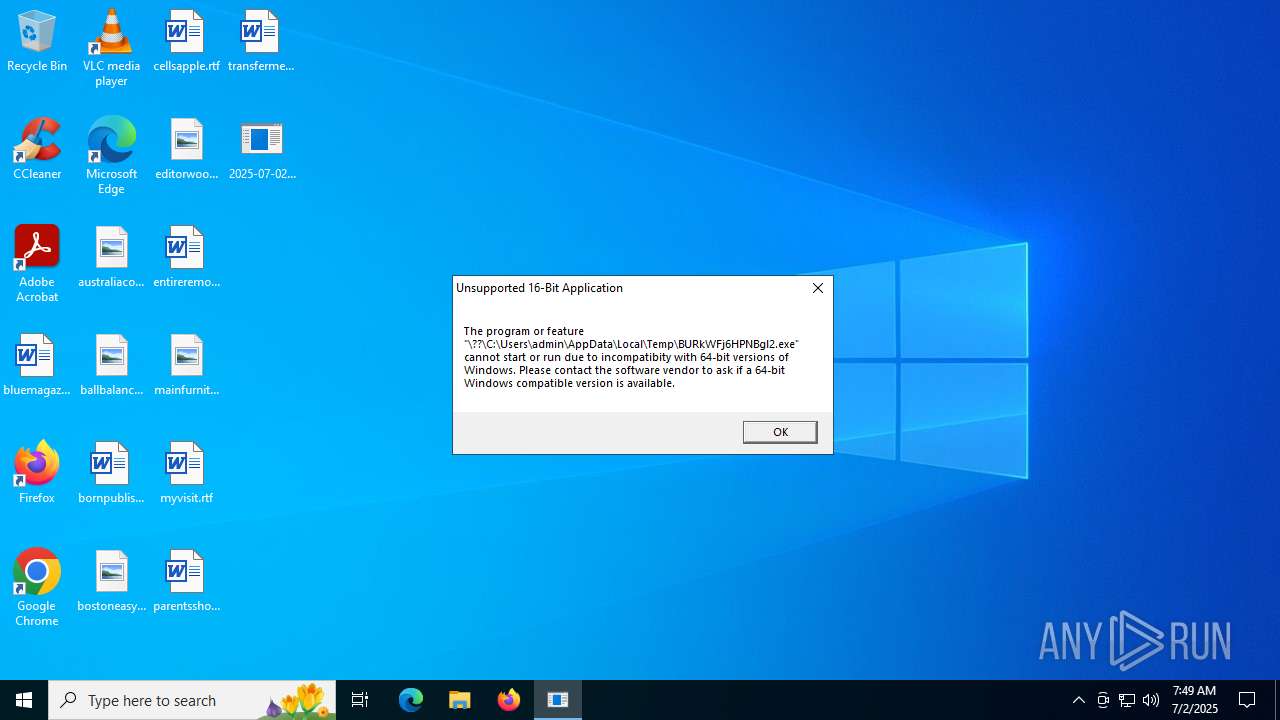
| File name: | 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys |
| Full analysis: | https://app.any.run/tasks/2e02f7dc-9dda-492b-abec-eaf99c01e9e1 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 07:49:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 27CCB92F85F8A0BC7FE0C24FB2F40DB8 |
| SHA1: | 3611E567E7F220AE7F23F3A298E250898C10F69A |
| SHA256: | 33EDD17E4EA4095F9470EB7EE17CFEC5411A2A26568E09539636942A711A0A6F |
| SSDEEP: | 3072:sEeHMiMmMfM9OcgD7eHFzpEbC7etIOxzd9UIx09d:BDyOcgDMFzwCCXnFi |
MALICIOUS
Changes the autorun value in the registry
- 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe (PID: 5480)
- CTS.exe (PID: 3688)
- CTS.exe (PID: 3960)
SUSPICIOUS
Starts itself from another location
- 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe (PID: 5480)
Executable content was dropped or overwritten
- 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe (PID: 5480)
- CTS.exe (PID: 3688)
INFO
Checks supported languages
- 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe (PID: 5480)
- CTS.exe (PID: 3688)
- CTS.exe (PID: 3960)
Reads the machine GUID from the registry
- 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe (PID: 5480)
- CTS.exe (PID: 3688)
- CTS.exe (PID: 3960)
Reads the computer name
- 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe (PID: 5480)
Launching a file from a Registry key
- 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe (PID: 5480)
- CTS.exe (PID: 3688)
- CTS.exe (PID: 3960)
Create files in a temporary directory
- 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe (PID: 5480)
Manual execution by a user
- CTS.exe (PID: 3960)
Checks proxy server information
- slui.exe (PID: 4936)
Reads the software policy settings
- slui.exe (PID: 4936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:07:12 09:13:02+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 60928 |
| InitializedDataSize: | 18944 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5cde |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
137
Monitored processes
4
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3688 | "C:\Users\admin\AppData\Local\Temp\CTS.exe" | C:\Users\admin\AppData\Local\Temp\CTS.exe | 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3960 | C:\Users\admin\AppData\Local\Temp\CTS.exe | C:\Users\admin\AppData\Local\Temp\CTS.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4936 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5480 | "C:\Users\admin\Desktop\2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe" | C:\Users\admin\Desktop\2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 634
Read events
3 631
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5480) 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CTS |
Value: C:\Users\admin\AppData\Local\Temp\CTS.exe | |||
| (PID) Process: | (3688) CTS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CTS |
Value: C:\Users\admin\AppData\Local\Temp\CTS.exe | |||
| (PID) Process: | (3960) CTS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CTS |
