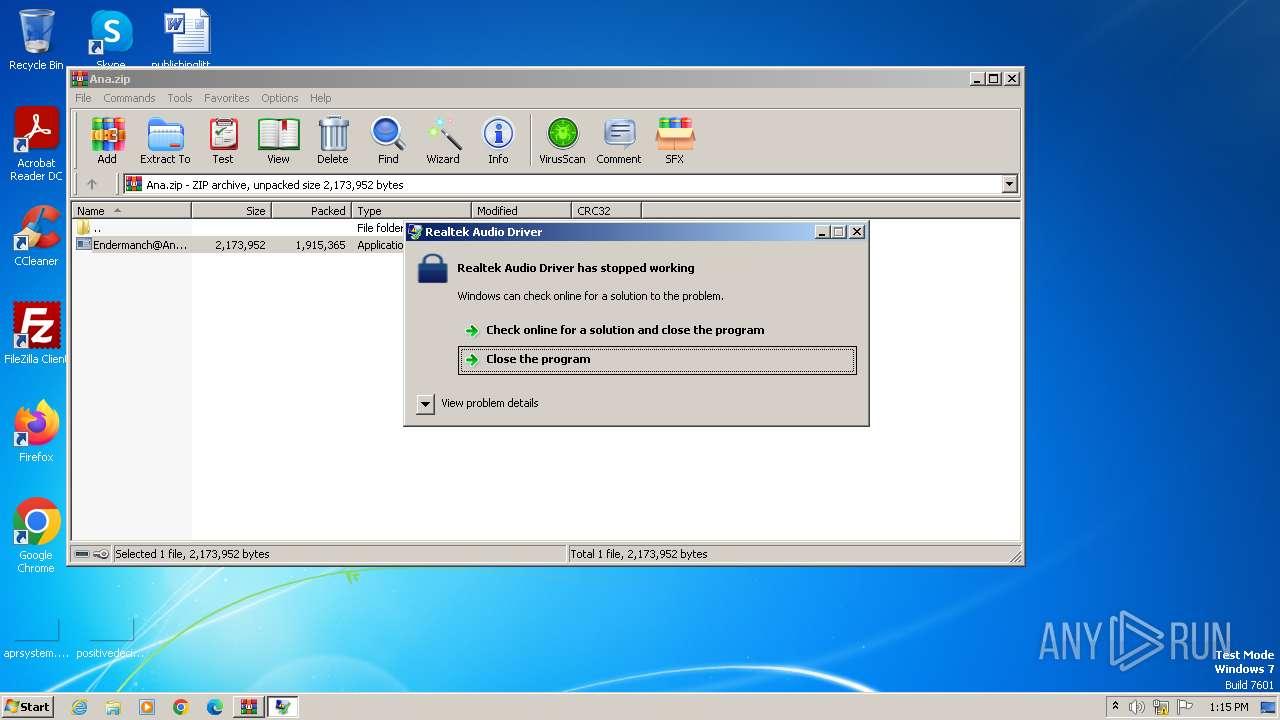
| File name: | Ana.zip |
| Full analysis: | https://app.any.run/tasks/e254d81d-02f7-4e4a-9b7b-4744006190c5 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 13:14:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | CB6E4F6660706C29035189F8AACFE3F8 |
| SHA1: | 7DD1E37A50D4BD7488A3966B8C7C2B99BBA2C037 |
| SHA256: | 3341ABF6DBEFB8AEC171F3766A4A23F323FF207E1B031946EE4DBE6DBB2D45A4 |
| SSDEEP: | 49152:8x24Hl93N3yArA1CYa0HnhDJBFxDXHVtQvEG:mHj3xyArA1CYfnhnLDkvEG |
MALICIOUS
Drops the executable file immediately after the start
- SB.EXE (PID: 1116)
- setup437922456.exe (PID: 3200)
- AV2.EXE (PID: 2628)
- DB.EXE (PID: 1992)
- Endermanch@Ana.exe (PID: 2248)
- Endermanch@Ana.exe (PID: 1924)
- SB.EXE (PID: 3096)
- setup2375382368.exe (PID: 3912)
Creates a writable file in the system directory
- DB.EXE (PID: 1992)
Changes the autorun value in the registry
- iK17766NiLjK17766.exe (PID: 4040)
SUSPICIOUS
Reads the Internet Settings
- Endermanch@Ana.exe (PID: 1924)
- EN.EXE (PID: 2540)
- DB.EXE (PID: 3064)
- SB.EXE (PID: 1116)
- AV2.EXE (PID: 2628)
- iK17766NiLjK17766.exe (PID: 4040)
- Endermanch@Ana.exe (PID: 2248)
- DB.EXE (PID: 1992)
- EN.EXE (PID: 1752)
- DB.EXE (PID: 1616)
- SB.EXE (PID: 3096)
Reads the BIOS version
- DB.EXE (PID: 3064)
- DB.EXE (PID: 1992)
- DB.EXE (PID: 1616)
Starts itself from another location
- SB.EXE (PID: 1116)
- SB.EXE (PID: 3096)
Application launched itself
- DB.EXE (PID: 3064)
The process executes via Task Scheduler
- rundll32.exe (PID: 284)
Executing commands from a ".bat" file
- DB.EXE (PID: 1992)
- DB.EXE (PID: 1616)
Starts CMD.EXE for commands execution
- DB.EXE (PID: 1992)
- EN.EXE (PID: 2540)
- DB.EXE (PID: 1616)
- EN.EXE (PID: 1752)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 844)
Create files in a temporary directory
- Endermanch@Ana.exe (PID: 1924)
- SB.EXE (PID: 1116)
- setup437922456.exe (PID: 3200)
- AV2.EXE (PID: 2628)
- EN.EXE (PID: 2540)
- Endermanch@Ana.exe (PID: 2248)
- DB.EXE (PID: 1992)
- AV.EXE (PID: 2780)
- SB.EXE (PID: 3096)
- setup2375382368.exe (PID: 3912)
- DB.EXE (PID: 1616)
- AV2.EXE (PID: 3860)
- EN.EXE (PID: 1752)
Checks supported languages
- Endermanch@Ana.exe (PID: 1924)
- EN.EXE (PID: 2540)
- AV.EXE (PID: 2780)
- DB.EXE (PID: 3064)
- dw20.exe (PID: 2908)
- setup437922456.exe (PID: 3200)
- iK17766NiLjK17766.exe (PID: 4040)
- DB.EXE (PID: 1992)
- Endermanch@Ana.exe (PID: 2248)
- AV.EXE (PID: 2112)
- AV2.EXE (PID: 2628)
- AV2.EXE (PID: 3860)
- dw20.exe (PID: 3524)
- SB.EXE (PID: 3096)
- EN.EXE (PID: 1752)
- setup2375382368.exe (PID: 3912)
- SB.EXE (PID: 1116)
- DB.EXE (PID: 1616)
Process checks are UAC notifies on
- DB.EXE (PID: 3064)
- DB.EXE (PID: 1992)
- DB.EXE (PID: 1616)
Checks proxy server information
- DB.EXE (PID: 3064)
- EN.EXE (PID: 2540)
- AV2.EXE (PID: 2628)
- iK17766NiLjK17766.exe (PID: 4040)
- DB.EXE (PID: 1992)
- DB.EXE (PID: 1616)
- EN.EXE (PID: 1752)
Reads the computer name
- Endermanch@Ana.exe (PID: 1924)
- dw20.exe (PID: 2908)
- setup437922456.exe (PID: 3200)
- SB.EXE (PID: 1116)
- AV2.EXE (PID: 2628)
- iK17766NiLjK17766.exe (PID: 4040)
- DB.EXE (PID: 1992)
- Endermanch@Ana.exe (PID: 2248)
- DB.EXE (PID: 3064)
- EN.EXE (PID: 2540)
- EN.EXE (PID: 1752)
- SB.EXE (PID: 3096)
- setup2375382368.exe (PID: 3912)
- AV2.EXE (PID: 3860)
- DB.EXE (PID: 1616)
- dw20.exe (PID: 3524)
Reads the machine GUID from the registry
- AV.EXE (PID: 2780)
- DB.EXE (PID: 3064)
- EN.EXE (PID: 2540)
- AV2.EXE (PID: 2628)
- dw20.exe (PID: 2908)
- iK17766NiLjK17766.exe (PID: 4040)
- DB.EXE (PID: 1992)
- AV.EXE (PID: 2112)
- DB.EXE (PID: 1616)
- EN.EXE (PID: 1752)
- dw20.exe (PID: 3524)
Creates files or folders in the user directory
- dw20.exe (PID: 2908)
- dw20.exe (PID: 3524)
Creates files in the program directory
- AV2.EXE (PID: 2628)
- iK17766NiLjK17766.exe (PID: 4040)
Reads Windows Product ID
- DB.EXE (PID: 1992)
- DB.EXE (PID: 3064)
- DB.EXE (PID: 1616)
Manual execution by a user
- Endermanch@Ana.exe (PID: 2248)
- AV2.EXE (PID: 944)
- rundll32.exe (PID: 924)
- notepad++.exe (PID: 1828)
- rundll32.exe (PID: 2308)
Application launched itself
- msedge.exe (PID: 3416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2011:09:21 08:09:08 |
| ZipCRC: | 0x8a7979e4 |
| ZipCompressedSize: | 1915365 |
| ZipUncompressedSize: | 2173952 |
| ZipFileName: | Endermanch@Ana.exe |
Total processes
99
Monitored processes
38
Malicious processes
9
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\system32\rundll32.exe "C:\Windows\system32\PINGM.dll",iyhrlpfrvl | C:\Windows\System32\rundll32.exe | — | taskeng.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 644 | "C:\Windows\system32\cmd.exe" /c del C:\Users\admin\AppData\Local\Temp\EN.EXE > nul | C:\Windows\System32\cmd.exe | — | EN.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 844 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Ana.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 924 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\q4hg4341.cc2 | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 944 | "C:\Users\admin\AppData\Local\Temp\AV2.EXE" | C:\Users\admin\AppData\Local\Temp\AV2.EXE | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 1116 | "C:\Users\admin\AppData\Local\Temp\SB.EXE" | C:\Users\admin\AppData\Local\Temp\SB.EXE | — | Endermanch@Ana.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1600 | /c C:\Users\admin\AppData\Local\Temp\~unins687.bat "C:\Users\admin\AppData\Local\Temp\DB.EXE" | C:\Windows\System32\cmd.exe | — | DB.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1608 | "C:\Users\admin\AppData\Local\Temp\setup437922456.exe" | C:\Users\admin\AppData\Local\Temp\setup437922456.exe | — | SB.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1616 | "C:\Users\admin\AppData\Local\Temp\DB.EXE" | C:\Users\admin\AppData\Local\Temp\DB.EXE | Endermanch@Ana.exe | ||||||||||||
User: admin Company: Prjfeusek Vdceboszrya Integrity Level: MEDIUM Description: Internet Connection Wizard Exit code: 0 Version: 6.00.3790.3959 (srv03_sp2_rtm.070216-1710) Modules
| |||||||||||||||
| 1752 | "C:\Users\admin\AppData\Local\Temp\EN.EXE" | C:\Users\admin\AppData\Local\Temp\EN.EXE | — | Endermanch@Ana.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
8 892
Read events
8 252
Write events
638
Delete events
2
Modification events
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
25
Suspicious files
38
Text files
40
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2908 | dw20.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_av.exe_bebff19cf845587bb44e6beb0e283247b493ae_0b7caf01\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1924 | Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV.EXE | executable | |
MD5:F284568010505119F479617A2E7DC189 | SHA256:26C8F13EA8DC17443A9FA005610537CB6700AEBAF748E747E9278D504E416EB1 | |||
| 1924 | Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV2.EXE | executable | |
MD5:014578EDB7DA99E5BA8DD84F5D26DFD5 | SHA256:4CE5E8B510895ABB204F97E883D8CBAACC29CCEF0844D9AE81F8666F234B0529 | |||
| 1924 | Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\GB.EXE | executable | |
MD5:FE731B4C6684D643EB5B55613EF9ED31 | SHA256:E7953DAAD7A68F8634DED31A21A31F0C2AA394CA9232E2F980321F7B69176496 | |||
| 1924 | Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\EN.EXE | executable | |
MD5:621F2279F69686E8547E476B642B6C46 | SHA256:C17A18CF2C243303B8A6688AAD83B3E6E9B727FCD89F69065785EF7F1A2A3E38 | |||
| 1924 | Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\SB.EXE | executable | |
MD5:9252E1BE9776AF202D6AD5C093637022 | SHA256:CE822FF86E584F15B6ABD14C61453BD3B481D4EC3FDEB961787FCEB52ACD8BD6 | |||
| 1924 | Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\DB.EXE | executable | |
MD5:C6746A62FEAFCB4FCA301F606F7101FA | SHA256:B5A255D0454853C8AFC0B321E1D86DCA22C3DBEFB88E5D385D2D72F9BC0109E6 | |||
| 1116 | SB.EXE | C:\Users\admin\AppData\Local\Temp\A240.tmp | executable | |
MD5:E670CDD55B7BA36F96B0C7B9A0E27E16 | SHA256:C1CB673B1CA6734C7C9EC126AA43C0C2E346AC94D4E7BD6545E1066107A3B703 | |||
| 844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb844.39263\Endermanch@Ana.exe | executable | |
MD5:F571FACA510BFFE809C76C1828D44523 | SHA256:117D7AF0DEB40B3FE532BB6CBE374884FA55ED7CFE053FE698720CDCCB5A59CB | |||
| 1116 | SB.EXE | C:\Users\admin\AppData\Local\Temp\A22F.tmp | executable | |
MD5:9252E1BE9776AF202D6AD5C093637022 | SHA256:CE822FF86E584F15B6ABD14C61453BD3B481D4EC3FDEB961787FCEB52ACD8BD6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
32
DNS requests
17
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3064 | DB.EXE | 66.96.162.135:80 | middlechrist.com | BIZLAND-SD | US | unknown |
2628 | AV2.EXE | 178.162.174.147:80 | — | LeaseWeb Netherlands B.V. | NL | unknown |
4040 | iK17766NiLjK17766.exe | 178.162.174.147:80 | — | LeaseWeb Netherlands B.V. | NL | unknown |
1992 | DB.EXE | 66.96.162.135:80 | middlechrist.com | BIZLAND-SD | US | unknown |
1616 | DB.EXE | 66.96.162.135:80 | middlechrist.com | BIZLAND-SD | US | unknown |
1216 | spoolsv.exe | 95.143.193.138:80 | — | Internetport Sweden AB | SE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
aeravine.com |
| unknown |
middlechrist.com |
| unknown |
bemachin.com |
| unknown |
dns.msftncsi.com |
| shared |
go.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
wrou1xamwafgmca8ip.com |
| unknown |
Threats
Process | Message |
|---|---|
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV2.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\DB.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\EN.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\GB.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\SB.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV2.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\DB.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\EN.EXE |