| File name: | atrem.exe |
| Full analysis: | https://app.any.run/tasks/dc07af04-1e1f-4764-a918-49f309bdd51d |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 13:32:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 7B922B9504882319DF9C7257673D86D5 |
| SHA1: | D557756706937DBAEA61452319C77C8E8D0ABF2B |
| SHA256: | 34433EFDAF9E6372B7A22D50EBA9852379A320AE2CD8AC99EF6F7AC0873030FA |
| SSDEEP: | 98304:Jjs07NMlyv8tTbpFuyVMwmzCkJVQEepu/4ooceCrJAKRjJ0D/71i5BwXo8tmm24D:I/QyJd |
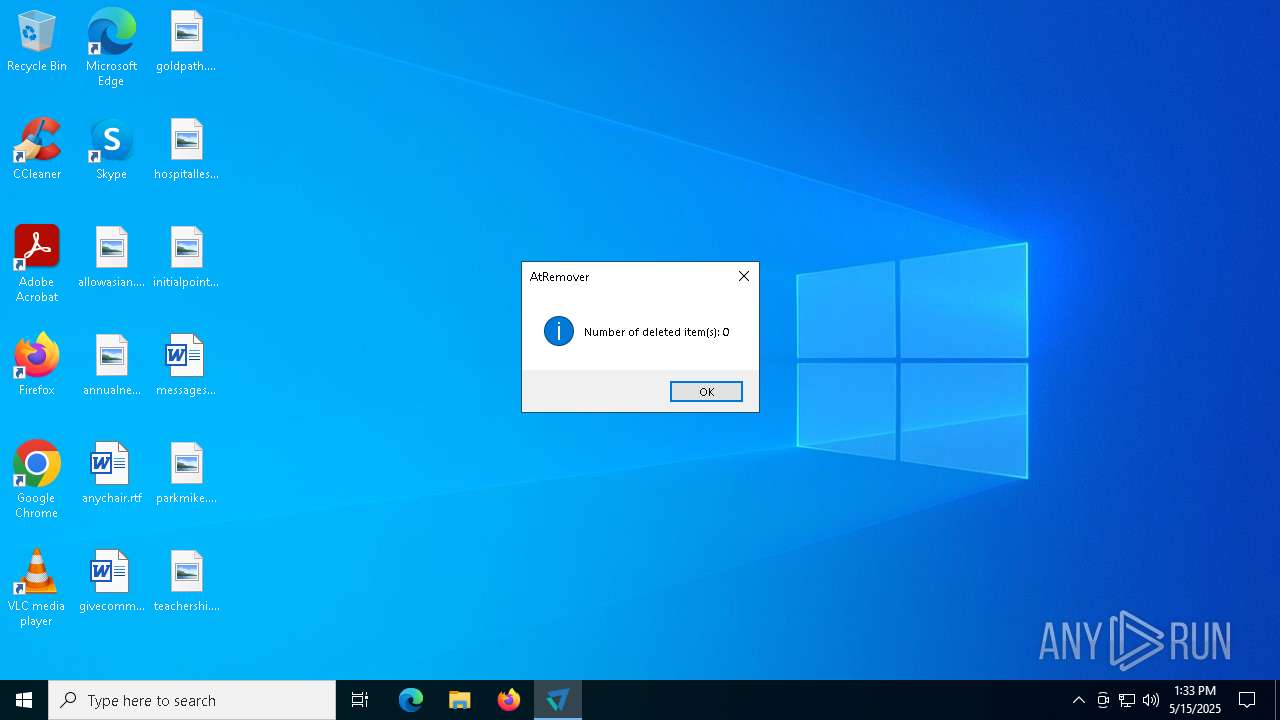
MALICIOUS
Changes the Windows auto-update feature
- atrem.exe (PID: 5048)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- atrem.exe (PID: 5048)
Checks supported languages
- atrem.exe (PID: 5048)
The sample compiled with english language support
- atrem.exe (PID: 5048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:28 04:54:18+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.42 |
| CodeSize: | 5878272 |
| InitializedDataSize: | 3289600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x49a910 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.7.0.0 |
| ProductVersionNumber: | 8.7.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | ActivTrak |
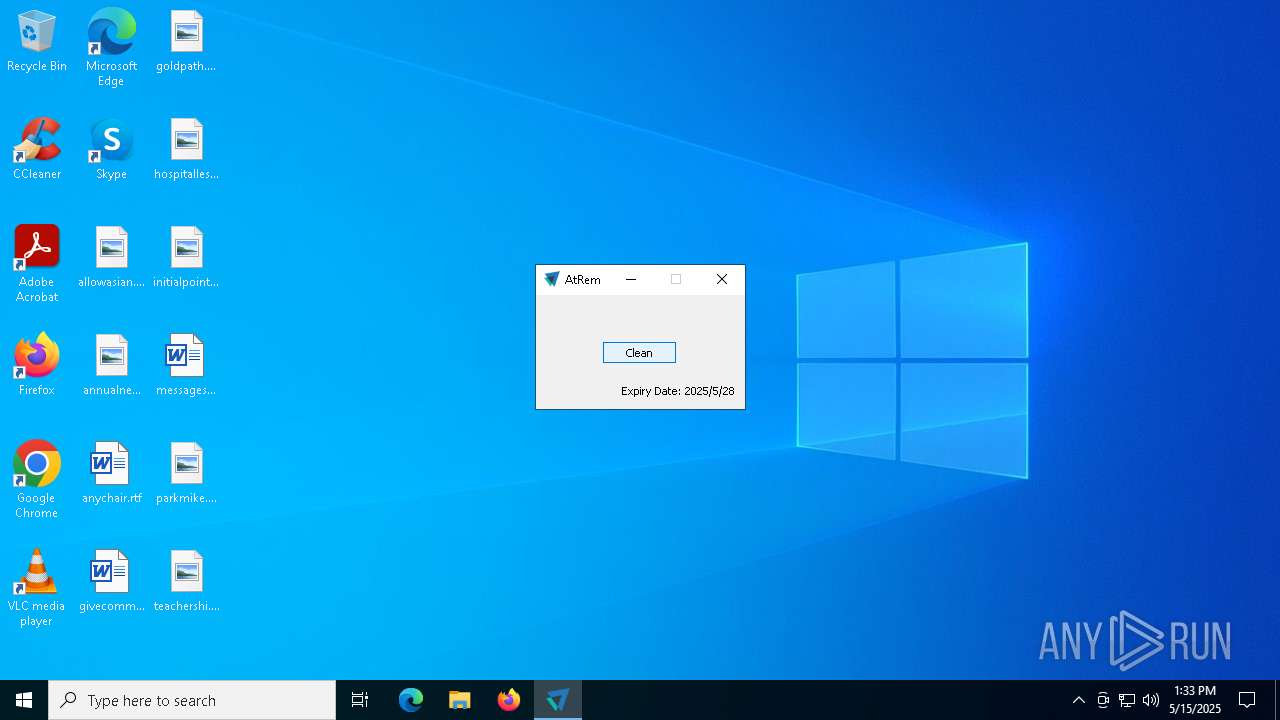
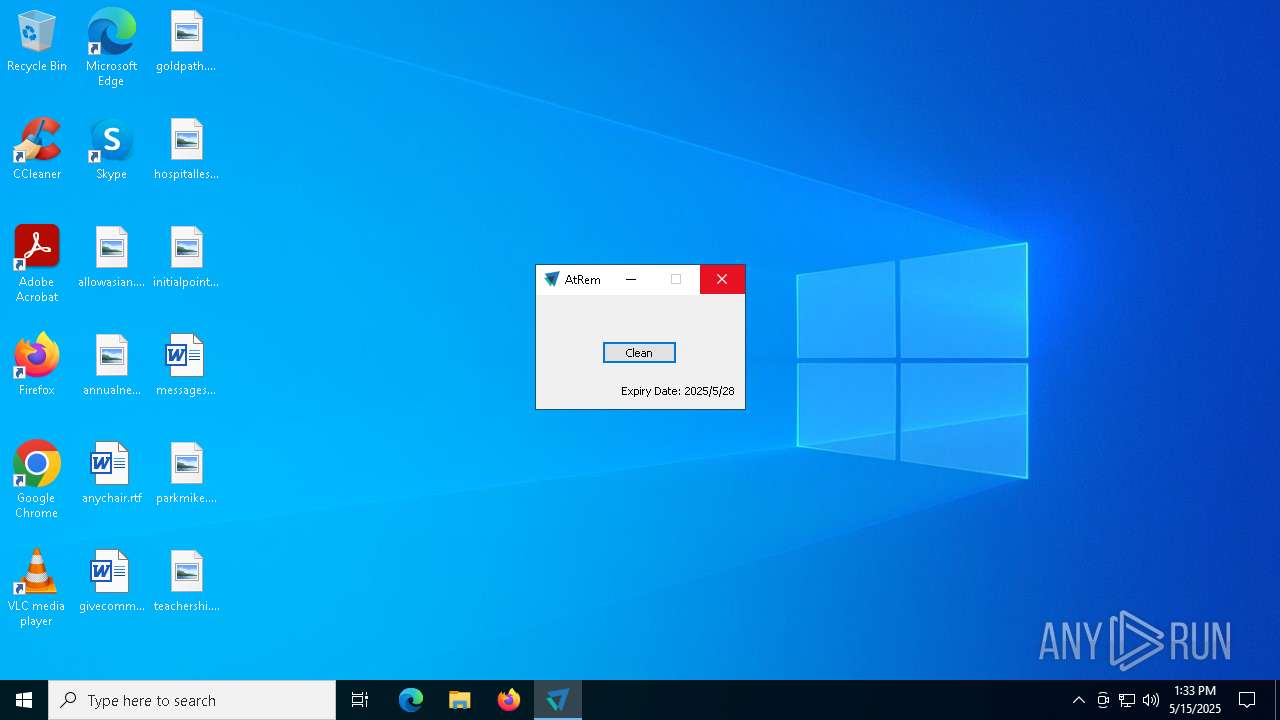
| FileDescription: | AtRemover |
| FileVersion: | 8.7.0.0 |
| InternalName: | AtRem.exe |
| LegalCopyright: | Copyright © 2009-2024 Birch Grove Software, Inc. All rights reserved. |
| OriginalFileName: | AtRem.exe |
| ProductName: | AtRemover |
| ProductVersion: | 8.7.0.0 |
Total processes
147
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
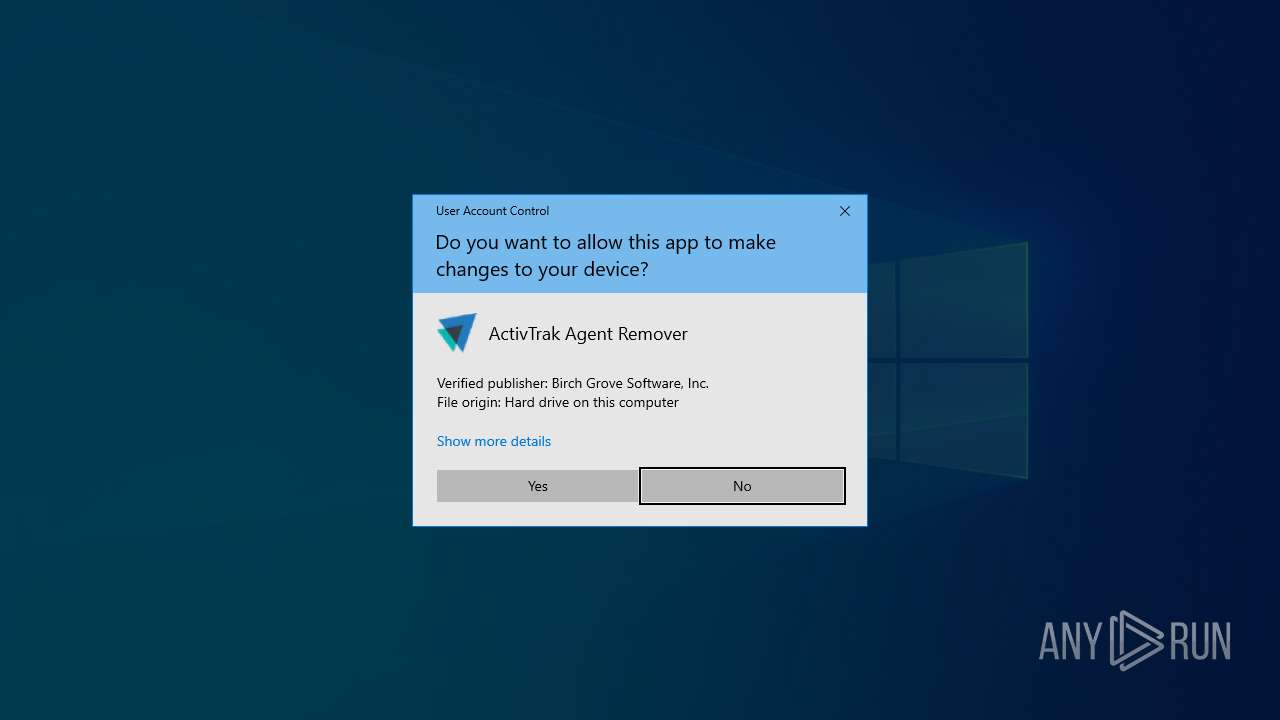
| 5048 | "C:\Users\admin\AppData\Local\Temp\atrem.exe" | C:\Users\admin\AppData\Local\Temp\atrem.exe | explorer.exe | ||||||||||||
User: admin Company: ActivTrak Integrity Level: HIGH Description: AtRemover Exit code: 2 Version: 8.7.0.0 Modules
| |||||||||||||||
| 6700 | "C:\Users\admin\AppData\Local\Temp\atrem.exe" | C:\Users\admin\AppData\Local\Temp\atrem.exe | — | explorer.exe | |||||||||||
User: admin Company: ActivTrak Integrity Level: MEDIUM Description: AtRemover Exit code: 3221226540 Version: 8.7.0.0 Modules
| |||||||||||||||
Total events
724
Read events
396
Write events
163
Delete events
165
Modification events
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\AppHVSI |
| Operation: | write | Name: | AllowAppHVSI_ProviderSet |
Value: 0 | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\EdgeUpdate |
| Operation: | write | Name: | UpdateDefault |
Value: 0 | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\Windows\Network Connections |
| Operation: | write | Name: | NC_DoNotShowLocalOnlyIcon |
Value: 1 | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\Windows\Windows Feeds |
| Operation: | write | Name: | EnableFeeds |
Value: 0 | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUServer |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUStatusServer |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | UpdateServiceUrlAlternate |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | **del.FillEmptyContentUrls |
Value: | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | UseWUServer |
Value: 1 | |||
| (PID) Process: | (5048) atrem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{038966A3-D14F-4DB0-993A-37D500D1F256}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | NoAutoUpdate |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5048 | atrem.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:C49B88A5D3FA6C96F4C75476A1E0C78C | SHA256:322292055D35DBECBD9199CE210E271DE9BB03ABAD52DE741E28F147F998036A | |||
| 5048 | atrem.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:0BBA88E4B009B44D87037B1B6EB1E7CB | SHA256:7CAE12E299AE4844A59E21128FB1109160A822C3132FEB4AE9239CA00FBC5203 | |||
| 5048 | atrem.exe | C:\Windows\SysWOW64\GroupPolicy\gpt.ini | text | |
MD5:39DFFC602ED934569F26BE44EC645814 | SHA256:B57A88E5B1ACF3A784BE88B87FA3EE1F0991CB7C1C66DA423F3595FFC6E0C5C2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
24
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5304 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5304 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
206.23.85.13.in-addr.arpa |
| unknown |