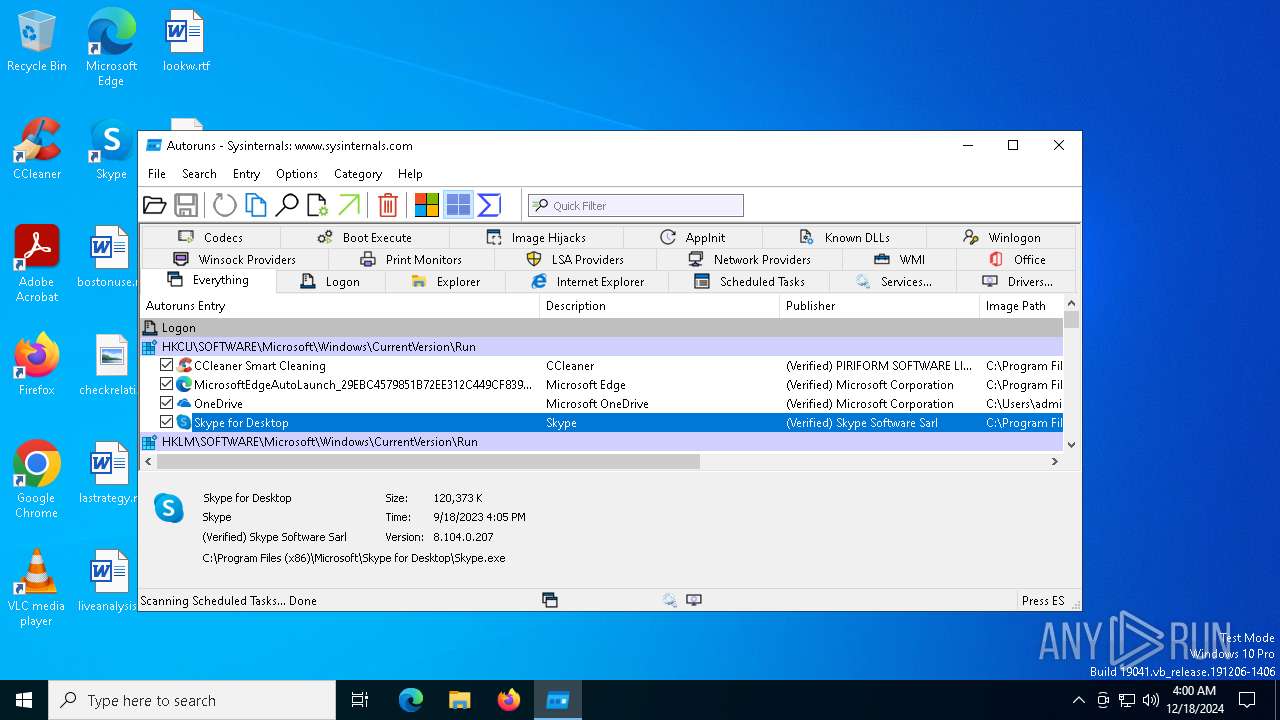
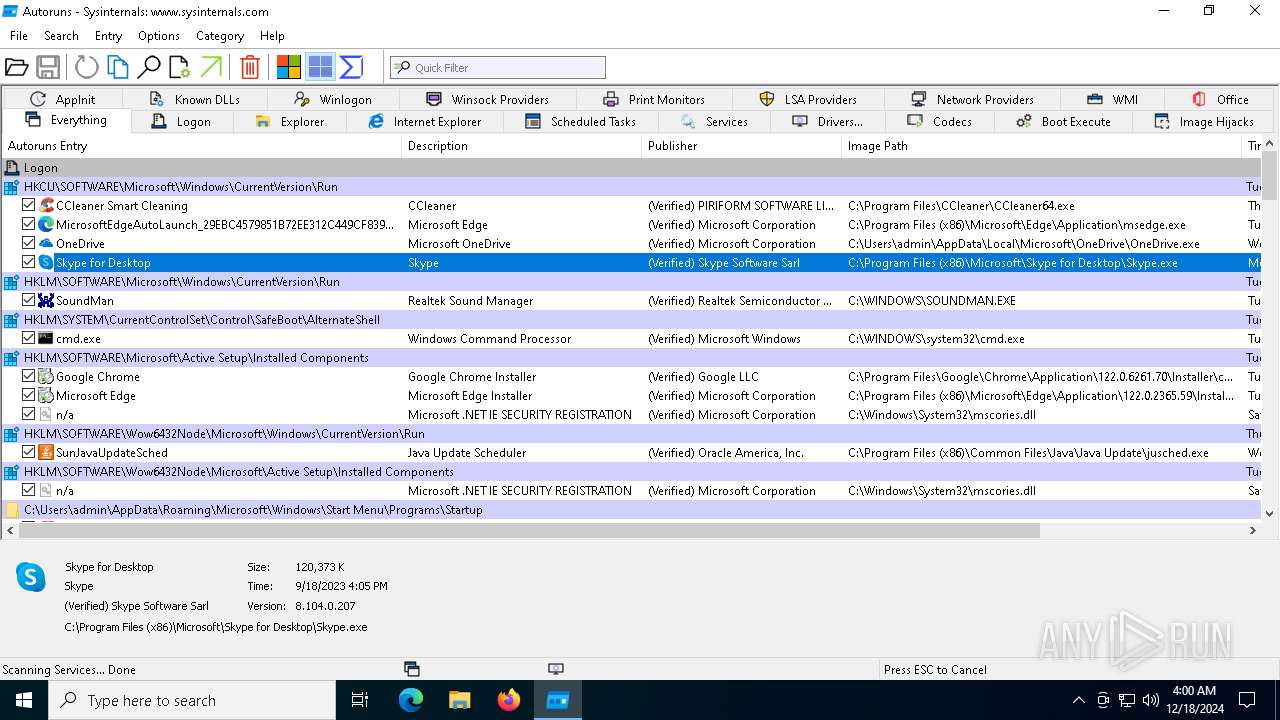
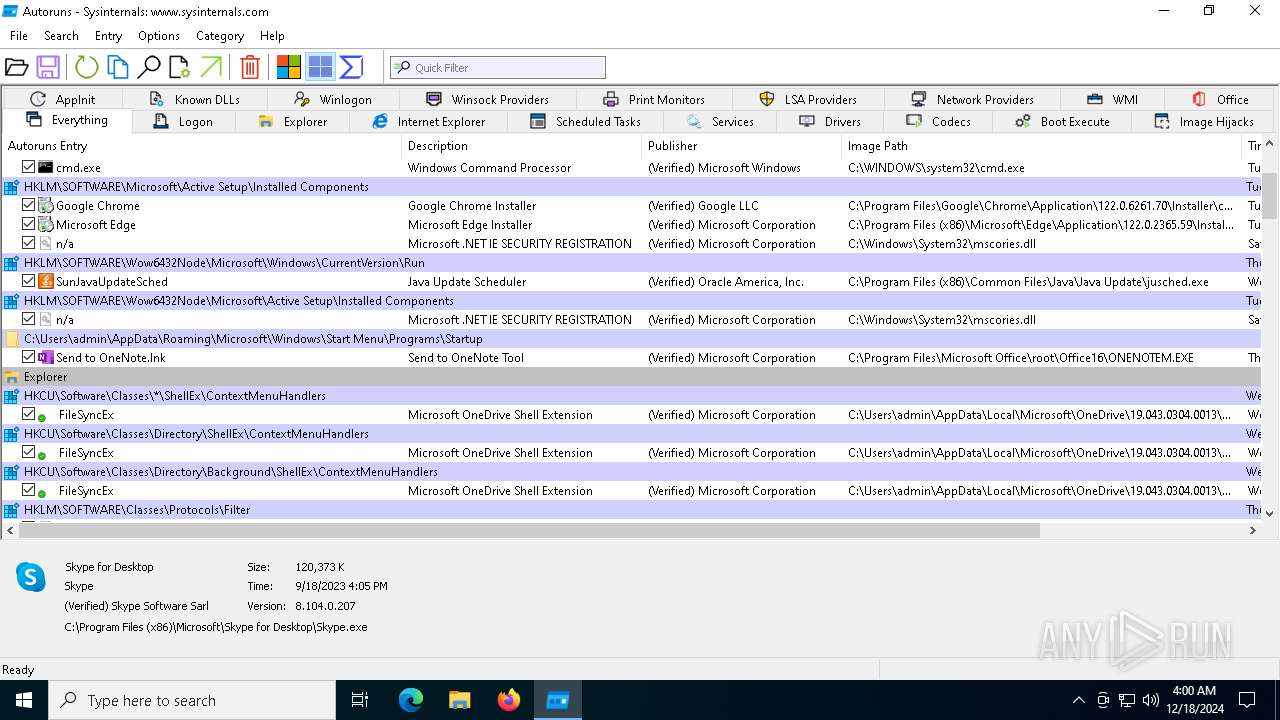
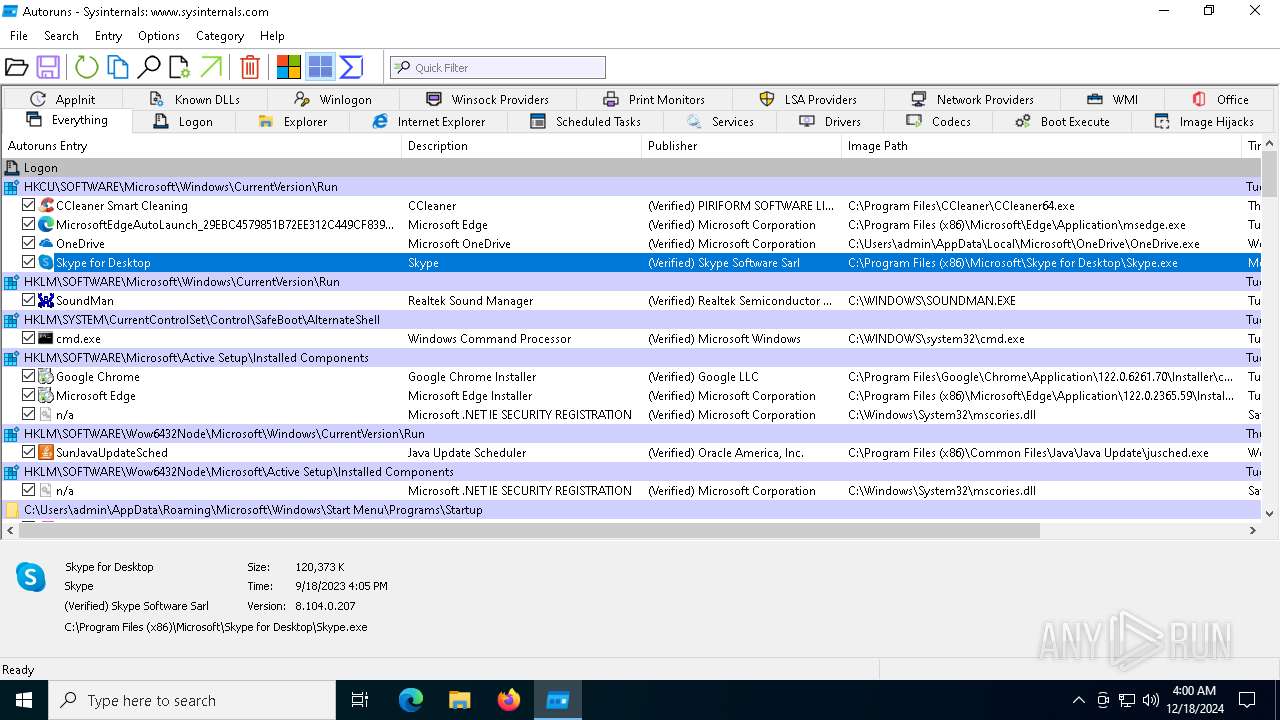
| File name: | Autoruns64.exe |
| Full analysis: | https://app.any.run/tasks/0a2a8d91-d7e4-4dd7-9302-ba8aa9d58699 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2024, 03:59:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 07F151495C65098FB635D3C95AAFC285 |
| SHA1: | 20A8A5BDF45F896FBCA70BCE4B99AFA2C7CB6F35 |
| SHA256: | 32E268B87130B7B24969718F81534BAFEC92985C2ECE6765A88C20C28C55BCA1 |
| SSDEEP: | 49152:KVDpiqIn08bZOinNQXF1OkwVw4uSOYj8noHd0Kdq6hYp:KVDpzIn08bvkF1nwVw4a96mp |
MALICIOUS
No malicious indicators.SUSPICIOUS
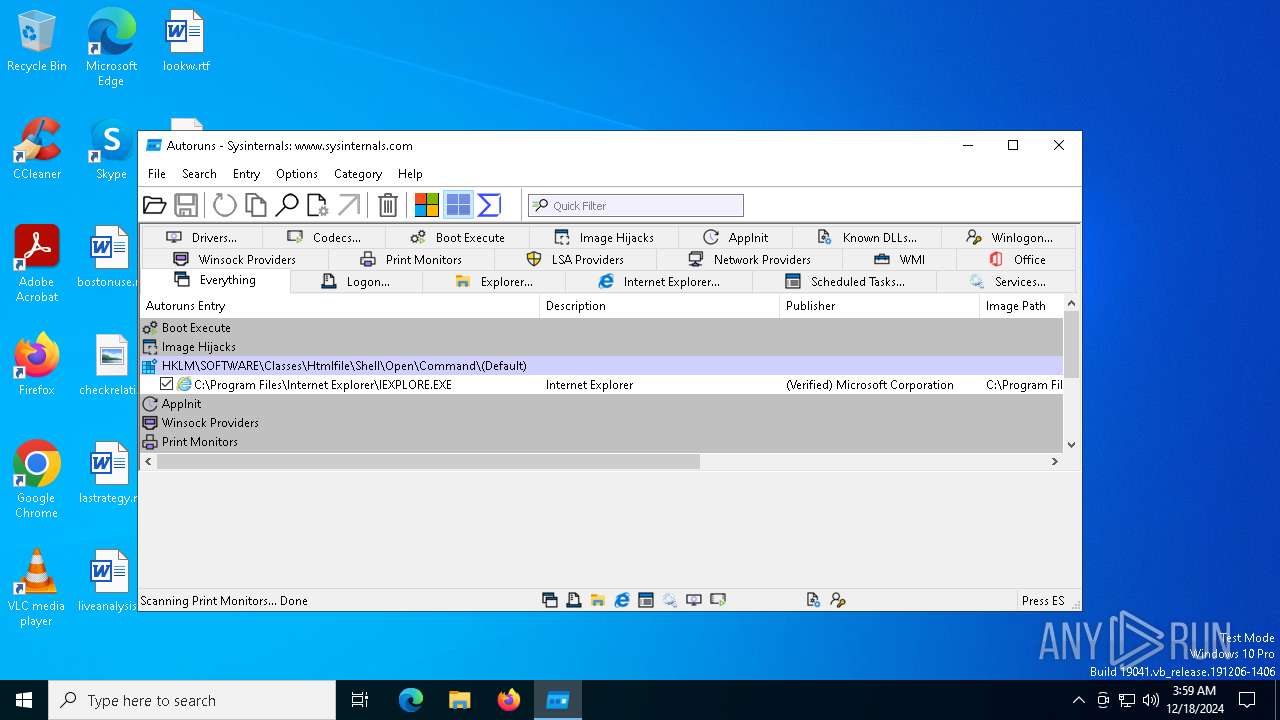
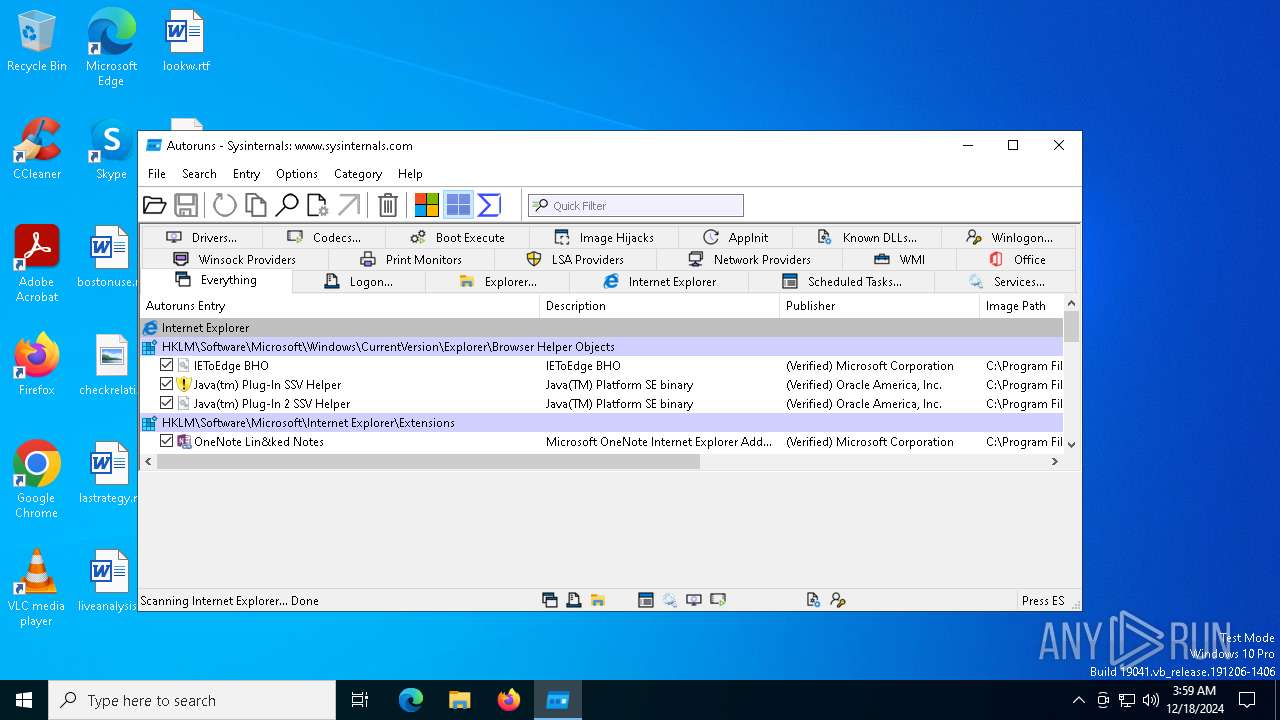
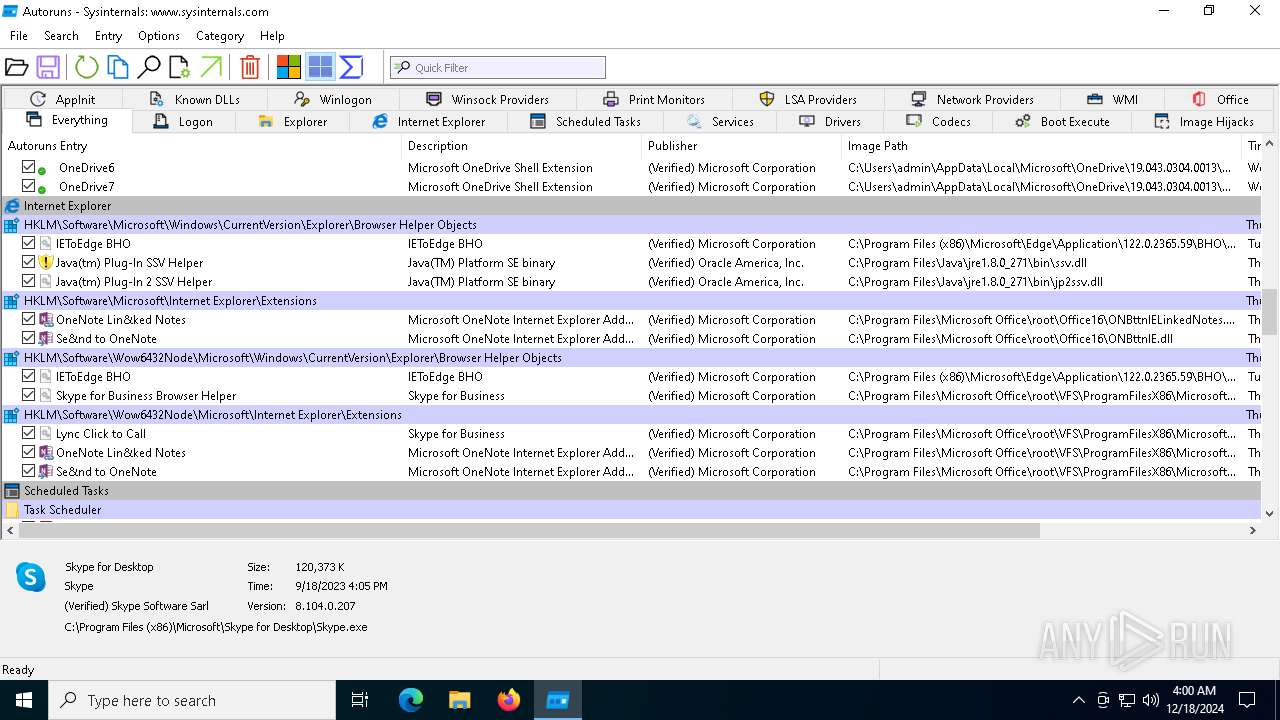
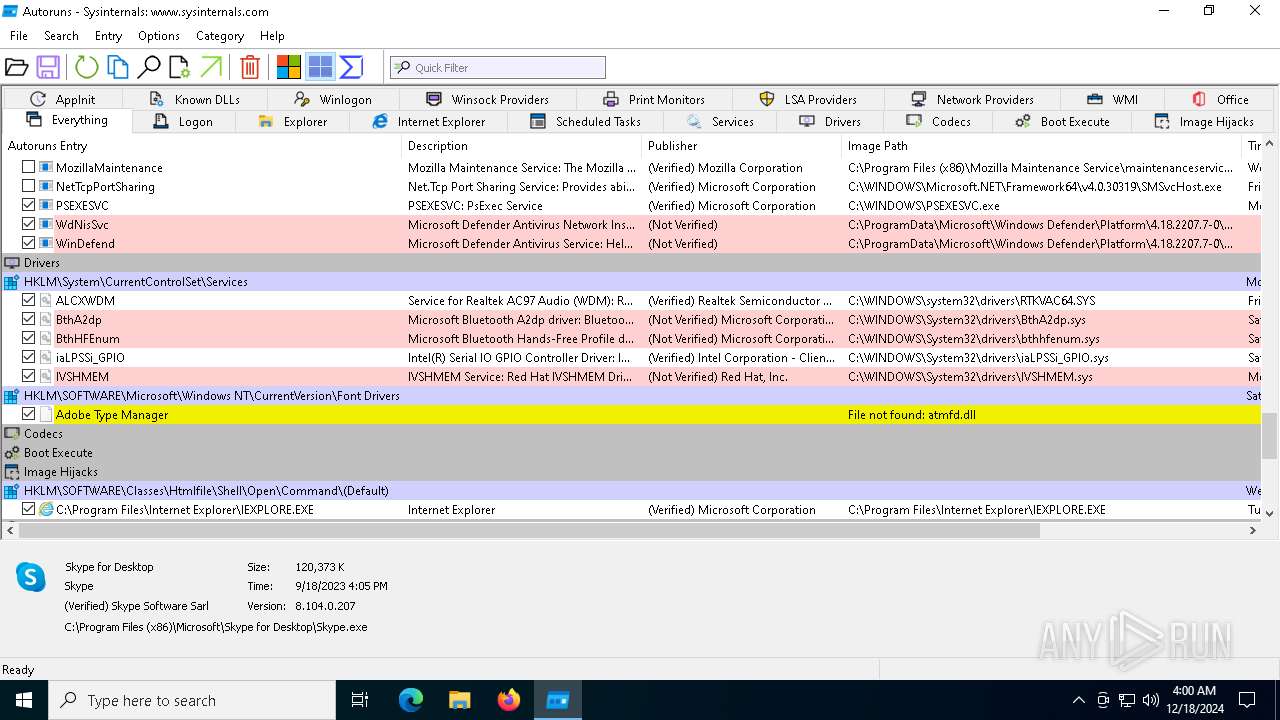
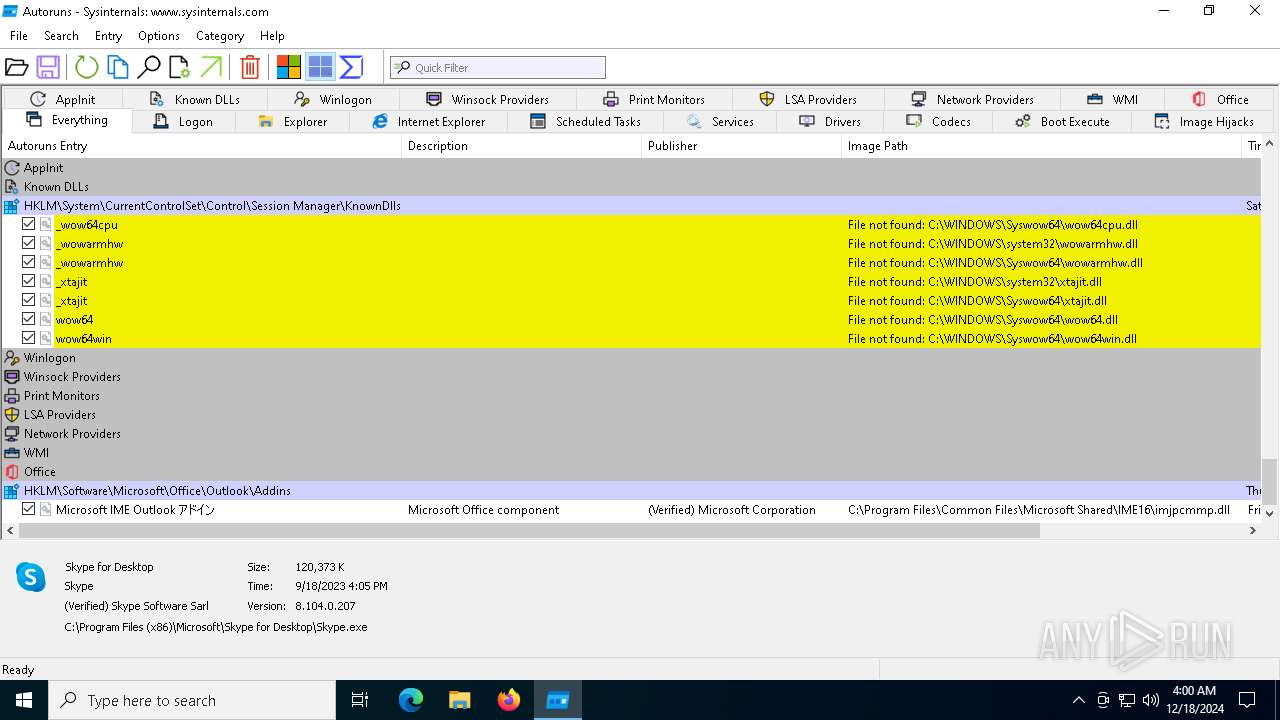
Reads security settings of Internet Explorer
- Autoruns64.exe (PID: 5464)
Checks Windows Trust Settings
- Autoruns64.exe (PID: 5464)
INFO
Reads product name
- Autoruns64.exe (PID: 5464)
The sample compiled with english language support
- Autoruns64.exe (PID: 5464)
Checks supported languages
- Autoruns64.exe (PID: 5464)
Creates files or folders in the user directory
- Autoruns64.exe (PID: 5464)
Reads Microsoft Office registry keys
- Autoruns64.exe (PID: 5464)
Checks proxy server information
- Autoruns64.exe (PID: 5464)
Reads Environment values
- Autoruns64.exe (PID: 5464)
Reads the machine GUID from the registry
- Autoruns64.exe (PID: 5464)
Reads the software policy settings
- Autoruns64.exe (PID: 5464)
Reads the computer name
- Autoruns64.exe (PID: 5464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:02:01 10:36:55+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.37 |
| CodeSize: | 854528 |
| InitializedDataSize: | 1164288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9d1b4 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 14.11.0.0 |
| ProductVersionNumber: | 14.11.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Autostart program viewer |
| FileVersion: | 14.11 |
| InternalName: | Sysinternals Autoruns |
| LegalCopyright: | Copyright (C) 2002-2024 Mark Russinovich |
| OriginalFileName: | autoruns.exe |
| ProductName: | Sysinternals autoruns |
| ProductVersion: | 14.11 |
Total processes
125
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5464 | "C:\Users\admin\AppData\Local\Temp\Autoruns64.exe" | C:\Users\admin\AppData\Local\Temp\Autoruns64.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Version: 14.11 Modules
| |||||||||||||||
Total events
41 849
Read events
41 848
Write events
1
Delete events
0
Modification events
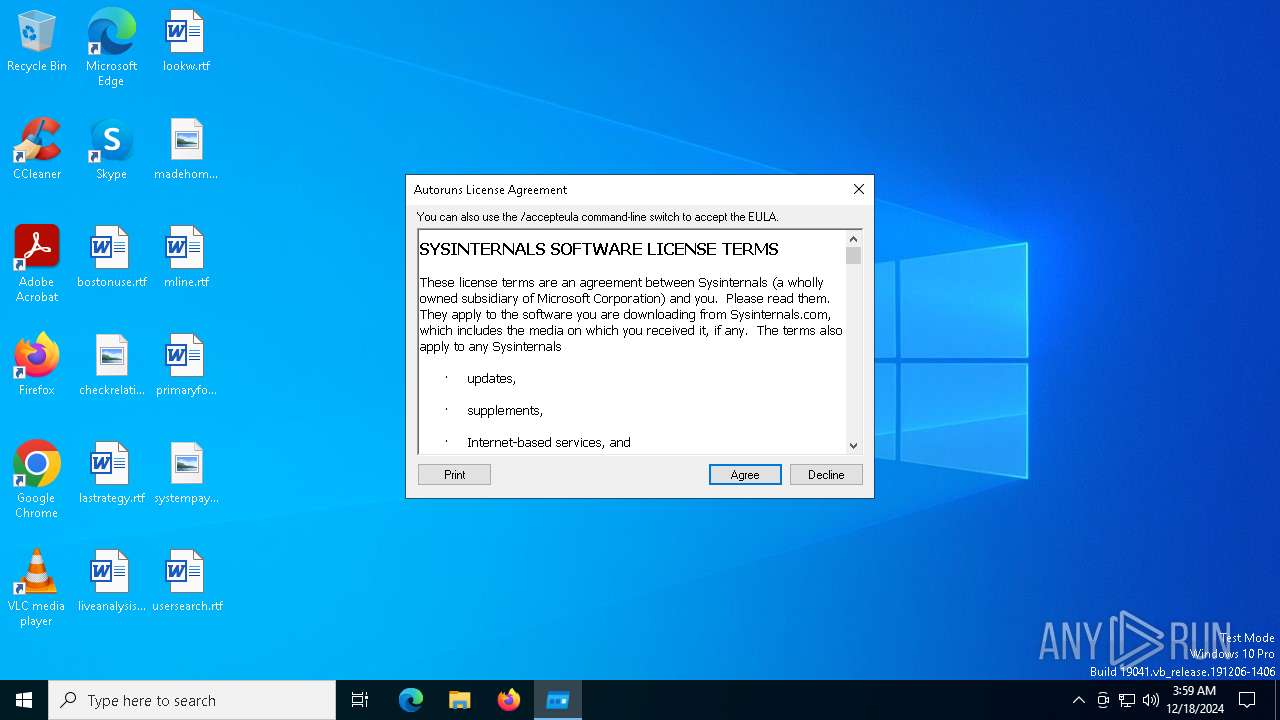
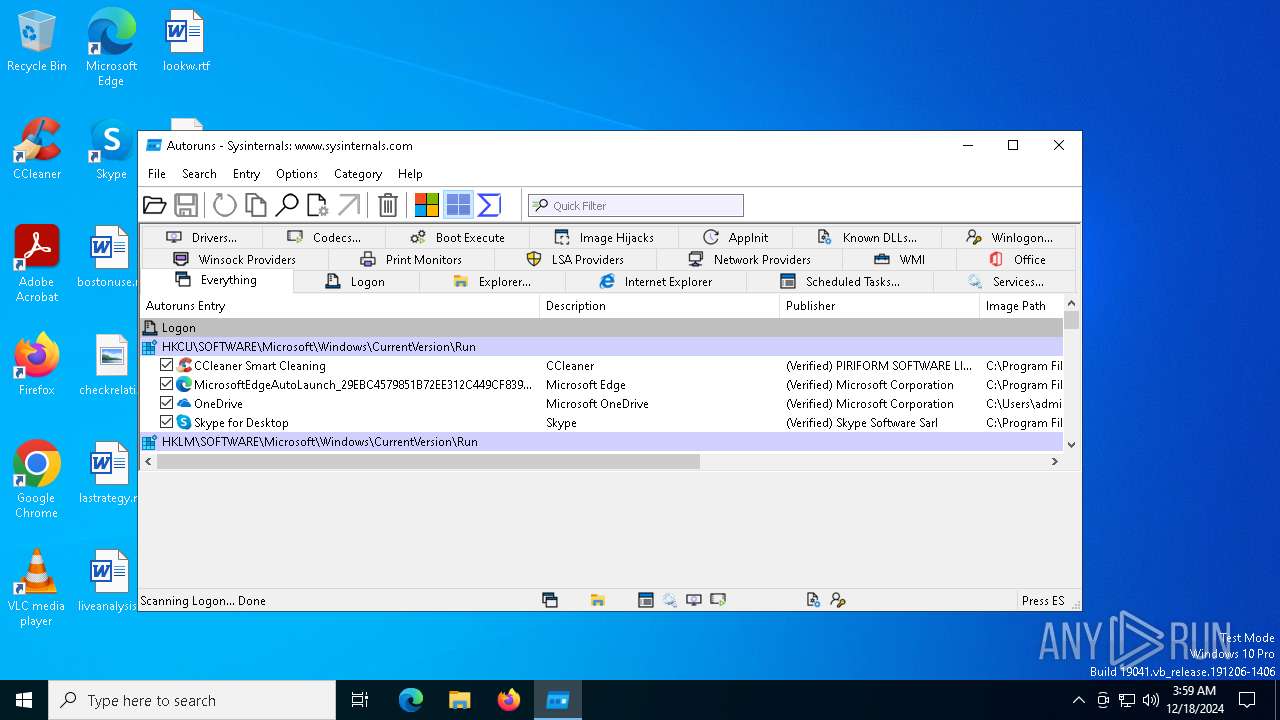
| (PID) Process: | (5464) Autoruns64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Autoruns |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
Executable files
0
Suspicious files
62
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:67A52A39F91421613A4D854BF8E8D791 | SHA256:D8B8FE5F54E4AFC75FBEC4BC8453D2FE7CF4E1A5959CD442CB0EE05223CF607E | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0B8A20E1F3F4D73D52A19929F922C892 | binary | |
MD5:4BB71C446533E3B735C069A975FDEC3A | SHA256:D854D6E3CFD975FB2B6E7BEF5B32815F18F2128C1892584383500C14D3B0BAAC | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:BEA650E9D669CF1C6C2EA6DEF826B955 | SHA256:E259199F60C1F26999723B5B2C2120DF8D35440B3F606DC0F8B79C896F54B49E | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:D80438E1D2A0AABFB85F0320CC3FCDA9 | SHA256:CD97A00221FEE3183E6B16AEF73479CFFAC000A415BFE07755326F2ED21A78E5 | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:530815A4DE593A620A36D5FC494B4474 | SHA256:EFAAF52243AA1271530DA2F4D691DBC3EF175AF68D8A761896E9ABAC51B72546 | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:87C44115E57665888B102ECD3F2FB4A5 | SHA256:9369934B9EF59D8F9B3ADE45D945E87BD7676E45114B9005DD458A970D3A561B | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:C2D5EA2A25E45FF67778A86019D35964 | SHA256:9A27FB104CD9F4D33A909E31B441F7D52E01CAFCEB67D5CA79A35E1DFF69B57B | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:395ED78BC123DDC70C5D138F6EFBECD8 | SHA256:A3FAAE9515B4195678810029BF1A6AB5F2D9792507EEE0CBF6DBDA81D73A4FCC | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:BC46681668027F27748DBDA2ABB8100D | SHA256:D7DB39DEAF6255E31F47EF9D9B8BB7812E274410F2BB951DFDE7874DFFD8542A | |||
| 5464 | Autoruns64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FA84E4BCC92AA5DB735AB50711040CDE | SHA256:6D7205E794FDE4219A62D9692ECDDF612663A5CF20399E79BE87B851FCA4CA33 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
44
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5464 | Autoruns64.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5464 | Autoruns64.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
5464 | Autoruns64.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
5464 | Autoruns64.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
5464 | Autoruns64.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5464 | Autoruns64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
1684 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |