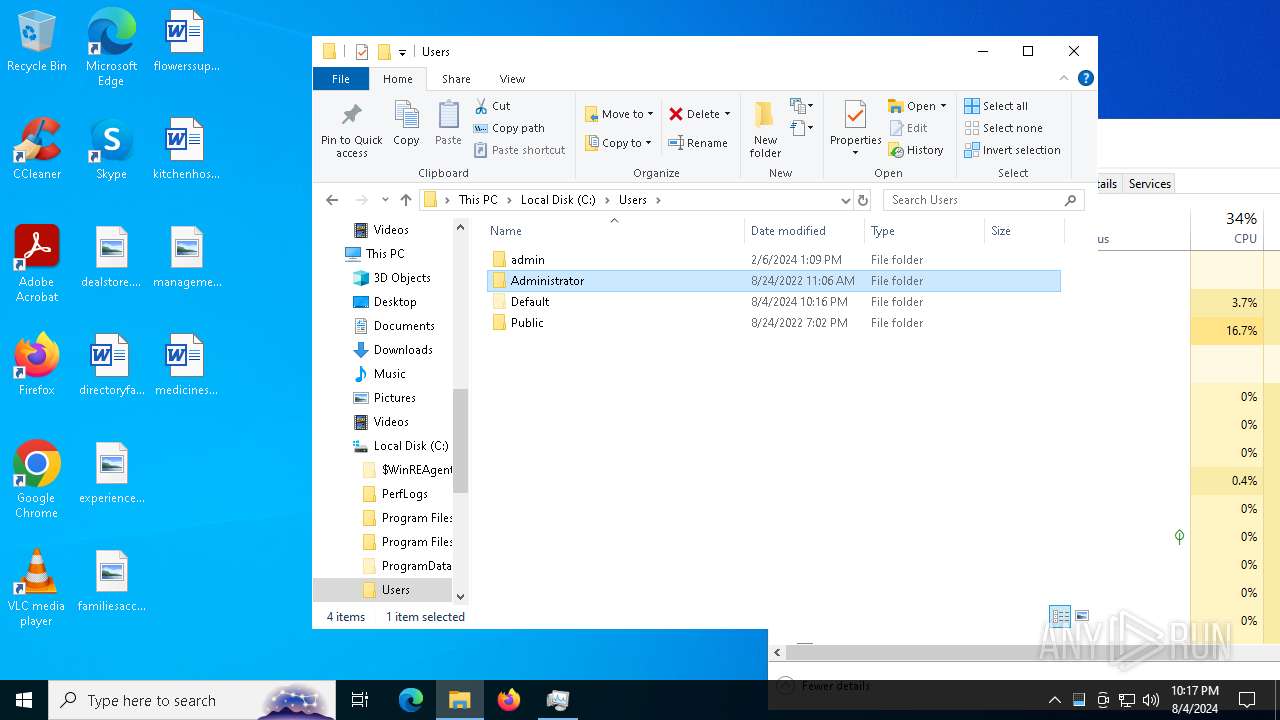
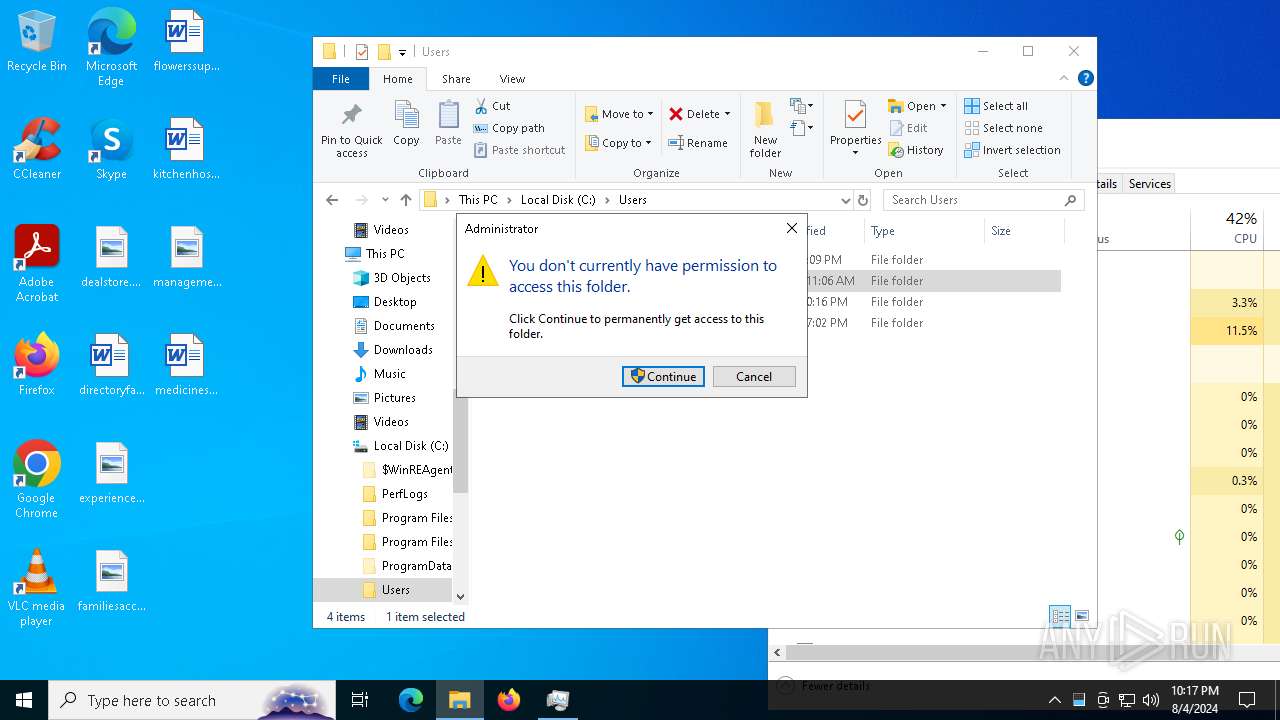
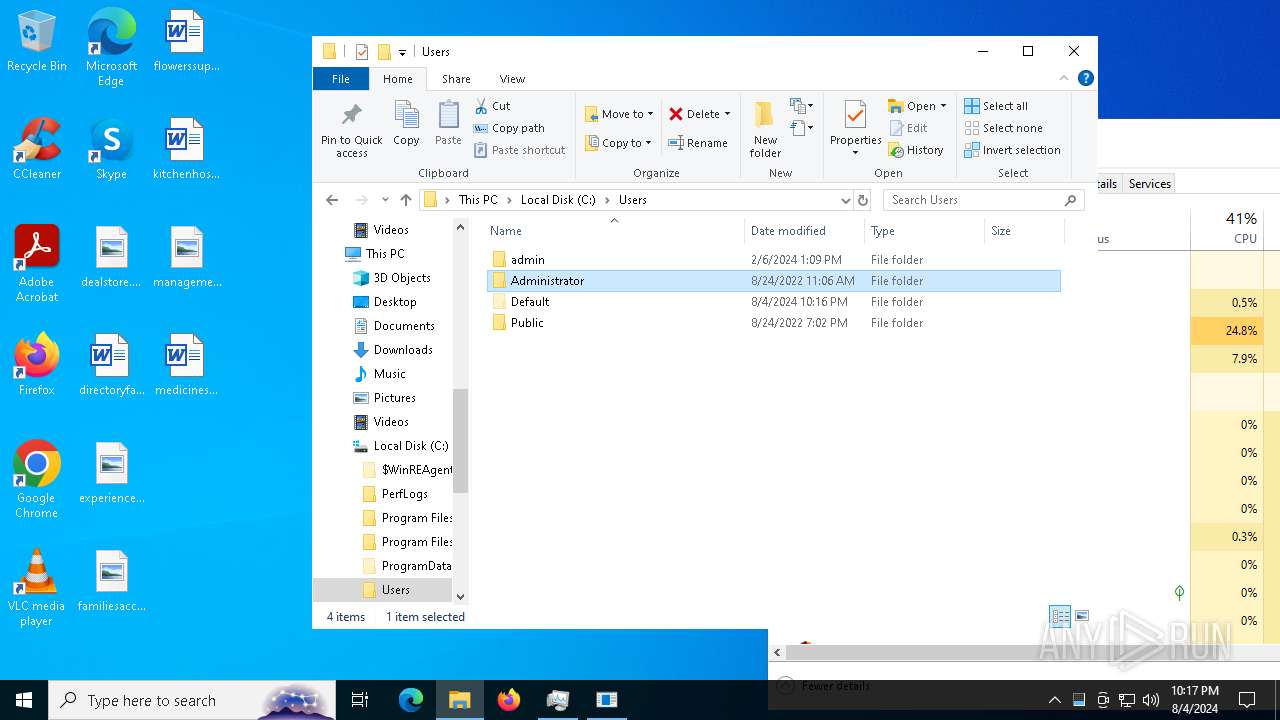
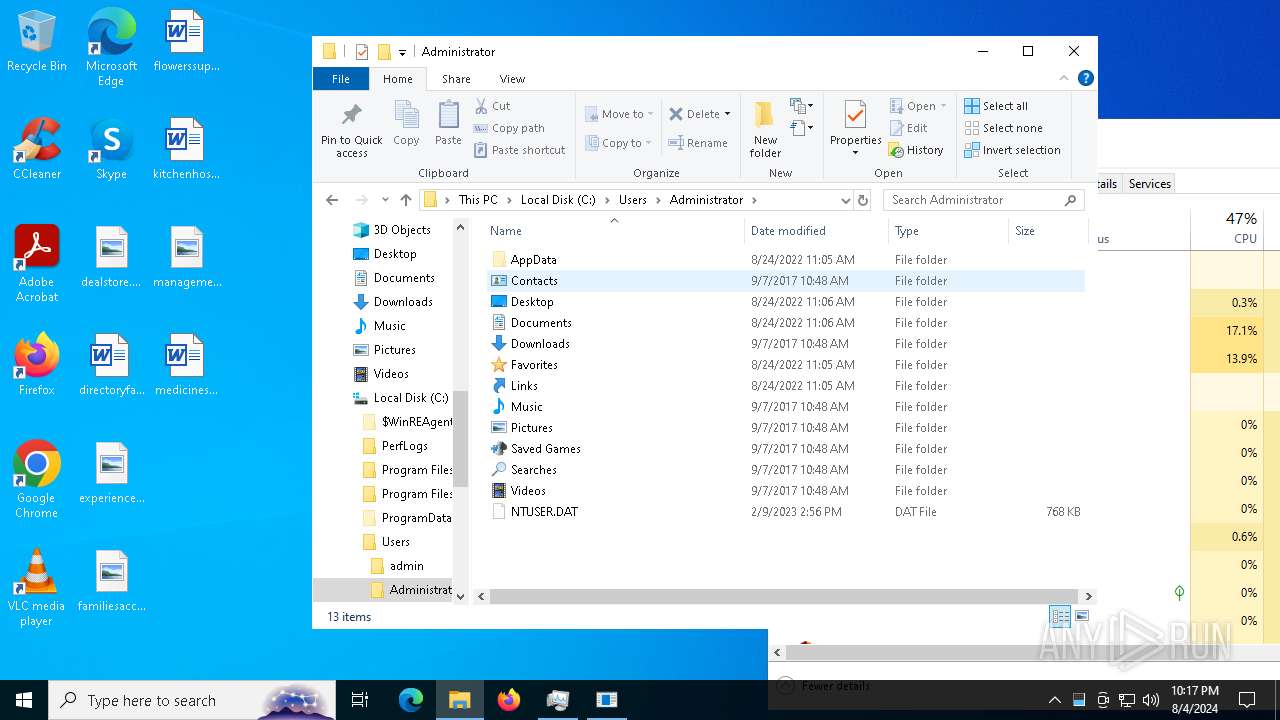
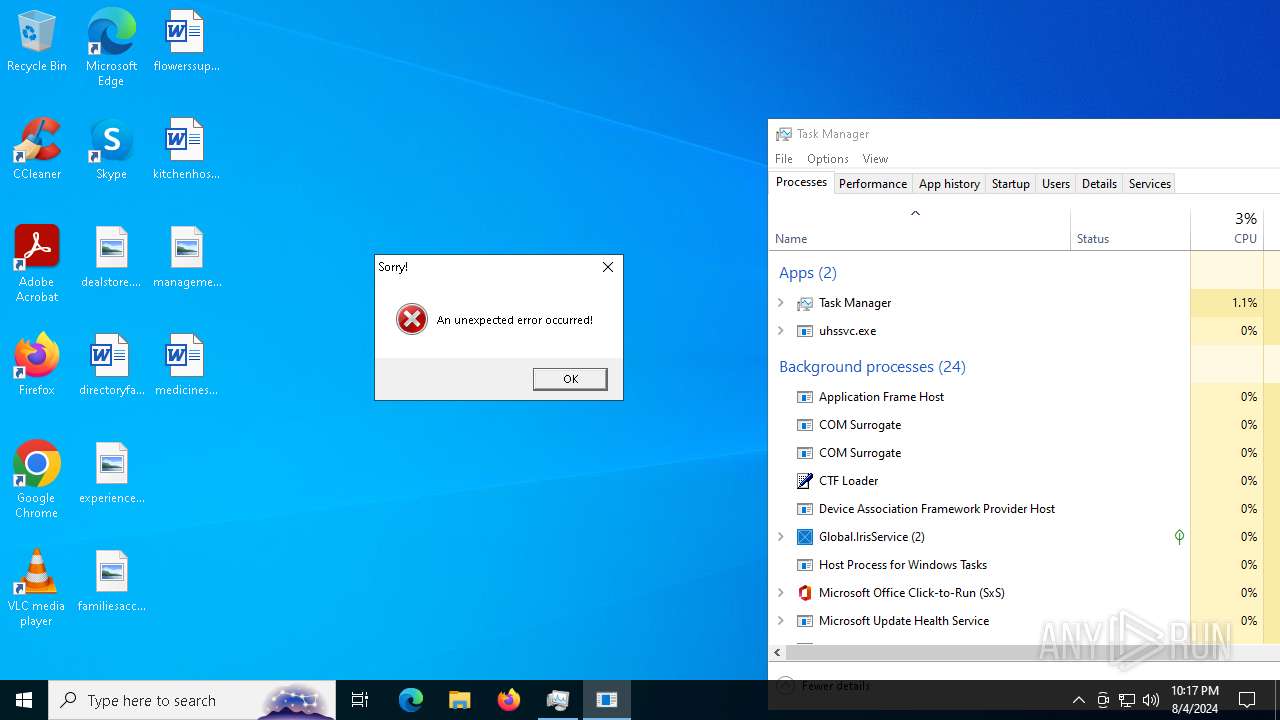
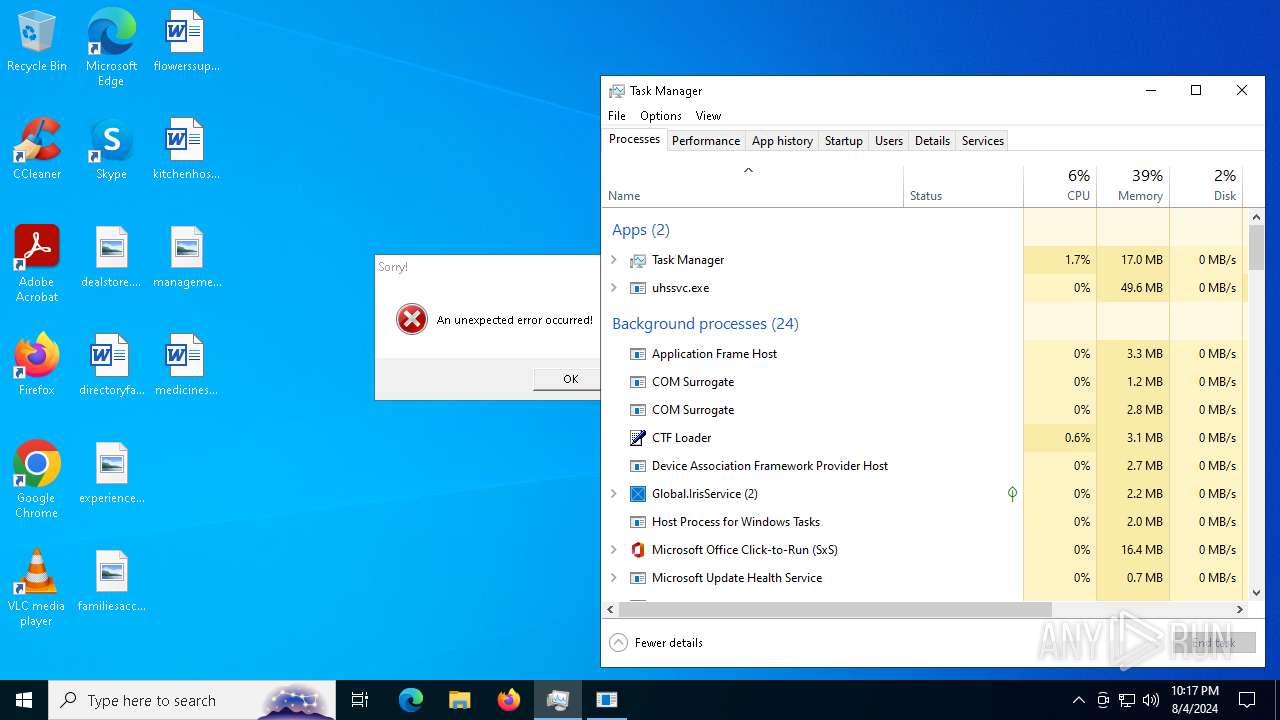
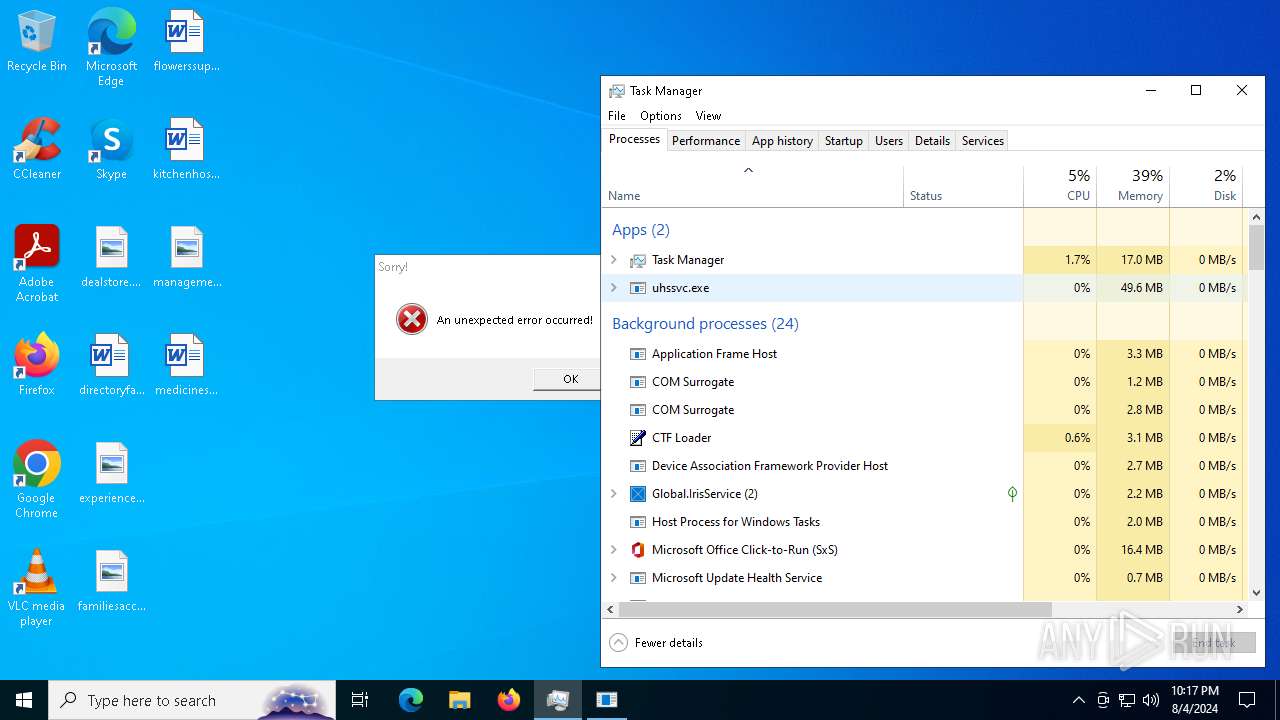
| File name: | Spoofer.exe |
| Full analysis: | https://app.any.run/tasks/4e31001d-9941-49bd-afad-2af45ae80136 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | August 04, 2024, 22:16:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9D528F8DD0EAB6F636A52D7EDB58AC76 |
| SHA1: | 7BC65573A92C73AC544DB072F224653FB4E9EA47 |
| SHA256: | 336DDCD6450C8BE05CB0ADE6A727B87F0B4FC1AA5F3ADB9248F5A4372BEED795 |
| SSDEEP: | 98304:Xyi3JJcMTz9GmwKGf3pkwsqGADUoNfW1P4c2LR4PLk85qtuxO98eEiSpe53XskGq:jKeYfJv |
MALICIOUS
Drops the executable file immediately after the start
- Spoofer.exe (PID: 6416)
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
- uhssvc.exe (PID: 4484)
Actions looks like stealing of personal data
- Spoofer.exe (PID: 6416)
- wscript.exe (PID: 6468)
- cmd.exe (PID: 6888)
- conhost.exe (PID: 6900)
- reg.exe (PID: 6952)
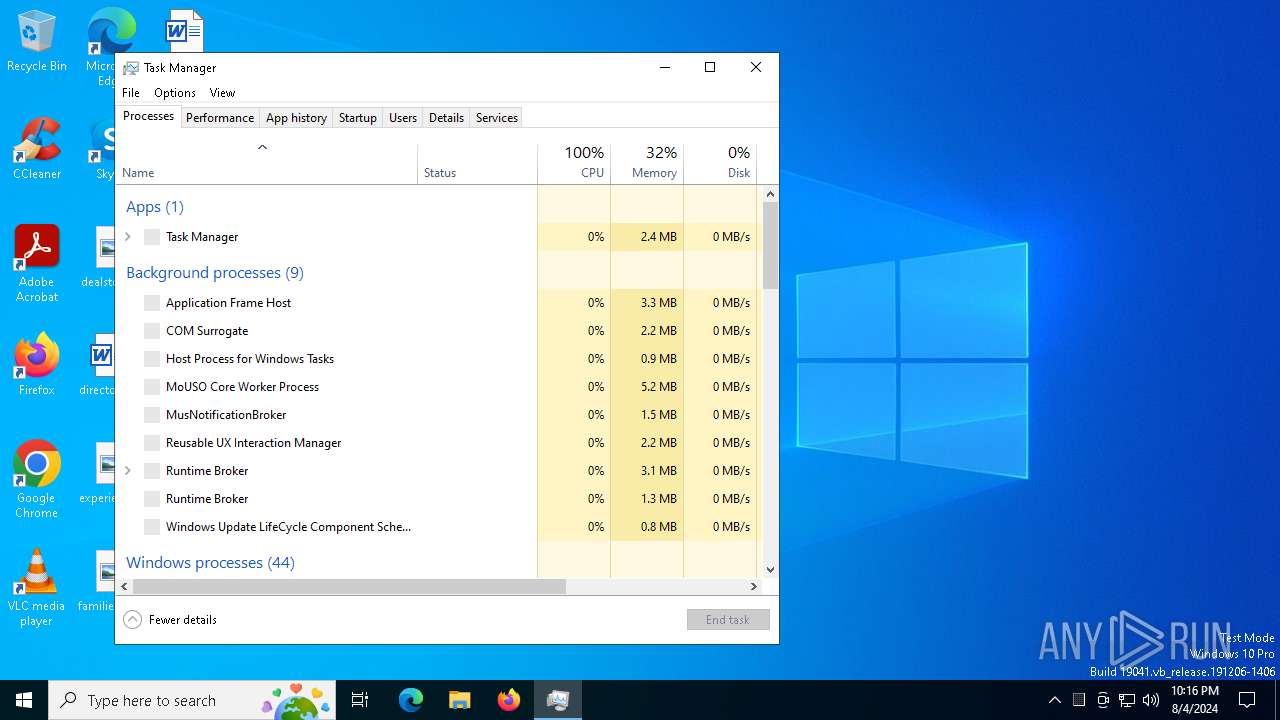
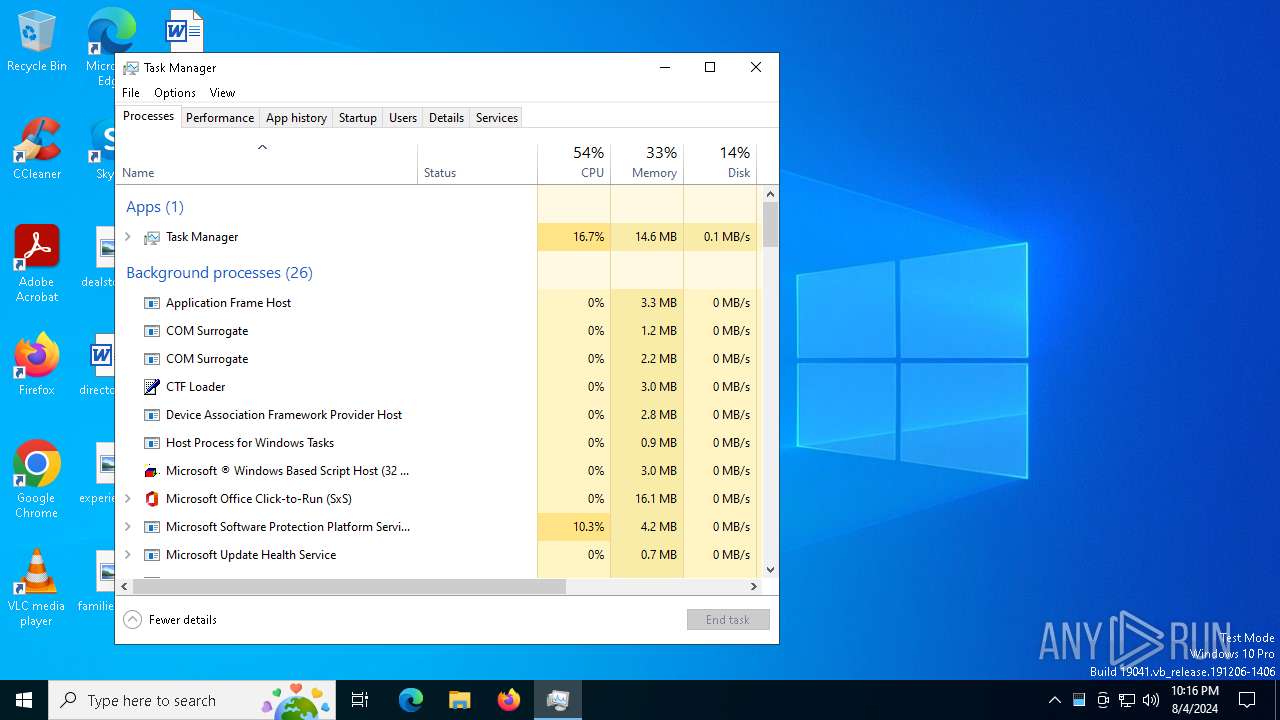
- Taskmgr.exe (PID: 6556)
- Runtimeperfdhcp.exe (PID: 6976)
- cmd.exe (PID: 7080)
- Runtimeperfdhcp.exe (PID: 7148)
- uhssvc.exe (PID: 4484)
Adds path to the Windows Defender exclusion list
- Runtimeperfdhcp.exe (PID: 7148)
Connects to the CnC server
- uhssvc.exe (PID: 4484)
DARKCRYSTAL has been detected (SURICATA)
- uhssvc.exe (PID: 4484)
DCRAT has been detected (YARA)
- uhssvc.exe (PID: 4484)
SUSPICIOUS
Executable content was dropped or overwritten
- Spoofer.exe (PID: 6416)
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
- uhssvc.exe (PID: 4484)
Reads security settings of Internet Explorer
- Spoofer.exe (PID: 6416)
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
Reads the date of Windows installation
- Spoofer.exe (PID: 6416)
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
Executing commands from a ".bat" file
- wscript.exe (PID: 6468)
- Runtimeperfdhcp.exe (PID: 7148)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6888)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6468)
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6468)
The executable file from the user directory is run by the CMD process
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
- uhssvc.exe (PID: 4484)
The process creates files with name similar to system file names
- Runtimeperfdhcp.exe (PID: 7148)
Starts POWERSHELL.EXE for commands execution
- Runtimeperfdhcp.exe (PID: 7148)
Reads browser cookies
- cmd.exe (PID: 6376)
Script adds exclusion path to Windows Defender
- Runtimeperfdhcp.exe (PID: 7148)
Connects to the server without a host name
- uhssvc.exe (PID: 4484)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6376)
Starts application with an unusual extension
- cmd.exe (PID: 6376)
INFO
Checks supported languages
- Spoofer.exe (PID: 6416)
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
- chcp.com (PID: 6296)
- uhssvc.exe (PID: 4484)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6556)
Reads the computer name
- Spoofer.exe (PID: 6416)
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
- uhssvc.exe (PID: 4484)
Creates files or folders in the user directory
- Spoofer.exe (PID: 6416)
- Runtimeperfdhcp.exe (PID: 7148)
Process checks computer location settings
- Spoofer.exe (PID: 6416)
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
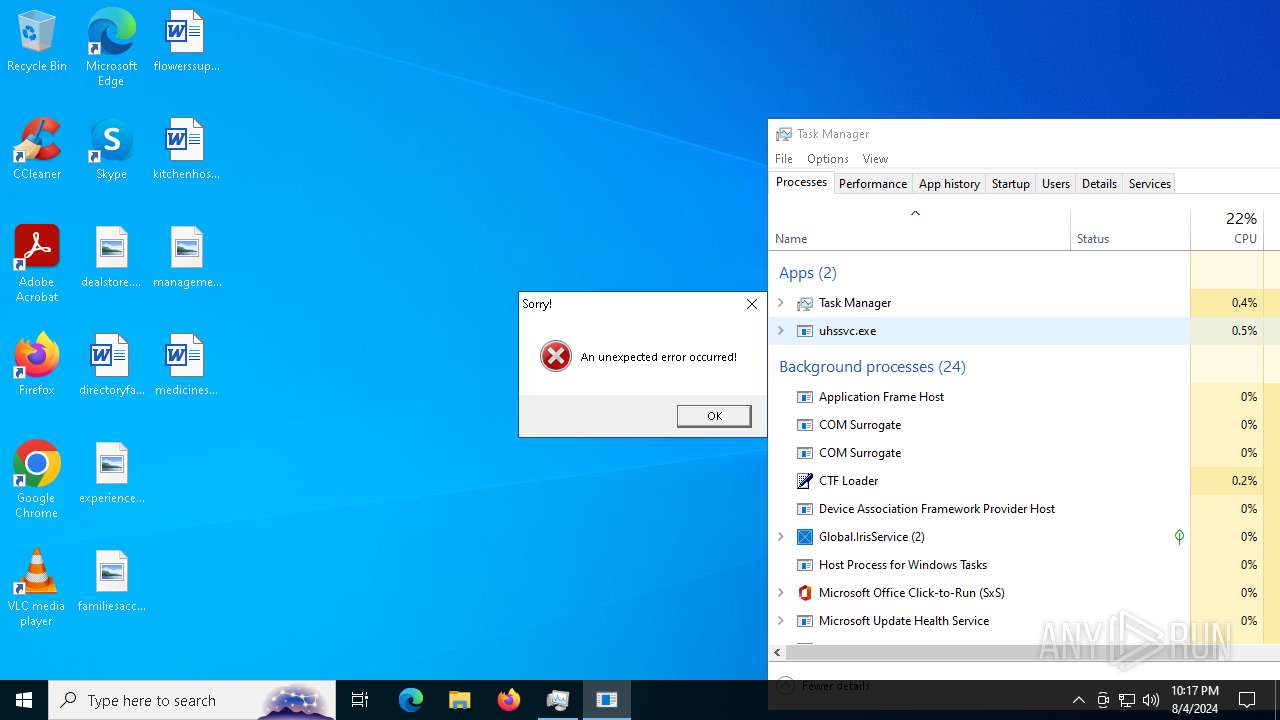
Manual execution by a user
- Taskmgr.exe (PID: 6556)
- Taskmgr.exe (PID: 6508)
Reads the machine GUID from the registry
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
- uhssvc.exe (PID: 4484)
Reads Environment values
- Runtimeperfdhcp.exe (PID: 6976)
- Runtimeperfdhcp.exe (PID: 7148)
- uhssvc.exe (PID: 4484)
Creates files in the program directory
- Runtimeperfdhcp.exe (PID: 7148)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3972)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 4128)
- powershell.exe (PID: 6160)
- powershell.exe (PID: 6220)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3972)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 4128)
- powershell.exe (PID: 6160)
Create files in a temporary directory
- Runtimeperfdhcp.exe (PID: 7148)
Checks proxy server information
- uhssvc.exe (PID: 4484)
.NET Reactor protector has been detected
- uhssvc.exe (PID: 4484)
Disables trace logs
- uhssvc.exe (PID: 4484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:03:03 13:15:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 203776 |
| InitializedDataSize: | 82432 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f530 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
163
Monitored processes
28
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2340 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2388 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3180 | C:\WINDOWS\system32\DllHost.exe /Processid:{4D111E08-CBF7-4F12-A926-2C7920AF52FC} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3972 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:\found.000\dir0000.chk\sihost.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Runtimeperfdhcp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:\Program Files (x86)\WindowsPowerShell\fontdrvhost.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Runtimeperfdhcp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4484 | "C:\Users\admin\Cookies\uhssvc.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCookies\uhssvc.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 16.10.31418.88 Modules
| |||||||||||||||
| 4692 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:\Program Files\Windows Sidebar\Shared Gadgets\WaaSMedicAgent.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Runtimeperfdhcp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5880 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
47 937
Read events
47 882
Write events
54
Delete events
1
Modification events
| (PID) Process: | (6416) Spoofer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | VBEFile_.vbe |
Value: 0 | |||
| (PID) Process: | (6416) Spoofer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (6416) Spoofer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6416) Spoofer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6416) Spoofer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6416) Spoofer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6556) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (6556) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AAC14FF77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AAC14FF77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AAC14FF77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AAC14FF77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AAC14FF77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000ABC14FF77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028ABC14FF77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050ABC14FF77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AAC14FF77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070ABC14FF77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088ABC14FF77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8ABC14FF77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8ABC14FF77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0ABC14FF77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010ACC14FF77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AAC14FF77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AAC14FF77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AAC14FF77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040ACC14FF77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068ACC14FF77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090ACC14FF77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8ACC14FF77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8ACC14FF77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8ACC14FF77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028ABC14FF77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AAC14FF77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020ADC14FF77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040ADC14FF77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068ADC14FF77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AAC14FF77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050ABC14FF77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AAC14FF77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070ABC14FF77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088ABC14FF77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8ABC14FF77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8ABC14FF77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AAC14FF77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088ADC14FF77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8ADC14FF77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0ADC14FF77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AEC14FF77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AEC14FF77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AEC14FF77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AEC14FF77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (6468) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6468) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
90
Suspicious files
2
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6416 | Spoofer.exe | C:\Users\admin\AppData\Roaming\YandexBrowser\data\Runtimeperfdhcp.exe | executable | |
MD5:33C2B68E1B2717A08B0F0AD5426E6C3F | SHA256:775781340BF4D6E7DA07AB04C6590A8EB80536E67BD11BEB25E6BE8B5EB8A255 | |||
| 6416 | Spoofer.exe | C:\Users\admin\AppData\Roaming\YandexBrowser\data\LUY71MzEmzc6rR1RgfGmO4Q2amz5olkK6diGfmeViSA5s7OiHJZQwvM.bat | text | |
MD5:585F387056A0D5F63272F0EA0CF03858 | SHA256:23E73154AD2F30A9668866AC33F5DA8238427956EF154C15EEFEFC64D8DA35AF | |||
| 6416 | Spoofer.exe | C:\Users\admin\AppData\Roaming\YandexBrowser\data\KsseToHSs.vbe | vbe | |
MD5:B8471F520B518615F5295D07EA7EFB02 | SHA256:2491647D9DF80ECED6536378582658AC6087610D9EF11D08D5654B82A9F2CE9E | |||
| 6976 | Runtimeperfdhcp.exe | C:\Users\admin\Desktop\QTCozphG.log | executable | |
MD5:E9CE850DB4350471A62CC24ACB83E859 | SHA256:7C95D3B38114E7E4126CB63AADAF80085ED5461AB0868D2365DD6A18C946EA3A | |||
| 6556 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 6976 | Runtimeperfdhcp.exe | C:\Users\admin\Desktop\RZNPzYXH.log | executable | |
MD5:D8BF2A0481C0A17A634D066A711C12E9 | SHA256:2B93377EA087225820A9F8E4F331005A0C600D557242366F06E0C1EAE003D669 | |||
| 6976 | Runtimeperfdhcp.exe | C:\Users\admin\Desktop\ORPGdFdL.log | executable | |
MD5:16B480082780CC1D8C23FB05468F64E7 | SHA256:7A080D8BD178EC02C7F39F7F941479074C450C4FDD8E963C993D2FB5537C7708 | |||
| 6976 | Runtimeperfdhcp.exe | C:\Users\admin\Desktop\VHTnclxu.log | executable | |
MD5:E84DCD8370FAC91DE71DEF8DCF09BFEC | SHA256:DD7AC164E789CAD96D30930EFE9BBA99698473EDEA38252C2C0EA44043FB1DB5 | |||
| 6976 | Runtimeperfdhcp.exe | C:\Users\admin\Desktop\MdLysshN.log | executable | |
MD5:A4F19ADB89F8D88DBDF103878CF31608 | SHA256:D0613773A711634434DB30F2E35C6892FF54EBEADF49CD254377CAECB204EAA4 | |||
| 6976 | Runtimeperfdhcp.exe | C:\Users\admin\Desktop\nTvtvHRJ.log | executable | |
MD5:87765D141228784AE91334BAE25AD743 | SHA256:9A121719F71383CF66FC36453679B36C8D24CC61EB335D0C304536E5D72AAAEB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
37
DNS requests
17
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4484 | uhssvc.exe | POST | 200 | 194.58.103.90:80 | http://194.58.103.90/publiceternal0/73/Proton2Voiddb/WordpressMariadb/Track2BaseBetter/vm/7/EternalprotonPoll/DbLocalsecureMulti/9Jsvoiddb/sqlTocdnflower/traffic/86/Dleserver/bigloadphpDbsql/imagegeoUpdatelongpollserverProtectGeneratordatalifetemp.php | unknown | — | — | unknown |
5484 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6832 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4484 | uhssvc.exe | POST | 200 | 194.58.103.90:80 | http://194.58.103.90/publiceternal0/73/Proton2Voiddb/WordpressMariadb/Track2BaseBetter/vm/7/EternalprotonPoll/DbLocalsecureMulti/9Jsvoiddb/sqlTocdnflower/traffic/86/Dleserver/bigloadphpDbsql/imagegeoUpdatelongpollserverProtectGeneratordatalifetemp.php | unknown | — | — | unknown |
6864 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4484 | uhssvc.exe | POST | 200 | 194.58.103.90:80 | http://194.58.103.90/publiceternal0/73/Proton2Voiddb/WordpressMariadb/Track2BaseBetter/vm/7/EternalprotonPoll/DbLocalsecureMulti/9Jsvoiddb/sqlTocdnflower/traffic/86/Dleserver/bigloadphpDbsql/imagegeoUpdatelongpollserverProtectGeneratordatalifetemp.php | unknown | — | — | unknown |
4484 | uhssvc.exe | POST | 200 | 194.58.103.90:80 | http://194.58.103.90/publiceternal0/73/Proton2Voiddb/WordpressMariadb/Track2BaseBetter/vm/7/EternalprotonPoll/DbLocalsecureMulti/9Jsvoiddb/sqlTocdnflower/traffic/86/Dleserver/bigloadphpDbsql/imagegeoUpdatelongpollserverProtectGeneratordatalifetemp.php | unknown | — | — | unknown |
4484 | uhssvc.exe | POST | 200 | 194.58.103.90:80 | http://194.58.103.90/publiceternal0/73/Proton2Voiddb/WordpressMariadb/Track2BaseBetter/vm/7/EternalprotonPoll/DbLocalsecureMulti/9Jsvoiddb/sqlTocdnflower/traffic/86/Dleserver/bigloadphpDbsql/imagegeoUpdatelongpollserverProtectGeneratordatalifetemp.php | unknown | — | — | unknown |
4484 | uhssvc.exe | POST | 200 | 194.58.103.90:80 | http://194.58.103.90/publiceternal0/73/Proton2Voiddb/WordpressMariadb/Track2BaseBetter/vm/7/EternalprotonPoll/DbLocalsecureMulti/9Jsvoiddb/sqlTocdnflower/traffic/86/Dleserver/bigloadphpDbsql/imagegeoUpdatelongpollserverProtectGeneratordatalifetemp.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3140 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5484 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5484 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4484 | uhssvc.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4484 | uhssvc.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4484 | uhssvc.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible DarkCrystal Rat Encrypted Connection |