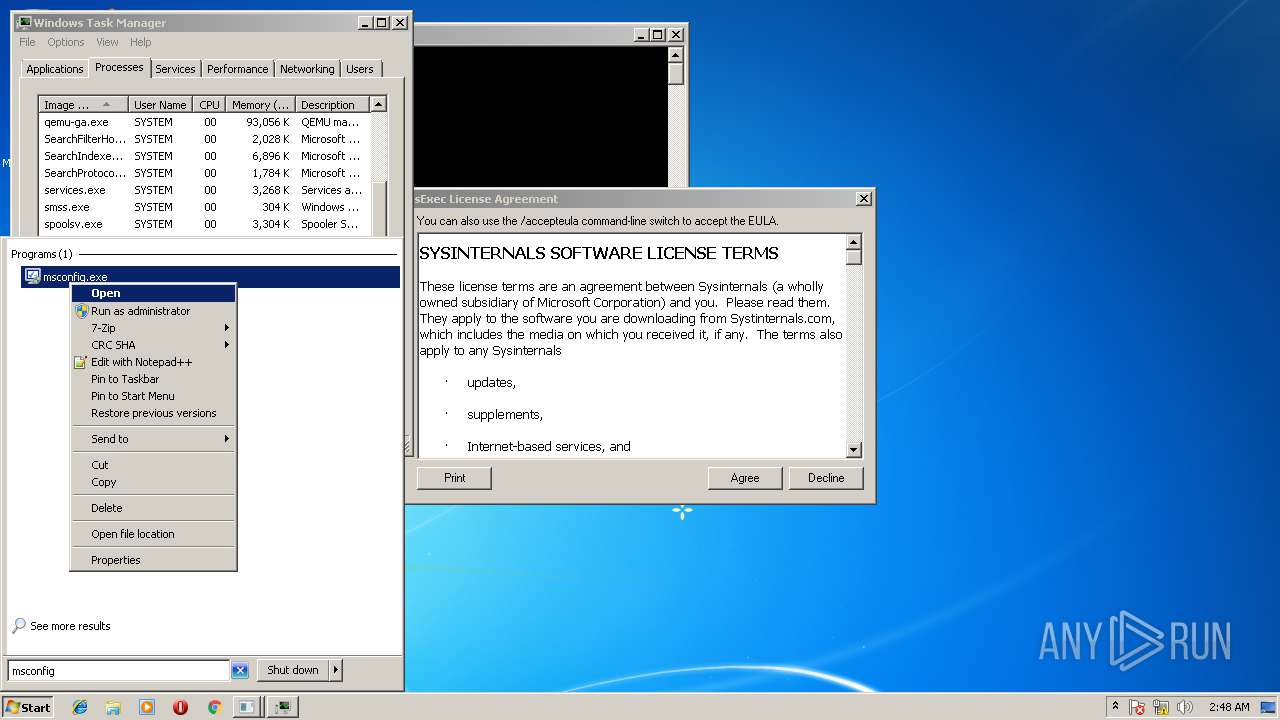
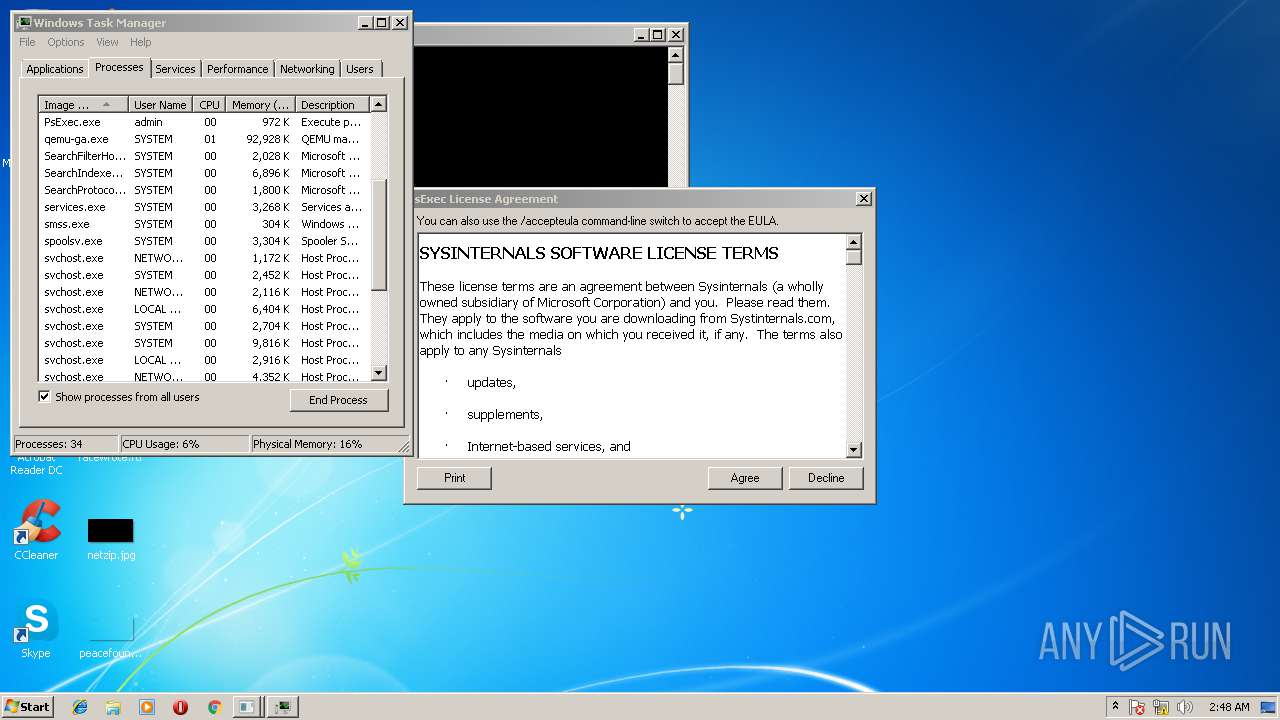
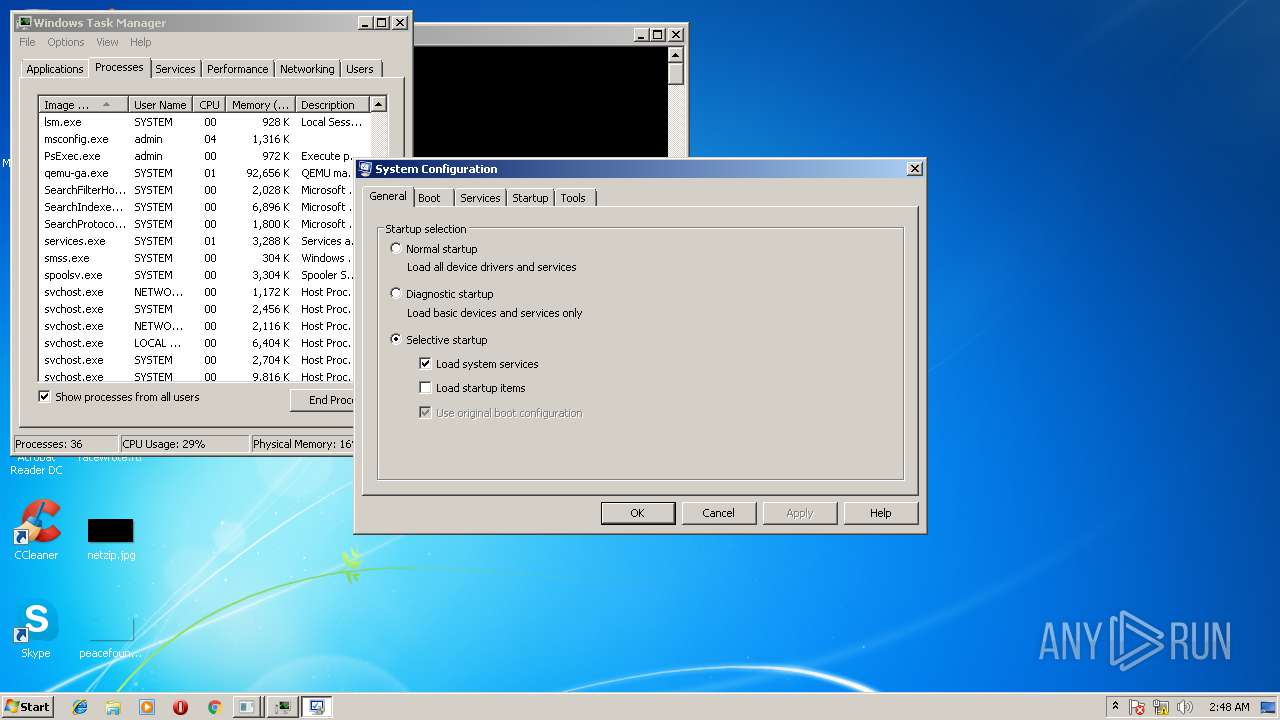
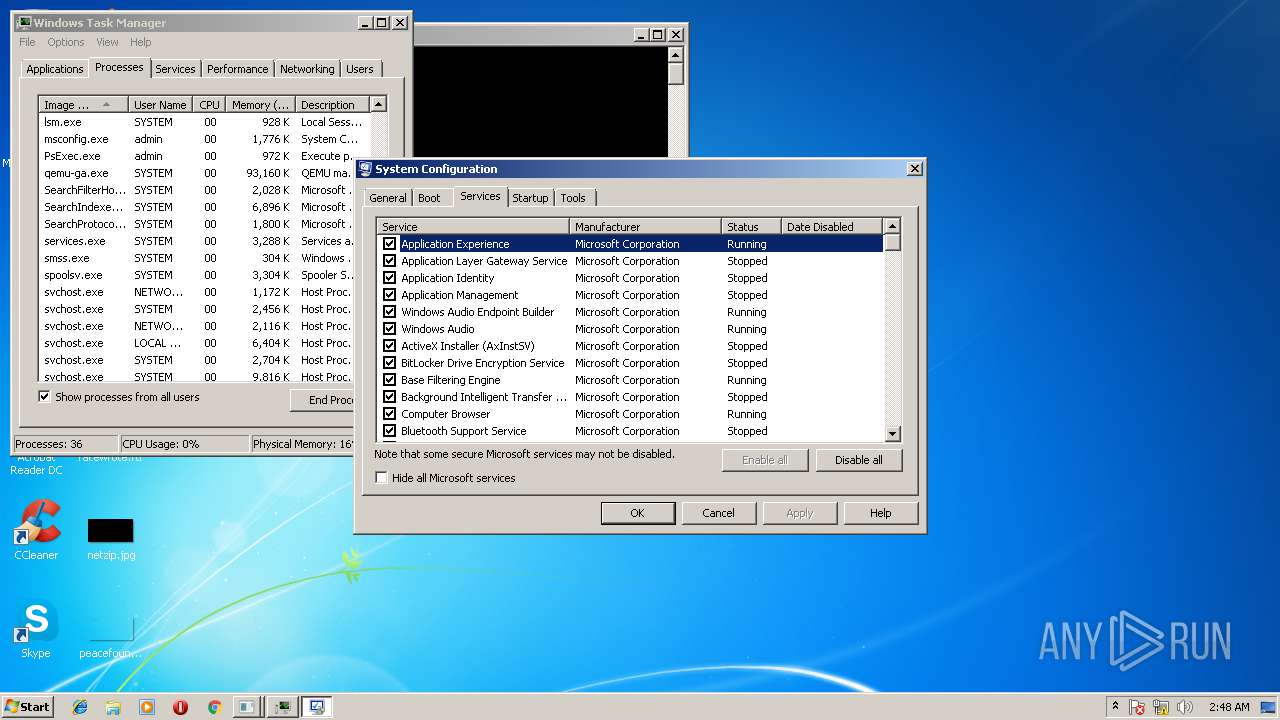
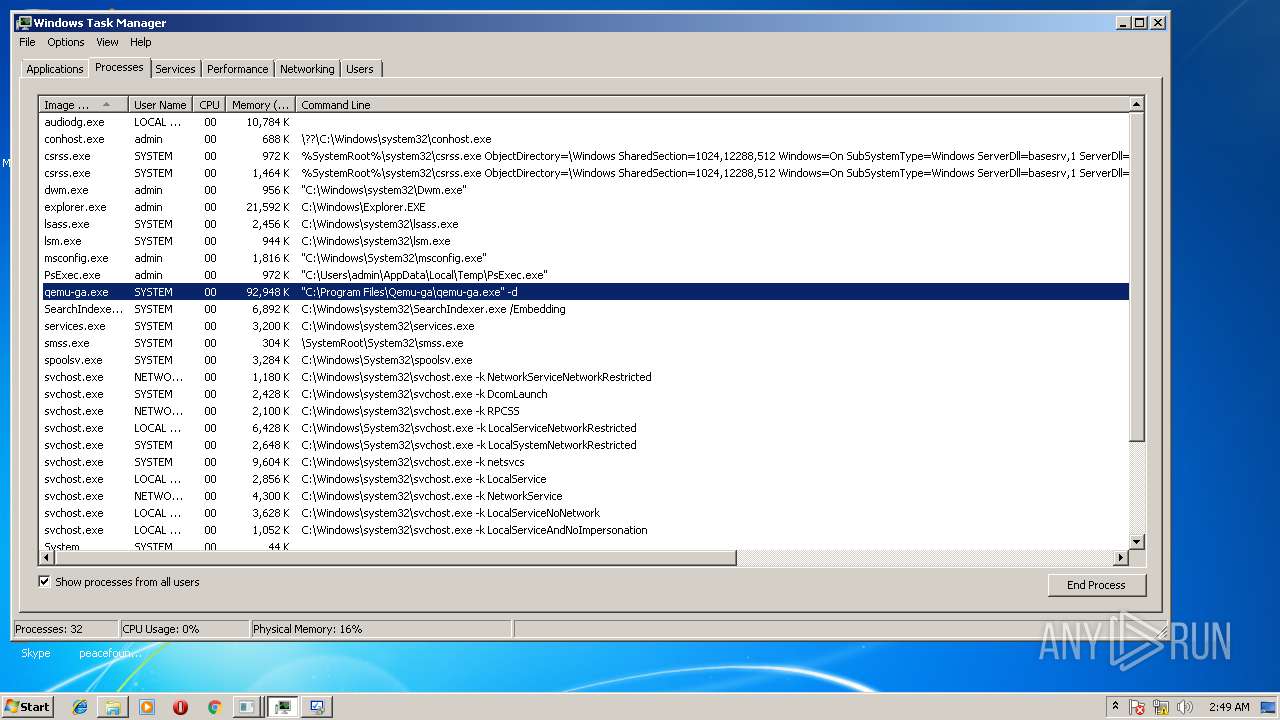
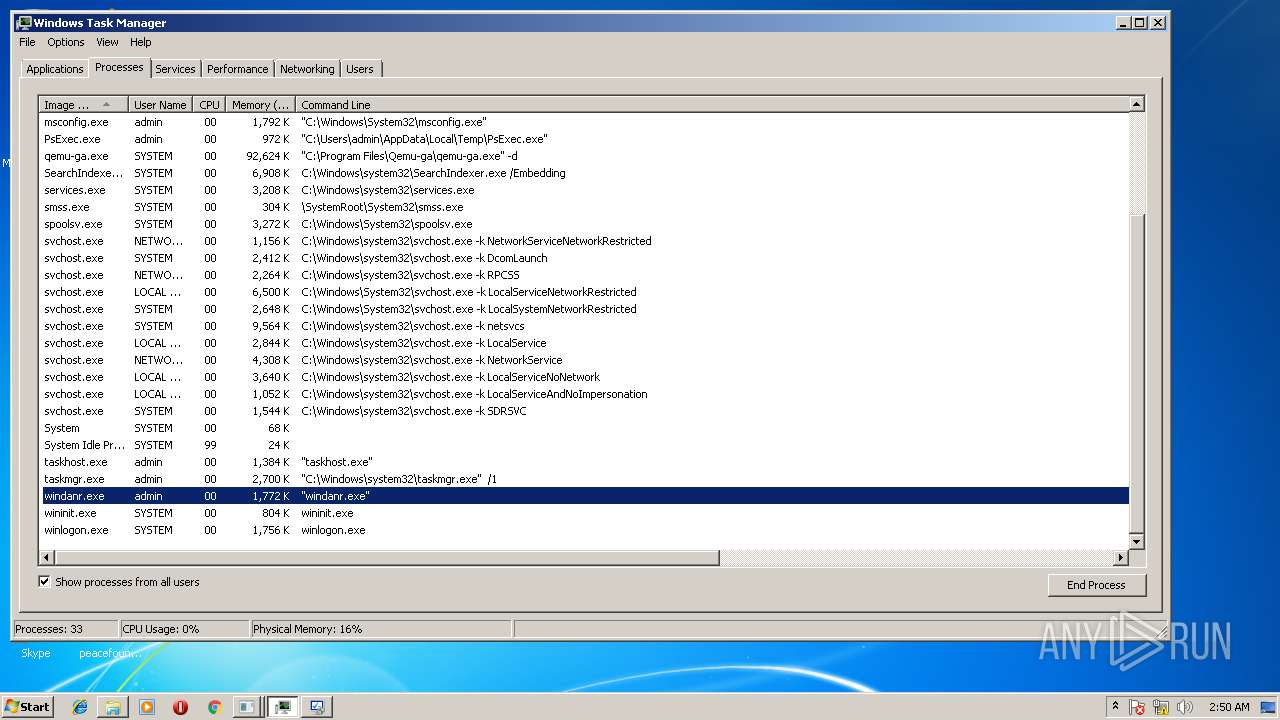
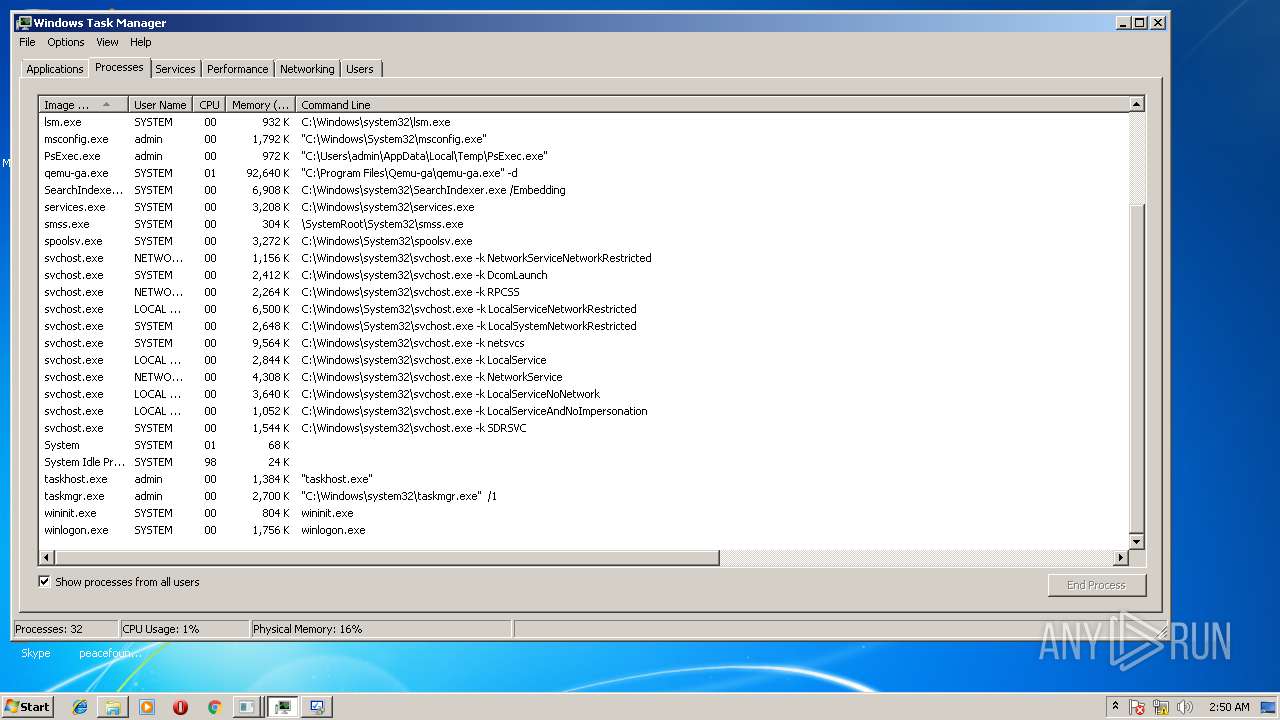
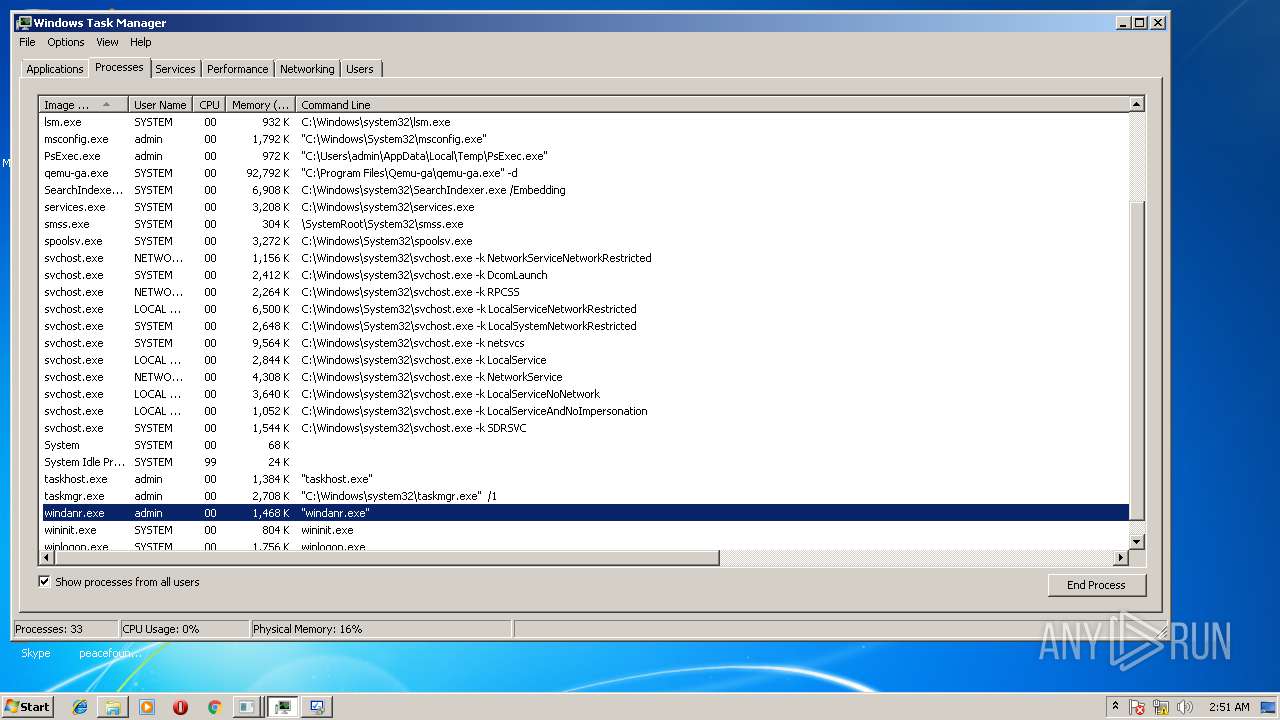
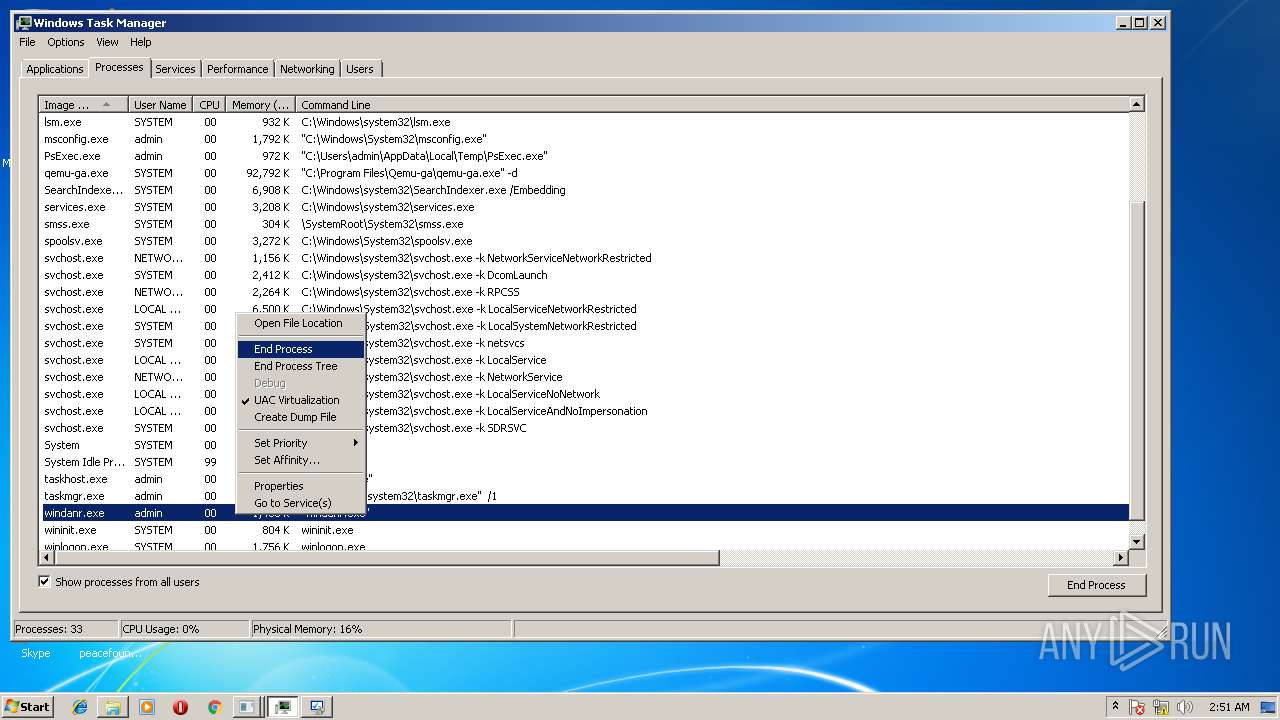
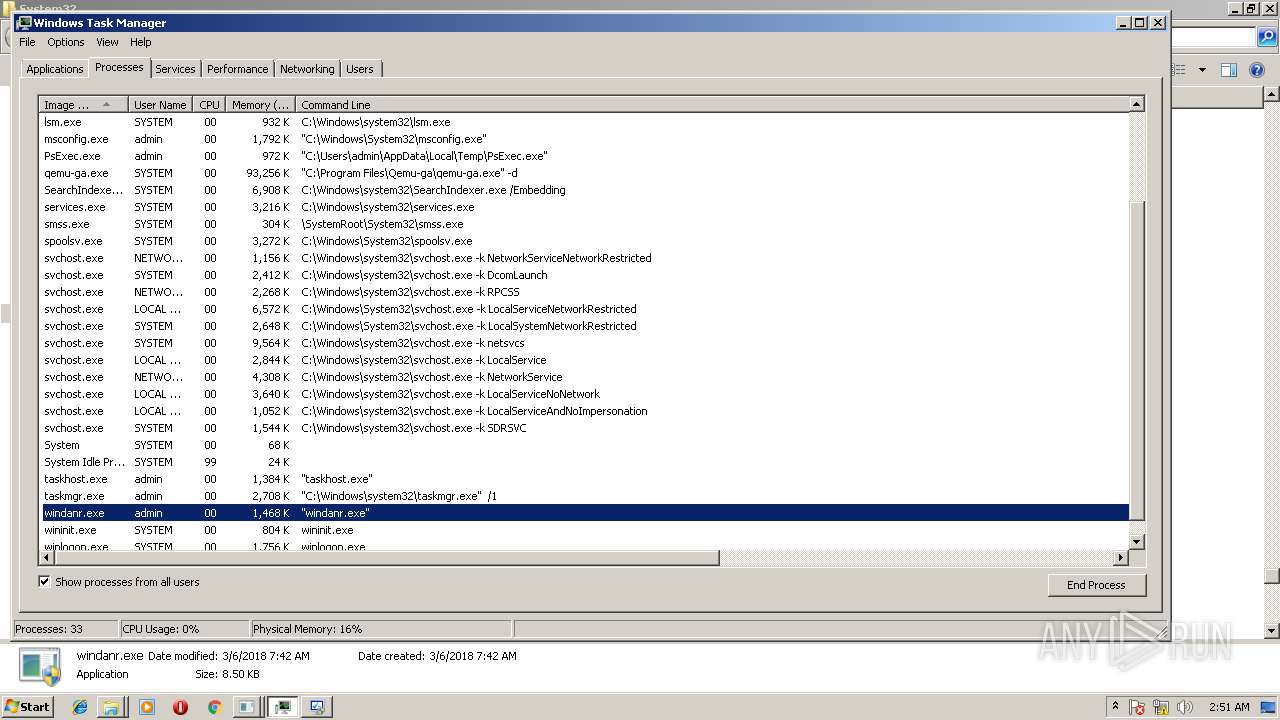
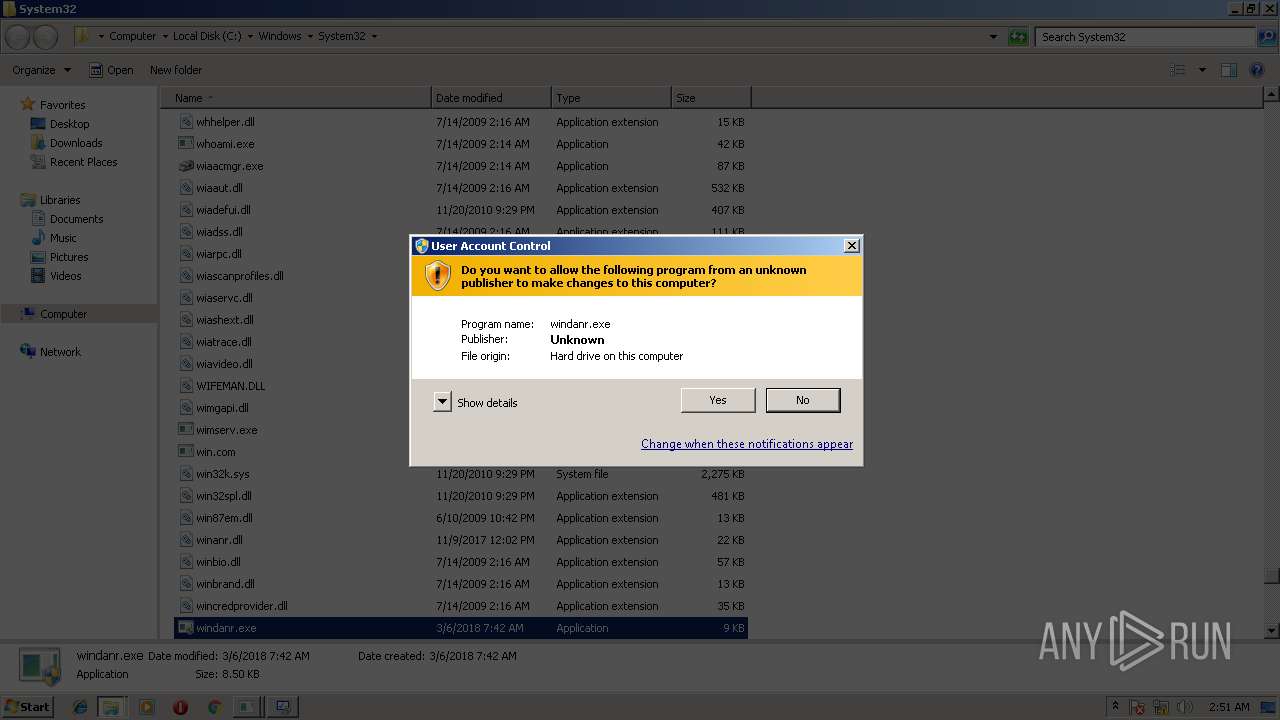
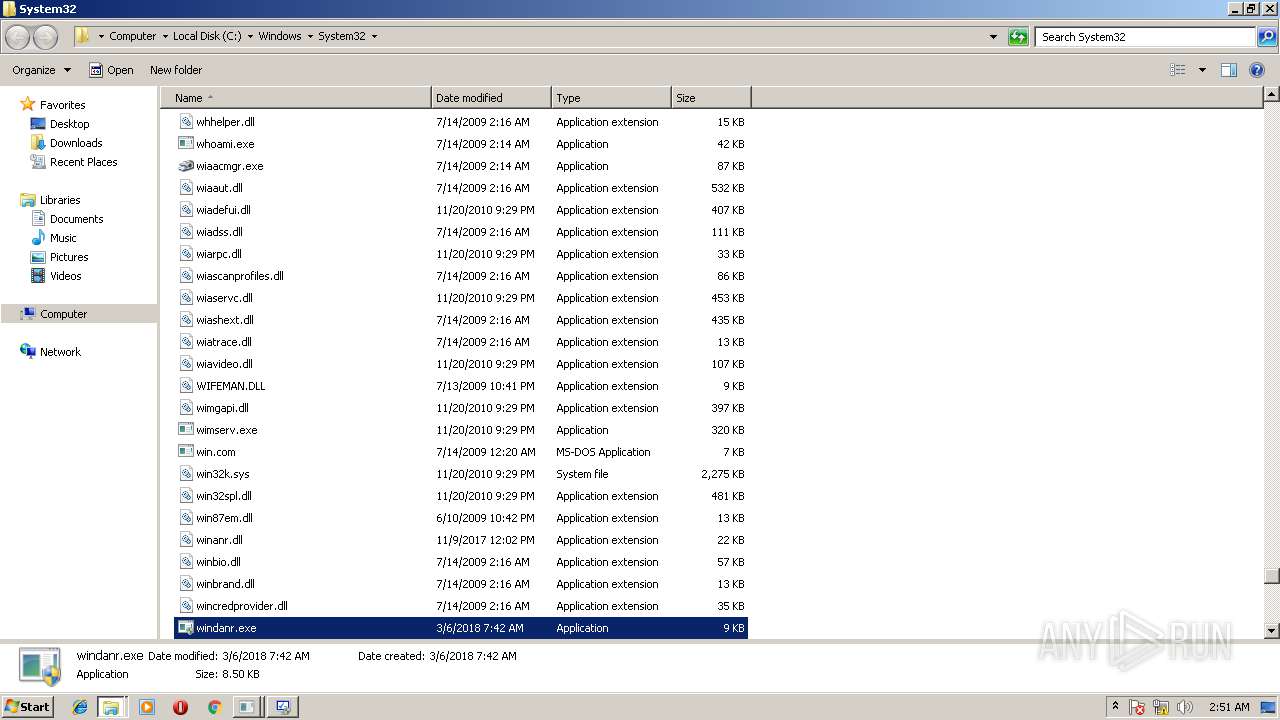
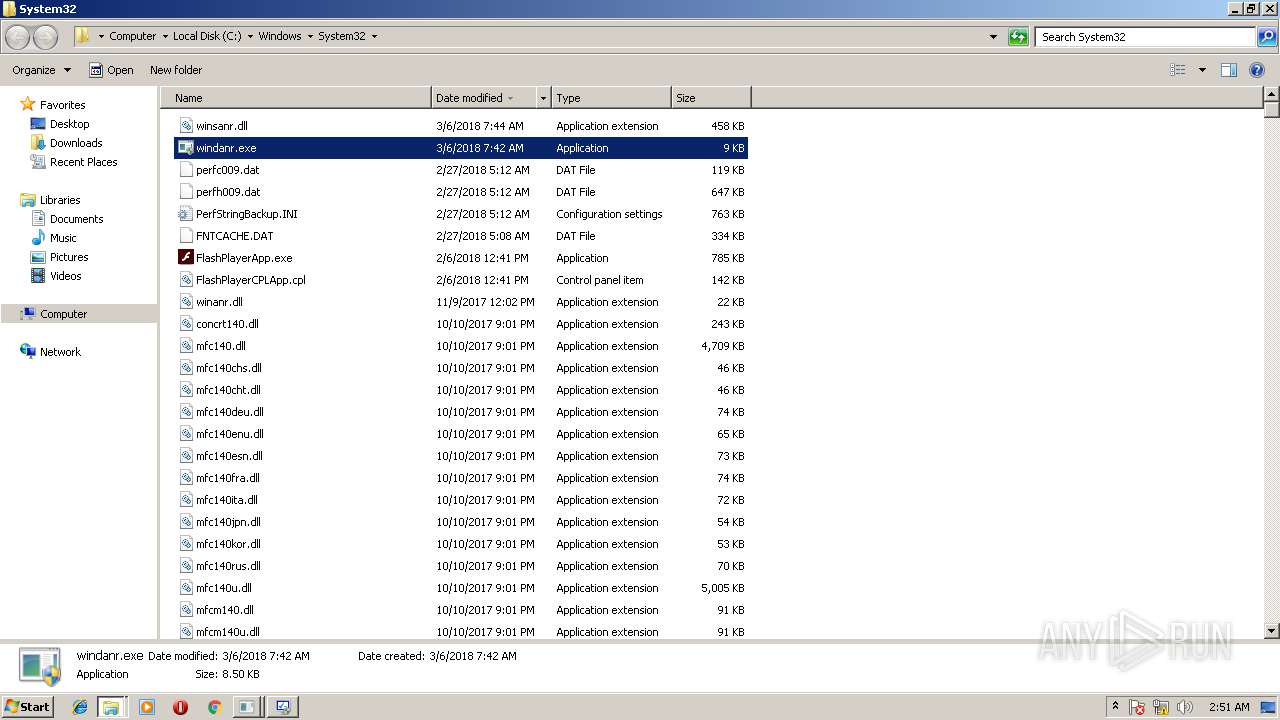
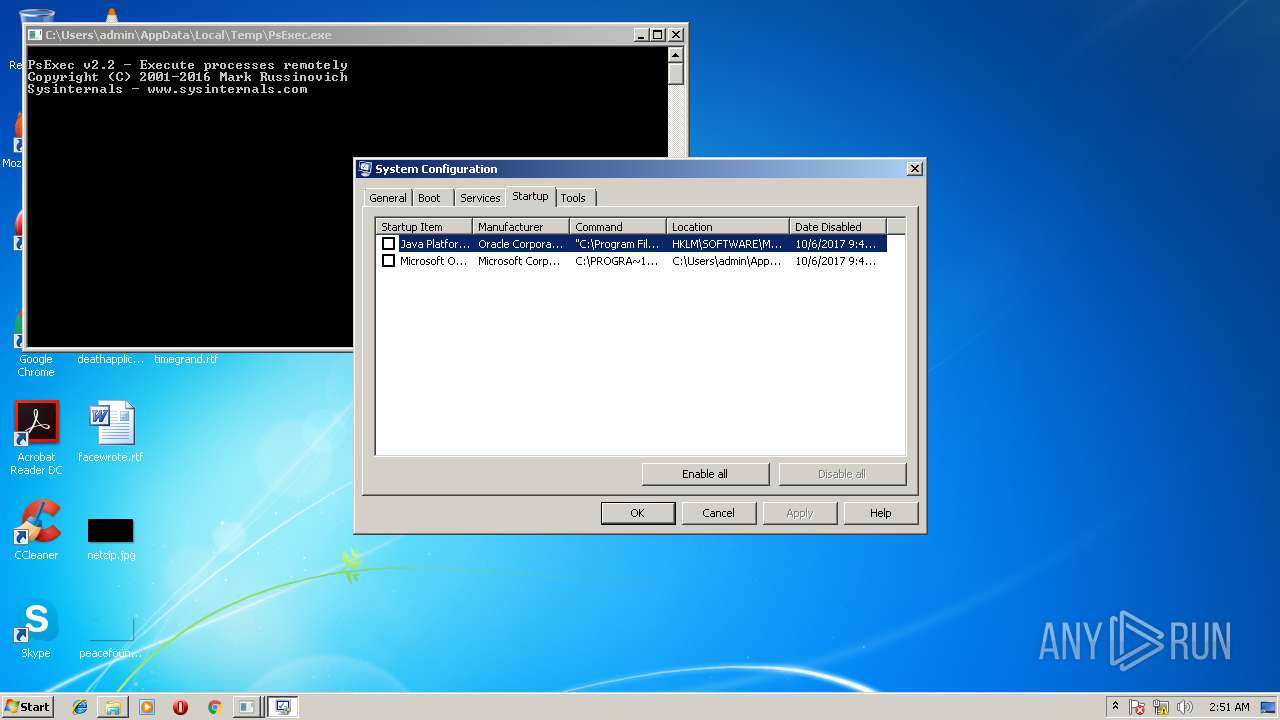
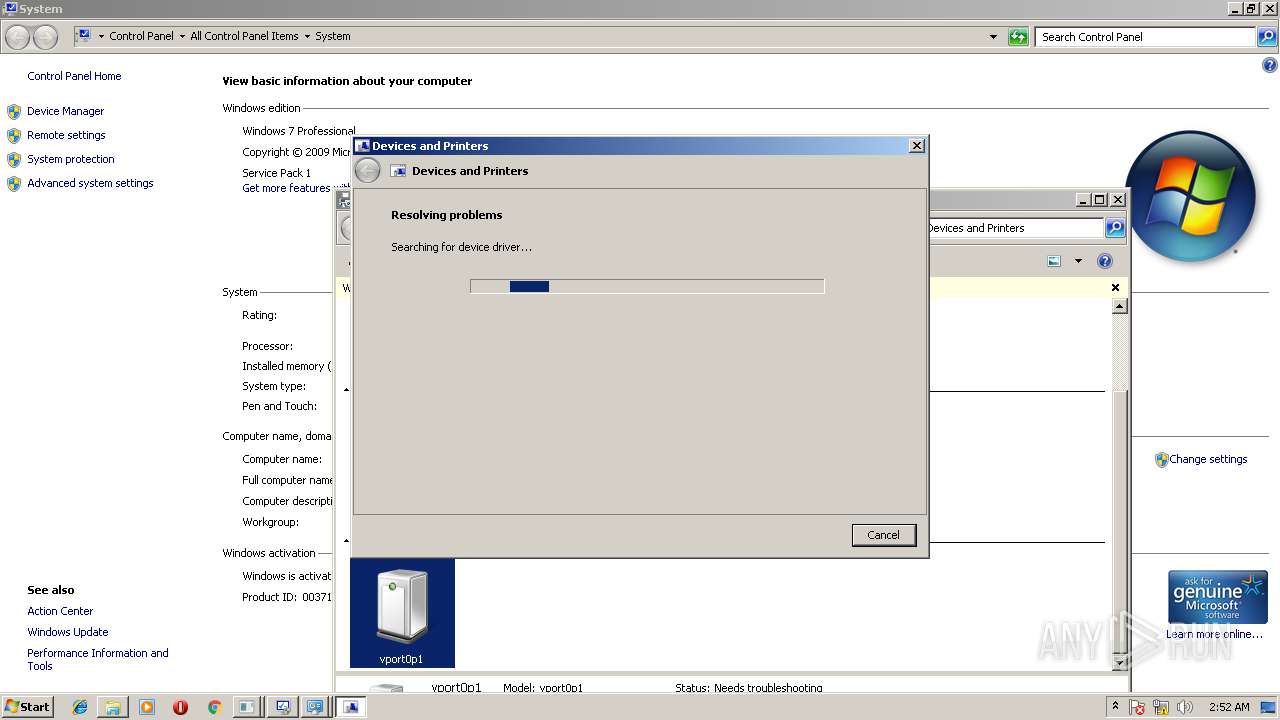
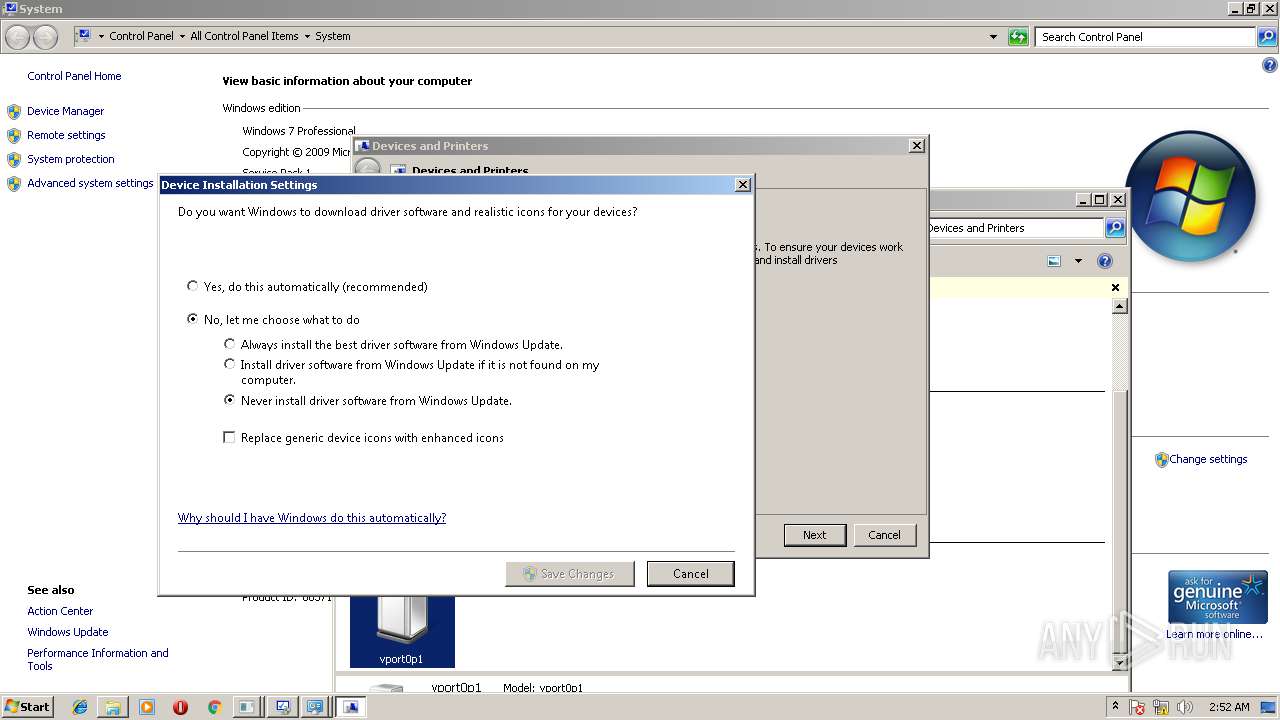
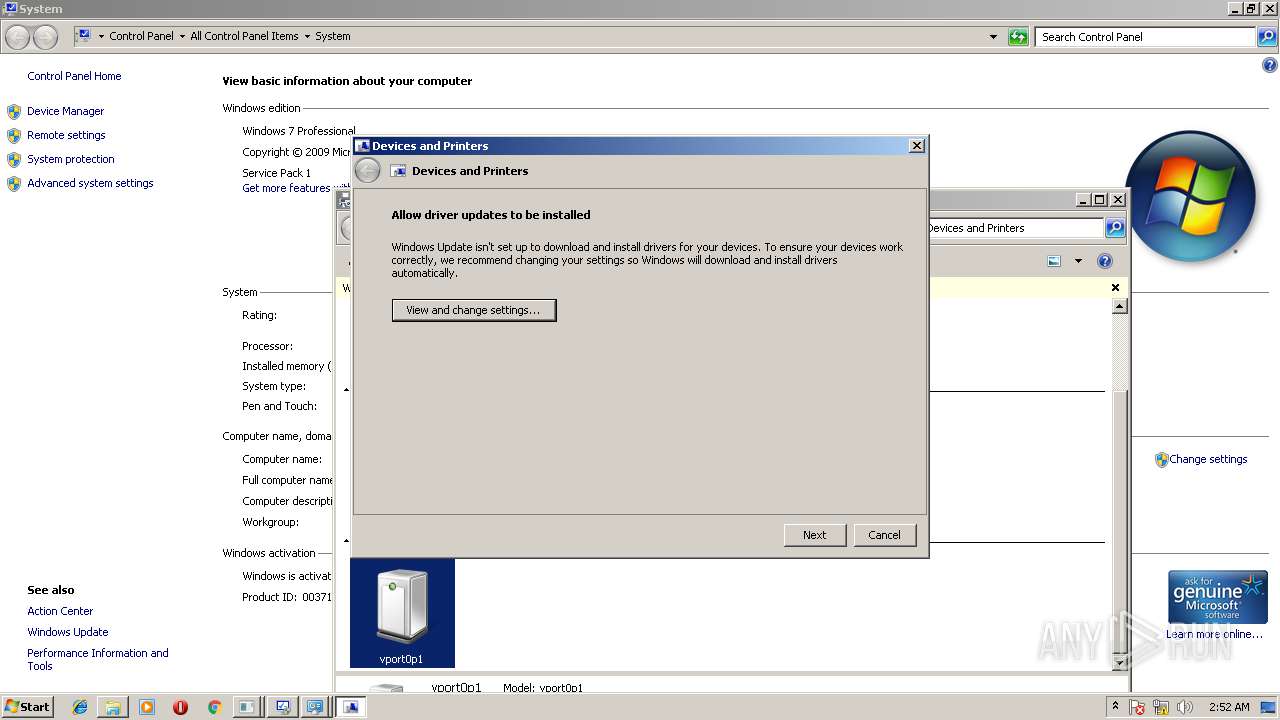
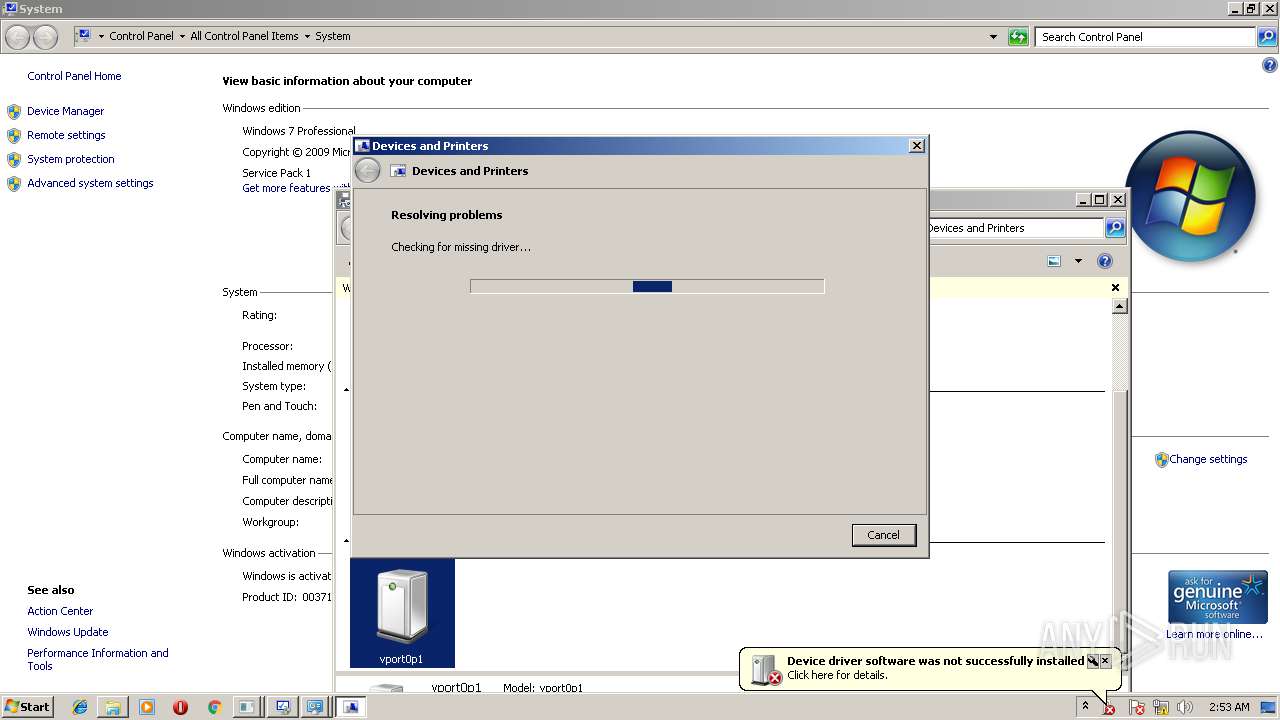
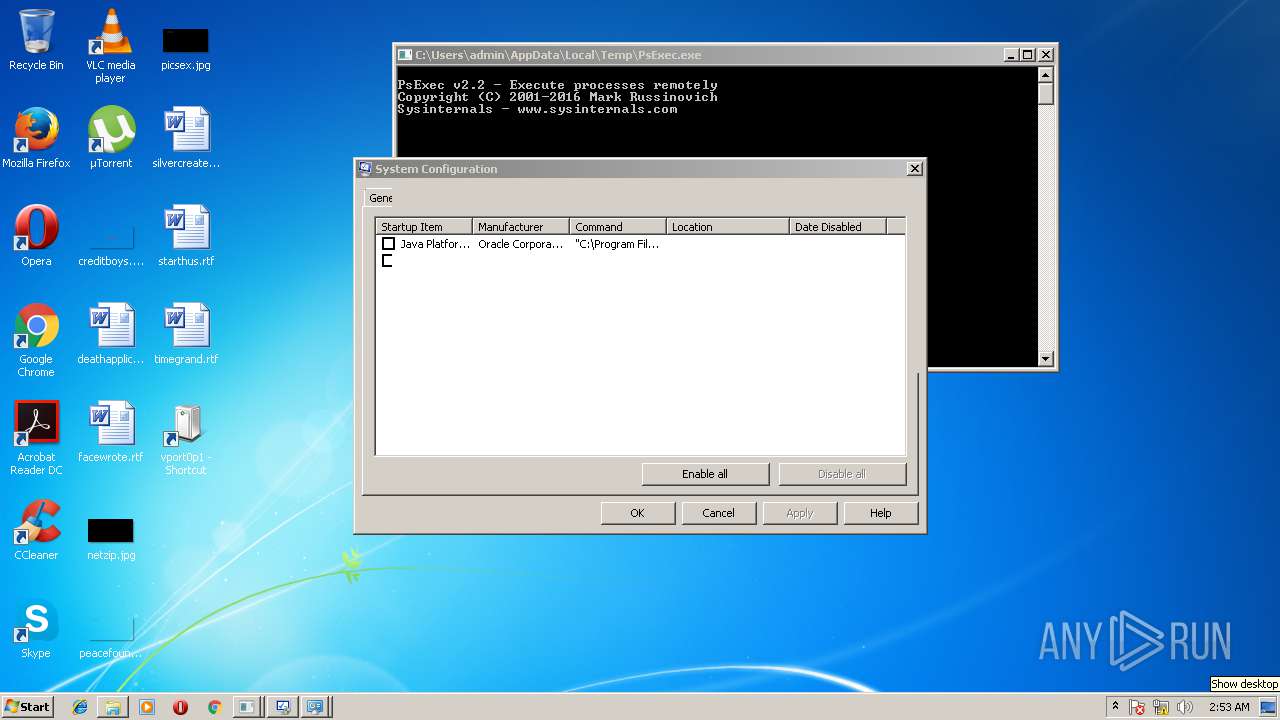
| File name: | PsExec.exe |
| Full analysis: | https://app.any.run/tasks/04893a3a-aa25-4112-9c7d-d166aefd7a2a |
| Verdict: | Malicious activity |
| Analysis date: | March 12, 2018, 02:48:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 27304B246C7D5B4E149124D5F93C5B01 |
| SHA1: | E50D9E3BD91908E13A26B3E23EDEAF577FB3A095 |
| SHA256: | 3337E3875B05E0BFBA69AB926532E3F179E8CFBF162EBB60CE58A0281437A7EF |
| SSDEEP: | 3072:Yao79VuJ6titIi/H7ZUFgllxiBD+P5xWr3geNtdS+DlGttzhA9HY4ZUFxPkwlmlP:YaSq4TBWISSTgu7DlGtEC1xn/O5r4S |
MALICIOUS
No malicious indicators.SUSPICIOUS
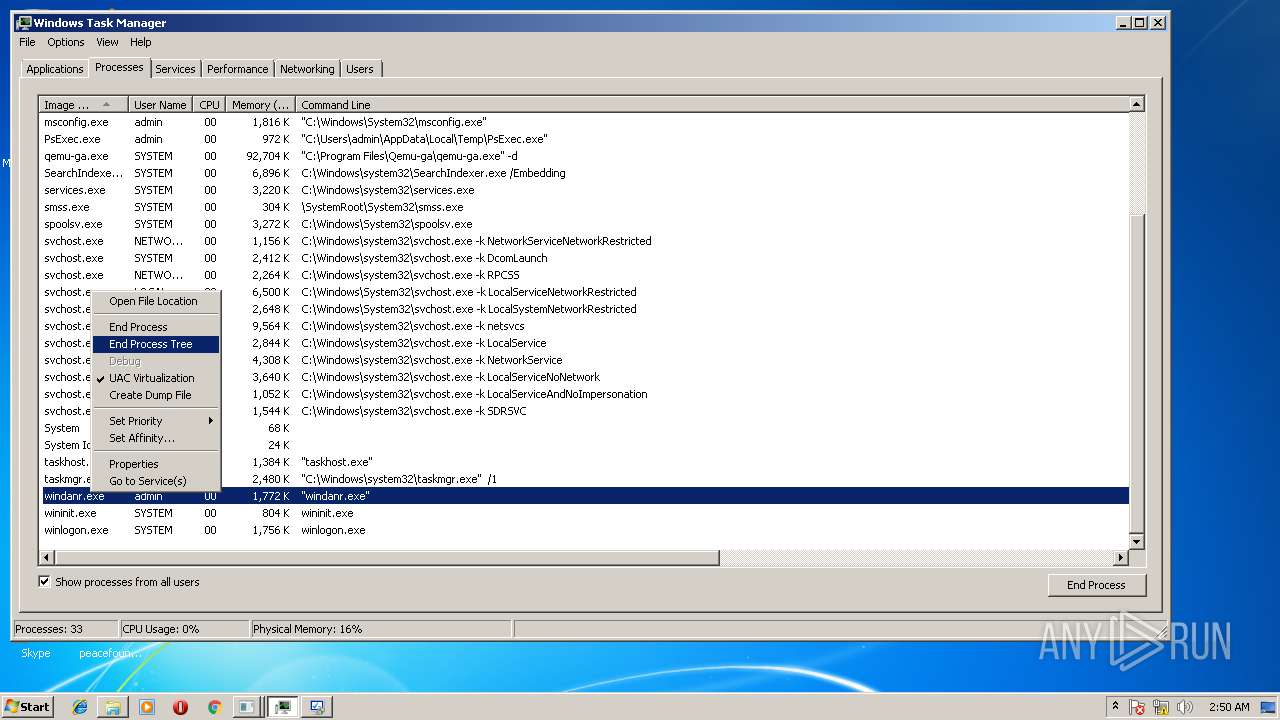
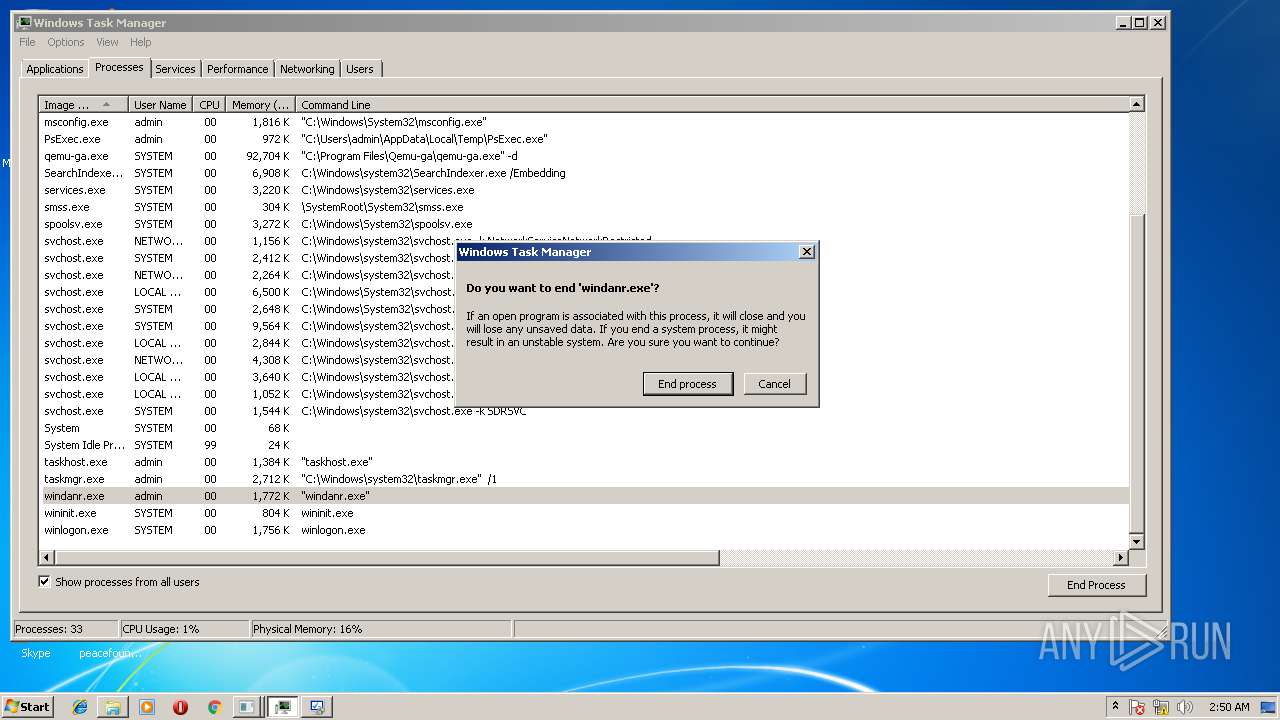
Application launched itself
- taskmgr.exe (PID: 3116)
- msdt.exe (PID: 2824)
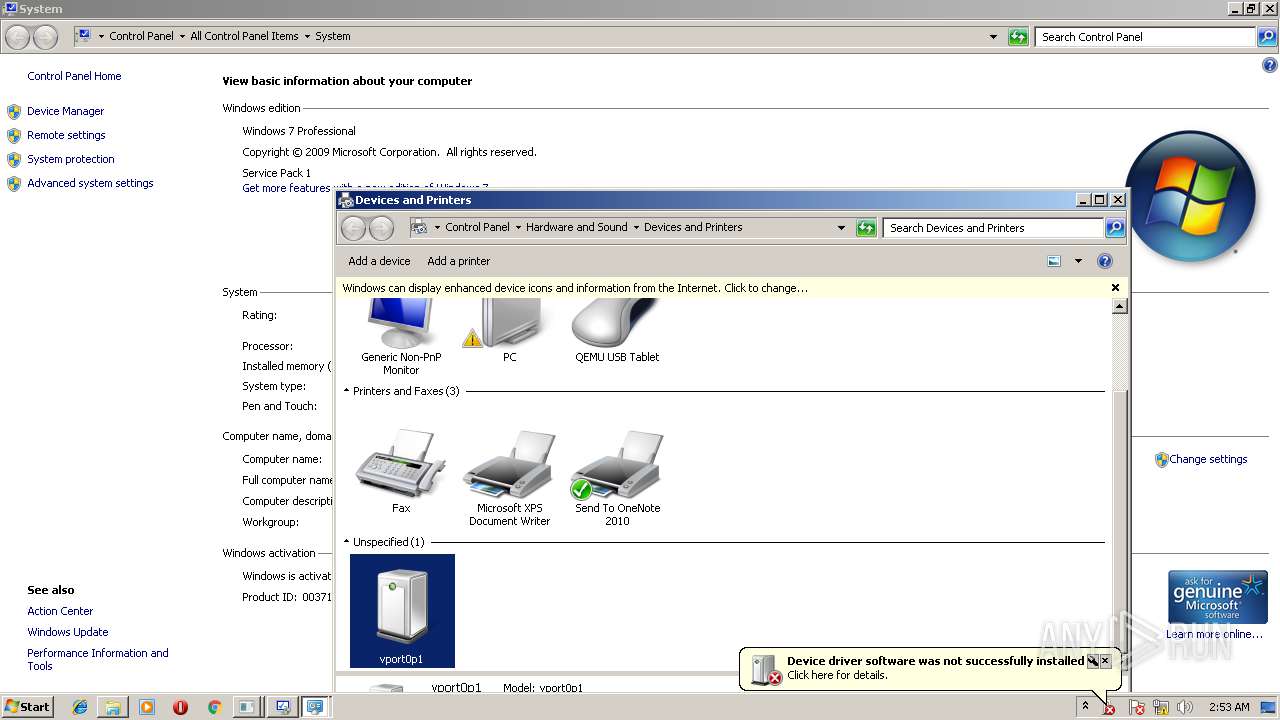
Low-level read access rights to disk partition
- msconfig.exe (PID: 2564)
Creates files in the program directory
- sdiagnhost.exe (PID: 2020)
Removes files from Windows directory
- msdt.exe (PID: 2844)
- DeviceDisplayObjectProvider.exe (PID: 1780)
Creates files in the Windows directory
- msdt.exe (PID: 2844)
- DeviceDisplayObjectProvider.exe (PID: 1780)
Modifies files in the system directory
- msdt.exe (PID: 2844)
- DeviceDisplayObjectProvider.exe (PID: 1780)
INFO
Loads rich edit control libraries
- PsExec.exe (PID: 2924)
Loads the .NET runtime environment
- sdiagnhost.exe (PID: 4068)
- sdiagnhost.exe (PID: 2020)
- sdiagnhost.exe (PID: 3460)
Dropped object may contain URL's
- msdt.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:06:28 20:43:09+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 99840 |
| InitializedDataSize: | 400896 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9de6 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.20.0.0 |
| ProductVersionNumber: | 2.20.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Execute processes remotely |
| FileVersion: | 2.2 |
| InternalName: | PsExec |
| LegalCopyright: | Copyright (C) 2001-2016 Mark Russinovich |
| OriginalFileName: | psexec.c |
| ProductName: | Sysinternals PsExec |
| ProductVersion: | 2.2 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 28-Jun-2016 18:43:09 |
| Detected languages: |
|
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Execute processes remotely |
| FileVersion: | 2.2 |
| InternalName: | PsExec |
| LegalCopyright: | Copyright (C) 2001-2016 Mark Russinovich |
| OriginalFilename: | psexec.c |
| ProductName: | Sysinternals PsExec |
| ProductVersion: | 2.2 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 28-Jun-2016 18:43:09 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000184C4 | 0x00018600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.58676 |
.rdata | 0x0001A000 | 0x0000E62A | 0x0000E800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.59667 |
.data | 0x00029000 | 0x0002DD9C | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.18234 |
.rsrc | 0x00057000 | 0x00023F18 | 0x00024000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.37889 |
.reloc | 0x0007B000 | 0x00001750 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.63142 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
7 | 2.38755 | 122 | UNKNOWN | English - United States | RT_STRING |
PSEXESVC | 6.40332 | 145568 | UNKNOWN | English - United States | BINRES |
Imports
ADVAPI32.dll |
COMDLG32.dll |
KERNEL32.dll |
MPR.dll |
NETAPI32.dll |
USER32.dll (delay-loaded) |
VERSION.dll |
WS2_32.dll |
Total processes
102
Monitored processes
37
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 500 | "C:\Windows\System32\dinotify.exe" pnpui.dll,SimplifiedDINotification | C:\Windows\System32\dinotify.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Device Installation Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 516 | "C:\Windows\System32\rundll32.exe" newdev.dll,DeviceInternetSettingUi 6 | C:\Windows\System32\rundll32.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1388 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES7E33.tmp" "c:\Users\admin\AppData\Local\Temp\CSC7E32.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1780 | C:\Windows\system32\DeviceDisplayObjectProvider.exe -Embedding | C:\Windows\system32\DeviceDisplayObjectProvider.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Device Display Object Function Discovery Provider Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2020 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2172 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\sipscvsj.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 2204 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\snscj2nx.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 2260 | "C:\Windows\System32\newdev.exe" "00000005" "1" "1" "1" | C:\Windows\System32\newdev.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Device driver software installation Exit code: 0 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 2432 | DrvInst.exe "1" "200" "{6FDE7547-1B65-48AE-B628-80BE62016026}\VIOSERIALPORT\4&7E8053E&0&01" "" "" "6392b1ab7" "00000000" "000005E4" "000005D0" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 3758096899 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2512 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\omseh-ag.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
Total events
795
Read events
743
Write events
52
Delete events
0
Modification events
| (PID) Process: | (3116) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3116) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3116) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 30030000E803000001000000010000000A0000000A0000009E010000C90100000100000001000000000000000000000001000000000000000100000000000000000000000200000004000000090000001D000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005A0000004000000021000000460000004A000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000000001000000020000000300000004000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0500000000000000FFFFFFFF00000000020000000300000004000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000630060003C005A00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000000010000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0400000000000000FFFFFFFF00000000010000004F00000028000000500000003400000050000000000000000100000002000000030000000400000000000000FFFFFFFF43000000000000000000000001000000 | |||
| (PID) Process: | (3116) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | UsrColumnSettings |
Value: 1C0C0000340400000000000050000000010000001D0C0000350400000000000023000000010000001E0C000036040000000000003C000000010000001F0C000039040000000000004E00000001000000200C000037040000000000004E00000001000000 | |||
| (PID) Process: | (3684) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | UsrColumnSettings |
Value: 1C0C0000340400000000000050000000010000001D0C0000350400000000000023000000010000001E0C000036040000000000003C000000010000001F0C000039040000000000004E00000001000000200C000037040000000000004E00000001000000 | |||
| (PID) Process: | (3684) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 30030000E803000001000000010000000A0000000A00000094040000820200000100000001000000000000000000000001000000000000000100000000000000000000000200000004000000090000001B0000001D000000FFFFFFFF000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005A0000004000000021000000460000007B0500004A000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000100000002000000030000000400000005000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0600000000000000FFFFFFFF00000000020000000300000004000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000630060003C005A00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000000010000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0400000000000000FFFFFFFF00000000010000004F00000028000000500000003400000050000000000000000100000002000000030000000400000000000000FFFFFFFF43000000000000000000000001000000 | |||
| (PID) Process: | (2972) control.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\8F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2824) msdt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2824) msdt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2844) msdt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\8F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
20
Suspicious files
12
Text files
327
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Temp\1520823127\PackageInfo.xml | — | |
MD5:— | SHA256:— | |||
| 2852 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Temp\DEL210E.tmp | — | |
MD5:— | SHA256:— | |||
| 2852 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Temp\DEL213E.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | wermgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\NonCritical_windanr.exe_a861fd63f52fa1473af65f3fe7d6ada6b8cd43f_cab_0c24541a\appcompat.txt | xml | |
MD5:— | SHA256:— | |||
| 3120 | wermgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\NonCritical_windanr.exe_a861fd63f52fa1473af65f3fe7d6ada6b8cd43f_cab_0c24541a\Report.wer | binary | |
MD5:— | SHA256:— | |||
| 2844 | msdt.exe | C:\Windows\TEMP\SDIAG_02d469ad-2070-43e3-850a-5af864eac43f\CL_Utility.ps1 | text | |
MD5:E9F758AACFF1008B8B85529ADC734F3B | SHA256:98736BA8B34E990474B807E8919D90451AF4765B9853FF2B71FFAAC2FEE0BB2A | |||
| 2844 | msdt.exe | C:\Windows\TEMP\SDIAG_02d469ad-2070-43e3-850a-5af864eac43f\TS_DeviceCenter.ps1 | text | |
MD5:3F879330B7CE24B103E0BAABDAB906DC | SHA256:EA24244624D2B4395BFDC26C18ED8E464A2D0CC1930991553F2B1EF0A0F58FF1 | |||
| 3120 | wermgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\NonCritical_windanr.exe_a861fd63f52fa1473af65f3fe7d6ada6b8cd43f_cab_0c24541a\Tab536E.tmp | text | |
MD5:35ED452BF054111134EE0A22CF29B770 | SHA256:A6C27302C2C28217F4619165F1FAEC76C65CC6B2E77C304A1D4EDBFB1BEC4A4F | |||
| 2844 | msdt.exe | C:\Windows\TEMP\SDIAG_7462255c-1c6c-4cad-b4a2-89c926fc8aac\DB_DeviceErrorLibrary.ps1 | text | |
MD5:5C7D876B5F80E19C72AFAAF81C33A790 | SHA256:F867FBF0BF3F31FC9A7D6B0AF60147D9565E74AF608F9FD4D71E58F737A3456C | |||
| 2844 | msdt.exe | C:\Windows\TEMP\SDIAG_02d469ad-2070-43e3-850a-5af864eac43f\DiagPackage.diagpkg | xml | |
MD5:E6AEE313842FA3676F75086EC5197D8A | SHA256:FD361E3AAAE6C133B6604F3B8E0B760D61B9A0AA894B90C194C82DF62E6F9633 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
windanr.exe | FTH: (4060): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|