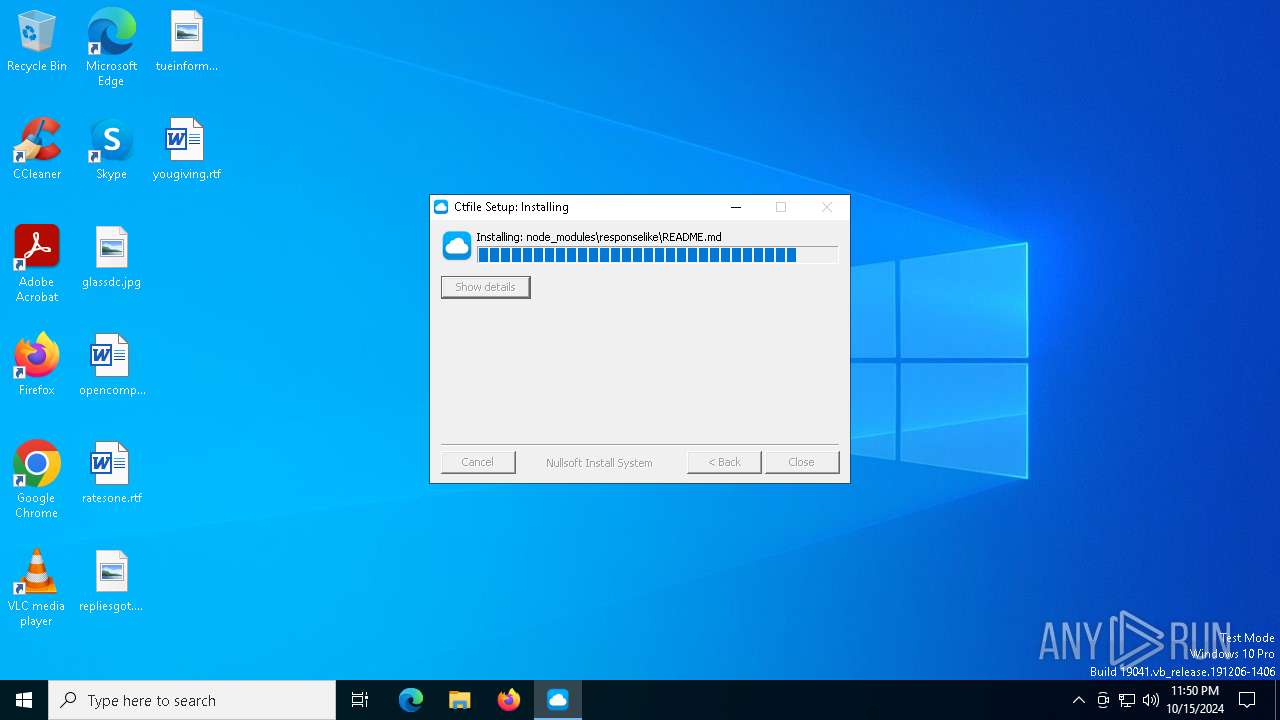
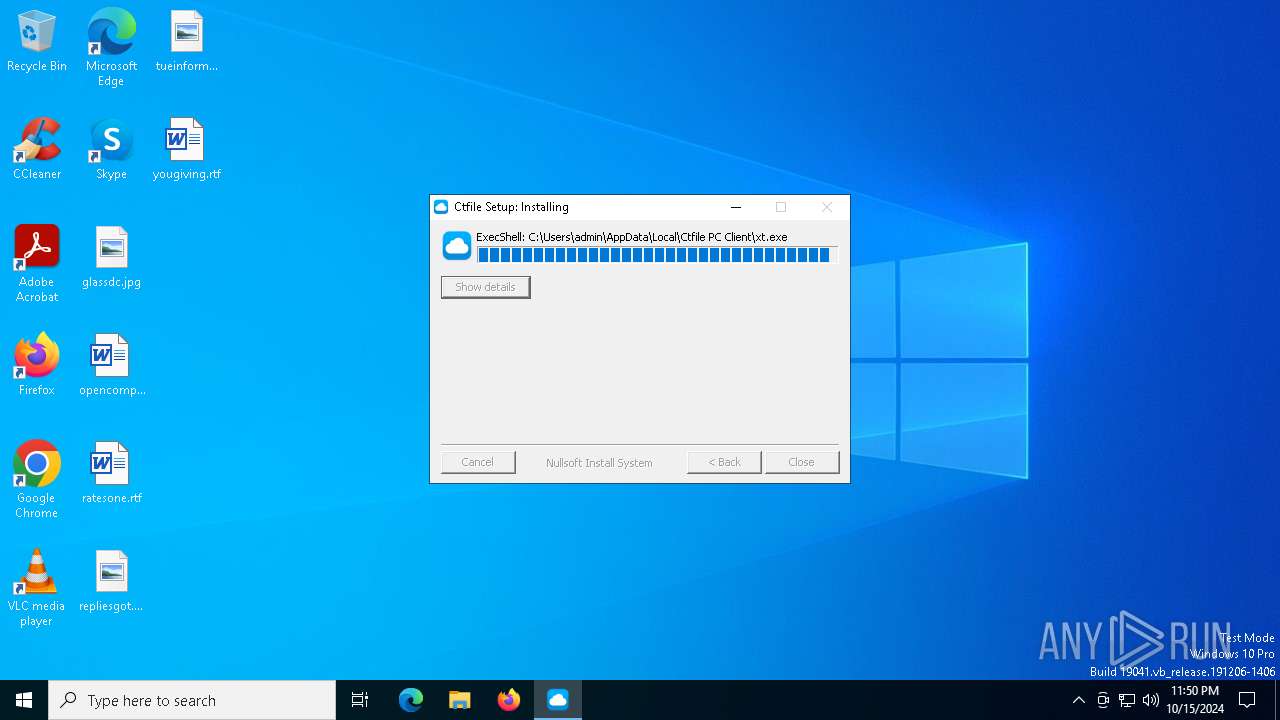
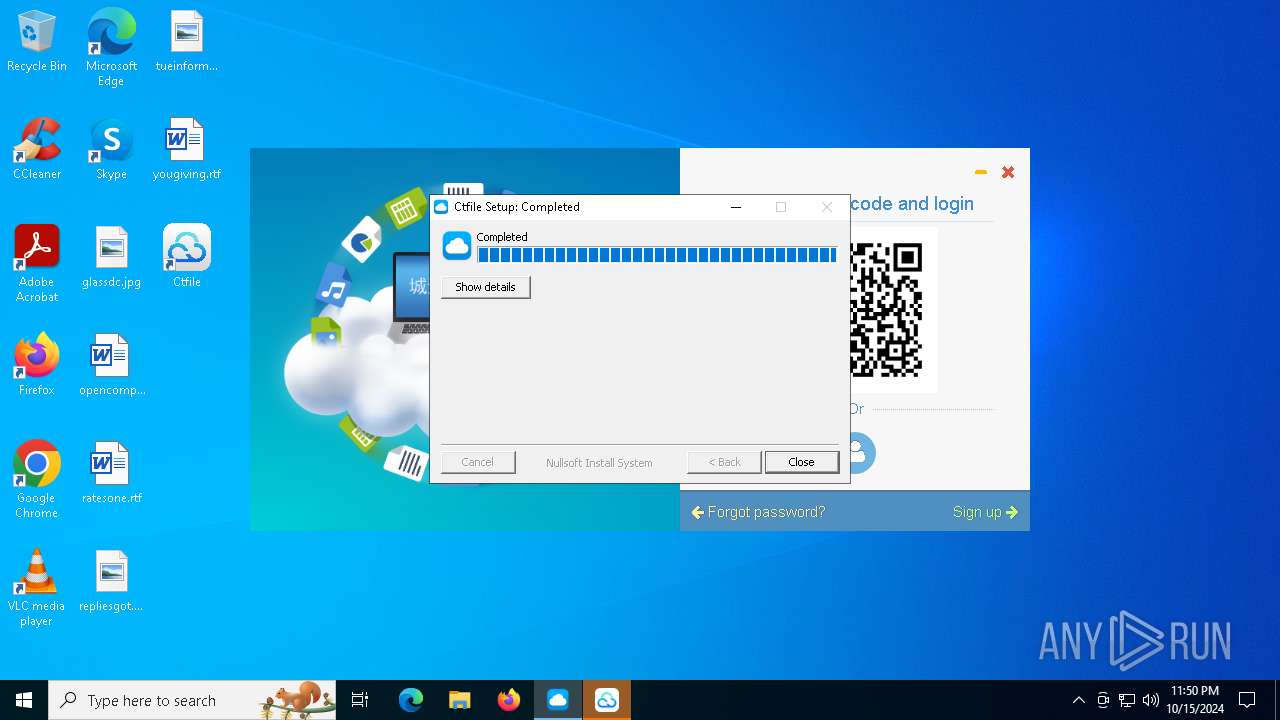
| File name: | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527 |
| Full analysis: | https://app.any.run/tasks/6edccd12-d57b-41ce-8bca-c747c1328de2 |
| Verdict: | Malicious activity |
| Analysis date: | October 15, 2024, 23:48:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | CB17596D65A15B3D0ED298789D41B38D |
| SHA1: | EC5BE5B1BF1B42AFC70E7A5F50AA1E031E10DA84 |
| SHA256: | 32C643694006075F1AC461DCFEE4E7DCCAFA249052F88CCC1D28C25FBF1ADA09 |
| SSDEEP: | 6144:xyNc1a7xk4X+sThLfOdB0prjc32EAIPRFyPM0hDFyyFMTI5iS:xok2xkY+qLfOdB09jcGEzjuDiyFEIIS |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Application launched itself
- xt.exe (PID: 3948)
- xt.exe (PID: 6868)
Process drops legitimate windows executable
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Malware-specific behavior (creating "System.dll" in Temp)
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
The process creates files with name similar to system file names
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Reads security settings of Internet Explorer
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Checks Windows Trust Settings
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
INFO
Checks supported languages
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Reads the computer name
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Create files in a temporary directory
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Creates files or folders in the user directory
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Checks proxy server information
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Reads the machine GUID from the registry
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Reads the software policy settings
- SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe (PID: 6360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:11:22 09:54:59+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 28672 |
| InitializedDataSize: | 186368 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3a0b |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
146
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1344 | "C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe" --type=gpu-process --no-sandbox --user-data-dir="C:\Users\admin\AppData\Local\ctfilepc\User Data" --nwapp-path="C:\Users\admin\AppData\Local\Ctfile PC Client" --start-stack-profiler --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1968 --field-trial-handle=1972,i,13756730630287709540,5581992763927526770,262144 /prefetch:2 | C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe | — | xt.exe | |||||||||||
User: admin Company: KingsWills LLC Integrity Level: HIGH Description: ctfile Version: 3.5 Modules
| |||||||||||||||
| 3432 | "C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-sandbox --user-data-dir="C:\Users\admin\AppData\Local\ctfilepc\User Data" --nwapp-path="C:\Users\admin\AppData\Local\Ctfile PC Client" --start-stack-profiler --mojo-platform-channel-handle=2052 --field-trial-handle=1972,i,13756730630287709540,5581992763927526770,262144 /prefetch:8 | C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe | xt.exe | ||||||||||||
User: admin Company: KingsWills LLC Integrity Level: HIGH Description: ctfile Version: 3.5 Modules
| |||||||||||||||
| 3948 | "C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\ctfilepc\User Data" /prefetch:7 --monitor-self --monitor-self-argument=--type=crashpad-handler "--monitor-self-argument=--user-data-dir=C:\Users\admin\AppData\Local\ctfilepc\User Data" --monitor-self-argument=/prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\ctfilepc\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\ctfilepc\User Data" --annotation=plat=Win64 --annotation=prod=ctfilepc --annotation=ver= --initial-client-data=0x270,0x274,0x278,0x26c,0x27c,0x7ffbcb29a970,0x7ffbcb29a980,0x7ffbcb29a990 | C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe | xt.exe | ||||||||||||
User: admin Company: KingsWills LLC Integrity Level: HIGH Description: ctfile Version: 3.5 Modules
| |||||||||||||||
| 5892 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6360 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6472 | "C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\ctfilepc\User Data" --nwapp-path="C:\Users\admin\AppData\Local\Ctfile PC Client" --nwjs --extension-process --first-renderer-process --no-sandbox --file-url-path-alias="/gen=C:\Users\admin\AppData\Local\Ctfile PC Client\gen" --no-zygote --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2792 --field-trial-handle=1972,i,13756730630287709540,5581992763927526770,262144 /prefetch:1 | C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe | — | xt.exe | |||||||||||
User: admin Company: KingsWills LLC Integrity Level: HIGH Description: ctfile Version: 3.5 Modules
| |||||||||||||||
| 6708 | "C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --no-sandbox --user-data-dir="C:\Users\admin\AppData\Local\ctfilepc\User Data" --nwapp-path="C:\Users\admin\AppData\Local\Ctfile PC Client" --mojo-platform-channel-handle=3356 --field-trial-handle=1972,i,13756730630287709540,5581992763927526770,262144 /prefetch:8 | C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe | — | xt.exe | |||||||||||
User: admin Company: KingsWills LLC Integrity Level: HIGH Description: ctfile Exit code: 0 Version: 3.5 Modules
| |||||||||||||||
| 6868 | "C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe" | C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | ||||||||||||
User: admin Company: KingsWills LLC Integrity Level: HIGH Description: ctfile Version: 3.5 Modules
| |||||||||||||||
| 6960 | "C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-sandbox --user-data-dir="C:\Users\admin\AppData\Local\ctfilepc\User Data" --nwapp-path="C:\Users\admin\AppData\Local\Ctfile PC Client" --mojo-platform-channel-handle=2340 --field-trial-handle=1972,i,13756730630287709540,5581992763927526770,262144 /prefetch:8 | C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe | — | xt.exe | |||||||||||
User: admin Company: KingsWills LLC Integrity Level: HIGH Description: ctfile Version: 3.5 Modules
| |||||||||||||||
| 7144 | "C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\ctfilepc\User Data" /prefetch:7 --no-periodic-tasks --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\ctfilepc\User Data\Crashpad" --annotation=plat=Win64 --annotation=prod=ctfilepc --annotation=ver= --initial-client-data=0x1f4,0x1f8,0x1fc,0x1ac,0x200,0x7ff63c4dca30,0x7ff63c4dca40,0x7ff63c4dca50 | C:\Users\admin\AppData\Local\Ctfile PC Client\xt.exe | — | xt.exe | |||||||||||
User: admin Company: KingsWills LLC Integrity Level: HIGH Description: ctfile Version: 3.5 Modules
| |||||||||||||||
Total events
3 139
Read events
3 103
Write events
35
Delete events
1
Modification events
| (PID) Process: | (6360) SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6360) SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6360) SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6360) SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\ctfile |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (6868) xt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\nwjs\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6868) xt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\nwjs |
| Operation: | write | Name: | metricsid |
Value: ce768fae-404b-4a2e-8f22-c4ec6046e737 | |||
| (PID) Process: | (6868) xt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\nwjs |
| Operation: | write | Name: | metricsid_installdate |
Value: 1729036240 | |||
| (PID) Process: | (6868) xt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\nwjs |
| Operation: | write | Name: | metricsid_enableddate |
Value: 1729036240 | |||
| (PID) Process: | (6868) xt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\nwjs |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6868) xt.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\nwjs |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
16
Suspicious files
386
Text files
610
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\3.27[1].zip | — | |
MD5:— | SHA256:— | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\Local\Temp\ctfile.zip | — | |
MD5:— | SHA256:— | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\Local\Ctfile PC Client\html\assets\css\ace-fonts.css | text | |
MD5:761C749C401EA9292D64B99898DCA603 | SHA256:D00968C240A59B80E2A9E5669901E6789CE551CD7701526B672DA6D162C35962 | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\Local\Ctfile PC Client\ffmpeg.dll | executable | |
MD5:6BAD5AFBD2D0E58DB22CD5FFF530DC22 | SHA256:D5275CF50E68EDE78A4FADFF6191467F9A7538788C36BC2C1B0CFAB2CBAFA18F | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\Local\Ctfile PC Client\html\assets\css\ace-part2.css | text | |
MD5:B9BEFBF4BE5B73628C628C001A28CFD2 | SHA256:67E51FB70738AA9AED4599BA41042A3E4A6C61DE694D5F10B7FC708EE0C2F281 | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\Local\Ctfile PC Client\app.js | text | |
MD5:037DBF0B8F73C400E453488BE6480B1C | SHA256:3ECA7919AD12C001382813ABA5A28E8BEC18E57DAE3FA649DD9F6DBEFA093F86 | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:7D3AF44EF9F6B19E493F6F921DAB9749 | SHA256:CBEE56E948176AF0037AB1252F902CB8E9C238BC17FEA888C8A3E82C161E627B | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:E935BC5762068CAF3E24A2683B1B8A88 | SHA256:A8ACCFCFEB51BD73DF23B91F4D89FF1A9EB7438EF5B12E8AFDA1A6FF1769E89D | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\Local\Temp\nstB698.tmp\inetc.dll | executable | |
MD5:38F2B22967573A872426D05BDC1A1A70 | SHA256:83005624A3C515E8E4454A416693BA0FBF384FF5EA0E1471F520DFAE790D4AB7 | |||
| 6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:DA6828DBF915C72CE24A57C6B1CC1F73 | SHA256:EB7035D40B3A6598E9D8047D35C69E040274E61CA260CFD5EC9B92CE1C6DEE5F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
70
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2724 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | GET | 200 | 142.250.184.195:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3824 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1252 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | 47.56.109.241:443 | web.ctfile.com | Alibaba US Technology Co., Ltd. | HK | whitelisted |
6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | 142.250.184.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
6944 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6360 | SecuriteInfo.com.suspected.of.Trojan.Downloader.gen.18111.15527.exe | 8.210.109.65:443 | imgstatic.ctfile.com | Alibaba US Technology Co., Ltd. | HK | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
web.ctfile.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
imgstatic.ctfile.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
xt.exe | [1015/235040.537:ERROR:filesystem_win.cc(130)] GetFileAttributes C:\Users\admin\AppData\Local\ctfilepc\User Data\Crashpad\attachments\b8c626fd-108b-425d-96ed-9ca9b02a101a: The system cannot find the file specified. (0x2)
|
xt.exe | [1015/235040.537:ERROR:filesystem_win.cc(130)] GetFileAttributes C:\Users\admin\AppData\Local\ctfilepc\User Data\Crashpad\attachments\b8c626fd-108b-425d-96ed-9ca9b02a101a: The system cannot find the file specified. (0x2)
|
xt.exe | [1015/235040.553:ERROR:filesystem_win.cc(130)] GetFileAttributes C:\Users\admin\AppData\Local\ctfilepc\User Data\Crashpad\attachments\b8c626fd-108b-425d-96ed-9ca9b02a101a: The system cannot find the file specified. (0x2)
|