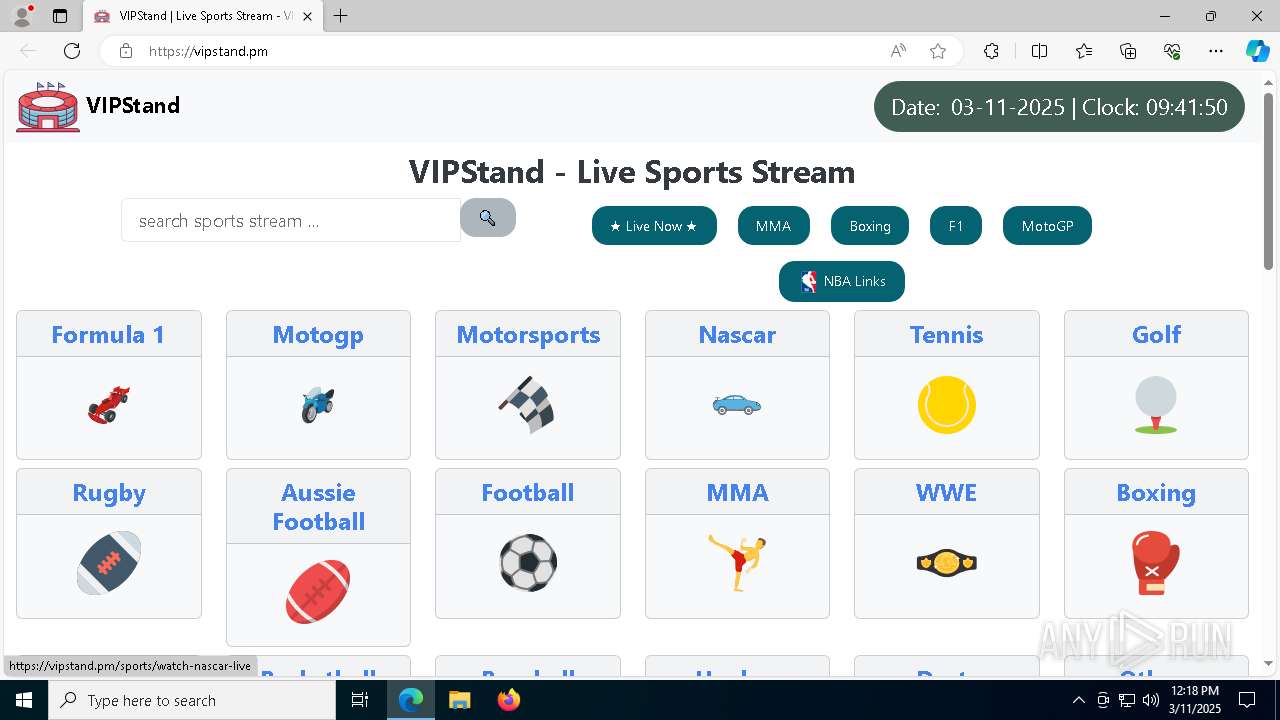
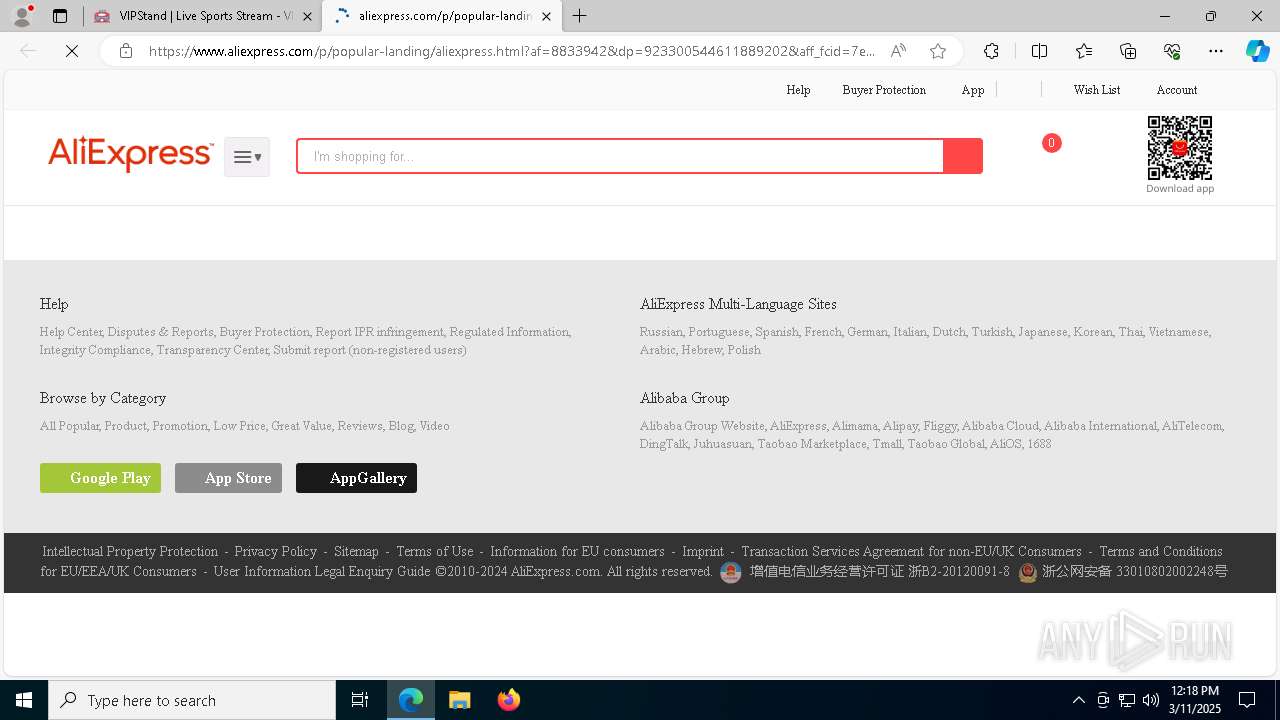
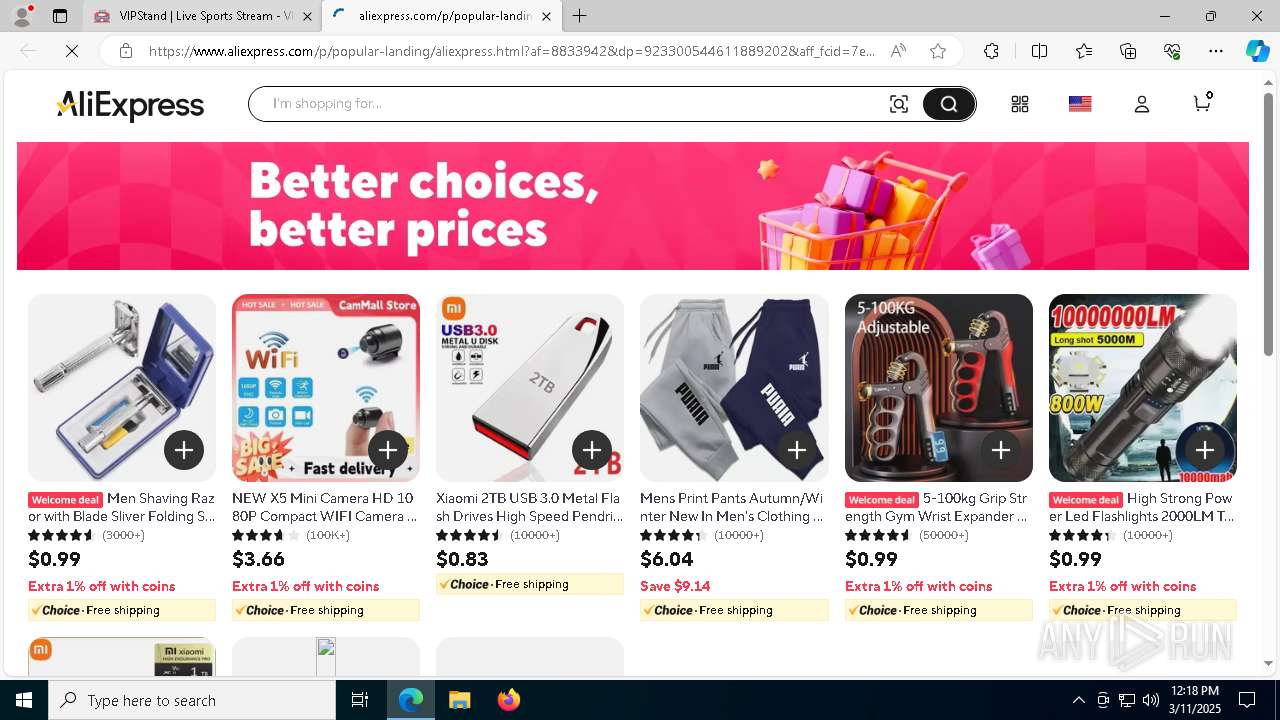
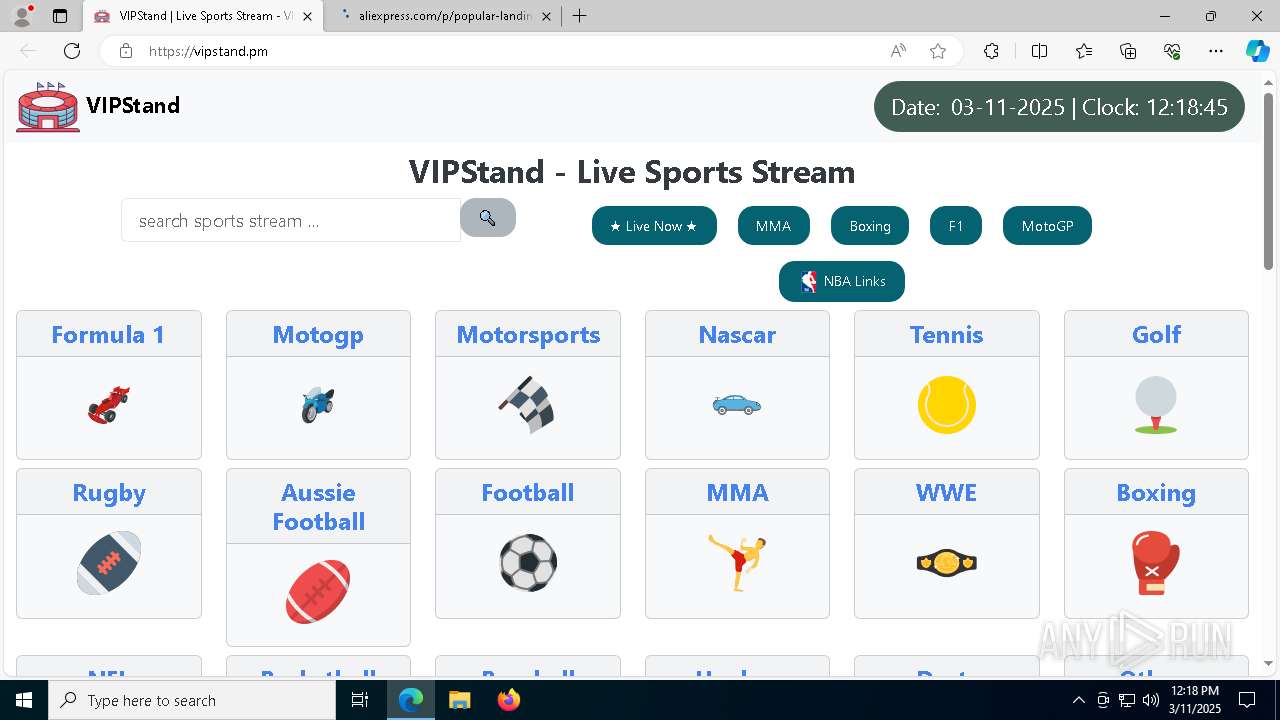
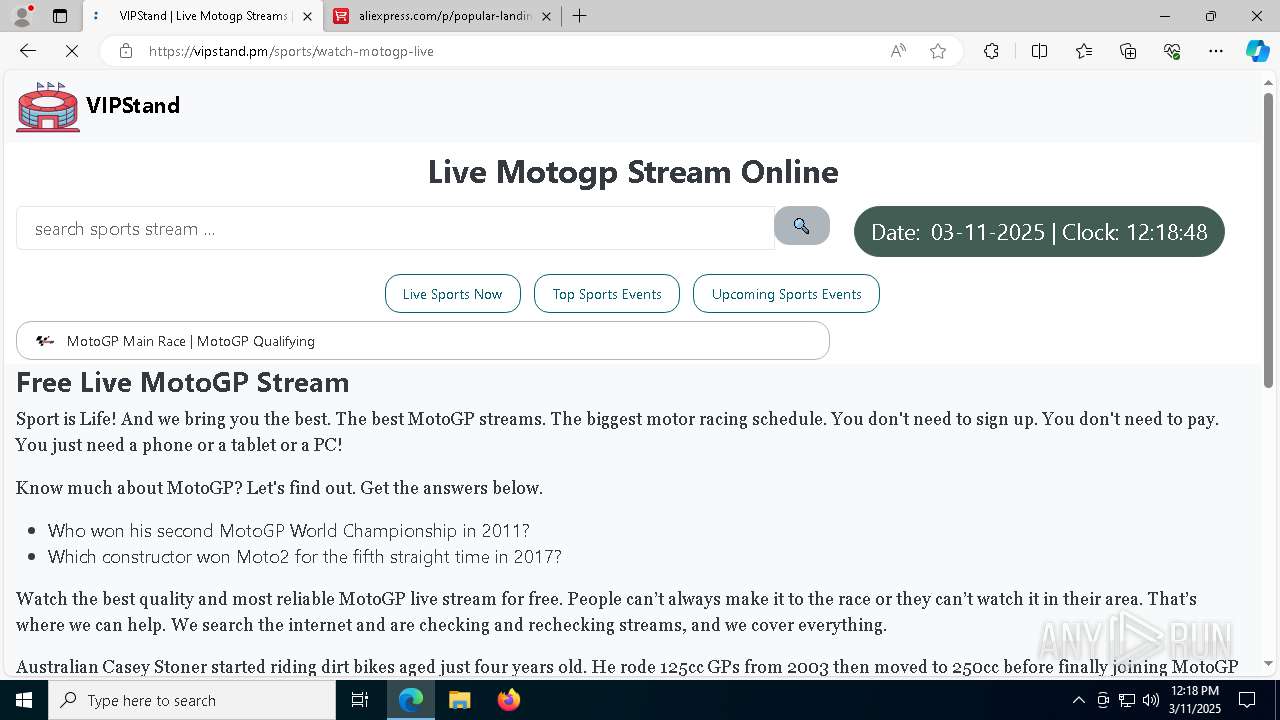
| URL: | vipstand.pm |
| Full analysis: | https://app.any.run/tasks/12e8bfe7-b8d7-43b4-93df-29bb2fb4fd27 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2025, 12:18:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A5F135170159CCD405161C5A0E429BE0 |
| SHA1: | C6706AB050F71C95C6FB14DC6D90817891506C09 |
| SHA256: | 346AD78FAF2E987B2CD22BEAE6511BD1975ABB1F662153FFDA1ADAE9171251F8 |
| SSDEEP: | 3:wRhI:wI |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 7320)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
164
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 7320 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2600 --field-trial-handle=2432,i,11785546014293489461,11355236345891825122,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
14
Suspicious files
75
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\SCT Auditing Pending Reports~RF10d65d.TMP | ini | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00025e | compressed | |
MD5:8A9100969E14F56B7C2B946944438329 | SHA256:0A1644723F3B7E001DDF1A7EE022BB2DD0B27090CF6ACAEE838DD5261D93A269 | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00025f | compressed | |
MD5:FB1061220C2144952D67860F11018EFC | SHA256:C257D976D39590D49AE5B80FBBA02DC3CA08ECD3968AF6E1AC0E22D6B346604C | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000261 | compressed | |
MD5:AAD899862B8B7BD33917CF0505F6B6A3 | SHA256:993746BB91032F0A52C2A9A8928B96814EE1C8ED892A6305728F97EEE6839E04 | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000266 | binary | |
MD5:8D9AB49176380D2967B36190F8AD366E | SHA256:E1618439ABE701725A962F8726C11CFE2803BBB0558577E297A635A36CCE29E3 | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000262 | compressed | |
MD5:FAD2ED44B35AB3A5E4D2A990F1637843 | SHA256:ECA0FF2F0F86733DC805F112663B401905717BEC984F31ED8B79209C404267BB | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000264 | text | |
MD5:8991C3EC80EC8FBC41382A55679E3911 | SHA256:F55BACD4A20FEF96F5C736A912D1947BE85C268DF18003395E511C1E860E8800 | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000263 | compressed | |
MD5:7EC12016F38CF18DFB5C8AC2895F7128 | SHA256:0A729E1C96BBF350D02F69959675B2162EA0364D85493BDF9C8BEC6F8FFD6CDC | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000265 | text | |
MD5:7A34E86CFFCC0729065E008DEC047122 | SHA256:9A3C60ADB187E0941AE91DBDC2A5470A47A19048104C6FBCD13BF79E4FA4FC90 | |||
| 7320 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000258 | binary | |
MD5:6C796BDF81B5F428DED509238A05BE86 | SHA256:53E0405891888B476395DFAFCB5B6CCDC337E7018612C854876C46B85365361F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
192
DNS requests
202
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 45.178.6.109:443 | vipstand.pm | — | — | unknown |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 13.107.253.44:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 45.178.6.109:80 | vipstand.pm | SWISS GLOBAL SERVICES S.A.S | CO | unknown |
— | — | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
vipstand.pm |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
— | — | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
— | — | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
— | — | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
— | — | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7320 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .pacifics .sbs) |
7320 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .pacifics .sbs) |
7320 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .pacifics .sbs) |
7320 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .pacifics .sbs) |
— | — | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |