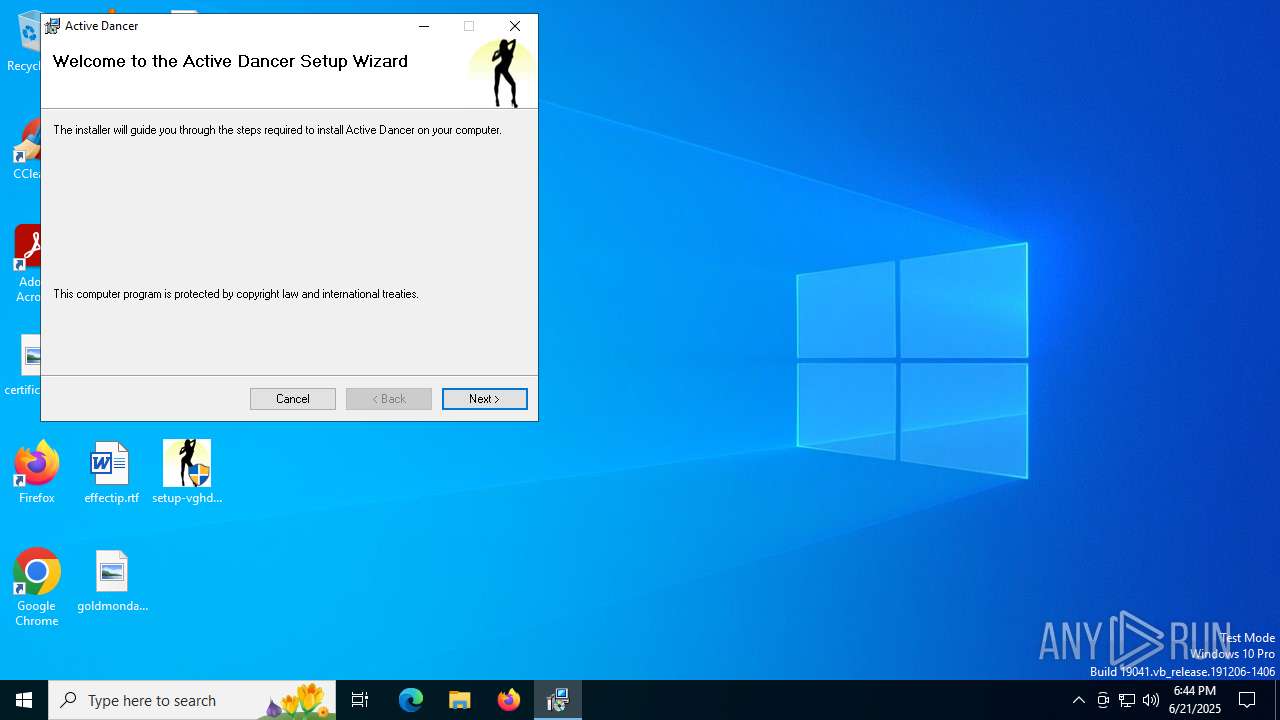
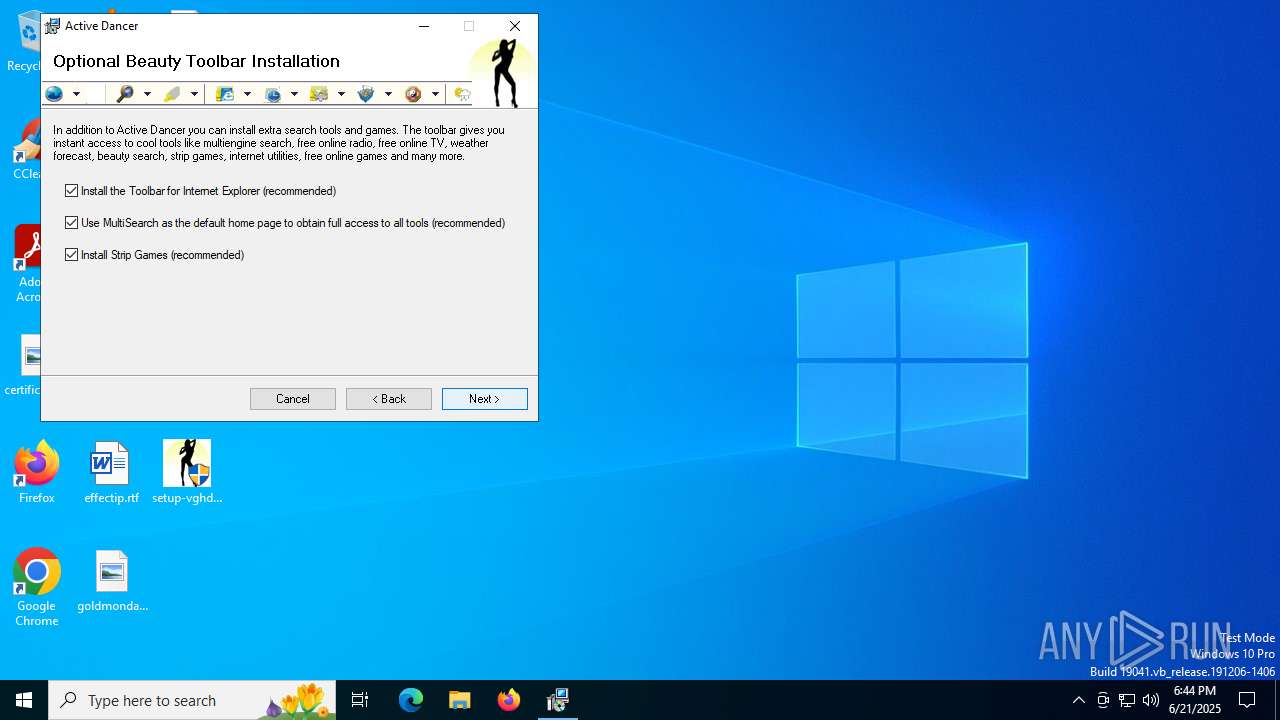
| FileDescription: | Self-Extracting Package for Active Dancer Installer |
| FileVersion: | 5.0.7.0 |
| LegalCopyright: | Copyright by ActiveDancer.com |
| ProductName: | Active Dancer Installer |
| ProductVersion: | 5.0.7.0 |
| Web: | http://www.activedancer.com |
| CompanyName: | ActiveDancer.com, activedancer@activedancer.com |
| Comments: | Packed with Paquet Builder, see http://www.gdgsoft.com |
Total processes
187
Monitored processes
48
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\WINDOWS\Installer\MSIBF2B.tmp" /S | C:\Windows\Installer\MSIBF2B.tmp | msiexec.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 472 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x1d4,0x28c,0x290,0x284,0x298,0x7ffc426df208,0x7ffc426df214,0x7ffc426df220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 472 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3644,i,8961980609921655912,11096085446473894426,262144 --variations-seed-version --mojo-platform-channel-handle=3732 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 504 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:6148 CREDAT:17410 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | "C:\Windows\SysWOW64\msiexec.exe" -I "C:\Users\admin\AppData\Local\Active Dancer\EN\ActiveDancer.msi" | C:\Windows\SysWOW64\msiexec.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1816 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2580,i,8961980609921655912,11096085446473894426,262144 --variations-seed-version --mojo-platform-channel-handle=2716 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2032 | "C:\Users\admin\AppData\Local\Temp\is-M6CA1.tmp\setup-vgirl-us_6aaQdW85sAW.tmp" /SL5="$B032A,14160617,137728,C:\Program Files (x86)\Active Dancer\EN\setup-vgirl-us_6aaQdW85sAW.exe" | C:\Users\admin\AppData\Local\Temp\is-M6CA1.tmp\setup-vgirl-us_6aaQdW85sAW.tmp | setup-vgirl-us_6aaQdW85sAW.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=4772,i,8961980609921655912,11096085446473894426,262144 --variations-seed-version --mojo-platform-channel-handle=4748 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2236,i,9527511679381865517,17327851319998531892,262144 --variations-seed-version --mojo-platform-channel-handle=2368 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2228 | "C:\Users\admin\Desktop\setup-vghd_zbmu3afflckhq.exe" | C:\Users\admin\Desktop\setup-vghd_zbmu3afflckhq.exe | explorer.exe | ||||||||||||
User: admin Company: ActiveDancer.com, activedancer@activedancer.com Integrity Level: HIGH Description: Self-Extracting Package for Active Dancer Installer Exit code: 0 Version: 5.0.7.0 Modules
| |||||||||||||||
Total events
31 105
Read events
30 329
Write events
752
Delete events
24
Modification events
| (PID) Process: | (6636) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (1204) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (1204) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (1204) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (1204) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000705FA290DCE2DB0194180000BC000000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000705FA290DCE2DB0194180000BC000000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000087FA8090DCE2DB0194180000BC000000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000087FA8090DCE2DB0194180000BC000000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6292) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000E0C2A490DCE2DB0194180000BC000000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
50
Suspicious files
168
Text files
448
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2228 | setup-vghd_zbmu3afflckhq.exe | C:\Users\admin\AppData\Local\Active Dancer\EN\ActiveDancer.msi | — | |
MD5:— | SHA256:— | |||
| 6292 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6292 | msiexec.exe | C:\Windows\Installer\17b95d.msi | — | |
MD5:— | SHA256:— | |||
| 2228 | setup-vghd_zbmu3afflckhq.exe | C:\Users\admin\AppData\Local\Active Dancer\EN\setup.exe | executable | |
MD5:2AE4D7613E0FD933D7EC2ED6F2829D8D | SHA256:A4754E72A6B18C8430F81C66DA841AC10BF0D59667E9D6D584A198D5840F8103 | |||
| 6636 | setup.exe | C:\Users\admin\AppData\Local\Temp\VSD7AEC.tmp\install.log | text | |
MD5:0175C1A643DEC6D713C39C75E3020D1A | SHA256:FC23454F90ECFFEAD0CDC2B765FA73449E938E54F4D07C842AB1906BEB9CA8B0 | |||
| 2228 | setup-vghd_zbmu3afflckhq.exe | C:\Users\admin\AppData\Local\Temp\PB77FE.tmp | executable | |
MD5:042ED449D4534E013466B7714DCD9EA8 | SHA256:63D513BD3BEAA48B5EB96847F0426C28A3352A21F31DDB19FF151E3258B095F5 | |||
| 6292 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:FFEA01E5A3CB8211046339993E081AFA | SHA256:D3EA07C9772DC8D93E995D550A21F67B4FB34F78BDBA24E6A343CE296F323D3B | |||
| 6292 | msiexec.exe | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngen.log | text | |
MD5:12B14F7AF6460D774BC22EE04D2D98B5 | SHA256:6E94F6A19984179955E1D8D29B8F76FB1186071157629D6F133BF558B4F415ED | |||
| 6292 | msiexec.exe | C:\Windows\Installer\MSIBB80.tmp | binary | |
MD5:86E2DD7E308C47D1F8C9A8D74933C48F | SHA256:3BBB969C155E6BA3155C36926ED9D9B0F444FC8C367EC17FD17D005D476B656F | |||
| 6292 | msiexec.exe | C:\Program Files (x86)\Active Dancer\EN\Search.url | binary | |
MD5:A6BE55C239739D70FF4BD232DA20B33B | SHA256:F37B67B8EA937CF5FA02396855BF30481DE7860DA77983ECC73CEFA7A952B13C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
132
TCP/UDP connections
137
DNS requests
92
Threats
32
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 23.9 Kb | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.2:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.22:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.comoestamos.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
504 | iexplore.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 4. |
— | — | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 4. |
— | — | Misc activity | INSTALLER [ANY.RUN] VCSoapClient Installer HTTP POST Request (UA) |
— | — | Misc activity | INSTALLER [ANY.RUN] VCSoapClient Installer HTTP POST Request (UA) |
— | — | Misc activity | INSTALLER [ANY.RUN] VCSoapClient Installer HTTP POST Request (UA) |
— | — | Misc activity | INSTALLER [ANY.RUN] VCSoapClient Installer HTTP POST Request (UA) |
— | — | Misc activity | INSTALLER [ANY.RUN] VCSoapClient Installer HTTP POST Request (UA) |
— | — | Misc activity | INSTALLER [ANY.RUN] VCSoapClient Installer HTTP POST Request (UA) |
— | — | Misc activity | INSTALLER [ANY.RUN] VCSoapClient Installer HTTP POST Request (UA) |
— | — | Misc activity | INSTALLER [ANY.RUN] VCSoapClient Installer HTTP POST Request (UA) |
Process | Message |
|---|---|
VirtuaGirl_Downloader.exe | VGHD Connected
|
vghd.exe | Sent to DLM: |
VirtuaGirl_Downloader.exe | VGHD Connected
|
vghd.exe | directaskserver %%DOWNLOAD_GETSCRIPT%%?command=report&code=DISPLAY_REGISTER&key=0060795801595856 |
vghd.exe | |
vghd.exe | directaskserver error |
vghd.exe | Received from DLM: |
vghd.exe | |
vghd.exe | , |
vghd.exe | 0 |