| File name: | eplan 2.1-27 x64 crack.exe |
| Full analysis: | https://app.any.run/tasks/7078d02b-f410-414e-bb01-7a52dd96ebe4 |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2024, 10:39:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive, 4 sections |
| MD5: | 7A7954BC26D8B13D330AFDA28AE556C1 |
| SHA1: | B68549DB6D34B1EAEC2FD47972DEC826324827FE |
| SHA256: | 329CEB1F4286F66F6D10923BEA737EF63193272121AB9C8E075FE33414C1EDFA |
| SSDEEP: | 12288:P8WWL6vPYy56IAjX2CSp/kbgFvyJYqgnPSLrutN03xVxF:Yop//PPSLrutN0BVn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- eplan 2.1-27 x64 crack.exe (PID: 624)
Executable content was dropped or overwritten
- eplan 2.1-27 x64 crack.exe (PID: 624)
Drops a system driver (possible attempt to evade defenses)
- eplan 2.1-27 x64 crack.exe (PID: 624)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 188)
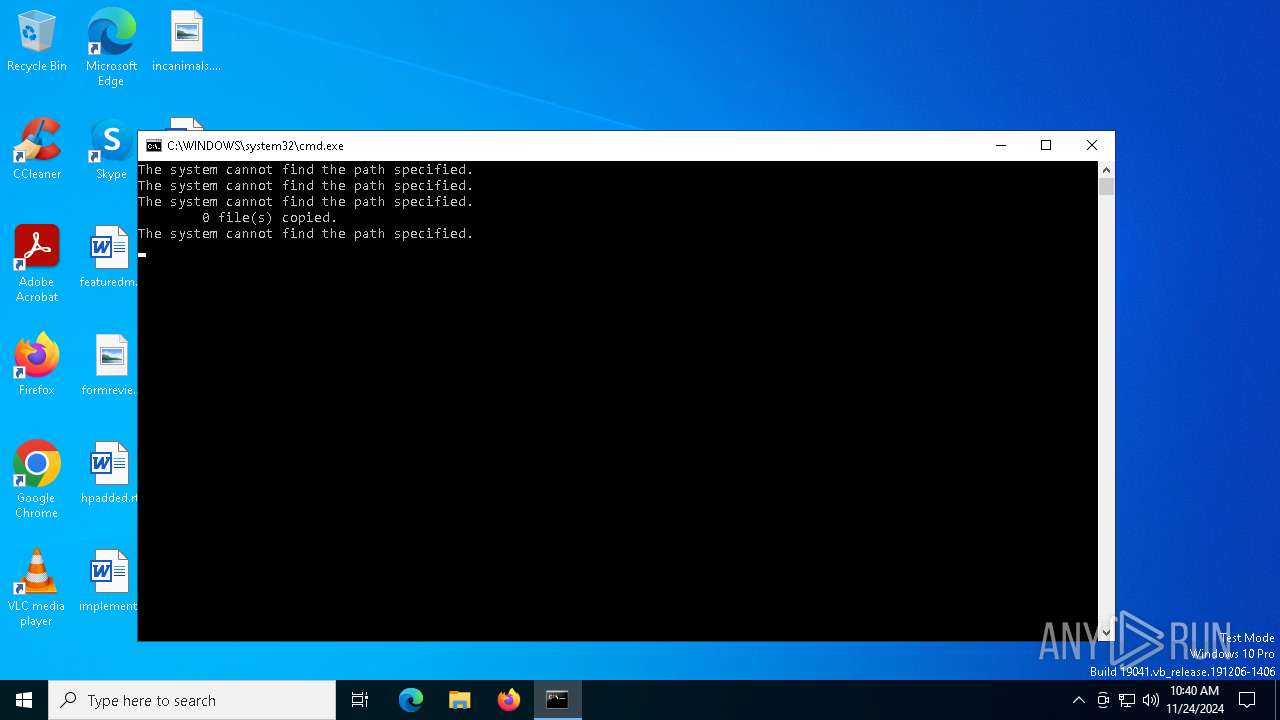
Starts CMD.EXE for commands execution
- eplan 2.1-27 x64 crack.exe (PID: 624)
The executable file from the user directory is run by the CMD process
- devcon.exe (PID: 5000)
- devcon.exe (PID: 2800)
Process drops legitimate windows executable
- eplan 2.1-27 x64 crack.exe (PID: 624)
Executing commands from ".cmd" file
- eplan 2.1-27 x64 crack.exe (PID: 624)
INFO
Checks supported languages
- eplan 2.1-27 x64 crack.exe (PID: 624)
- devcon.exe (PID: 2800)
- devcon.exe (PID: 5000)
The process uses the downloaded file
- cmd.exe (PID: 188)
- eplan 2.1-27 x64 crack.exe (PID: 624)
Process checks computer location settings
- eplan 2.1-27 x64 crack.exe (PID: 624)
Reads the computer name
- eplan 2.1-27 x64 crack.exe (PID: 624)
Create files in a temporary directory
- eplan 2.1-27 x64 crack.exe (PID: 624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:12:02 10:07:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 165376 |
| InitializedDataSize: | 306688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d5db |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
137
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX0\install.cmd" " | C:\Windows\SysWOW64\cmd.exe | — | eplan 2.1-27 x64 crack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | "C:\Users\admin\AppData\Local\Temp\eplan 2.1-27 x64 crack.exe" | C:\Users\admin\AppData\Local\Temp\eplan 2.1-27 x64 crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2800 | devcon install multikey.inf root\multikey | C:\Users\admin\AppData\Local\Temp\RarSFX0\devcon.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 3524 | "C:\WINDOWS\SysWOW64\regedit.exe" /S "C:\Users\admin\AppData\Local\Temp.\DefOpen.reg" | C:\Windows\SysWOW64\regedit.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3836 | REGEDIT /S "C:\Users\admin\AppData\Local\Temp.\DefOpen.reg" | C:\Windows\SysWOW64\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3952 | REGEDIT /S "C:\Users\admin\AppData\Local\Temp.\DefOpen.reg" | C:\Windows\SysWOW64\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | "C:\WINDOWS\system32\regedit.exe" /S "C:\Users\admin\AppData\Local\Temp.\DefOpen.reg" | C:\Windows\SysWOW64\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | "C:\WINDOWS\system32\regedit.exe" /S "C:\Users\admin\AppData\Local\Temp.\DefOpen.reg" | C:\Windows\SysWOW64\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | devcon remove root\multikey | C:\Users\admin\AppData\Local\Temp\RarSFX0\devcon.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
890
Read events
880
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | Name |
Value: EPLAN P8 | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | Copyright |
Value: EPLAN | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | Created |
Value: 31082016 | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | DongleType |
Value: 2 | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | ID |
Value: | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | withMemory |
Value: 1 | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | Seed1 |
Value: 54722 | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | Seed2 |
Value: 24798 | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | Seed3 |
Value: 51105 | |||
| (PID) Process: | (5432) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\MultiKey\Dumps\00005189 |
| Operation: | write | Name: | HlkMemory |
Value: 00005755503055313030363600000000000000000000000000000000000000000000000000000000000000000000000045504C414E00536F6674776172650026005365727669636500476D6248002600436F2E004B470000000000000000000000000000000000000000000000000000000000000000000000000000000004A7 | |||
Executable files
3
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 624 | eplan 2.1-27 x64 crack.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\multikey.inf | binary | |
MD5:AB30AE08DECA636A3C45ACB810C6A26C | SHA256:6D8DBC670C860FC16329F16FB597F75838C3DFA4B60BC6E264C9D6DF6F3999CB | |||
| 624 | eplan 2.1-27 x64 crack.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\MultiKey.sys | executable | |
MD5:8894A680F52C01D00A8582C853651CB1 | SHA256:327E45098296D3B6871752C299527C0F61E0D00A2E002B301C41F4A9601D6D9E | |||
| 624 | eplan 2.1-27 x64 crack.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\install.cmd | text | |
MD5:6E2D3A124AE318AF5549128FB8533221 | SHA256:EDEE41204087754E9B82002232317AB1E63B58728E4B3F58BDA97DD9DCBAB8DE | |||
| 624 | eplan 2.1-27 x64 crack.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\devcon.exe | executable | |
MD5:F5F53991CD2F3159BD72682BE2077B1E | SHA256:75F087B047BF870C25FF26AE059E888355F11B3CEE72818CEDC02586316B73BA | |||
| 624 | eplan 2.1-27 x64 crack.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\SN10066.exe | executable | |
MD5:D5ED909E37F053CE7C8EA758F2563393 | SHA256:62825D36DE805E349852FF126AB683E01C41253DAD4243F5E8A0FC2E63AECD00 | |||
| 624 | eplan 2.1-27 x64 crack.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\multikey.cat | text | |
MD5:DCE732477F7970A39A0FF4327A77460F | SHA256:9C91349644C245CEFF90DA6FD23EF1ACCBCF79E1CF3E9F0F2D10B2301E8E85E3 | |||
| 188 | cmd.exe | C:\Users\admin\AppData\Local\Temp\DefOpen.reg | text | |
MD5:C756B8EAC93DE58D57105A6C35ADB50F | SHA256:853448E59C9BB7599FA8A5FF03A0B608781A02D41F58576F1192E0C48CB8D635 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
520 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
640 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.170:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |