| File name: | 1uf.msi |
| Full analysis: | https://app.any.run/tasks/569c5daf-38e8-4ee9-91bf-7775c3ab5365 |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2025, 21:57:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
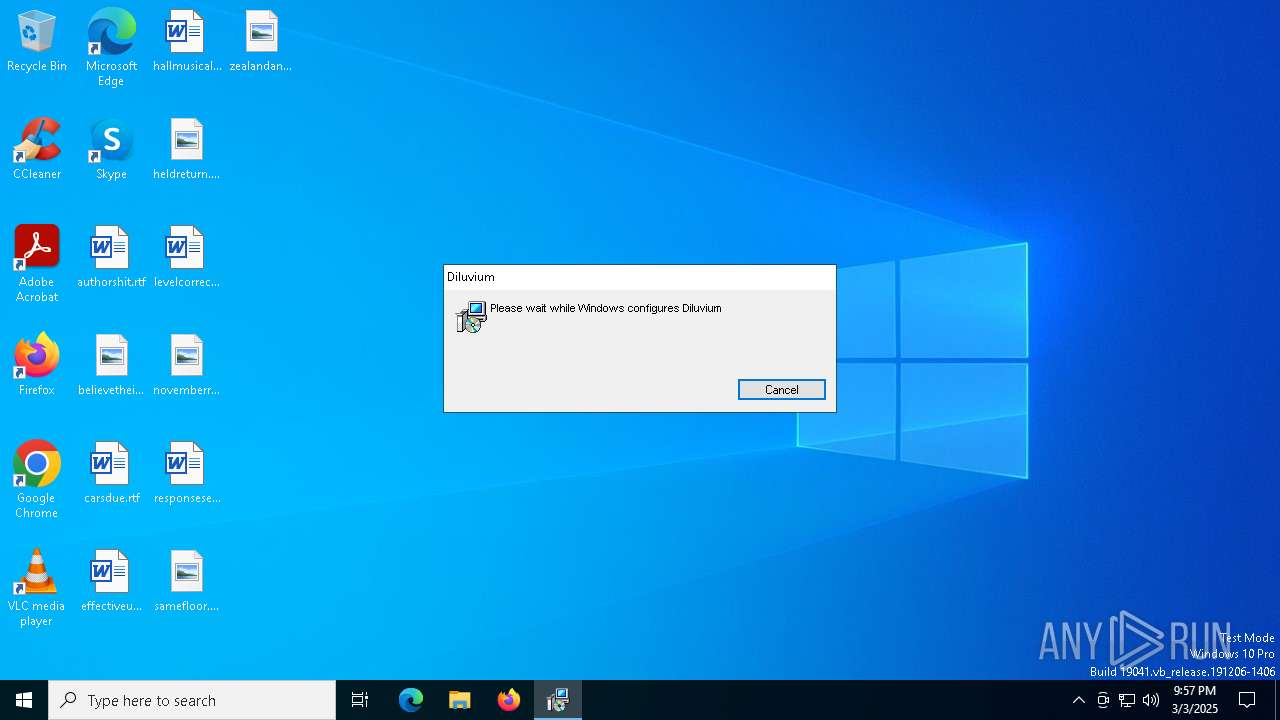
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Diluvium, Author: Blacksmith Chesterfield, Keywords: Installer, Comments: This installer database contains the logic and data required to install Diluvium., Template: Intel;1033, Revision Number: {221BB9A8-DE69-4689-92F2-B69AB71EF26F}, Create Time/Date: Mon Mar 3 18:17:28 2025, Last Saved Time/Date: Mon Mar 3 18:17:28 2025, Number of Pages: 500, Number of Words: 10, Name of Creating Application: WiX Toolset (4.0.0.0), Security: 2 |
| MD5: | B33B2C6C7073518F674F74DD19BC536F |
| SHA1: | 2CA97BF54A468F4CB5C83B679A16DAF0C7F9530F |
| SHA256: | 342117D5786F6C02C86671FC05A1D7B86F8C20C7543C9EA2EA1CF7F3B56F82B0 |
| SSDEEP: | 98304:8td0O99u21UPzm6XPbfsN8tplXRkPo5qe0vxz3TmFMNr6QLHPRWcoqeGRehHKSwU:5Wo+tHcujR |
MALICIOUS
GENERIC has been found (auto)
- msiexec.exe (PID: 7596)
SUSPICIOUS
The process drops C-runtime libraries
- msiexec.exe (PID: 7512)
- msiexec.exe (PID: 7596)
- SplashWin.exe (PID: 6476)
Process drops legitimate windows executable
- msiexec.exe (PID: 7512)
- msiexec.exe (PID: 7596)
- SplashWin.exe (PID: 6476)
Executes as Windows Service
- VSSVC.exe (PID: 7644)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7596)
Starts CMD.EXE for commands execution
- SplashWin.exe (PID: 1072)
Starts itself from another location
- SplashWin.exe (PID: 6476)
Executable content was dropped or overwritten
- SplashWin.exe (PID: 6476)
- cmd.exe (PID: 2108)
The executable file from the user directory is run by the CMD process
- Syncsign_v1.exe (PID: 2096)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 5324)
Reads the date of Windows installation
- Syncsign_v1.exe (PID: 2096)
INFO
Checks supported languages
- msiexec.exe (PID: 7596)
- SplashWin.exe (PID: 6476)
- SplashWin.exe (PID: 1072)
- Syncsign_v1.exe (PID: 2096)
- ShellExperienceHost.exe (PID: 5324)
Reads the computer name
- msiexec.exe (PID: 7596)
- SplashWin.exe (PID: 6476)
- SplashWin.exe (PID: 1072)
- ShellExperienceHost.exe (PID: 5324)
- Syncsign_v1.exe (PID: 2096)
The sample compiled with english language support
- msiexec.exe (PID: 7512)
- msiexec.exe (PID: 7596)
- SplashWin.exe (PID: 6476)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 4688)
- BackgroundTransferHost.exe (PID: 5552)
- BackgroundTransferHost.exe (PID: 1300)
- BackgroundTransferHost.exe (PID: 8056)
- BackgroundTransferHost.exe (PID: 4844)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 5552)
- Syncsign_v1.exe (PID: 2096)
- slui.exe (PID: 5404)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 5552)
- Syncsign_v1.exe (PID: 2096)
- slui.exe (PID: 5404)
- slui.exe (PID: 7992)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 5552)
- msiexec.exe (PID: 7596)
- SplashWin.exe (PID: 6476)
Manages system restore points
- SrTasks.exe (PID: 4172)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7596)
Creates a software uninstall entry
- msiexec.exe (PID: 7596)
Create files in a temporary directory
- SplashWin.exe (PID: 1072)
Reads the machine GUID from the registry
- Syncsign_v1.exe (PID: 2096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Diluvium |
| Author: | Blacksmith Chesterfield |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Diluvium. |
| Template: | Intel;1033 |
| RevisionNumber: | {221BB9A8-DE69-4689-92F2-B69AB71EF26F} |
| CreateDate: | 2025:03:03 18:17:28 |
| ModifyDate: | 2025:03:03 18:17:28 |
| Pages: | 500 |
| Words: | 10 |
| Software: | WiX Toolset (4.0.0.0) |
| Security: | Read-only recommended |
Total processes
162
Monitored processes
19
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | C:\Users\admin\AppData\Roaming\sqSystem\SplashWin.exe | C:\Users\admin\AppData\Roaming\sqSystem\SplashWin.exe | — | SplashWin.exe | |||||||||||
User: admin Company: AOMEI International Network Limited Integrity Level: MEDIUM Description: Splash Window Exit code: 1 Version: 4.0.0.0 Modules
| |||||||||||||||
| 1300 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | C:\Users\admin\AppData\Local\Temp\Syncsign_v1.exe | C:\Users\admin\AppData\Local\Temp\Syncsign_v1.exe | cmd.exe | ||||||||||||
User: admin Company: Nenad Hrg (SoftwareOK.com) Integrity Level: MEDIUM Description: Q-Dir Exit code: 0 Version: 11,4,4,0 Modules
| |||||||||||||||
| 2108 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | SplashWin.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4172 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4688 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5324 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5404 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 195
Read events
6 913
Write events
264
Delete events
18
Modification events
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000DEF74150878CDB01AC1D0000CC1D0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000DEF74150878CDB01AC1D0000CC1D0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000007EFF9250878CDB01AC1D0000CC1D0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000007EFF9250878CDB01AC1D0000CC1D0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000061C69750878CDB01AC1D0000CC1D0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000822B9A50878CDB01AC1D0000CC1D0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000C9A95D51878CDB01AC1D0000CC1D0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7596) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000000F0D6051878CDB01AC1D0000701E0000E8030000010000000000000000000000403F45A9B17660498C81D4EB8A007CD000000000000000000000000000000000 | |||
| (PID) Process: | (7644) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000004EC57051878CDB01DC1D0000941E0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
9
Suspicious files
26
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5552 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\827d948e-e3d5-4b1d-bbe8-a7a8bbff050d.down_data | — | |
MD5:— | SHA256:— | |||
| 7596 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7596 | msiexec.exe | C:\Windows\Installer\11023f.msi | — | |
MD5:— | SHA256:— | |||
| 7596 | msiexec.exe | C:\Users\admin\AppData\Local\Florilegium\fizgig.avi | — | |
MD5:— | SHA256:— | |||
| 7596 | msiexec.exe | C:\Windows\Installer\110241.msi | — | |
MD5:— | SHA256:— | |||
| 7596 | msiexec.exe | C:\Windows\Temp\~DFCA510F8F16A3395B.TMP | binary | |
MD5:9D7BF45BF4EC15A77370766DA08518B5 | SHA256:C8C887B6EB80583D4DA20063173586E69BF719D1EBBB05F0691723B9F0DFFC6B | |||
| 5552 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\827d948e-e3d5-4b1d-bbe8-a7a8bbff050d.e7d1e687-b8d2-4bb9-ad29-134895ea1352.down_meta | binary | |
MD5:27D6B66E0DE08E3E8022CA72B448A2AB | SHA256:6C421B50D8E539CF81092EBF704C23033CD905B59377B23C63E819C3CC860EEB | |||
| 5552 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\89e8e419-4aa5-4e62-abd1-2f3d33e46a8d.up_meta_secure | binary | |
MD5:F977188FDA7E43EAD5BF98CC7628BCA7 | SHA256:B03EA6B5AAB9D711AB66DE36890DA86EF79B9FA558B46F9521A27ACA178F8F9A | |||
| 5552 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:996DA96F7B324AF393887F84E28588CF | SHA256:1C50F1B776319E2A94A083CC14276F5E0BA1F37A8AB6E56A4CBD07D926E72F73 | |||
| 7596 | msiexec.exe | C:\Windows\Installer\MSI452.tmp | binary | |
MD5:884EBA65DBFD15A39123F4324ADCC2A3 | SHA256:8FA6D3C533AD1A2CFBD34709371A27BCDF27A1D901D44D831385FE9ABACDB997 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
34
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5552 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7880 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7880 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7880 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
5552 | BackgroundTransferHost.exe | 2.23.227.221:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |