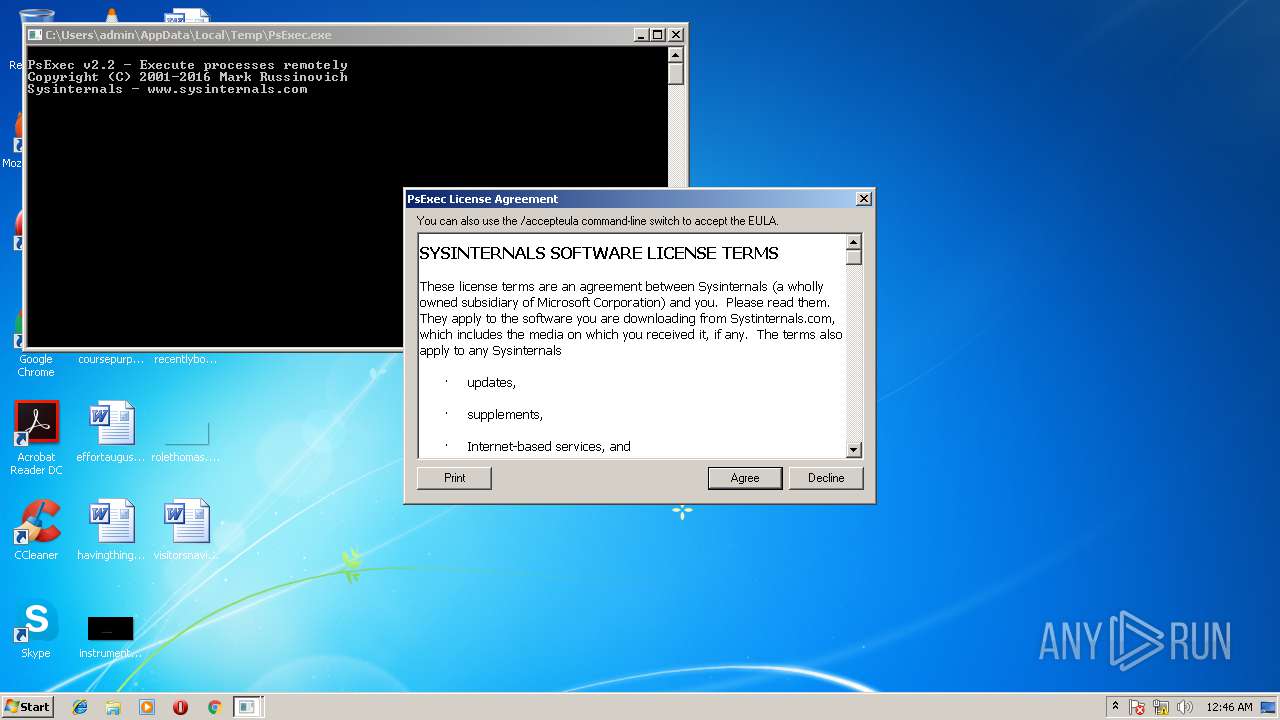
| File name: | PsExec.exe |
| Full analysis: | https://app.any.run/tasks/59027e3d-cf65-4486-9ff1-d67944999b61 |
| Verdict: | Malicious activity |
| Analysis date: | March 12, 2018, 00:46:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 27304B246C7D5B4E149124D5F93C5B01 |
| SHA1: | E50D9E3BD91908E13A26B3E23EDEAF577FB3A095 |
| SHA256: | 3337E3875B05E0BFBA69AB926532E3F179E8CFBF162EBB60CE58A0281437A7EF |
| SSDEEP: | 3072:Yao79VuJ6titIi/H7ZUFgllxiBD+P5xWr3geNtdS+DlGttzhA9HY4ZUFxPkwlmlP:YaSq4TBWISSTgu7DlGtEC1xn/O5r4S |
MALICIOUS
Loads the Task Scheduler COM API
- software_reporter_tool.exe (PID: 3704)
SUSPICIOUS
Application launched itself
- chrome.exe (PID: 3652)
INFO
Dropped object may contain URL's
- chrome.exe (PID: 3652)
Loads rich edit control libraries
- PsExec.exe (PID: 3368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:06:28 20:43:09+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 99840 |
| InitializedDataSize: | 400896 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9de6 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.20.0.0 |
| ProductVersionNumber: | 2.20.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Execute processes remotely |
| FileVersion: | 2.2 |
| InternalName: | PsExec |
| LegalCopyright: | Copyright (C) 2001-2016 Mark Russinovich |
| OriginalFileName: | psexec.c |
| ProductName: | Sysinternals PsExec |
| ProductVersion: | 2.2 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 28-Jun-2016 18:43:09 |
| Detected languages: |
|
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Execute processes remotely |
| FileVersion: | 2.2 |
| InternalName: | PsExec |
| LegalCopyright: | Copyright (C) 2001-2016 Mark Russinovich |
| OriginalFilename: | psexec.c |
| ProductName: | Sysinternals PsExec |
| ProductVersion: | 2.2 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 28-Jun-2016 18:43:09 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000184C4 | 0x00018600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.58676 |
.rdata | 0x0001A000 | 0x0000E62A | 0x0000E800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.59667 |
.data | 0x00029000 | 0x0002DD9C | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.18234 |
.rsrc | 0x00057000 | 0x00023F18 | 0x00024000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.37889 |
.reloc | 0x0007B000 | 0x00001750 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.63142 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
7 | 2.38755 | 122 | UNKNOWN | English - United States | RT_STRING |
PSEXESVC | 6.40332 | 145568 | UNKNOWN | English - United States | BINRES |
Imports
ADVAPI32.dll |
COMDLG32.dll |
KERNEL32.dll |
MPR.dll |
NETAPI32.dll |
USER32.dll (delay-loaded) |
VERSION.dll |
WS2_32.dll |
Total processes
59
Monitored processes
16
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1604,6803015007238025687,14773704437680470256,131072 --service-pipe-token=9DA40C4205D3B5ECFFD5FB7362A93497 --lang=en-US --disable-client-side-phishing-detection --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=9DA40C4205D3B5ECFFD5FB7362A93497 --renderer-client-id=5 --mojo-platform-channel-handle=3164 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1604,6803015007238025687,14773704437680470256,131072 --service-pipe-token=BBF4033D16316C58D2FB826F595BE559 --lang=en-US --disable-client-side-phishing-detection --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=BBF4033D16316C58D2FB826F595BE559 --renderer-client-id=6 --mojo-platform-channel-handle=3056 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 1444 | "c:\users\admin\appdata\local\google\chrome\user data\swreporter\23.129.0\software_reporter_tool.exe" --crash-handler "--database=c:\users\admin\appdata\local\Google\Software Reporter Tool" --url=https://clients2.google.com/cr/report --annotation=plat=Win32 --annotation=prod=ChromeFoil --annotation=ver=23.129.0 --initial-client-data=0xe4,0xec,0xf0,0xe8,0xf4,0xe2c42c,0xe2c43c,0xe2c44c | c:\users\admin\appdata\local\google\chrome\user data\swreporter\23.129.0\software_reporter_tool.exe | — | software_reporter_tool.exe | |||||||||||
User: admin Company: Google Integrity Level: MEDIUM Description: Software Reporter Tool Exit code: 0 Version: 23.129.0 Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1604,6803015007238025687,14773704437680470256,131072 --service-pipe-token=764F4B754793A7A5605348B4CFF97A5B --lang=en-US --extension-process --disable-client-side-phishing-detection --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=764F4B754793A7A5605348B4CFF97A5B --renderer-client-id=2 --mojo-platform-channel-handle=1772 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 2884 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
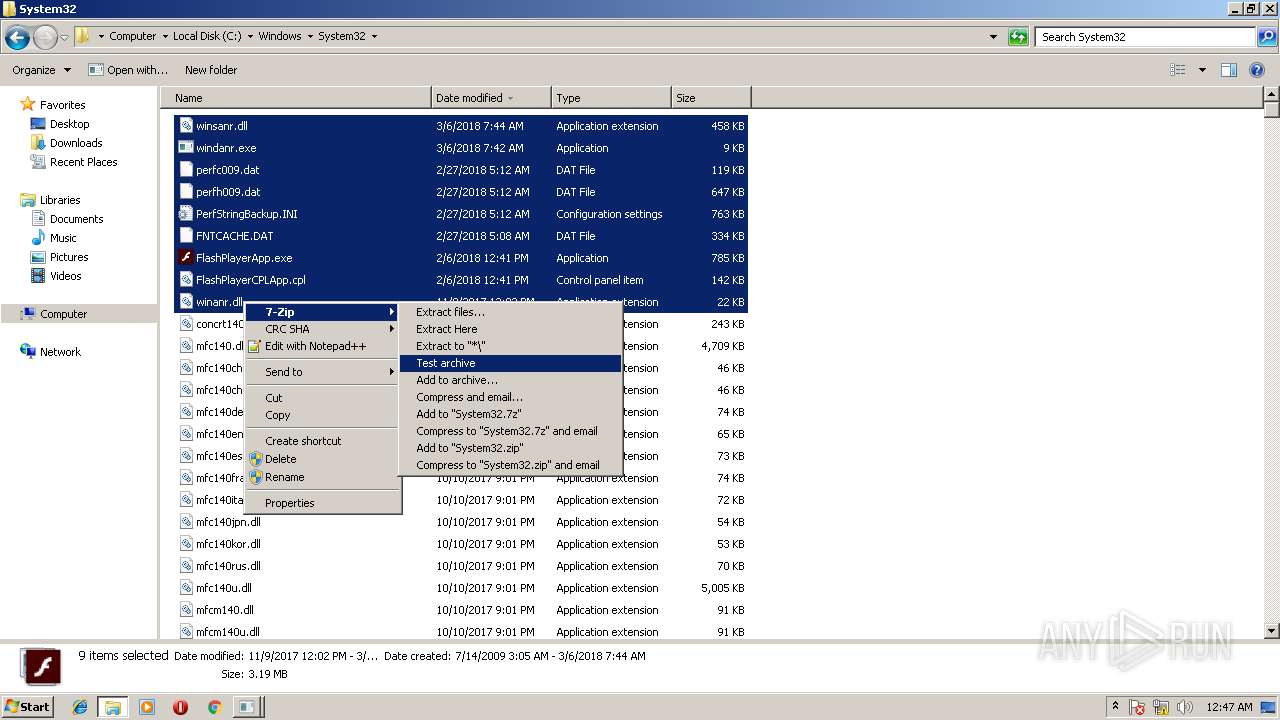
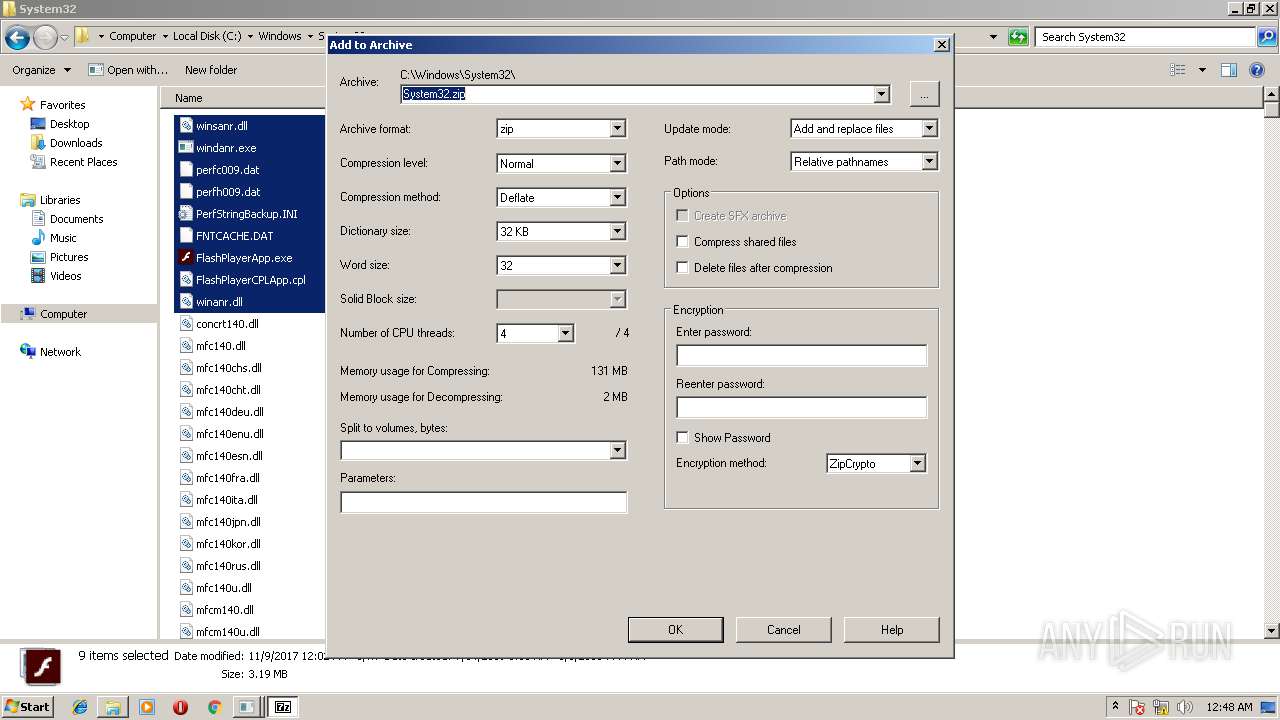
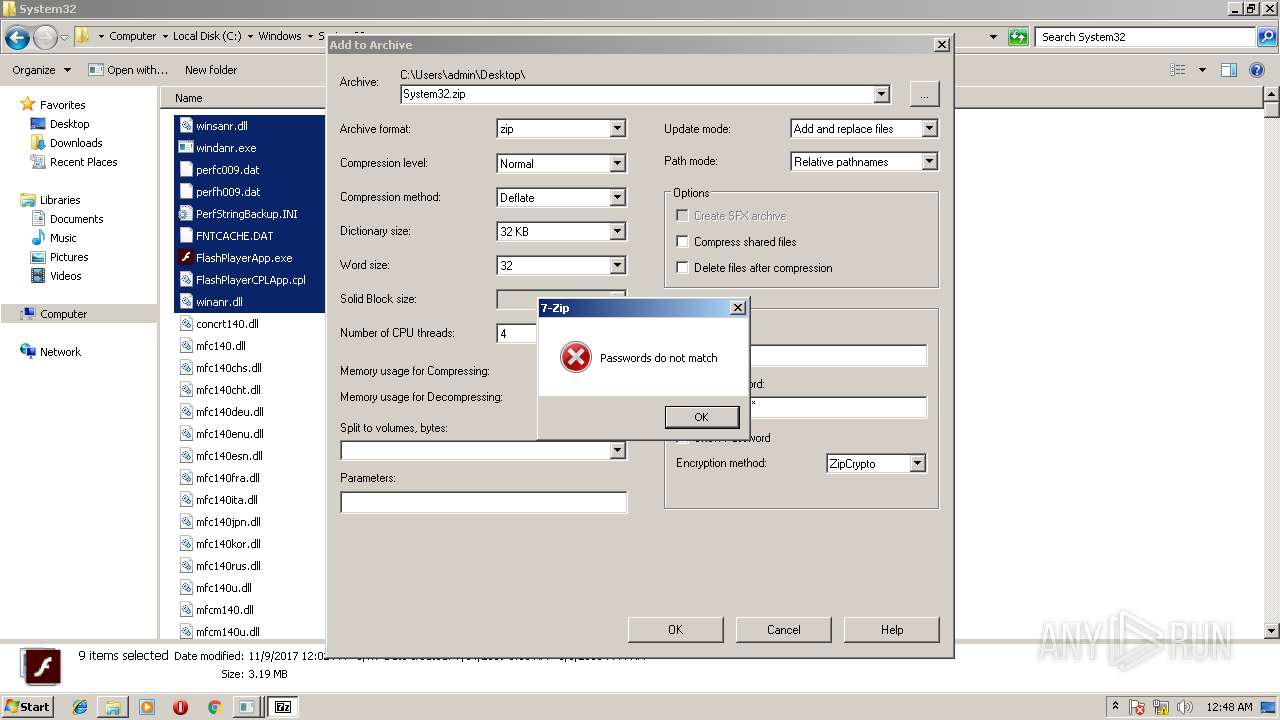
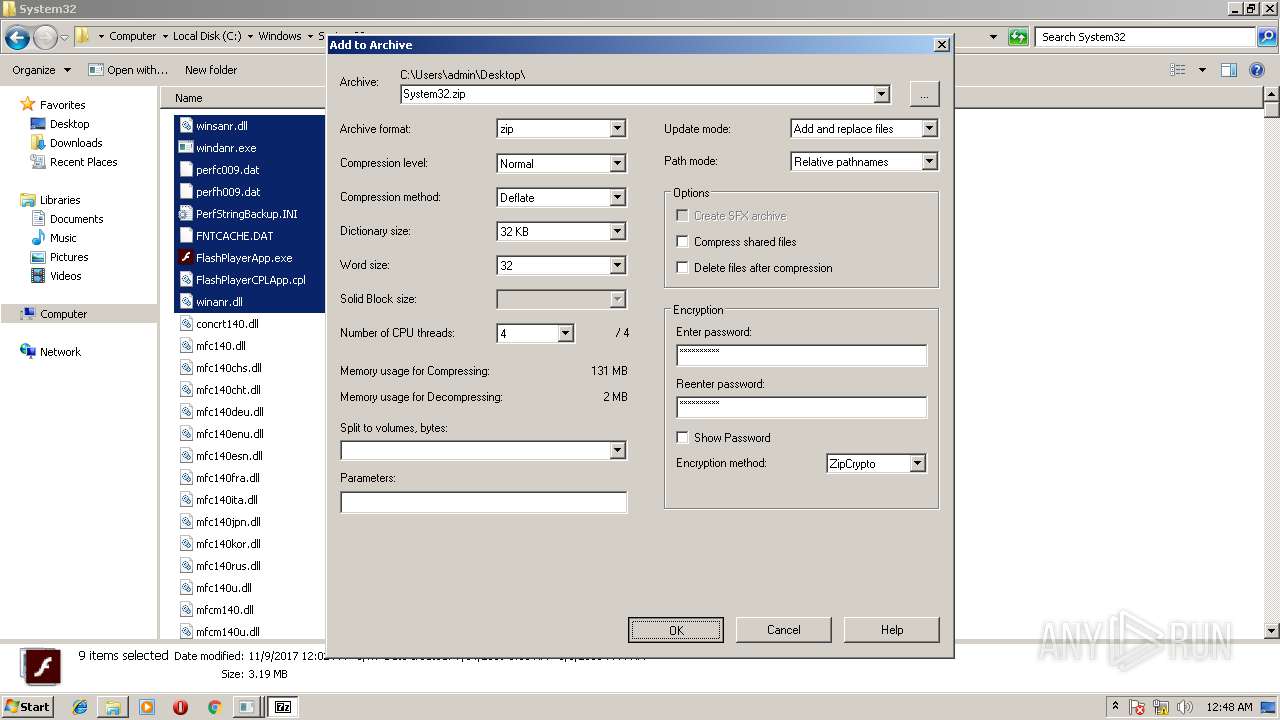
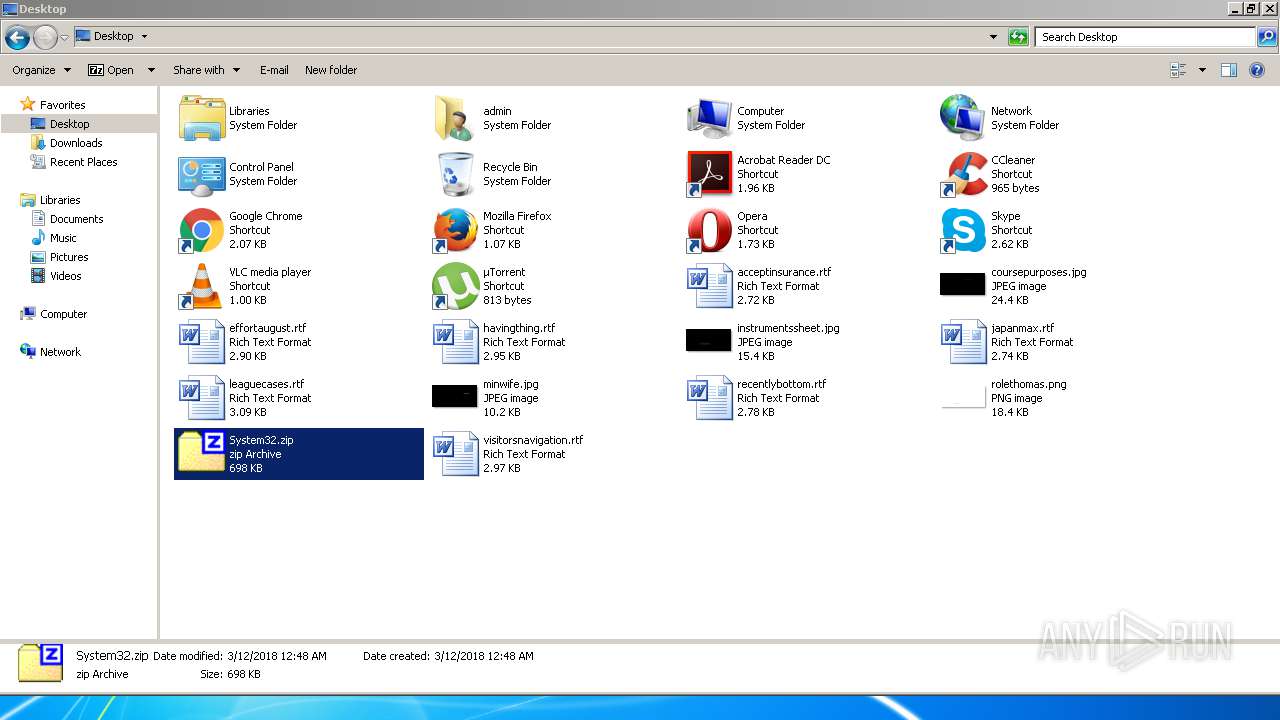
| 3016 | "C:\Program Files\7-Zip\7zG.exe" a -i#7zMap8534:634:7zEvent25630 -ad -slp- -saa -- "C:\Windows\System32\System32" | C:\Program Files\7-Zip\7zG.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip GUI Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 3032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1604,6803015007238025687,14773704437680470256,131072 --lang=en-US --no-sandbox --service-request-channel-token=4BA6F87865C48A49B2FFAAC98897CFC0 --mojo-platform-channel-handle=824 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 3104 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1604,6803015007238025687,14773704437680470256,131072 --lang=en-US --service-request-channel-token=9330CF7D01C6C1765CB03CE00080C7D2 --mojo-platform-channel-handle=3440 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 3256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1604,6803015007238025687,14773704437680470256,131072 --disable-direct-composition --use-gl=swiftshader-webgl --supports-dual-gpus=false --gpu-driver-bug-workarounds=9,12,13,22,23,24,27,49,84 --disable-gl-extensions="GL_KHR_blend_equation_advanced GL_KHR_blend_equation_advanced_coherent" --disable-accelerated-video-decode --gpu-vendor-id=0x1234 --gpu-device-id=0x1111 --gpu-driver-vendor="Google Inc." --gpu-driver-version=3.3.0.2 --gpu-driver-date=2017/04/07 --service-request-channel-token=6E36FC49D28184D4D39A8EAA04B0FC47 --mojo-platform-channel-handle=4080 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 3368 | "C:\Users\admin\AppData\Local\Temp\PsExec.exe" | C:\Users\admin\AppData\Local\Temp\PsExec.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Execute processes remotely Exit code: 1073807364 Version: 2.2 Modules
| |||||||||||||||
Total events
1 992
Read events
1 385
Write events
592
Delete events
15
Modification events
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | MRUListEx |
Value: FFFFFFFF | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000900000000000000080000000300000006000000070000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\74\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\8F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\74\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\74\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\74\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | FFlags |
Value: 1092616257 | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\74\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
| (PID) Process: | (3016) 7zG.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\74\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | ColInfo |
Value: 00000000000000000000000000000000FDDFDFFD100000000000000000000000040000001800000030F125B7EF471A10A5F102608C9EEBAC0A0000001001000030F125B7EF471A10A5F102608C9EEBAC0E0000007800000030F125B7EF471A10A5F102608C9EEBAC040000007800000030F125B7EF471A10A5F102608C9EEBAC0C00000050000000 | |||
Executable files
0
Suspicious files
50
Text files
61
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3016 | 7zG.exe | C:\Users\admin\Desktop\System32.zip.tmp | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d60979a0-dccd-4557-ae14-bd2c9ac246bc.tmp | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\data_2 | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\data_3 | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extension State\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\IndexedDB\https_www.google.it_0.indexeddb.leveldb\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
35
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.217.22.66:443 | adservice.google.it | Google Inc. | US | whitelisted |
— | — | 172.217.16.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
— | — | 172.217.21.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
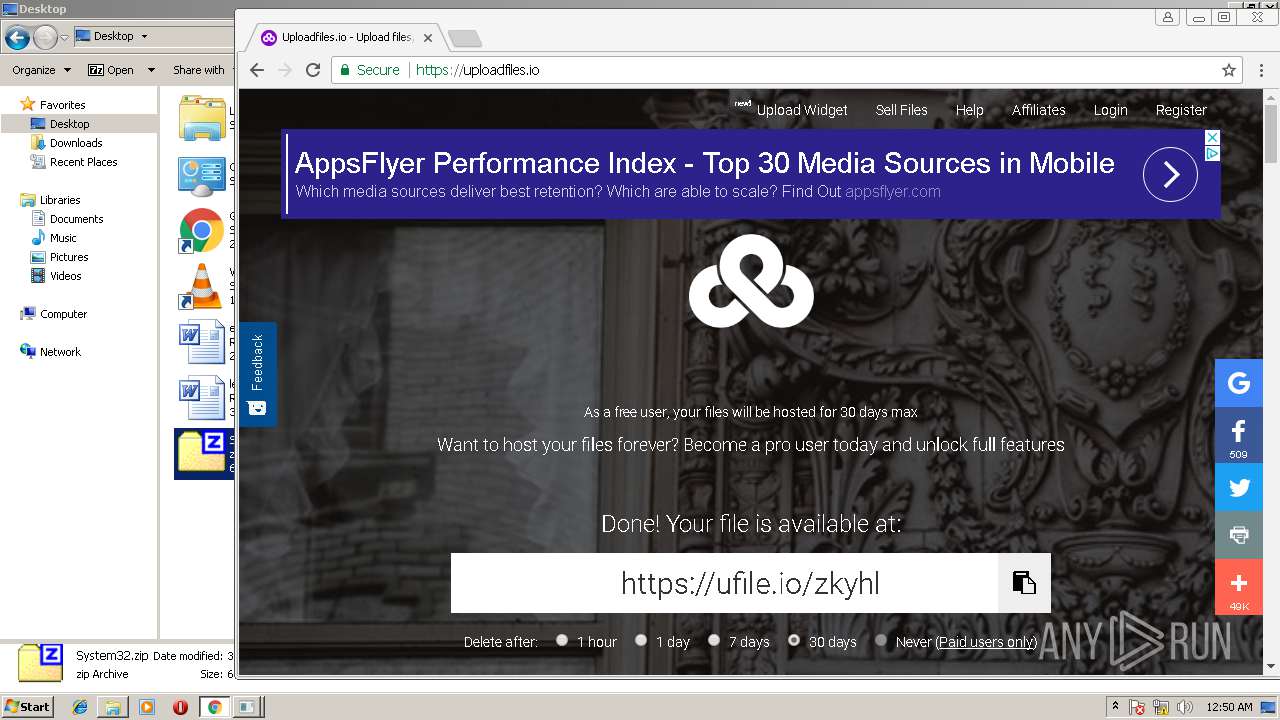
— | — | 104.18.59.162:443 | uploadfiles.io | Cloudflare Inc | US | shared |
— | — | 216.58.210.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
— | — | 216.58.210.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
— | — | 216.58.214.98:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
— | — | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 174.129.231.114:443 | source.unsplash.com | Amazon.com, Inc. | US | unknown |
— | — | 216.58.210.2:443 | adservice.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
teredo.ipv6.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.it |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
consent.google.com |
| shared |
www.google.com |
| malicious |
adservice.google.it |
| whitelisted |
uploadfiles.io |
| whitelisted |