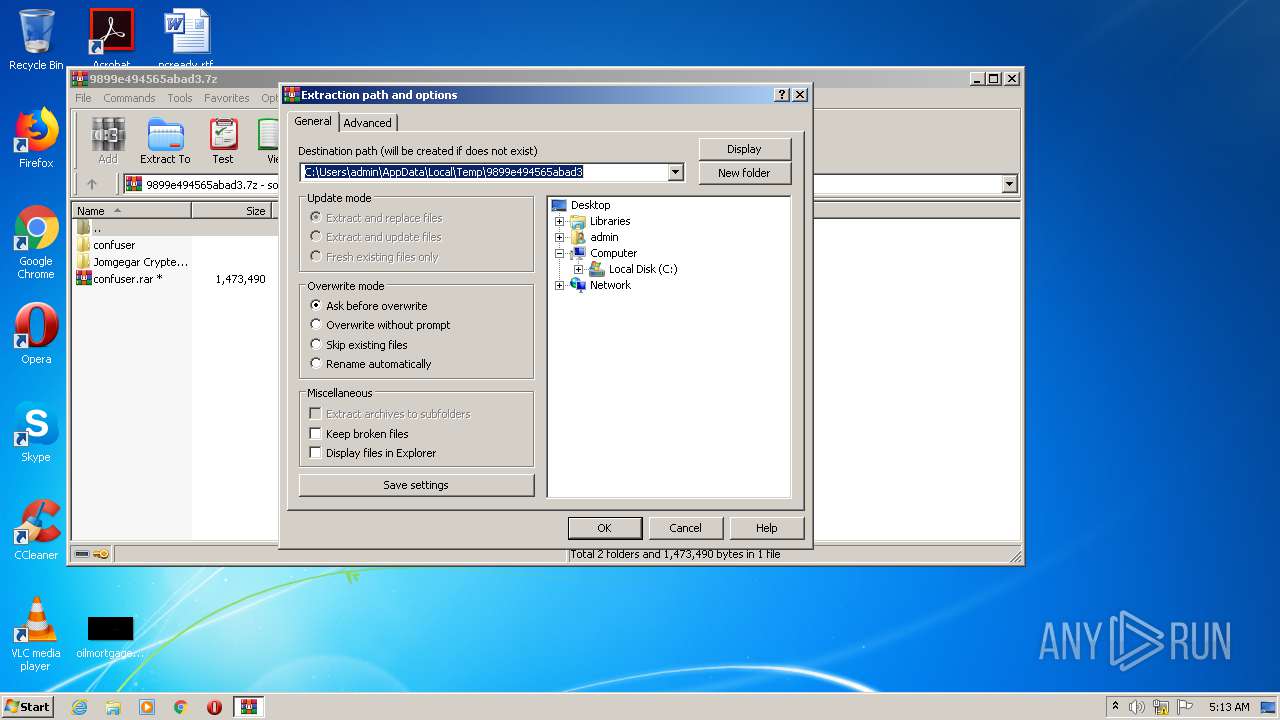
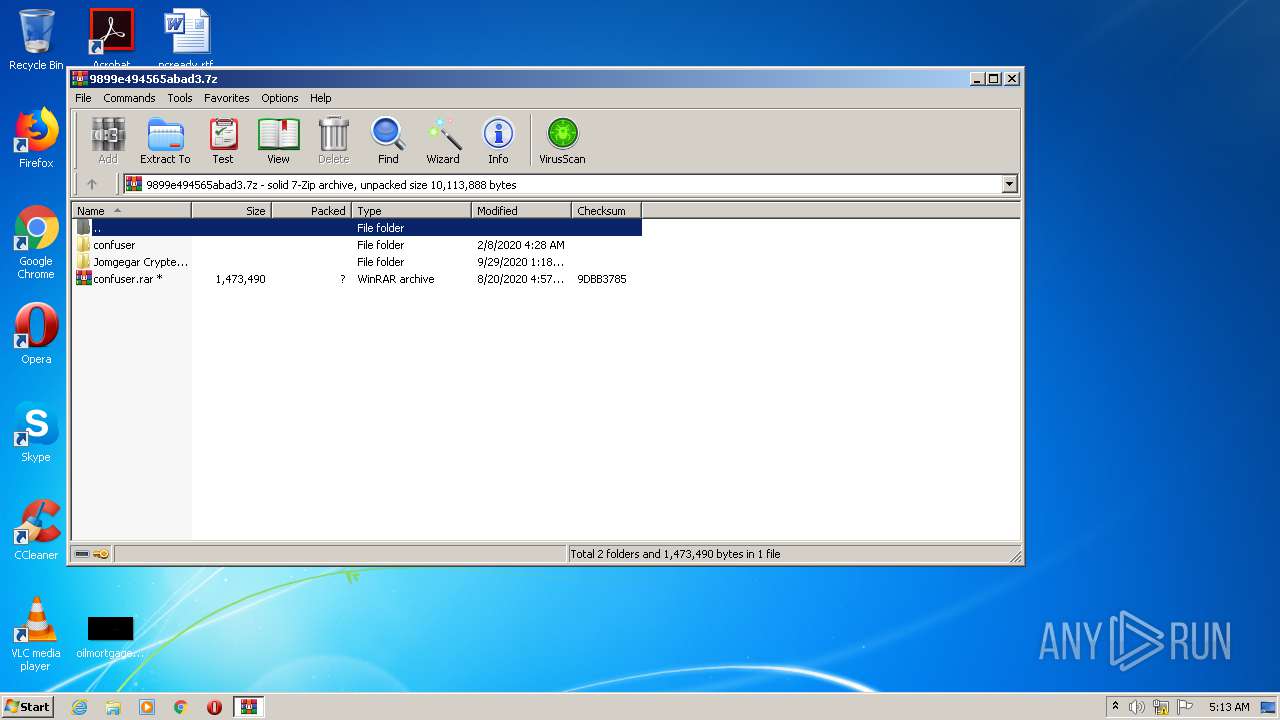
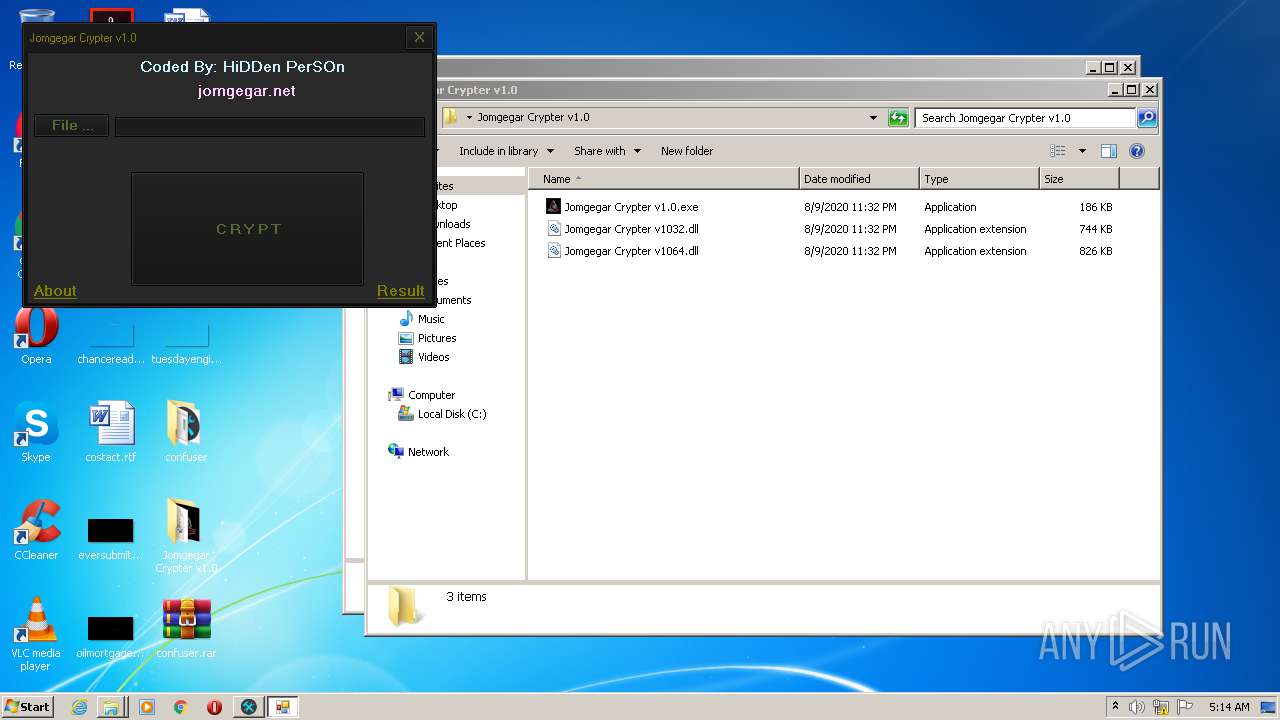
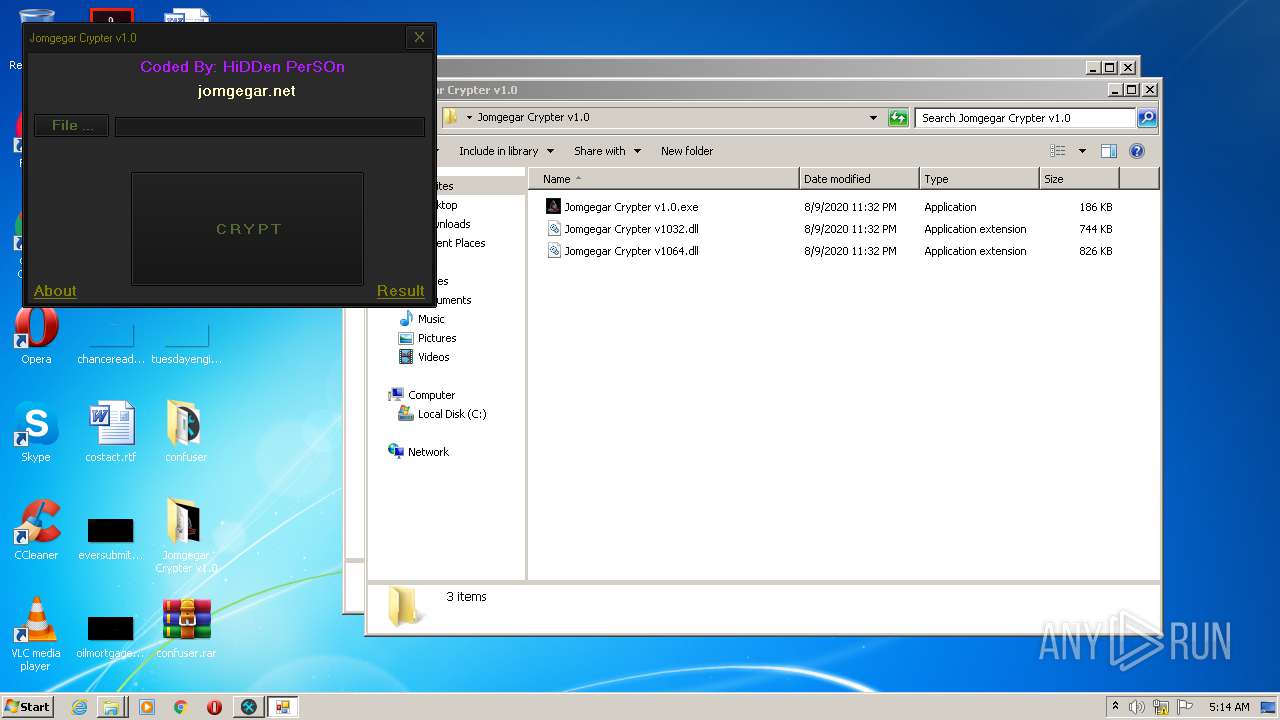
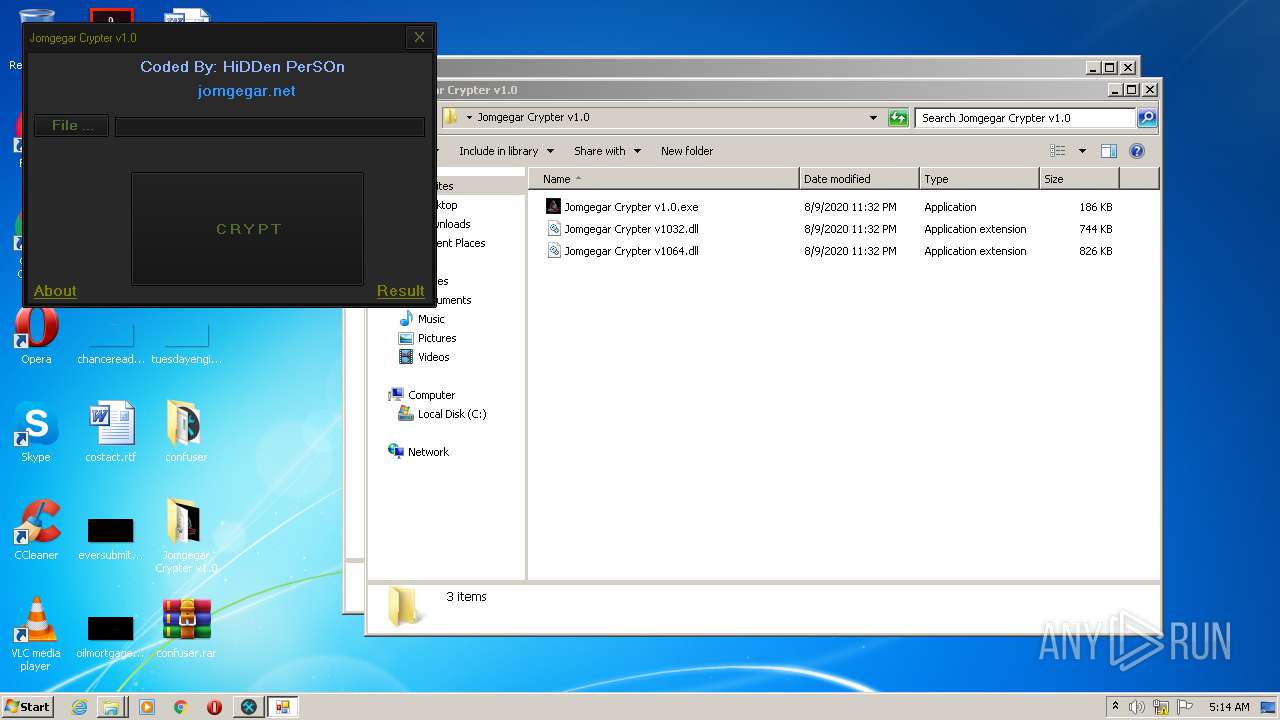
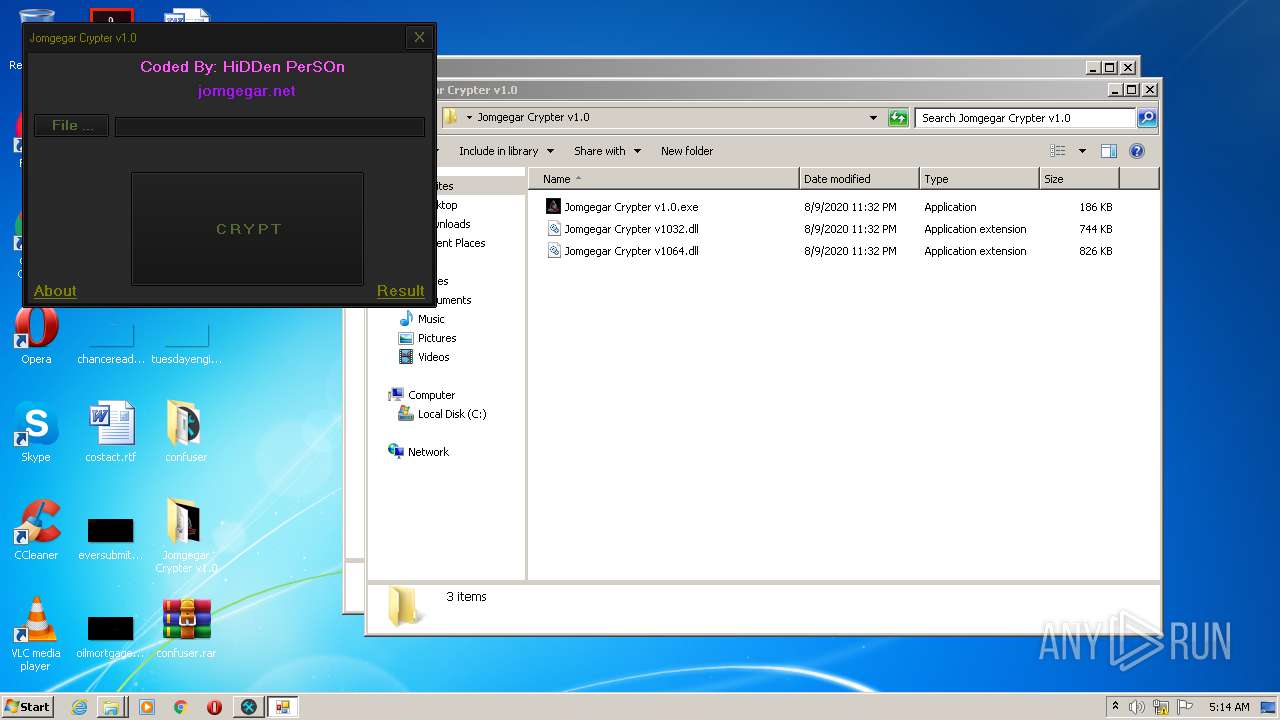
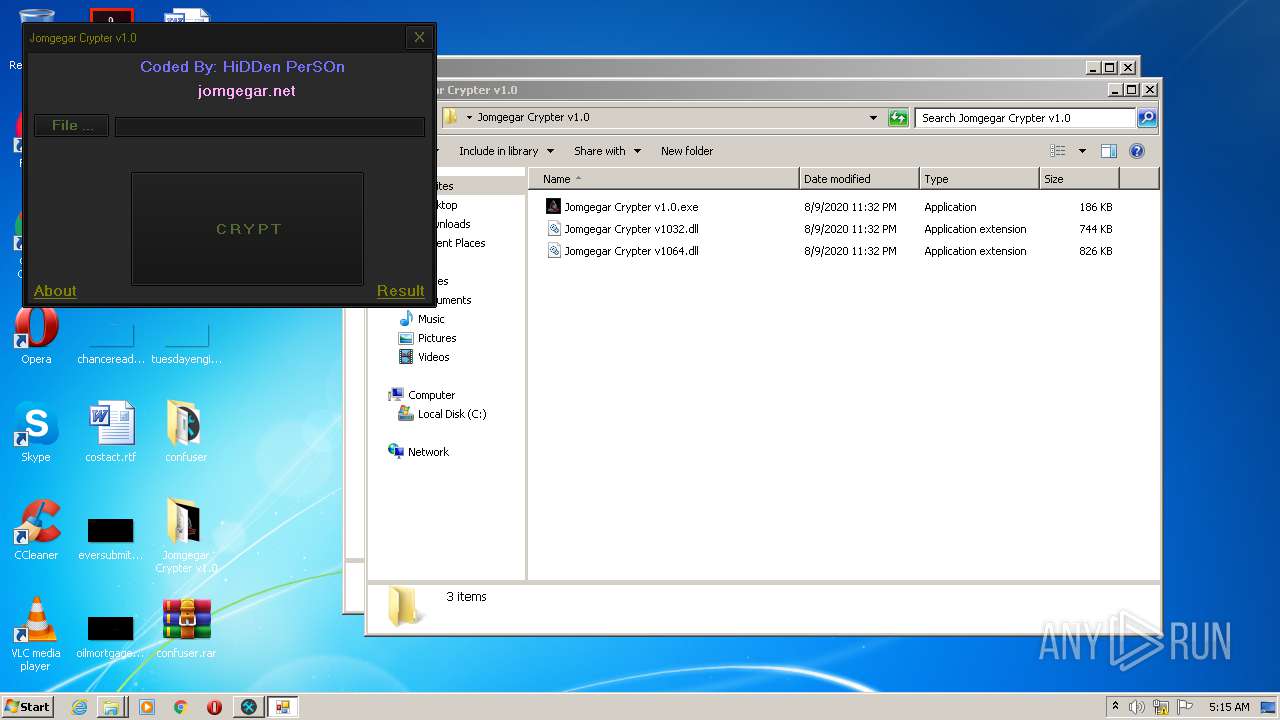
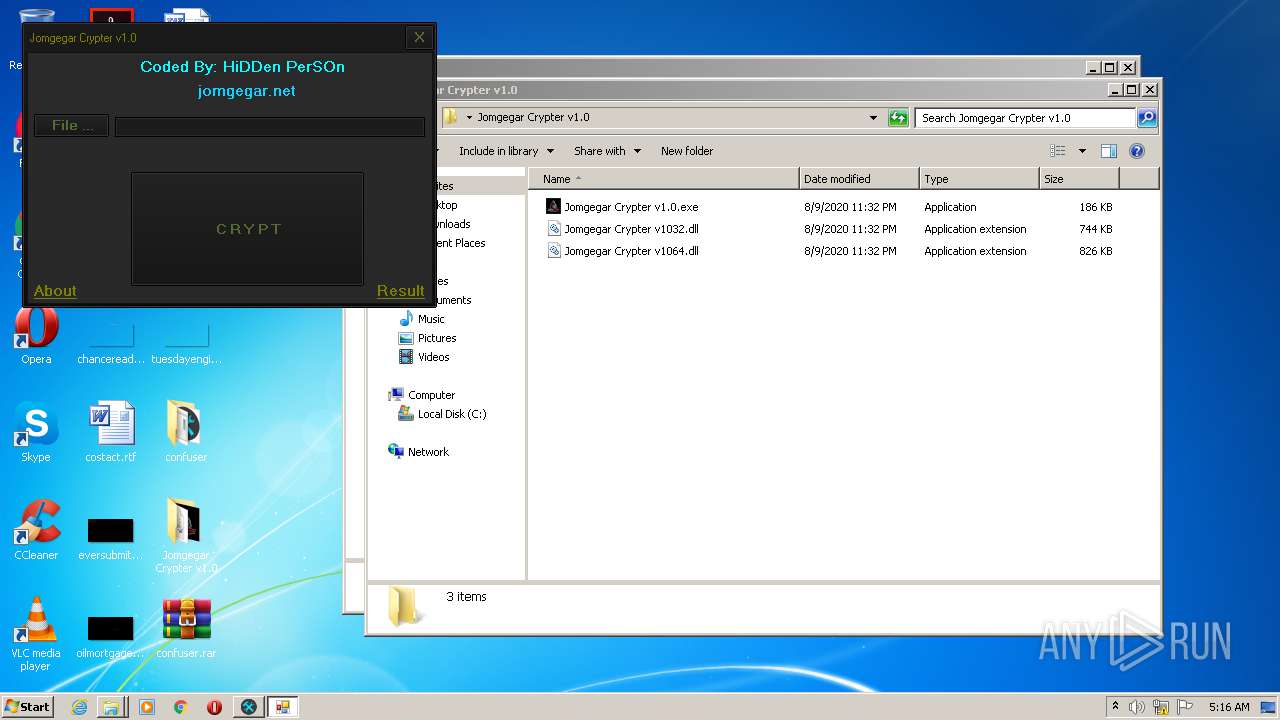
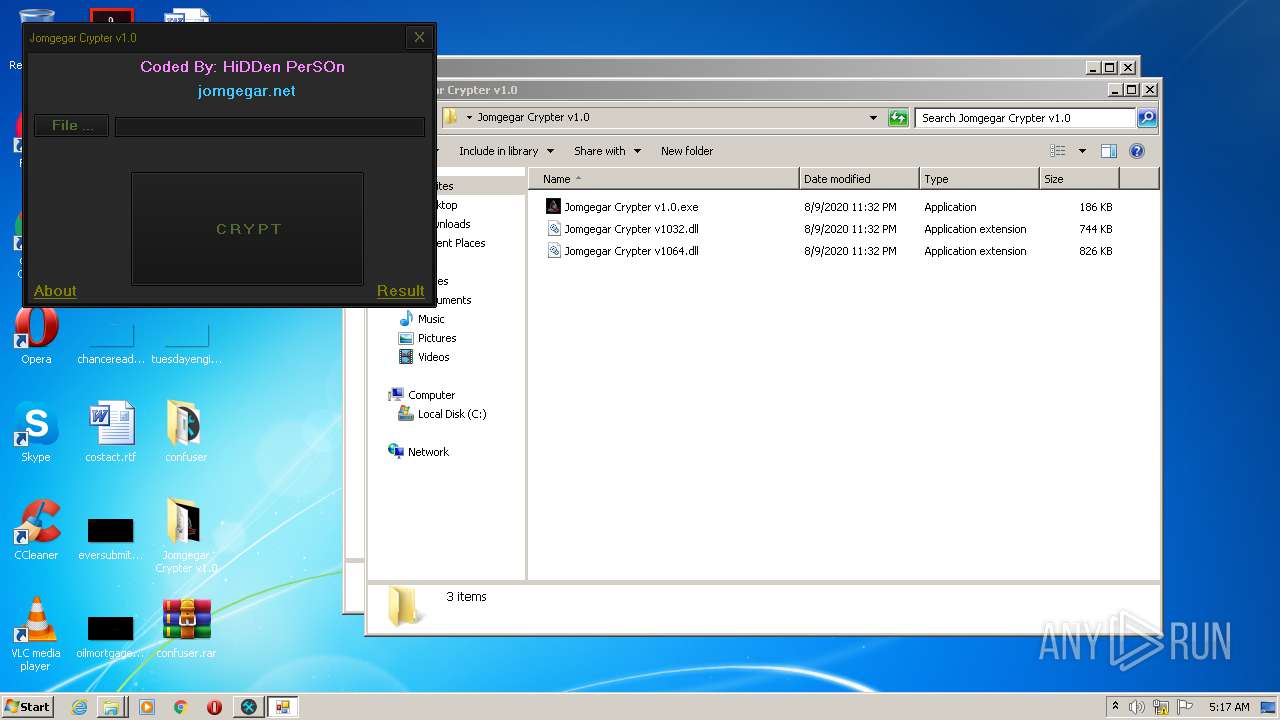
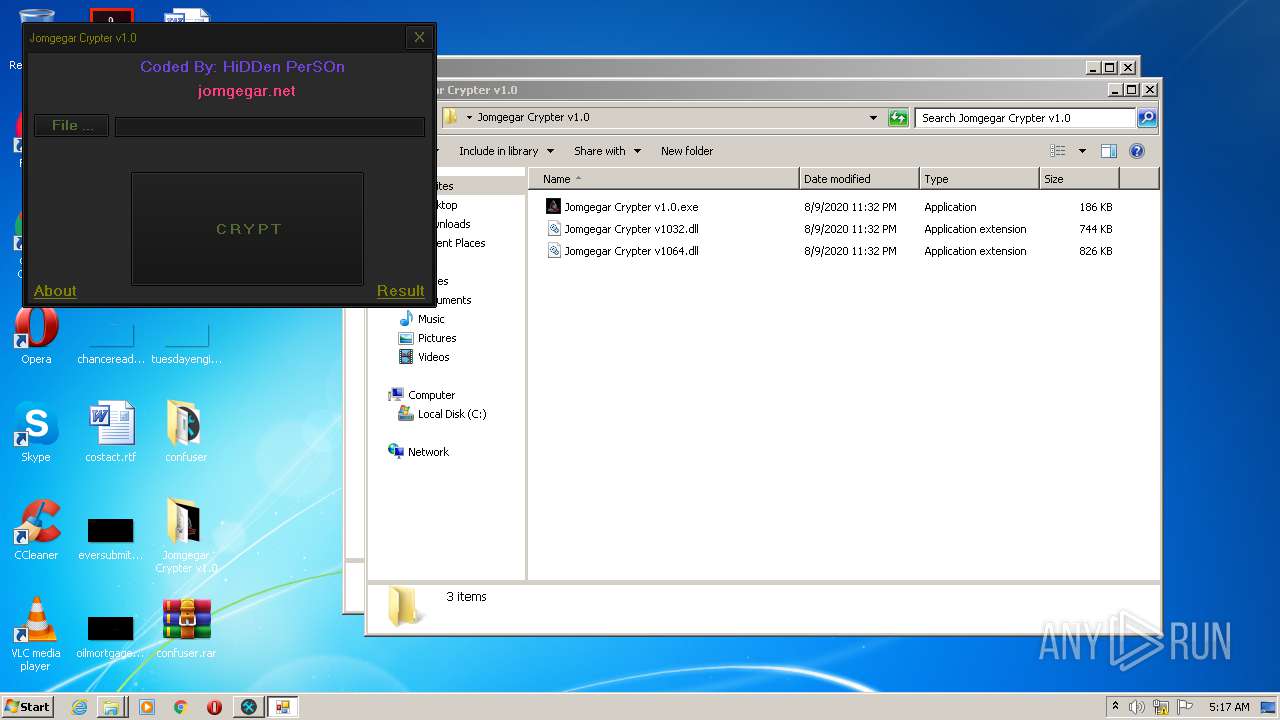
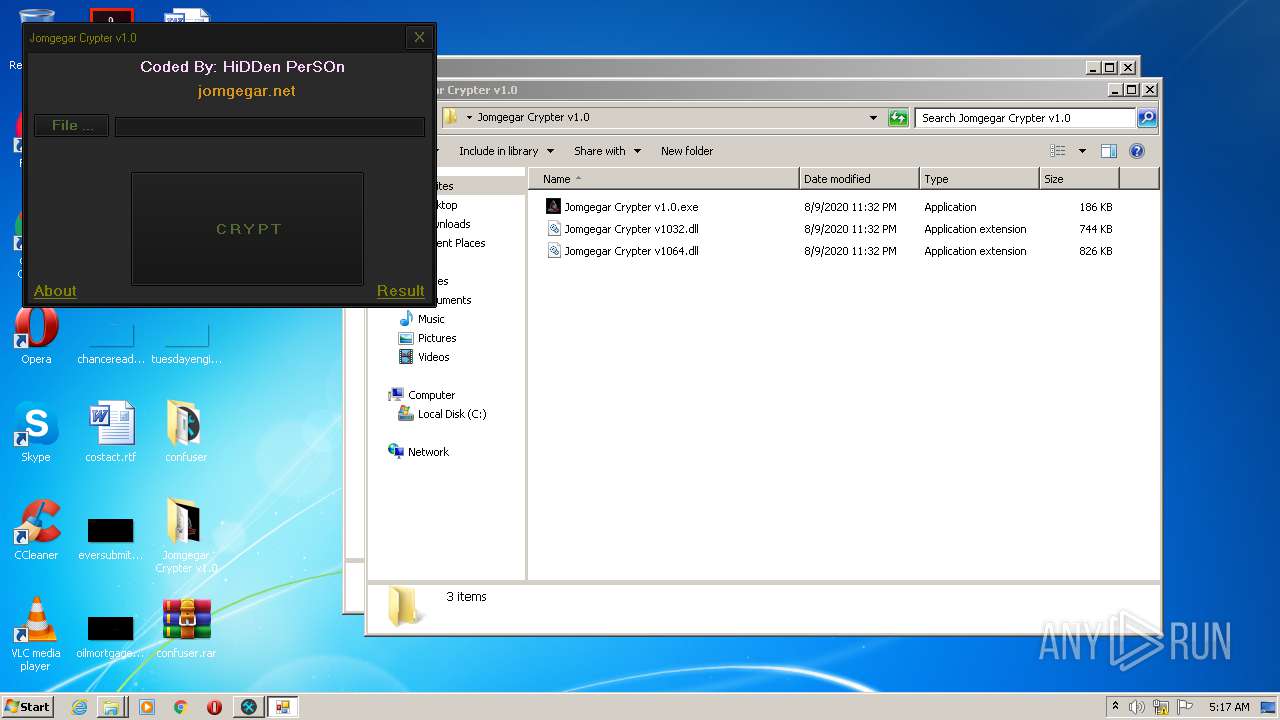
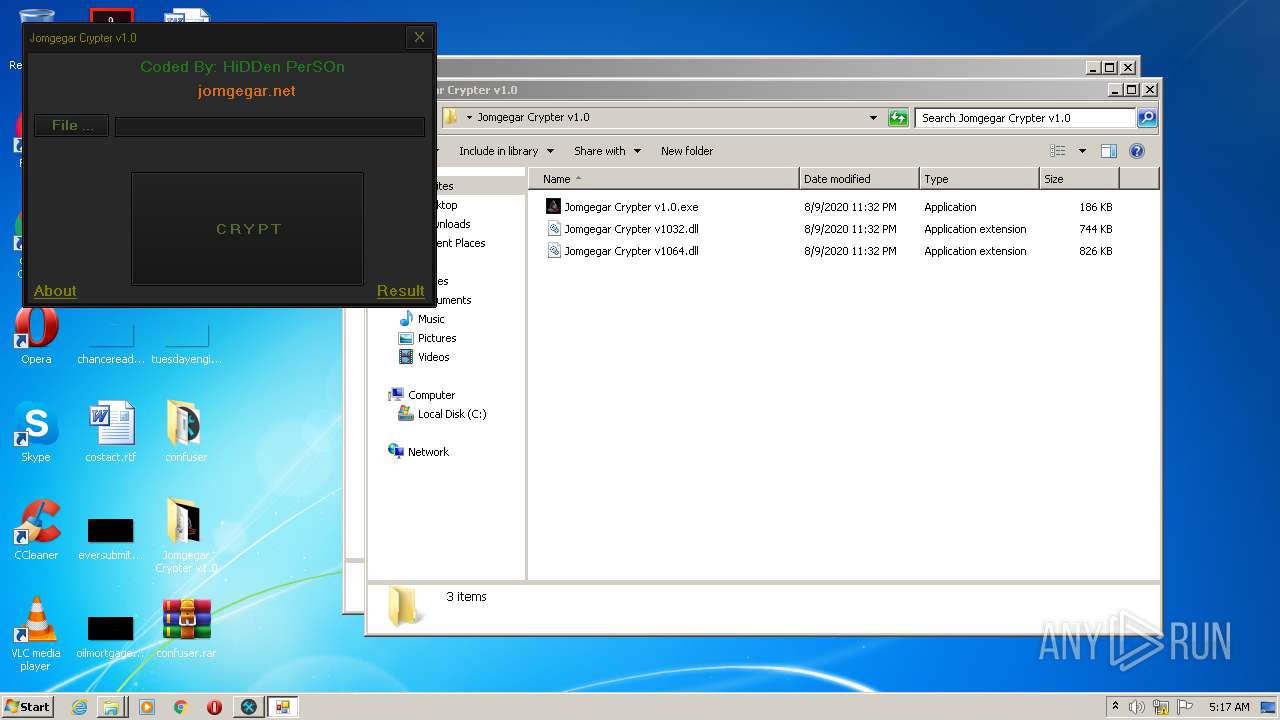
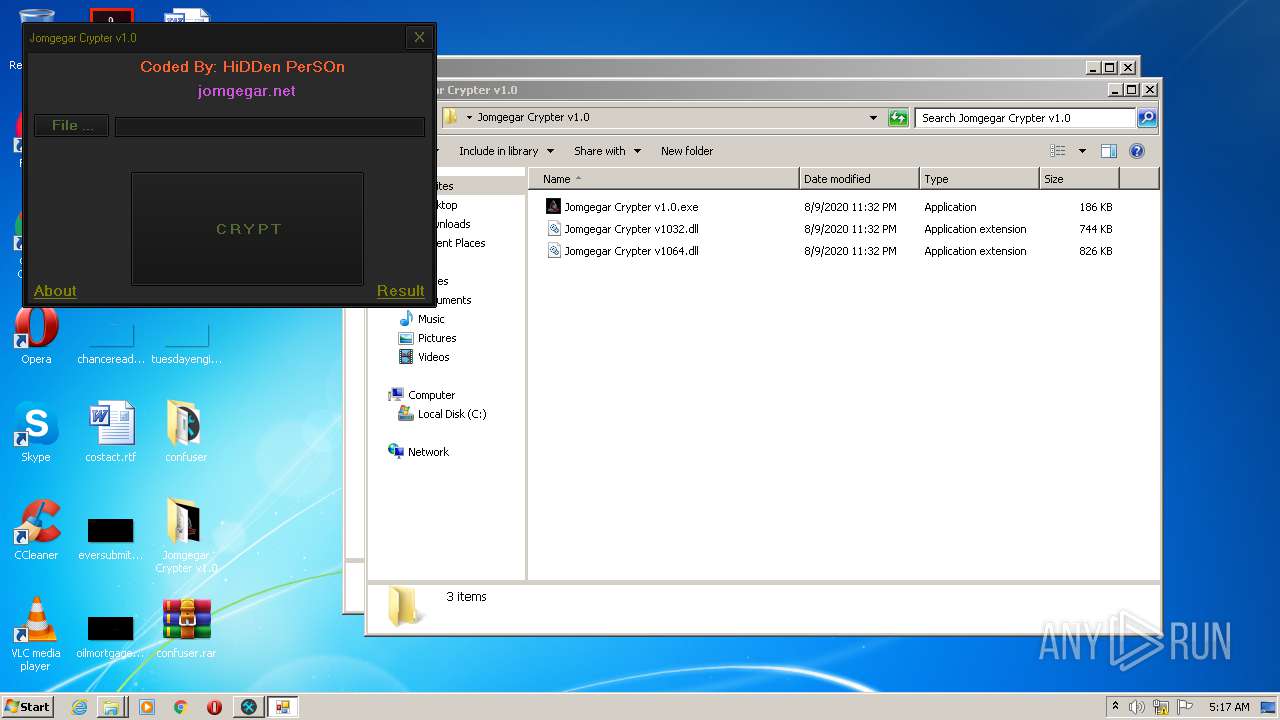
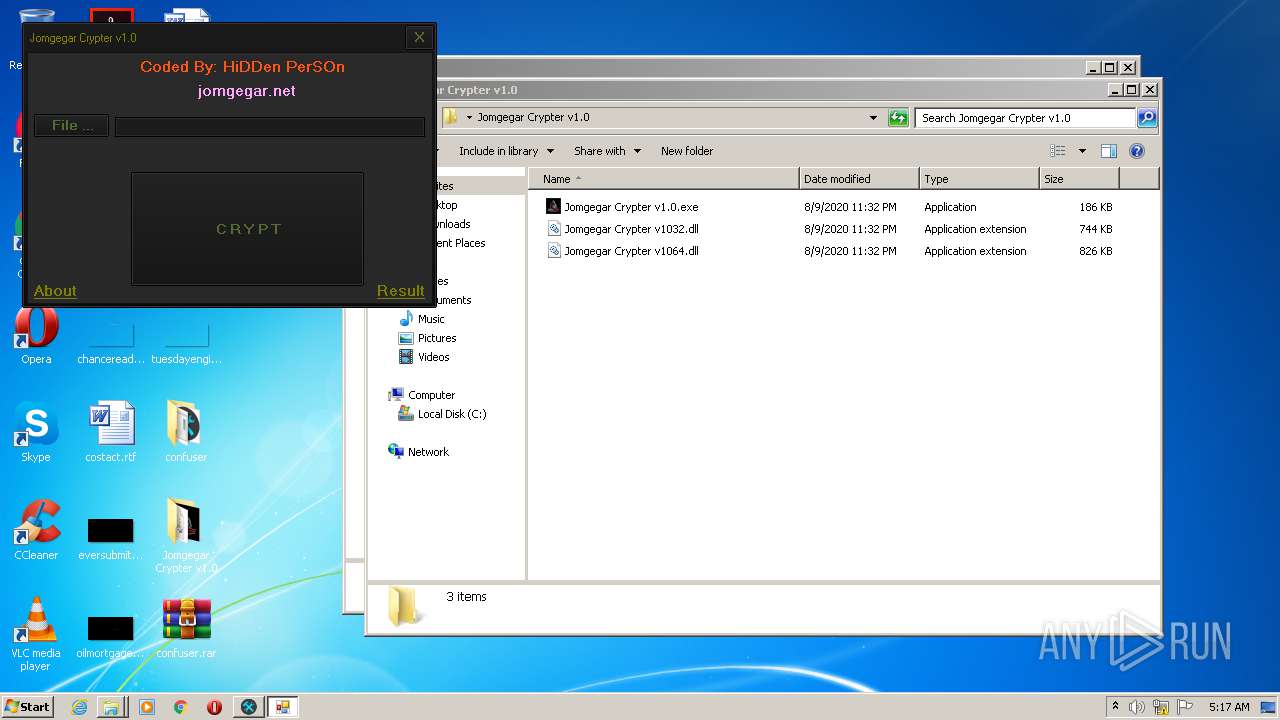
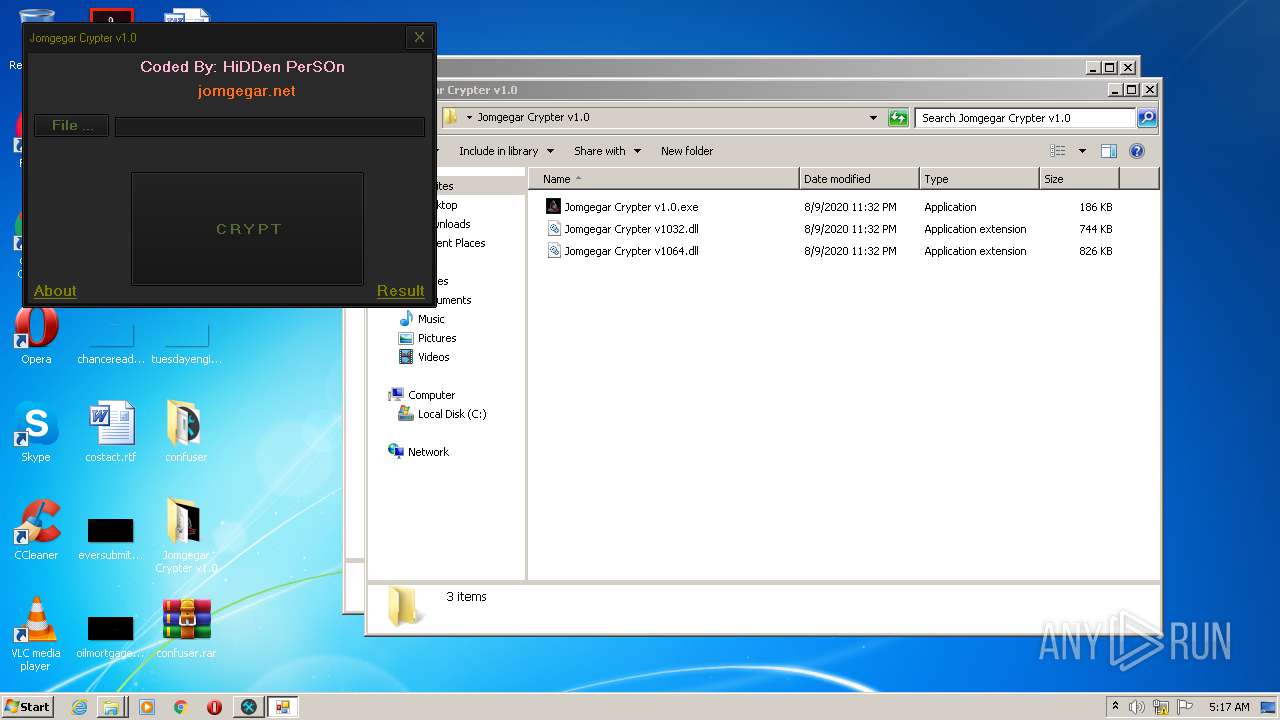
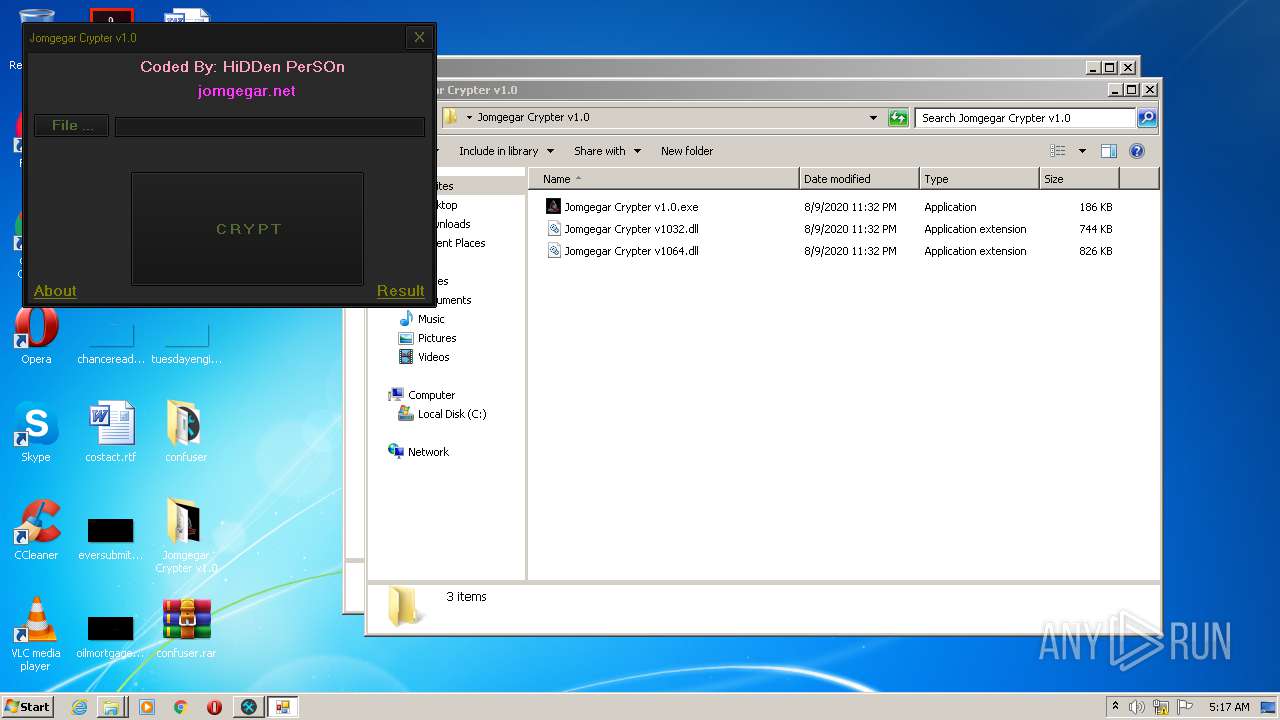
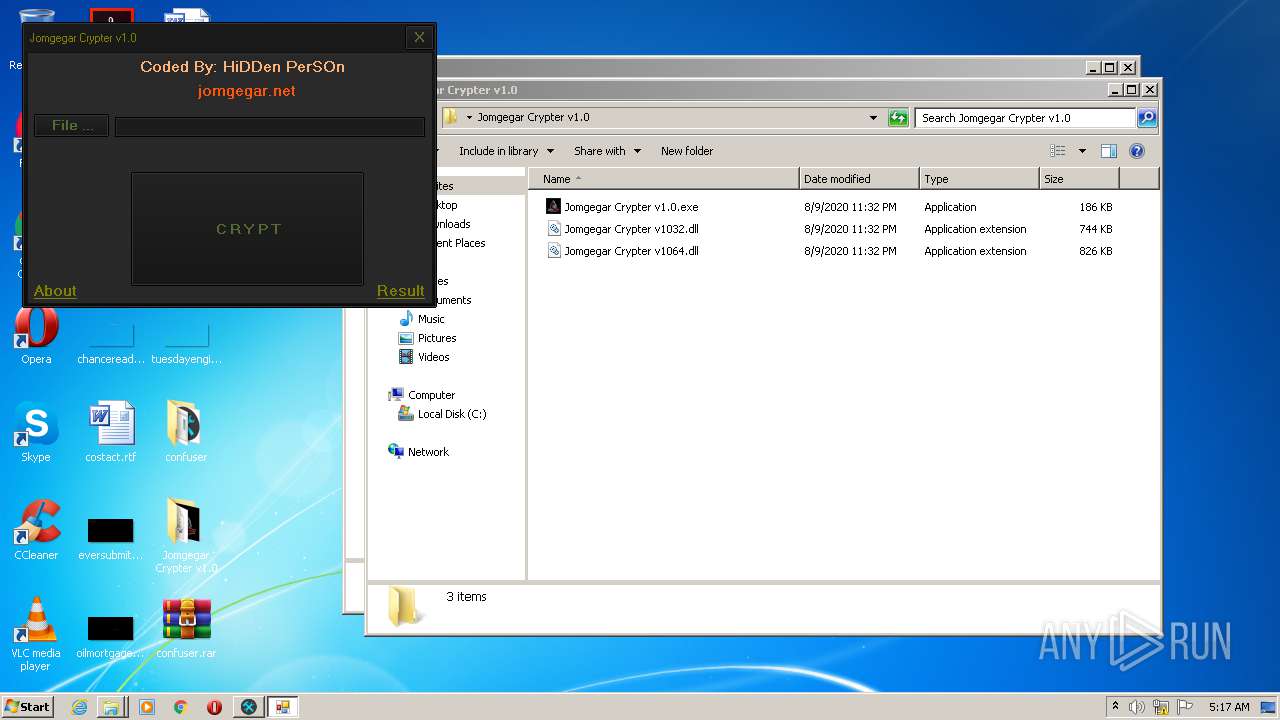
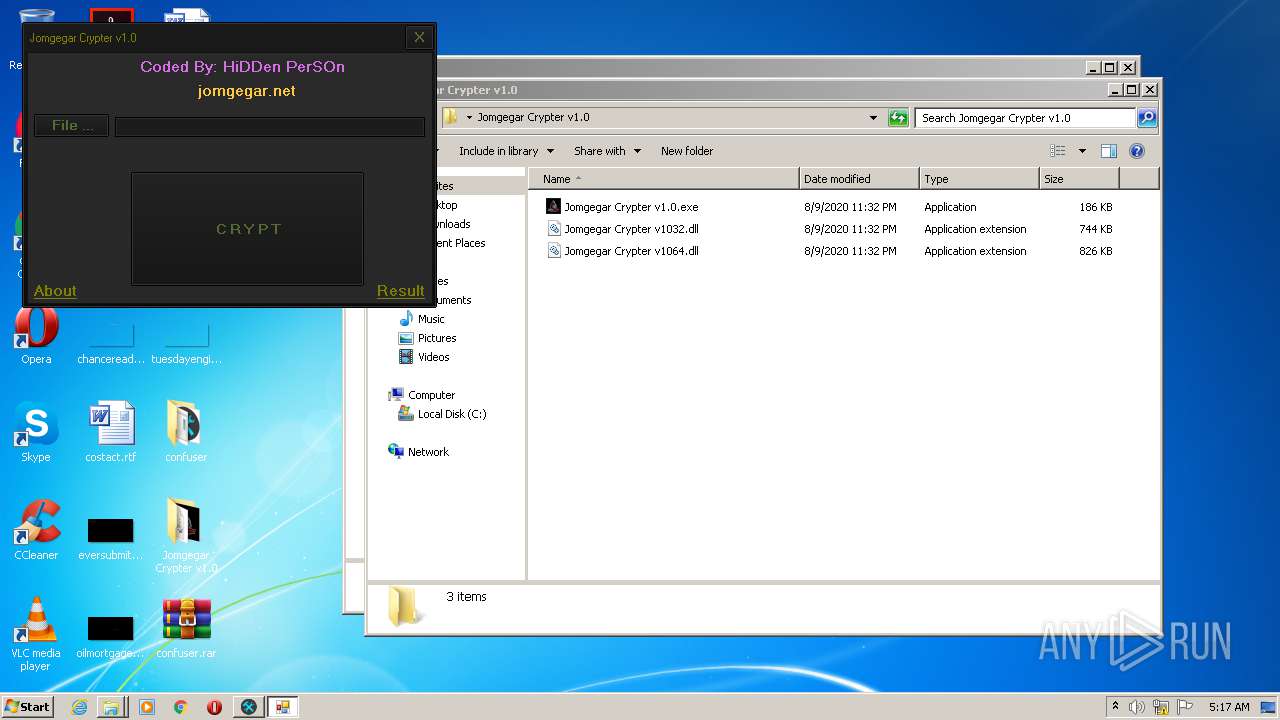
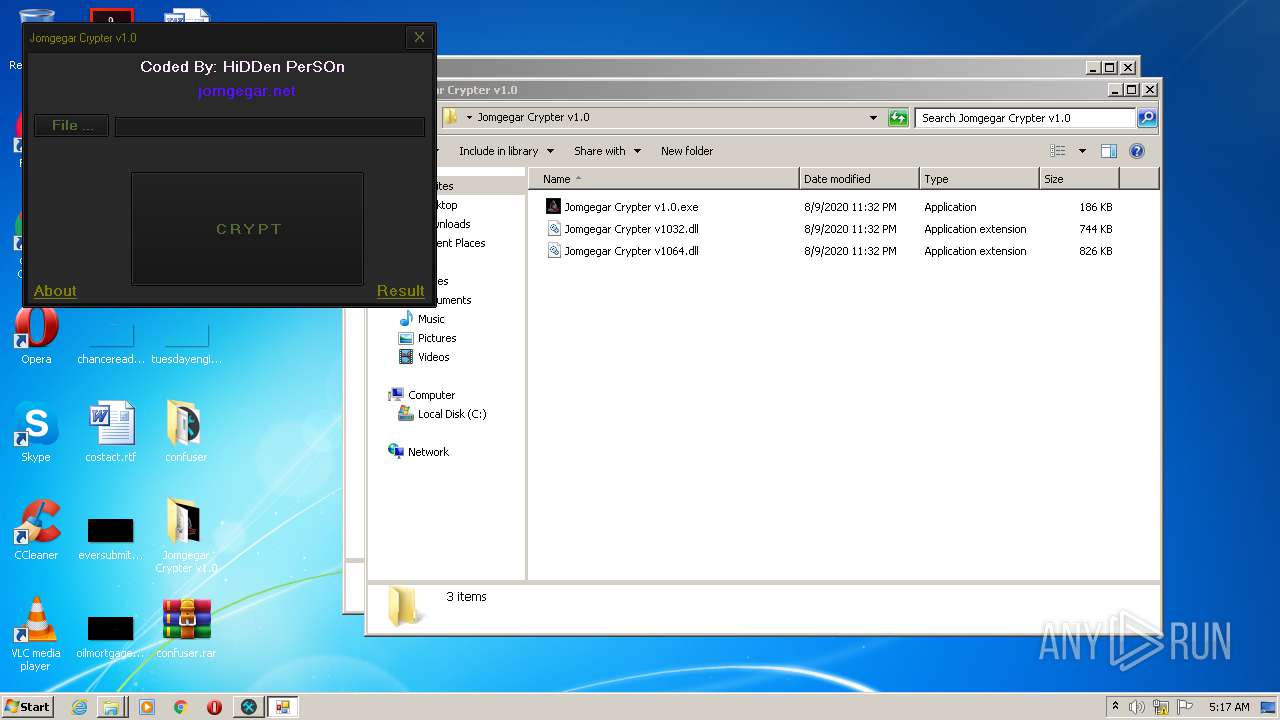
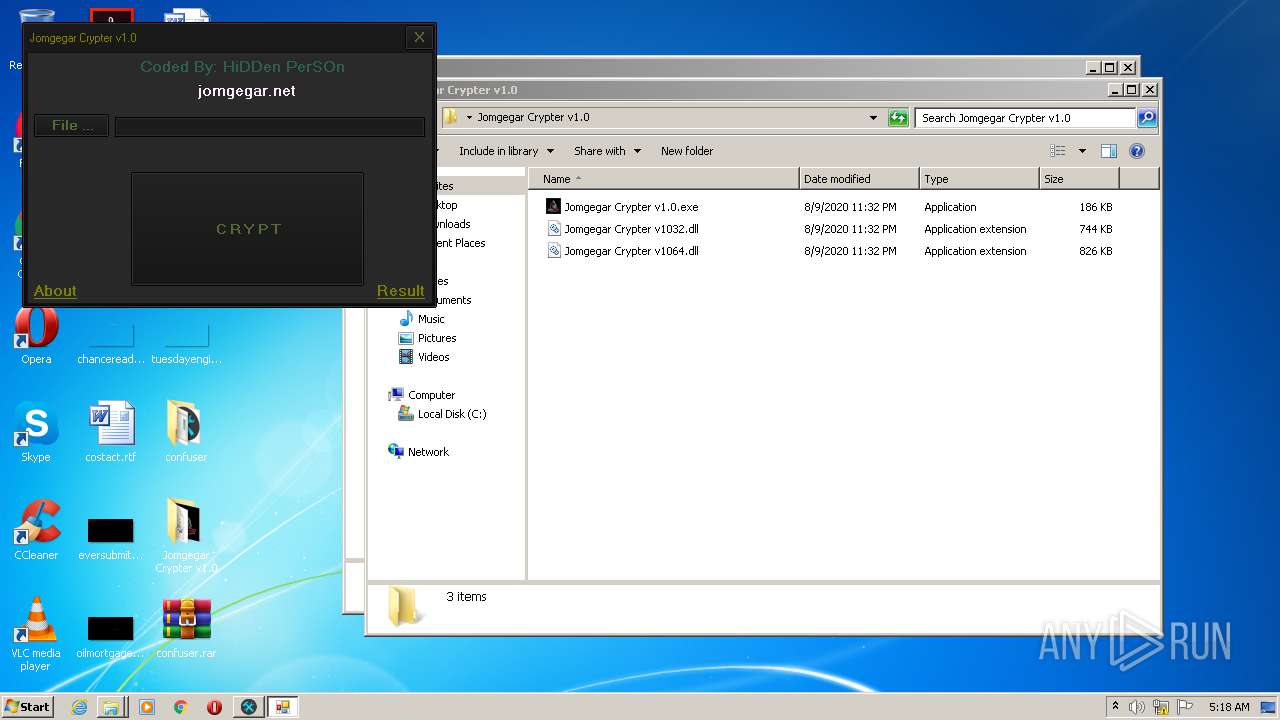
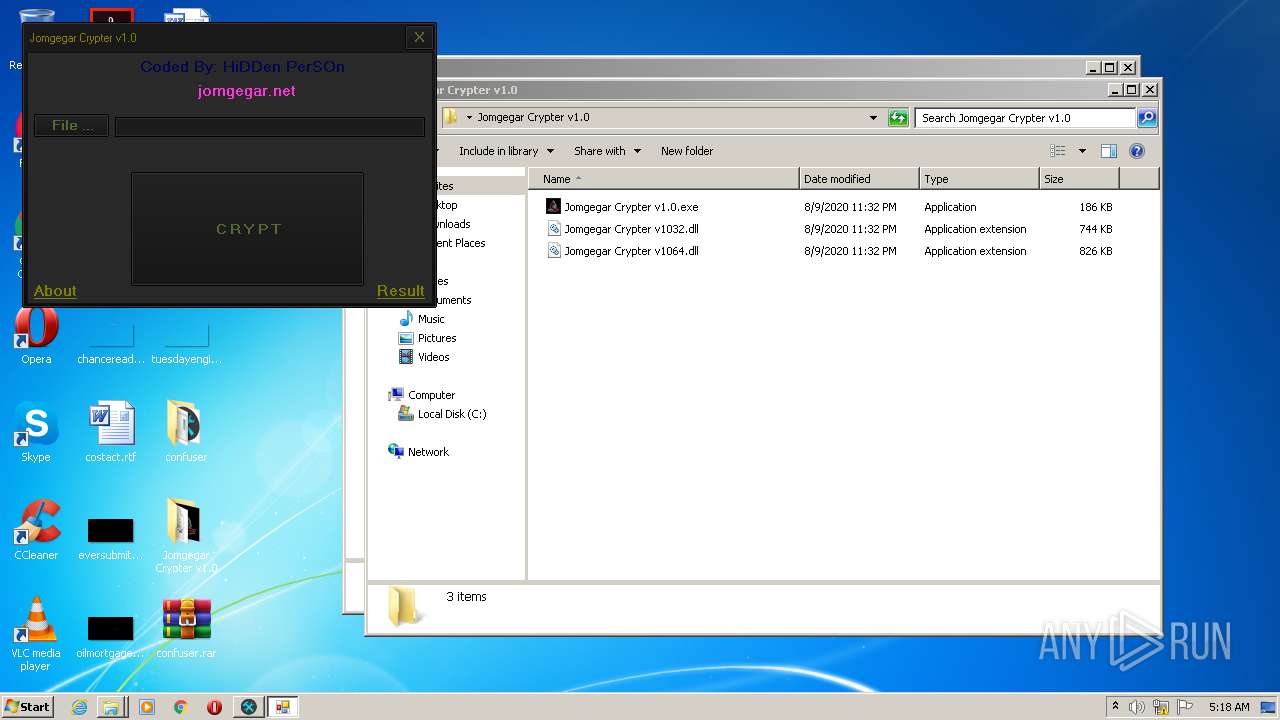
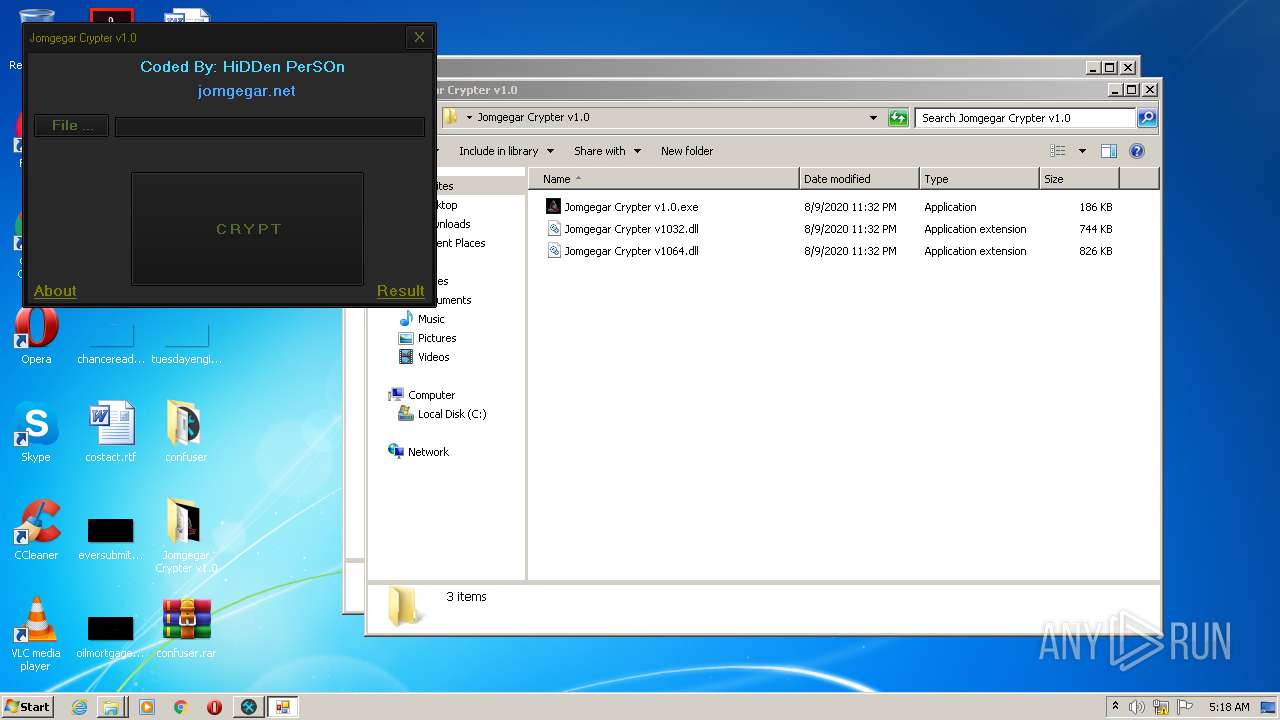
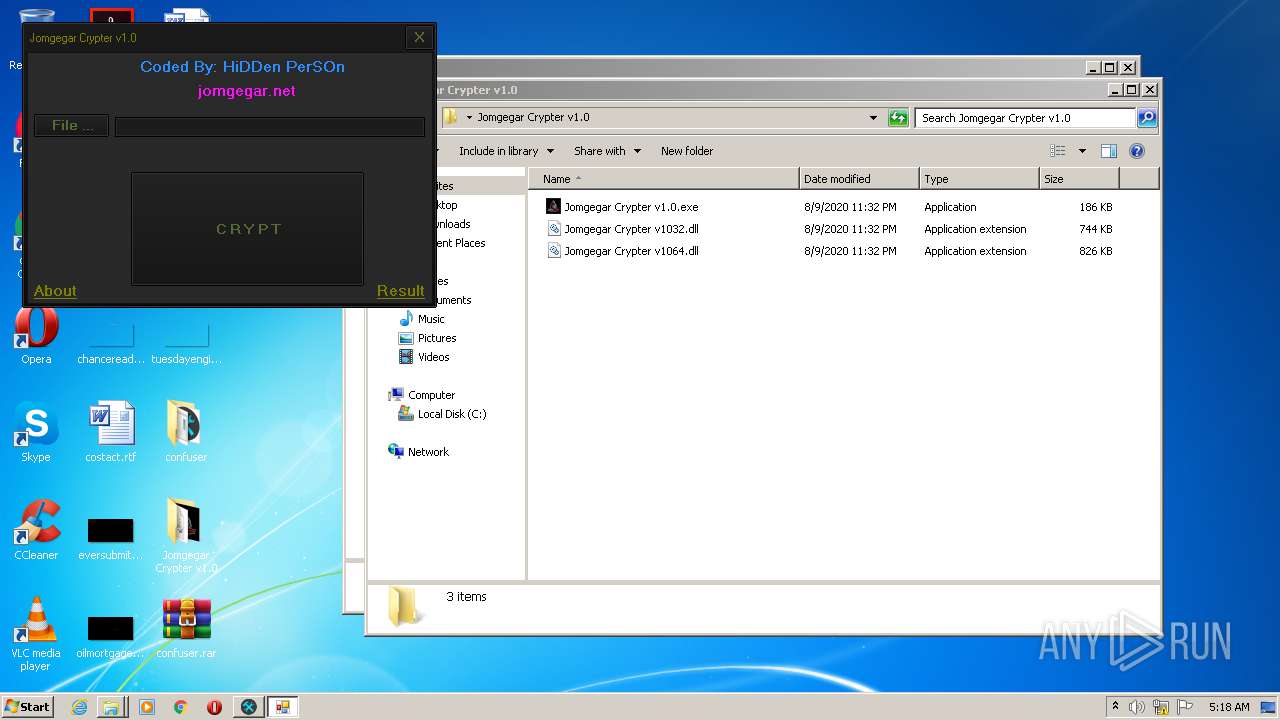
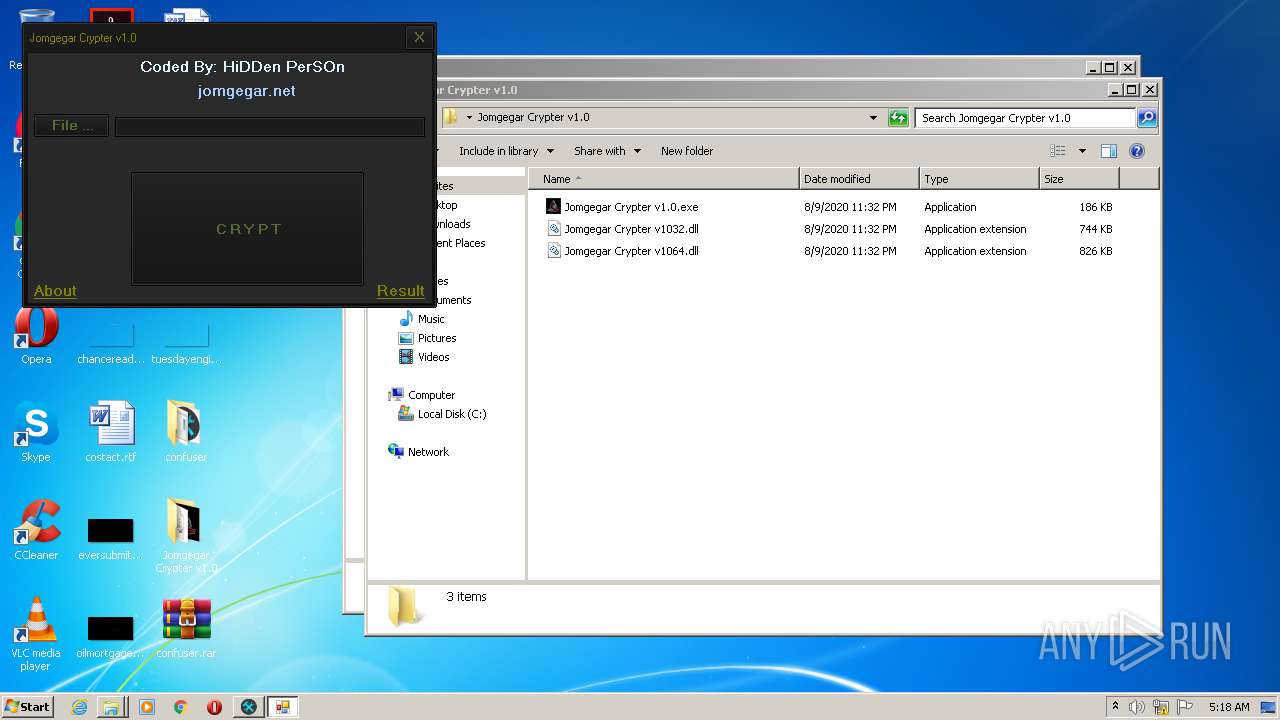
| File name: | 9899e494565abad3.7z |
| Full analysis: | https://app.any.run/tasks/aeaae955-aa43-4511-8484-d9251cac3f89 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 04:13:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.3 |
| MD5: | 0CC5533200EBF2C1BB0A583E1497D884 |
| SHA1: | 84AF63F7A30D7BA3DB0C83742979160A13328C9D |
| SHA256: | 325FDBEBEFECBAE4E3A0B2FCE93BA028F226FFA1833F08B787F2105B48B43A69 |
| SSDEEP: | 49152:PDDE0mIk92qUu7j29VyGp5nXWSfJIIoF9PEyvRUILOV5z/A/gzOaaNEtlHMzftwn:S6vyOVVKFzvZCV+/gOaYEXuf92 |
MALICIOUS
Application was dropped or rewritten from another process
- ConfuserEx.exe (PID: 812)
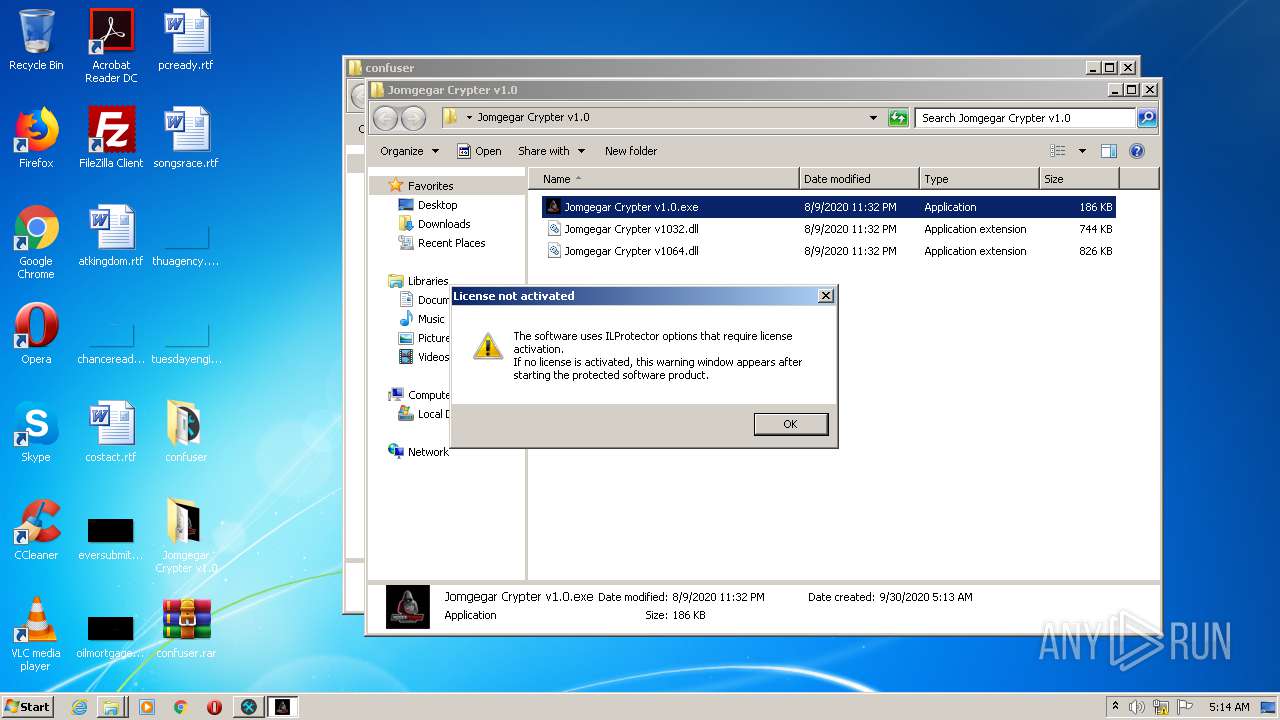
- Jomgegar Crypter v1.0.exe (PID: 3276)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3880)
- Jomgegar Crypter v1.0.exe (PID: 3276)
- ConfuserEx.exe (PID: 812)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2744)
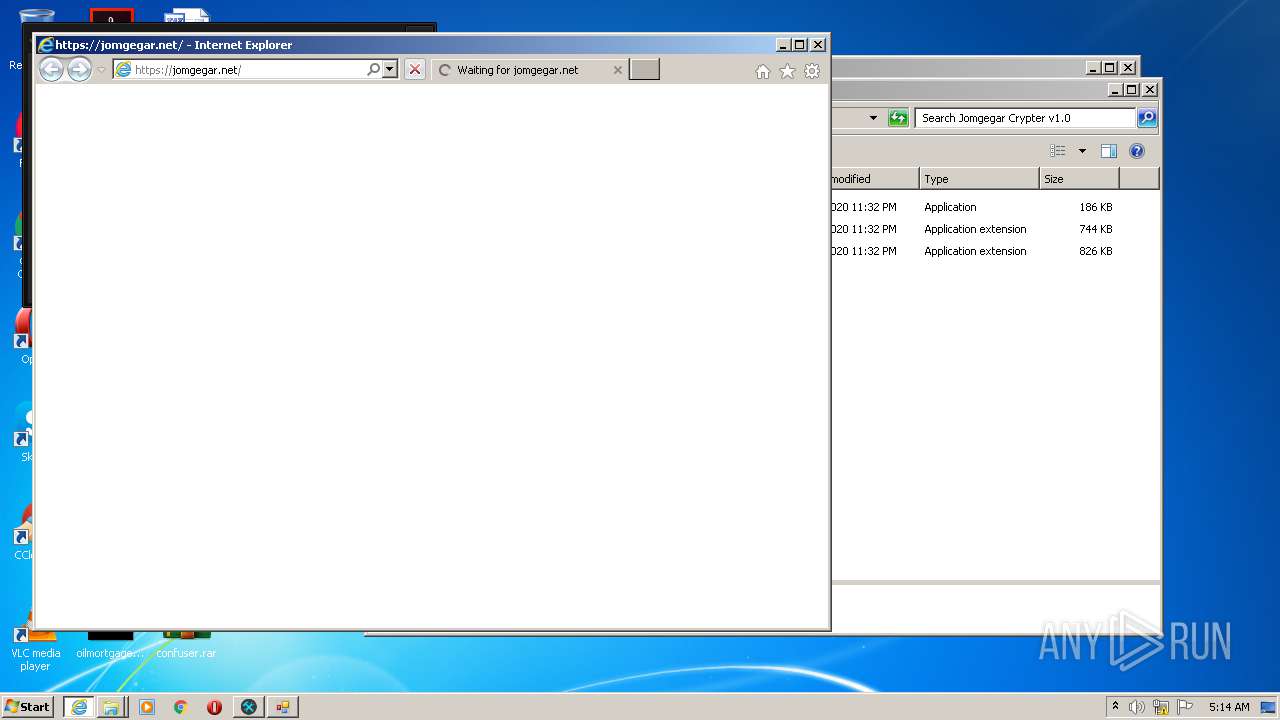
Starts Internet Explorer
- Jomgegar Crypter v1.0.exe (PID: 3276)
INFO
Application launched itself
- iexplore.exe (PID: 2132)
Reads Internet Cache Settings
- iexplore.exe (PID: 2132)
- iexplore.exe (PID: 936)
Reads settings of System Certificates
- iexplore.exe (PID: 936)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 936)
Changes internet zones settings
- iexplore.exe (PID: 2132)
Reads internet explorer settings
- iexplore.exe (PID: 936)
Manual execution by user
- ConfuserEx.exe (PID: 812)
- Jomgegar Crypter v1.0.exe (PID: 3276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (gen) (100) |
|---|
Total processes
39
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
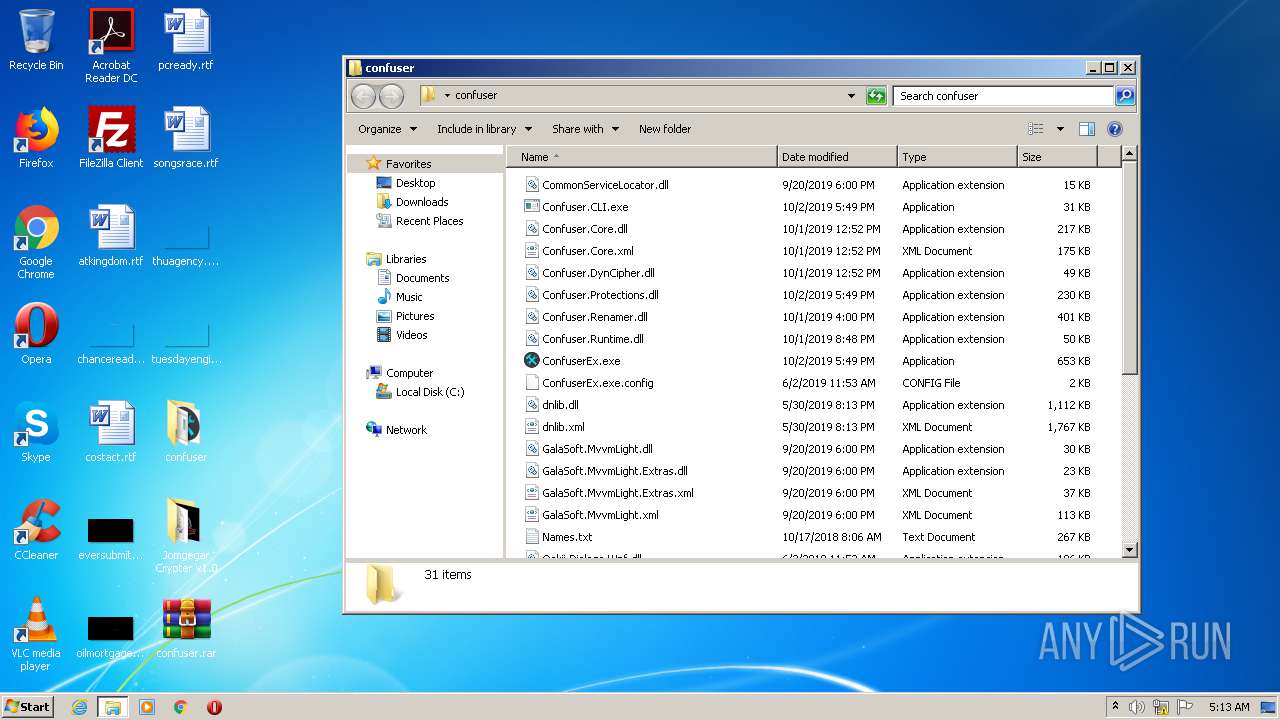
| 812 | "C:\Users\admin\Desktop\confuser\ConfuserEx.exe" | C:\Users\admin\Desktop\confuser\ConfuserEx.exe | — | explorer.exe | |||||||||||
User: admin Company: Wadu Integrity Level: MEDIUM Description: 198 Protector V2 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 936 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2132 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
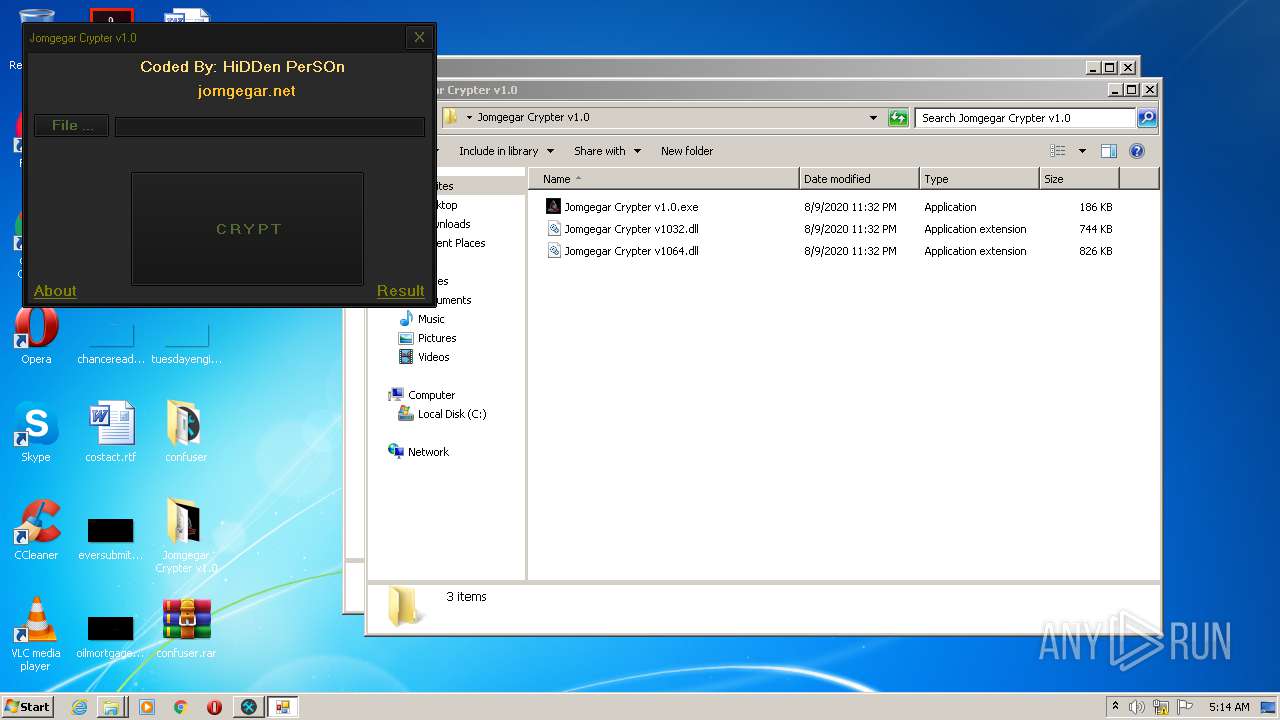
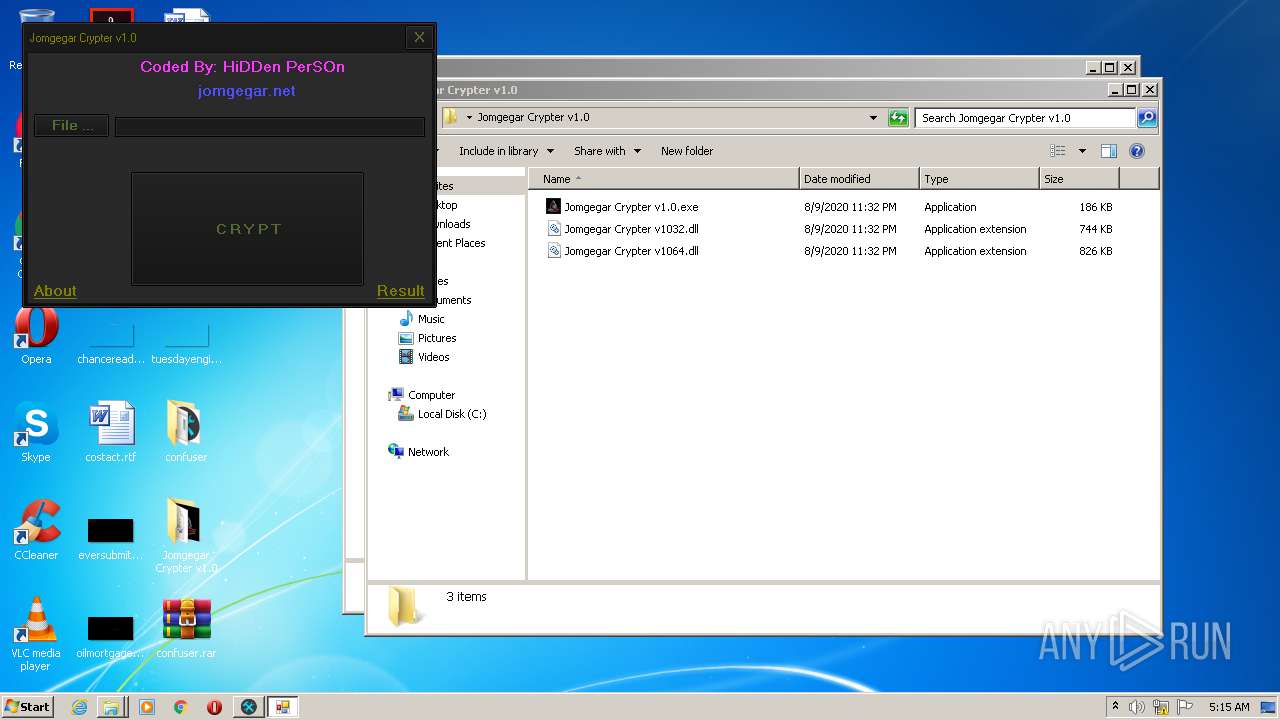
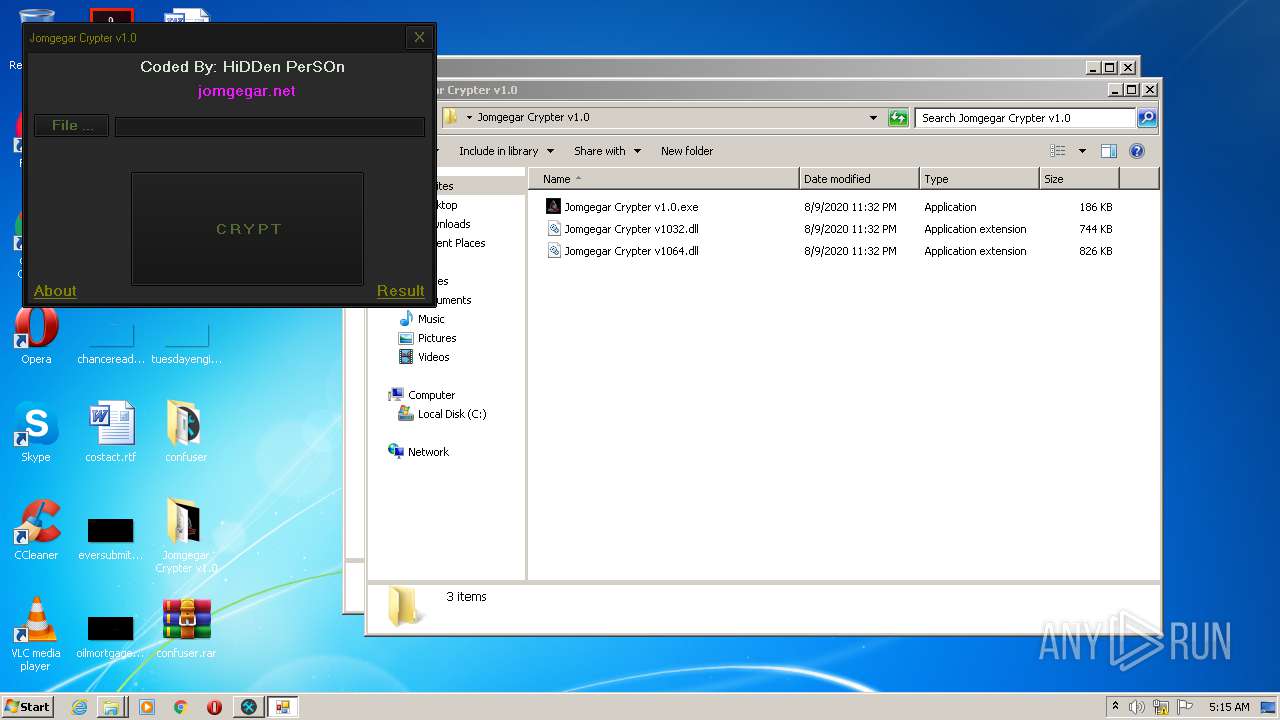
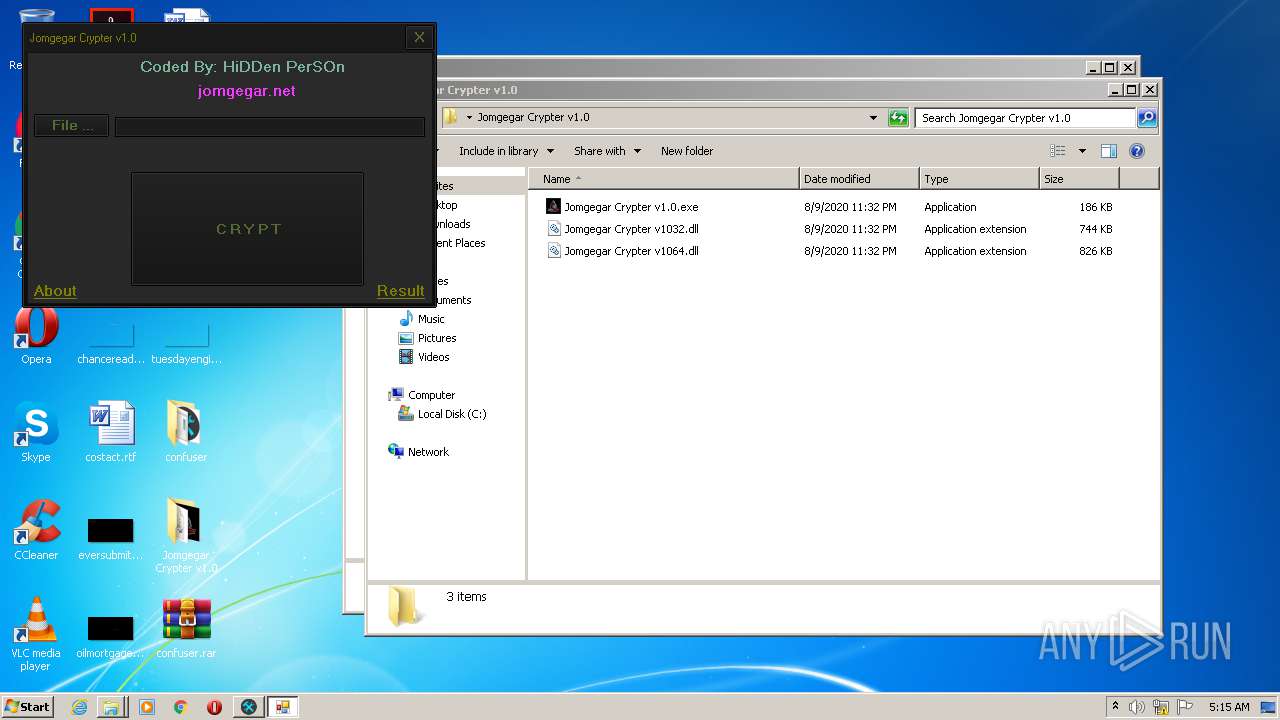
| 2132 | "C:\Program Files\Internet Explorer\iexplore.exe" https://jomgegar.net/ | C:\Program Files\Internet Explorer\iexplore.exe | — | Jomgegar Crypter v1.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2744 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\9899e494565abad3.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
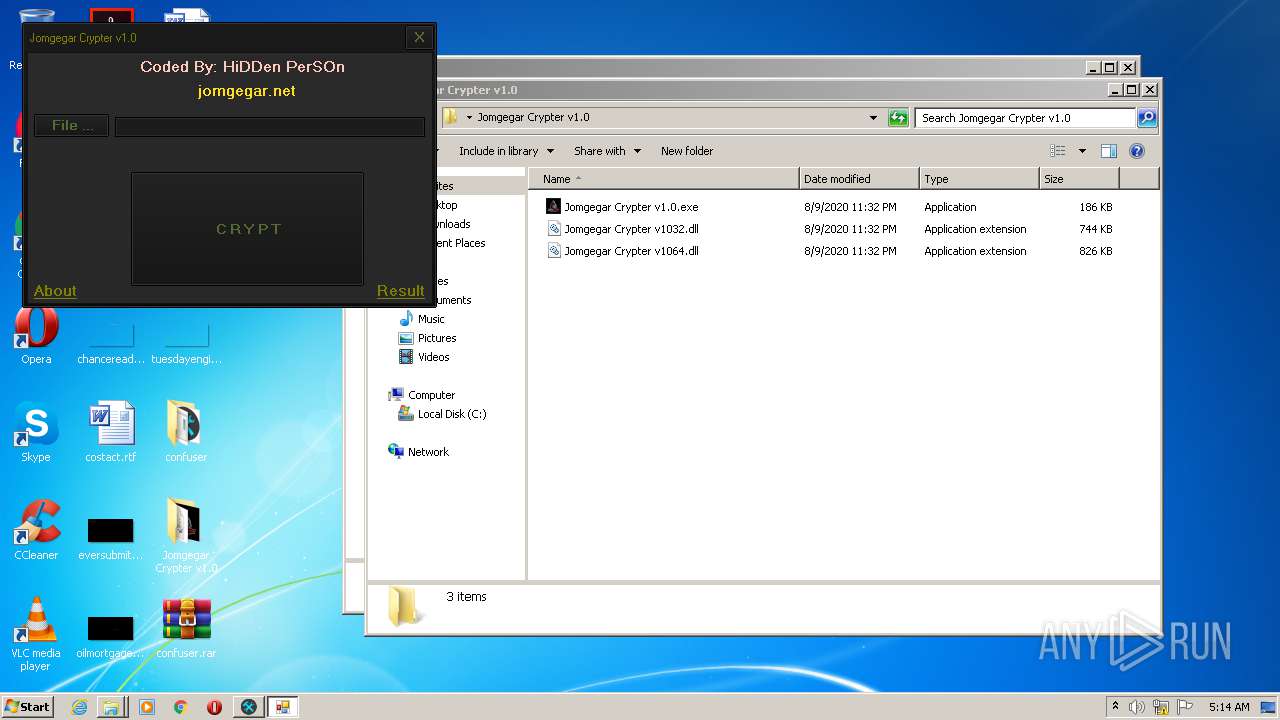
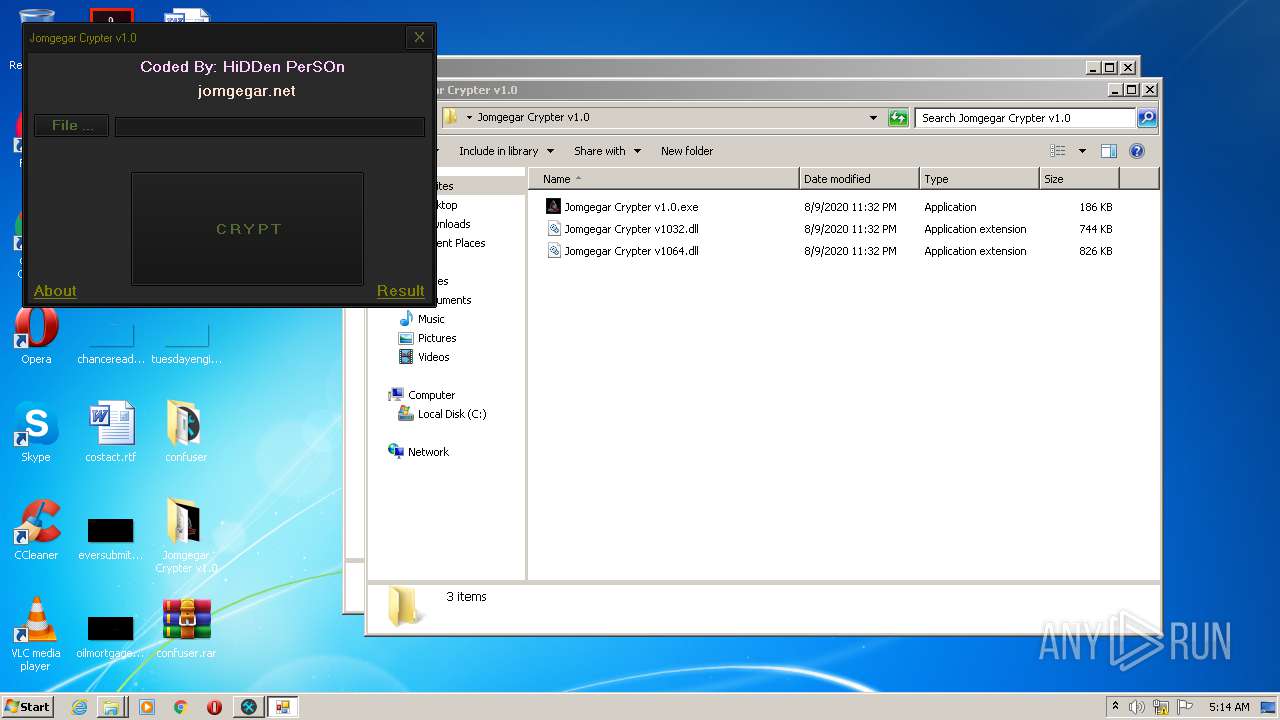
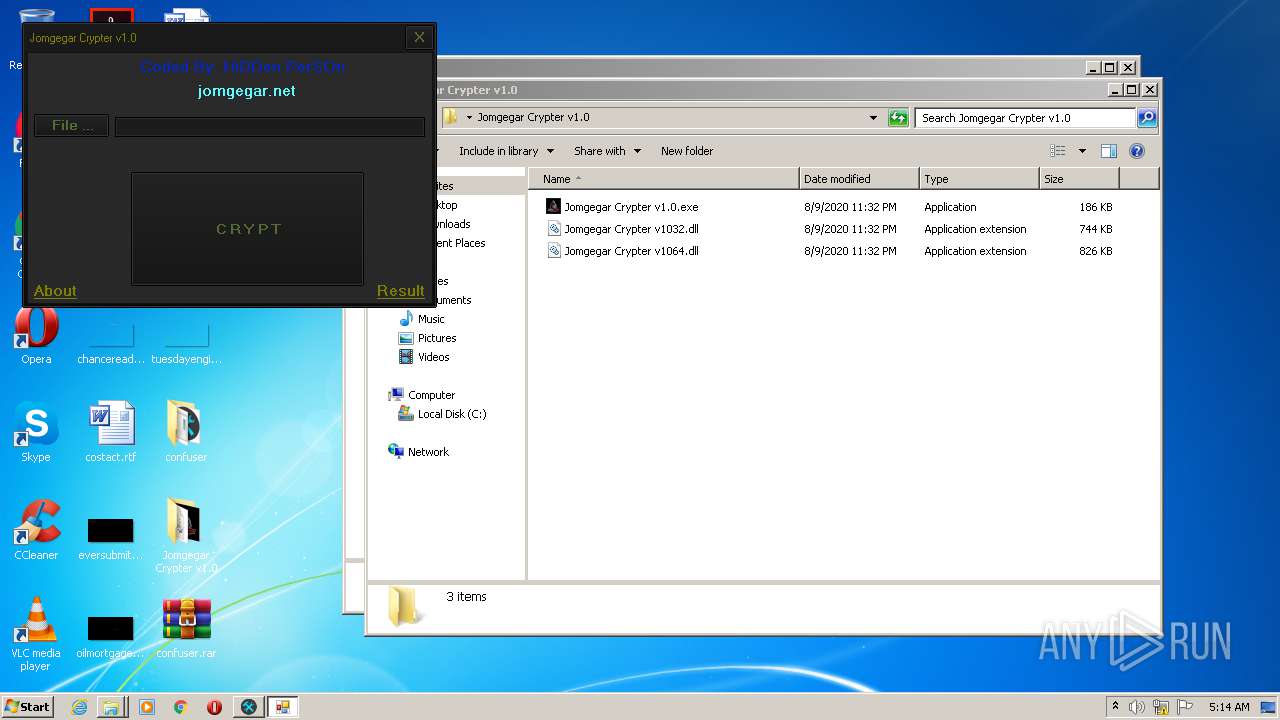
| 3276 | "C:\Users\admin\Desktop\Jomgegar Crypter v1.0\Jomgegar Crypter v1.0.exe" | C:\Users\admin\Desktop\Jomgegar Crypter v1.0\Jomgegar Crypter v1.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Jomgegar Crypter v1.0 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3880 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 215
Read events
1 141
Write events
73
Delete events
1
Modification events
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\9899e494565abad3.7z | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
21
Suspicious files
11
Text files
46
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\ConfuserEx.exe.config | xml | |
MD5:— | SHA256:— | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\Confuser.CLI.exe | executable | |
MD5:— | SHA256:— | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\Confuser.Core.dll | executable | |
MD5:— | SHA256:— | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\Confuser.DynCipher.dll | executable | |
MD5:— | SHA256:— | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\Confuser.Renamer.dll | executable | |
MD5:— | SHA256:— | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\Confuser.Protections.dll | executable | |
MD5:— | SHA256:— | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\System.Memory.dll | executable | |
MD5:2BC5DE386A4297144781D15B8E812B63 | SHA256:9C266080FB5F31E02A5005B91657093BD8C1FAED23102E021A8BE283C1753461 | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\System.Runtime.CompilerServices.Unsafe.dll | executable | |
MD5:A5AA80F49AD64689085755AB1EBF086E | SHA256:A79E1C30E9308AFE4D680F0BFB82DE3E8C1FE94AECA453EC4092C3ED4789AE6B | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\System.Windows.Interactivity.dll | executable | |
MD5:3AB57A33A6E3A1476695D5A6E856C06A | SHA256:4AACE8C8A330AE8429CD8CC1B6804076D3A9FFD633470F91FD36BDD25BB57876 | |||
| 2744 | WinRAR.exe | C:\Users\admin\Desktop\confuser\System.ValueTuple.dll | executable | |
MD5:99CEC77DBEE0AB10B9FC4D52A1D414BE | SHA256:D6FB0DCFEE1490A8168117ED1B55758F11DB38475417B3668D19F89DCB55CBDD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
936 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
936 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
936 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
1052 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
936 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
936 | iexplore.exe | 185.163.44.87:443 | jomgegar.net | MivoCloud SRL | MD | unknown |
936 | iexplore.exe | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
936 | iexplore.exe | 172.217.22.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
936 | iexplore.exe | 23.111.9.35:443 | use.fontawesome.com | netDNA | US | suspicious |
936 | iexplore.exe | 172.217.23.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
936 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1052 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jomgegar.net |
| unknown |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
use.fontawesome.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |