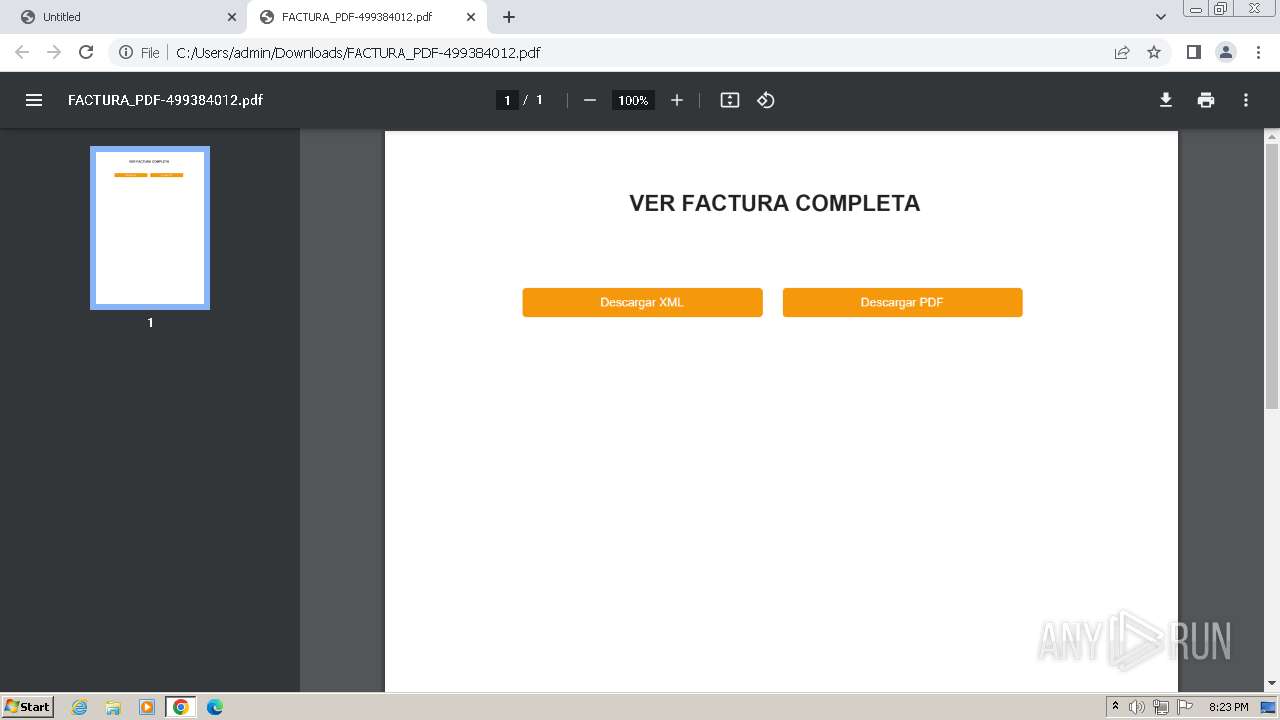
| URL: | https://webattach.mail.yandex.net/message_part_real/?sid=YWVzX3NpZDp7ImFlc0tleUlkIjoiMTc4IiwiaG1hY0tleUlkIjoiMTc4IiwiaXZCYXNlNjQiOiIvbzRHSzhESEVPdXh6L09zbURQRVB3PT0iLCJzaWRCYXNlNjQiOiJIWWVuUkhlZUpEV0JicGFPUFRtbktqK1I3MWdzSDN4dUlGMUUzdThFMU95cnhrZmVia3lRbXNLM1BuQUZiYlFDbHBIVFBHZHhPTUlMaDQwOHVOa3F1dWNmcFgrVTJpMjBsVGdZcEhqdys1YmpmRzNoUklvRGRHelB5cjFuWHluZiIsImhtYWNCYXNlNjQiOiIxWnFtQmdUVEtVYzlpdnEyNVNGMUxoa2lTUFZueXJVbW1hZ2ZOWjRERVpFPSJ9&name=FACTURA_PDF-499384012.pdf |
| Full analysis: | https://app.any.run/tasks/d320d2a0-ebb3-487a-8626-73e82a45911c |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2023, 20:22:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 3664F03500EC385C41DAC94D2A205069C46BF42F |
| SHA256: | 324E9ADC63805B10FB8137B636C8EC13BF8644BBB5F40B8907BCE954777D685D |
| SSDEEP: | 12:2iWFTj+JpVy0Ygzq2jo+GxjEnIGm1KU3qrWBC4uBV4AQ0n:2iW52cGS6lnrj1ByAQ0 |
MALICIOUS
Unusual connection from system programs
- wscript.exe (PID: 2128)
Accesses name of a computer manufacturer via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Accesses BIOS(Win32_BIOS, may evade sandboxes) via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 2128)
SUSPICIOUS
Starts CMD.EXE for commands execution
- mshta.exe (PID: 3012)
- cmd.exe (PID: 2828)
Reads the Internet Settings
- mshta.exe (PID: 3012)
- cmd.exe (PID: 1868)
- wscript.exe (PID: 2128)
Application launched itself
- cmd.exe (PID: 2828)
Accesses domain name via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 2128)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Accesses language version of the operating system installed via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 2128)
Accesses ComputerSystem(Win32_ComputerSystem) via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Access Product Name via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Gets computer name (SCRIPT)
- wscript.exe (PID: 2128)
Accesses operating system name via WMI (SCRIPT)
- wscript.exe (PID: 2128)
Accesses WMI object caption (SCRIPT)
- wscript.exe (PID: 2128)
The process executes VB scripts
- cmd.exe (PID: 1868)
Adds/modifies Windows certificates
- cmd.exe (PID: 1868)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3140)
- wmpnscfg.exe (PID: 1752)
Manual execution by a user
- wmpnscfg.exe (PID: 3140)
- wmpnscfg.exe (PID: 1752)
Application launched itself
- chrome.exe (PID: 3448)
Reads the computer name
- wmpnscfg.exe (PID: 3140)
- wmpnscfg.exe (PID: 1752)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3140)
- wmpnscfg.exe (PID: 1752)
The process uses the downloaded file
- chrome.exe (PID: 2064)
- chrome.exe (PID: 3800)
- chrome.exe (PID: 2096)
- chrome.exe (PID: 988)
- WinRAR.exe (PID: 2860)
- chrome.exe (PID: 3548)
Reads Internet Explorer settings
- mshta.exe (PID: 3012)
Checks proxy server information
- wscript.exe (PID: 2128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
73
Monitored processes
37
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3480 --field-trial-handle=1176,i,8942788189295451246,5645754794289549337,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 528 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3708 --field-trial-handle=1176,i,8942788189295451246,5645754794289549337,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 924 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3600 --field-trial-handle=1176,i,8942788189295451246,5645754794289549337,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2144 --field-trial-handle=1176,i,8942788189295451246,5645754794289549337,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1248 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --pdf-renderer --disable-gpu-compositing --lang=en-US --js-flags=--jitless --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3860 --field-trial-handle=1176,i,8942788189295451246,5645754794289549337,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1052 --field-trial-handle=1176,i,8942788189295451246,5645754794289549337,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4296 --field-trial-handle=1176,i,8942788189295451246,5645754794289549337,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
12 481
Read events
12 290
Write events
182
Delete events
9
Modification events
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3140) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{25B546B1-A5A8-45EE-885B-D4B842384872}\{22B64DDF-BBCF-4431-82A9-B0CD595C44C0} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3140) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{25B546B1-A5A8-45EE-885B-D4B842384872} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3140) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{D5A4089A-263F-474E-97B5-7CEB90A5F883} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
Executable files
1
Suspicious files
99
Text files
31
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF166e20.TMP | — | |
MD5:— | SHA256:— | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:513218482935B0D388C0A990D868387A | SHA256:8E39CBAAF4AACC3A01AFA74EA8C30FB24FE69A22B8B30728AFB1614FD68809D9 | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:B806171F9E7C87423595645872D869B0 | SHA256:851A8D533BEBF6A69C5518375396E97463302C1E2031D04F8EB5851C5C82CEB9 | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:E91E138A25FD7E5BCA5E60111F39C91A | SHA256:B1F7E3537A31A4B847F862858E5D2581993CC9372F19ABF19EA2A9185FE42A4F | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF166f2a.TMP | text | |
MD5:561161B0FF5BCA89BF47F8AC972A7499 | SHA256:ECCA5CCFA0BEED7581B39FCE03D0FD3B694DF0F92BFFF780F702118AD51FC17D | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old~RF1671c9.TMP | — | |
MD5:— | SHA256:— | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF167014.TMP | text | |
MD5:56C75810BDDDD686D123E6E36F56E012 | SHA256:3D51A6EF85A51056E1A379D795F55C84A321EC2000DD69F5D70ABA038C61522E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
53
DNS requests
53
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
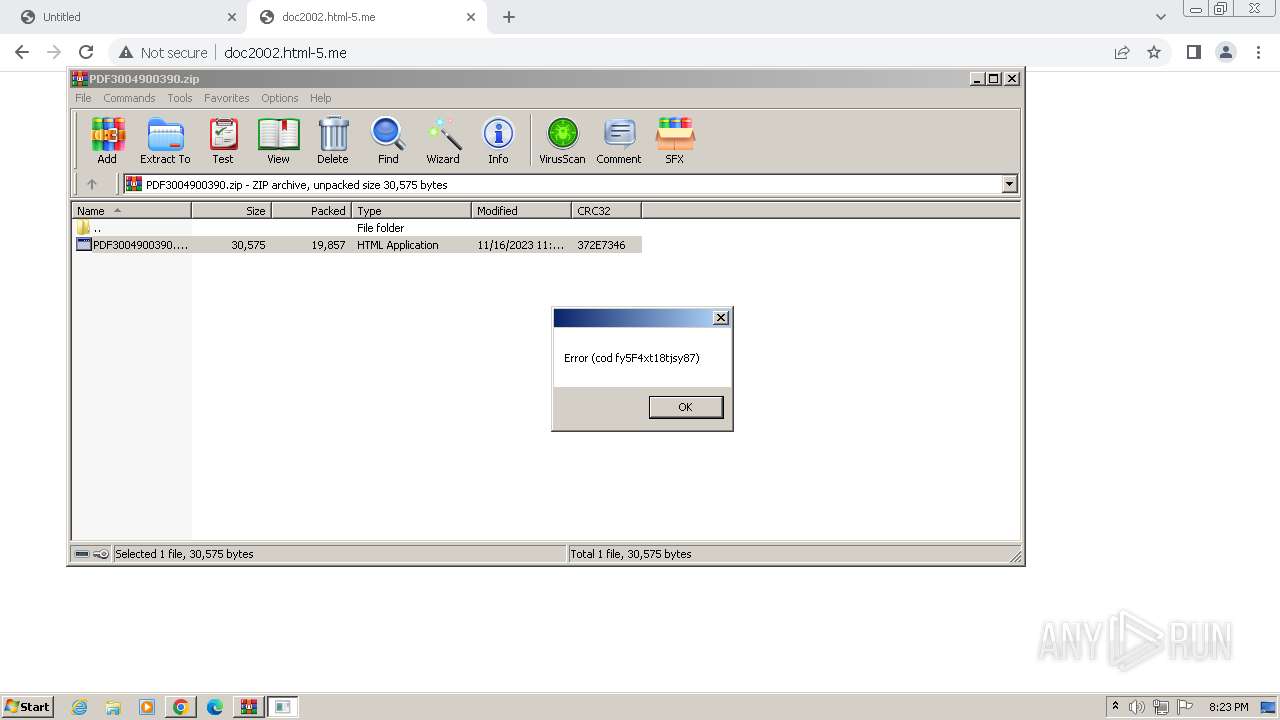
3624 | chrome.exe | GET | 301 | 157.245.113.153:80 | http://tiny.cc/factura-mail-pdf1023-y4m | unknown | html | 169 b | unknown |
3624 | chrome.exe | GET | 200 | 185.27.134.176:80 | http://doc2002.html-5.me/aes.js | unknown | text | 13.4 Kb | unknown |
3624 | chrome.exe | GET | 200 | 185.27.134.176:80 | http://doc2002.html-5.me/ | unknown | html | 828 b | unknown |
3624 | chrome.exe | GET | 301 | 185.27.134.176:80 | http://doc2002.html-5.me/?i=1 | unknown | html | 672 b | unknown |
2128 | wscript.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6c947ebbc9e45b80 | unknown | compressed | 61.6 Kb | unknown |
2128 | wscript.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2128 | wscript.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?29e53a529a0b33bb | unknown | compressed | 4.66 Kb | unknown |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
2128 | wscript.exe | GET | 200 | 184.24.77.74:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPmXEYhFpEleLOxPpS2jliXpA%3D%3D | unknown | binary | 503 b | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 10.0 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3448 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3624 | chrome.exe | 142.250.186.45:443 | accounts.google.com | GOOGLE | US | unknown |
3624 | chrome.exe | 87.250.251.147:443 | webattach.mail.yandex.net | YANDEX LLC | RU | whitelisted |
3624 | chrome.exe | 142.250.185.206:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
3448 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
3624 | chrome.exe | 172.217.18.4:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
webattach.mail.yandex.net |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
tiny.cc |
| shared |
doc2002.html-5.me |
| unknown |
www.googleapis.com |
| whitelisted |
linuxkkll.zapto.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3624 | chrome.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3624 | chrome.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3624 | chrome.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (tiny .cc) |
3624 | chrome.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (tiny .cc) |
3624 | chrome.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3624 | chrome.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3624 | chrome.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (tiny .cc) |
3624 | chrome.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (tiny .cc) |
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |