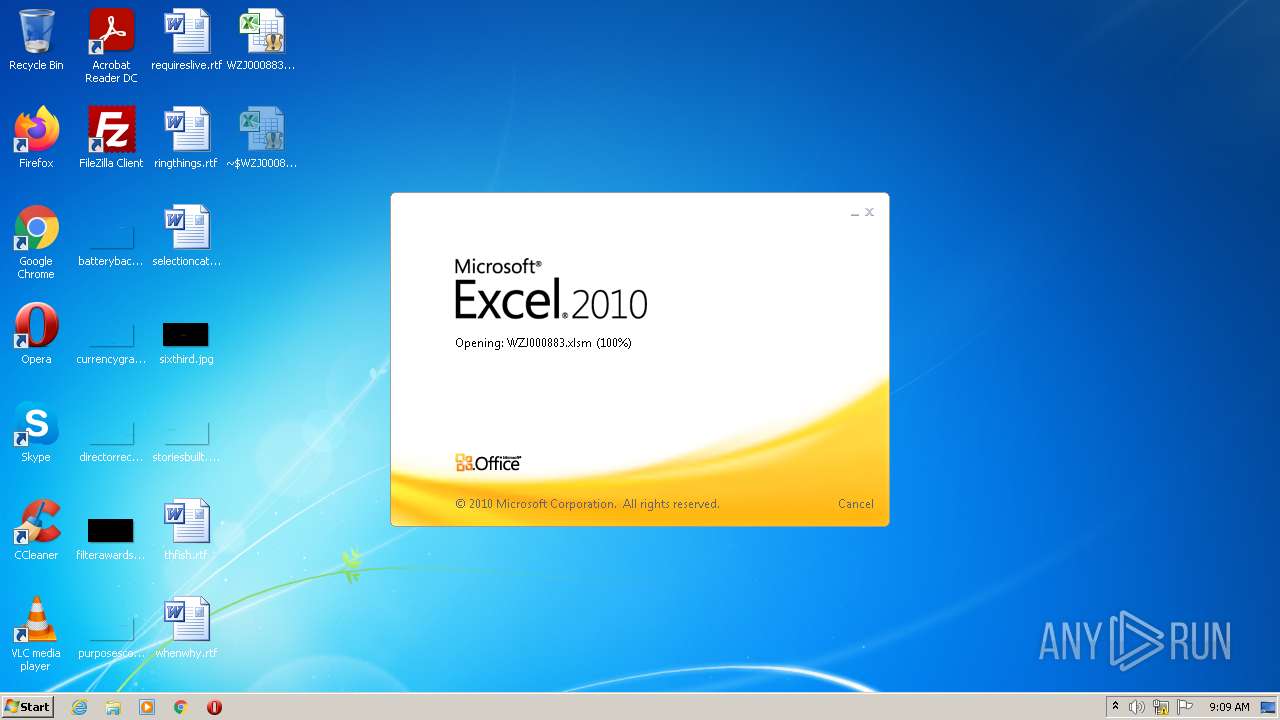
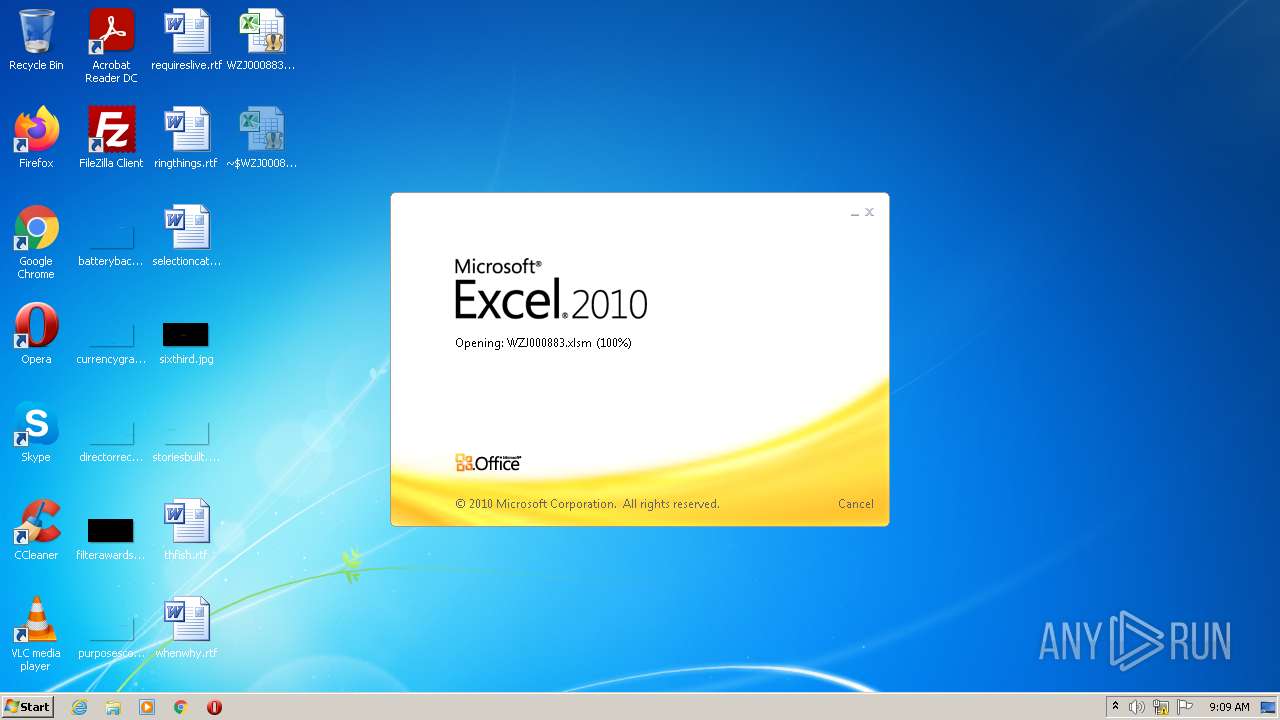
| File name: | WZJ000883.xlsm |
| Full analysis: | https://app.any.run/tasks/3fda5a0b-09c4-492d-b79d-64a2d01d220f |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | June 02, 2022, 08:09:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 00BD27A66D752E35A41CB7CE82524C3C |
| SHA1: | 3E62B73A46E418B2AC1EB2D37A4EBF7F61C891B1 |
| SHA256: | 33DC0546D60F496508E95293772364BF7E913D52EC3D606B326ADFF6CBFE7FD7 |
| SSDEEP: | 768:Ub/Mvd5dhTJxmxE7l0VGpevZCw4VmUxjfC30+kS4QyoX0VyY5G:Ubmd5zmxE7W0XYk4pEVyV |
MALICIOUS
Drops executable file immediately after starts
- EXCEL.EXE (PID: 3208)
- rundll32.exe (PID: 3224)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3208)
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 3208)
Loads dropped or rewritten executable
- rundll32.exe (PID: 2344)
- SearchProtocolHost.exe (PID: 1448)
- rundll32.exe (PID: 3224)
- rundll32.exe (PID: 3720)
- rundll32.exe (PID: 764)
EMOTET detected by memory dumps
- rundll32.exe (PID: 3720)
Connects to CnC server
- rundll32.exe (PID: 3720)
Changes the autorun value in the registry
- rundll32.exe (PID: 3720)
SUSPICIOUS
Drops a file with a compile date too recent
- EXCEL.EXE (PID: 3208)
- rundll32.exe (PID: 3224)
Reads default file associations for system extensions
- SearchProtocolHost.exe (PID: 1448)
- rundll32.exe (PID: 3224)
Uses RUNDLL32.EXE to load library
- EXCEL.EXE (PID: 3208)
- rundll32.exe (PID: 2344)
- rundll32.exe (PID: 3224)
- rundll32.exe (PID: 764)
Starts itself from another location
- rundll32.exe (PID: 2344)
Application launched itself
- rundll32.exe (PID: 3224)
- rundll32.exe (PID: 764)
Executable content was dropped or overwritten
- rundll32.exe (PID: 3224)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 3208)
Checks supported languages
- EXCEL.EXE (PID: 3208)
- rundll32.exe (PID: 2344)
- rundll32.exe (PID: 3224)
- rundll32.exe (PID: 764)
- rundll32.exe (PID: 3720)
Reads settings of System Certificates
- EXCEL.EXE (PID: 3208)
- rundll32.exe (PID: 3720)
Reads the computer name
- EXCEL.EXE (PID: 3208)
- rundll32.exe (PID: 3224)
- rundll32.exe (PID: 3720)
Checks Windows Trust Settings
- EXCEL.EXE (PID: 3208)
- rundll32.exe (PID: 3720)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Emotet
(PID) Process(3720) rundll32.exe
C2 (31)172.104.227.98:443
31.207.89.74:8080
46.55.222.11:443
41.76.108.46:8080
103.8.26.103:8080
185.184.25.237:8080
103.8.26.102:8080
203.114.109.124:443
45.118.115.99:8080
178.79.147.66:8080
58.227.42.236:80
45.118.135.203:7080
103.75.201.2:443
195.154.133.20:443
192.254.71.210:443
45.142.114.231:8080
212.237.5.209:443
207.38.84.195:8080
104.251.214.46:8080
212.237.17.99:8080
212.237.56.116:7080
216.158.226.206:443
110.232.117.186:8080
158.69.222.101:443
107.182.225.142:8080
176.104.106.96:8080
81.0.236.90:443
50.116.54.215:443
138.185.72.26:8080
51.68.175.8:8080
210.57.217.132:8080
ECS1-----BEGIN PUBLIC KEY-----
MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEQF90tsTY3Aw9HwZ6N9y5+be9Xoov
pqHyD6F5DRTl9THosAoePIs/e5AdJiYxhmV8Gq3Zw1ysSPBghxjZdDxY+Q==
-----END PUBLIC KEY-----
ECK1-----BEGIN PUBLIC KEY-----
MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAE86M1tQ4uK/Q1Vs0KTCk+fPEQ3cuw
TyCz+gIgzky2DB5Elr60DubJW5q9Tr2dj8/gEFs0TIIEJgLTuqzx+58sdg==
-----END PUBLIC KEY-----
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
XML
| AppVersion: | 16.03 |
|---|---|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| Company: | - |
| TitlesOfParts: |
|
| HeadingPairs: |
|
| ScaleCrop: | No |
| DocSecurity: | None |
| Application: | Microsoft Excel |
| ModifyDate: | 2021:12:03 13:37:58Z |
| CreateDate: | 2015:06:05 18:19:34Z |
| LastModifiedBy: | Админ |
XMP
| Creator: | Админ |
|---|
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 2833 |
| ZipCompressedSize: | 505 |
| ZipCRC: | 0x5ba70022 |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0006 |
| ZipRequiredVersion: | 20 |
Total processes
41
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | C:\Windows\system32\rundll32.exe "C:\Users\admin\AppData\Local\Hspakb\bilal.bay",iwfEvdvgZDHtvSU | C:\Windows\system32\rundll32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1448 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2344 | C:\Windows\SysWow64\rundll32.exe ..\bestb.ocx,D"&"l"&"l"&"R"&"eg"&"i"&"s"&"t"&"erServer | C:\Windows\SysWow64\rundll32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3208 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3224 | C:\Windows\system32\rundll32.exe "C:\Users\admin\bestb.ocx",DllRegisterServer | C:\Windows\system32\rundll32.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3720 | C:\Windows\system32\rundll32.exe "C:\Users\admin\AppData\Local\Hspakb\bilal.bay",DllRegisterServer | C:\Windows\system32\rundll32.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
Emotet(PID) Process(3720) rundll32.exe C2 (31)172.104.227.98:443 31.207.89.74:8080 46.55.222.11:443 41.76.108.46:8080 103.8.26.103:8080 185.184.25.237:8080 103.8.26.102:8080 203.114.109.124:443 45.118.115.99:8080 178.79.147.66:8080 58.227.42.236:80 45.118.135.203:7080 103.75.201.2:443 195.154.133.20:443 192.254.71.210:443 45.142.114.231:8080 212.237.5.209:443 207.38.84.195:8080 104.251.214.46:8080 212.237.17.99:8080 212.237.56.116:7080 216.158.226.206:443 110.232.117.186:8080 158.69.222.101:443 107.182.225.142:8080 176.104.106.96:8080 81.0.236.90:443 50.116.54.215:443 138.185.72.26:8080 51.68.175.8:8080 210.57.217.132:8080 ECS1-----BEGIN PUBLIC KEY-----
MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEQF90tsTY3Aw9HwZ6N9y5+be9Xoov
pqHyD6F5DRTl9THosAoePIs/e5AdJiYxhmV8Gq3Zw1ysSPBghxjZdDxY+Q==
-----END PUBLIC KEY----- ECK1-----BEGIN PUBLIC KEY-----
MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAE86M1tQ4uK/Q1Vs0KTCk+fPEQ3cuw
TyCz+gIgzky2DB5Elr60DubJW5q9Tr2dj8/gEFs0TIIEJgLTuqzx+58sdg==
-----END PUBLIC KEY----- | |||||||||||||||
Total events
9 974
Read events
9 854
Write events
108
Delete events
12
Modification events
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | '}? |
Value: 277D3F00880C0000010000000000000000000000 | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
3
Suspicious files
7
Text files
2
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR4D87.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E20BC11E69EA6FC0A4EBF4F49320B908 | der | |
MD5:— | SHA256:— | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\WZJ000883.xlsm.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Cab63DF.tmp | compressed | |
MD5:— | SHA256:— | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Tar63E0.tmp | cat | |
MD5:— | SHA256:— | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:54E9306F95F32E50CCD58AF19753D929 | SHA256:45F94DCEB18A8F738A26DA09CE4558995A4FE02B971882E8116FC9B59813BB72 | |||
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
4
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3208 | EXCEL.EXE | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5b28546cff9a7f3b | US | compressed | 60.0 Kb | whitelisted |
3208 | EXCEL.EXE | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?168c8e68a620006e | US | compressed | 4.70 Kb | whitelisted |
3208 | EXCEL.EXE | GET | 200 | 104.90.178.254:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
3208 | EXCEL.EXE | GET | 200 | 92.123.195.28:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQ8o0nj%2Fz2ePJs9pMIFRPxL2A%3D%3D | unknown | der | 503 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3208 | EXCEL.EXE | 42.2.93.31:443 | ordereasy.hk | PCCW Limited | HK | unknown |
3208 | EXCEL.EXE | 92.123.195.28:80 | r3.o.lencr.org | Akamai International B.V. | — | suspicious |
3208 | EXCEL.EXE | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3720 | rundll32.exe | 172.104.227.98:443 | — | — | US | malicious |
3720 | rundll32.exe | 31.207.89.74:8080 | — | Propelin Consulting S.L.U. | ES | malicious |
3720 | rundll32.exe | 46.55.222.11:443 | — | Cifrova Kabelna Korporacia EOOD | BG | malicious |
3208 | EXCEL.EXE | 104.90.178.254:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ordereasy.hk |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3720 | rundll32.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 19 |
2 ETPRO signatures available at the full report