Value: C:\Users\admin\AppData\Local\Temp\CTS.exe | |||
Executable files
50
Suspicious files
0
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3688 | CTS.exe | C:\Users\admin\AppData\Local\dummy\officebackgroundtaskhandler.exe_c2rdll(20190323113912E90).log | executable | |
MD5:AF7E532BA7BEFB369B59D9CF497C2CA8 | SHA256:A8E203D72F5540247B4C5C890674591FB2354CE6B997044ABD26A59EEB8702CA | |||
| 5480 | 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\CTS.exe | executable | |
MD5:F9D4AB0A726ADC9B5E4B7D7B724912F1 | SHA256:B43BE87E8586CA5E995979883468F3B3D9DC5212FBFD0B5F3341A5B7C56E0FBC | |||
| 3688 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\mmc.exe.log | executable | |
MD5:B4844D75B5CA6035255181F94E0EC787 | SHA256:E901E5C716F20161368942ADE93FEA1162A81429E552616D6E957456D4926915 | |||
| 3688 | CTS.exe | C:\Users\admin\AppData\Local\dummy\officeclicktorun.exe_c2ruidll(201903231148171364).log | executable | |
MD5:2531B6A4B8C602237E7258FF0DF6CE8D | SHA256:D37DCB3B9A85091673964C01A0F33398C1F60B37D35AA971DB7C6DA547974D70 | |||
| 3688 | CTS.exe | C:\Users\admin\AppData\Local\dummy\officebackgroundtaskhandler.exe_c2rdll(2019032311484051C).log | executable | |
MD5:F16382D15B30128566B05BB40237920C | SHA256:2DD4CE70BA42185D1D43D3F20EF3848E350E03FDCBCE90B978BECB93399FADBE | |||
| 5480 | 2025-07-02_27ccb92f85f8a0bc7fe0c24fb2f40db8_bkransomware_elex_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\BURkWFj6HPNBgl2.exe | sqlite | |
MD5:DB7DC8B4767E1B252C8B30A79EC8A799 | SHA256:F5C727923367D6F87BBAEC0933F377057F1526610986B8EC7381A7401B7BFEE4 | |||
| 3688 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\setup.def.en-us_professional2019retail_04640089-6fb7-4a4d-ae33-18e0c4a879d8_tx_db_platform_def_.exe_Rules.xml | executable | |
MD5:C455F801104E83A650829E1855887744 | SHA256:C677E51BB3B40E9ABF3156B374C23AF73DA8E63908165D98BB3AE6B1054CB462 | |||
| 3688 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\sdxhelper.exe_Rules.xml | executable | |
MD5:ADFA896C9917E546C0B8E2DBF463145A | SHA256:A5199A83267C39584E1734BAE26789E3CC2A3D17F28E6530C0BDF4528E65F66E | |||
| 3688 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\setup32.exe_Rules.xml | executable | |
MD5:73DF86A9C75094C5CECB20F11091E08A | SHA256:32C0E2E23772E2E78A57CC0822BCE32F4683B4EA94705A17263C0104FEC893CA | |||
| 3688 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\setup64.exe_Rules.xml | executable | |
MD5:69CC0994AAF3F3B10D4EC09CBC481C1E | SHA256:A7CB73459E0FE1AAB2D0D7F61AA08452BB5B8E55070FC280704CB8807E942CB4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
27
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4680 | RUXIMICS.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4680 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
2180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4680 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4680 | RUXIMICS.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4680 | RUXIMICS.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |