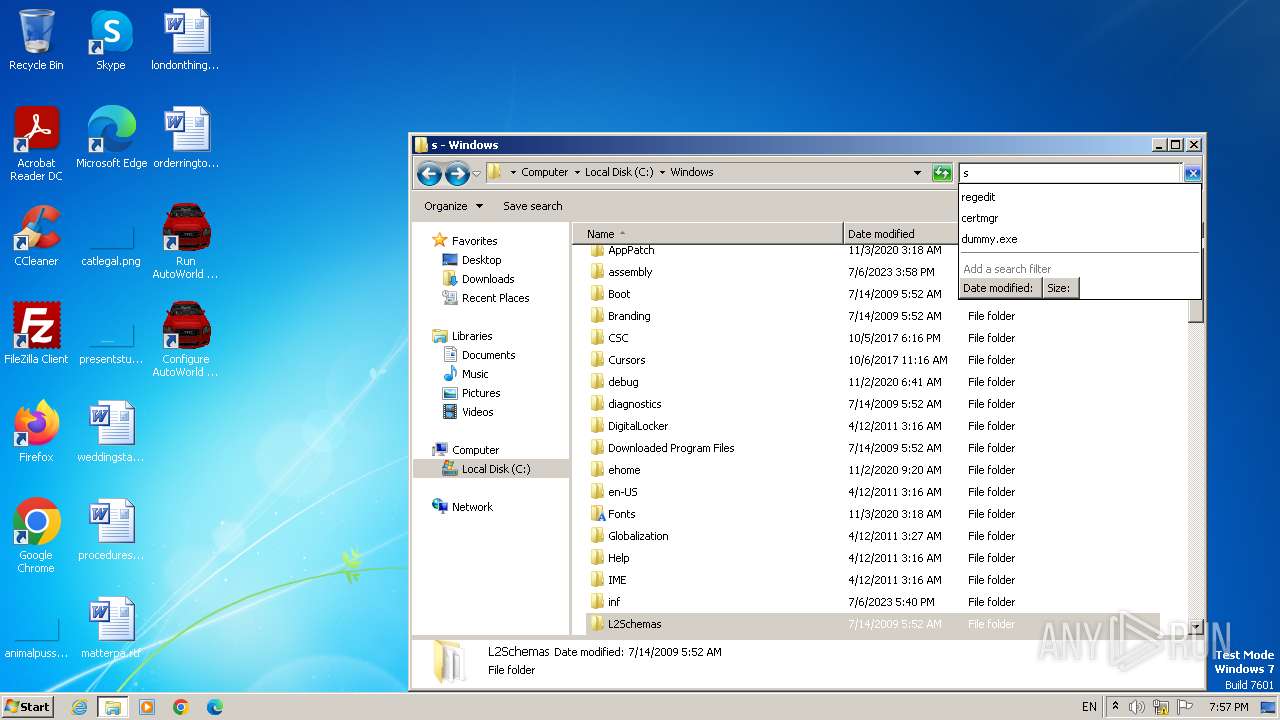
| File name: | Virus.Win32.Neshta.a.exe |
| Full analysis: | https://app.any.run/tasks/020ebe43-b17d-45fd-9fe6-4bad37820699 |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2023, 19:56:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 24DB1532ABB0BEDBA58666198A45C119 |
| SHA1: | EA44C486E5025CC720851931B1CE43C5FC364803 |
| SHA256: | 342E6EC58511B5AF7FEE92D1C31AEA6C615BD5034DF100C416EF9A2D5ED07525 |
| SSDEEP: | 196608:4HRI7/absLlVuXyEmaJHmAETdh2svml4kFRbicy27QYmjwhI:4HSObywXyEfmAGWRWcycmshI |
MALICIOUS
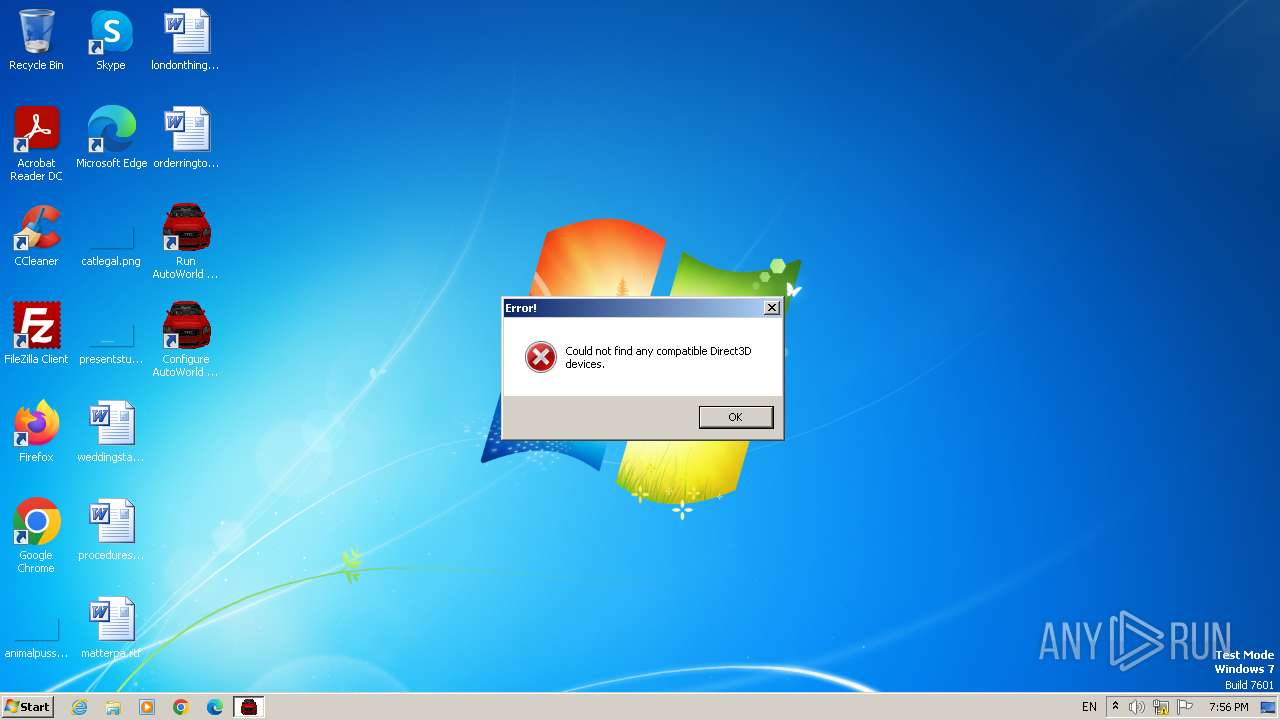
Drops the executable file immediately after the start
- Virus.Win32.Neshta.a.exe (PID: 3564)
- is-1P5GS.tmp (PID: 3572)
- Virus.Win32.Neshta.a.exe (PID: 3440)
Creates a writable file the system directory
- is-1P5GS.tmp (PID: 3572)
Actions looks like stealing of personal data
- Virus.Win32.Neshta.a.exe (PID: 3440)
SUSPICIOUS
Reads the Internet Settings
- Virus.Win32.Neshta.a.exe (PID: 3440)
- is-1P5GS.tmp (PID: 3572)
Reads the Windows owner or organization settings
- is-1P5GS.tmp (PID: 3572)
Process drops legitimate windows executable
- is-1P5GS.tmp (PID: 3572)
INFO
Checks supported languages
- Virus.Win32.Neshta.a.exe (PID: 3440)
- Virus.Win32.Neshta.a.exe (PID: 3564)
- is-1P5GS.tmp (PID: 3572)
- AutoWorld 3D Garage.exe (PID: 3444)
Create files in a temporary directory
- Virus.Win32.Neshta.a.exe (PID: 3440)
- Virus.Win32.Neshta.a.exe (PID: 3564)
- is-1P5GS.tmp (PID: 3572)
Reads the computer name
- Virus.Win32.Neshta.a.exe (PID: 3440)
- is-1P5GS.tmp (PID: 3572)
- AutoWorld 3D Garage.exe (PID: 3444)
Creates files or folders in the user directory
- is-1P5GS.tmp (PID: 3572)
Creates files in the program directory
- is-1P5GS.tmp (PID: 3572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 6 (65) |
|---|---|---|
| .exe | | | Inno Setup installer (27.1) |
| .exe | | | Win32 Executable Delphi generic (3.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.6) |
| .exe | | | Win32 Executable (generic) (1.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 29696 |
| InitializedDataSize: | 10752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x80e4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
46
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3204 | "C:\Users\admin\AppData\Local\Temp\3582-490\Virus.Win32.Neshta.a.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\Virus.Win32.Neshta.a.exe | — | Virus.Win32.Neshta.a.exe | |||||||||||
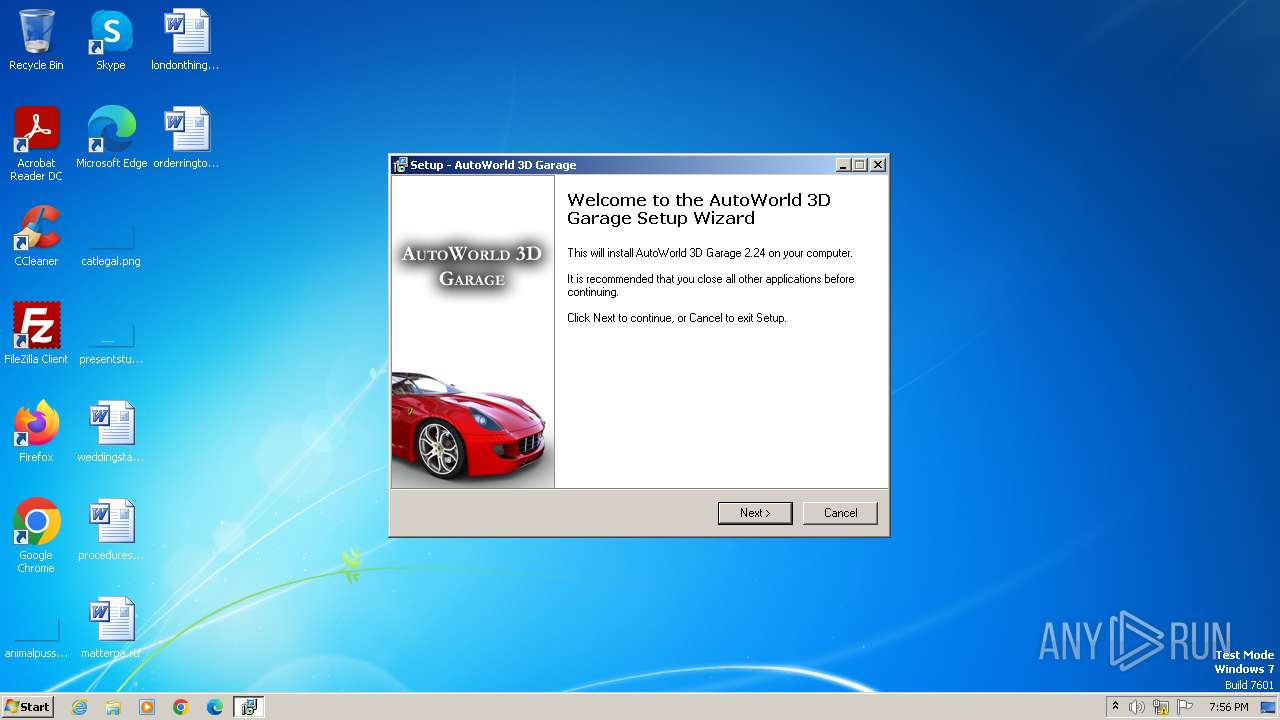
User: admin Company: StatusSoft Team Integrity Level: MEDIUM Description: AutoWorld 3D Garage Setup Exit code: 3221226540 Version: 2.2.4.0 Modules
| |||||||||||||||
| 3440 | "C:\Users\admin\AppData\Local\Temp\Virus.Win32.Neshta.a.exe" | C:\Users\admin\AppData\Local\Temp\Virus.Win32.Neshta.a.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
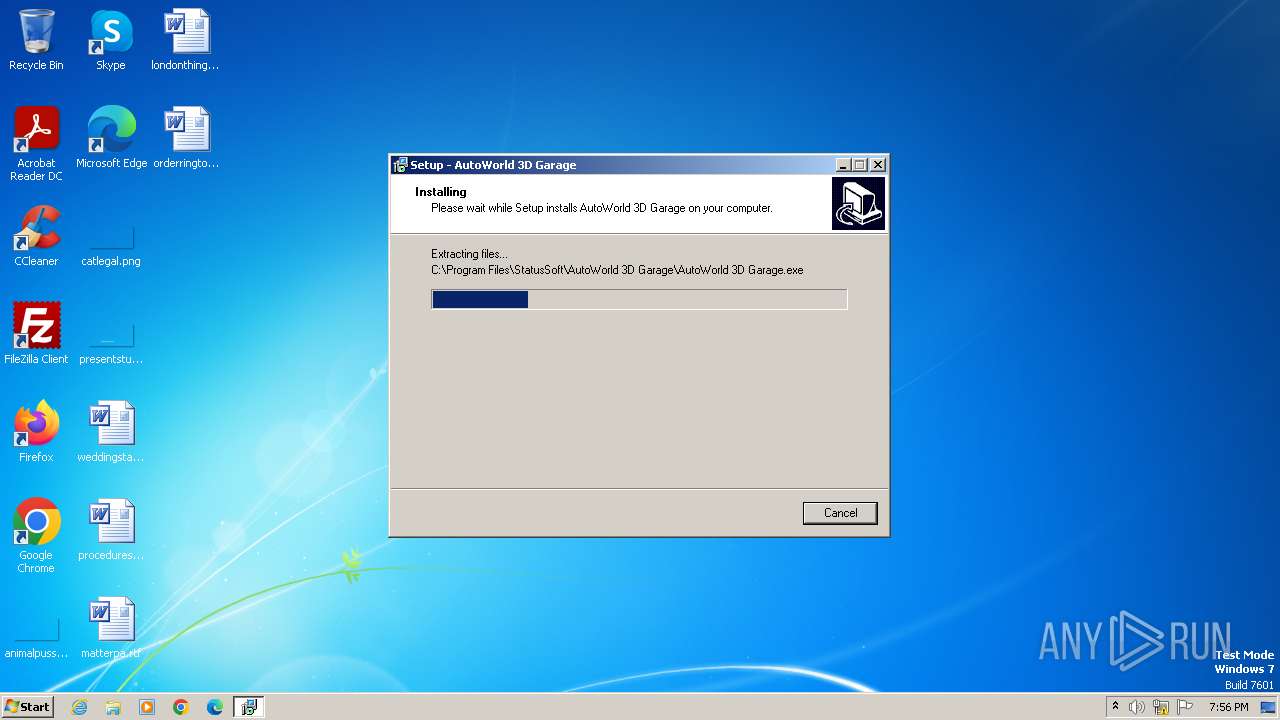
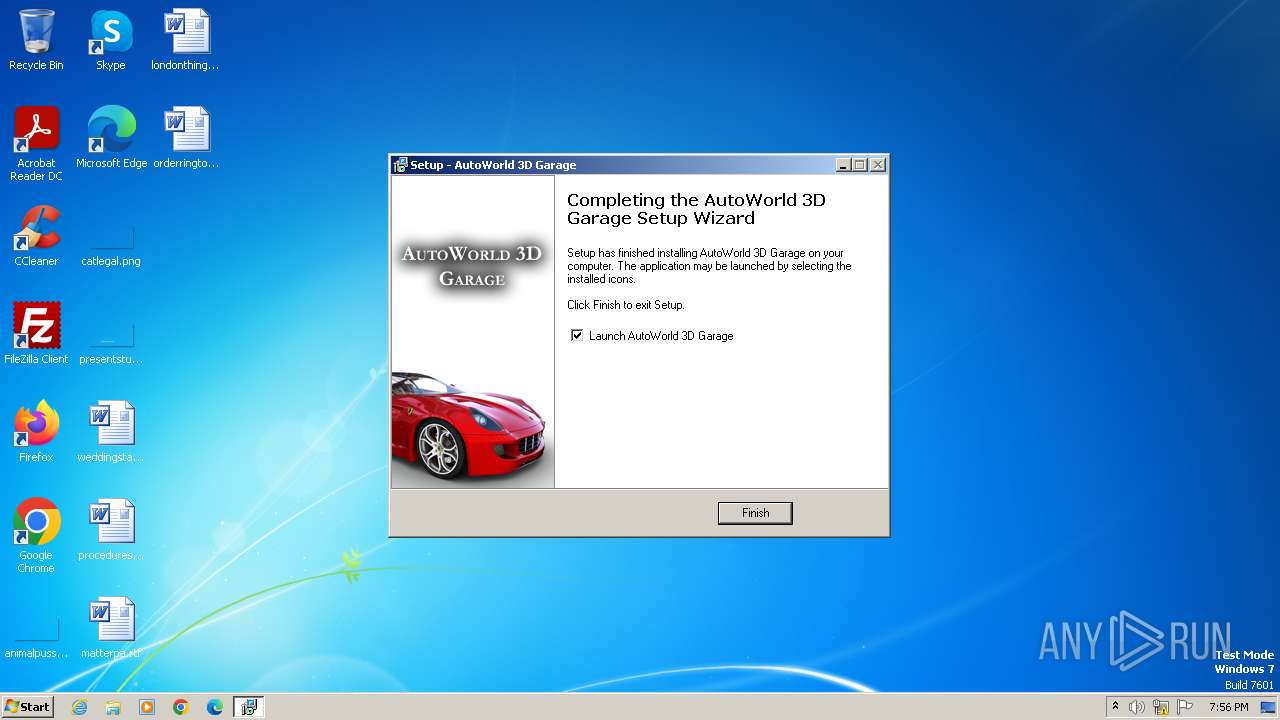
| 3444 | "C:\Program Files\StatusSoft\AutoWorld 3D Garage\AutoWorld 3D Garage.exe" /s | C:\Program Files\StatusSoft\AutoWorld 3D Garage\AutoWorld 3D Garage.exe | — | is-1P5GS.tmp | |||||||||||
User: admin Company: StatusSoft Integrity Level: HIGH Description: AutoWorld 3D Exit code: 0 Version: 2, 2, 4, 0 Modules
| |||||||||||||||
| 3564 | "C:\Users\admin\AppData\Local\Temp\3582-490\Virus.Win32.Neshta.a.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\Virus.Win32.Neshta.a.exe | Virus.Win32.Neshta.a.exe | ||||||||||||
User: admin Company: StatusSoft Team Integrity Level: HIGH Description: AutoWorld 3D Garage Setup Exit code: 0 Version: 2.2.4.0 Modules
| |||||||||||||||
| 3572 | "C:\Users\admin\AppData\Local\Temp\is-7V8GM.tmp\is-1P5GS.tmp" /SL4 $60194 "C:\Users\admin\AppData\Local\Temp\3582-490\Virus.Win32.Neshta.a.exe" 8277160 52224 | C:\Users\admin\AppData\Local\Temp\is-7V8GM.tmp\is-1P5GS.tmp | — | Virus.Win32.Neshta.a.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.43.0.0 Modules
| |||||||||||||||
Total events
1 690
Read events
1 673
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3440) Virus.Win32.Neshta.a.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3440) Virus.Win32.Neshta.a.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3440) Virus.Win32.Neshta.a.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3440) Virus.Win32.Neshta.a.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3572) is-1P5GS.tmp | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | ScreenSaveActive |
Value: 1 | |||
| (PID) Process: | (3572) is-1P5GS.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3572) is-1P5GS.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3572) is-1P5GS.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3572) is-1P5GS.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
57
Suspicious files
27
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3572 | is-1P5GS.tmp | C:\Users\admin\AppData\Local\Temp\is-3SCVM.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 3440 | Virus.Win32.Neshta.a.exe | C:\MSOCache\All Users\{90140000-006E-0407-0000-0000000FF1CE}-C\dwtrig20.exe | executable | |
MD5:CF6C595D3E5E9667667AF096762FD9C4 | SHA256:593E60CC30AE0789448547195AF77F550387F6648D45847EA244DD0DD7ABF03D | |||
| 3572 | is-1P5GS.tmp | C:\Users\admin\AppData\Local\Temp\is-3SCVM.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:054EED91B90C8066725331381C056A0B | SHA256:17DB74C713E0C12DF74245243E7A63E75815E4F4D6FD9FECA2D4D38041DD6EF0 | |||
| 3440 | Virus.Win32.Neshta.a.exe | C:\MSOCache\All Users\{90140000-006E-0416-0000-0000000FF1CE}-C\dwtrig20.exe | executable | |
MD5:CF6C595D3E5E9667667AF096762FD9C4 | SHA256:593E60CC30AE0789448547195AF77F550387F6648D45847EA244DD0DD7ABF03D | |||
| 3440 | Virus.Win32.Neshta.a.exe | C:\MSOCache\All Users\{90140000-006E-0410-0000-0000000FF1CE}-C\dwtrig20.exe | executable | |
MD5:CF6C595D3E5E9667667AF096762FD9C4 | SHA256:593E60CC30AE0789448547195AF77F550387F6648D45847EA244DD0DD7ABF03D | |||
| 3440 | Virus.Win32.Neshta.a.exe | C:\MSOCache\All Users\{90140000-003D-0000-0000-0000000FF1CE}-C\setup.exe | executable | |
MD5:566ED4F62FDC96F175AFEDD811FA0370 | SHA256:E17CD94C08FC0E001A49F43A0801CEA4625FB9AEE211B6DFEBEBEC446C21F460 | |||
| 3440 | Virus.Win32.Neshta.a.exe | C:\MSOCache\All Users\{90140000-003D-0000-0000-0000000FF1CE}-C\ose.exe | executable | |
MD5:58B58875A50A0D8B5E7BE7D6AC685164 | SHA256:2A0AA0763FDEF9C38C5DD4D50703F0C7E27F4903C139804EC75E55F8388139AE | |||
| 3440 | Virus.Win32.Neshta.a.exe | C:\MSOCache\All Users\{90140000-006E-040C-0000-0000000FF1CE}-C\DW20.EXE | executable | |
MD5:02EE6A3424782531461FB2F10713D3C1 | SHA256:EAD58C483CB20BCD57464F8A4929079539D634F469B213054BF737D227C026DC | |||
| 3440 | Virus.Win32.Neshta.a.exe | C:\Users\admin\AppData\Local\Temp\3582-490\Virus.Win32.Neshta.a.exe | executable | |
MD5:F925030A80349FF8A60B90440FF6A005 | SHA256:351E5A96206B2FA75DC95F786A8EAD931B7C73213DB5977926B7982482A5E9F4 | |||
| 3564 | Virus.Win32.Neshta.a.exe | C:\Users\admin\AppData\Local\Temp\is-7V8GM.tmp\is-1P5GS.tmp | executable | |
MD5:0360B1D1195775766B2E78A7B463F658 | SHA256:BEE86B674D51B4E21822E44F9408A69D60E282E39F5897888DF334C74D840AA4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 88.221.124.138:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |