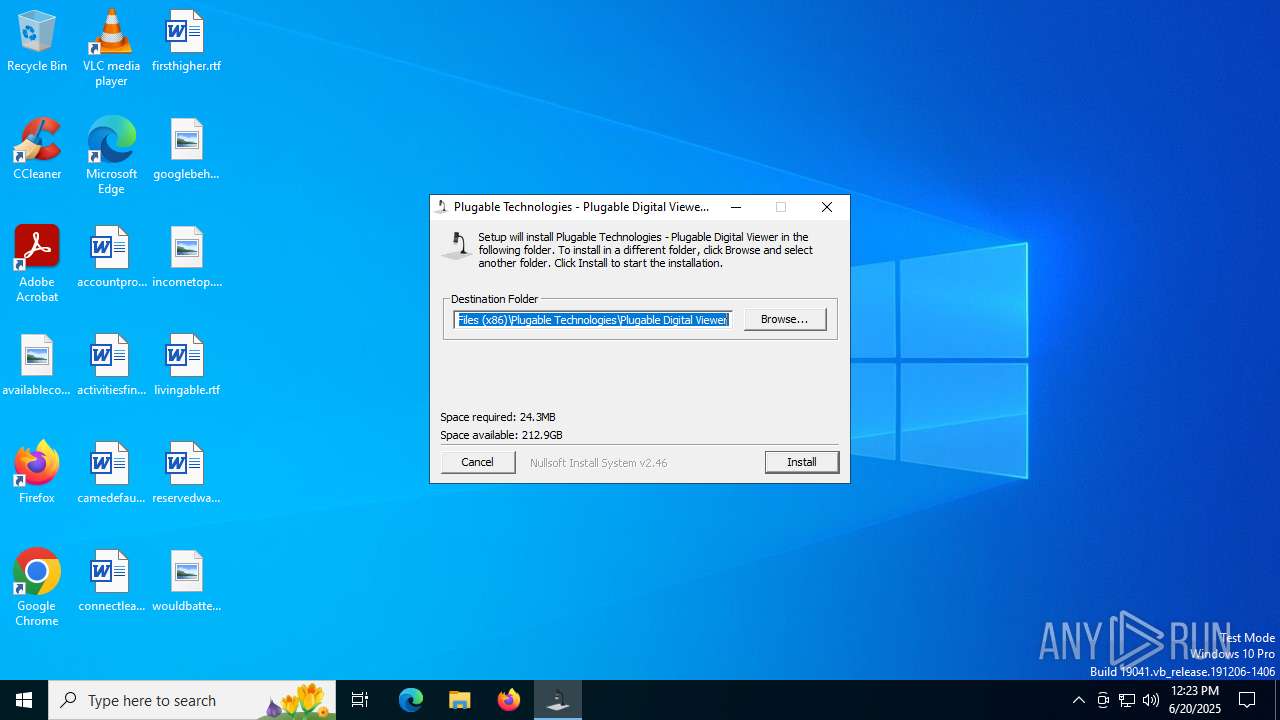
| File name: | Digital_Viewer.exe |
| Full analysis: | https://app.any.run/tasks/57b525ee-6334-4b5c-9180-ba33bf42fb96 |
| Verdict: | Malicious activity |
| Analysis date: | June 20, 2025, 12:23:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 821B37E3F8A9DDB36FF21026651A467B |
| SHA1: | FC0BE6EC62ACE14332E711BD6BBB57D083201338 |
| SHA256: | 32D2967C69D4115BC196AFB6ADE22FA45EC6C49B0CC705265F3DFEF3FFF357CC |
| SSDEEP: | 196608:rIC/C6oEHVQNbvshf0cDVZSSSbr46pEORI+tJEiVPsIypRBEb6c2:rICArNba8cCDbU6pdR7HGHEv2 |
MALICIOUS
Executing a file with an untrusted certificate
- Digital_Viewer.exe (PID: 4216)
Changes the autorun value in the registry
- rundll32.exe (PID: 5400)
- rundll32.exe (PID: 3628)
Registers / Runs the DLL via REGSVR32.EXE
- Xvid-1.3.3-20141019.exe (PID: 5644)
SUSPICIOUS
Executable content was dropped or overwritten
- Digital_Viewer.exe (PID: 6224)
- Xvid-1.3.3-20141019.exe (PID: 5644)
- rundll32.exe (PID: 5400)
- rundll32.exe (PID: 3628)
Uses RUNDLL32.EXE to load library
- Xvid-1.3.3-20141019.exe (PID: 5644)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 6408)
- regsvr32.exe (PID: 6220)
There is functionality for taking screenshot (YARA)
- Digital_Viewer.exe (PID: 6224)
Creates a software uninstall entry
- Digital_Viewer.exe (PID: 6224)
- Xvid-1.3.3-20141019.exe (PID: 5644)
INFO
Reads the computer name
- Digital_Viewer.exe (PID: 6224)
- Xvid-1.3.3-20141019.exe (PID: 5644)
Checks supported languages
- Digital_Viewer.exe (PID: 6224)
- Xvid-1.3.3-20141019.exe (PID: 5644)
- setavi32.exe (PID: 2864)
- setavi64.exe (PID: 316)
Create files in a temporary directory
- Digital_Viewer.exe (PID: 6224)
- Xvid-1.3.3-20141019.exe (PID: 5644)
Creates files in the program directory
- Digital_Viewer.exe (PID: 6224)
- Xvid-1.3.3-20141019.exe (PID: 5644)
Process checks whether UAC notifications are on
- Xvid-1.3.3-20141019.exe (PID: 5644)
Reads the time zone
- Xvid-1.3.3-20141019.exe (PID: 5644)
- runonce.exe (PID: 3092)
- runonce.exe (PID: 4104)
Reads CPU info
- Xvid-1.3.3-20141019.exe (PID: 5644)
The sample compiled with english language support
- Xvid-1.3.3-20141019.exe (PID: 5644)
- Digital_Viewer.exe (PID: 6224)
The sample compiled with german language support
- Xvid-1.3.3-20141019.exe (PID: 5644)
Launching a file from a Registry key
- rundll32.exe (PID: 5400)
- rundll32.exe (PID: 3628)
Reads security settings of Internet Explorer
- runonce.exe (PID: 3092)
- runonce.exe (PID: 4104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
150
Monitored processes
14
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | C:\Users\admin\AppData\Local\Temp\xvid_x64\setavi64.exe | C:\Users\admin\AppData\Local\Temp\xvid_x64\setavi64.exe | Xvid-1.3.3-20141019.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2864 | C:\Users\admin\AppData\Local\Temp\xvid_x86\setavi32.exe | C:\Users\admin\AppData\Local\Temp\xvid_x86\setavi32.exe | Xvid-1.3.3-20141019.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 3092 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\SysWOW64\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3628 | C:\Windows\System32\rundll32.exe setupapi.dll,InstallHinfSection DefaultInstall 0 C:\Users\admin\AppData\Local\Temp/xvid_x64/xvid.inf | C:\Windows\System32\rundll32.exe | Xvid-1.3.3-20141019.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4104 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4216 | "C:\Users\admin\AppData\Local\Temp\Digital_Viewer.exe" | C:\Users\admin\AppData\Local\Temp\Digital_Viewer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4768 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4768 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5080 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\SysWOW64\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | C:\Windows\System32\rundll32.exe setupapi.dll,InstallHinfSection DefaultInstall 0 C:\Users\admin\AppData\Local\Temp/xvid_x86/xvid.inf | C:\Windows\SysWOW64\rundll32.exe | Xvid-1.3.3-20141019.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 230
Read events
2 117
Write events
84
Delete events
29
Modification events
| (PID) Process: | (5400) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\drivers.desc |
| Operation: | write | Name: | xvidvfw.dll |
Value: Xvid MPEG-4 Video Codec | |||
| (PID) Process: | (5400) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32 |
| Operation: | write | Name: | vidc.XVID |
Value: xvidvfw.dll | |||
| (PID) Process: | (5400) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (3092) runonce.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | GrpConv |
Value: grpconv -o | |||
| (PID) Process: | (5644) Xvid-1.3.3-20141019.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32 |
| Operation: | write | Name: | msacm.l3acm |
Value: l3codecp.acm | |||
| (PID) Process: | (5644) Xvid-1.3.3-20141019.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\drivers.desc |
| Operation: | write | Name: | l3codecp.acm |
Value: Fraunhofer IIS MPEG Layer-3 Codec (professional) | |||
| (PID) Process: | (5644) Xvid-1.3.3-20141019.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\drivers.desc |
| Operation: | delete value | Name: | l3codeca.acm |
Value: | |||
| (PID) Process: | (5644) Xvid-1.3.3-20141019.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\msacm\msacm.l3acm |
| Operation: | write | Name: | Driver |
Value: l3codecp.acm | |||
| (PID) Process: | (6408) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\MediaFoundation\Transforms\64697678-0000-0010-8000-00aa00389b71 |
| Operation: | write | Name: | InputTypes |
Value: 7669647300001000800000AA00389B717876696400001000800000AA00389B717669647300001000800000AA00389B715856494400001000800000AA00389B717669647300001000800000AA00389B716469767800001000800000AA00389B717669647300001000800000AA00389B714449565800001000800000AA00389B717669647300001000800000AA00389B716478353000001000800000AA00389B717669647300001000800000AA00389B714458353000001000800000AA00389B717669647300001000800000AA00389B713369767800001000800000AA00389B717669647300001000800000AA00389B713349565800001000800000AA00389B717669647300001000800000AA00389B713369763000001000800000AA00389B717669647300001000800000AA00389B713349563000001000800000AA00389B717669647300001000800000AA00389B713369763100001000800000AA00389B717669647300001000800000AA00389B713349563100001000800000AA00389B717669647300001000800000AA00389B713369763200001000800000AA00389B717669647300001000800000AA00389B713349563200001000800000AA00389B717669647300001000800000AA00389B716C6D703400001000800000AA00389B717669647300001000800000AA00389B714C4D503400001000800000AA00389B717669647300001000800000AA00389B71726D703400001000800000AA00389B717669647300001000800000AA00389B71524D503400001000800000AA00389B717669647300001000800000AA00389B71736D703400001000800000AA00389B717669647300001000800000AA00389B71534D503400001000800000AA00389B717669647300001000800000AA00389B716864783400001000800000AA00389B717669647300001000800000AA00389B714844583400001000800000AA00389B717669647300001000800000AA00389B716D70347600001000800000AA00389B717669647300001000800000AA00389B714D50345600001000800000AA00389B71 | |||
| (PID) Process: | (6408) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\MediaFoundation\Transforms\64697678-0000-0010-8000-00aa00389b71 |
| Operation: | write | Name: | OutputTypes |
Value: 7669647300001000800000AA00389B7100000000000000000000000000000000 | |||
Executable files
48
Suspicious files
11
Text files
24
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5644 | Xvid-1.3.3-20141019.exe | C:\Users\admin\AppData\Local\Temp\be29e7f1-71ae-4703-50cb-1d52be512f51\twapi-be29e7f1-71ae-4703-50cb-1d52be512f51.dll | executable | |
MD5:A210F1AC135E5331C314CE5F394FB5A5 | SHA256:65B32EA2982078FB9A18E88FEEC238CB76ED2AE6C2BB4DDB0F6A9C4F57B1D62B | |||
| 6224 | Digital_Viewer.exe | C:\Xvid-1.3.3-20141019.exe | executable | |
MD5:542BB1E4393255C16F03583727320812 | SHA256:23ACF6354A07C28DF537144BF9290586C4A9FFB3A373142CC5FC66D3BE9AF39D | |||
| 5644 | Xvid-1.3.3-20141019.exe | C:\Users\admin\AppData\Local\Temp\BR77D1.tmp | executable | |
MD5:08AD4CD2A940379F1DCDBDB9884A1375 | SHA256:78827E2B1EF0AAD4F8B1B42D0964064819AA22BFCD537EBAACB30D817EDC06D8 | |||
| 5644 | Xvid-1.3.3-20141019.exe | C:\Users\admin\AppData\Local\Temp\BR77D2.tmp | executable | |
MD5:D33EE6D856350F321189138134745388 | SHA256:9EB5405449BE0D43FEE145B5B6D5FE01799C6F635389A44F58A0AF2793A1B737 | |||
| 5644 | Xvid-1.3.3-20141019.exe | C:\Users\admin\AppData\Local\Temp\BR7762.tmp | executable | |
MD5:98E531FFD84600DD27E8BC4A83DCDD5E | SHA256:09DD23B63F9FE79D039E43F274B5AEB9DF01A816DEFC8C503531E1B3643921A3 | |||
| 5644 | Xvid-1.3.3-20141019.exe | C:\Users\admin\AppData\Local\Temp\BR7851.tmp | executable | |
MD5:72FAB2C90296330ECA3787DC4093E208 | SHA256:6251F51D616CDCB4256D73A67819A3419E5B59158BE358CF387B90E39C05C260 | |||
| 5644 | Xvid-1.3.3-20141019.exe | C:\Users\admin\AppData\Local\Temp\BR7AB3.tmp | executable | |
MD5:B4EB1E7438DC099078CE8FE6E5A2C99D | SHA256:F9AB62A357A9D964CEE9E078EF5C6A66D3AFE9B27C57D01D8B4FE1D7930C630B | |||
| 5644 | Xvid-1.3.3-20141019.exe | C:\Users\admin\AppData\Local\Temp\BR7AC4.tmp | executable | |
MD5:FA89B48BF972FEF2F26C24A5C1BD1689 | SHA256:6E5348CBCE980777D8E9827B57A90BE829F94884C9F96395807BABDB9B445756 | |||
| 6224 | Digital_Viewer.exe | C:\Users\admin\AppData\Local\Temp\nsk6785.tmp\UserInfo.dll | executable | |
MD5:7579ADE7AE1747A31960A228CE02E666 | SHA256:564C80DEC62D76C53497C40094DB360FF8A36E0DC1BDA8383D0F9583138997F5 | |||
| 5644 | Xvid-1.3.3-20141019.exe | C:\Users\admin\AppData\Local\Temp\BR77E2.tmp | executable | |
MD5:027491B39A7B16B116E780F55ABC288E | SHA256:EEF69D005BF1C0B715C8D6205400D4755C261DD38DDFBBFE918E6EE91F21F1F0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5600 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5600 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5012 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6356 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5600 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
setavi32.exe | Successfully changed DACL
|
setavi64.exe | Successfully changed DACL
|