| File name: | GHOSTFUDCRYPTER.exe |
| Full analysis: | https://app.any.run/tasks/732a419e-73bb-49de-93ad-1f4d7aded2fb |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 19:59:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 15 sections |
| MD5: | 513424ED6D555BF357EE44846F510FAF |
| SHA1: | 3C2EE69C49A7D28A7720937D273836293C75DC36 |
| SHA256: | 339A880408B453DF07D35DBA3979144B2CEE3A778BC3906E52D1B72ACAF5B045 |
| SSDEEP: | 49152:BJMr7Nwia8d0JBJm6b7xeJnQ7SN0xD/j285goJ0a/f4h8Rsm/fTyBQif5q5W3iF1:Kq60JBDFeD0xDRBS4D9F0YO/te6xM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Suspicious files were dropped or overwritten
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 4172)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 5024)
Executable content was dropped or overwritten
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 5024)
- GHOSTFUDCRYPTER.exe (PID: 4172)
Executing commands from a ".bat" file
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 4172)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 5024)
Starts CMD.EXE for commands execution
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 4172)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 5024)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5972)
- cmd.exe (PID: 4220)
- cmd.exe (PID: 1184)
- cmd.exe (PID: 524)
Starts application with an unusual extension
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 4172)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 5024)
Write to the desktop.ini file (may be used to cloak folders)
- diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 716)
Reads browser cookies
- diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 716)
Reads the date of Windows installation
- SearchApp.exe (PID: 8052)
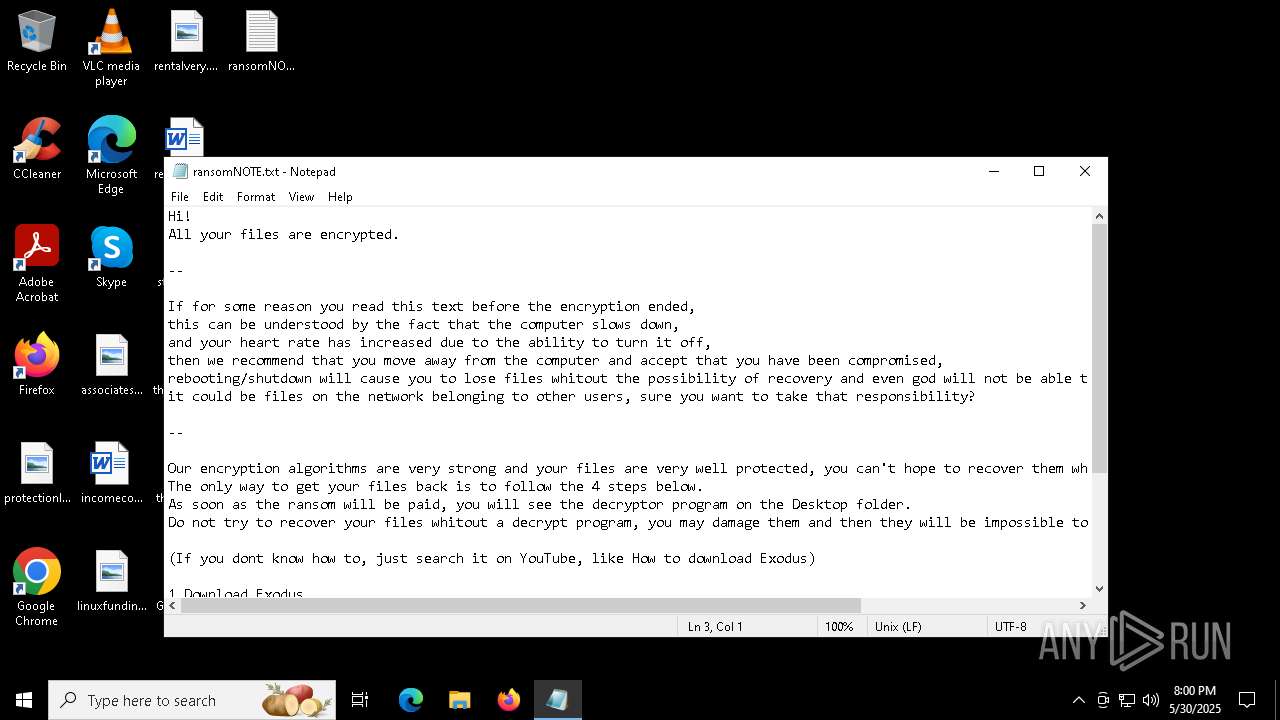
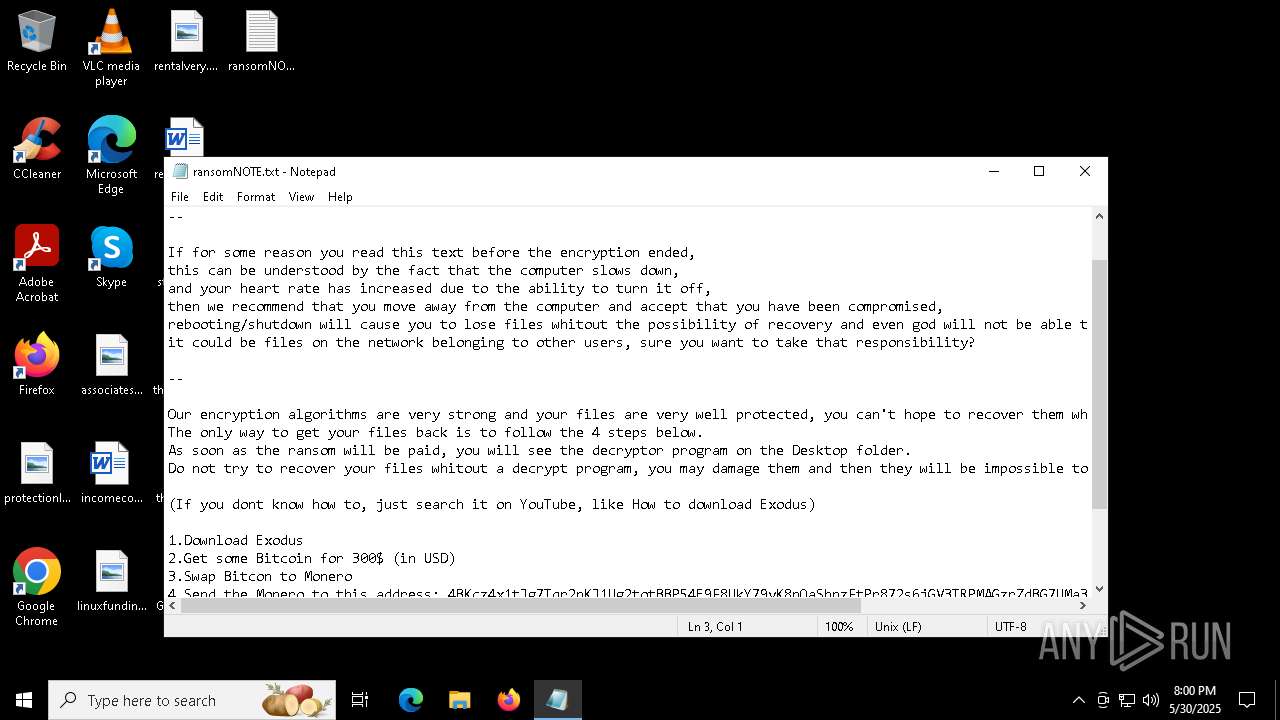
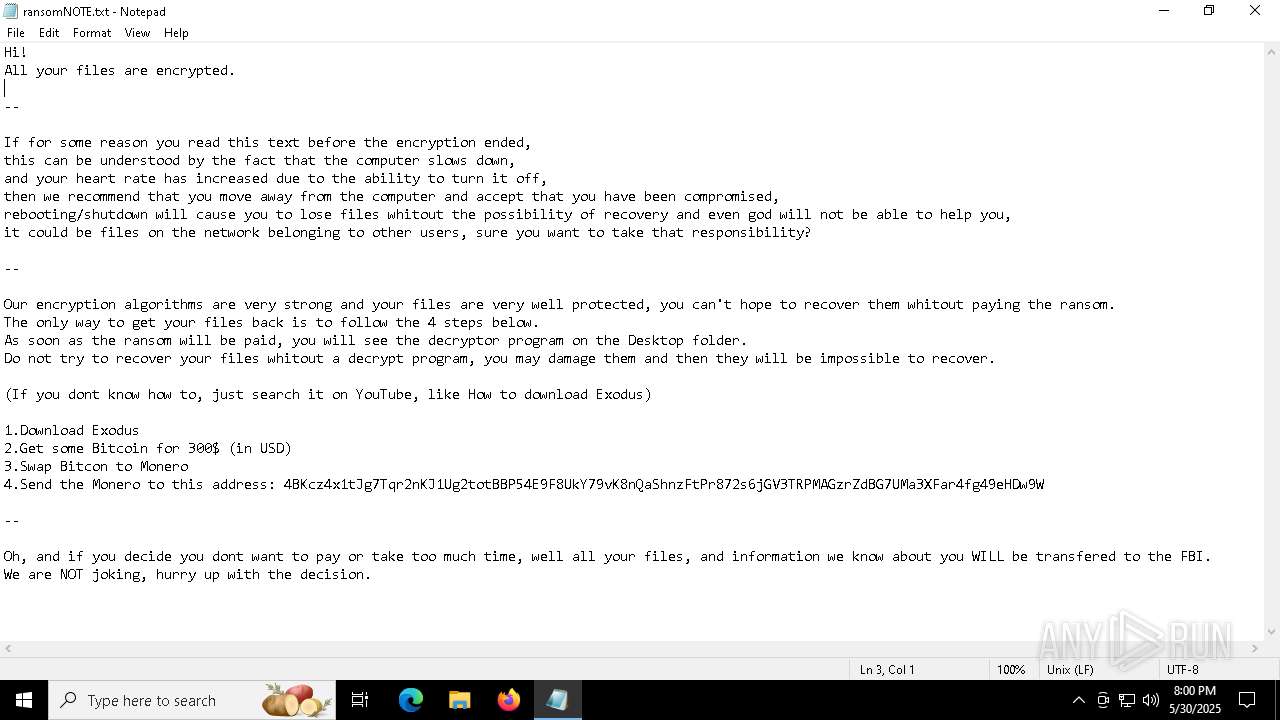
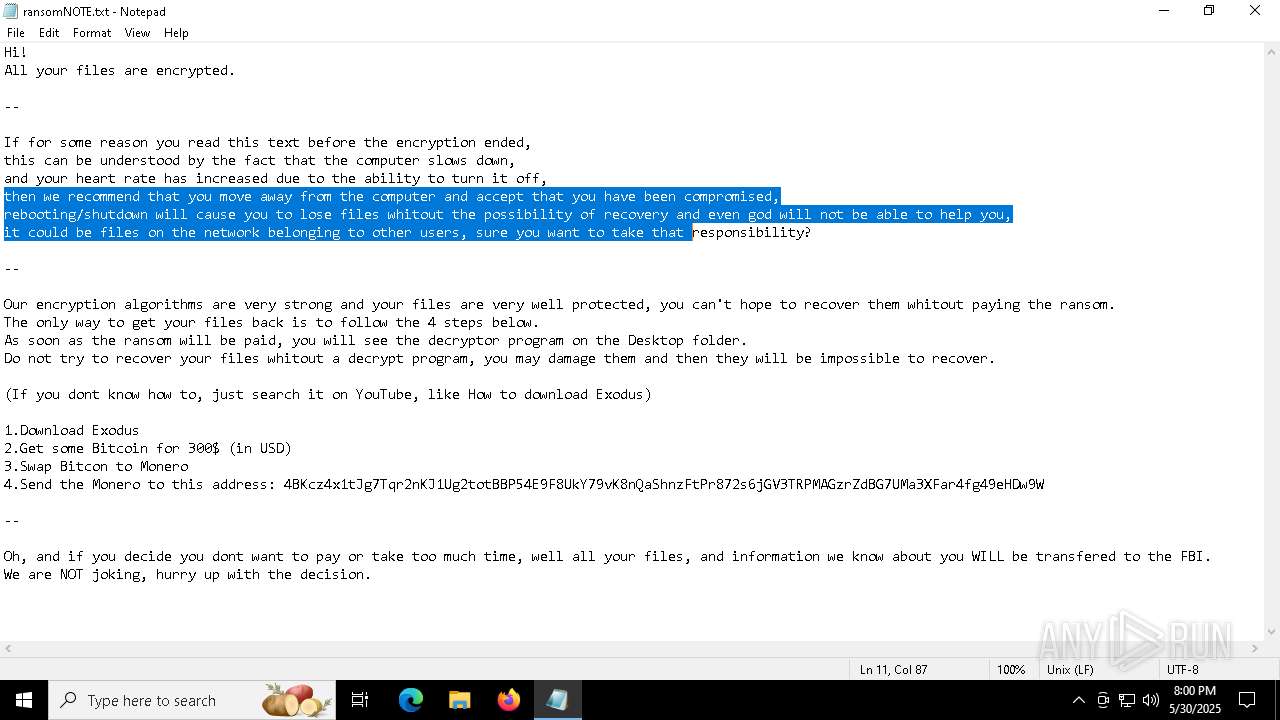
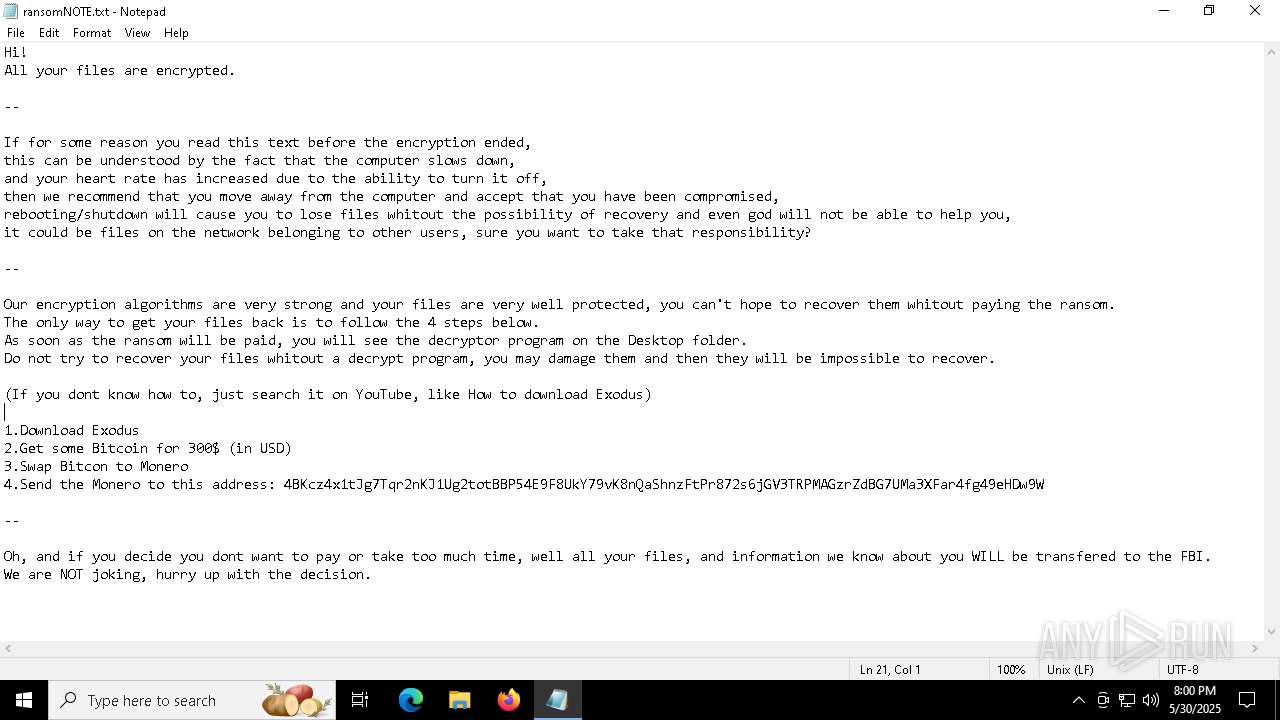
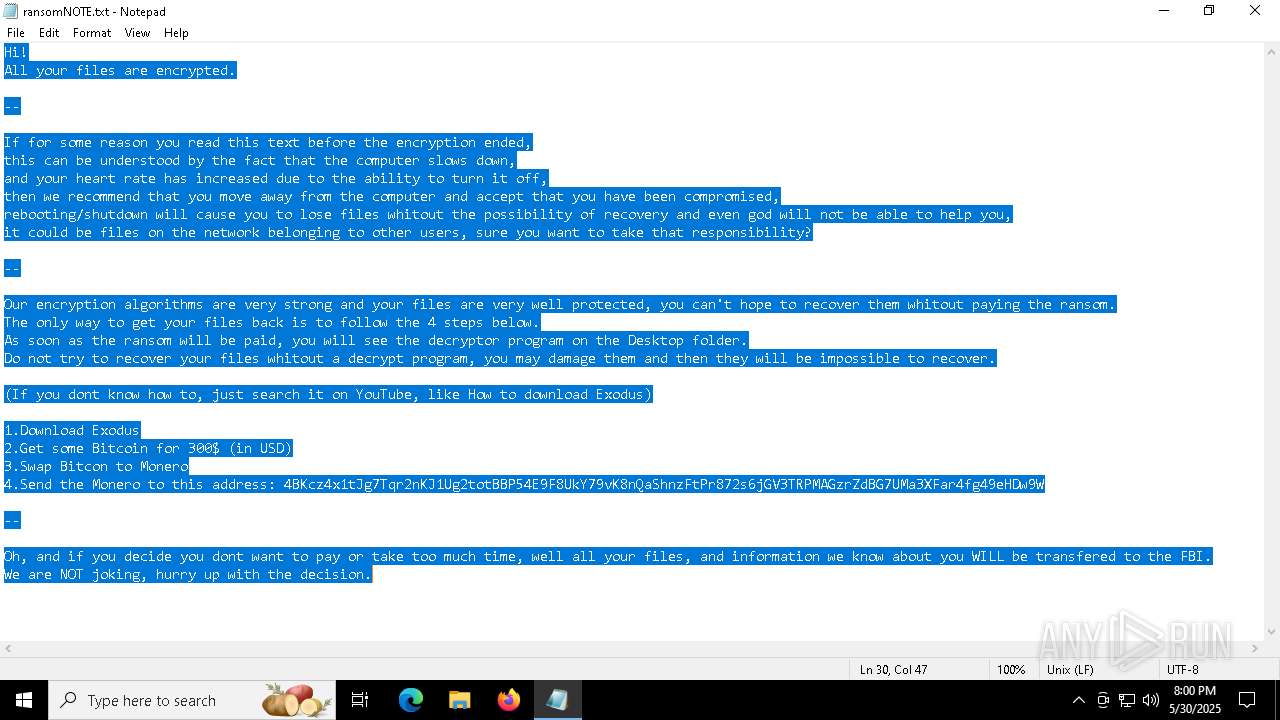
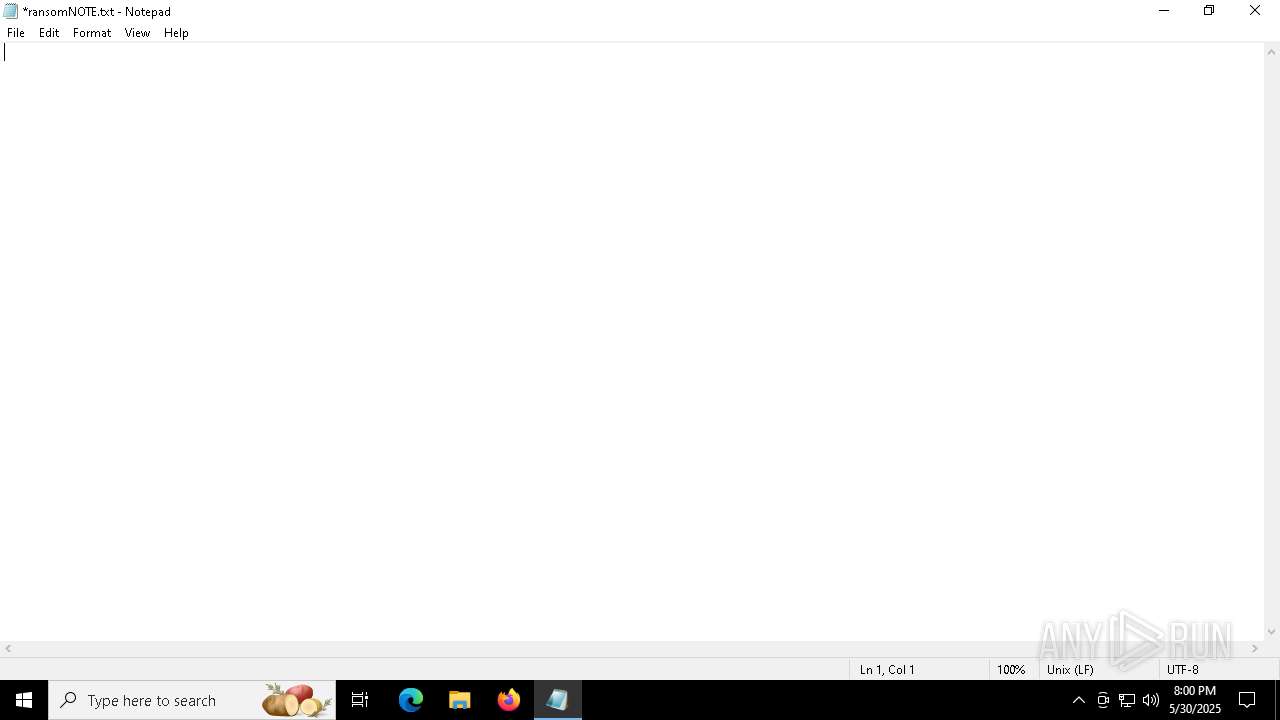
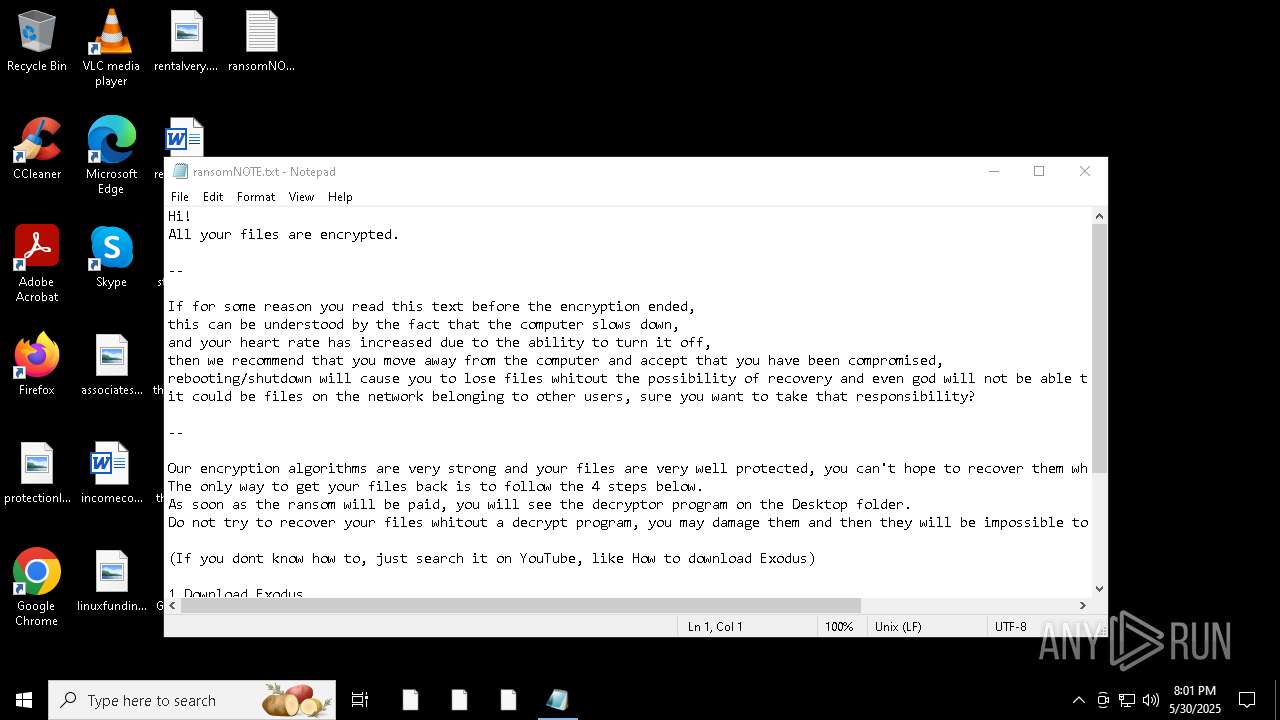
Start notepad (likely ransomware note)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 5024)
INFO
Checks supported languages
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 716)
- SearchApp.exe (PID: 8052)
Drops encrypted JS script (Microsoft Script Encoder)
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
Reads the computer name
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- SearchApp.exe (PID: 8052)
Potential library load (Base64 Encoded 'LoadLibrary')
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 4172)
Application based on Golang
- GHOSTFUDCRYPTER.exe (PID: 3784)
- diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 716)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 4172)
Potential modification of remote process state (Base64 Encoded 'SetThreadContext')
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 4172)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- GHOSTFUDCRYPTER.exe (PID: 3784)
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 4172)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat (PID: 6584)
- GHOSTFUDCRYPTER.exe (PID: 3784)
- GHOSTFUDCRYPTER.exe (PID: 4172)
Checks proxy server information
- SearchApp.exe (PID: 8052)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 8052)
Process checks computer location settings
- SearchApp.exe (PID: 8052)
Manual execution by a user
- GHOSTFUDCRYPTER.exe (PID: 4424)
- GHOSTFUDCRYPTER.exe (PID: 6892)
- GHOSTFUDCRYPTER.exe (PID: 4172)
- GHOSTFUDCRYPTER.exe (PID: 1916)
- notepad.exe (PID: 3176)
- Acrobat.exe (PID: 5176)
- notepad.exe (PID: 7560)
- GHOSTFUDCRYPTER.exe (PID: 7548)
Application launched itself
- Acrobat.exe (PID: 5176)
- AcroCEF.exe (PID: 924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 740352 |
| InitializedDataSize: | 59904 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x652c0 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
Total processes
165
Monitored processes
40
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | cmd /C "attrib +h C:\Users\admin\Downloads\diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat" | C:\Windows\System32\cmd.exe | — | adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 716 | C:\Users\admin\Downloads\diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\Downloads\diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | — | adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1184 | cmd /C "attrib +h C:\Users\admin\Downloads\adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat" | C:\Windows\System32\cmd.exe | — | GHOSTFUDCRYPTER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1368 | attrib +h C:\Users\admin\Downloads\diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1536 --field-trial-handle=1624,i,18439229285801361789,1957901527609585005,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2148 --field-trial-handle=1624,i,18439229285801361789,1957901527609585005,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1916 | "C:\Users\admin\Desktop\GHOSTFUDCRYPTER.exe" | C:\Users\admin\Desktop\GHOSTFUDCRYPTER.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2432 | attrib +h C:\Users\admin\Downloads\diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 044
Read events
29 373
Write events
652
Delete events
19
Modification events
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState |
| Operation: | write | Name: | ShouldShowCombinedConsent |
Value: 01A6F35C699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState |
| Operation: | write | Name: | ShouldUnregisterAllBackgroundTasks |
Value: 0142435D699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState |
| Operation: | write | Name: | CortanaCapabilities |
Value: 0000000042435D699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState |
| Operation: | write | Name: | RPSServerBing |
Value: 63006F007200740061006E0061002E00620069006E0067002E0063006F006D00000042435D699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState |
| Operation: | write | Name: | RPSServerLive |
Value: 730073006C002E006C006900760065002E0063006F006D00000042435D699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState\OnlineServices |
| Operation: | write | Name: | UseTestServer |
Value: 00000000946A5D699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState\OnlineServices\Providers\RulesRequest |
| Operation: | write | Name: | Id |
Value: 1E000000946A5D699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState\OnlineServices\Providers\RulesRequest\HttpRequestCmd |
| Operation: | write | Name: | Id |
Value: 00000000946A5D699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState\OnlineServices\Providers\RulesRequest\HttpRequestCmd |
| Operation: | write | Name: | HeaderTemplate |
Value: 58002D005300650061007200630068002D00490047003A002000250032000D000A0058002D005300650061007200630068002D00550049004C0061006E0067003A002000250033000D000A0058002D005300650061007200630068002D004D00610072006B00650074003A002000250034000D000A0058002D005300650061007200630068002D0043006C00690065006E007400490044003A002000250035000D000A0058002D004100670065006E0074002D00520075006C0065007300560065007200730069006F006E003A002000250036000D000A0058002D004100670065006E0074002D005200650073006F006C007500740069006F006E003A002000250037000D000A0058002D004100670065006E0074002D00440065007600690063006500490064003A002000250038000D000A0058002D0042004D002D004F0045004D003A002000250039000D000A0058002D0042004D002D004D004F003A0020002500310030000D000A0058002D004100670065006E0074002D00500068006F006E0065004F0053005600650072003A0020002500310031000D000A00540069006D0065007A006F006E0065003A0020002500310032000000946A5D699DD1DB01 | |||
| (PID) Process: | (8052) SearchApp.exe | Key: | \REGISTRY\A\{25a74e0d-2cf2-49f7-e112-8395af5e6296}\LocalState\OnlineServices\Providers\RulesRequest\HttpRequestCmd |
| Operation: | write | Name: | ParamCount |
Value: 0C000000946A5D699DD1DB01 | |||
Executable files
28
Suspicious files
2 735
Text files
326
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 716 | diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\DC_Reader_Disc_LHP_Retention | binary | |
MD5:0BC68257028F360AD40120C71A694BC6 | SHA256:662AFA1099E2DE9F090C4530ECCFB47DAD44090E14768952A7791A12421C1D0A | |||
| 716 | diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\DC_FirstMile_Right_Sec_Surface | binary | |
MD5:DA892CDE7D39FDD85A6E003894A859AE | SHA256:6ED275F4D262B64A541F2E8363C41230A1E1DB6233E5FFB59E0156D8F92FEC21 | |||
| 716 | diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:3BFF5D30F30577AC468A30547997451A | SHA256:EDD5C20DB86E80109956175F9042A32034DC43FB550BC9CE4D6C0817CB114881 | |||
| 3784 | GHOSTFUDCRYPTER.exe | C:\Users\admin\Downloads\adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | executable | |
MD5:5A188FE50EF67683FB6DAAFC262A4160 | SHA256:14A3FB3A4B574DE080A528E2B73D286976A6C4CE2400B1F60AE64275F71AD7F5 | |||
| 716 | diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\AppData\Local\Comms\Unistore\data\AggregateCache.uca | binary | |
MD5:76ACCE696DAE04B20E11B110E847E6C4 | SHA256:4F4EF854FBA7FE8C6443BBE5874F918B819B8181D5149ABBFC1A4DA5EA9A73D0 | |||
| 716 | diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\AppData\Local\Comms\UnistoreDB\USS.jcp | binary | |
MD5:D184C3F23DA8DE552FD27F7661E80314 | SHA256:86EC2C7FDA712D7279D90048279D6FCB242DC62009047DA433AB3FD7479238C0 | |||
| 716 | diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\AppData\Local\Adobe\Color\ACECache11.lst | binary | |
MD5:78B297038179147E097BA5EA7DC29576 | SHA256:92B538FC1263821FB24F10A251B6B95F18AD8C5A12B571E98A74549896ABE0E6 | |||
| 716 | diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeCMapFnt23.lst | binary | |
MD5:0C2C09DA3ED5014BEDE1E1E670E1878B | SHA256:A6AFEF6B43B1AD6E6AA989E60D9EC03D37A6F289AAC24A086D7E757BEA2C3EF0 | |||
| 716 | diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\DC_Reader_Disc_LHP_Banner | binary | |
MD5:1BA1865B00CF28DB8A9110ADAED65840 | SHA256:B333A1F95A1FF577BCFE3CA6D497122BC4011CDC4A7B65A6CE9EB733CCEC9818 | |||
| 6584 | adiwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | C:\Users\admin\Downloads\diwejdiowejdoiewdeowedopwedxcmkedtmpScript.bat | executable | |
MD5:1EE63ACF2D06F7BCD3933185C9860D19 | SHA256:D9E2F27AD1C4285A9D71DC5295FCF2E2C194447F0E7456C74CC601202AF7830F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
50
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2516 | svchost.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2516 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8052 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3300 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3300 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8052 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8052 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5024 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2516 | svchost.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2516 | svchost.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |