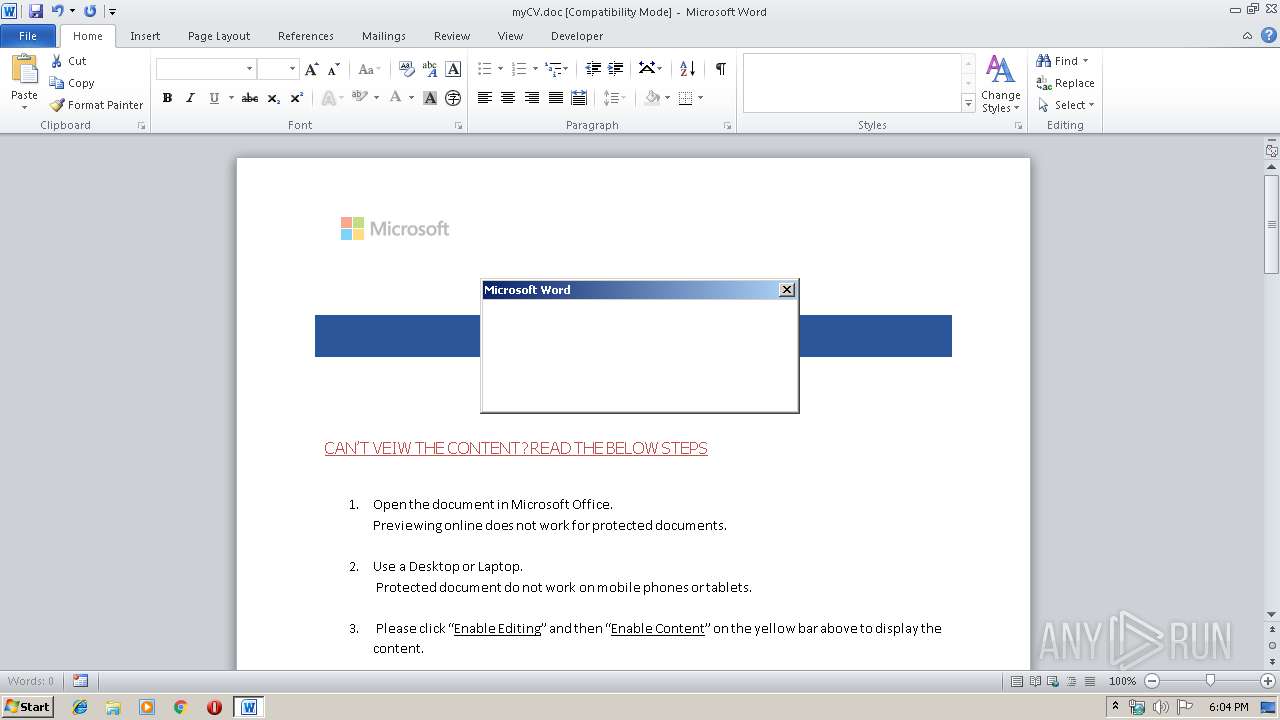
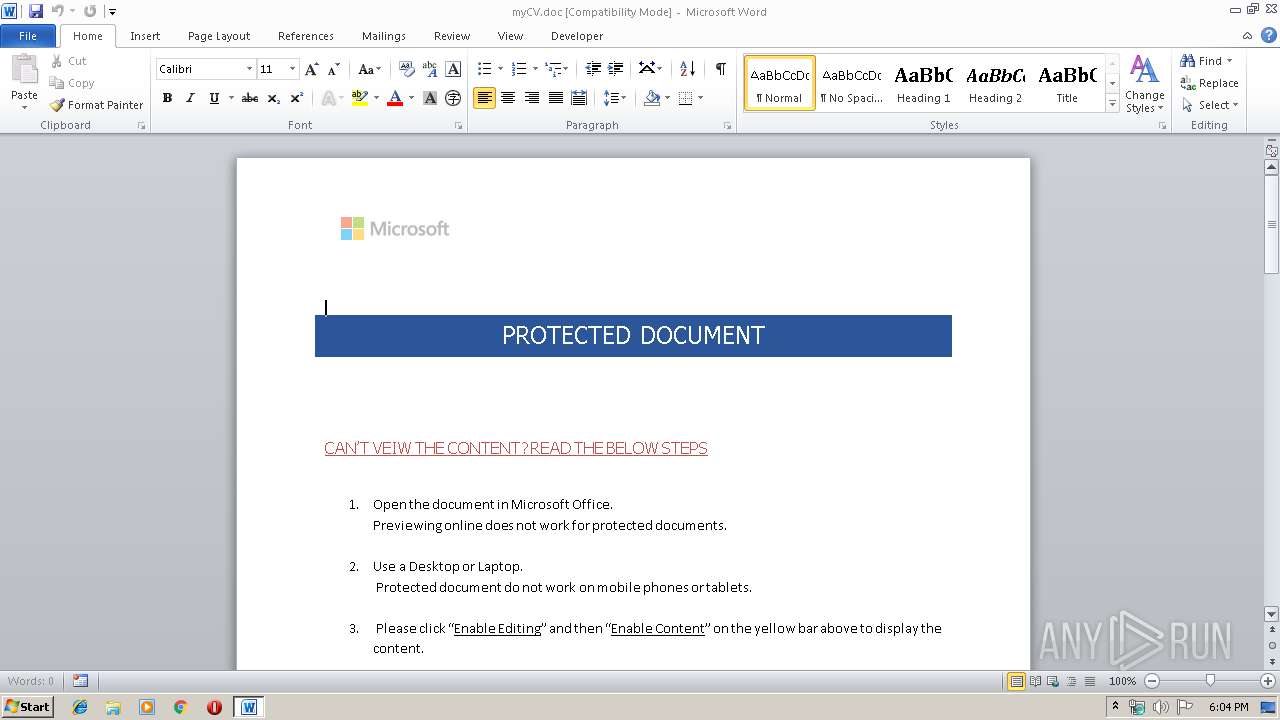
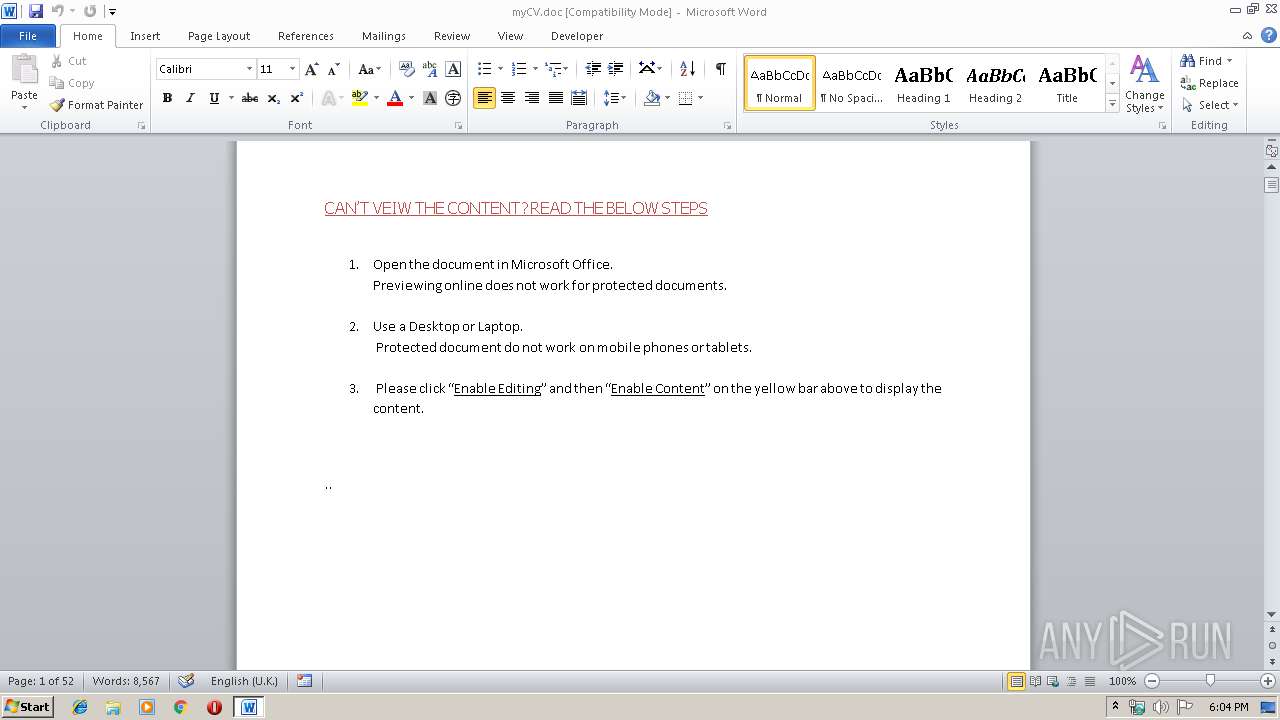
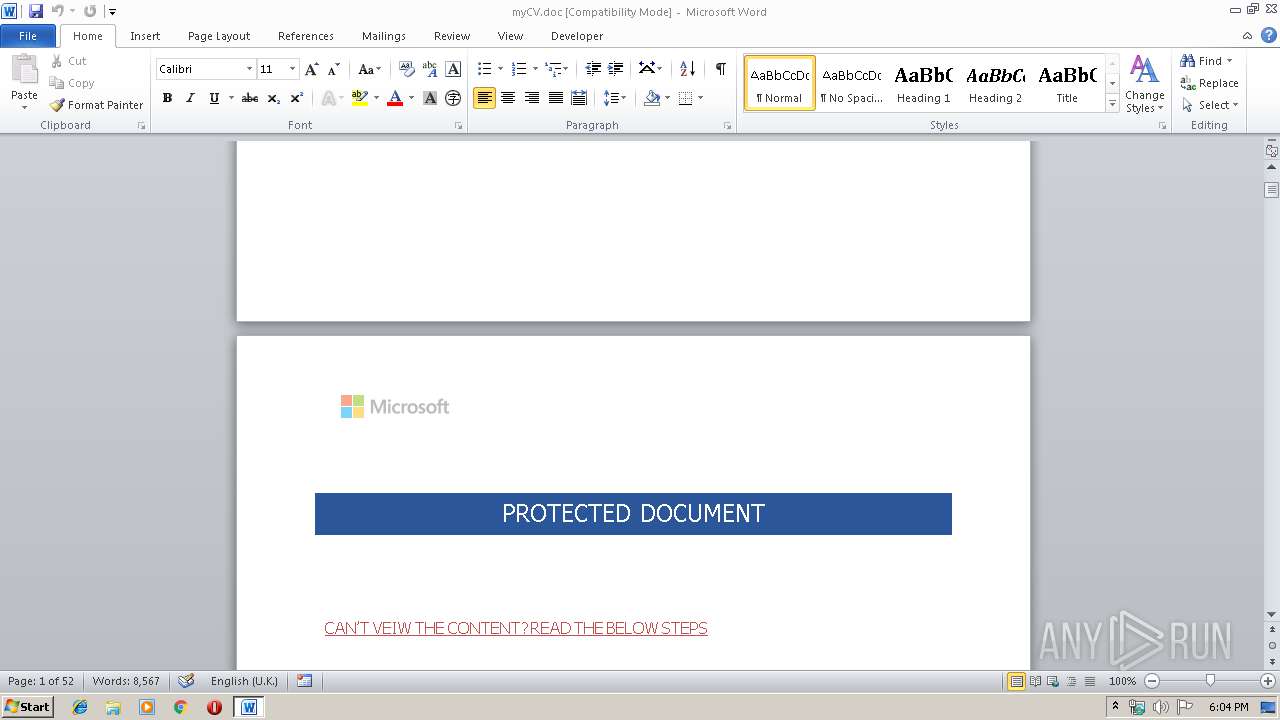
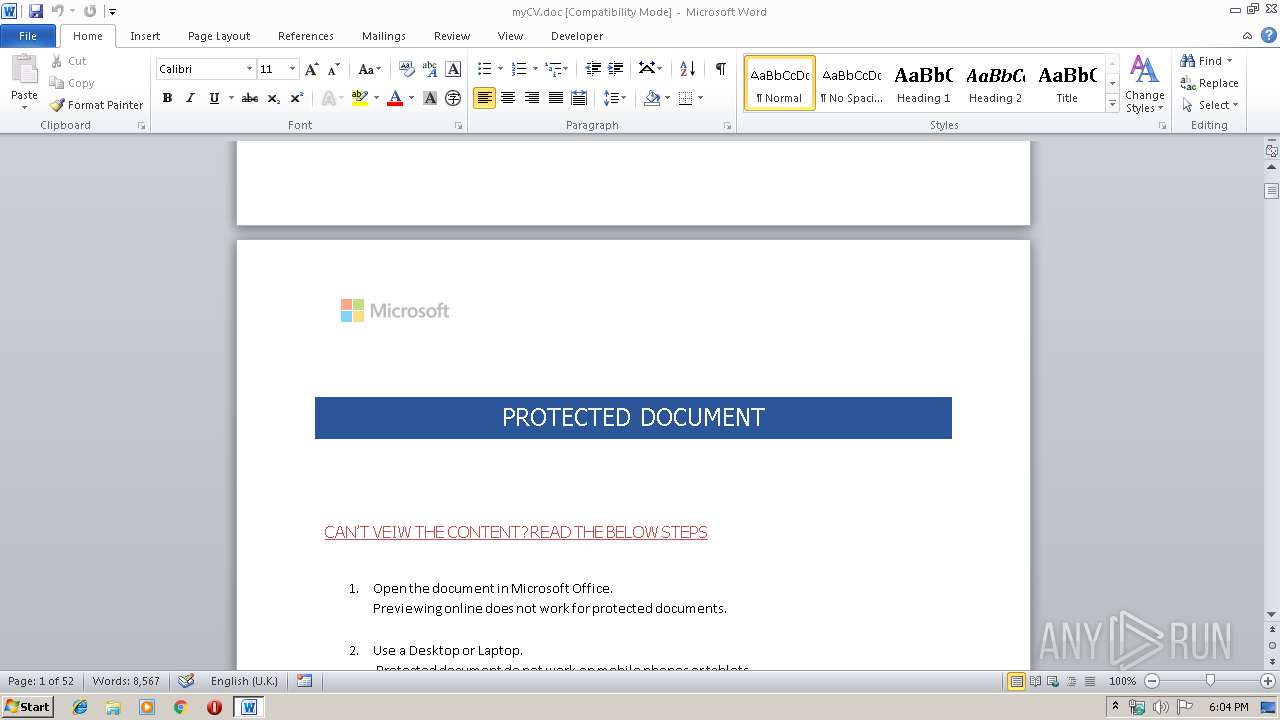
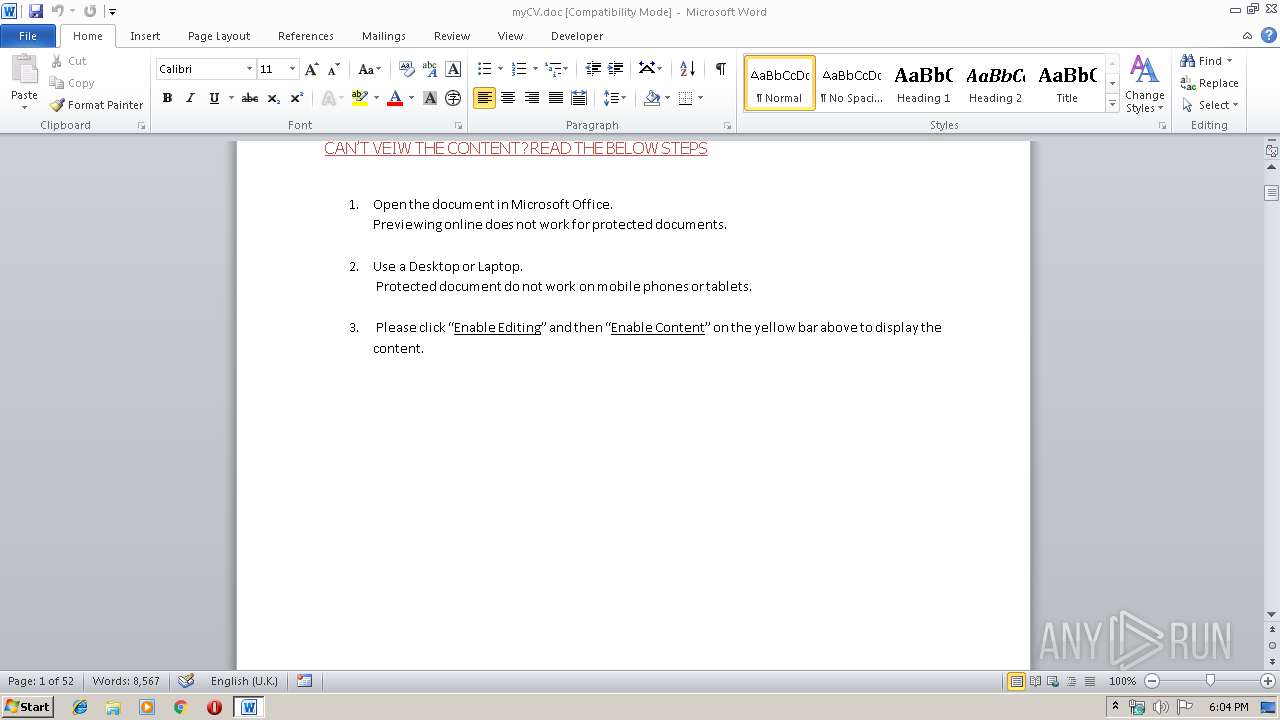
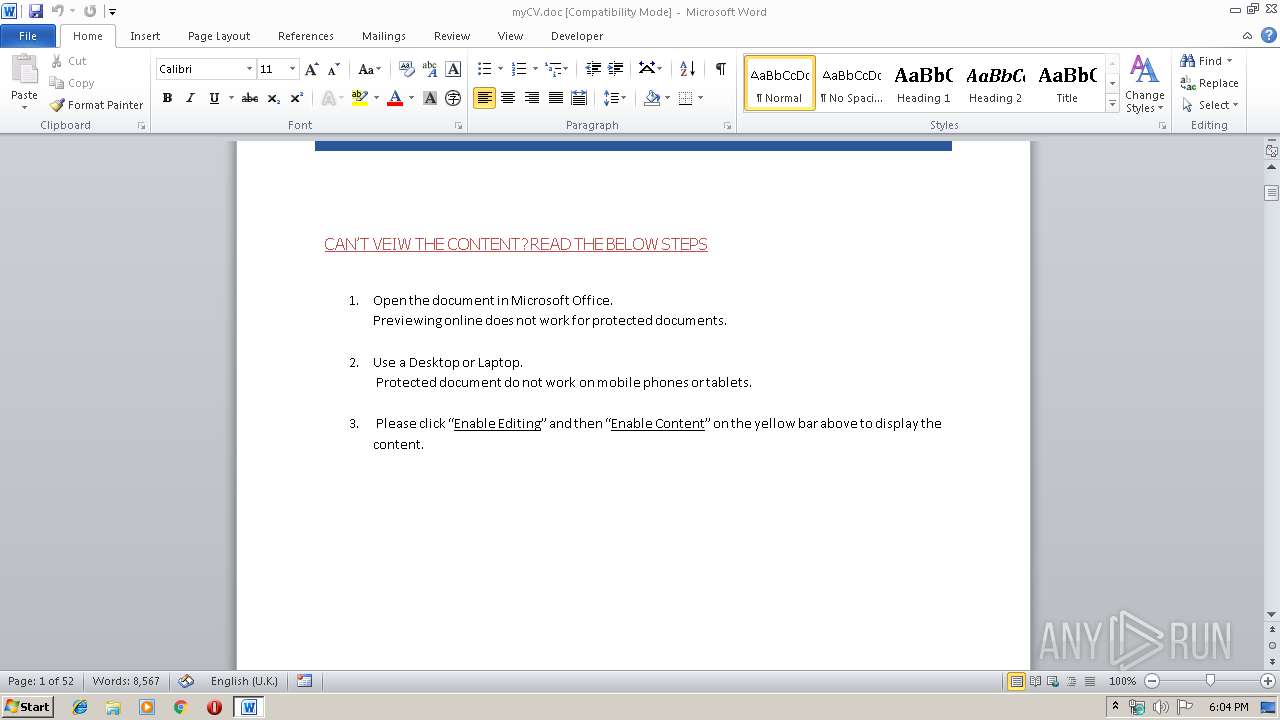
| File name: | myCV.doc |
| Full analysis: | https://app.any.run/tasks/20f5679f-47d3-4b5c-a90f-cb0e856d2199 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2020, 18:03:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.3, Code page: 1252, Author: JULIET MAYNARD, Template: Normal.dotm, Last Saved By: Mark1, Revision Number: 125, Name of Creating Application: Microsoft Office Word, Total Editing Time: 4d+19:37:00, Create Time/Date: Tue Oct 29 02:36:00 2019, Last Saved Time/Date: Wed Jan 15 22:51:00 2020, Number of Pages: 52, Number of Words: 12094, Number of Characters: 68939, Security: 0 |
| MD5: | A175B3B4579368979FD5B3636DE21C87 |
| SHA1: | E440F67CA7D34BE0F7346013D078072F64774E8C |
| SHA256: | 331308E689132C43D8FA6D8E290254F7A51525F99AFEECEBF212CA1C7EA24F17 |
| SSDEEP: | 3072:TeYBwnR4b2Jv8LYmeT3GkNuGyN600YsTyorToWpbl0+x+4g9r:TeYBwnR4bav8LYNT3G+FbTHou06Gr |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2168)
Runs app for hidden code execution
- WINWORD.EXE (PID: 2168)
- endocarp.exe (PID: 1704)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2168)
Loads dropped or rewritten executable
- WINWORD.EXE (PID: 2168)
- 15d0a3bd.exe (PID: 3040)
- endocarp.exe (PID: 1704)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2168)
Application was dropped or rewritten from another process
- 15d0a3bd.exe (PID: 3040)
- endocarp.exe (PID: 1704)
- cmd.exe (PID: 2524)
- cmd.exe (PID: 3000)
- cmd.exe (PID: 2820)
Writes to a start menu file
- DllHost.exe (PID: 3472)
SUSPICIOUS
Executable content was dropped or overwritten
- cmd.exe (PID: 3000)
- 15d0a3bd.exe (PID: 3040)
- cmd.exe (PID: 2524)
- DllHost.exe (PID: 3472)
Creates files in the user directory
- cmd.exe (PID: 3000)
- cmd.exe (PID: 2524)
- DllHost.exe (PID: 3472)
Starts CMD.EXE for commands execution
- endocarp.exe (PID: 1704)
- cmd.exe (PID: 2820)
Application launched itself
- cmd.exe (PID: 2820)
Executed via COM
- DllHost.exe (PID: 3472)
Connects to unusual port
- WerFault.exe (PID: 2800)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2168)
Creates files in the user directory
- WINWORD.EXE (PID: 2168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | JULIET MAYNARD |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Mark1 |
| RevisionNumber: | 125 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 4.8 days |
| CreateDate: | 2019:10:29 02:36:00 |
| ModifyDate: | 2020:01:15 22:51:00 |
| Pages: | 52 |
| Words: | 12094 |
| Characters: | 68939 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | University of Bradford |
| Lines: | 574 |
| Paragraphs: | 161 |
| CharCountWithSpaces: | 80872 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
45
Monitored processes
8
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1704 | C:\Users\admin\AppData\Local\Temp\endocarp.exe | C:\Users\admin\AppData\Local\Temp\endocarp.exe | — | 15d0a3bd.exe | |||||||||||
User: admin Company: Intel Corporation. Integrity Level: MEDIUM Description: ippchv8-6.1.dll is an ippCH dynamic library Exit code: 0 Version: 6,1,137,768 Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\myCV.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2524 | C:\Windows\system32\cmd.exe /c "COPY /Y /B "C:\Users\admin\AppData\Local\Temp\15d0a3bd.exe" "C:\Users\admin\AppData\Roaming\Adobe\Headlights\WUDFHost.exe"" | C:\Windows\system32\cmd.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2800 | "C:\Windows\System32\WerFault.exe" | C:\Windows\System32\WerFault.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2820 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | endocarp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3000 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3040 | "C:\Users\admin\AppData\Local\Temp\15d0a3bd.exe" | C:\Users\admin\AppData\Local\Temp\15d0a3bd.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 3472 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 594
Read events
1 821
Write events
649
Delete events
124
Modification events
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | |x= |
Value: 7C783D0078080000010000000000000000000000 | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1345388606 | |||
Executable files
9
Suspicious files
2
Text files
33
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA8FC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\ssh2_poll.dll | — | |
MD5:— | SHA256:— | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3000 | cmd.exe | C:\Users\admin\AppData\Local\Temp\15dfdcd5.dat | text | |
MD5:— | SHA256:— | |||
| 3000 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@pastebin[1].txt | text | |
MD5:— | SHA256:— | |||
| 3040 | 15d0a3bd.exe | C:\Users\admin\AppData\Local\Temp\rd\websphere\shoutbox\sites\voter\co5580getcanwrite.cs | text | |
MD5:— | SHA256:— | |||
| 3040 | 15d0a3bd.exe | C:\Users\admin\AppData\Local\Temp\25\columnists\printpdf\received\doit\43.opends60.dll | binary | |
MD5:— | SHA256:— | |||
| 3040 | 15d0a3bd.exe | C:\Users\admin\AppData\Local\Temp\rd\websphere\shoutbox\sites\voter\jpverb207.gif | image | |
MD5:— | SHA256:— | |||
| 3040 | 15d0a3bd.exe | C:\Users\admin\AppData\Local\Temp\rd\websphere\shoutbox\sites\voter\libssl1.1amd64.list | text | |
MD5:— | SHA256:— | |||
| 3040 | 15d0a3bd.exe | C:\Users\admin\AppData\Local\Temp\wp-trackback\installation\_media\agency\imports\administrivia\Drum.gif | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
3
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3000 | cmd.exe | 104.20.68.143:443 | pastebin.com | Cloudflare Inc | US | malicious |
2800 | WerFault.exe | 194.5.99.206:4181 | roboticsnetwork.duckdns.org | — | FR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
roboticsnetwork.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |