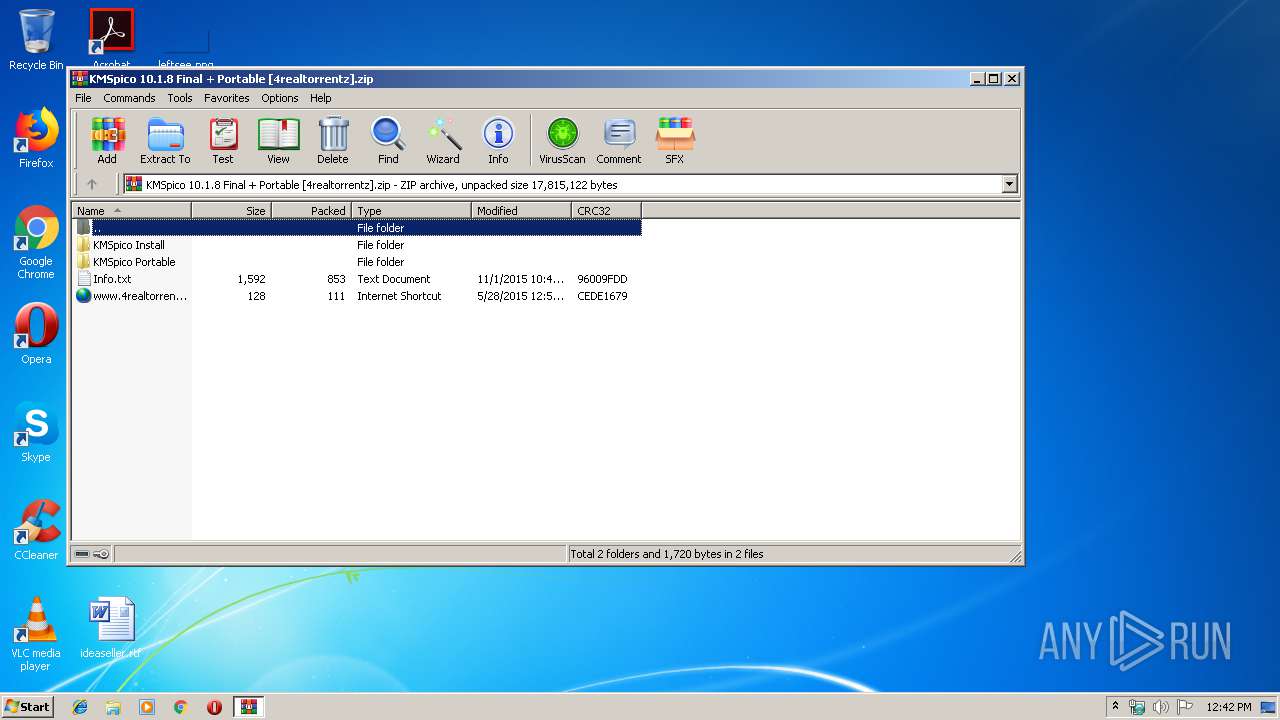
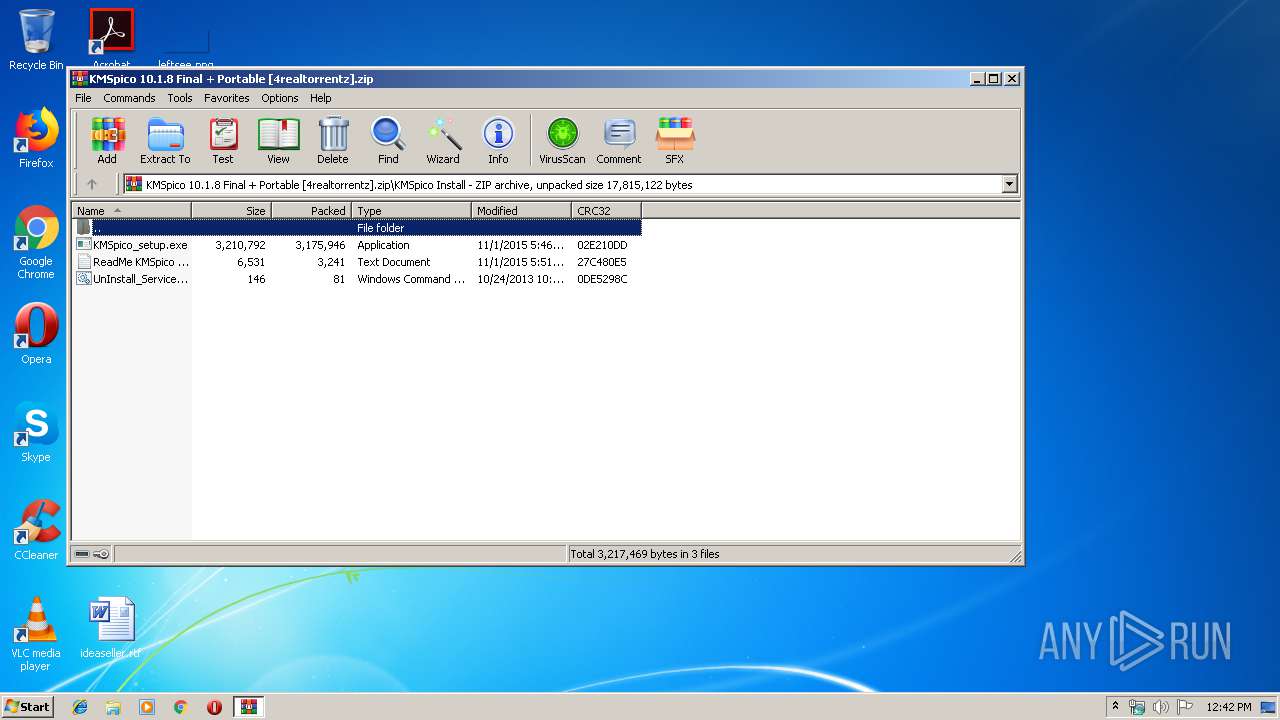
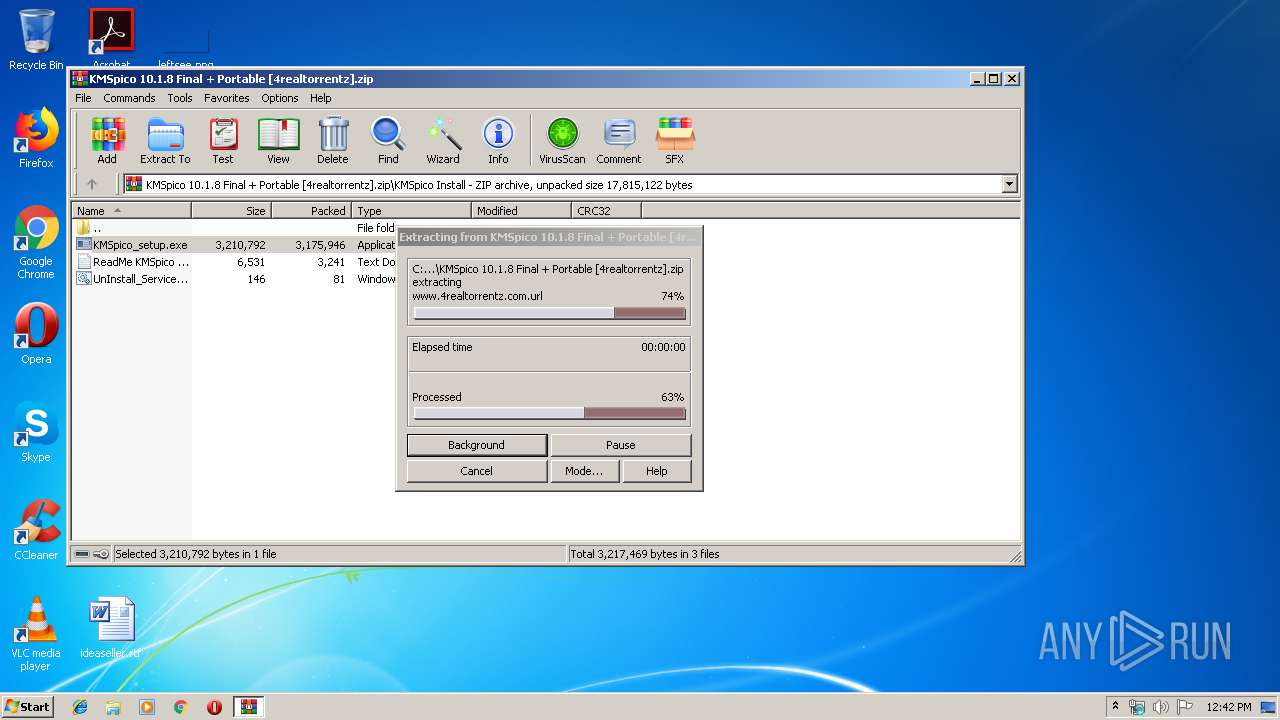
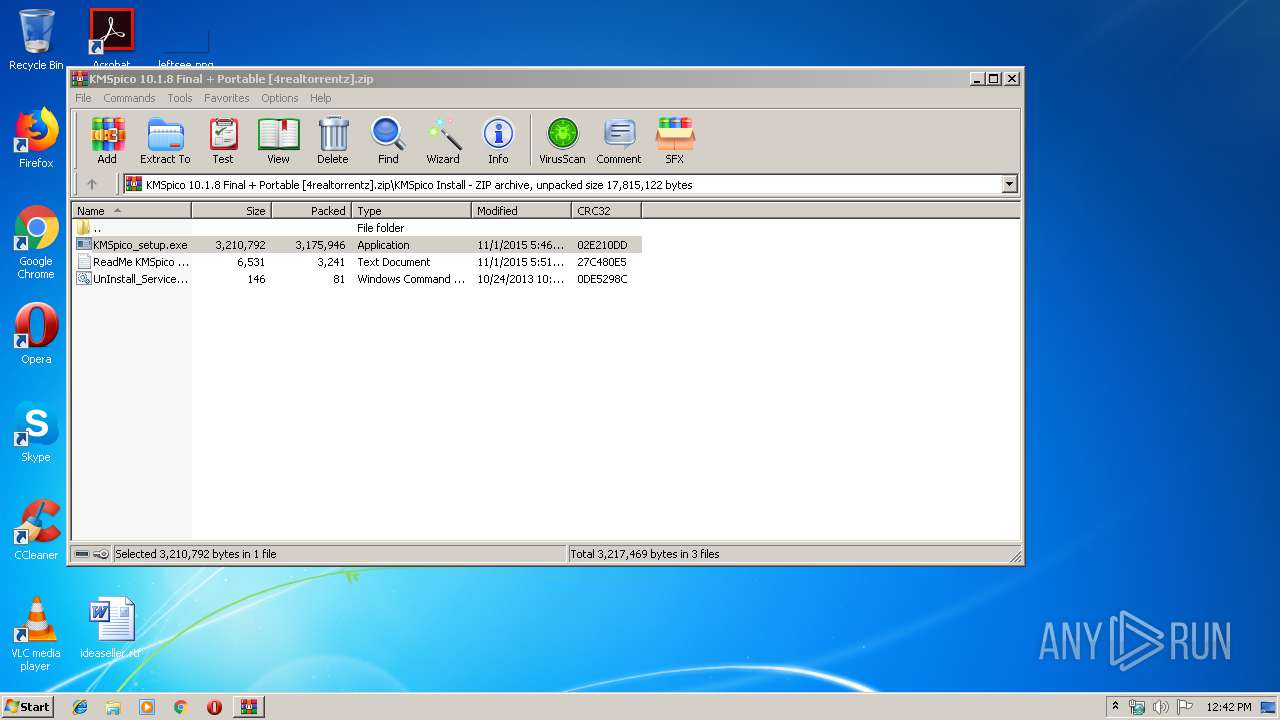
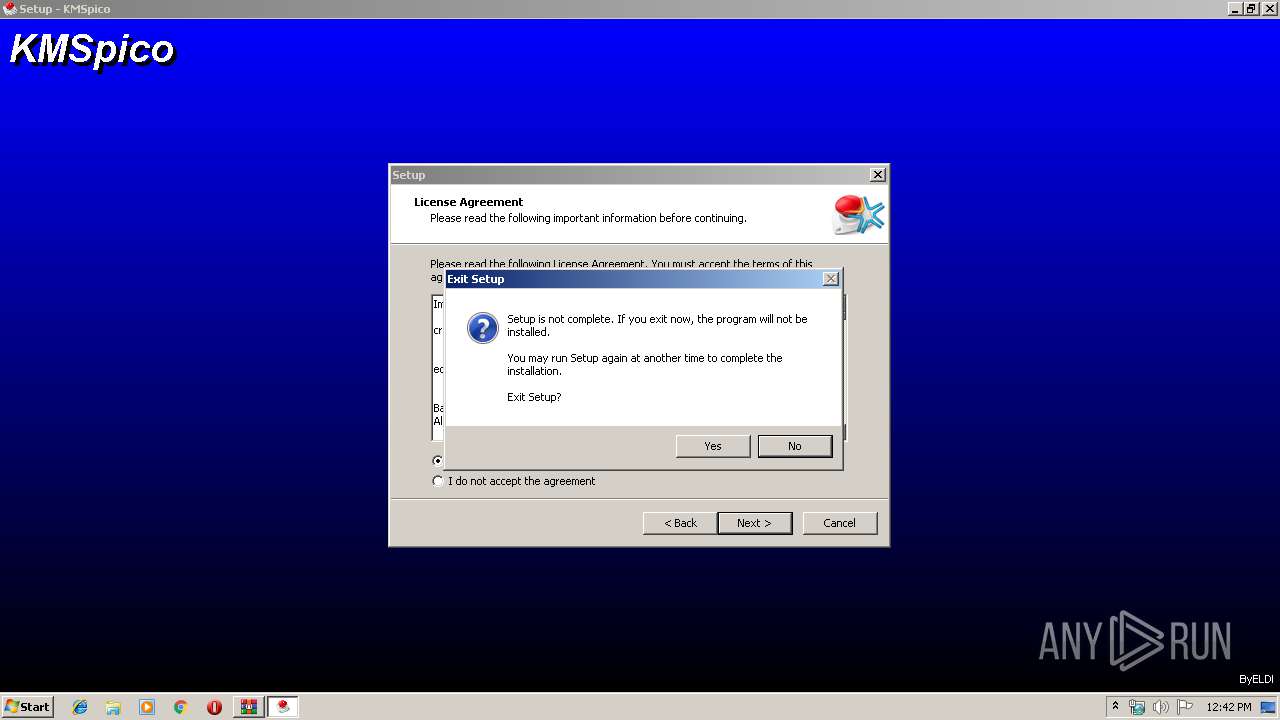
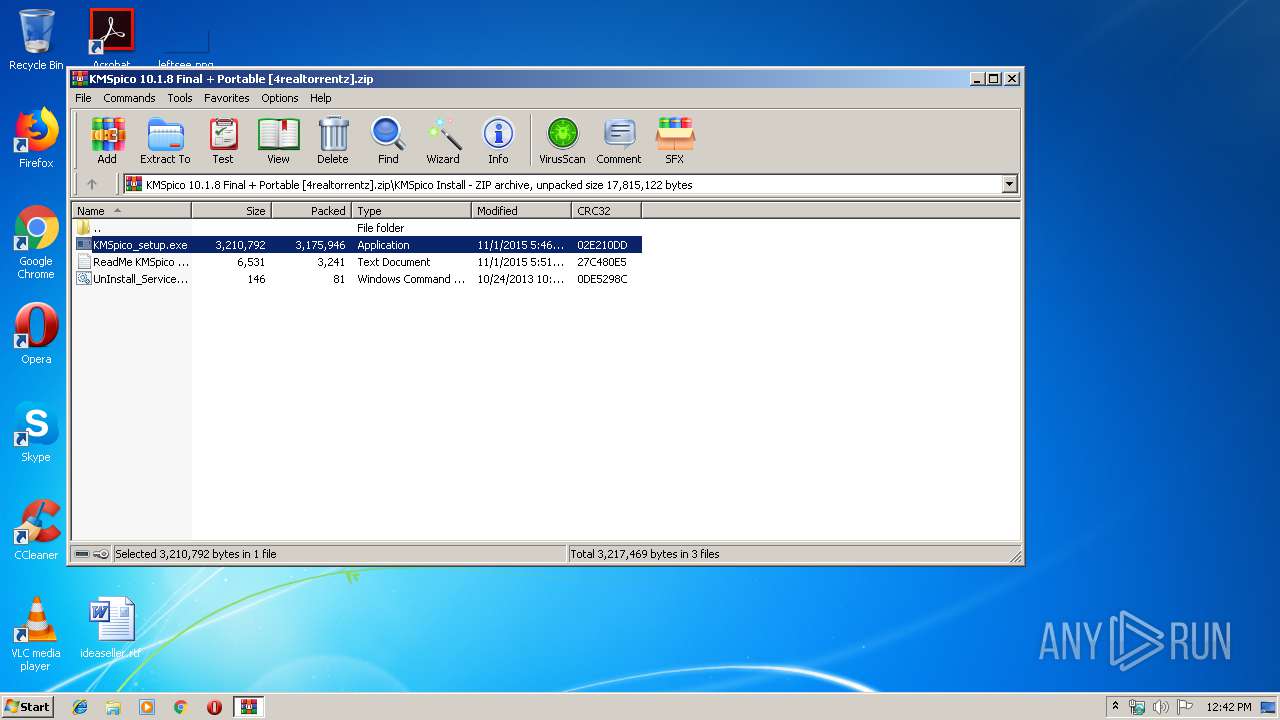
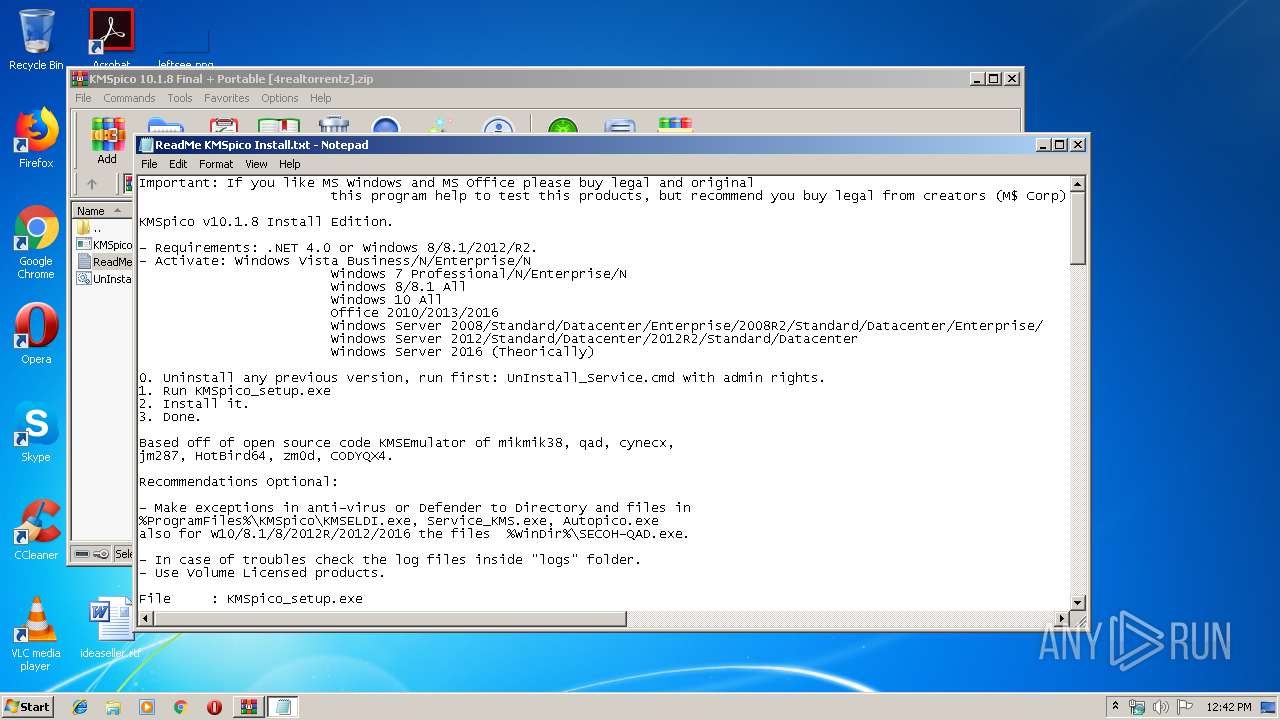
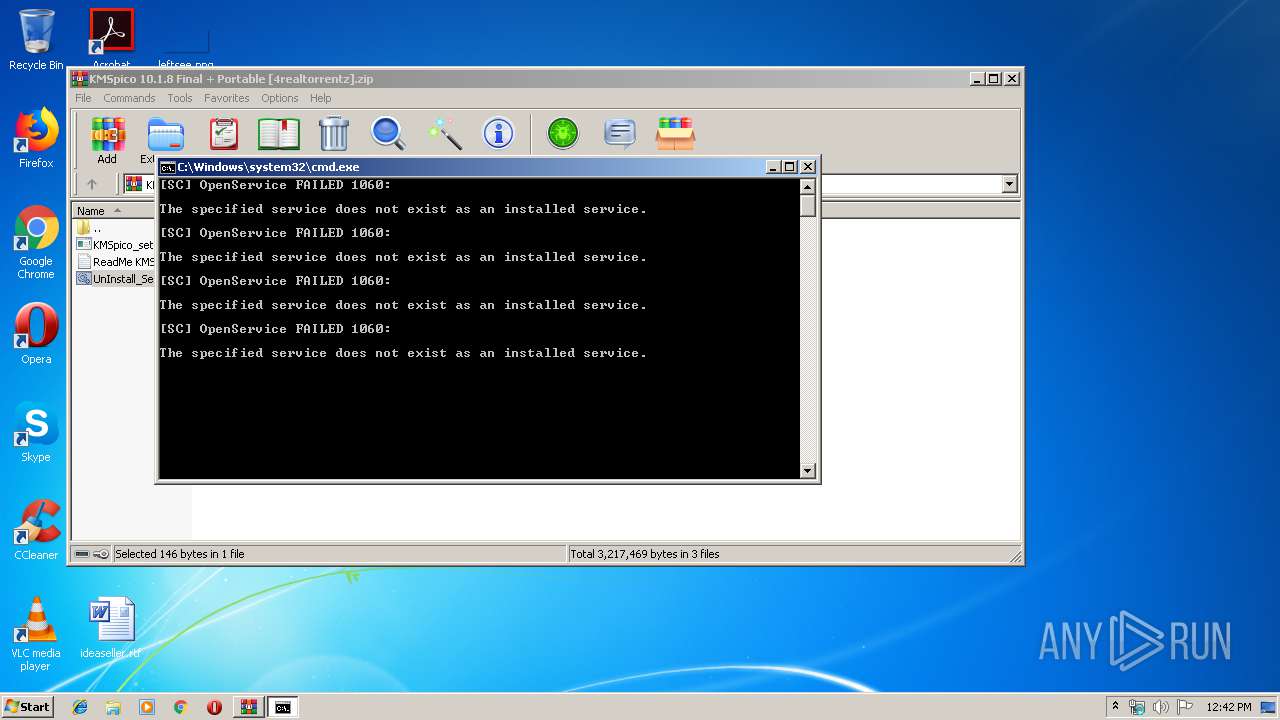
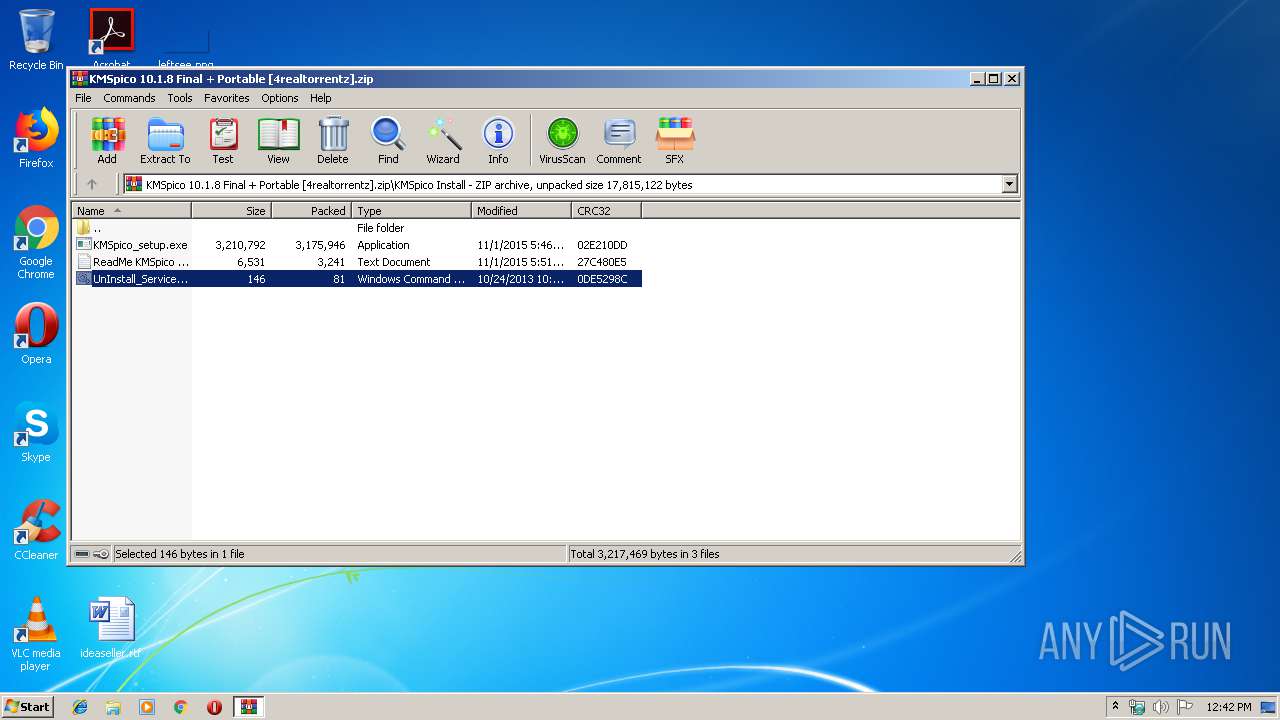
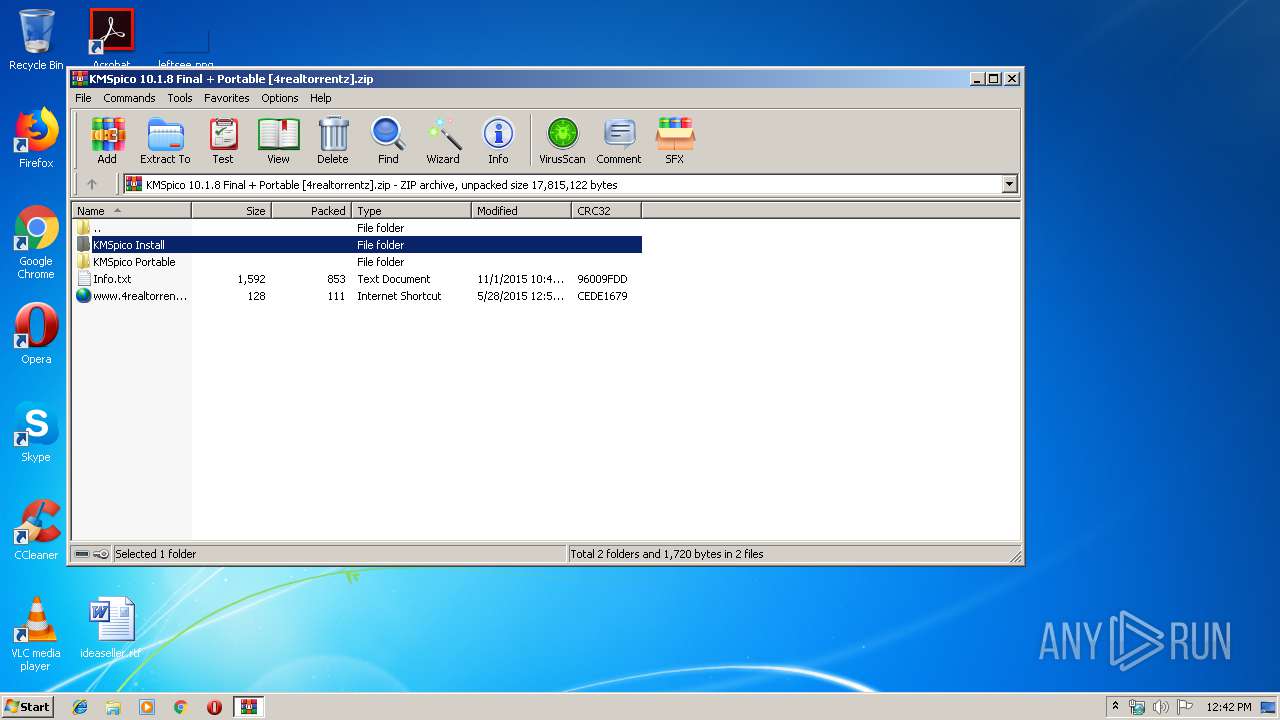
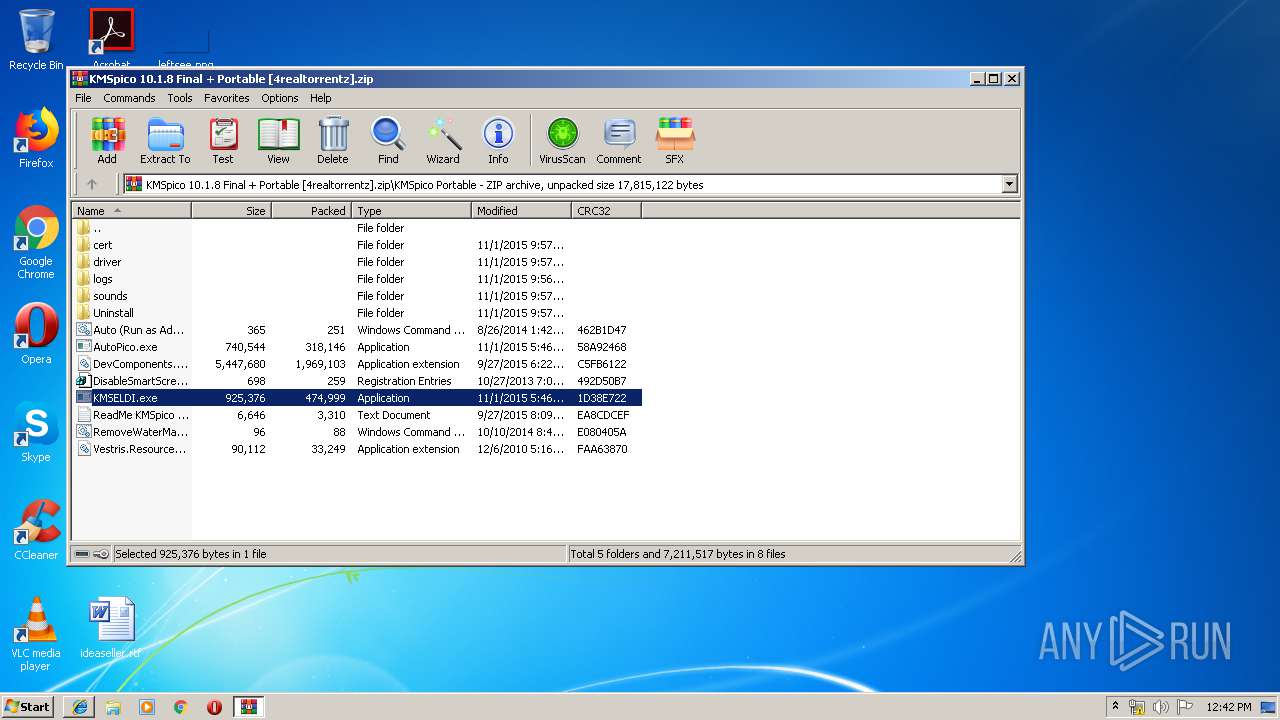
| File name: | KMSpico 10.1.8 Final + Portable [4realtorrentz].zip |
| Full analysis: | https://app.any.run/tasks/1ba6dd08-8320-46a2-9603-750c9c31e8f7 |
| Verdict: | Malicious activity |
| Analysis date: | May 05, 2019, 11:41:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 807AAD729C335CCBD642AF1020F66A19 |
| SHA1: | 1C7A9DF4D891C4F31572A16CEF5355608DC2AA8F |
| SHA256: | 324A7F0171C106ACD368BCFFC527AA79C41D77A969039ACD680BD66A8E90FE37 |
| SSDEEP: | 196608:RKlPipkpqeTOlIj5oexfXvM7gp+ZRnOh1Vm:RKlYZGOlImsfXXp+ZpO9m |
MALICIOUS
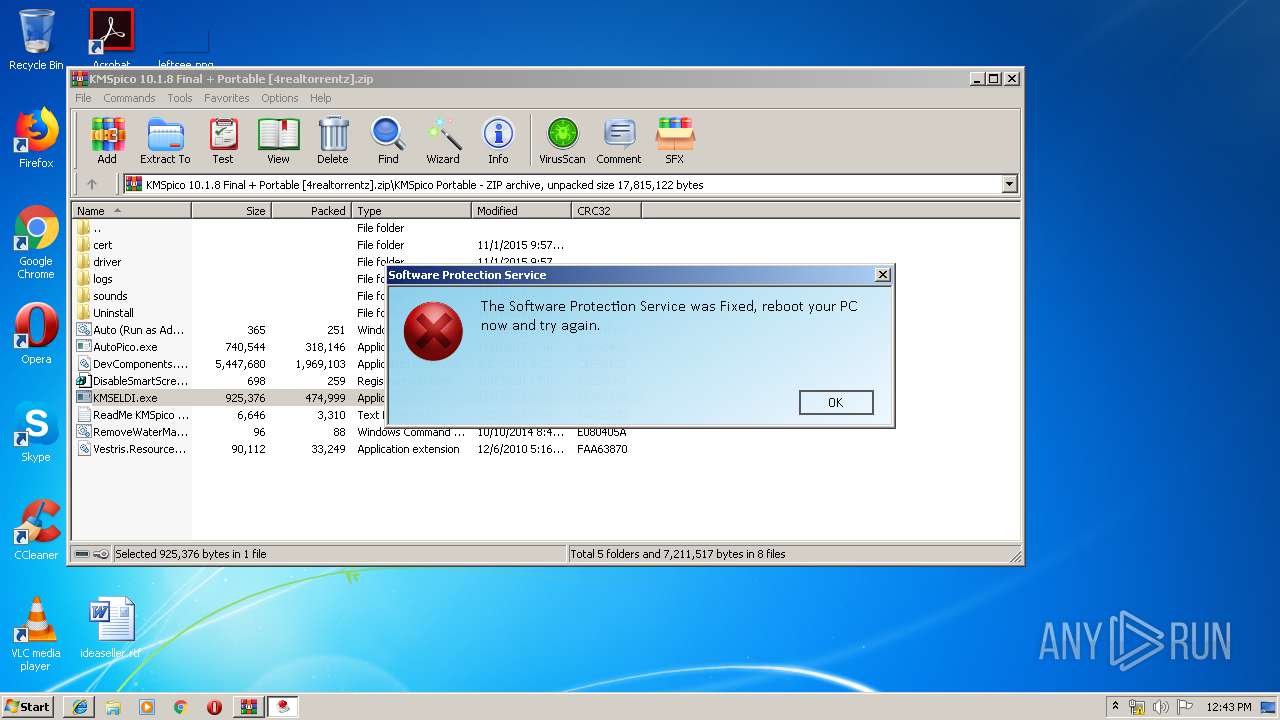
Application was dropped or rewritten from another process
- KMSpico_setup.exe (PID: 2516)
- KMSpico_setup.exe (PID: 2336)
- KMSELDI.exe (PID: 2356)
- KMSELDI.exe (PID: 3368)
Loads dropped or rewritten executable
- KMSELDI.exe (PID: 2356)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3140)
- KMSpico_setup.exe (PID: 2336)
- KMSpico_setup.exe (PID: 2516)
- KMSpico_setup.tmp (PID: 2876)
Starts SC.EXE for service management
- cmd.exe (PID: 2668)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3140)
Creates or modifies windows services
- KMSELDI.exe (PID: 2356)
Reads Environment values
- KMSELDI.exe (PID: 2356)
INFO
Loads dropped or rewritten executable
- KMSpico_setup.tmp (PID: 2876)
Application was dropped or rewritten from another process
- KMSpico_setup.tmp (PID: 2748)
- KMSpico_setup.tmp (PID: 2876)
Reads Internet Cache Settings
- iexplore.exe (PID: 3388)
- iexplore.exe (PID: 1680)
Changes internet zones settings
- iexplore.exe (PID: 1680)
Creates files in the user directory
- iexplore.exe (PID: 3388)
Reads settings of System Certificates
- iexplore.exe (PID: 1680)
Reads internet explorer settings
- iexplore.exe (PID: 3388)
Changes settings of System certificates
- iexplore.exe (PID: 1680)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2015:11:01 05:46:20 |
| ZipCRC: | 0x02e210dd |
| ZipCompressedSize: | 3175946 |
| ZipUncompressedSize: | 3210792 |
| ZipFileName: | KMSpico Install/KMSpico_setup.exe |
Total processes
54
Monitored processes
15
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1680 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
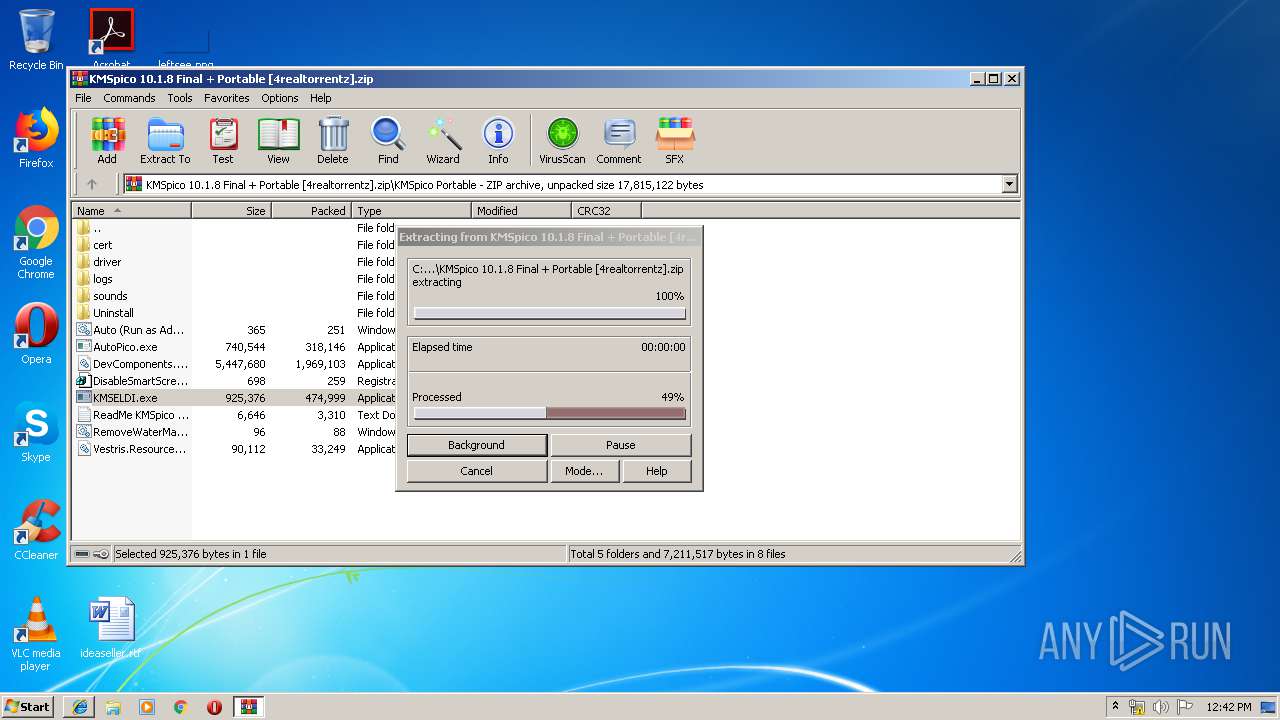
| 2336 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Install\KMSpico_setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Install\KMSpico_setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: KMSpico Setup Exit code: 2 Version: 10.1.8 Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.7723\KMSpico Portable\KMSELDI.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.7723\KMSpico Portable\KMSELDI.exe | WinRAR.exe | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 0 Version: 36.0.0.8 Modules
| |||||||||||||||
| 2516 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Install\KMSpico_setup.exe" /SPAWNWND=$30186 /NOTIFYWND=$5013E | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Install\KMSpico_setup.exe | KMSpico_setup.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: KMSpico Setup Exit code: 2 Version: 10.1.8 Modules
| |||||||||||||||
| 2668 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa3140.5744\UnInstall_Service.cmd" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2748 | "C:\Users\admin\AppData\Local\Temp\is-NMIOJ.tmp\KMSpico_setup.tmp" /SL5="$5013E,2933903,69120,C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Install\KMSpico_setup.exe" | C:\Users\admin\AppData\Local\Temp\is-NMIOJ.tmp\KMSpico_setup.tmp | — | KMSpico_setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 2 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2876 | "C:\Users\admin\AppData\Local\Temp\is-AS5LL.tmp\KMSpico_setup.tmp" /SL5="$40184,2933903,69120,C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Install\KMSpico_setup.exe" /SPAWNWND=$30186 /NOTIFYWND=$5013E | C:\Users\admin\AppData\Local\Temp\is-AS5LL.tmp\KMSpico_setup.tmp | KMSpico_setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 2 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3140 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\KMSpico 10.1.8 Final + Portable [4realtorrentz].zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3256 | sc stop "Service KMSELDI" | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3368 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.7723\KMSpico Portable\KMSELDI.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.7723\KMSpico Portable\KMSELDI.exe | — | WinRAR.exe | |||||||||||
User: admin Company: @ByELDI Integrity Level: MEDIUM Description: KMS GUI ELDI Exit code: 3221226540 Version: 36.0.0.8 Modules
| |||||||||||||||
Total events
1 537
Read events
1 400
Write events
129
Delete events
8
Modification events
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSpico 10.1.8 Final + Portable [4realtorrentz].zip | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-10046 |
Value: Internet Shortcut | |||
Executable files
15
Suspicious files
0
Text files
772
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Install\KMSpico_setup.exe | executable | |
MD5:BD8CB75CD1D80A311D72DB68B7BDE770 | SHA256:88F11ABDD3E82C4FF30C0B67D4AF73E10DF6F83D6CBE0CE4F94FC2B2EBC013B8 | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Portable\cert\kmscert2010\Excel\ExcelVLReg32.reg | text | |
MD5:28BD0428CA20C5E612D7EC795BBB9EA9 | SHA256:3D1A428865F4F4FB5AFDB7CD69F0619C9A5F466EBA160F63DB8ED376C721563C | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Portable\cert\kmscert2010\Access\Access_KMS_Client.RAC_Priv.xrm-ms | xml | |
MD5:A279AB8F8C617DF9C5411FDC199E7676 | SHA256:9084E7F35F7220EC760719B29721A267943178972578E739BDAC2D6475A573E3 | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Install\ReadMe KMSpico Install.txt | text | |
MD5:48CEDF7CFFF080EE0F296B20182DA27B | SHA256:5D2644CBD9EE95B045DDE9A557D3D75A2232133224BD5F8160F18AAA09B97CF6 | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Portable\cert\kmscert2010\Access\Access_KMS_Client.OOB.xrm-ms | xml | |
MD5:3958FF865F2BFBE00BB97D50E250B241 | SHA256:A0213A19815ECB6BE15D08ABFA18FD23BB203937C4700637ABB29B5F5F3DB27F | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Portable\cert\kmscert2010\Excel\Excel_KMS_Client.RAC_Priv.xrm-ms | xml | |
MD5:F337534801463A265E94DD34745B3302 | SHA256:AE237C3EAFD09ED83FFD4A27376703D4DCB3EC2C142D557BDFD3FE1C761690AC | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Portable\cert\kmscert2010\Excel\Excel_KMS_Client.OOB.xrm-ms | xml | |
MD5:14D12F9F6107BBF0C0314FE02FF5DC27 | SHA256:C66AA472011A02DAD09971C29320E55F6B46DF9DCCCE4D9F01EC6D147D9BC99F | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Portable\AutoPico.exe | executable | |
MD5:A69ACB01B99959EFEC7C0A2A8CAA7545 | SHA256:470A75FE3DA2DDF9D27FB3F9C96E6C665506EA7BA26AB89F0C89606F678AE4A2 | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Portable\cert\kmscert2010\Access\AccessVLRegWOW.reg | text | |
MD5:50122EA723FFE7367AD811FC333594C2 | SHA256:18B8099777C8956C4299DA79A44BF9CB3ADDE96B652A0C6D063BF6C9A925B0B8 | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3140.3677\KMSpico Portable\cert\kmscert2010\Access\Access_KMS_Client.PL.xrm-ms | xml | |
MD5:CEE2D16BF6FBA85A5DE6ED12CBADA5BB | SHA256:40040A704FA891D7EA4F5791759023527B3C024A94EE76F1CDCB01C71B8E9898 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
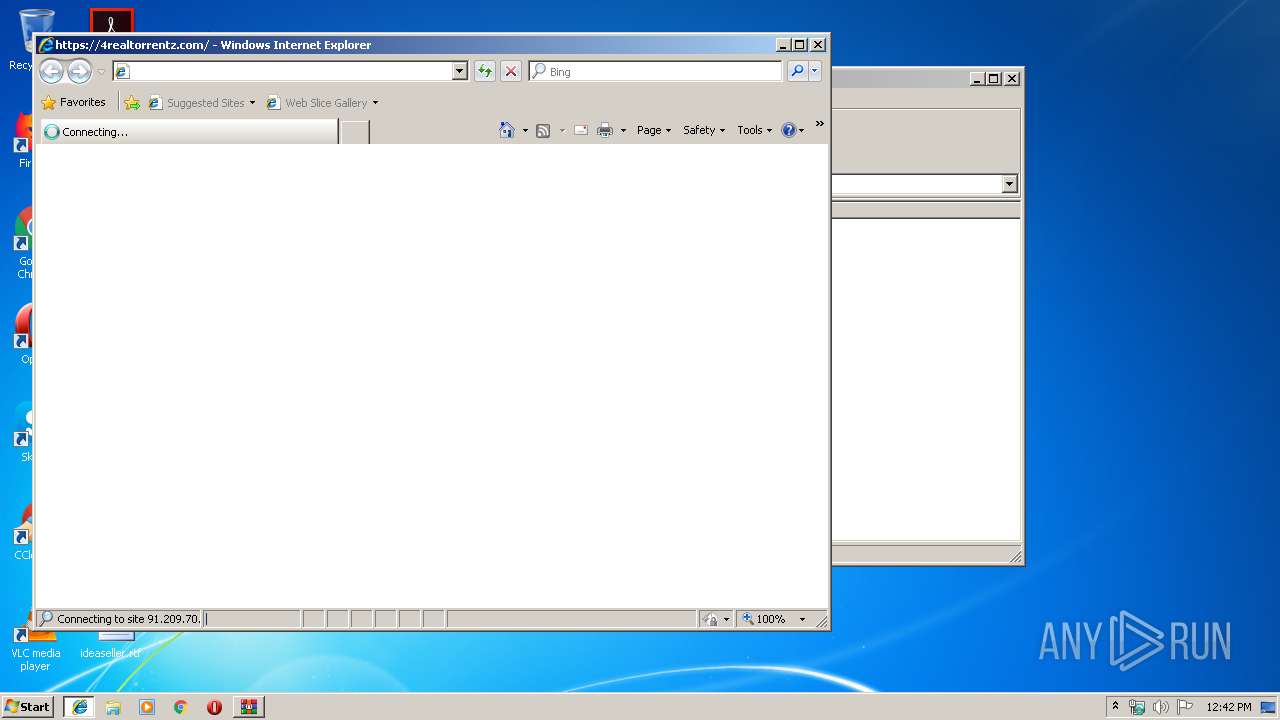
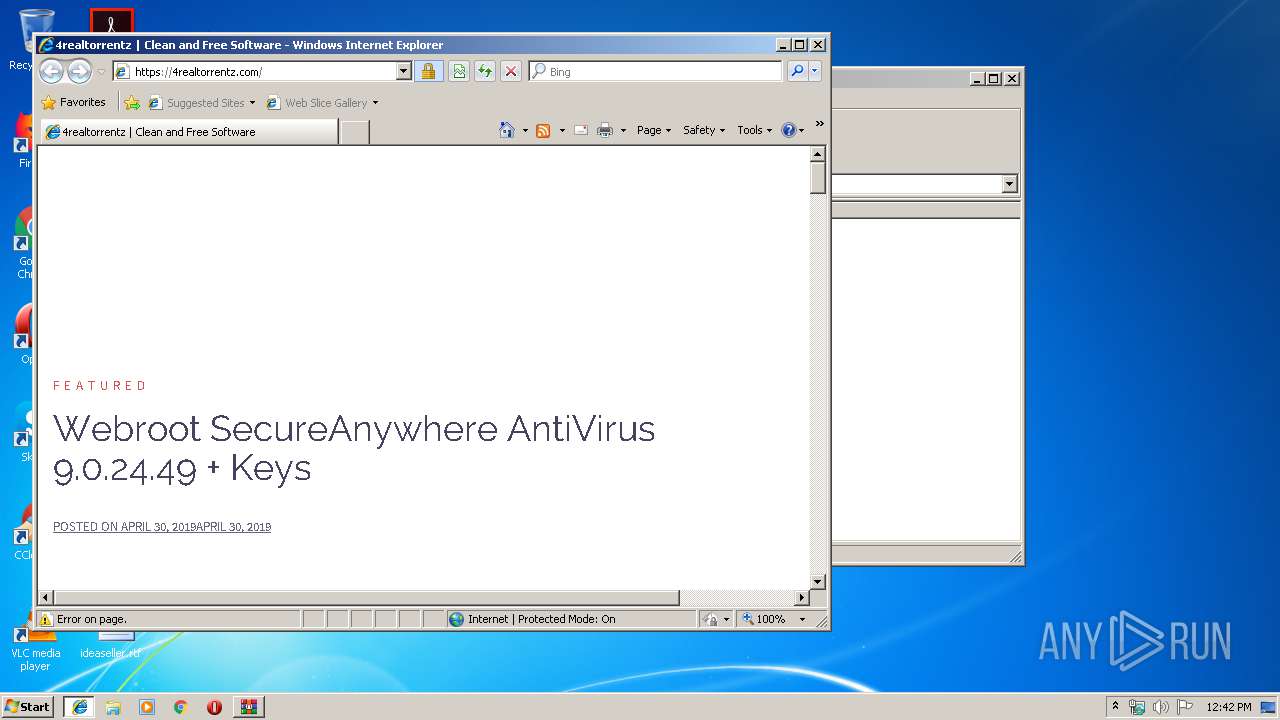
3388 | iexplore.exe | GET | 301 | 91.209.70.107:80 | http://www.4realtorrentz.com/ | RU | binary | 20 b | malicious |
1680 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1680 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3388 | iexplore.exe | 91.209.70.107:80 | www.4realtorrentz.com | OOO Fishnet Communications | RU | unknown |
3388 | iexplore.exe | 91.209.70.107:443 | www.4realtorrentz.com | OOO Fishnet Communications | RU | unknown |
3388 | iexplore.exe | 172.217.23.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3388 | iexplore.exe | 216.58.205.227:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3388 | iexplore.exe | 192.0.78.17:443 | wordpress.com | Automattic, Inc | US | unknown |
3388 | iexplore.exe | 192.0.77.2:443 | i0.wp.com | Automattic, Inc | US | suspicious |
3388 | iexplore.exe | 192.0.76.3:443 | stats.wp.com | Automattic, Inc | US | suspicious |
3388 | iexplore.exe | 192.0.77.32:443 | s0.wp.com | Automattic, Inc | US | suspicious |
3388 | iexplore.exe | 185.60.216.19:443 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.4realtorrentz.com |
| malicious |
c0.wp.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
wordpress.com |
| whitelisted |
i0.wp.com |
| whitelisted |
i2.wp.com |
| whitelisted |
i1.wp.com |
| whitelisted |
stats.wp.com |
| whitelisted |