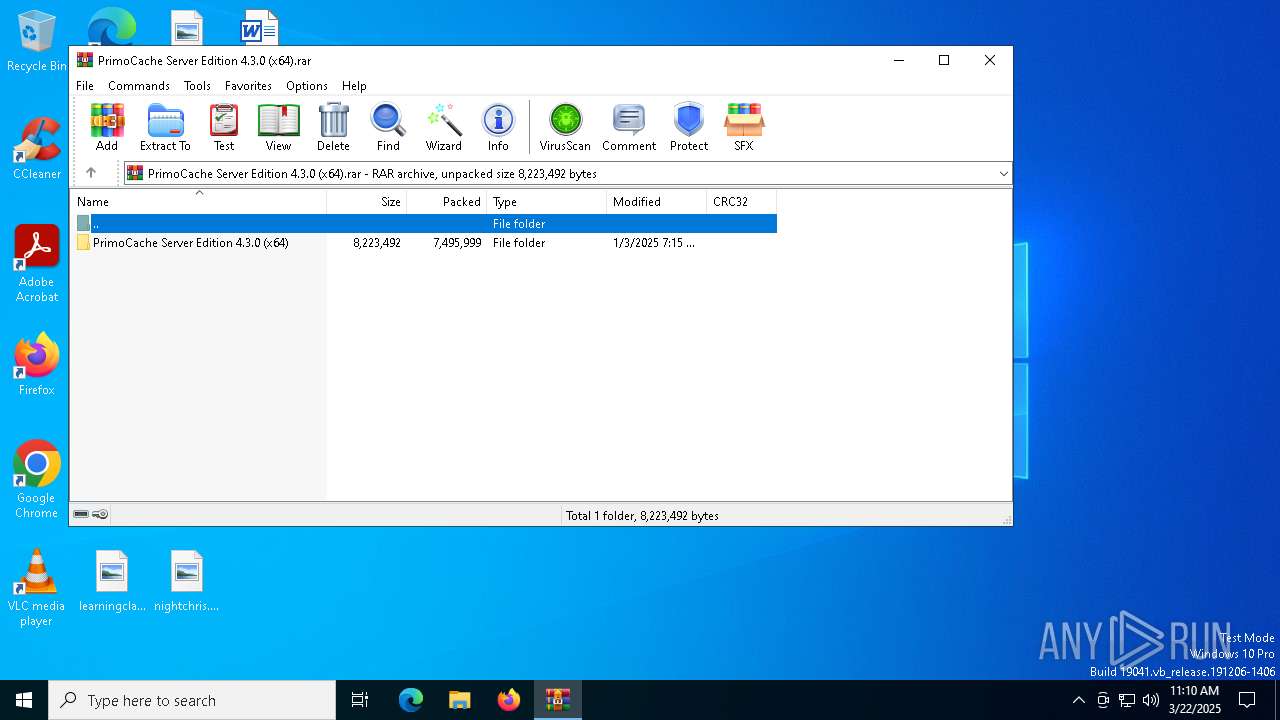
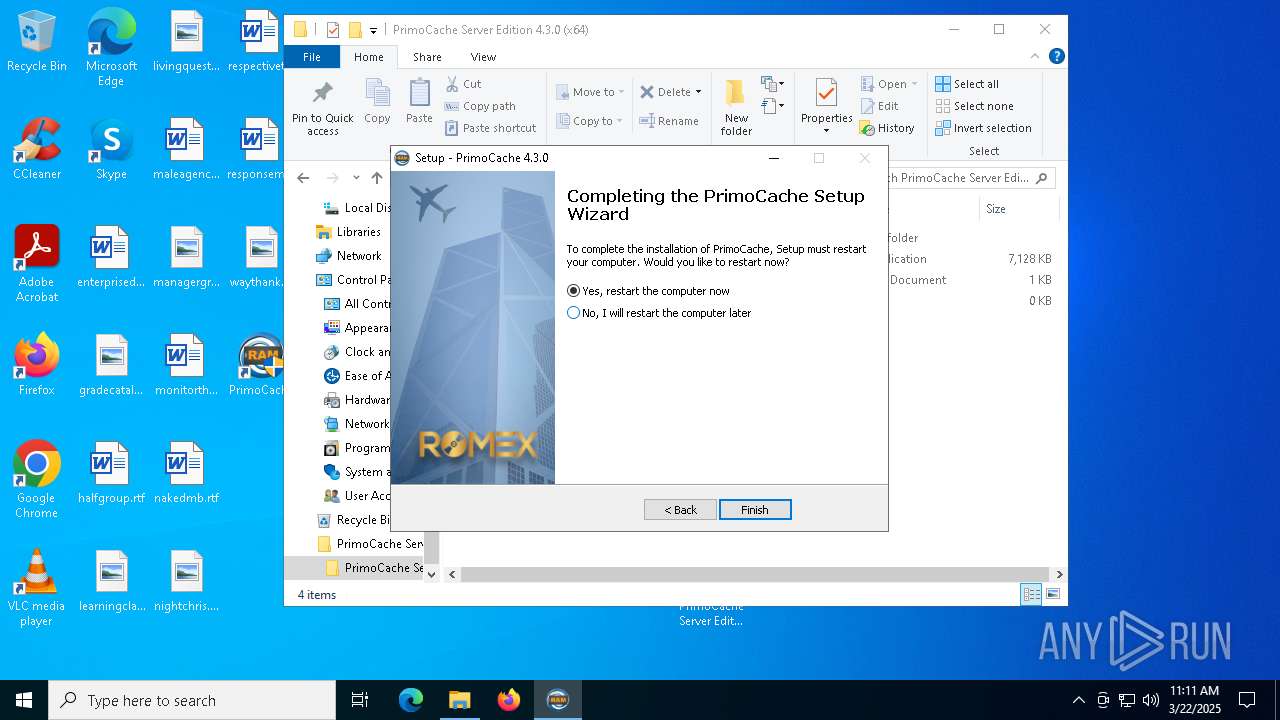
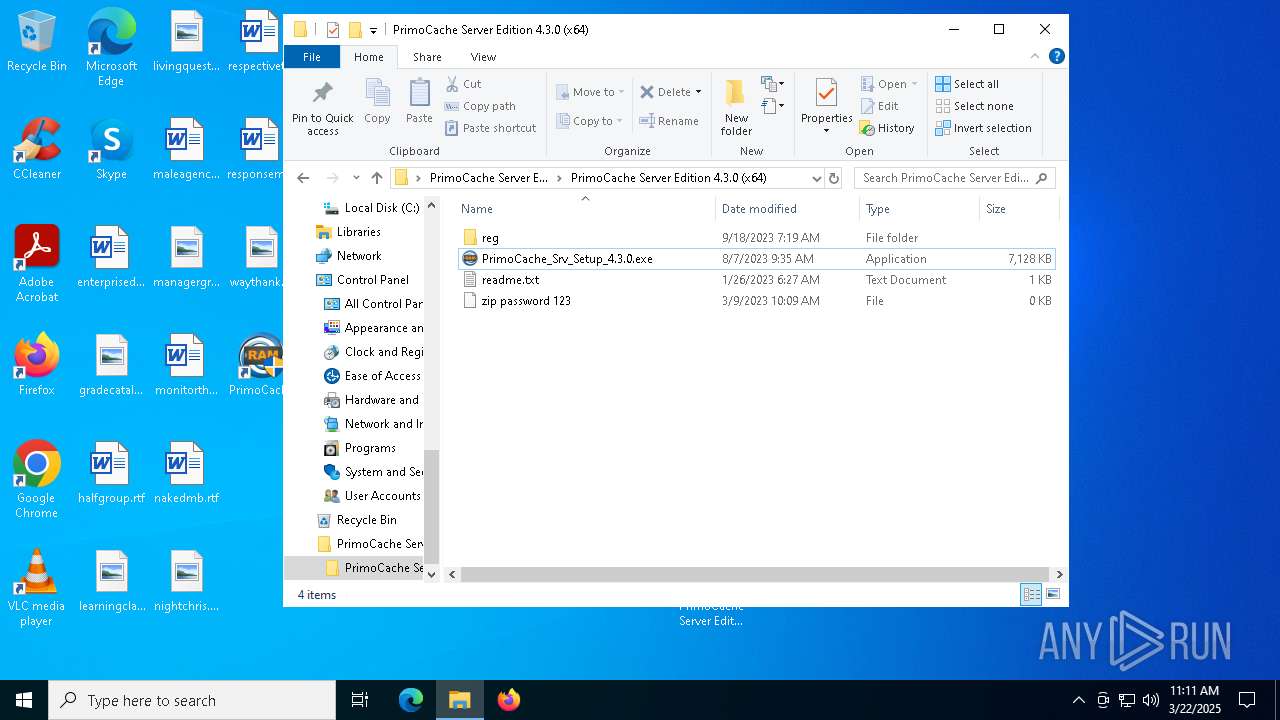
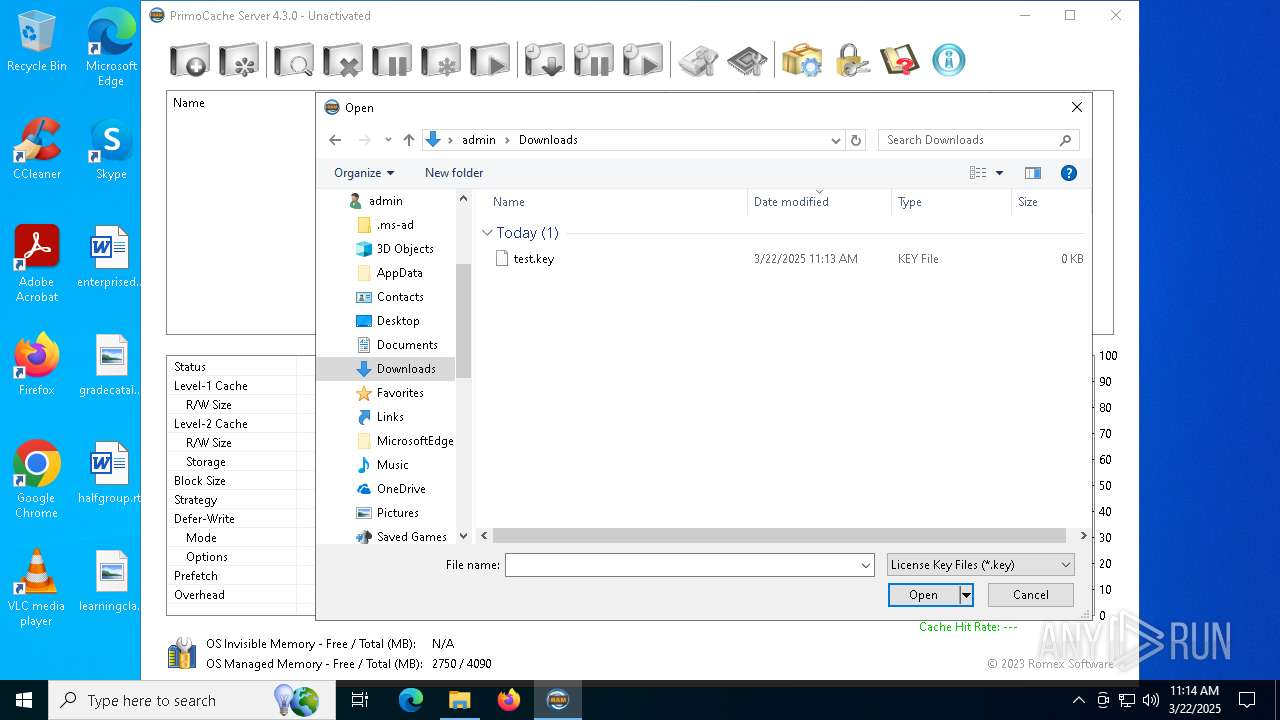
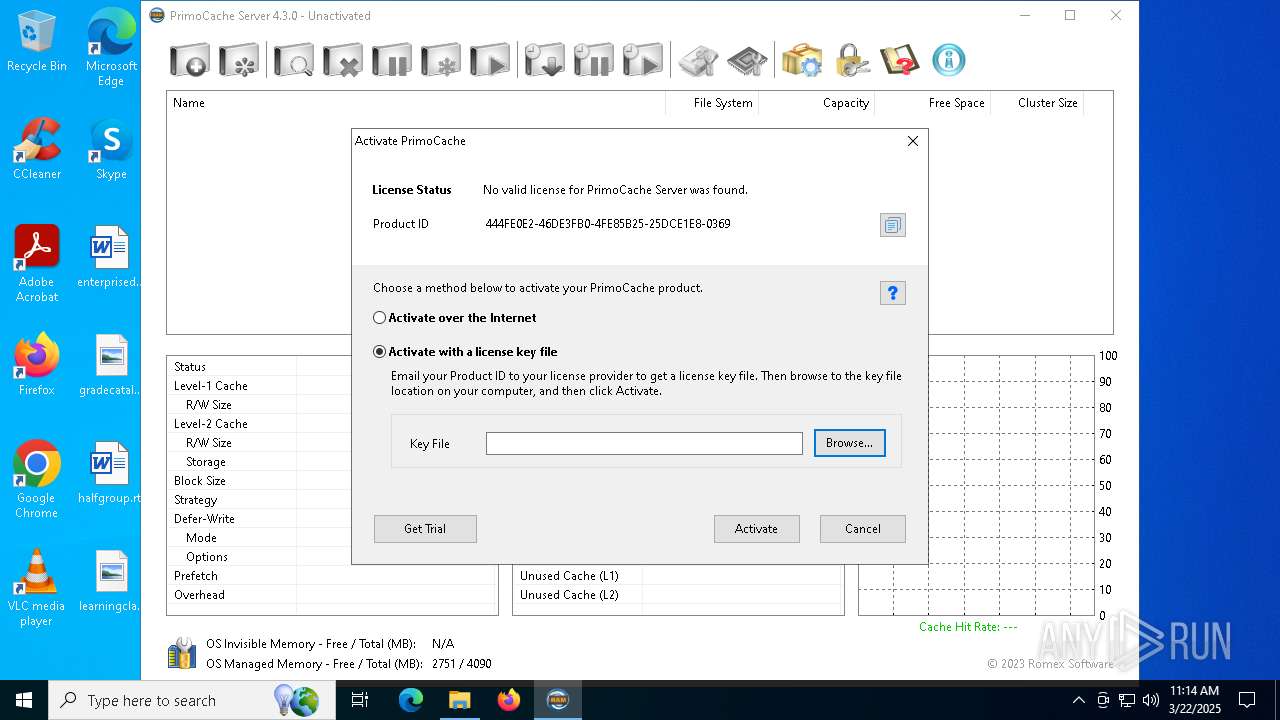
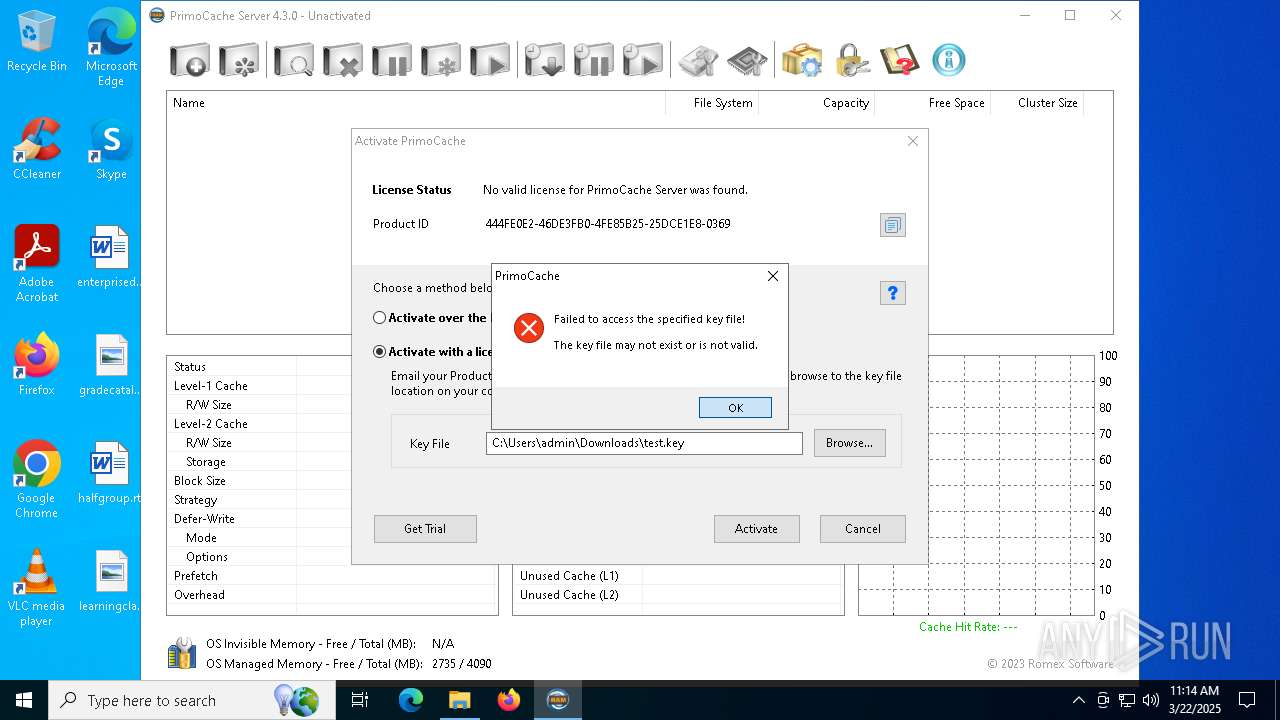
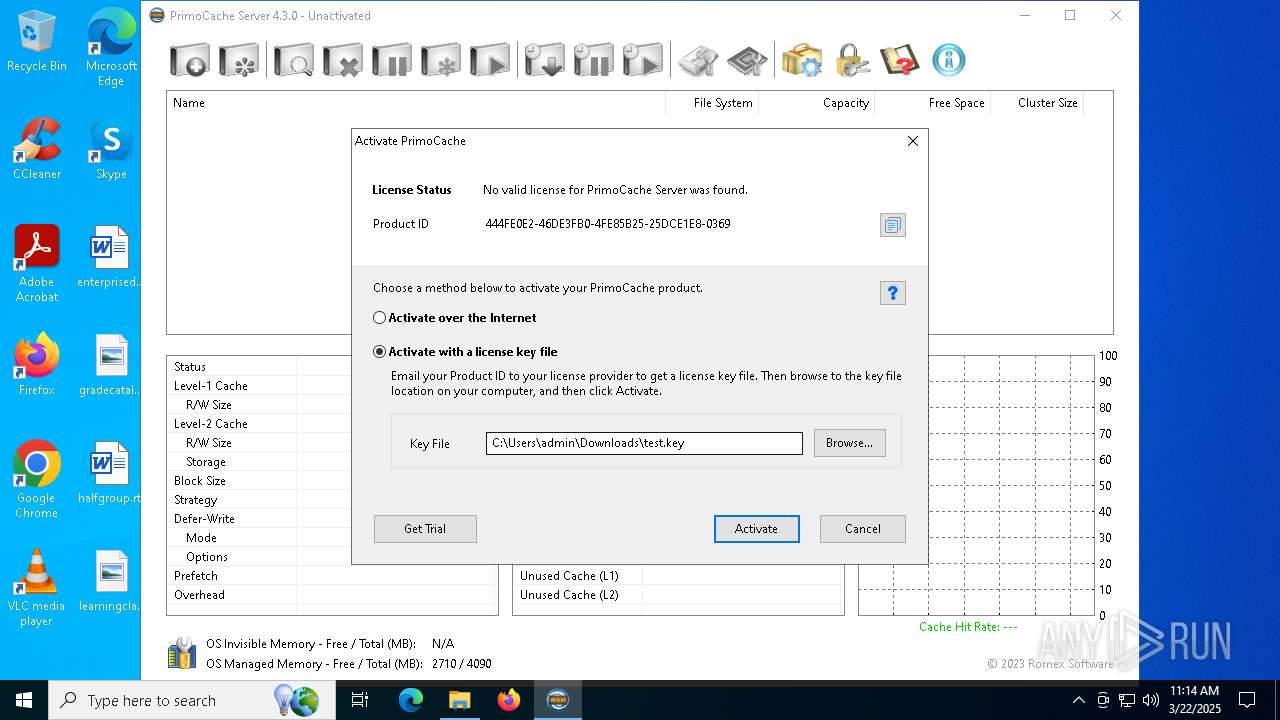
| File name: | PrimoCache Server Edition 4.3.0 (x64).rar |
| Full analysis: | https://app.any.run/tasks/302afaad-85e1-4ab4-ba27-31bdc64b55b5 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2025, 11:10:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 96610154E1E7BC6F0FDB227A1A88AE35 |
| SHA1: | 475FEFBA606709EF1BE6DE85B6D2EB237FB7C414 |
| SHA256: | 32FB6851D33D399F47B1C64A909864D48537B1E618FFC643460CE566BFBA6B92 |
| SSDEEP: | 98304:qC9IuiSledVil0RGk7O6cB4JfbJe8IZZVGJXktrMAsbGcC6ZvE6V5kGmSNm2/uZq:k11ROhJfOJrq2PZ4Wt |
MALICIOUS
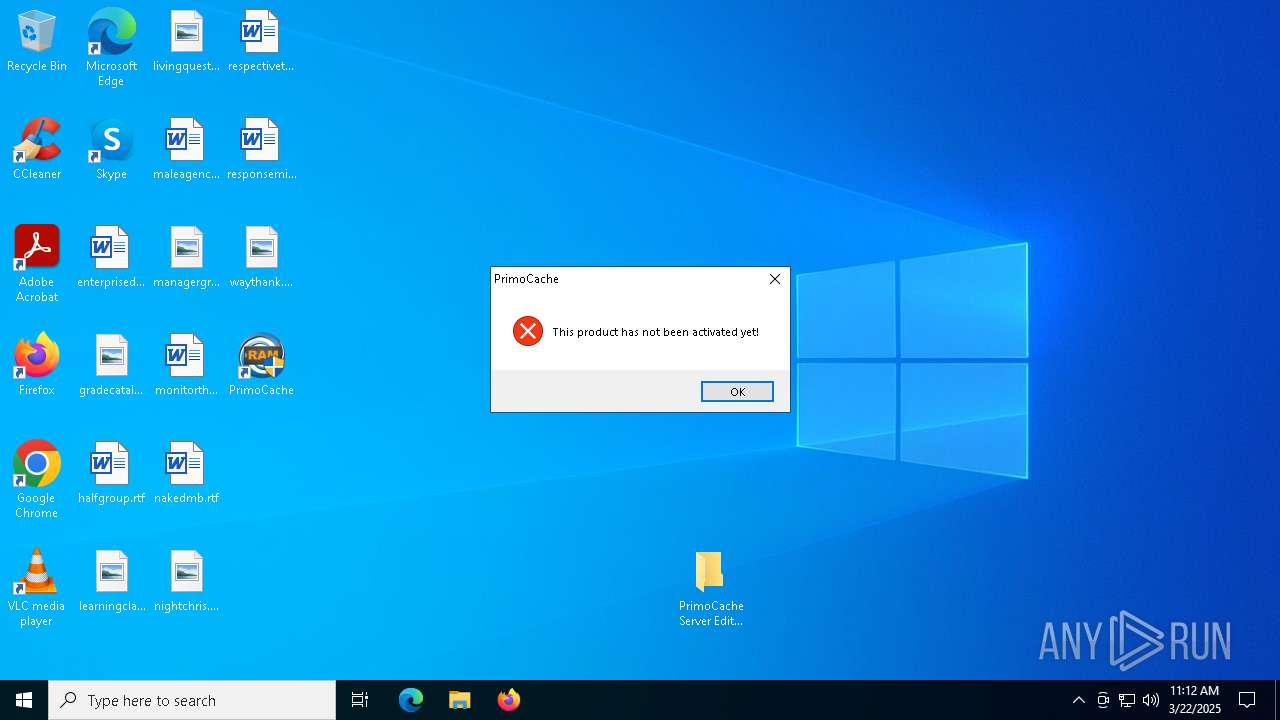
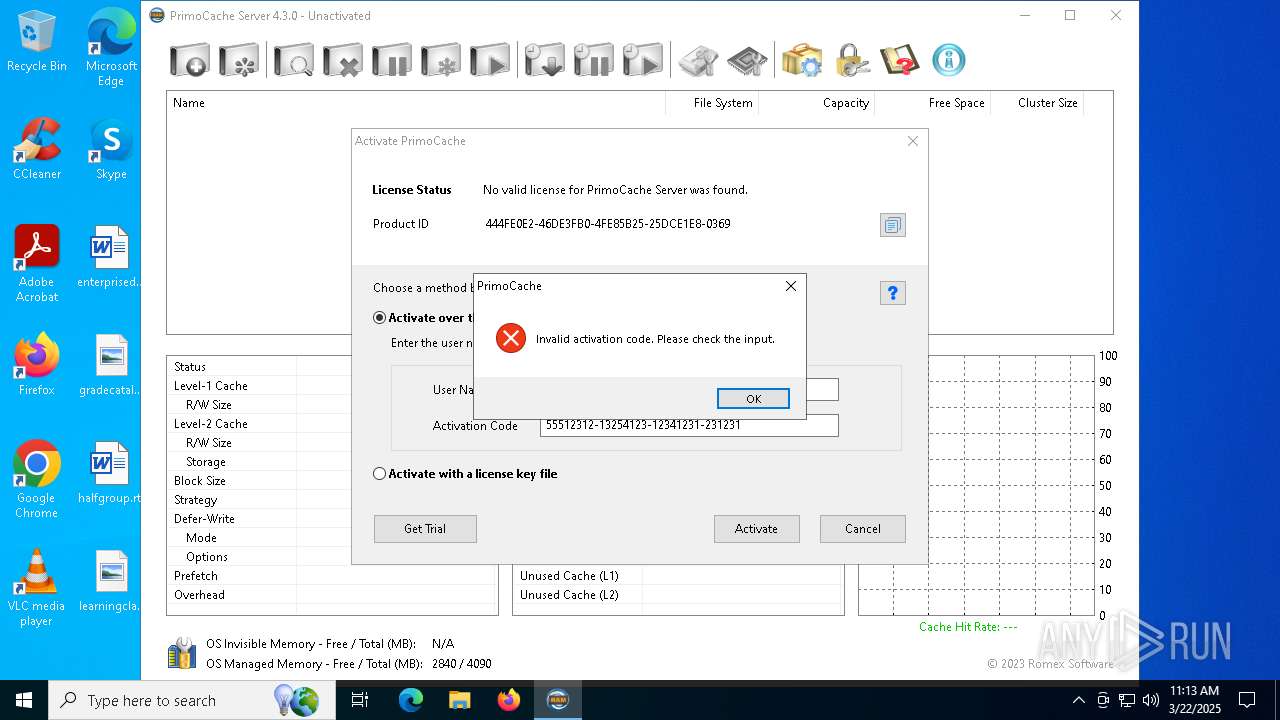
Executing a file with an untrusted certificate
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 7936)
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 8052)
- FancyCcV.exe (PID: 6220)
- FancyCcV.exe (PID: 6300)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 4428)
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
- fcsetup.exe (PID: 1672)
Executable content was dropped or overwritten
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 7936)
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 8052)
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
- fcsetup.exe (PID: 1672)
Reads security settings of Internet Explorer
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 7956)
- FancyCcV.exe (PID: 6300)
Reads the Windows owner or organization settings
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
Creates files in the driver directory
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
- fcsetup.exe (PID: 1672)
Starts SC.EXE for service management
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4100)
Windows service management via SC.EXE
- sc.exe (PID: 4448)
INFO
Manual execution by a user
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 7936)
- FancyCcV.exe (PID: 6220)
- FancyCcV.exe (PID: 6300)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4428)
The sample compiled with english language support
- WinRAR.exe (PID: 4428)
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
- fcsetup.exe (PID: 1672)
Create files in a temporary directory
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 7936)
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 8052)
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
Reads the computer name
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 7956)
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
- fcsetup.exe (PID: 1672)
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 7936)
- PLUGScheduler.exe (PID: 4100)
- FancyCcV.exe (PID: 6300)
Checks supported languages
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 7956)
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 8052)
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 7936)
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
- fcsetup.exe (PID: 1672)
- PLUGScheduler.exe (PID: 4100)
- FancyCcV.exe (PID: 6300)
Process checks computer location settings
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 7956)
Creates a software uninstall entry
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
Detects InnoSetup installer (YARA)
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 7956)
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 7936)
Creates files in the program directory
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 8076)
- PLUGScheduler.exe (PID: 4100)
Compiled with Borland Delphi (YARA)
- PrimoCache_Srv_Setup_4.3.0.exe (PID: 7936)
- PrimoCache_Srv_Setup_4.3.0.tmp (PID: 7956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 7013643 |
| UncompressedSize: | 7298888 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | PrimoCache Server Edition 4.3.0 (x64)/PrimoCache Server Edition 4.3.0 (x64)/PrimoCache_Srv_Setup_4.3.0.exe |
Total processes
293
Monitored processes
15
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fcsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | "C:\Program Files\PrimoCache\fcsetup.exe" -i "C:\Program Files\PrimoCache\drv\rxfcv.inf" 257 | C:\Program Files\PrimoCache\fcsetup.exe | PrimoCache_Srv_Setup_4.3.0.tmp | ||||||||||||
User: admin Company: Romex Software Integrity Level: HIGH Description: fcsetup Exit code: 0 Version: 1.3.1.1 built by: WinDDK Modules
| |||||||||||||||
| 4100 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\PrimoCache Server Edition 4.3.0 (x64).rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4448 | "sc" delete PrimoCacheSvc | C:\Windows\System32\sc.exe | — | PrimoCache_Srv_Setup_4.3.0.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6220 | "C:\Program Files\PrimoCache\FancyCcV.exe" | C:\Program Files\PrimoCache\FancyCcV.exe | — | explorer.exe | |||||||||||
User: admin Company: Romex Software Integrity Level: MEDIUM Description: PrimoCache GUI Program Exit code: 3221226540 Version: 4.3.0 Modules
| |||||||||||||||
| 6300 | "C:\Program Files\PrimoCache\FancyCcV.exe" | C:\Program Files\PrimoCache\FancyCcV.exe | explorer.exe | ||||||||||||
User: admin Company: Romex Software Integrity Level: HIGH Description: PrimoCache GUI Program Version: 4.3.0 Modules
| |||||||||||||||
| 7316 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7348 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 214
Read events
8 011
Write events
193
Delete events
10
Modification events
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\PrimoCache Server Edition 4.3.0 (x64).rar | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
23
Suspicious files
61
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv.bak\win10-11_srv2016-2022\rxfcv.inf | binary | |
MD5:6A5FC2E7E59C001D425B56D65B02D8DB | SHA256:EF85C3E4894E51D624FD7BB52A41AB5EB3C1F29C1970E209AAF6934B8929D812 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv.bak\win10-11_srv2016-2022\rxfcv.sys | executable | |
MD5:473B8ADFBE072B7801769AAA4737DB33 | SHA256:3CD21708C94B637C524D2FE229EFE9FC746A78C8D548CF5C3A4D982EB43DF1BD | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv.bak\win7-8.1_srv2008-2012\rxfcv.cat | binary | |
MD5:024E484E91836DB6BCDCBC077F893869 | SHA256:2FCA24E2EF17ED40FE6DDDD5E8DB4CB04EF251A9752BE954AC46E87FD3C5D9F7 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv10\rxfcv.cat | binary | |
MD5:3A4B2493DEE5D6B6348D6CDF66032040 | SHA256:5BB694E36F33C42D6C4611FE51CA27E65CFBA825D93B88D806355E440FEE78BE | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv7\rxfcv.cat | binary | |
MD5:14C856C4AE36668F489BF0BC9C8DB821 | SHA256:D35E9AA331C220201CFCE039BE364FC22ABD7DA14B27A779D656C84D9F81CDD0 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv10\rxfcv.inf | binary | |
MD5:6A5FC2E7E59C001D425B56D65B02D8DB | SHA256:EF85C3E4894E51D624FD7BB52A41AB5EB3C1F29C1970E209AAF6934B8929D812 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv.bak\win10-11_srv2016-2022\rxfcv.cat | binary | |
MD5:E82FB2AD70788E7FB854413A991AF223 | SHA256:4B61323C5A283FFEE4908841657CD3A63D52D467F36EA8D1DD0EFD4B173D9CF2 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache_Srv_Setup_4.3.0.exe | executable | |
MD5:6EEF34FCB55DD0B46686BB4FF4B9AF2A | SHA256:72272AD5A44142416F124E206A689C7D92B7FA1CDC6EFB2E3388343E75D2A0B2 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv10\rxfcv.sys | executable | |
MD5:ADDD5F744B04737D236CD0BC042EE004 | SHA256:C97F9BCAC30E7C2C29D9B49A0FD192B8722FE041536B66B817F31D47449A2227 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4428.17373\PrimoCache Server Edition 4.3.0 (x64)\PrimoCache Server Edition 4.3.0 (x64)\reg\drv.bak\win7-8.1_srv2008-2012\rxfcv.inf | binary | |
MD5:6A5FC2E7E59C001D425B56D65B02D8DB | SHA256:EF85C3E4894E51D624FD7BB52A41AB5EB3C1F29C1970E209AAF6934B8929D812 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
57
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1228 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6640 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1228 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2852 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 20.198.162.76:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2852 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |