| File name: | raonkSetup.exe |
| Full analysis: | https://app.any.run/tasks/5fd1b82c-216e-4e0d-999d-6ed4d66d81d4 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2022, 18:20:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 45DB34D274A958C3479F9D91018AF842 |
| SHA1: | 5A452A62D343D4BDAB694F981583537BBEB9FF76 |
| SHA256: | 324BDAD3C5988D48E10792635D1F2AAF86343DD2C4C9F32E34D2661E0901BE0E |
| SSDEEP: | 98304:fKcF+AIu1QEXpzxQuuP2OFWVSjVECWIZFt9Fe/C53cmxmA5MEPCdgyjp:fTMKhXpzCPFWVKdWIjYa7MEPCdJ |
MALICIOUS
Drops executable file immediately after starts
- raonkSetup.exe (PID: 2184)
- raonkSetup_s.exe (PID: 3904)
Application was dropped or rewritten from another process
- raonkSetup_s.exe (PID: 3904)
- certutil.exe (PID: 1280)
- raonk.svc.exe (PID: 1552)
- raonk.moni.exe (PID: 1472)
- raonk.exe (PID: 3588)
- certutil.exe (PID: 3616)
- raonk.svc.exe (PID: 2152)
Changes settings of System certificates
- raonkSetup_s.exe (PID: 3904)
Loads dropped or rewritten executable
- certutil.exe (PID: 1280)
- raonkSetup_s.exe (PID: 3904)
- certutil.exe (PID: 3616)
Changes the autorun value in the registry
- raonkSetup_s.exe (PID: 3904)
Changes internet zones settings
- raonkSetup_s.exe (PID: 3904)
SUSPICIOUS
Drops a file with a compile date too recent
- raonkSetup.exe (PID: 2184)
- raonkSetup_s.exe (PID: 3904)
Checks supported languages
- raonkSetup.exe (PID: 2184)
- raonkSetup_s.exe (PID: 3904)
- raonk.svc.exe (PID: 1552)
- cmd.exe (PID: 3352)
- raonk.svc.exe (PID: 2152)
- raonk.moni.exe (PID: 1472)
- raonk.exe (PID: 3588)
Reads the computer name
- raonk.svc.exe (PID: 1552)
- raonkSetup_s.exe (PID: 3904)
- raonk.svc.exe (PID: 2152)
Executable content was dropped or overwritten
- raonkSetup.exe (PID: 2184)
- raonkSetup_s.exe (PID: 3904)
Creates a software uninstall entry
- raonkSetup_s.exe (PID: 3904)
Creates files in the program directory
- raonkSetup_s.exe (PID: 3904)
Reads Environment values
- netsh.exe (PID: 3552)
- netsh.exe (PID: 2648)
- netsh.exe (PID: 344)
- netsh.exe (PID: 2612)
- netsh.exe (PID: 3048)
- netsh.exe (PID: 1188)
Executed as Windows Service
- raonk.svc.exe (PID: 2152)
INFO
Reads settings of System Certificates
- raonkSetup_s.exe (PID: 3904)
- raonk.exe (PID: 3588)
Checks supported languages
- netsh.exe (PID: 3552)
- netsh.exe (PID: 344)
- netsh.exe (PID: 2648)
- netsh.exe (PID: 3048)
- netsh.exe (PID: 2612)
- netsh.exe (PID: 1188)
Reads the computer name
- netsh.exe (PID: 3552)
- netsh.exe (PID: 2612)
- netsh.exe (PID: 344)
- netsh.exe (PID: 2648)
- netsh.exe (PID: 3048)
- netsh.exe (PID: 1188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| ProductVersion: | 2018.0.2.58 |
|---|---|
| ProductName: | RAON K 2018 |
| OriginalFileName: | RaonKSetup.exe |
| LegalCopyright: | Copyright (C)2017 RAONWiZ Inc. All rights reserved. |
| InternalName: | RaonKSetup |
| FileVersion: | 2018.0.2.58 |
| FileDescription: | RAON K 2018 Setup |
| CompanyName: | RAONWiZ Inc. |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Dynamic link library |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 2018.0.2.58 |
| FileVersionNumber: | 2018.0.2.58 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0xeffb |
| UninitializedDataSize: | - |
| InitializedDataSize: | 4820992 |
| CodeSize: | 117248 |
| LinkerVersion: | 12 |
| PEType: | PE32 |
| TimeStamp: | 2020:09:04 07:43:53+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 04-Sep-2020 05:43:53 |
| Detected languages: |
|
| CompanyName: | RAONWiZ Inc. |
| FileDescription: | RAON K 2018 Setup |
| FileVersion: | 2018.0.2.58 |
| InternalName: | RaonKSetup |
| LegalCopyright: | Copyright (C)2017 RAONWiZ Inc. All rights reserved. |
| OriginalFilename: | RaonKSetup.exe |
| ProductName: | RAON K 2018 |
| ProductVersion: | 2018.0.2.58 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 04-Sep-2020 05:43:53 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001C90A | 0x0001CA00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65029 |
.rdata | 0x0001E000 | 0x0000AD1A | 0x0000AE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.23762 |
.data | 0x00029000 | 0x00003980 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.94125 |
.rsrc | 0x0002D000 | 0x00488B58 | 0x00488C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.98103 |
.reloc | 0x004B6000 | 0x00001AC4 | 0x00001C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.48904 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.32525 | 1081 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.17761 | 1128 | UNKNOWN | Korean - Korea | RT_ICON |
3 | 2.94885 | 4264 | UNKNOWN | Korean - Korea | RT_ICON |
4 | 3.22486 | 9640 | UNKNOWN | Korean - Korea | RT_ICON |
5 | 2.66454 | 38056 | UNKNOWN | Korean - Korea | RT_ICON |
9 | 1.60504 | 56 | UNKNOWN | Korean - Korea | RT_STRING |
128 | 2.79289 | 76 | UNKNOWN | Korean - Korea | RT_GROUP_ICON |
129 | 2.32548 | 64 | UNKNOWN | Korean - Korea | RT_DIALOG |
245 | 7.99859 | 4630723 | UNKNOWN | Korean - Korea | K_EXE |
Imports
ADVAPI32.dll |
COMCTL32.dll |
KERNEL32.dll |
OLEAUT32.dll |
USER32.dll |
ole32.dll |
Total processes
57
Monitored processes
16
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 344 | netsh advfirewall firewall add rule name="RAONK" dir=in action=allow program="C:\ProgramData\RAONWIZ\RAON K\raonk.exe" enable=yes | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1188 | netsh advfirewall firewall add rule name="RAONKSVC" dir=out action=allow program="C:\ProgramData\RAONWIZ\RAON K\raonk.svc.exe" enable=yes | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
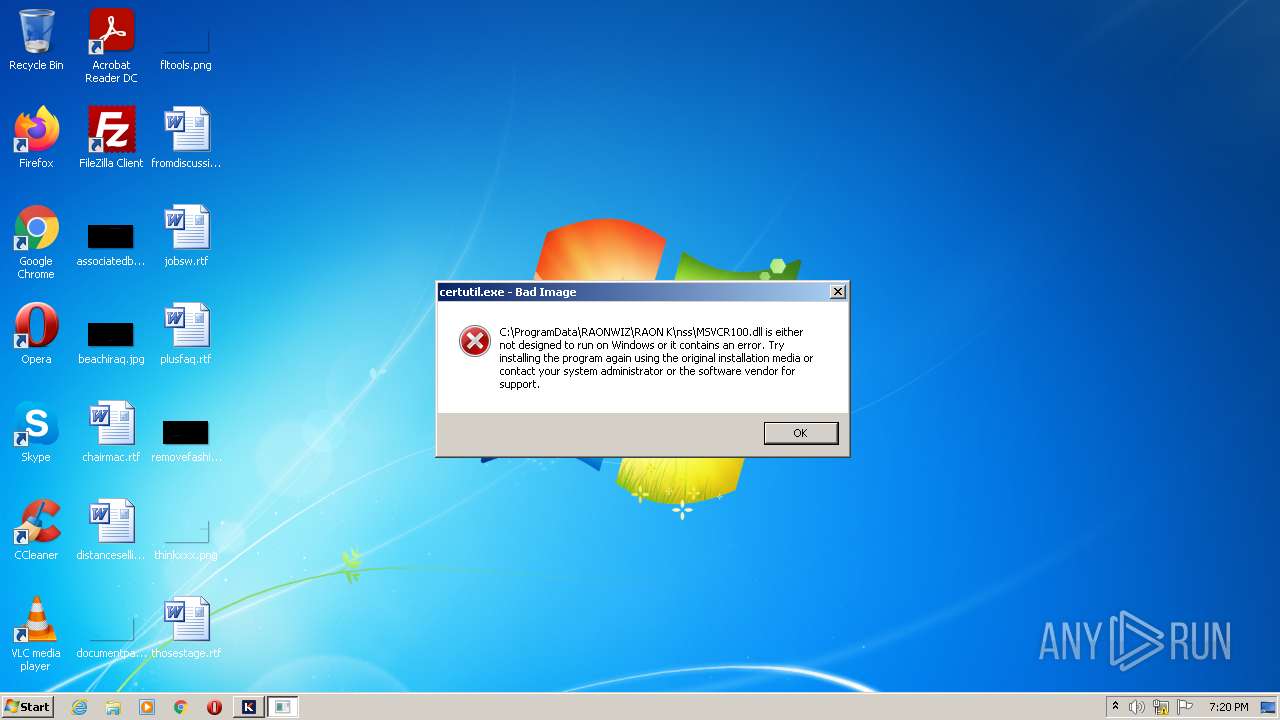
| 1280 | "C:\ProgramData\RAONWIZ\RAON K\nss\certutil" -A -n "CN=RAON K ROOT CA" -t "C,C,C" -d sql:"C:/Users/admin/AppData/Roaming/Mozilla/Firefox/Profiles/qldyz51w.default" -i "C:\ProgramData\RAONWIZ\RAON K\nss\raonkca.crt" | C:\ProgramData\RAONWIZ\RAON K\nss\certutil.exe | — | raonkSetup_s.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221226330 Modules
| |||||||||||||||
| 1472 | "C:\ProgramData\RAONWIZ\RAON K\raonk.moni.exe" | C:\ProgramData\RAONWIZ\RAON K\raonk.moni.exe | — | raonk.svc.exe | |||||||||||
User: admin Company: RAONWiZ Inc. Integrity Level: HIGH Description: RAON K Moni Exit code: 0 Version: 2018.0.0.9 Modules
| |||||||||||||||
| 1552 | "C:\ProgramData\RAONWIZ\RAON K\raonk.svc.exe" -install | C:\ProgramData\RAONWIZ\RAON K\raonk.svc.exe | — | raonkSetup_s.exe | |||||||||||
User: admin Company: RAONWiZ Inc. Integrity Level: HIGH Description: RAON K Service, Auit Improved Exit code: 0 Version: 2018.0.0.10 Modules
| |||||||||||||||
| 2152 | "C:\ProgramData\RAONWIZ\RAON K\raonk.svc.exe" | C:\ProgramData\RAONWIZ\RAON K\raonk.svc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: RAONWiZ Inc. Integrity Level: SYSTEM Description: RAON K Service, Auit Improved Exit code: 0 Version: 2018.0.0.10 Modules
| |||||||||||||||
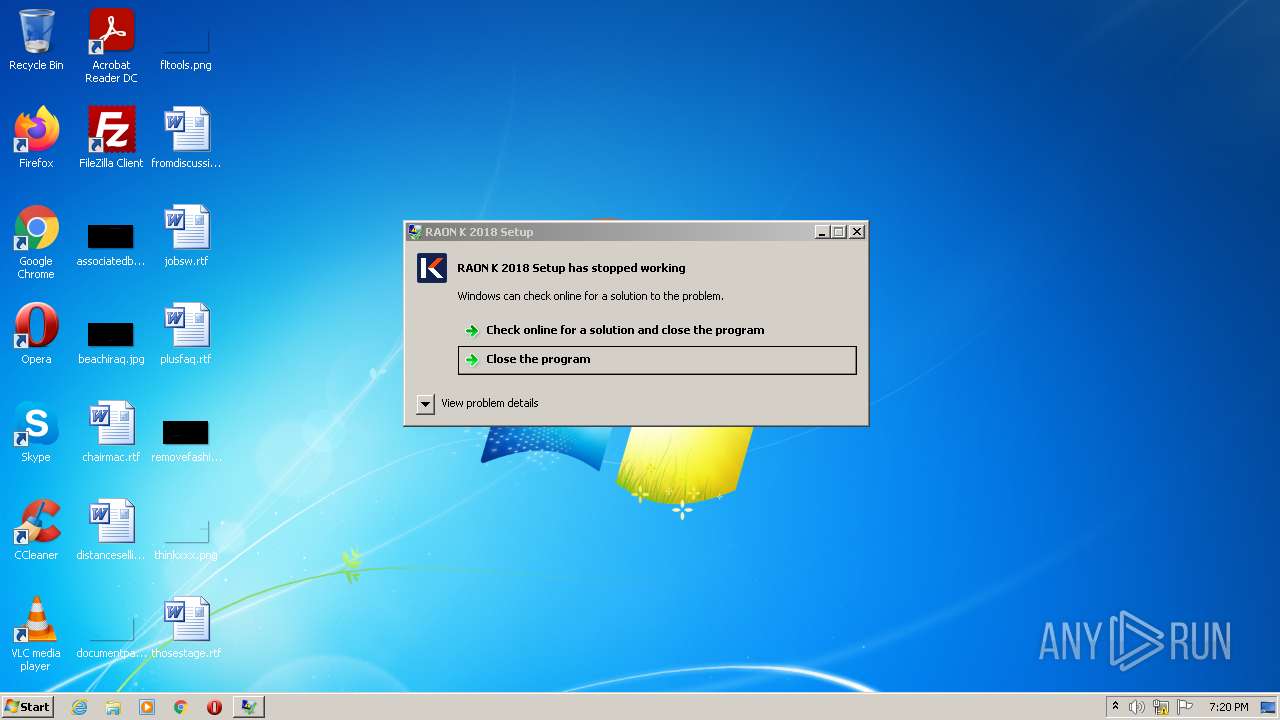
| 2184 | "C:\Users\admin\AppData\Local\Temp\raonkSetup.exe" | C:\Users\admin\AppData\Local\Temp\raonkSetup.exe | Explorer.EXE | ||||||||||||
User: admin Company: RAONWiZ Inc. Integrity Level: HIGH Description: RAON K 2018 Setup Exit code: 0 Version: 2018.0.2.58 Modules
| |||||||||||||||
| 2612 | netsh advfirewall firewall add rule name="RAONKSVC" dir=in action=allow program="C:\ProgramData\RAONWIZ\RAON K\raonk.svc.exe" enable=yes | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2648 | netsh advfirewall firewall add rule name="RAONK" dir=out action=allow program="C:\ProgramData\RAONWIZ\RAON K\raonk.exe" enable=yes | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | netsh advfirewall firewall delete rule name="RAONKSVC" | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 103
Read events
7 783
Write events
320
Delete events
0
Modification events
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyOverride |
Value: 127.0.0.1:47317;127.0.0.1:47337;127.0.0.1:47139;127.0.0.1:47159;127.0.0.1:57317;127.0.0.1:57337;127.0.0.1:57318;127.0.0.1:57338;127.0.0.1:57419;127.0.0.1:57439 | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\ECEE052F995765664EE76FBF29EE491E36E8B156 |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000ECEE052F995765664EE76FBF29EE491E36E8B15620000000010000002B040000308204273082030FA00302010202090086595CB263071EE4300D06092A864886F70D01010B05003069310B3009060355040613024B5231153013060355040A0C0C52414F4E57495A20496E632E312A3028060355040B0C21526573656172636820616E6420446576656C6F706D656E74204469766973696F6E3117301506035504030C0E52414F4E204B20524F4F54204341301E170D3138303931393032303135335A170D3338313233313032303135335A3069310B3009060355040613024B5231153013060355040A0C0C52414F4E57495A20496E632E312A3028060355040B0C21526573656172636820616E6420446576656C6F706D656E74204469766973696F6E3117301506035504030C0E52414F4E204B20524F4F5420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100DA1980EDE10B7C474FFF329932502EB379A738EDD971B1BE914EEDE0C58C21D9DB1186999E4DC09E0E5D73C733D0D8FB86779E74590F19657FD66A274A478754C24274F951C783125B96C1819538984EC3B2D71C079D0A066A20D46F7FC6CF0ECD754AEE997805B9CB605CB9BC820BBCECF5B278E869945AB341CDFB03ACFF785C877F4C0E3A549345AC0C351CA5D2FDDA00C9FD2E524FDD28B75A6105DE25BC240BEEBB2E46447A72331954B9AE4CF7C9C62BF9E08BFF310AE51B2575DD2056AE28EC78500EB7FCB897B278C08C74320330365AB685C3AFE90FCD2074273CC6054AF9F24F017C9CD6AAA2CD3CCAD5BD9BB464EC038057AF63DFC3305B66E2170203010001A381D13081CE300F0603551D130101FF040530030101FF301D0603551D0E041604146AA702326DC0BB9B82195D3214E1C9D8F25B886A30819B0603551D2304819330819080146AA702326DC0BB9B82195D3214E1C9D8F25B886AA16DA46B3069310B3009060355040613024B5231153013060355040A0C0C52414F4E57495A20496E632E312A3028060355040B0C21526573656172636820616E6420446576656C6F706D656E74204469766973696F6E3117301506035504030C0E52414F4E204B20524F4F5420434182090086595CB263071EE4300D06092A864886F70D01010B05000382010100AAAE0C28946E6E3611CA5FBD1FFD1759182A0052A70830ADF69E313D175F4A53991DC4FD41637788C7D88A6BD4131ED25167670F77C69BBC9D5254C1F44BDAD7B3A6C9A892905E04E739B39EEB49CFCD0F939F7DC0AEC5C0DE32BE2BE2C0B094637B42FC8ACF47A1901FBF05D7FC03840C0CF3C83BEB3E3DFC0D4C09732DDBAA75655DD0201BE1AAA60099D88985FCE85A7FD7985DCF101C072DB00081B217D13E22ACAA342B4ACEE965F3CAAD03326D15BBE9F08310FF9C942E55E16D931C330ACA95F70170A431207FF12D22985AD6E385B62EB32A61BD07E11707AD137D0982CBC36EB868BA7E4668E386CA60DE2FB08471E53FA6C591AC6D716EB6C08F8E | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | RAONK |
Value: C:\ProgramData\RAONWIZ\RAON K\raonk.moni.exe | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_CURRENT_USER\Software\HNC\HwpCtrl\Modules |
| Operation: | write | Name: | raonkhwp |
Value: C:\ProgramData\RAONWIZ\RAON K\raonkhwp.dll | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\Application\RAON K |
| Operation: | write | Name: | EventMessageFile |
Value: C:\ProgramData\RAONWIZ\RAON K\raonk.svc.exe | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\Application\RAON K |
| Operation: | write | Name: | TypesSupported |
Value: 7 | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RAON K 2018 |
| Operation: | write | Name: | DisplayName |
Value: RAON K 2018 | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RAON K 2018 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\ProgramData\RAONWIZ\RAON K\bin\raonk.exe | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RAON K 2018 |
| Operation: | write | Name: | InstallLocation |
Value: C:\ProgramData\RAONWIZ\RAON K | |||
| (PID) Process: | (3904) raonkSetup_s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RAON K 2018 |
| Operation: | write | Name: | UninstallString |
Value: C:\ProgramData\RAONWIZ\RAON K\uninstall.exe /u | |||
Executable files
26
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | raonkSetup.exe | C:\Users\admin\AppData\Local\Temp\raonkSetup_s.zip | compressed | |
MD5:AF0C07151E0C1781008B8263EC9C23D6 | SHA256:E116E5508B0C98B914B1E5A842C8ECA6554390E34D45D3C48617AD4B30D7F71C | |||
| 3904 | raonkSetup_s.exe | C:\ProgramData\RAONWIZ\RAON K\nss\freebl3.dll | executable | |
MD5:269BEB631B580C6D54DB45B5573B1DE5 | SHA256:FFC7558A61A4E6546CF095BDEABEA19F05247A0DAA02DCA20EA3605E7FC62C77 | |||
| 3904 | raonkSetup_s.exe | C:\ProgramData\RAONWIZ\RAON K\nss\nssckbi.dll | executable | |
MD5:D1243817A1B22B855DE0852CF5B53BF5 | SHA256:93E99CFBA00348BE3A102DC9F41ACD39BBA91D7F4E0149A9EA6C53FCC50ADAEE | |||
| 3904 | raonkSetup_s.exe | C:\ProgramData\RAONWIZ\RAON K\nss\softokn3.dll | executable | |
MD5:2AB31C9401870ADB4E9D88B5A6837ABF | SHA256:22ECECE561510F77B100CFF8109E5ED492C34707B7B14E0774AAA9CA813DE4AD | |||
| 3904 | raonkSetup_s.exe | C:\ProgramData\RAONWIZ\RAON K\nss\libplds4.dll | executable | |
MD5:9AE76DB13972553A5DE5BDD07B1B654D | SHA256:38A906373419501966DAF6EC19CA2F8DB7B29609128AE5CB424D2AA511652C29 | |||
| 3904 | raonkSetup_s.exe | C:\ProgramData\RAONWIZ\RAON K\nss\nssutil3.dll | executable | |
MD5:C26E940B474728E728CAFE5912BA418A | SHA256:1AF1AC51A92B36DE8D85D1F572369815404912908C3A489A6CD7CA2350C2A93D | |||
| 3904 | raonkSetup_s.exe | C:\ProgramData\RAONWIZ\RAON K\nss\raonkca.crt | text | |
MD5:8109F560B1D42EA3226F29060C60A7CA | SHA256:F0743FBBABBBFBBC8272D699178E8E20F9557AB6EE1B2285C86CD83EC0073A03 | |||
| 3904 | raonkSetup_s.exe | C:\ProgramData\RAONWIZ\RAON K\raonk.svc.exe | executable | |
MD5:90AB763C32288A2BFA4650BC0E3E0D2F | SHA256:D3B8008BD368ADCA7A0857907C3EAD510B7B9DBDF9C374879C8F5FADBDF5E6DF | |||
| 2184 | raonkSetup.exe | C:\Users\admin\AppData\Local\Temp\raonkSetup_s.exe | executable | |
MD5:7B142E245E7AFAB40A63DFE119B8673A | SHA256:BD320155673A0623C0490B31C3F23FB949D0DBA1ADA9C1AAFDEDEB8AB91EC953 | |||
| 3904 | raonkSetup_s.exe | C:\ProgramData\RAONWIZ\RAON K\nss.zip | compressed | |
MD5:E45D85AB3D4AF7AED1FB1583D29E877F | SHA256:4BDCAA7A3AE9AFFD69856160024AA63F4384020F0C5ED06FD2CDDF9E54DF3BCC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report