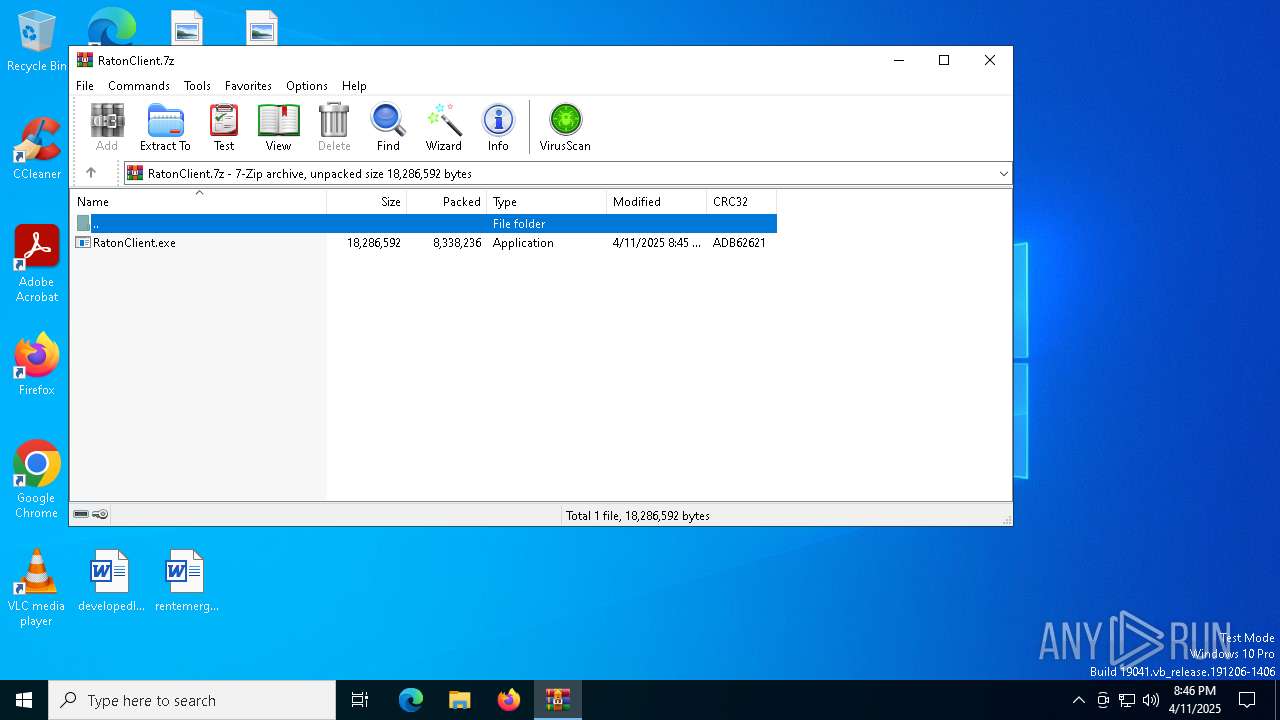
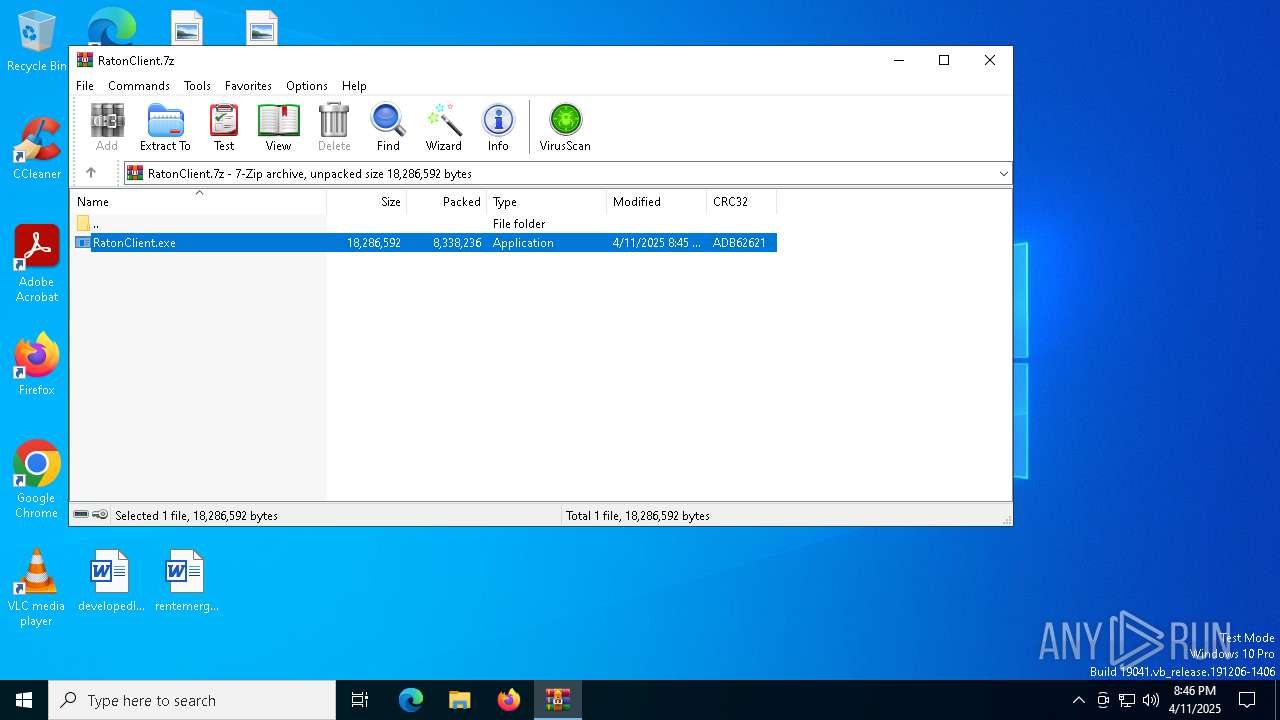
| File name: | RatonClient.7z |
| Full analysis: | https://app.any.run/tasks/8b606a3d-3ac0-4d39-8f43-bf3b673f81dc |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2025, 20:46:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 8AACA03F2F87B71B0F8AAB1436E02BE5 |
| SHA1: | 0D8CBAC9487F2D15B20AEDC12554501C486BF753 |
| SHA256: | 33F48E49093C30B93334F4DFF45376068D67091C27EABD9D065C8A87B89889E2 |
| SSDEEP: | 98304:6TwfyNXCh4zIXXKKcADFSMLHw00mgTrsoXCCx+ZEDjAcc5ngqs4cZqjlY1kdaj3g:PLnZpEvMzFA69WYZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Potential Corporate Privacy Violation
- svchost.exe (PID: 2196)
Connects to unusual port
- RatonClient.exe (PID: 5936)
Checks for external IP
- RatonClient.exe (PID: 5936)
- svchost.exe (PID: 2196)
Executable content was dropped or overwritten
- RatonClient.exe (PID: 5936)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1628)
Disables trace logs
- RatonClient.exe (PID: 5936)
Checks proxy server information
- RatonClient.exe (PID: 5936)
- slui.exe (PID: 4728)
Reads Environment values
- RatonClient.exe (PID: 5936)
Reads the machine GUID from the registry
- RatonClient.exe (PID: 5936)
Reads the software policy settings
- RatonClient.exe (PID: 5936)
- slui.exe (PID: 2284)
- slui.exe (PID: 4728)
Checks supported languages
- RatonClient.exe (PID: 5936)
Manual execution by a user
- WINWORD.EXE (PID: 1748)
Create files in a temporary directory
- RatonClient.exe (PID: 5936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:04:11 20:45:30+00:00 |
| ArchivedFileName: | RatonClient.exe |
Total processes
144
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1628 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\RatonClient.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\rentemergency.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "538BD750-6303-42D5-BBC3-0A7D2148E8E1" "631C14E9-0DBC-4DE5-9000-5EF08CE07808" "1748" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 4728 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
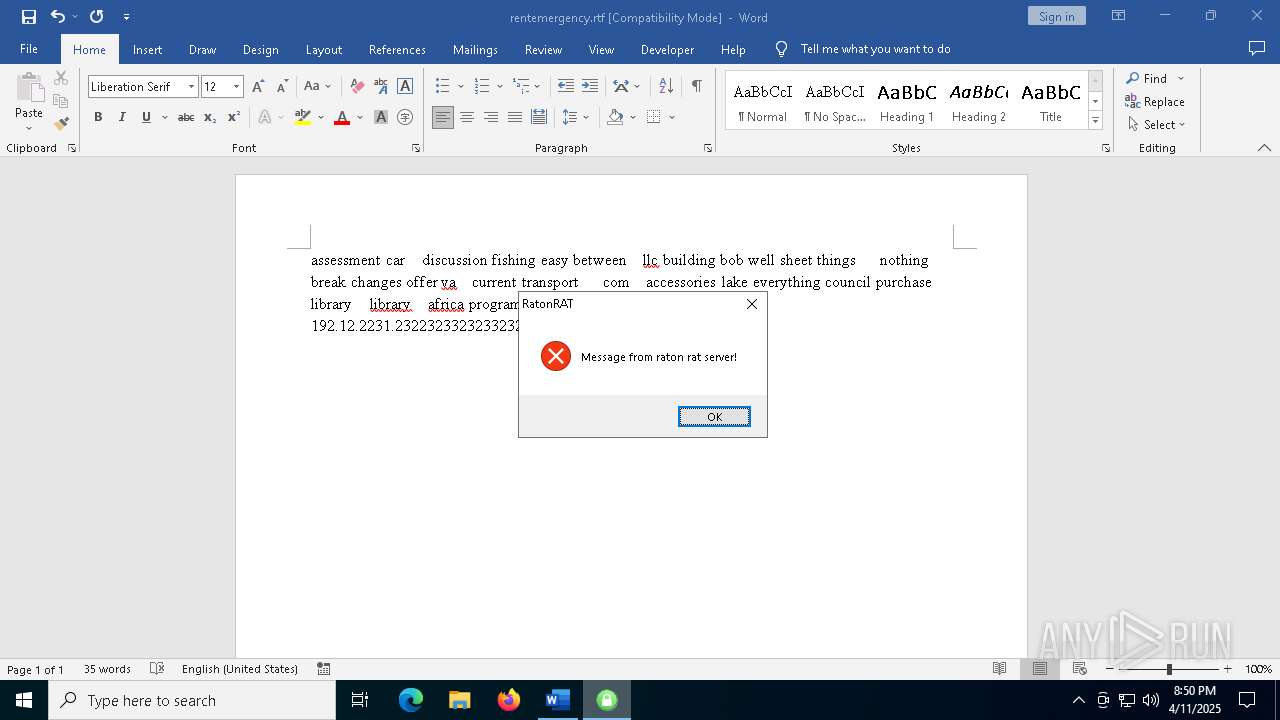
| 5936 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1628.21757\RatonClient.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1628.21757\RatonClient.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Client Version: 1.0.0.0 Modules
| |||||||||||||||
| 6476 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 807
Read events
20 374
Write events
400
Delete events
33
Modification events
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RatonClient.7z | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5936) RatonClient.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RatonClient_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5936) RatonClient.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RatonClient_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
36
Suspicious files
150
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_41.ttf | binary | |
MD5:A807151D5747F6460143DC1FD2C3195F | SHA256:C0C3B354480E34CCC0C25D371B30D0272DB86C786AF6438C217998B0A30E5EB0 | |||
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:0D60C54A653AB67831508E48CAF37BCC | SHA256:D7310B2B871F850C2A29740BCABB412C090822ACBDD966BAF439C60ED509096A | |||
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:F8F80D0624EB0F30BA1871FE55878097 | SHA256:CCB02B03CA8E2FD262293FAB9E8C08A18E9642DCE2D5BDFCAAFCA1D02AF49E0C | |||
| 1748 | WINWORD.EXE | C:\Users\admin\Desktop\~$ntemergency.rtf | binary | |
MD5:64B5A8D65C73DFF579E1ED3510FCD08D | SHA256:DDEAD15D33831E655BEAA3A135FB346CDC82180F0B43BAD4A8D28A20095500F8 | |||
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:BF0C464A0FA4C5B13276BF6AD7C06355 | SHA256:20C5896DE65FDF907EFCE70CE97E27A98257E6389E9DB816E5D5EA23CF772442 | |||
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:7F7EEBA308EAD18F58E7C82D89BDA1B7 | SHA256:B8D50C78925C373E2EDE10117B6823ADB7432EBC062590F77C3185A73946416C | |||
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\rentemergency.rtf.LNK | binary | |
MD5:FF9C110418689D78B3E38E58AC1366E1 | SHA256:38507FE3B2CCE09A4774D5C68F9CD0E277F12FCC8095B874DCE2B05D82B3124E | |||
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:03637E304FA72093E131B2B49A198399 | SHA256:B12DCAFD49028317B0AB83280F5F9A4C3956D55A6C09C80EEBD5376A9487019F | |||
| 1748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:7F7EEBA308EAD18F58E7C82D89BDA1B7 | SHA256:B8D50C78925C373E2EDE10117B6823ADB7432EBC062590F77C3185A73946416C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
71
DNS requests
37
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1748 | WINWORD.EXE | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
1748 | WINWORD.EXE | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
1748 | WINWORD.EXE | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5936 | RatonClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line | unknown | — | — | whitelisted |
5936 | RatonClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line?fields=proxy | unknown | — | — | whitelisted |
5936 | RatonClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line?fields=hosting | unknown | — | — | whitelisted |
2420 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1748 | WINWORD.EXE | GET | 200 | 2.16.189.232:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5936 | RatonClient.exe | 193.161.193.99:59733 | FEllo-59733.portmap.io | OOO Bitree Networks | RU | malicious |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
FEllo-59733.portmap.io |
| malicious |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ip-api.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potential Corporate Privacy Violation | ET INFO DNS Query to a Reverse Proxy Service Observed |
2196 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .io) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
5936 | RatonClient.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
5936 | RatonClient.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
5936 | RatonClient.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |