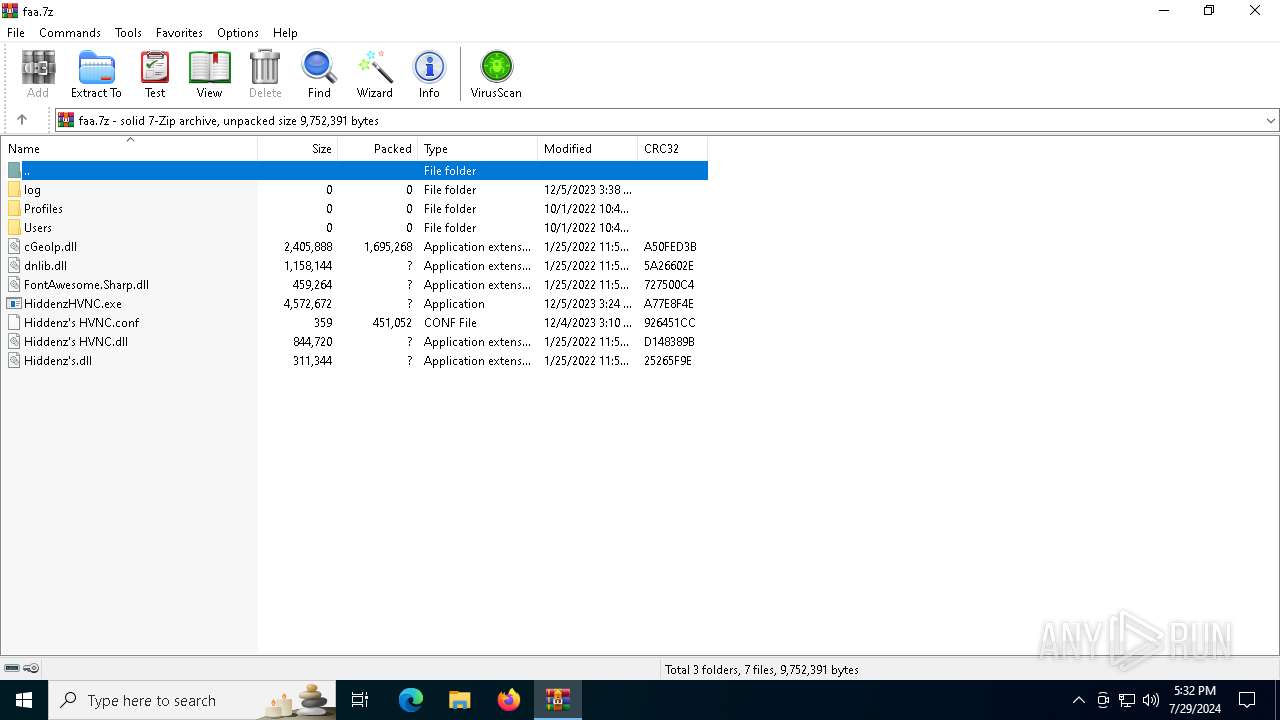
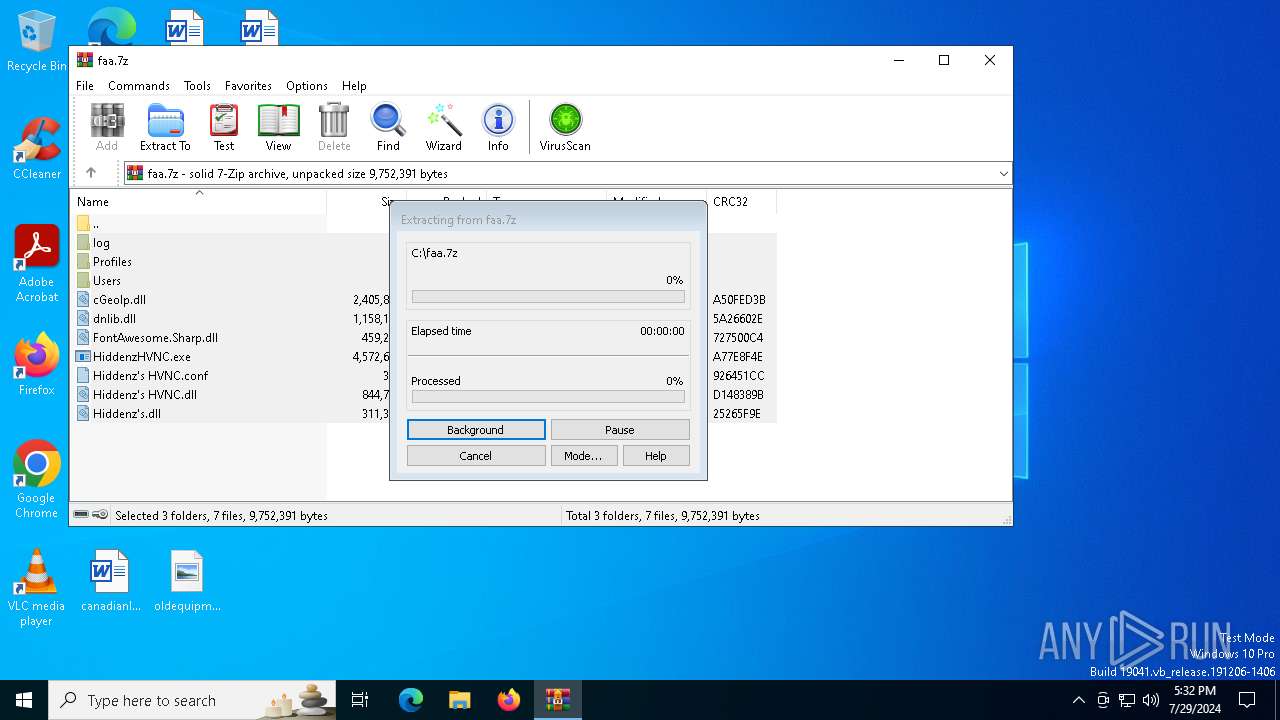
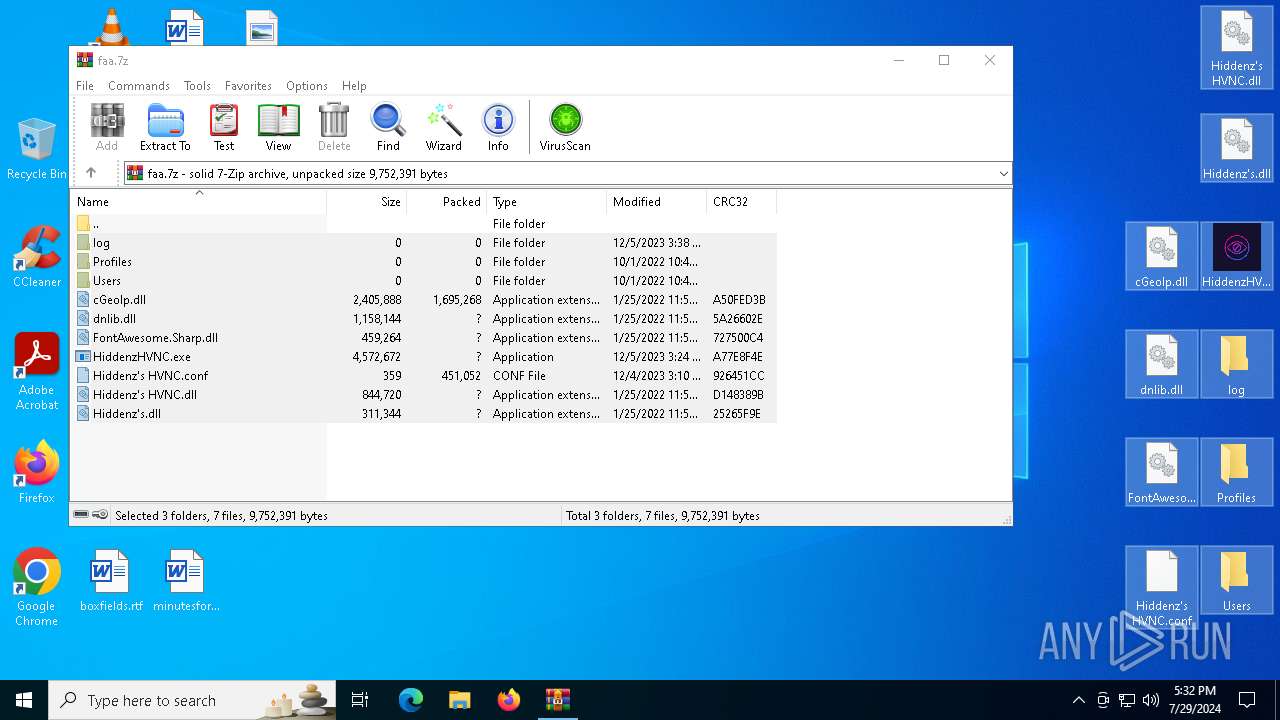
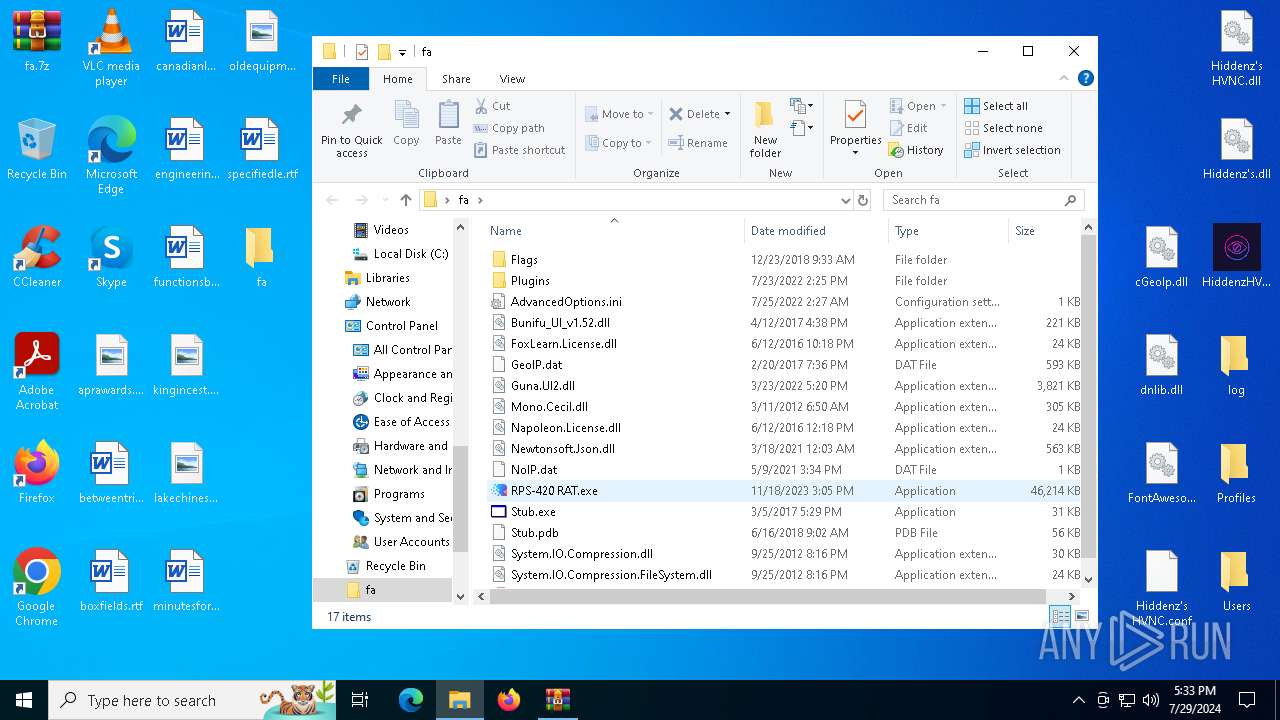
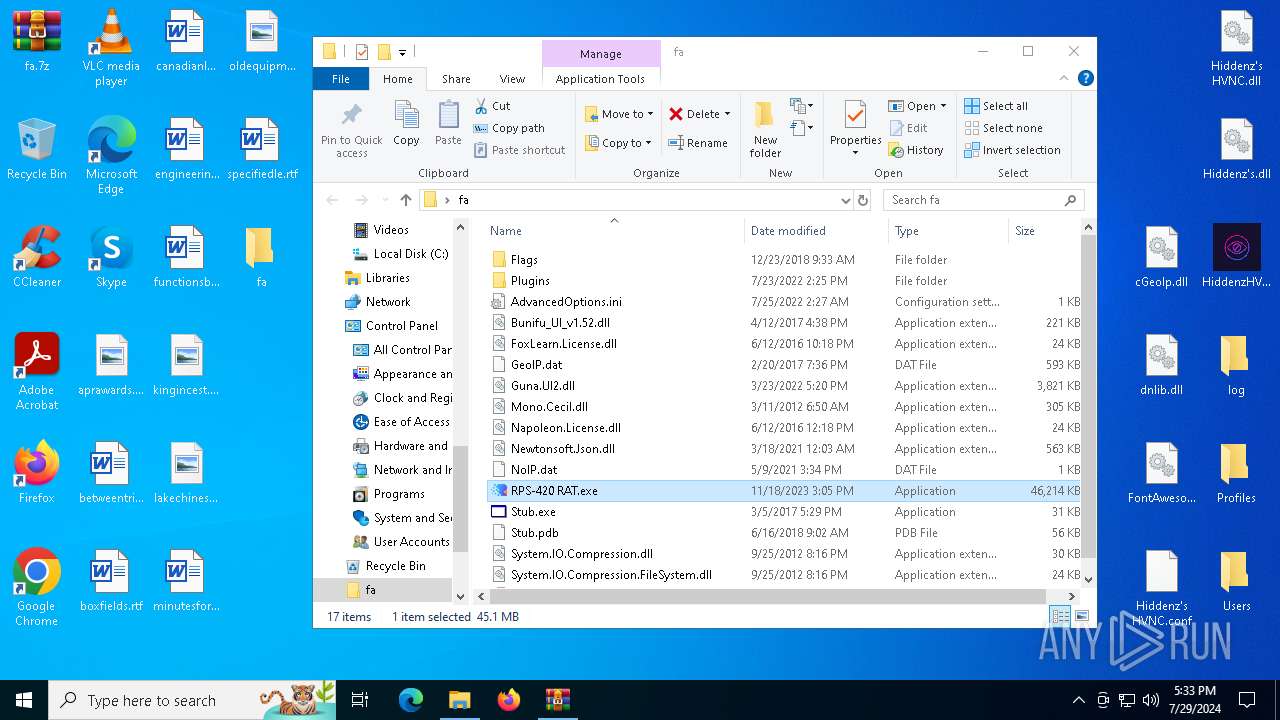
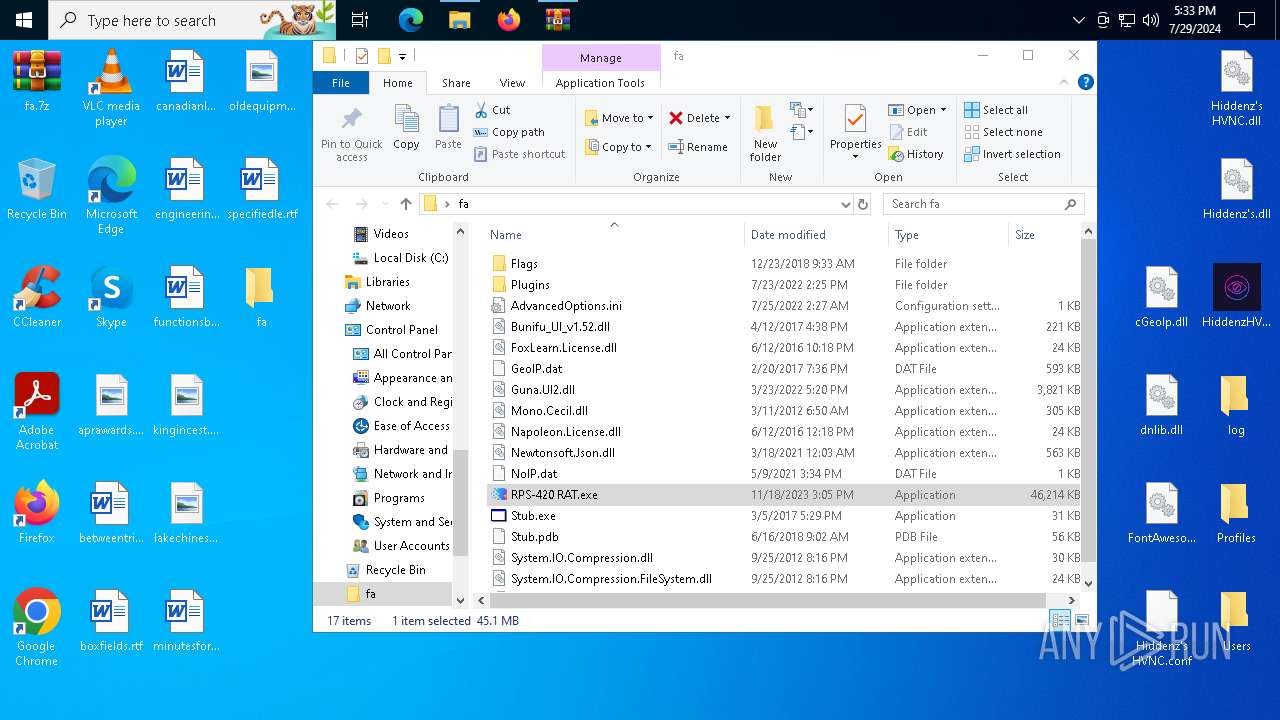
| File name: | faa.7z |
| Full analysis: | https://app.any.run/tasks/7e98b2d5-392e-4967-a9c9-0819e16dcf1b |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2024, 17:32:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A198FEDDD7167C62B242DE19A850351A |
| SHA1: | A7562754AA3B6F6B513EE86B80707986A94D7348 |
| SHA256: | 33923F0ED3C744E43CC216DBB46E1C5E97020A7069C2A8CA8CD5A1B65BD1F20F |
| SSDEEP: | 98304:SYLtr7NHb2Gy71Ob+l8emVMbW1NtWdbXn3rV5QH0BTY04Sm2qMXf7KSYTkpvFgTR:p48jz |
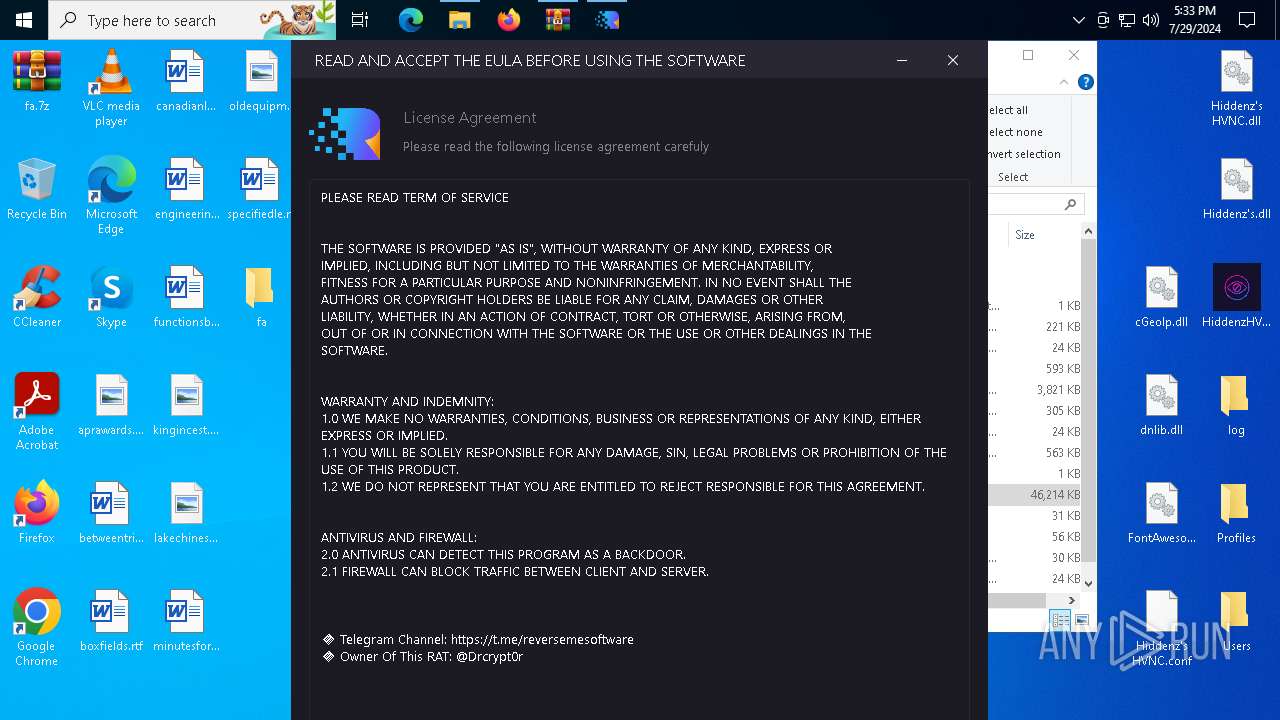
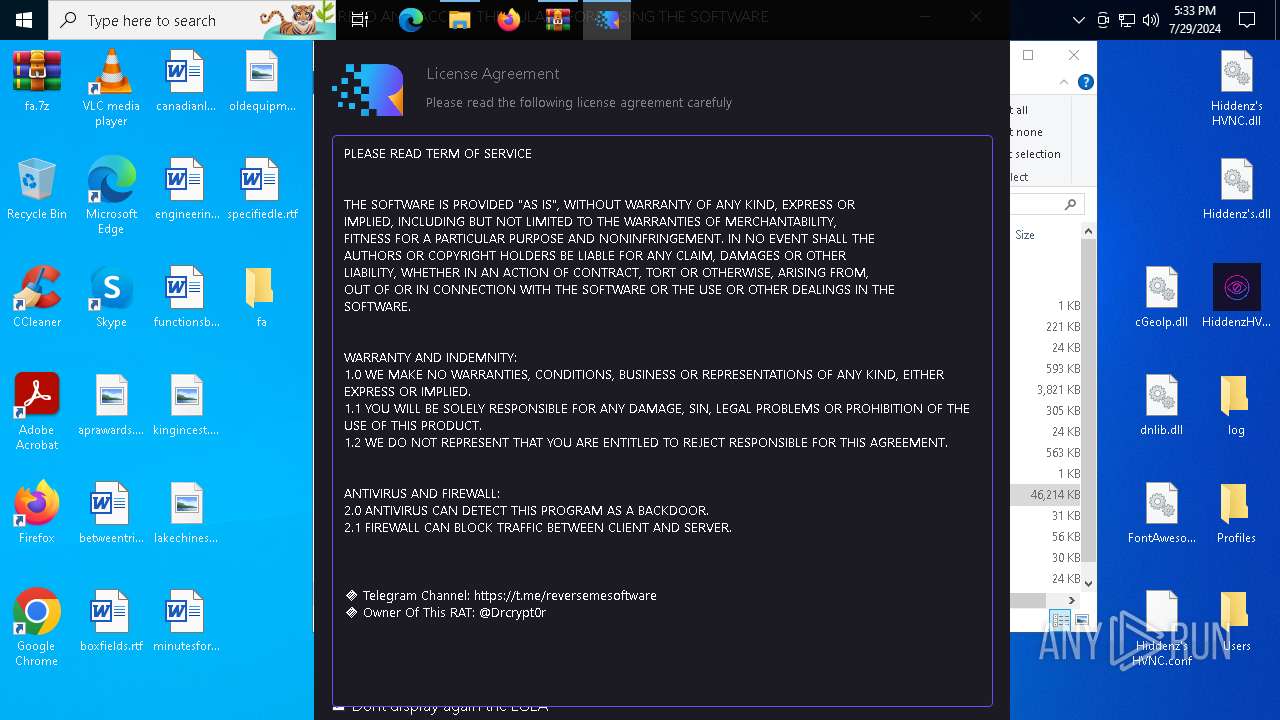
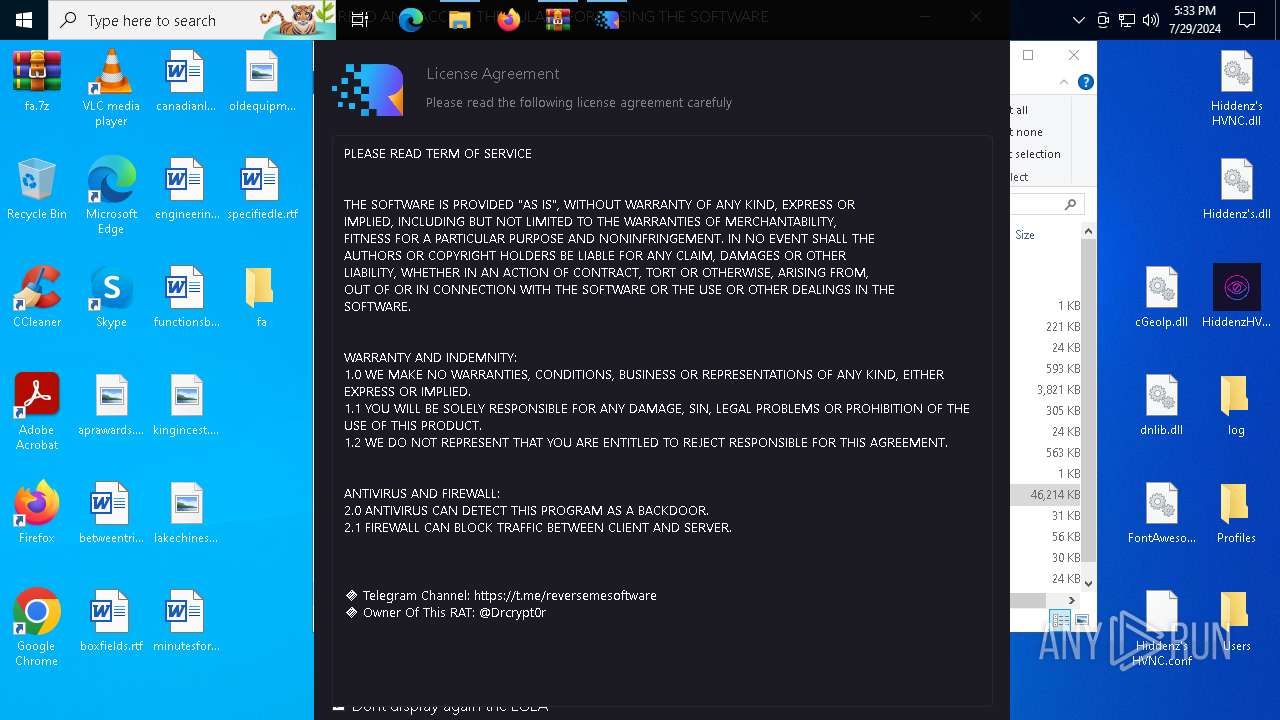
MALICIOUS
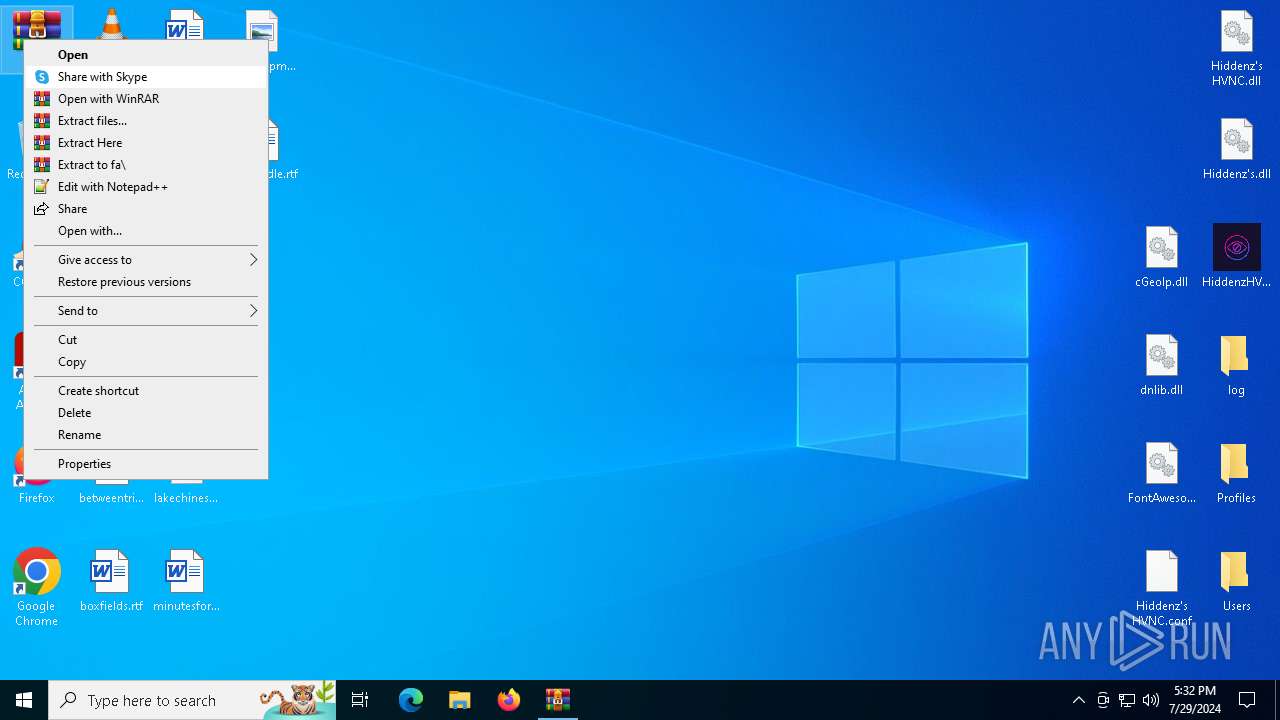
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7032)
SUSPICIOUS
Creates file in the systems drive root
- WinRAR.exe (PID: 7032)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6648)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6648)
The process checks if it is being run in the virtual environment
- RPS-420 RAT.exe (PID: 3108)
Reads the BIOS version
- RPS-420 RAT.exe (PID: 3108)
Reads security settings of Internet Explorer
- RPS-420 RAT.exe (PID: 3108)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7032)
- WinRAR.exe (PID: 6648)
Manual execution by a user
- WinRAR.exe (PID: 6648)
- RPS-420 RAT.exe (PID: 3108)
Reads Environment values
- RPS-420 RAT.exe (PID: 3108)
Disables trace logs
- RPS-420 RAT.exe (PID: 3108)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6648)
Checks supported languages
- RPS-420 RAT.exe (PID: 3108)
Reads the software policy settings
- RPS-420 RAT.exe (PID: 3108)
Reads the computer name
- RPS-420 RAT.exe (PID: 3108)
Reads the machine GUID from the registry
- RPS-420 RAT.exe (PID: 3108)
Checks proxy server information
- RPS-420 RAT.exe (PID: 3108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
141
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3076 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3108 | "C:\Users\admin\Desktop\fa\RPS-420 RAT.exe" | C:\Users\admin\Desktop\fa\RPS-420 RAT.exe | explorer.exe | ||||||||||||
User: admin Company: RPS-420 Integrity Level: MEDIUM Description: RPS-420 RAT Version: 1.0.0.0 Modules
| |||||||||||||||
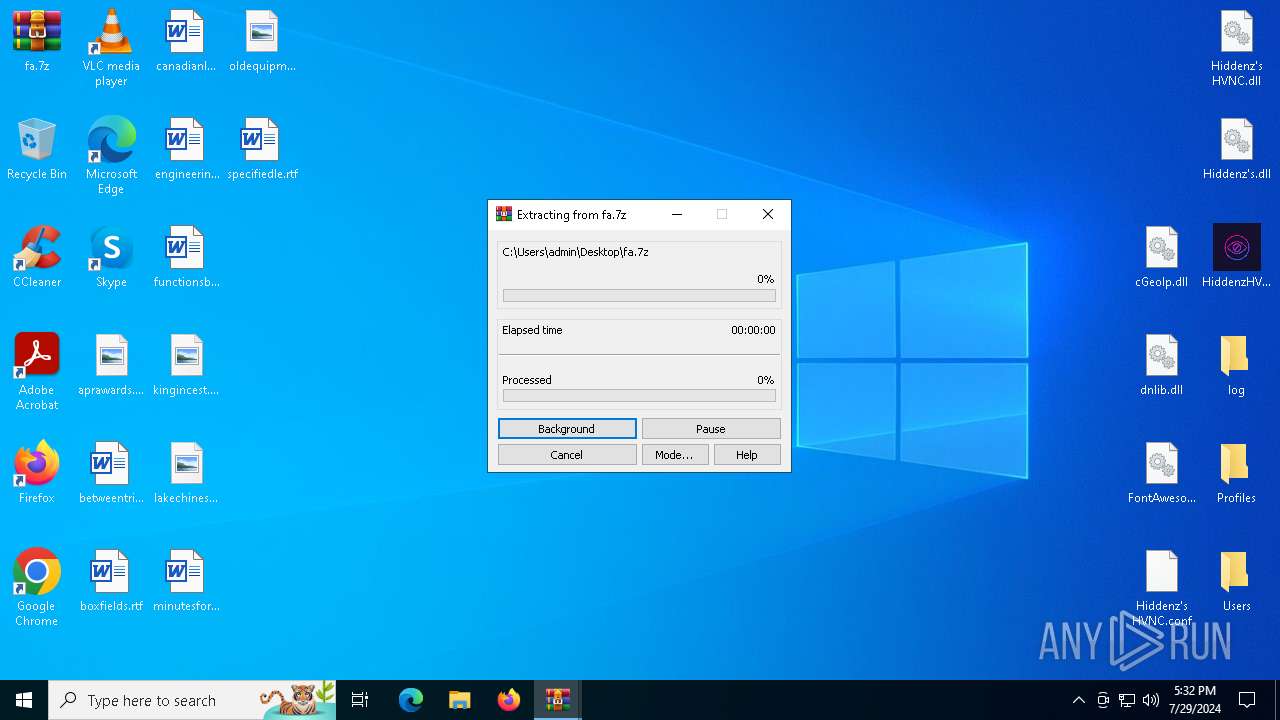
| 6648 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\fa.7z" C:\Users\admin\Desktop\fa\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7032 | "C:\Program Files\WinRAR\WinRAR.exe" C:\faa.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 910
Read events
6 873
Write events
37
Delete events
0
Modification events
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\faa.7z | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
23
Suspicious files
31
Text files
257
Unknown types
1
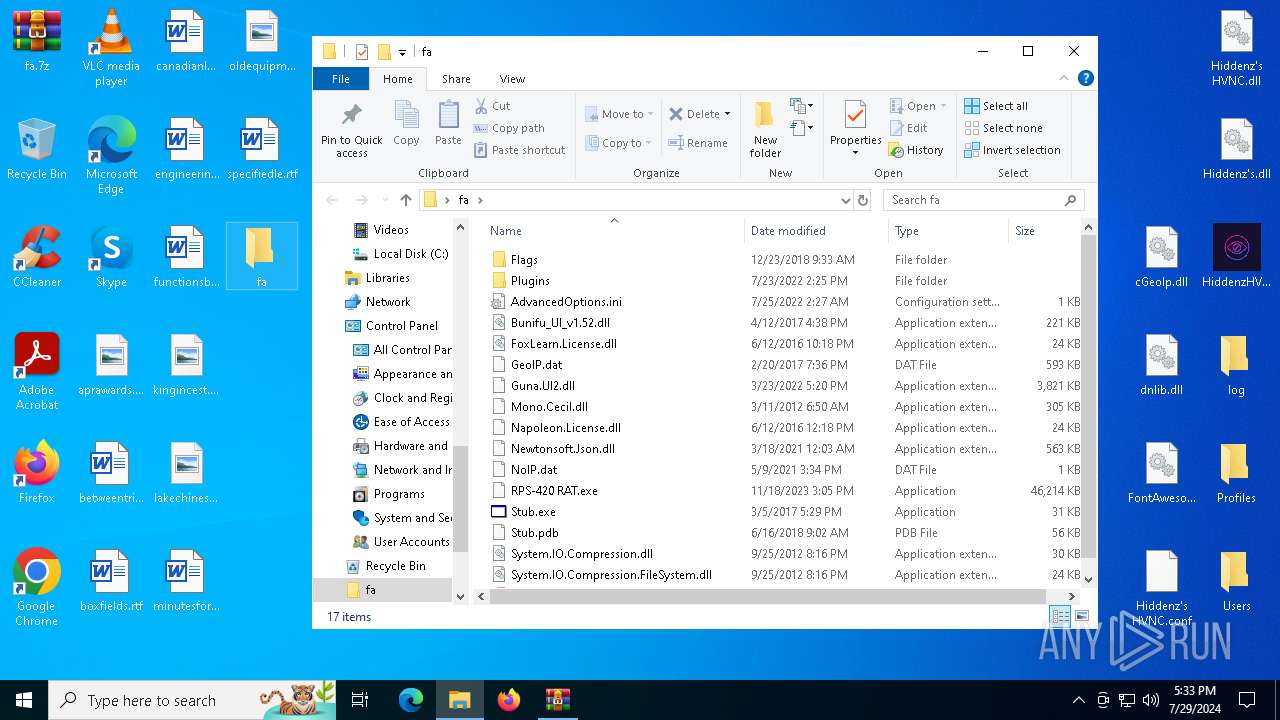
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\fa\AdvancedOptions.ini | text | |
MD5:0313B427BB08C8B24A0E9EDFC6099ACD | SHA256:9F4F5F60426010DB2165D2F5C0F6069F96B056DC7F1E264432B98B09FE0B81BD | |||
| 7032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7032.15474\FontAwesome.Sharp.dll | executable | |
MD5:F47EB5427819C89DBE76F392BE46AA95 | SHA256:02AFB53D63005AD511A7FB8C2F7A41D68ED83FD41F15AEF3C491F1E87B095C8E | |||
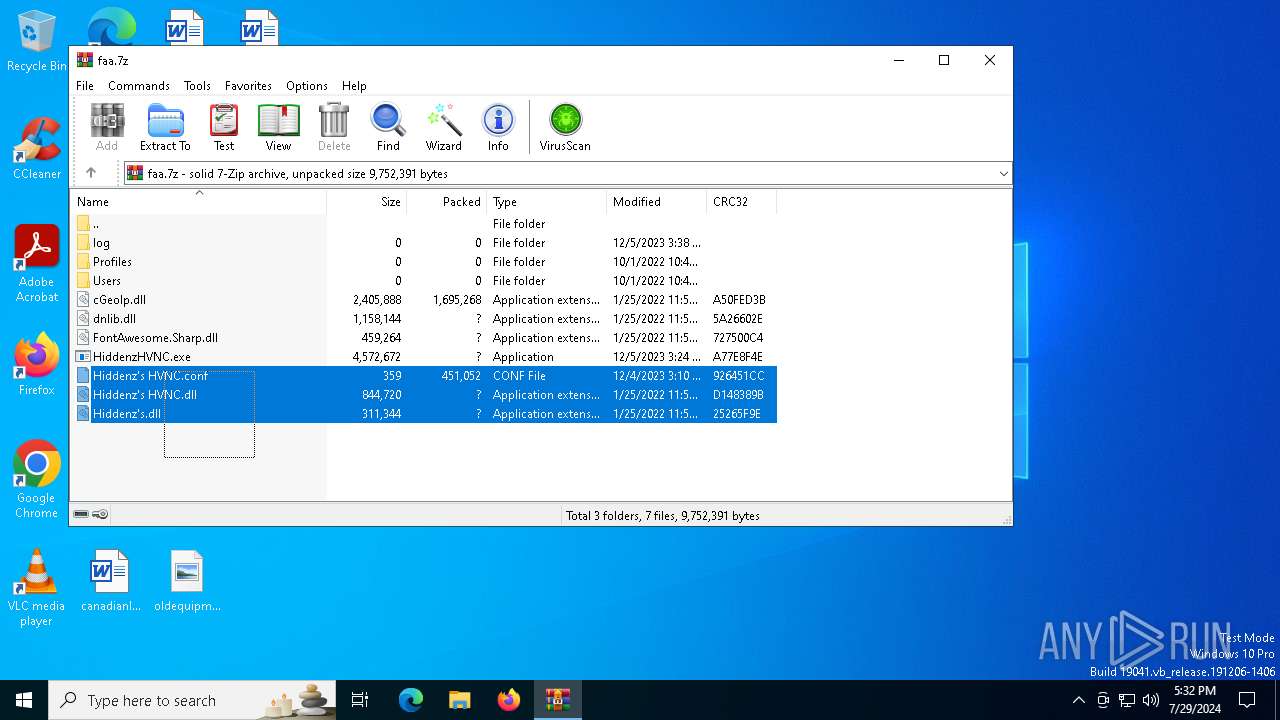
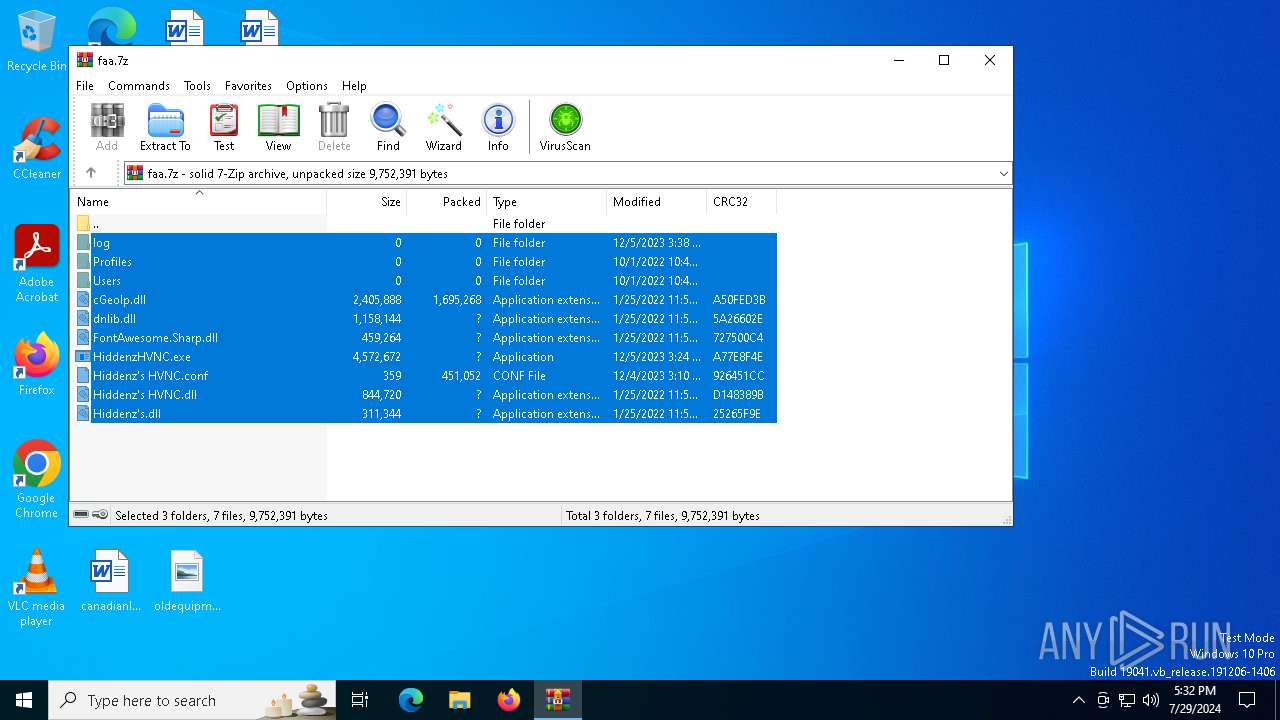
| 7032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7032.15474\Hiddenz's HVNC.dll | binary | |
MD5:F6B210209A44D2D04D2A246CAABB4A45 | SHA256:3A09193B6DEBE1C9BE2B16CAD932450E2D407F233A720C2B435A9F73FCC0E452 | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\fa\Flags\--.png | image | |
MD5:DF38A5600F8BF82663B45BD483E47D1D | SHA256:C327FD59D6016C4DCD90D6F7C388B366EF8954BE80508F57C92A0DE555B5A175 | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\fa\Flags\ae.png | image | |
MD5:09CE31C648D538E45713FFF6BB96E3FA | SHA256:A5F07E254C0564F8C03FEEC2786E7649E751477CA08163744B7419AFB6680534 | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\fa\Flags\ad.png | image | |
MD5:4B5C4F8C7CCC9BC5CF050BC4A00E4A58 | SHA256:EF0CE3874569C00A30083E9D488A0823303D2F8F2C71040F4E7AC83EC92DBC47 | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\fa\Flags\ai.png | image | |
MD5:38EFB57EB0DF9FC5C43700712F0012F4 | SHA256:4649E7E3D4B830ED8AA635B37F36025859295E9D9F1A3941D17793086528BA8B | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\fa\Flags\an.png | image | |
MD5:7F3E5F95255F9DBFD090F287E06F46C8 | SHA256:463E3132A43D367B0B3527B5DF29481DB0E60B03F1A3F71E7508E35932F27E0E | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\fa\Flags\am.png | image | |
MD5:074409791EC9C93471F3FFF0EEA3B9DC | SHA256:CE588159E5633783C01C7CD80085B5464A6F91770AC9C8FAC63F2D0DB1271040 | |||
| 7032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7032.15474\Hiddenz's HVNC.conf | xml | |
MD5:B3700A892091FFA5E7539E6464798576 | SHA256:EA0B13947DB8A8D6633A991C4D87C6FDEC3DF3EE76994B05686D9F653BC2ACC1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
48
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6860 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
996 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 131.253.33.254:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 2.23.209.177:443 | www.bing.com | Akamai International B.V. | GB | unknown |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5900 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6572 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
488 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |