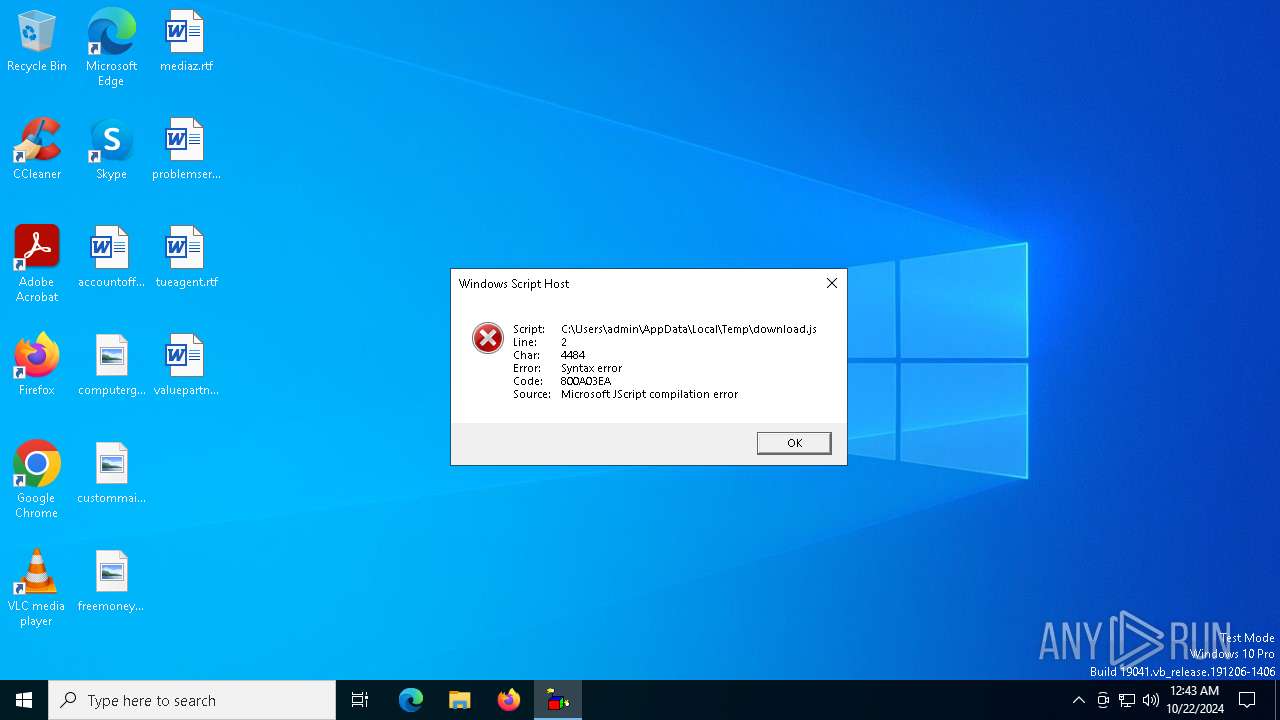
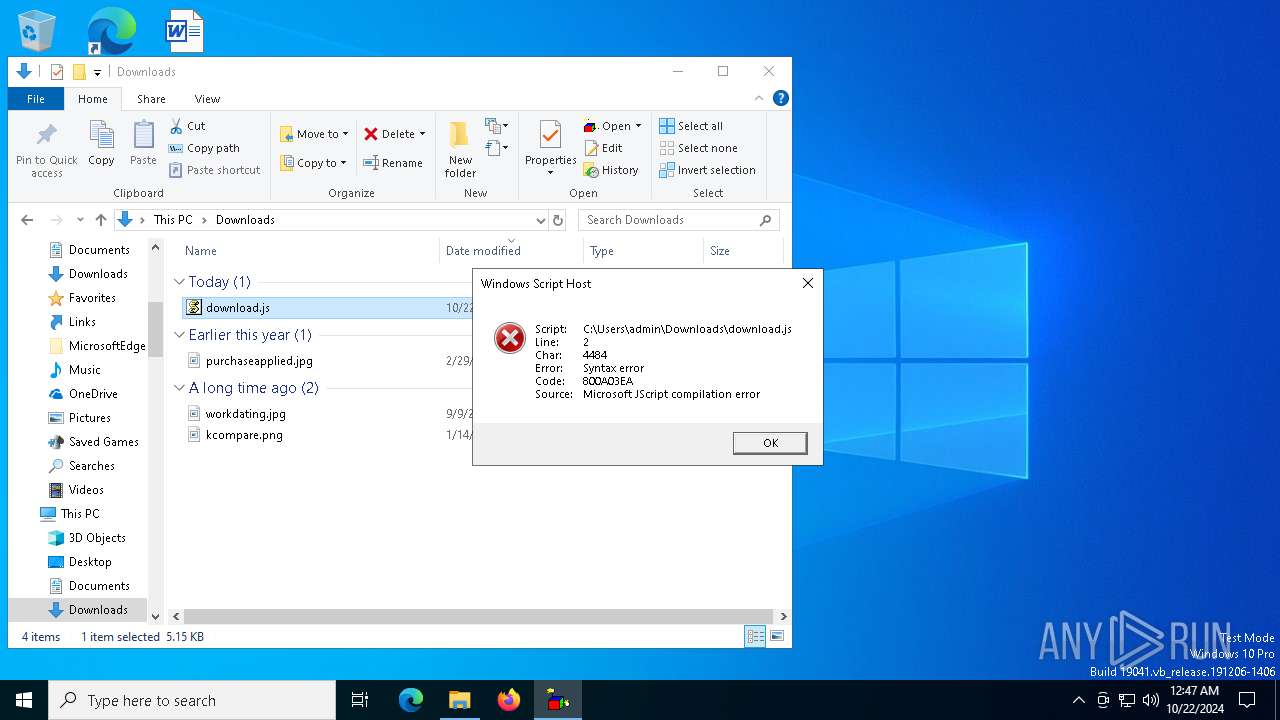
| File name: | download.js |
| Full analysis: | https://app.any.run/tasks/8cd304c3-9d59-4c54-82d7-aa06e78f8822 |
| Verdict: | Malicious activity |
| Analysis date: | October 22, 2024, 00:43:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (5264) |
| MD5: | 25967016EFBA03E749A06852D86C880B |
| SHA1: | E3CDD352BC8308545A4E94DBBCE1FA83E11558B4 |
| SHA256: | 328646CC250E95C0C0411FC975DBD96A8076632216E17F0B9C64CC46C2D2598E |
| SSDEEP: | 96:04meNpR6s5QKtmmA1hgBJ6CXck/nVsDUpMpwitDdvvMUVtQpUGWJUhSSk:04meQIEjgBVXck/naDUpSwyDBFbUsSk |
MALICIOUS
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 5276)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 5276)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 5276)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 5276)
SUSPICIOUS
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 5276)
INFO
Checks proxy server information
- wscript.exe (PID: 5276)
Manual execution by a user
- wscript.exe (PID: 6212)
- wscript.exe (PID: 4380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
132
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\download.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5276 | "C:\Windows\System32\WScript.exe" C:\Users\admin\AppData\Local\Temp\download.js | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6212 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\download.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
2 494
Read events
2 484
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5276) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5276) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5276) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5276) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 8804090000000000 | |||
| (PID) Process: | (4380) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4380) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4380) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6212) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6212) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6212) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
3
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5276 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | der | |
MD5:95E370CE8A91E7A448383A34D7BB1398 | SHA256:2E6435E6D78CFABE0DCAF55C96FAF45B7641F2B6CB66337C01AC64F57DD731E4 | |||
| 5276 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | der | |
MD5:57F146970A710F91461395ACC07C4D51 | SHA256:C33DAAE8FED8A3EC619E7AFC8C84982FB2D49F0933426993A7621CC44421AA80 | |||
| 5276 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6717D6332C59EB8BDD5771C5A184159B | binary | |
MD5:8577D61C334BC5D66B930B15EE4625A9 | SHA256:DC9ED03A399BDF5F9033FE57D26BC61990751F013C6F841EA2A4B2615023CDEB | |||
| 5276 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6717D6332C59EB8BDD5771C5A184159B | der | |
MD5:D2DC521D4F5E35DB4D1584A9B520356B | SHA256:412791A3326F6083EAA5B51F1A1A5042DF084B2209A59937BC77F8E35D789039 | |||
| 5276 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:F6ABA814B310F5765DFDF93B643349E6 | SHA256:E2D6A9EA128BBE3F0AEF1FFBAE8CDA0ABEA4F880CBD7B3FBC6EDC6CF3D92EA77 | |||
| 5276 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:9AB181986CEBFE3BCE55AC3D08E0E0B0 | SHA256:84B670CBE29EA55F7F33B5429302CB46162C05D1F2007797CAF10686E32C8725 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
59
DNS requests
23
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5276 | wscript.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5276 | wscript.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCECO3bePBuysaUZYeCOq3ZOg%3D | unknown | — | — | whitelisted |
5276 | wscript.exe | GET | 200 | 104.18.38.233:80 | http://zerossl.ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQzH%2F4%2F%2FQuEFihPlI1WwH4Dktj2TQQUD2vmS845R672fpAeefAwkZLIX6MCEQDkjJZvqTG%2FzqC54nm5%2BNBf | unknown | — | — | whitelisted |
944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
696 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
696 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5068 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7060 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5276 | wscript.exe | 88.119.175.247:443 | cuevz.house.zionanakwenze.com | Informacines sistemos ir technologijos, UAB | US | malicious |
5276 | wscript.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cuevz.house.zionanakwenze.com |
| unknown |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
zerossl.ocsp.sectigo.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5276 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
4380 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
6212 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |