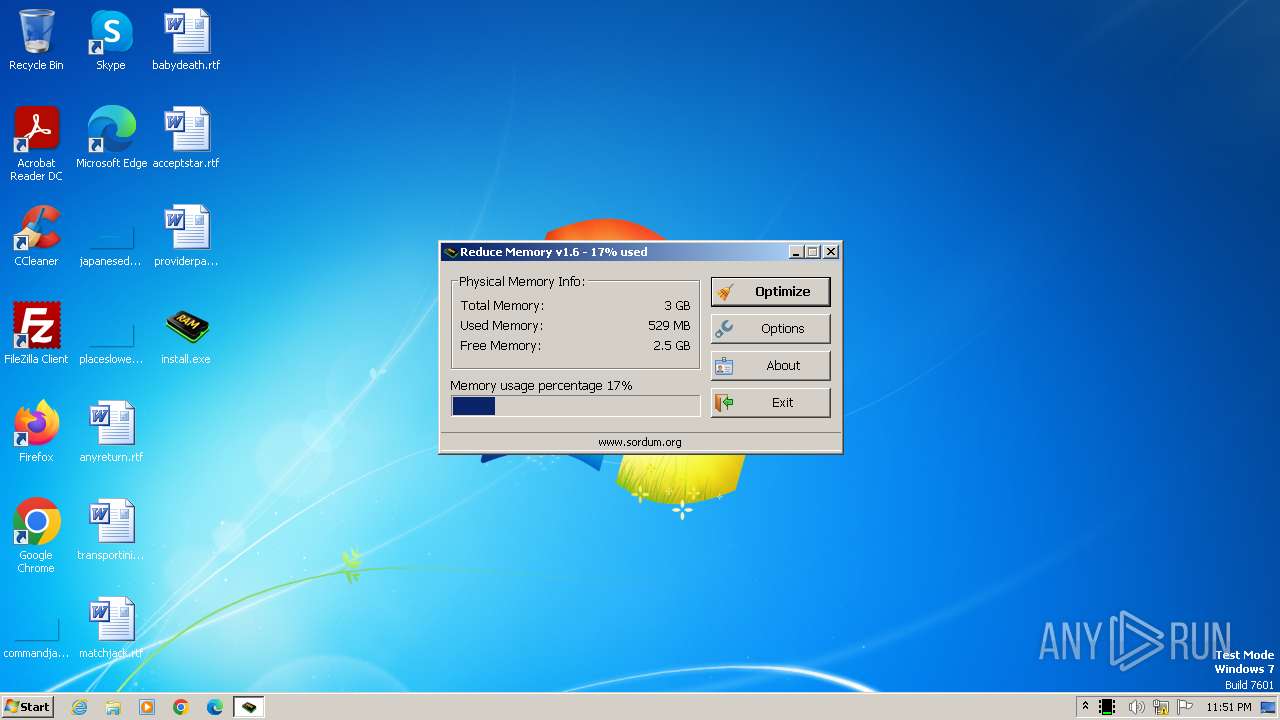
| File name: | install.exe |
| Full analysis: | https://app.any.run/tasks/29f215c1-1f59-4d70-a375-3c52c226e957 |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2023, 23:51:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9AA39A7C40A0807C0015DF61D463CA1D |
| SHA1: | 5410ACEABCE2679C0E09AF94D94F64E4B197B794 |
| SHA256: | 333304EDF4C371F627A365CBC348B1C644ADF36E38EA3B9C6E9DB0834A9D8976 |
| SSDEEP: | 98304:X+cD4dnPpkz+a+itlNLY0xvcVIDT1wJx33F+W+vDw8NNyAFEFczU3vdpjpr4VvZX:9U/m1WLYaHG |
MALICIOUS
Drops the executable file immediately after the start
- install.exe (PID: 3220)
- install.exe (PID: 3400)
- install.tmp (PID: 3624)
Creates a writable file the system directory
- install.tmp (PID: 3624)
SUSPICIOUS
Reads the Windows owner or organization settings
- install.tmp (PID: 3624)
The process drops C-runtime libraries
- install.tmp (PID: 3624)
Process drops legitimate windows executable
- install.tmp (PID: 3624)
Starts CMD.EXE for commands execution
- install.tmp (PID: 3624)
Executing commands from a ".bat" file
- install.tmp (PID: 3624)
Starts SC.EXE for service management
- cmd.exe (PID: 3688)
INFO
Create files in a temporary directory
- install.exe (PID: 3220)
- install.exe (PID: 3400)
- install.tmp (PID: 3624)
- ReduceMemory.exe (PID: 3812)
Checks supported languages
- install.tmp (PID: 3624)
- install.tmp (PID: 2912)
- install.exe (PID: 3220)
- ReduceMemory.exe (PID: 3812)
- install.exe (PID: 3400)
Creates files in the program directory
- install.tmp (PID: 3624)
Reads the computer name
- install.tmp (PID: 2912)
- install.tmp (PID: 3624)
- ReduceMemory.exe (PID: 3812)
Creates files or folders in the user directory
- install.tmp (PID: 3624)
Reads mouse settings
- ReduceMemory.exe (PID: 3812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 15:54:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 95232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Sordum |
| FileDescription: | Reduce Memory Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Reduce Memory |
| ProductVersion: | 1.6.2 |
Total processes
46
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2912 | "C:\Users\admin\AppData\Local\Temp\is-O3PUG.tmp\install.tmp" /SL5="$80180,4395467,838144,C:\Users\admin\Desktop\install.exe" | C:\Users\admin\AppData\Local\Temp\is-O3PUG.tmp\install.tmp | — | install.exe | |||||||||||
User: admin Company: Sordum Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3220 | "C:\Users\admin\Desktop\install.exe" | C:\Users\admin\Desktop\install.exe | — | explorer.exe | |||||||||||
User: admin Company: Sordum Integrity Level: MEDIUM Description: Reduce Memory Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3400 | "C:\Users\admin\Desktop\install.exe" /SPAWNWND=$601F4 /NOTIFYWND=$80180 | C:\Users\admin\Desktop\install.exe | install.tmp | ||||||||||||
User: admin Company: Sordum Integrity Level: HIGH Description: Reduce Memory Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\AppData\Local\Temp\is-EHLH4.tmp\install.tmp" /SL5="$501E6,4395467,838144,C:\Users\admin\Desktop\install.exe" /SPAWNWND=$601F4 /NOTIFYWND=$80180 | C:\Users\admin\AppData\Local\Temp\is-EHLH4.tmp\install.tmp | — | install.exe | |||||||||||
User: admin Company: Sordum Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3644 | sc create MsHelper binpath= "C:\Windows\System32\SysWin.exe" start=auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1639 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3688 | "C:\Windows\system32\cmd.exe" /C ""C:\Users\admin\AppData\Local\Temp\is-IO8GB.tmp\version.bat"" | C:\Windows\System32\cmd.exe | — | install.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3812 | "C:\Program Files\Reduce Memory\ReduceMemory.exe" | C:\Program Files\Reduce Memory\ReduceMemory.exe | — | install.tmp | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: Reduce Memory v1.6 Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 3852 | sc start MsHelper | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
541
Read events
535
Write events
0
Delete events
6
Modification events
| (PID) Process: | (3624) install.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: 160BA1FF778D949A455A6D60DCCAE90F7691C0EF7B9A87E067A3ABAAE1399D27 | |||
| (PID) Process: | (3624) install.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Windows\system32\vcruntime140_1.dll | |||
| (PID) Process: | (3624) install.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3624) install.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 4C46D4D34F9C14E4C0A218EB73F1D52DCCC29A4A0FB528349426002B44237E37 | |||
| (PID) Process: | (3624) install.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 280E0000C2634C57D511DA01 | |||
| (PID) Process: | (3624) install.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
16
Suspicious files
5
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3400 | install.exe | C:\Users\admin\AppData\Local\Temp\is-EHLH4.tmp\install.tmp | executable | |
MD5:43B0C7552B75960940A265585C6313E1 | SHA256:38EBC244904C22F8FE74BDDDD27E228C1DE55EC1870E8C24EFD08C3F46EBAA01 | |||
| 3220 | install.exe | C:\Users\admin\AppData\Local\Temp\is-O3PUG.tmp\install.tmp | executable | |
MD5:43B0C7552B75960940A265585C6313E1 | SHA256:38EBC244904C22F8FE74BDDDD27E228C1DE55EC1870E8C24EFD08C3F46EBAA01 | |||
| 3624 | install.tmp | C:\Program Files\Reduce Memory\unins000.exe | executable | |
MD5:13B54077E14D86958BA74196EDB070D9 | SHA256:BABBA8C8CD235EEFBCD7CD1010B4F15F5257716EEE95C4774D705A9F0CD44EFA | |||
| 3624 | install.tmp | C:\Program Files\Reduce Memory\is-MVO0E.tmp | executable | |
MD5:13B54077E14D86958BA74196EDB070D9 | SHA256:BABBA8C8CD235EEFBCD7CD1010B4F15F5257716EEE95C4774D705A9F0CD44EFA | |||
| 3624 | install.tmp | C:\Windows\system32\is-Q5NK4.tmp | executable | |
MD5:D6BAE36424C338607B79E7903E9DF10C | SHA256:37C48BAC38FAD93BFC5EAFB4D48CC145EA0BF8724F8F377406A3609883694904 | |||
| 3624 | install.tmp | C:\Windows\system32\is-PHO6S.tmp | executable | |
MD5:F7CD95A47F9C2291DB184C6C4AD7E120 | SHA256:10859F06F41144FA32CF5DA223511F85FE349B1D76471EF65F0395DAC606EF63 | |||
| 3624 | install.tmp | C:\Windows\System32\vcruntime140_1.dll | executable | |
MD5:D6BAE36424C338607B79E7903E9DF10C | SHA256:37C48BAC38FAD93BFC5EAFB4D48CC145EA0BF8724F8F377406A3609883694904 | |||
| 3624 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-IO8GB.tmp\is-C4JME.tmp | text | |
MD5:62098E319E21A4DFCBD6E9790DC61F7D | SHA256:3865E1DFBD08F9D3692A09BDF73DB6A3A17388A947503EA9A52C464F2CC120A7 | |||
| 3624 | install.tmp | C:\Windows\System32\msvcp90.dll | executable | |
MD5:F7CD95A47F9C2291DB184C6C4AD7E120 | SHA256:10859F06F41144FA32CF5DA223511F85FE349B1D76471EF65F0395DAC606EF63 | |||
| 3624 | install.tmp | C:\Users\admin\AppData\Local\Sordum\is-HNP95.tmp | text | |
MD5:DEE7283182D0F88E95E41848E394A5CA | SHA256:F145E35EB715F88C5FAFA300296B4E5B554DA3B9CFF51A88C58C784134B4D1C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |