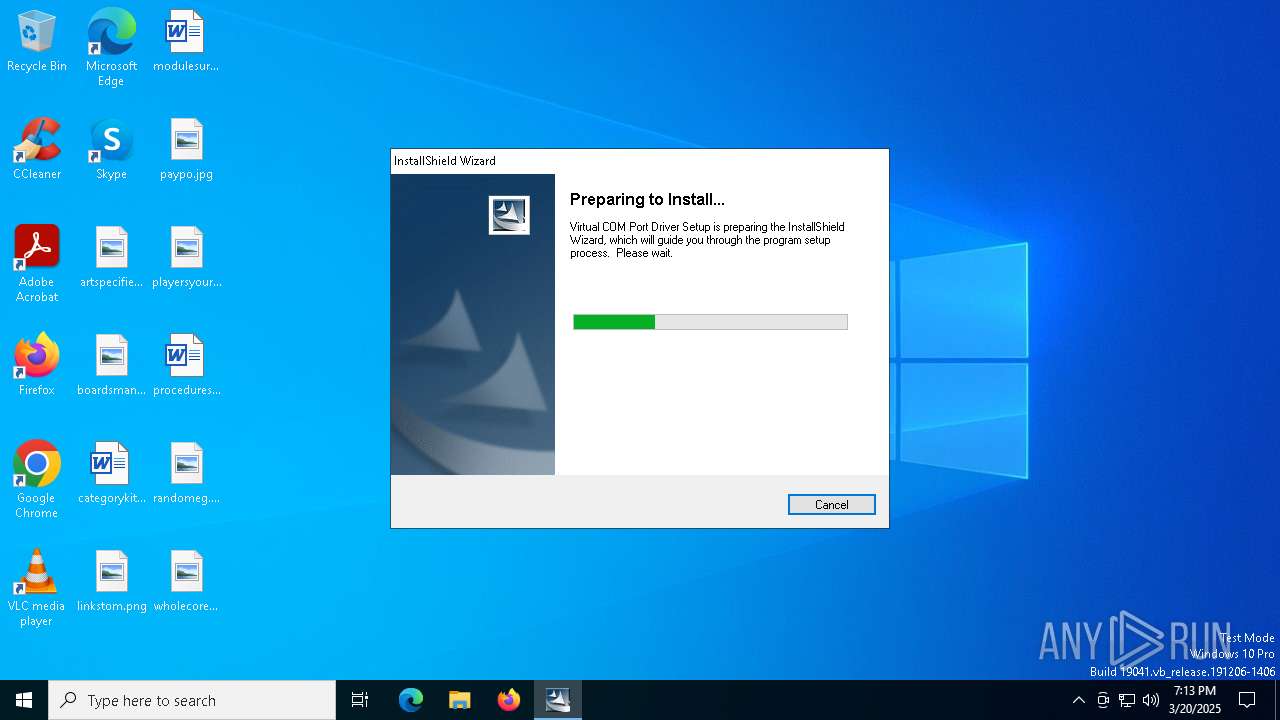
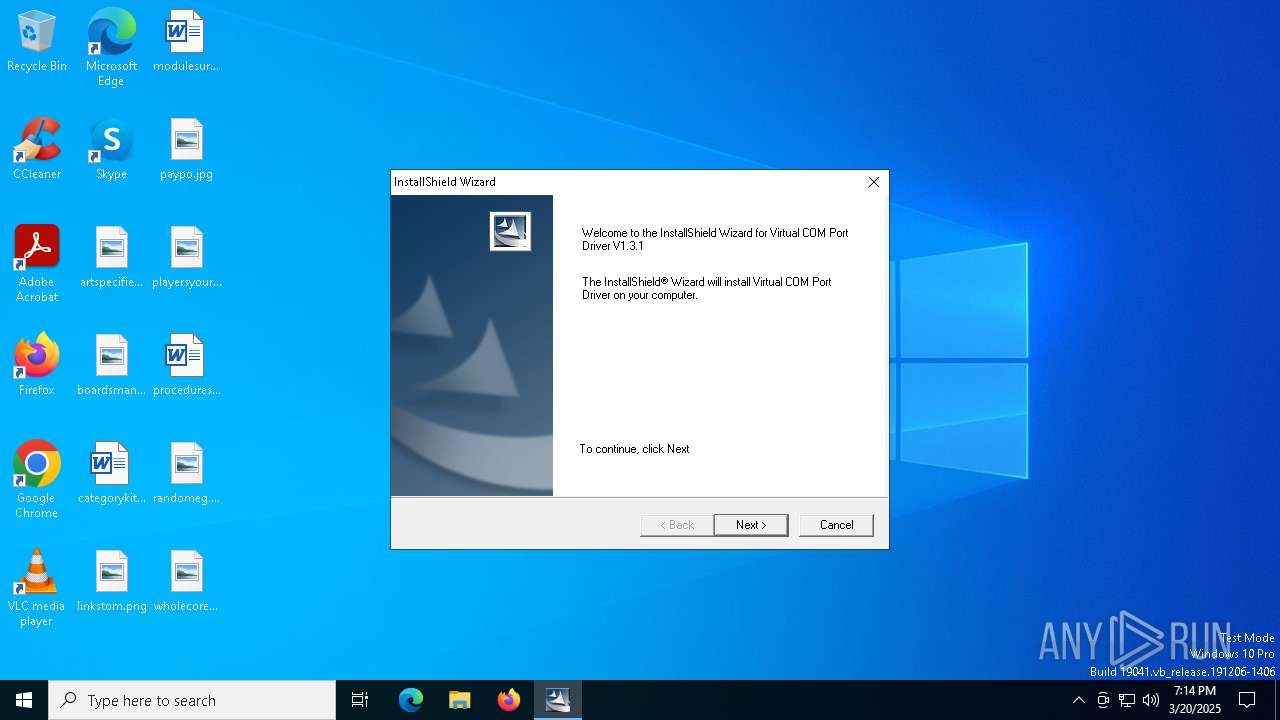
| File name: | VCP_V1.3.1_Setup_x64.ex_ |
| Full analysis: | https://app.any.run/tasks/9c242ad4-55c0-4829-97fc-98cc6f425110 |
| Verdict: | Malicious activity |
| Analysis date: | March 20, 2025, 19:13:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 42843519D903A5106E42FB7AB5D8A3D7 |
| SHA1: | 7DF78699A3711684D6A6CBA8BAB1389185BE3195 |
| SHA256: | 3466641DD9B6F809E5485BC99D06D3312350EB58F6C8E1BF7F5FFA811014CA31 |
| SSDEEP: | 98304:uehPpkVZPLDf83l0hbrpND1FyfQmmP1HoAJE8+yYdHo+wr8uBk2ZR+tEur+4BvdR:rglCr5GdpMcpo |
MALICIOUS
Executing a file with an untrusted certificate
- dpinst_amd64.exe (PID: 5436)
SUSPICIOUS
Adds/modifies Windows certificates
- msiexec.exe (PID: 7896)
Executable content was dropped or overwritten
- VCP_V1.3.1_Setup_x64.ex_.exe (PID: 7200)
- IDriver.exe (PID: 8020)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7896)
- IDriver.exe (PID: 8020)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 7896)
Process drops legitimate windows executable
- VCP_V1.3.1_Setup_x64.ex_.exe (PID: 7200)
- msiexec.exe (PID: 7896)
Executes as Windows Service
- VSSVC.exe (PID: 8176)
There is functionality for taking screenshot (YARA)
- VCP_V1.3.1_Setup_x64.ex_.exe (PID: 7200)
Searches for installed software
- dllhost.exe (PID: 8128)
Creates a software uninstall entry
- IDriver.exe (PID: 8020)
INFO
Reads the computer name
- VCP_V1.3.1_Setup_x64.ex_.exe (PID: 7200)
- msiexec.exe (PID: 7896)
- IDriver.exe (PID: 8020)
- msiexec.exe (PID: 8064)
The sample compiled with english language support
- VCP_V1.3.1_Setup_x64.ex_.exe (PID: 7200)
- msiexec.exe (PID: 7896)
- IDriver.exe (PID: 8020)
Checks supported languages
- VCP_V1.3.1_Setup_x64.ex_.exe (PID: 7200)
- msiexec.exe (PID: 7896)
- IDriver.exe (PID: 8020)
- msiexec.exe (PID: 8064)
- msiexec.exe (PID: 6436)
- drvinst.exe (PID: 4428)
Create files in a temporary directory
- VCP_V1.3.1_Setup_x64.ex_.exe (PID: 7200)
- IDriver.exe (PID: 8020)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7896)
- drvinst.exe (PID: 4428)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7896)
The sample compiled with arabic language support
- VCP_V1.3.1_Setup_x64.ex_.exe (PID: 7200)
- msiexec.exe (PID: 7896)
Reads the software policy settings
- msiexec.exe (PID: 7896)
- BackgroundTransferHost.exe (PID: 7504)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 7504)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 1056)
- BackgroundTransferHost.exe (PID: 7504)
- BackgroundTransferHost.exe (PID: 8008)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 7504)
Manages system restore points
- SrTasks.exe (PID: 2096)
Creates a software uninstall entry
- msiexec.exe (PID: 7896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2003:03:05 23:13:56+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 139264 |
| InitializedDataSize: | 102400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x188dc |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.1.160.0 |
| ProductVersionNumber: | 8.1.0.0 |
| FileFlagsMask: | 0x0002 |
| FileFlags: | Pre-release |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | |
| CompanyName: | STMicroelectronics |
| FileDescription: | Setup Launcher |
| FileVersion: | 1.3.1 |
| InternalName: | setup.exe |
| OriginalFileName: | setup.exe |
| LegalCopyright: | Copyright (C) 2003 InstallShield Software Corp. |
| ProductName: | Virtual COM Port Driver |
| ProductVersion: | 1.3.1 |
Total processes
158
Monitored processes
21
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 960 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{f87c1043-9ba2-cb4c-99e2-79265ad1707a}\stmcdc.inf" "9" "4c9ad20d7" "0000000000000174" "WinSta0\Default" "00000000000001E0" "208" "c:\program files (x86)\stmicroelectronics\software\virtual com port driver" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5436 | "C:\Program Files (x86)\STMicroelectronics\Software\Virtual COM Port Driver\dpinst_amd64.exe" /LM | C:\Program Files (x86)\STMicroelectronics\Software\Virtual COM Port Driver\dpinst_amd64.exe | — | IDriver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 256 Version: 2.1 Modules
| |||||||||||||||
| 5984 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6436 | C:\Windows\syswow64\MsiExec.exe -Embedding 27A15782466C796D5DCB9D2F27A9D681 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | "C:\Users\admin\AppData\Local\Temp\VCP_V1.3.1_Setup_x64.ex_.exe" | C:\Users\admin\AppData\Local\Temp\VCP_V1.3.1_Setup_x64.ex_.exe | — | explorer.exe | |||||||||||
User: admin Company: STMicroelectronics Integrity Level: MEDIUM Description: Setup Launcher Exit code: 3221226540 Version: 1.3.1 Modules
| |||||||||||||||
| 7200 | "C:\Users\admin\AppData\Local\Temp\VCP_V1.3.1_Setup_x64.ex_.exe" | C:\Users\admin\AppData\Local\Temp\VCP_V1.3.1_Setup_x64.ex_.exe | explorer.exe | ||||||||||||
User: admin Company: STMicroelectronics Integrity Level: HIGH Description: Setup Launcher Version: 1.3.1 Modules
| |||||||||||||||
Total events
13 729
Read events
13 261
Write events
430
Delete events
38
Modification events
| (PID) Process: | (7200) VCP_V1.3.1_Setup_x64.ex_.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{31EE4FE8-7F9C-11D5-ABB8-00B0D02332EB} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 23E594945195F2414803B4D564D2A3A3F5D88B8C |
Value: | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\23E594945195F2414803B4D564D2A3A3F5D88B8C |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C570C4A2ED53780CC810538164CBD01D0B000000010000000E00000074006800610077007400650000001400000001000000140000000715286D7073AAB28A7C0F86CE38930038058AB1620000000100000020000000B4410B73E2E6EACA47FBC42F8FA4018AF4381DC54CFAA84450461EED09454DE90F00000001000000100000001015676C3B5DEDEC330183A43E1FCCA203000000010000001400000023E594945195F2414803B4D564D2A3A3F5D88B8C1900000001000000100000004187D1F7D569D7CAB129111DF8999181090000000100000016000000301406082B0601050507030306082B060105050703011D0000000100000010000000FF28C3DDD914074F50198F568DBE43A66800000001000000080000000000876ACE99D101200000000100000017030000308203133082027CA003020102020101300D06092A864886F70D01010405003081C4310B3009060355040613025A41311530130603550408130C5765737465726E204361706531123010060355040713094361706520546F776E311D301B060355040A131454686177746520436F6E73756C74696E6720636331283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E3119301706035504031310546861777465205365727665722043413126302406092A864886F70D01090116177365727665722D6365727473407468617774652E636F6D301E170D3936303830313030303030305A170D3230313233313233353935395A3081C4310B3009060355040613025A41311530130603550408130C5765737465726E204361706531123010060355040713094361706520546F776E311D301B060355040A131454686177746520436F6E73756C74696E6720636331283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E3119301706035504031310546861777465205365727665722043413126302406092A864886F70D01090116177365727665722D6365727473407468617774652E636F6D30819F300D06092A864886F70D010101050003818D0030818902818100D3A4506EC8FF566BE6CF5DB6EA0C687547A2AAC2DA8425FCA8F44751DA85B5207494861E0F75C9E90861F5066D306E151902E952C062DB4D999EE26A0C4438CDFEBEE3640970C5FEB16B29B62F49C83BD427042510972FE7906DC0284299D74C43DEC3F5216D549F5DC358E1C0E4D95BB0B8DCB47BDF363AC2B5662212D6870D0203010001A3133011300F0603551D130101FF040530030101FF300D06092A864886F70D01010405000381810007FA4C695CFB95CC46EE85834D21308ECAD9A86F491AE6DA51E360706C846111A11AC8483E59437D4F953DA18BB70B62987A758ADD884E4E9E40DBA8CC3274B96F0DC6E3B3440BD98A6F9A299B9918283BD1E340289A5A3CD5B5E7201B8BCAA4AB8DE951D9E24C2C59A9DAB9B2751BF642F2EFC7F218F989BCA3FF8A232E7047 | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\23E594945195F2414803B4D564D2A3A3F5D88B8C |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000000400006800000001000000080000000000876ACE99D1011D0000000100000010000000FF28C3DDD914074F50198F568DBE43A6090000000100000016000000301406082B0601050507030306082B060105050703011900000001000000100000004187D1F7D569D7CAB129111DF899918103000000010000001400000023E594945195F2414803B4D564D2A3A3F5D88B8C0F00000001000000100000001015676C3B5DEDEC330183A43E1FCCA2620000000100000020000000B4410B73E2E6EACA47FBC42F8FA4018AF4381DC54CFAA84450461EED09454DE91400000001000000140000000715286D7073AAB28A7C0F86CE38930038058AB10B000000010000000E0000007400680061007700740065000000040000000100000010000000C570C4A2ED53780CC810538164CBD01D200000000100000017030000308203133082027CA003020102020101300D06092A864886F70D01010405003081C4310B3009060355040613025A41311530130603550408130C5765737465726E204361706531123010060355040713094361706520546F776E311D301B060355040A131454686177746520436F6E73756C74696E6720636331283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E3119301706035504031310546861777465205365727665722043413126302406092A864886F70D01090116177365727665722D6365727473407468617774652E636F6D301E170D3936303830313030303030305A170D3230313233313233353935395A3081C4310B3009060355040613025A41311530130603550408130C5765737465726E204361706531123010060355040713094361706520546F776E311D301B060355040A131454686177746520436F6E73756C74696E6720636331283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E3119301706035504031310546861777465205365727665722043413126302406092A864886F70D01090116177365727665722D6365727473407468617774652E636F6D30819F300D06092A864886F70D010101050003818D0030818902818100D3A4506EC8FF566BE6CF5DB6EA0C687547A2AAC2DA8425FCA8F44751DA85B5207494861E0F75C9E90861F5066D306E151902E952C062DB4D999EE26A0C4438CDFEBEE3640970C5FEB16B29B62F49C83BD427042510972FE7906DC0284299D74C43DEC3F5216D549F5DC358E1C0E4D95BB0B8DCB47BDF363AC2B5662212D6870D0203010001A3133011300F0603551D130101FF040530030101FF300D06092A864886F70D01010405000381810007FA4C695CFB95CC46EE85834D21308ECAD9A86F491AE6DA51E360706C846111A11AC8483E59437D4F953DA18BB70B62987A758ADD884E4E9E40DBA8CC3274B96F0DC6E3B3440BD98A6F9A299B9918283BD1E340289A5A3CD5B5E7201B8BCAA4AB8DE951D9E24C2C59A9DAB9B2751BF642F2EFC7F218F989BCA3FF8A232E7047 | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10e043.rbs |
Value: 31168972 | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10e043.rbsLow |
Value: 926250288 | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Program Files (x86)\Common Files\InstallShield\Driver\8\Intel 32\ |
Value: 1 | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Program Files (x86)\Common Files\InstallShield\Driver\8\ |
Value: 1 | |||
| (PID) Process: | (7896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Program Files (x86)\Common Files\InstallShield\Driver\ |
Value: 1 | |||
Executable files
34
Suspicious files
61
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7200 | VCP_V1.3.1_Setup_x64.ex_.exe | C:\Users\admin\AppData\Local\Temp\~D0CF.tmp | binary | |
MD5:3F4AEA1AEADCC777DDF03BCAAA2E9BA6 | SHA256:C21E665C31CB5F861AAA4C9207A430EC84F350CAB6BFCC2A24535D07811B0A1C | |||
| 7200 | VCP_V1.3.1_Setup_x64.ex_.exe | C:\Users\admin\AppData\Local\Temp\_isD0DF\0x0409.ini | binary | |
MD5:77F533C7496E780AABF541D08588415B | SHA256:4F4E9ECE644C5EA4C4CD81FBC0FCF716E6C8BFB9B833A4DAD6C0A502464FD739 | |||
| 7200 | VCP_V1.3.1_Setup_x64.ex_.exe | C:\Users\admin\AppData\Local\Temp\_isD0DF\Setup.INI | binary | |
MD5:3F4AEA1AEADCC777DDF03BCAAA2E9BA6 | SHA256:C21E665C31CB5F861AAA4C9207A430EC84F350CAB6BFCC2A24535D07811B0A1C | |||
| 7896 | msiexec.exe | C:\Program Files (x86)\Common Files\InstallShield\Driver\8\Intel 32\IUser8.dll | executable | |
MD5:C607892AEDF6917DB25D38357C71FAED | SHA256:CCFF4C3E65408FC907DBBC7EFAABA8BA2339FB15CA83DEC8E3BEB63EE721F9E0 | |||
| 7896 | msiexec.exe | C:\Program Files (x86)\Common Files\InstallShield\Driver\8\Intel 32\objps8.dll | executable | |
MD5:8EA5AAAA9B795E0BEC82913FDE0498B1 | SHA256:3022F4E76F54C5796DB4D38455A6D50125C387BE2948A7A0CF656FAC493153EA | |||
| 7896 | msiexec.exe | C:\Program Files (x86)\Common Files\InstallShield\Driver\8\Intel 32\IScript8.dll | executable | |
MD5:9E45A9EA665A3663ABC4338DB1A2D232 | SHA256:AB4B1FD9827789FEFBB9B6524C059BAF50D62958B989B1746AF85FF81C4F5575 | |||
| 7896 | msiexec.exe | C:\Program Files (x86)\Common Files\InstallShield\Driver\8\Intel 32\_ISRES1033.dll | executable | |
MD5:6421C95F920C1FFFEF28AADCEA18E029 | SHA256:86A2656643731D193AEA4A8EAB69BB519D740C4FB8DAD45B134767BE8E638BD9 | |||
| 7896 | msiexec.exe | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngen.log | text | |
MD5:38B7949EF8F1055D9298E03CE79EC323 | SHA256:EB0A4D90A73E37DBBB12918912FFE23ED9C8AE730F800C440507F1BAEE0D4803 | |||
| 7200 | VCP_V1.3.1_Setup_x64.ex_.exe | C:\Users\admin\AppData\Local\Temp\_isD0DF\_ISMSIDEL.INI | text | |
MD5:E564AD53E024A9125A8F47B4AD9063C1 | SHA256:6B07C324566578C51EEDFAF8E426A49CCC3AA47FAAA4394EDAE73DA087543975 | |||
| 7896 | msiexec.exe | C:\Windows\Installer\10e041.mst | binary | |
MD5:15F6A1F88ADAF0B2E8BB6855920308F2 | SHA256:DF261144D496975E5C9D847BB8BF253A3B6BC263919C44163551D91E7848E1D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
32
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4112 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4112 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7176 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4188 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7504 | BackgroundTransferHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4188 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4112 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
7176 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7176 | backgroundTaskHost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |