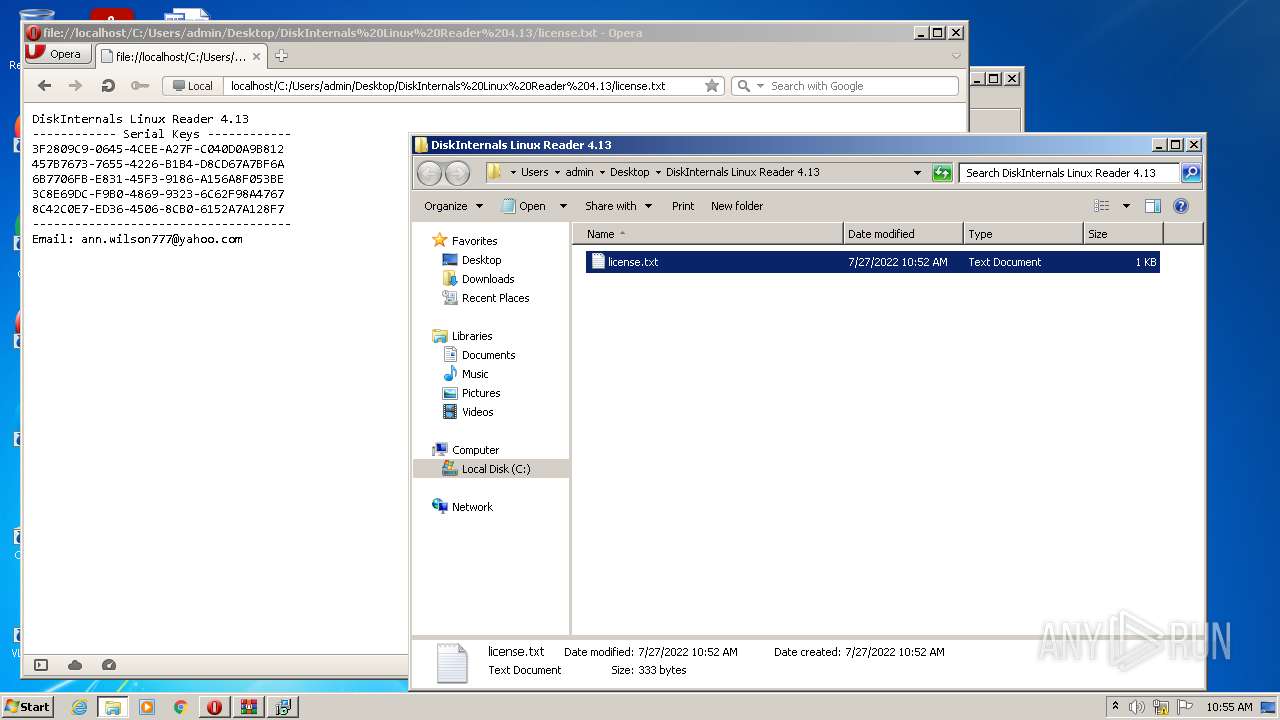
| URL: | http://free2pc.site/download?id=yA9Ht_bxnnM&s=844D7978 |
| Full analysis: | https://app.any.run/tasks/dfb0860c-4368-4801-87b3-052adecbc763 |
| Verdict: | Malicious activity |
| Analysis date: | July 27, 2022, 09:50:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B02932F0E1E25499168FF76C6CAB7285 |
| SHA1: | 607E78E3A8B858D3B16BADC3004157537DAF593A |
| SHA256: | 33B37A7CA6A7B16B2214A59223AC8B2CADFDF03D4F9D5988FF63F3474DC7F7E6 |
| SSDEEP: | 3:N1KYQySKSS+HcHdLddn:CYTSb89Lf |
MALICIOUS
Drops executable file immediately after starts
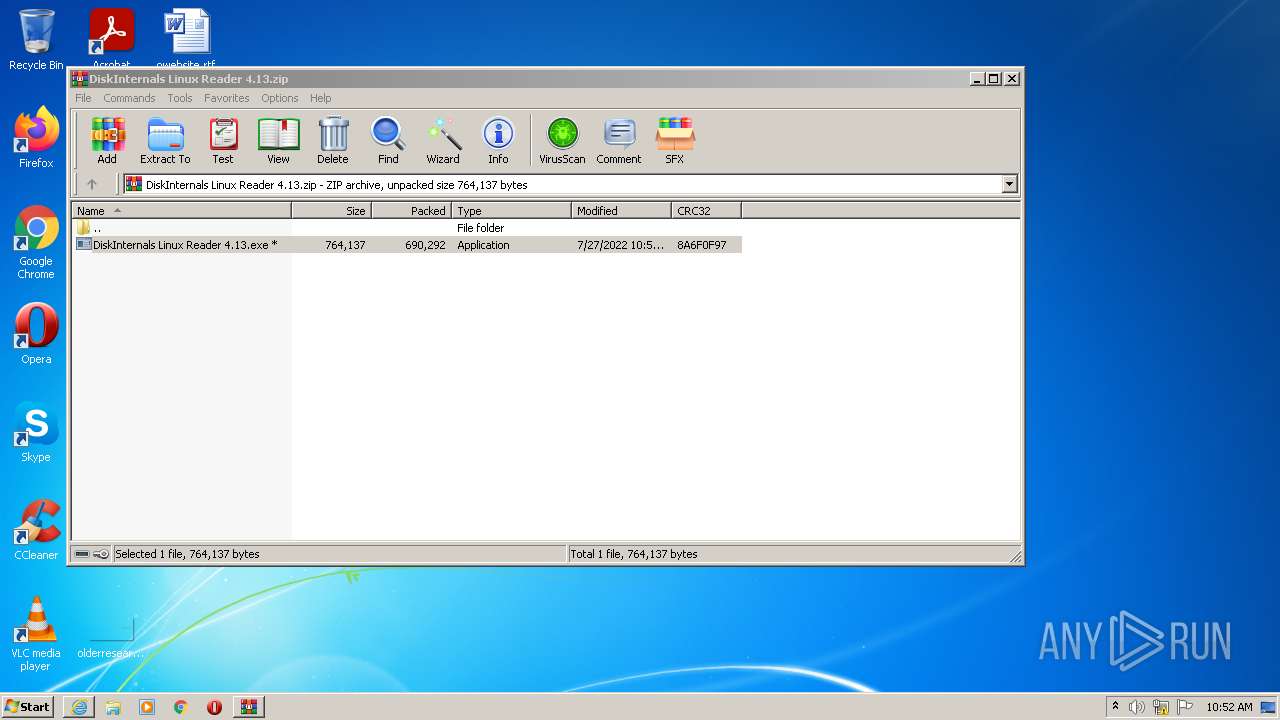
- WinRAR.exe (PID: 3532)
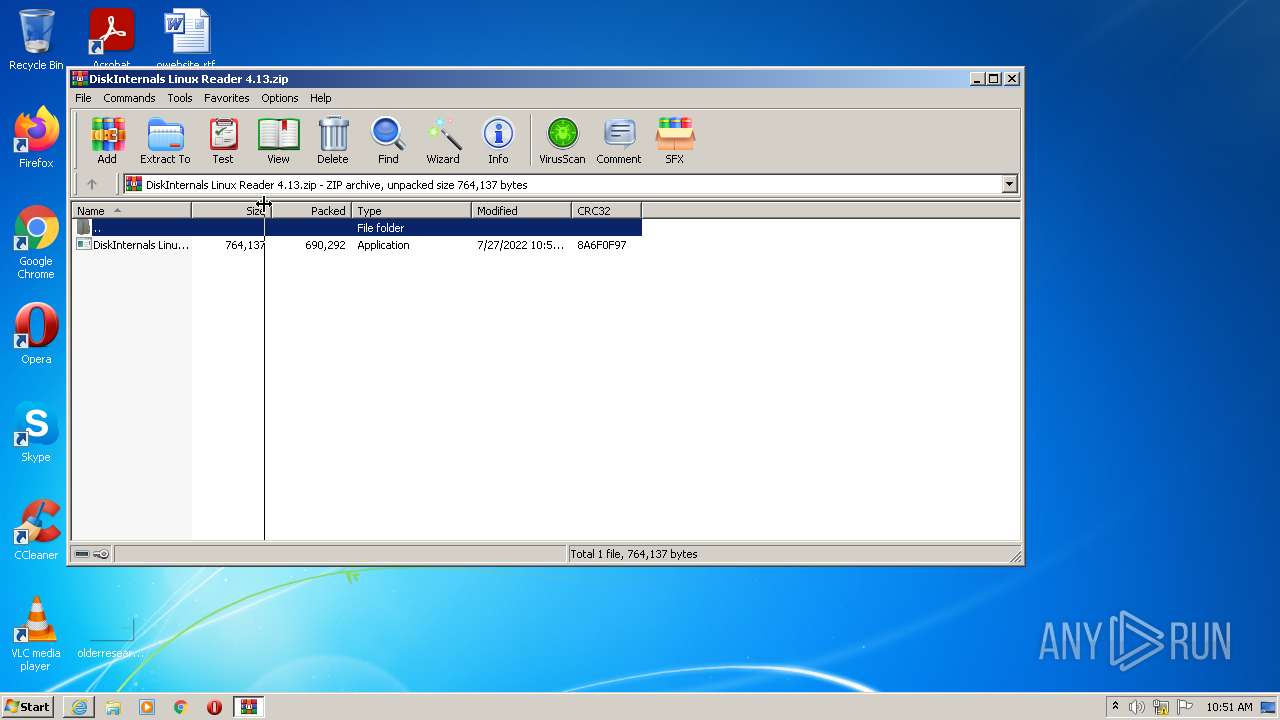
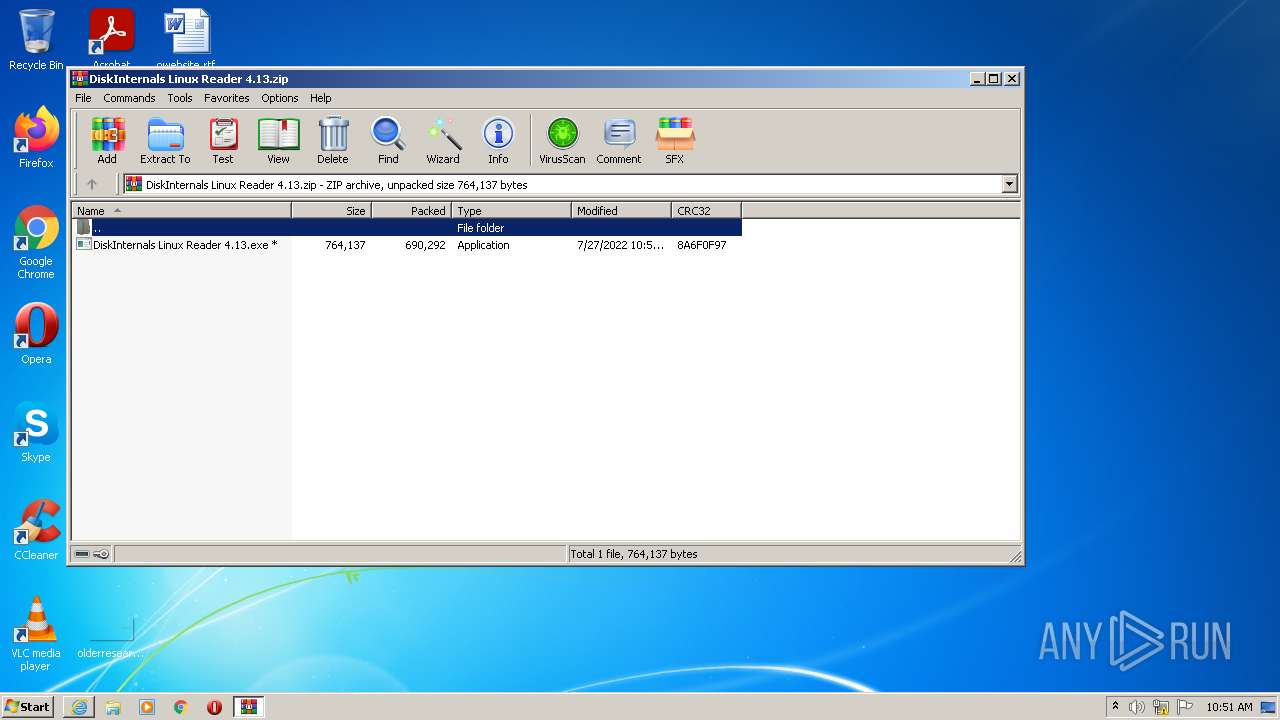
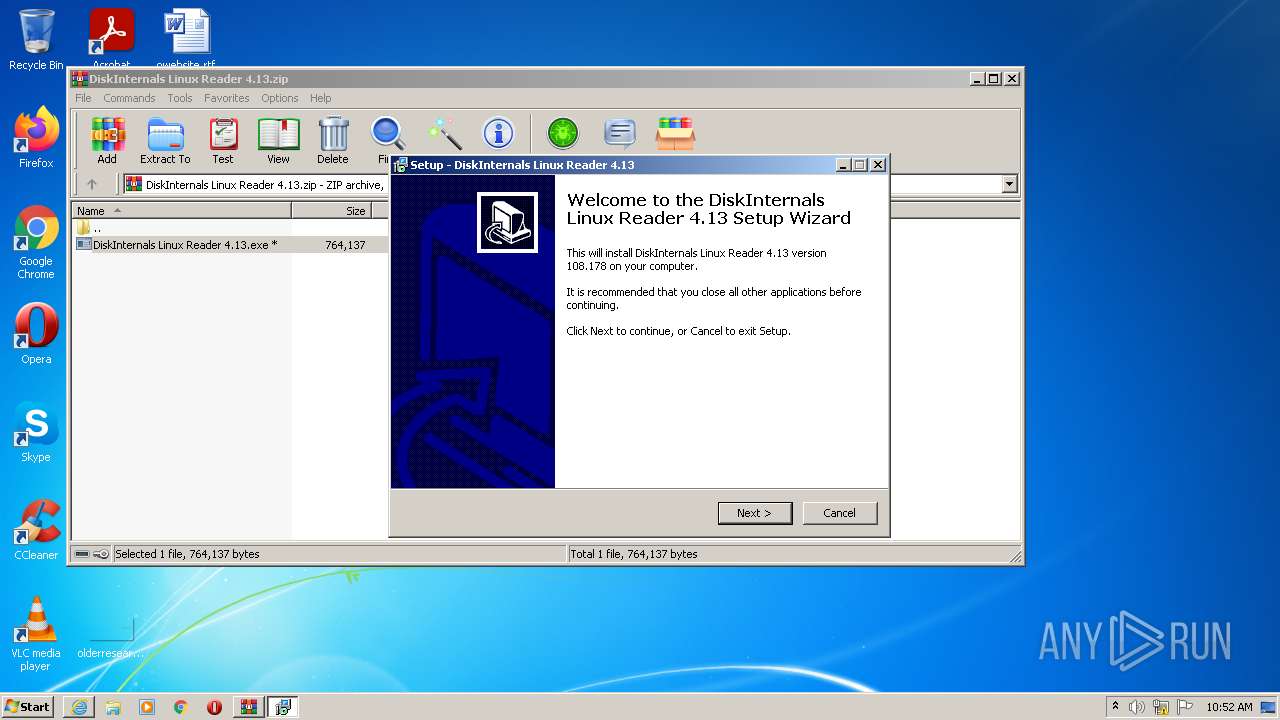
- DiskInternals Linux Reader 4.13.exe (PID: 3464)
- DiskInternals Linux Reader 4.13.exe (PID: 2032)
- DiskInternals Linux Reader 4.13.tmp (PID: 2372)
- 7za.exe (PID: 632)
Application was dropped or rewritten from another process
- DiskInternals Linux Reader 4.13.exe (PID: 2032)
- DiskInternals Linux Reader 4.13.exe (PID: 3464)
- sitool.exe (PID: 3488)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3532)
- DiskInternals Linux Reader 4.13.tmp (PID: 3500)
- DiskInternals Linux Reader 4.13.tmp (PID: 2372)
- sitool.exe (PID: 3488)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3532)
- DiskInternals Linux Reader 4.13.exe (PID: 3464)
- DiskInternals Linux Reader 4.13.exe (PID: 2032)
- DiskInternals Linux Reader 4.13.tmp (PID: 2372)
- 7za.exe (PID: 632)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3324)
Checks supported languages
- WinRAR.exe (PID: 3532)
- DiskInternals Linux Reader 4.13.exe (PID: 3464)
- DiskInternals Linux Reader 4.13.tmp (PID: 3500)
- DiskInternals Linux Reader 4.13.exe (PID: 2032)
- DiskInternals Linux Reader 4.13.tmp (PID: 2372)
- 7za.exe (PID: 2052)
- 7za.exe (PID: 3148)
- 7za.exe (PID: 632)
- sitool.exe (PID: 3488)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3532)
- DiskInternals Linux Reader 4.13.exe (PID: 3464)
- DiskInternals Linux Reader 4.13.exe (PID: 2032)
- DiskInternals Linux Reader 4.13.tmp (PID: 2372)
- 7za.exe (PID: 632)
Reads Windows owner or organization settings
- DiskInternals Linux Reader 4.13.tmp (PID: 2372)
Reads the Windows organization settings
- DiskInternals Linux Reader 4.13.tmp (PID: 2372)
Executed via COM
- explorer.exe (PID: 3444)
Reads the date of Windows installation
- explorer.exe (PID: 3444)
INFO
Checks Windows Trust Settings
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 3324)
Checks supported languages
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 3324)
- schtasks.exe (PID: 3228)
- explorer.exe (PID: 3444)
- NOTEPAD.EXE (PID: 1000)
- opera.exe (PID: 2208)
- NOTEPAD.EXE (PID: 2064)
- NOTEPAD.EXE (PID: 3480)
- schtasks.exe (PID: 1536)
- explorer.exe (PID: 1556)
Reads internet explorer settings
- iexplore.exe (PID: 3324)
Reads the computer name
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 3324)
- schtasks.exe (PID: 3228)
- explorer.exe (PID: 1556)
- explorer.exe (PID: 3444)
- opera.exe (PID: 2208)
- schtasks.exe (PID: 1536)
Changes internet zones settings
- iexplore.exe (PID: 2832)
Reads settings of System Certificates
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 3324)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2832)
Application launched itself
- iexplore.exe (PID: 2832)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2832)
Reads the date of Windows installation
- iexplore.exe (PID: 2832)
- opera.exe (PID: 2208)
Changes settings of System certificates
- iexplore.exe (PID: 2832)
Application was dropped or rewritten from another process
- DiskInternals Linux Reader 4.13.tmp (PID: 2372)
- DiskInternals Linux Reader 4.13.tmp (PID: 3500)
- 7za.exe (PID: 632)
- 7za.exe (PID: 3148)
- 7za.exe (PID: 2052)
Manual execution by user
- opera.exe (PID: 2208)
Check for Java to be installed
- opera.exe (PID: 2208)
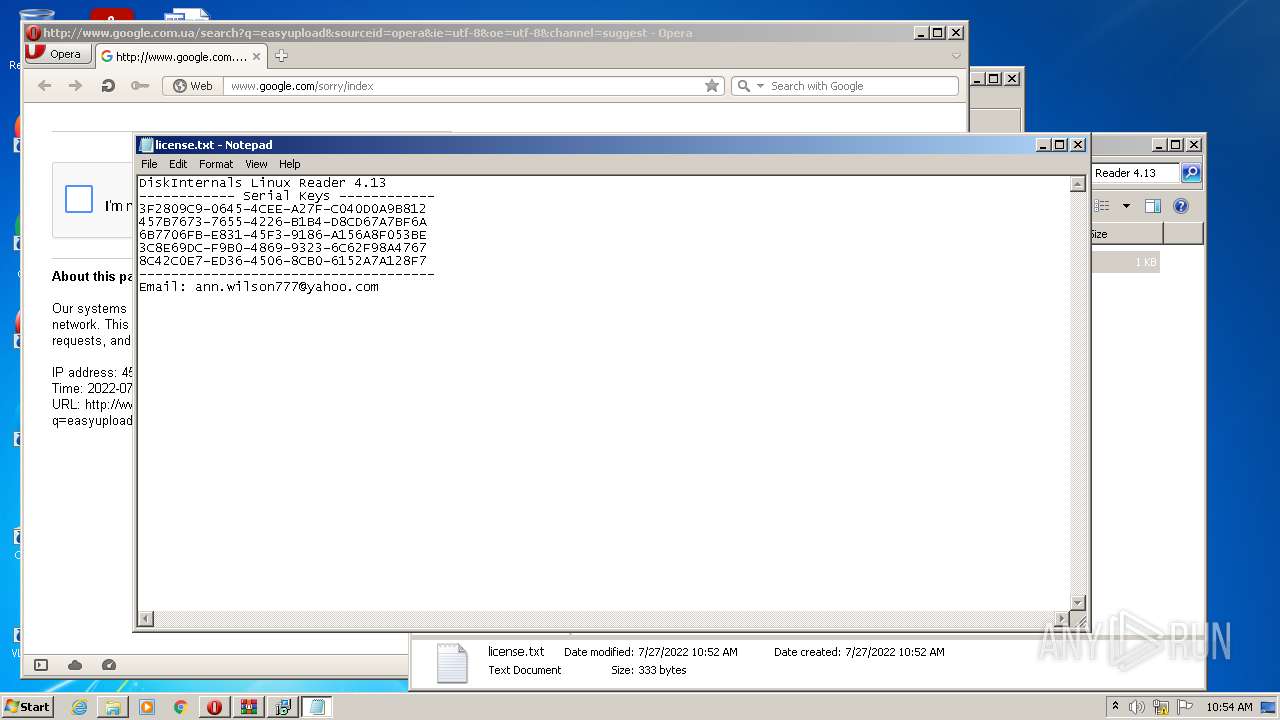
Dropped object may contain Bitcoin addresses
- opera.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
63
Monitored processes
19
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
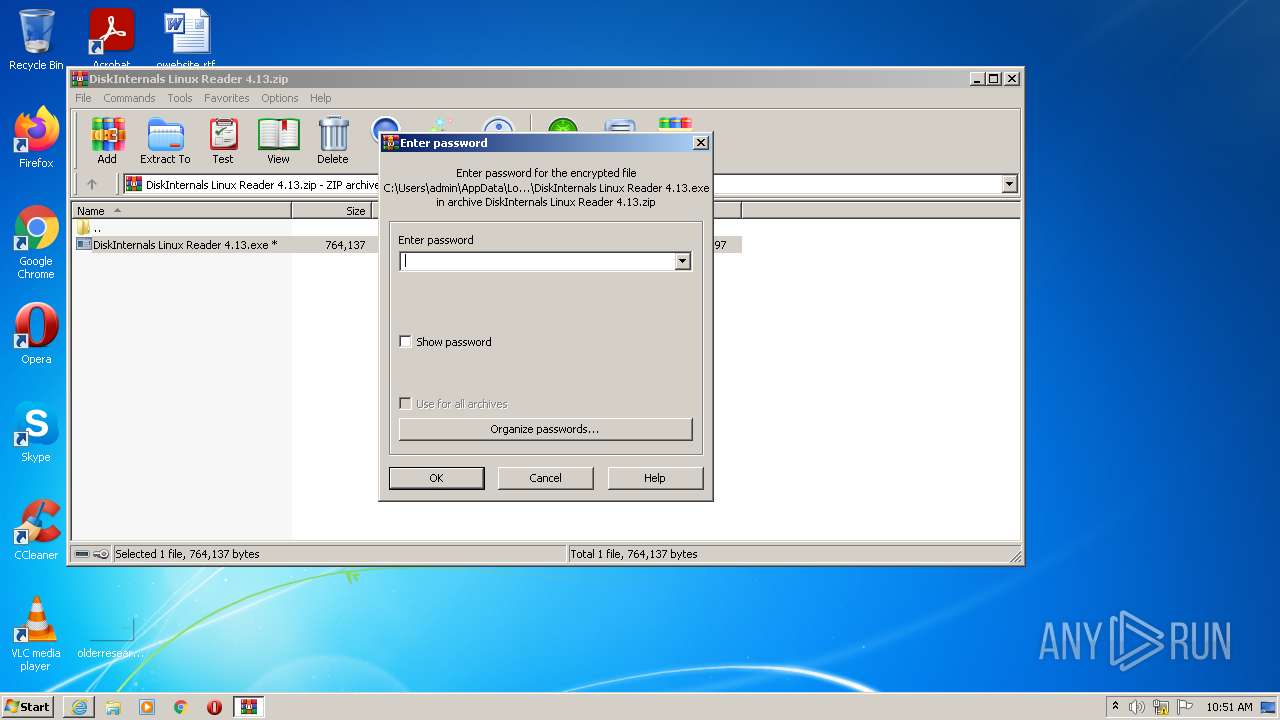
| 632 | "C:\Users\admin\AppData\Local\Temp\is-HBBUR.tmp\7za.exe" x "C:\Users\admin\AppData\Local\Temp\is-HBBUR.tmp\form.res" -p"mSR-@sM1tH" | C:\Users\admin\AppData\Local\Temp\is-HBBUR.tmp\7za.exe | DiskInternals Linux Reader 4.13.tmp | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 4.65 Modules
| |||||||||||||||
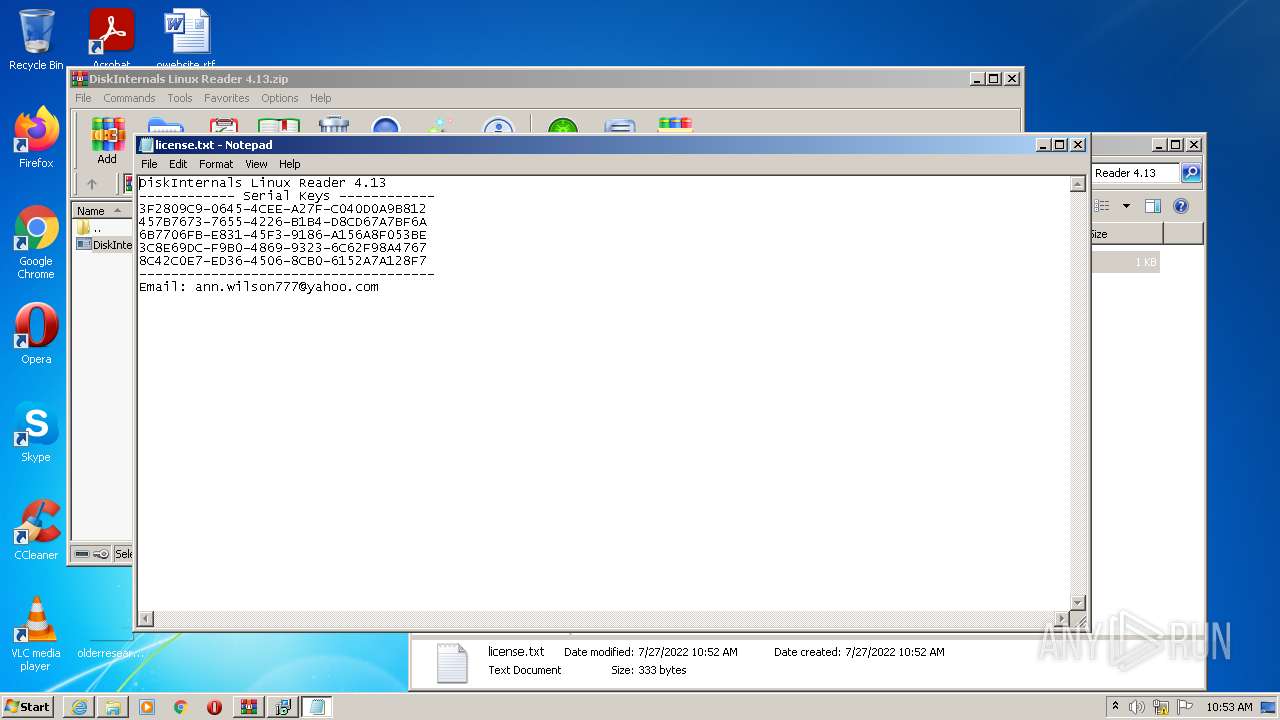
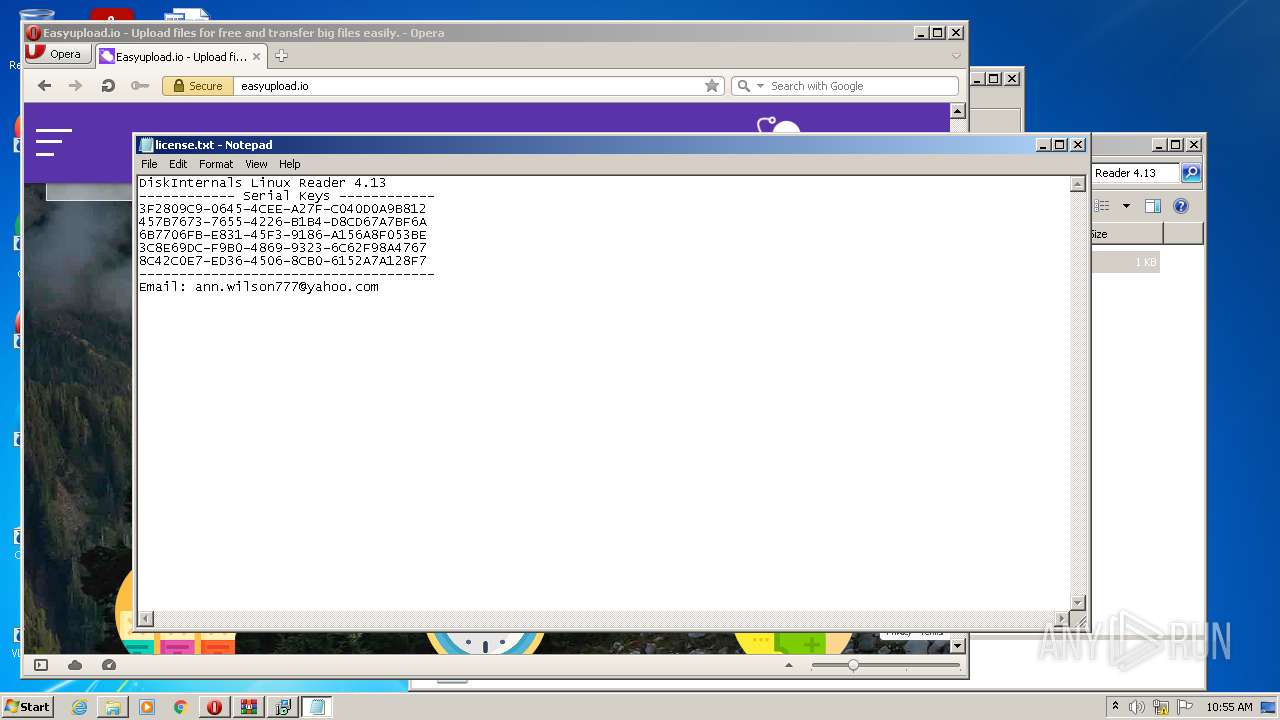
| 1000 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\DiskInternals Linux Reader 4.13\license.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1536 | "C:\Windows\system32\schtasks.exe" /Create /f /XML "C:\Users\admin\AppData\Roaming\SysInfoTool\data.xml" /tn "Microsoft\Windows\Windows Error Reporting\SystemInfo" | C:\Windows\system32\schtasks.exe | — | sitool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | "explorer.exe" "C:\Users\admin\Desktop\DiskInternals Linux Reader 4.13" | C:\Windows\explorer.exe | — | DiskInternals Linux Reader 4.13.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
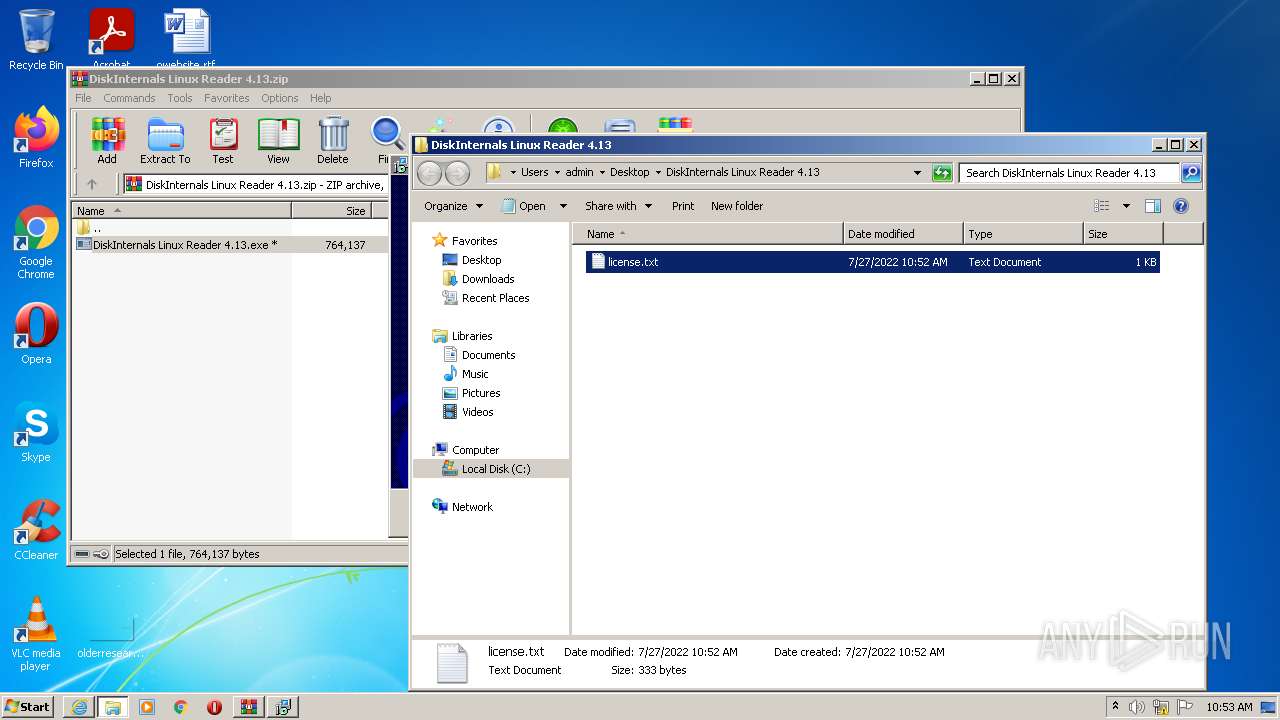
| 2032 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3532.13626\DiskInternals Linux Reader 4.13.exe" /SPAWNWND=$30170 /NOTIFYWND=$4014C | C:\Users\admin\AppData\Local\Temp\Rar$EXb3532.13626\DiskInternals Linux Reader 4.13.exe | DiskInternals Linux Reader 4.13.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Exit code: 0 Version: 108.178 Modules
| |||||||||||||||
| 2052 | "C:\Users\admin\AppData\Local\Temp\is-HBBUR.tmp\7za.exe" x "C:\Users\admin\AppData\Local\Temp\is-HBBUR.tmp\misc.res" -p"mSR-@sM1tH" | C:\Users\admin\AppData\Local\Temp\is-HBBUR.tmp\7za.exe | — | DiskInternals Linux Reader 4.13.tmp | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 4.65 Modules
| |||||||||||||||
| 2064 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\DiskInternals Linux Reader 4.13\license.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | Explorer.EXE | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
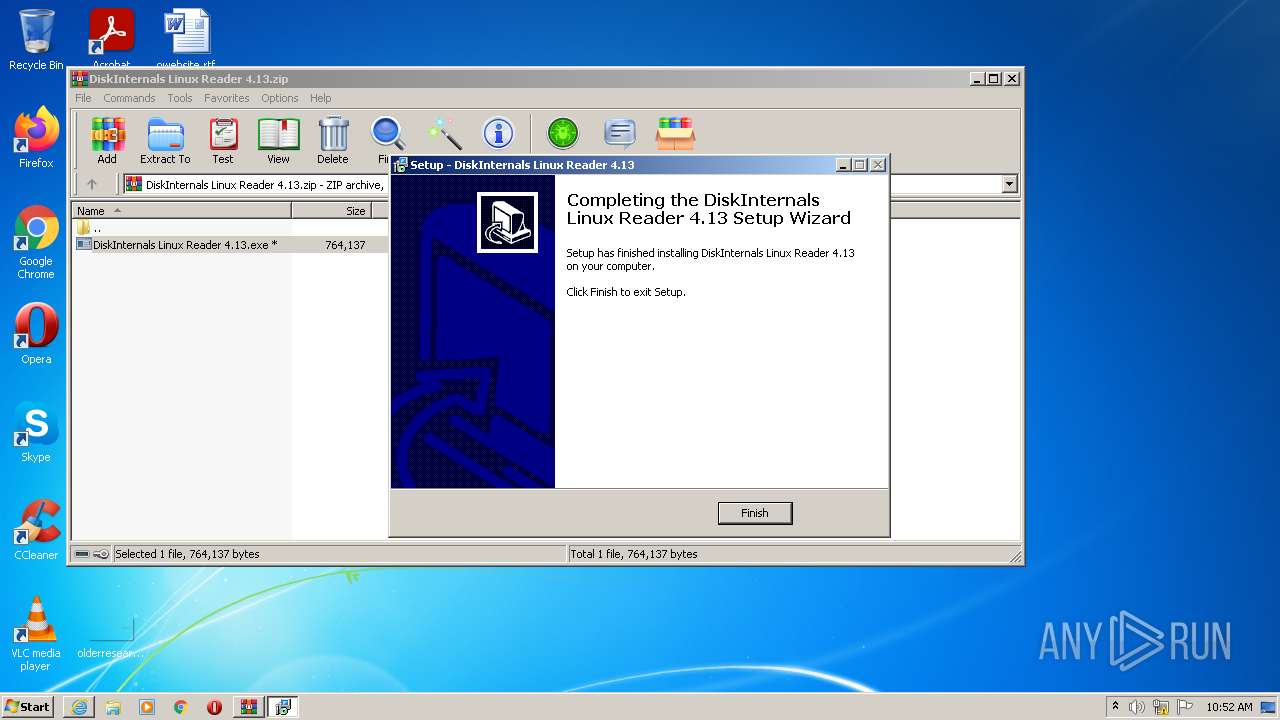
| 2372 | "C:\Users\admin\AppData\Local\Temp\is-1KNGS.tmp\DiskInternals Linux Reader 4.13.tmp" /SL5="$40158,373666,121344,C:\Users\admin\AppData\Local\Temp\Rar$EXb3532.13626\DiskInternals Linux Reader 4.13.exe" /SPAWNWND=$30170 /NOTIFYWND=$4014C | C:\Users\admin\AppData\Local\Temp\is-1KNGS.tmp\DiskInternals Linux Reader 4.13.tmp | DiskInternals Linux Reader 4.13.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2832 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://free2pc.site/download?id=yA9Ht_bxnnM&s=844D7978" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 979
Read events
19 584
Write events
392
Delete events
3
Modification events
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30974366 | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30974366 | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
6
Suspicious files
103
Text files
160
Unknown types
44
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 3324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 2832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 2832 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{9D4891D2-0D91-11ED-8C9F-1203334A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 2832 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF7A7F84A55C614EBB.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\DiskInternals Linux Reader 4.13.zip.6hl2w22.partial | compressed | |
MD5:— | SHA256:— | |||
| 2832 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\DiskInternals Linux Reader 4.13.zip | compressed | |
MD5:— | SHA256:— | |||
| 3324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\DiskInternals Linux Reader 4.13[1].zip | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
117
DNS requests
47
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3324 | iexplore.exe | GET | 301 | 188.114.97.3:80 | http://free2pc.site/download?id=yA9Ht_bxnnM&s=844D7978 | US | — | — | malicious |
2372 | DiskInternals Linux Reader 4.13.tmp | GET | — | 188.114.97.3:80 | http://worldofbooks.org/getchannel | US | — | — | malicious |
2832 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2208 | opera.exe | GET | 200 | 142.250.186.46:80 | http://clients1.google.com/complete/search?q=abo&client=opera-suggest-omnibox&hl=de | US | text | 142 b | whitelisted |
3324 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2208 | opera.exe | GET | 200 | 142.250.186.46:80 | http://clients1.google.com/complete/search?q=eas&client=opera-suggest-omnibox&hl=de | US | text | 155 b | whitelisted |
2208 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
2832 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
2208 | opera.exe | GET | 200 | 142.250.186.46:80 | http://clients1.google.com/complete/search?q=easyu&client=opera-suggest-omnibox&hl=de | US | text | 157 b | whitelisted |
2208 | opera.exe | GET | 200 | 142.250.186.46:80 | http://clients1.google.com/complete/search?q=easyupl&client=opera-suggest-omnibox&hl=de | US | text | 164 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3324 | iexplore.exe | 188.114.97.3:80 | free2pc.site | Cloudflare Inc | US | malicious |
3324 | iexplore.exe | 188.114.97.3:443 | free2pc.site | Cloudflare Inc | US | malicious |
2832 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2832 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2832 | iexplore.exe | 96.16.143.41:443 | go.microsoft.com | Akamai International B.V. | US | whitelisted |
2208 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2208 | opera.exe | 142.250.186.46:80 | clients1.google.com | Google Inc. | US | whitelisted |
2208 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2832 | iexplore.exe | 131.253.33.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
2832 | iexplore.exe | 20.25.53.147:443 | query.prod.cms.msn.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
free2pc.site |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2372 | DiskInternals Linux Reader 4.13.tmp | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
2372 | DiskInternals Linux Reader 4.13.tmp | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
2208 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2208 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
4 ETPRO signatures available at the full report