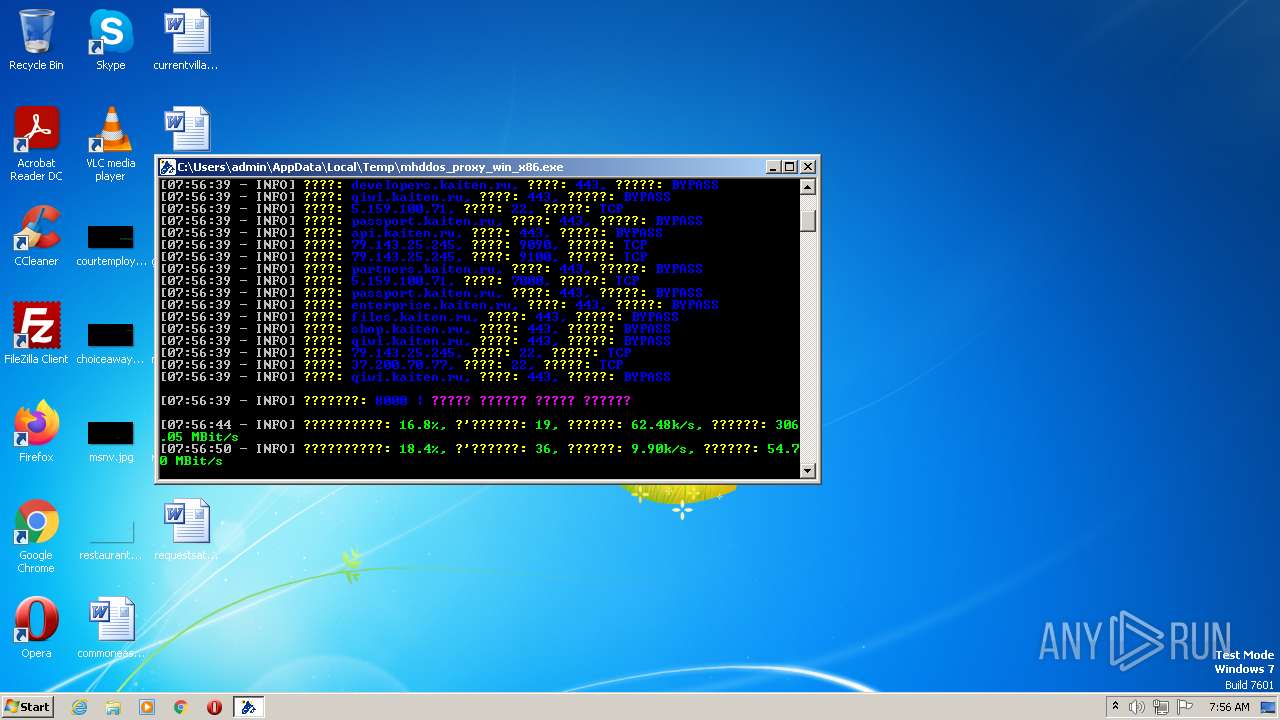
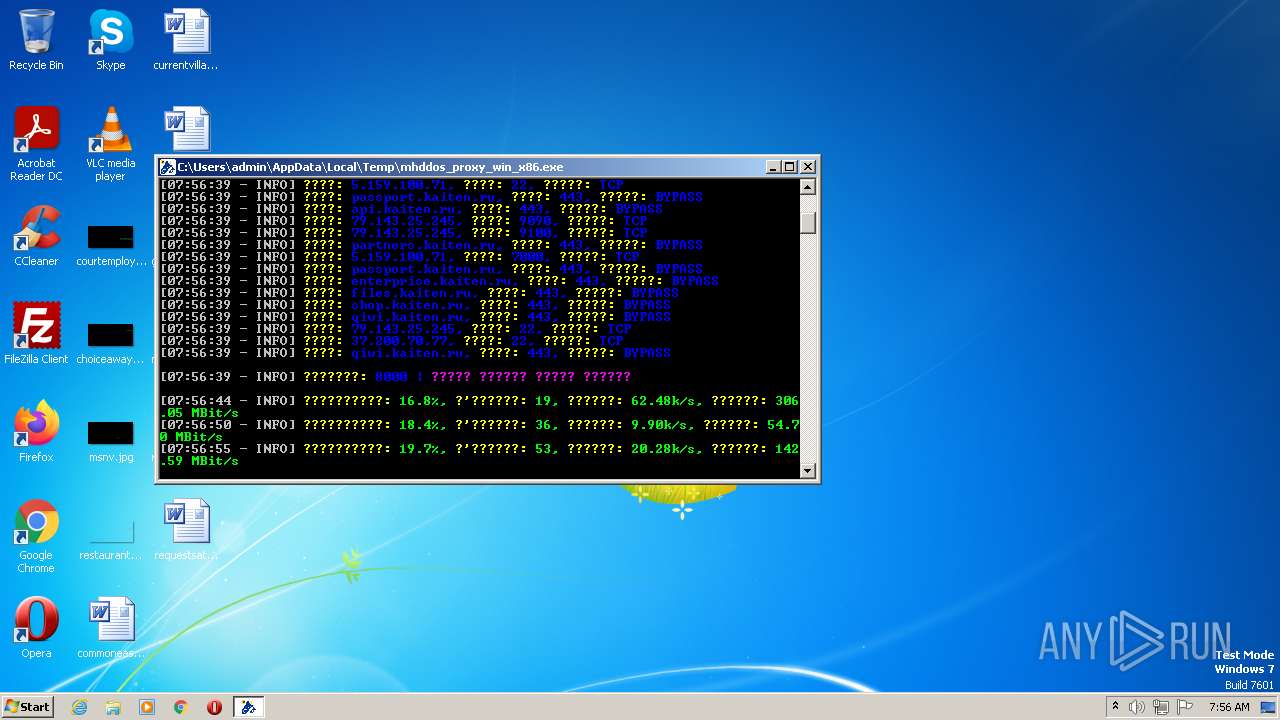
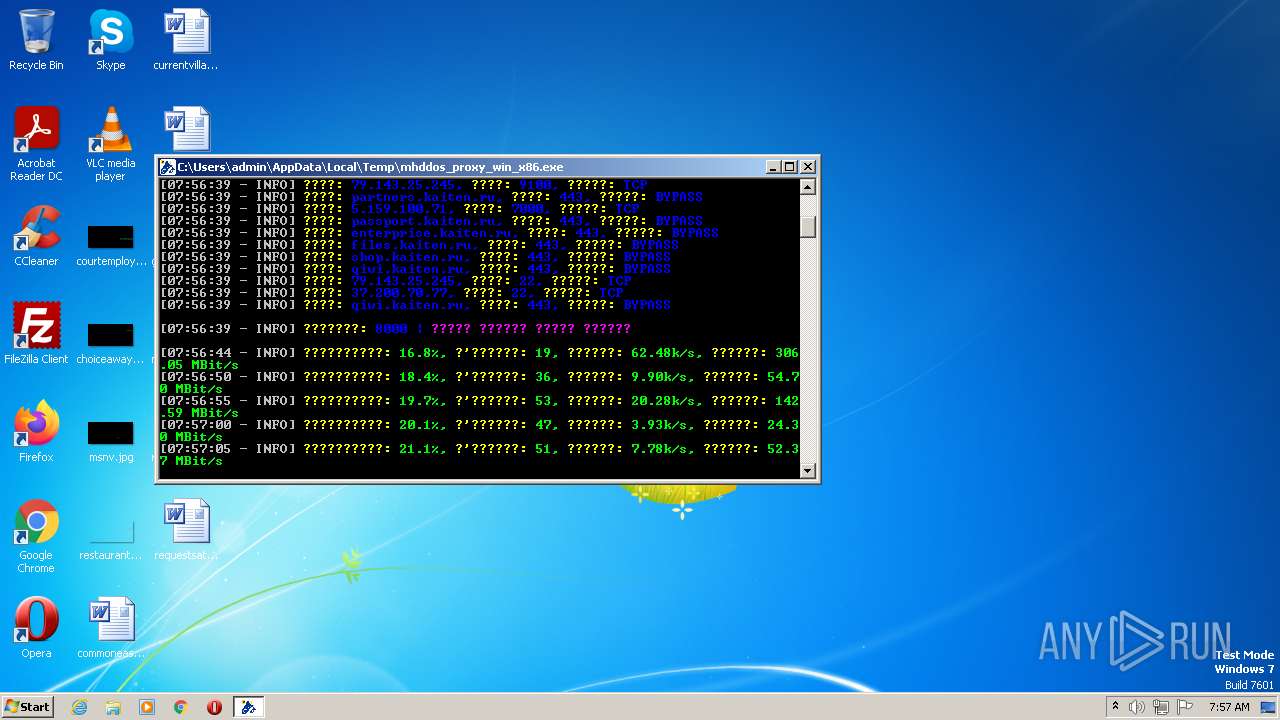
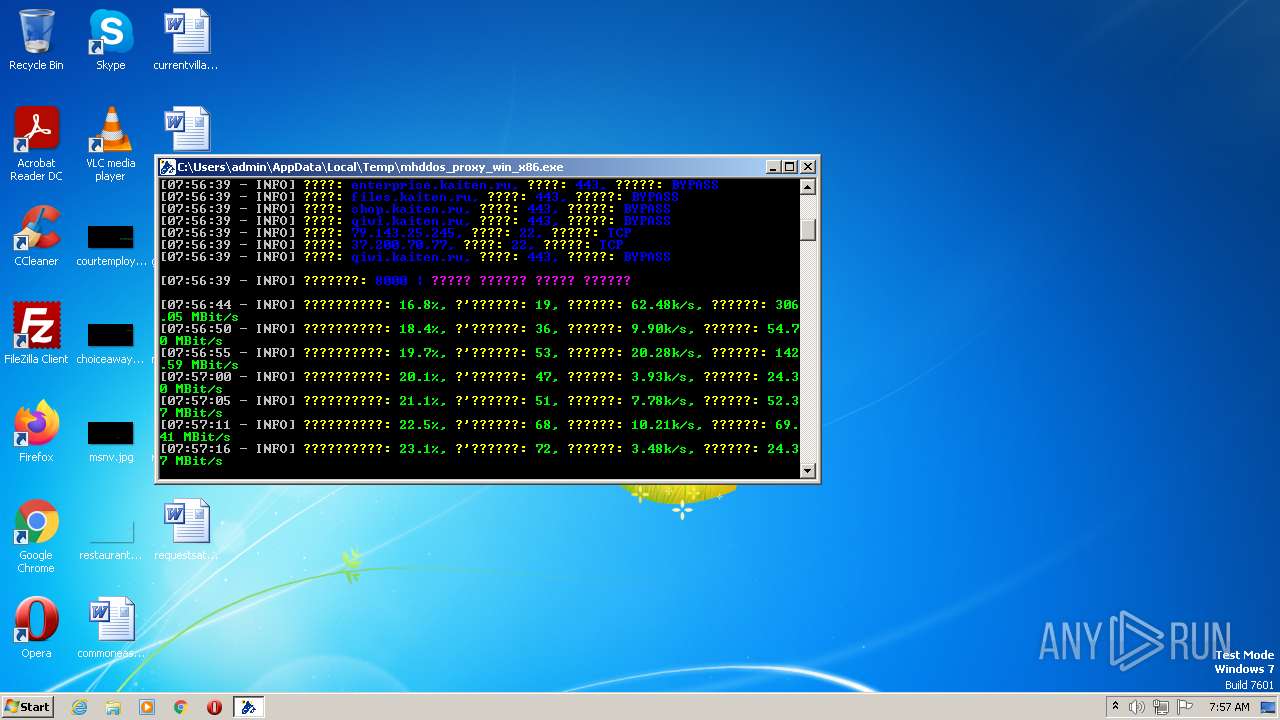
| File name: | C:\Users\admin\AppData\Local\Temp\Rar$EXa2588.49230\mhddos_proxy_win_x86.exe |
| Full analysis: | https://app.any.run/tasks/92d8df2a-bc81-4877-bbc8-4b77d82c79b0 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 06:56:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | C6C685FE2EA4E15F833E02906E40024F |
| SHA1: | D19355AD380992B9F3523F6A8A0C12FB86340702 |
| SHA256: | 33C32B31EA9D92F87CE99946FD55A9009E9463405060AFA0698D5931FFE12C2A |
| SSDEEP: | 196608:FXTwwzQiMOERyOGAgyc23qp2ijDk18RxdgdoRIST8AujgrQBsfmJ:FXTwxltyPAs23ie18zY5ACgQ |
MALICIOUS
Loads dropped or rewritten executable
- mhddos_proxy_win_x86.exe (PID: 3200)
SUSPICIOUS
Application launched itself
- mhddos_proxy_win_x86.exe (PID: 2956)
- mhddos_proxy_win_x86.exe (PID: 3200)
Executable content was dropped or overwritten
- mhddos_proxy_win_x86.exe (PID: 2956)
Loads Python modules
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2348)
Reads settings of System Certificates
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2348)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 3588)
Starts CMD.EXE for commands execution
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2348)
Reads the Internet Settings
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2348)
Checks for external IP
- mhddos_proxy_win_x86.exe (PID: 2348)
Connects to FTP
- mhddos_proxy_win_x86.exe (PID: 2348)
Connects to unusual port
- mhddos_proxy_win_x86.exe (PID: 2348)
INFO
Reads the machine GUID from the registry
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2348)
- wmpnscfg.exe (PID: 2936)
Checks supported languages
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2956)
- mhddos_proxy_win_x86.exe (PID: 2348)
- wmpnscfg.exe (PID: 2936)
Reads the computer name
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2956)
- mhddos_proxy_win_x86.exe (PID: 2348)
- wmpnscfg.exe (PID: 2936)
The process checks LSA protection
- mhddos_proxy_win_x86.exe (PID: 3200)
- netsh.exe (PID: 3552)
- mhddos_proxy_win_x86.exe (PID: 2348)
- wmpnscfg.exe (PID: 2936)
Create files in a temporary directory
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2956)
Checks proxy server information
- mhddos_proxy_win_x86.exe (PID: 3200)
- mhddos_proxy_win_x86.exe (PID: 2348)
Manual execution by a user
- wmpnscfg.exe (PID: 2936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| Subsystem: | Windows command line |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x99d0 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 95232 |
| CodeSize: | 152064 |
| LinkerVersion: | 14.33 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| TimeStamp: | 2023:03:11 13:40:48+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 11-Mar-2023 13:40:48 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 11-Mar-2023 13:40:48 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000250A2 | 0x00025200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65443 |
.rdata | 0x00027000 | 0x0000DAAC | 0x0000DC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.12547 |
.data | 0x00035000 | 0x0000F8DC | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.88802 |
.rsrc | 0x00045000 | 0x00006D10 | 0x00006E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.96511 |
.reloc | 0x0004C000 | 0x00001D90 | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.66422 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
0 | 1.51664 | 20 | Latin 1 / Western European | UNKNOWN | RT_GROUP_ICON |
1 | 5.30353 | 1443 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
Imports
ADVAPI32.dll |
KERNEL32.dll |
Total processes
42
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2348 | "C:\Users\admin\AppData\Local\Temp\mhddos_proxy_win_x86.exe" "--multiprocessing-fork" "parent_pid=3200" "pipe_handle=144" | C:\Users\admin\AppData\Local\Temp\mhddos_proxy_win_x86.exe | mhddos_proxy_win_x86.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2896 | C:\Windows\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | mhddos_proxy_win_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2936 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\AppData\Local\Temp\mhddos_proxy_win_x86.exe" | C:\Users\admin\AppData\Local\Temp\mhddos_proxy_win_x86.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3200 | "C:\Users\admin\AppData\Local\Temp\mhddos_proxy_win_x86.exe" | C:\Users\admin\AppData\Local\Temp\mhddos_proxy_win_x86.exe | mhddos_proxy_win_x86.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3456 | C:\Windows\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | mhddos_proxy_win_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3552 | netsh int ipv4 show dynamicport tcp | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3588 | C:\Windows\system32\cmd.exe /c "netsh int ipv4 show dynamicport tcp" | C:\Windows\System32\cmd.exe | — | mhddos_proxy_win_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
23 874
Read events
23 776
Write events
92
Delete events
6
Modification events
| (PID) Process: | (3552) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2936) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{5DDD0CBE-C730-4EFF-AEF9-909A7F7D839D}\{DB9DDB72-43B8-4BC8-BFB7-485D69D3D0A2} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2936) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{5DDD0CBE-C730-4EFF-AEF9-909A7F7D839D} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2936) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{27AE809D-F374-4406-8F19-9D9685B86261} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
70
Suspicious files
232
Text files
162
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\VCRUNTIME140.dll | executable | |
MD5:5F9D90D666620944943B0D6D1CCA1945 | SHA256:9EC4AFAD505E0A3DAD760FA5B59C66606AE54DD043C16914CF56D7006E46D375 | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\_ctypes.pyd | executable | |
MD5:76816A27C925F301F9776FFD76E6F6D4 | SHA256:3A94A3525B0531524AABC7F8FC9F1253894CD612A9823D9CDD5070AB81B9D329 | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\_asyncio.pyd | executable | |
MD5:C109DB7C30EBC7145F669B0C45AC9D7B | SHA256:89B48A77BE8FA5B1614152F79C85B56BC26F026B0491749908CDF2186407B06F | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\_lzma.pyd | executable | |
MD5:B23D17B4B3B15DAB84E384B8DD1D8FC6 | SHA256:D3350AD957D6C37B2C75F56A5A149F0EEB58295227F78C15048669A2E816AE3A | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\_elementtree.pyd | executable | |
MD5:1E5920AFADD11C90ADCE867F0E0CD406 | SHA256:ACBD9EC39CED8B521DD637209F88C366C455A18C884D8F02BBEDDCF50DC7AF6B | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\_bz2.pyd | executable | |
MD5:18CD8755E6D4559840D07467DF26AF34 | SHA256:82A85187FAF8786216C82AC1C4CCF32C8839048E242025ED4E7A1E3AB870255F | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\_decimal.pyd | executable | |
MD5:1FF7408362C06CE1C23D8E371CE18A16 | SHA256:44107DF49D7DBEA4E5D1C7F8A24B2D30C7F4D1623F599C4EA9F5F36C05FE0EE6 | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\_hashlib.pyd | executable | |
MD5:FE12F0301B1E8749108627F1085FD10C | SHA256:8929B5818AAA0F595B8CC3B6AADDC630F2B27BCDE3A29D44C13D95037596AA1B | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\aiohttp\_http_writer.cp38-win32.pyd | executable | |
MD5:2186B72F5BC88D944BD5B4EFEFBFFA02 | SHA256:D748953108601E6E052824D2C49DA332639EAEF301285BD64B52BC2FB37F809C | |||
| 2956 | mhddos_proxy_win_x86.exe | C:\Users\admin\AppData\Local\Temp\_MEI29562\_cffi_backend.cp38-win32.pyd | executable | |
MD5:FC7AAB36287CBEAE140E1BA35FF06DD2 | SHA256:2C939BEAE37667B797A04CD0EE36F25E7838E7F2FE7DC7C68C5203162187B573 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
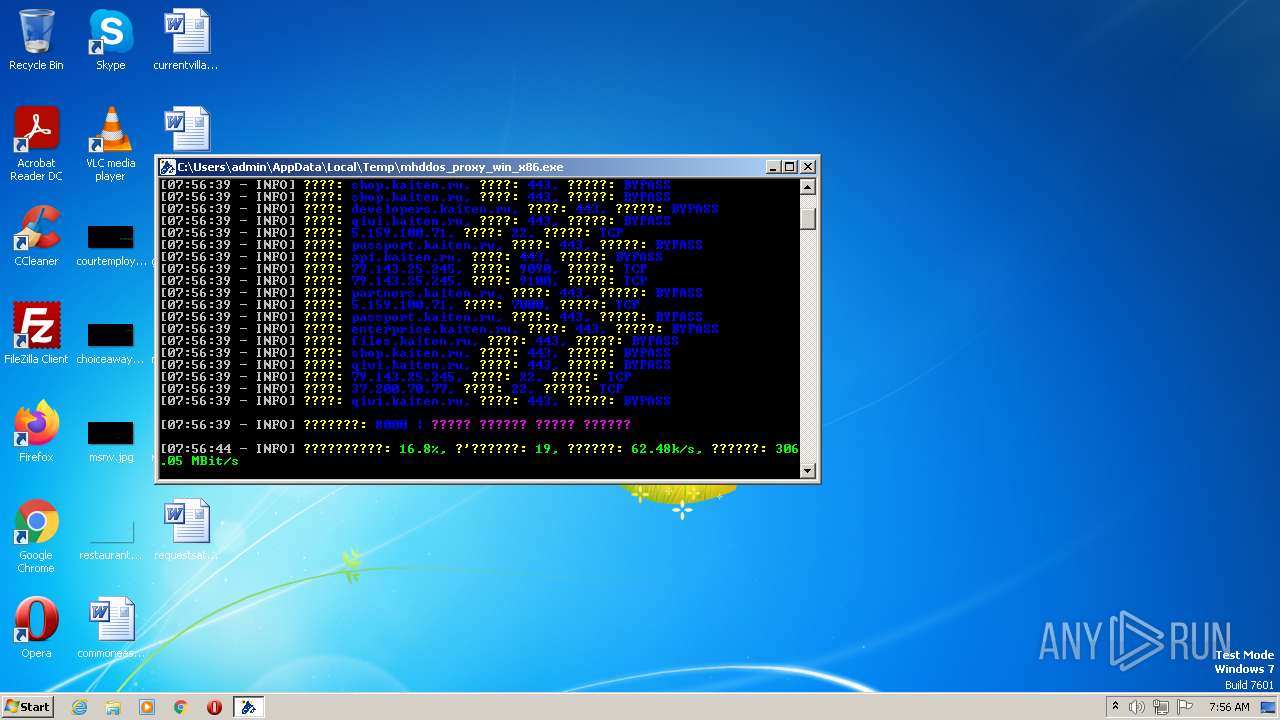
HTTP(S) requests
593
TCP/UDP connections
6 094
DNS requests
17
Threats
45
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 103.159.195.226:3125 | http://79.143.25.245:22 | ID | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 185.110.208.177:8080 | http://79.143.25.245:9090 | RU | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 165.1.167.228:8080 | http://79.143.25.245:22 | ZA | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 103.167.69.90:8080 | http://79.143.25.245:22 | ID | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 103.147.246.212:8080 | http://5.159.100.71:22 | ID | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 196.251.222.225:8080 | http://79.143.25.245:9100 | ZA | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 190.61.57.42:8080 | http://79.143.25.245:9090 | CO | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 202.65.192.252:9443 | http://79.143.25.245:8080 | HK | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 43.130.61.230:3128 | http://partners.kaiten.ru:443 | US | — | — | unknown |
2348 | mhddos_proxy_win_x86.exe | CONNECT | — | 202.8.74.9:8080 | http://79.143.25.245:9090 | KH | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3200 | mhddos_proxy_win_x86.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | malicious |
2348 | mhddos_proxy_win_x86.exe | 114.231.45.21:8089 | — | Chinanet | CN | unknown |
2348 | mhddos_proxy_win_x86.exe | 165.1.167.228:8080 | — | AMAZON-02 | ZA | unknown |
2348 | mhddos_proxy_win_x86.exe | 103.167.15.76:82 | — | Sajid Trading Ltd. | BD | unknown |
2348 | mhddos_proxy_win_x86.exe | 120.79.112.57:51281 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
2348 | mhddos_proxy_win_x86.exe | 223.247.46.147:8089 | — | Chinanet | CN | unknown |
2348 | mhddos_proxy_win_x86.exe | 31.170.19.142:4153 | — | DNET ITRisinajumi Ltd. | LV | unknown |
2348 | mhddos_proxy_win_x86.exe | 220.132.181.64:21 | — | Data Communication Business Group | TW | unknown |
2348 | mhddos_proxy_win_x86.exe | 45.168.15.81:4153 | — | Taquara Informatica Ltda ME | BR | unknown |
2348 | mhddos_proxy_win_x86.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
ip-api.com |
| malicious |
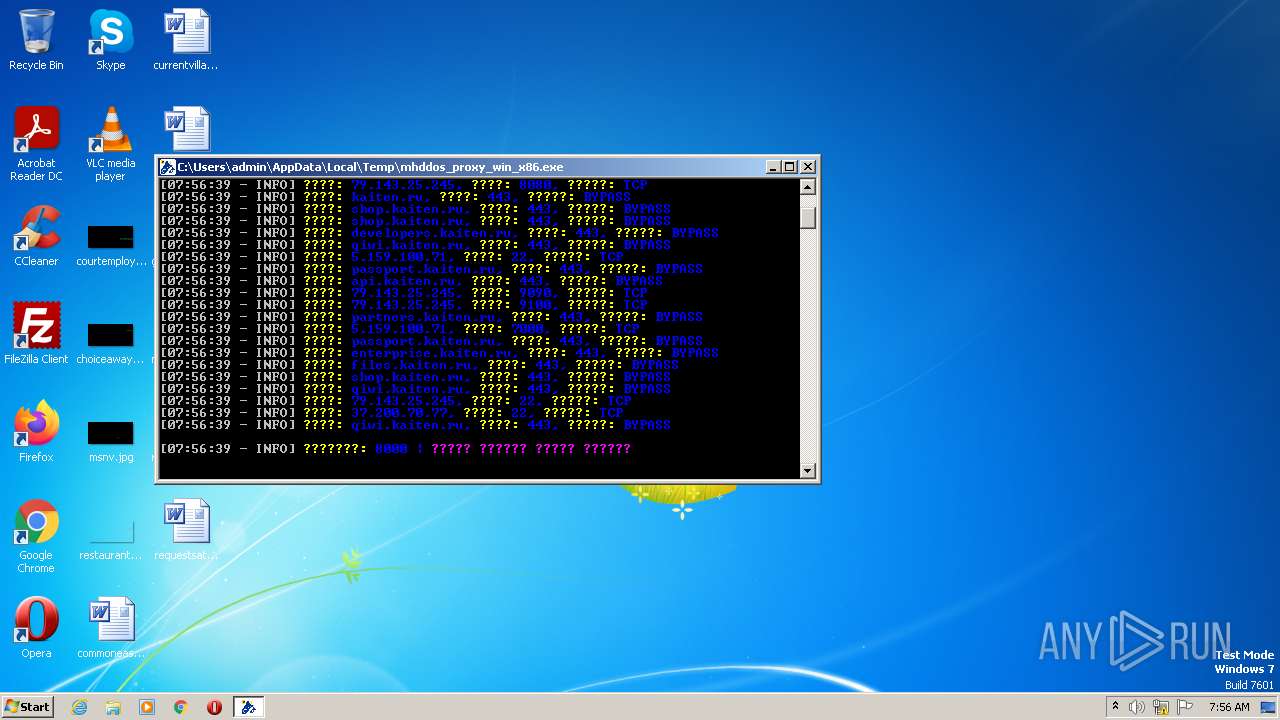
kaiten.ru |
| unknown |
partners.kaiten.ru |
| unknown |
files.kaiten.ru |
| unknown |
passport.kaiten.ru |
| unknown |
enterprise.kaiten.ru |
| unknown |
shop.kaiten.ru |
| unknown |
developers.kaiten.ru |
| unknown |
api.kaiten.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2348 | mhddos_proxy_win_x86.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2348 | mhddos_proxy_win_x86.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2348 | mhddos_proxy_win_x86.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2348 | mhddos_proxy_win_x86.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2348 | mhddos_proxy_win_x86.exe | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
2348 | mhddos_proxy_win_x86.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2348 | mhddos_proxy_win_x86.exe | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
2348 | mhddos_proxy_win_x86.exe | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
2348 | mhddos_proxy_win_x86.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2348 | mhddos_proxy_win_x86.exe | Generic Protocol Command Decode | SURICATA STREAM suspected RST injection |
1 ETPRO signatures available at the full report