| File name: | Exe2Aut v0.11.rar |
| Full analysis: | https://app.any.run/tasks/0575611b-2b69-4a5f-8c0c-db8974ec66e4 |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 16:44:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 48EE8905C196A20DE313C656580589D6 |
| SHA1: | 2B466FBA87876E3A71A843151DBFFA0D0558746D |
| SHA256: | 32C6C7A3E93FAEB74AD56230EA7A037BDBC2FE11E231D8078BFE5039EA18B4E2 |
| SSDEEP: | 24576:yw9z7xcTLRSfgr/EJ90TI7Mvwnvg7d6BX41t5ppMnL3GGPPga1D3m/6BPOAPO2YI:b9z7xcPRetJ99gwv+1tM2GPPfS/l0BN7 |
MALICIOUS
Application was dropped or rewritten from another process
- Exe2Aut.exe (PID: 3444)
- New AutoIt v3 Script.exe (PID: 2320)
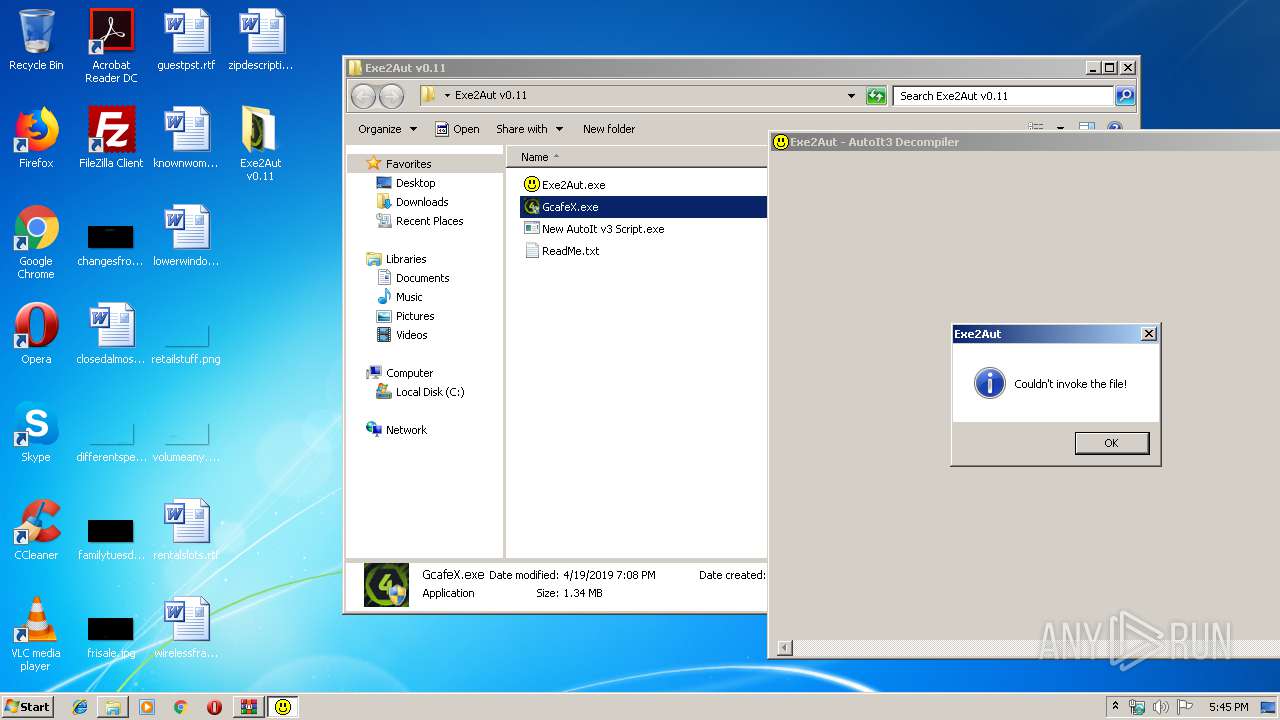
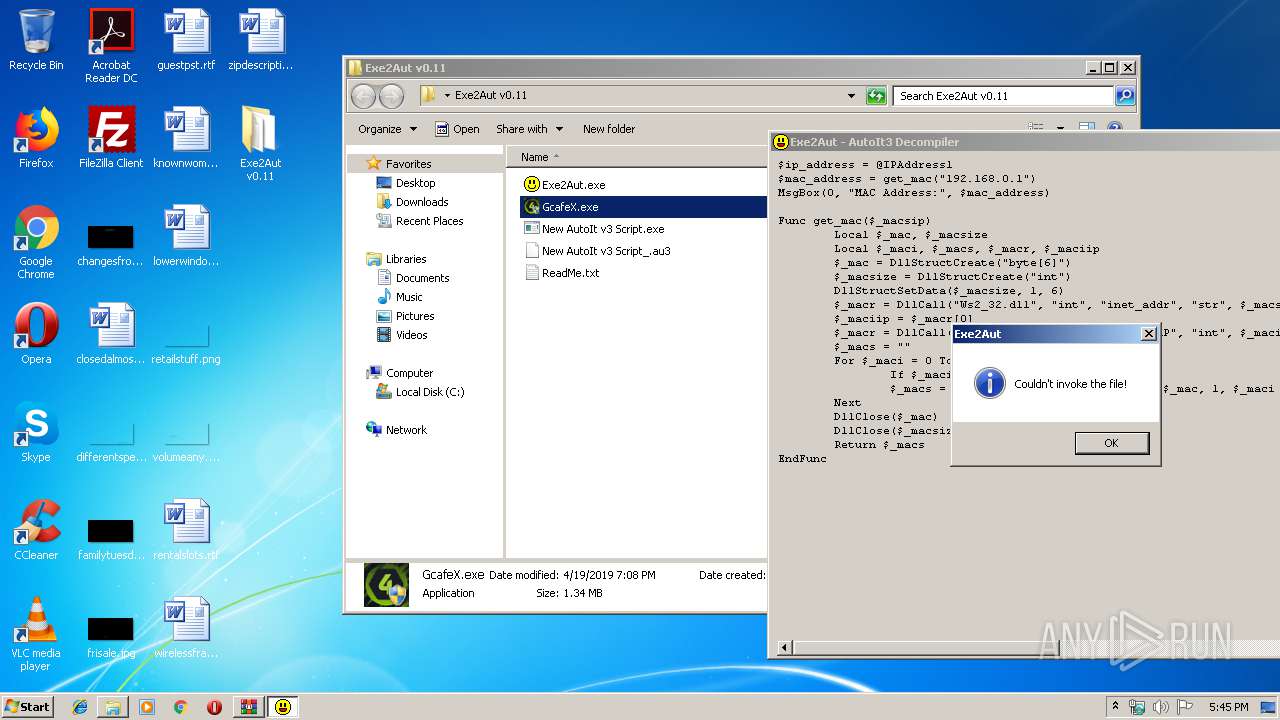
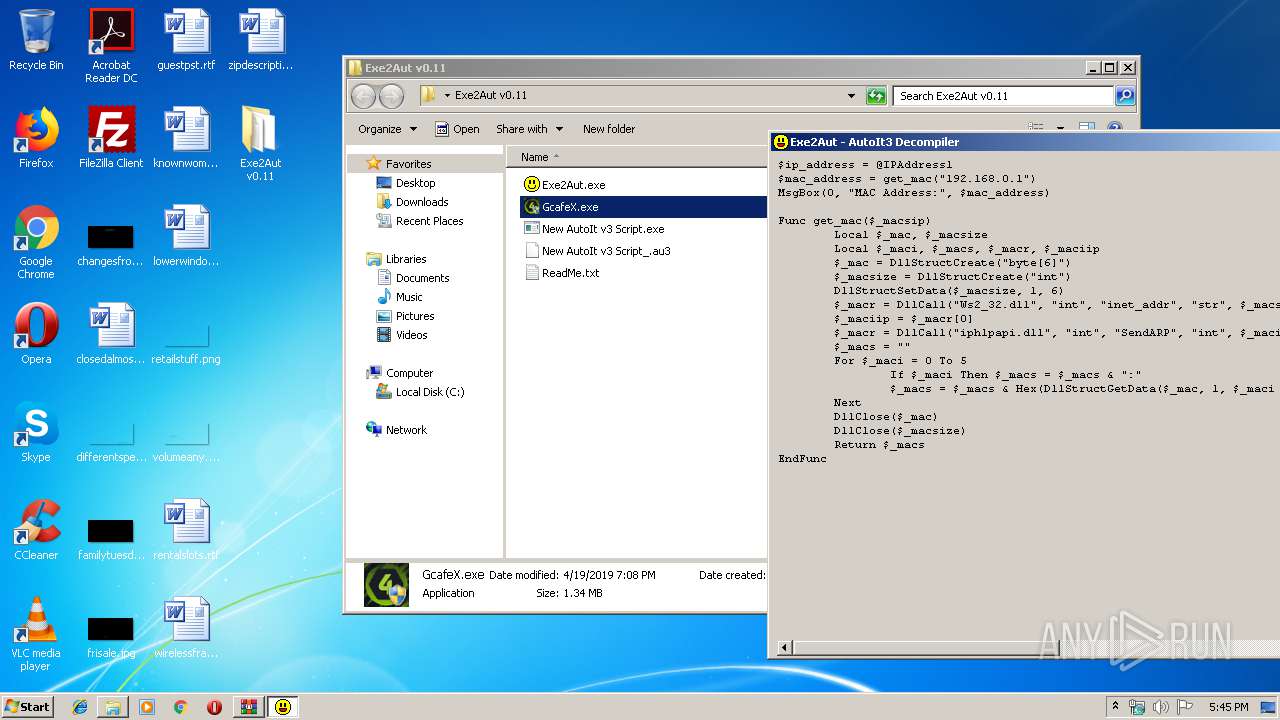
- GcafeX.exe (PID: 3608)
- GcafeX.exe (PID: 2848)
- Exe2Aut.exe (PID: 2128)
- GcafeX.exe (PID: 3020)
Loads dropped or rewritten executable
- New AutoIt v3 Script.exe (PID: 2320)
- Exe2Aut.exe (PID: 2128)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2792)
- Exe2Aut.exe (PID: 3444)
Application launched itself
- Exe2Aut.exe (PID: 3444)
INFO
Manual execution by user
- Exe2Aut.exe (PID: 3444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 42406 |
|---|---|
| UncompressedSize: | 50176 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2016:04:24 18:44:03 |
| PackingMethod: | Normal |
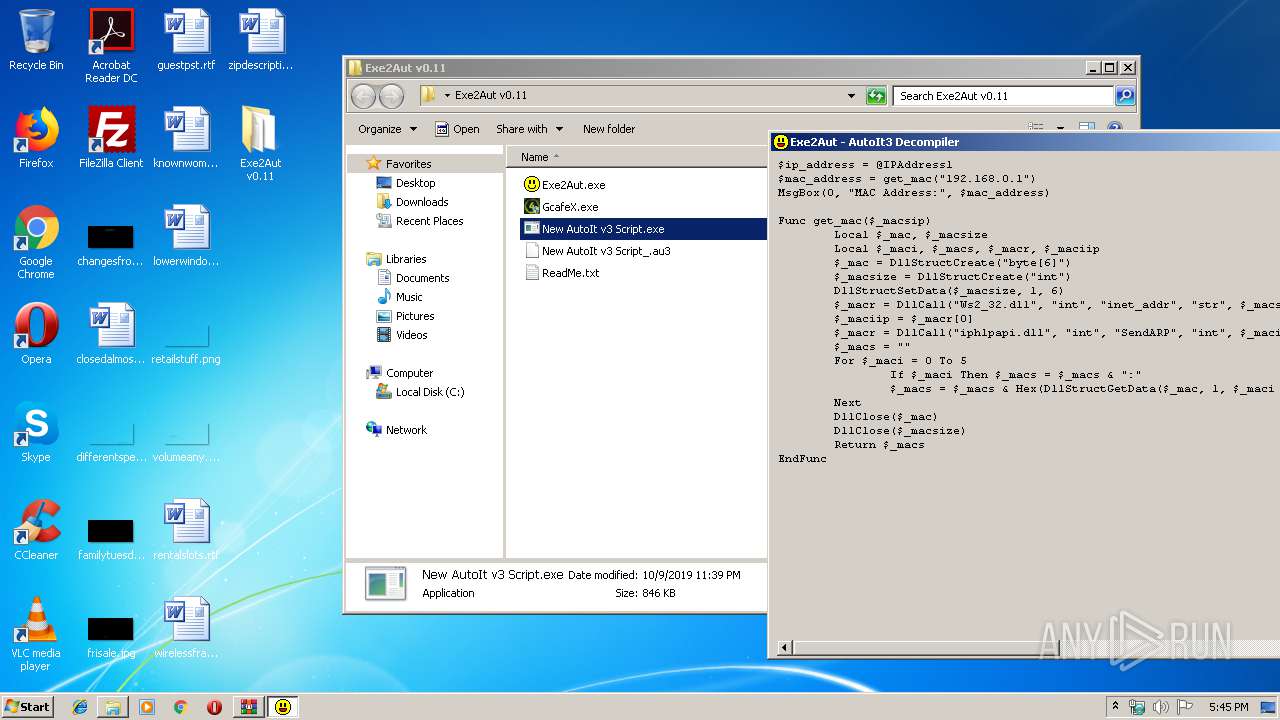
| ArchivedFileName: | Exe2Aut v0.11\Exe2Aut.exe |
Total processes
41
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2128 | "C:\Users\admin\Desktop\Exe2Aut v0.11\Exe2Aut.exe" | C:\Users\admin\Desktop\Exe2Aut v0.11\Exe2Aut.exe | — | Exe2Aut.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\Desktop\Exe2Aut v0.11\New AutoIt v3 Script.exe" | C:\Users\admin\Desktop\Exe2Aut v0.11\New AutoIt v3 Script.exe | — | Exe2Aut.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2792 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Exe2Aut v0.11.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\Desktop\Exe2Aut v0.11\GcafeX.exe" | C:\Users\admin\Desktop\Exe2Aut v0.11\GcafeX.exe | — | Exe2Aut.exe | |||||||||||
User: admin Company: TranNghiaIT Integrity Level: MEDIUM Description: TranNghiaIT Exit code: 3221226540 Version: 3.3.14.5 Modules
| |||||||||||||||
| 3020 | "C:\Users\admin\Desktop\Exe2Aut v0.11\GcafeX.exe" | C:\Users\admin\Desktop\Exe2Aut v0.11\GcafeX.exe | — | Exe2Aut.exe | |||||||||||
User: admin Company: TranNghiaIT Integrity Level: MEDIUM Description: TranNghiaIT Exit code: 3221226540 Version: 3.3.14.5 Modules
| |||||||||||||||
| 3444 | "C:\Users\admin\Desktop\Exe2Aut v0.11\Exe2Aut.exe" | C:\Users\admin\Desktop\Exe2Aut v0.11\Exe2Aut.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3608 | "C:\Users\admin\Desktop\Exe2Aut v0.11\GcafeX.exe" | C:\Users\admin\Desktop\Exe2Aut v0.11\GcafeX.exe | — | Exe2Aut.exe | |||||||||||
User: admin Company: TranNghiaIT Integrity Level: MEDIUM Description: TranNghiaIT Exit code: 3221226540 Version: 3.3.14.5 Modules
| |||||||||||||||
Total events
438
Read events
428
Write events
10
Delete events
0
Modification events
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Exe2Aut v0.11.rar | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
4
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3444 | Exe2Aut.exe | C:\Users\admin\AppData\Local\Temp\18C1.tmp | — | |
MD5:— | SHA256:— | |||
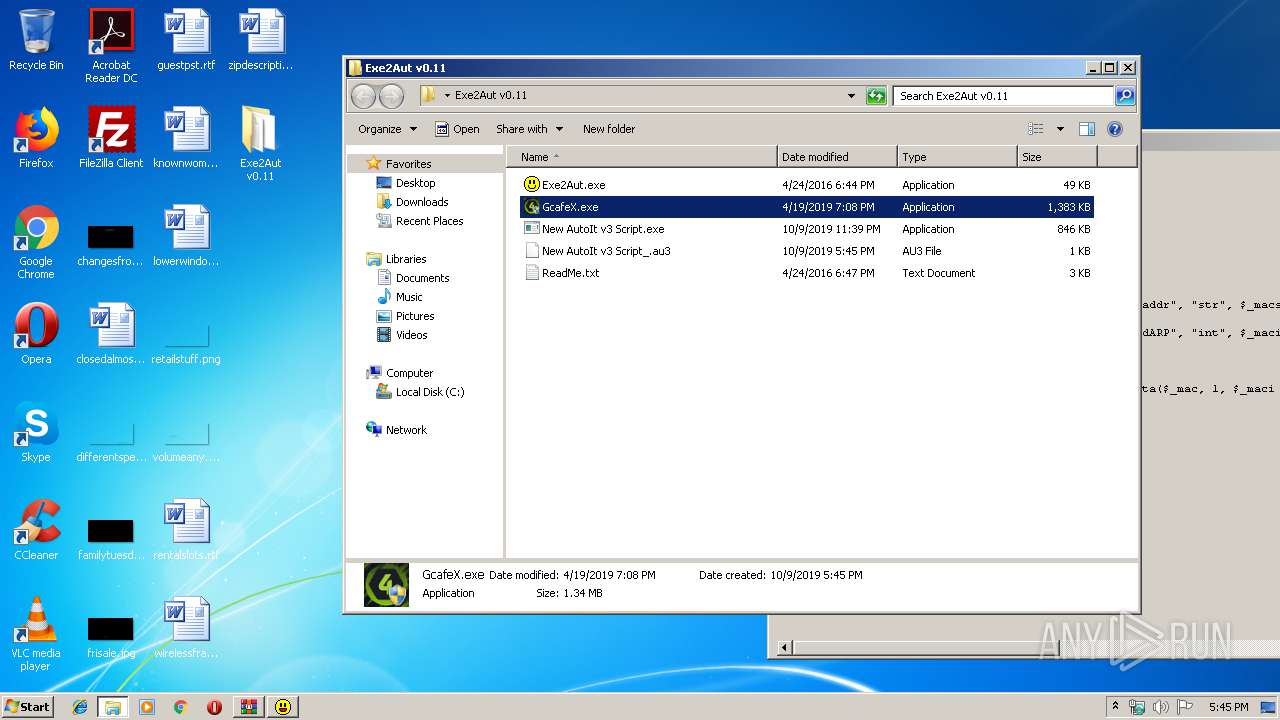
| 2792 | WinRAR.exe | C:\Users\admin\Desktop\Exe2Aut v0.11\Exe2Aut.exe | executable | |
MD5:— | SHA256:— | |||
| 2792 | WinRAR.exe | C:\Users\admin\Desktop\Exe2Aut v0.11\ReadMe.txt | text | |
MD5:— | SHA256:— | |||
| 2792 | WinRAR.exe | C:\Users\admin\Desktop\Exe2Aut v0.11\GcafeX.exe | executable | |
MD5:— | SHA256:— | |||
| 2792 | WinRAR.exe | C:\Users\admin\Desktop\Exe2Aut v0.11\New AutoIt v3 Script.exe | executable | |
MD5:— | SHA256:— | |||
| 3444 | Exe2Aut.exe | C:\Users\admin\AppData\Local\Temp\C36C.tmp | executable | |
MD5:— | SHA256:— | |||
| 2320 | New AutoIt v3 Script.exe | C:\Users\admin\Desktop\Exe2Aut v0.11\New AutoIt v3 Script_.au3 | binary | |
MD5:— | SHA256:— | |||
| 3444 | Exe2Aut.exe | C:\Users\admin\Desktop\Exe2Aut v0.11\New AutoIt v3 Script_.au3 | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report