| File name: | broken_phishing1.docx.bin |
| Full analysis: | https://app.any.run/tasks/cf4c4a99-6641-4ba9-8af4-510865bd9333 |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2024, 09:33:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive, with extra data prepended |
| MD5: | 44A464C5E8266FADE272C3E5B24FECCF |
| SHA1: | 5A9974BD044B3A739E035438A6E4E056F533936D |
| SHA256: | 3245CA6C7F9F78E6B8FC0F05E7821E4B4E0D1ABF24719D9457A7640F3F447C58 |
| SSDEEP: | 1536:phMDIDDhBhDsdoDsjhLhnFDkeDT+IxfpDIf2M2hMDIDDhBhDsdoDsjhLhIDFDkfx:phMDIDDhBhDsdoDsjhLhnFDkeDT+IxfE |
MALICIOUS
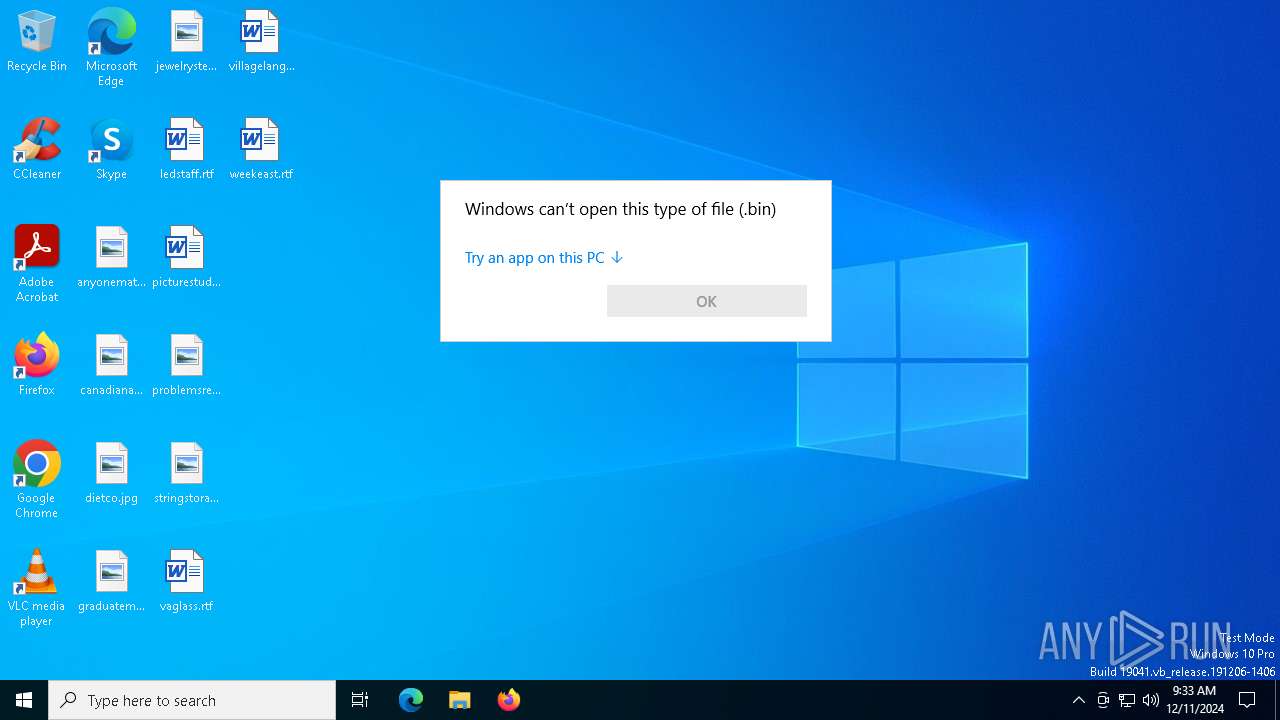
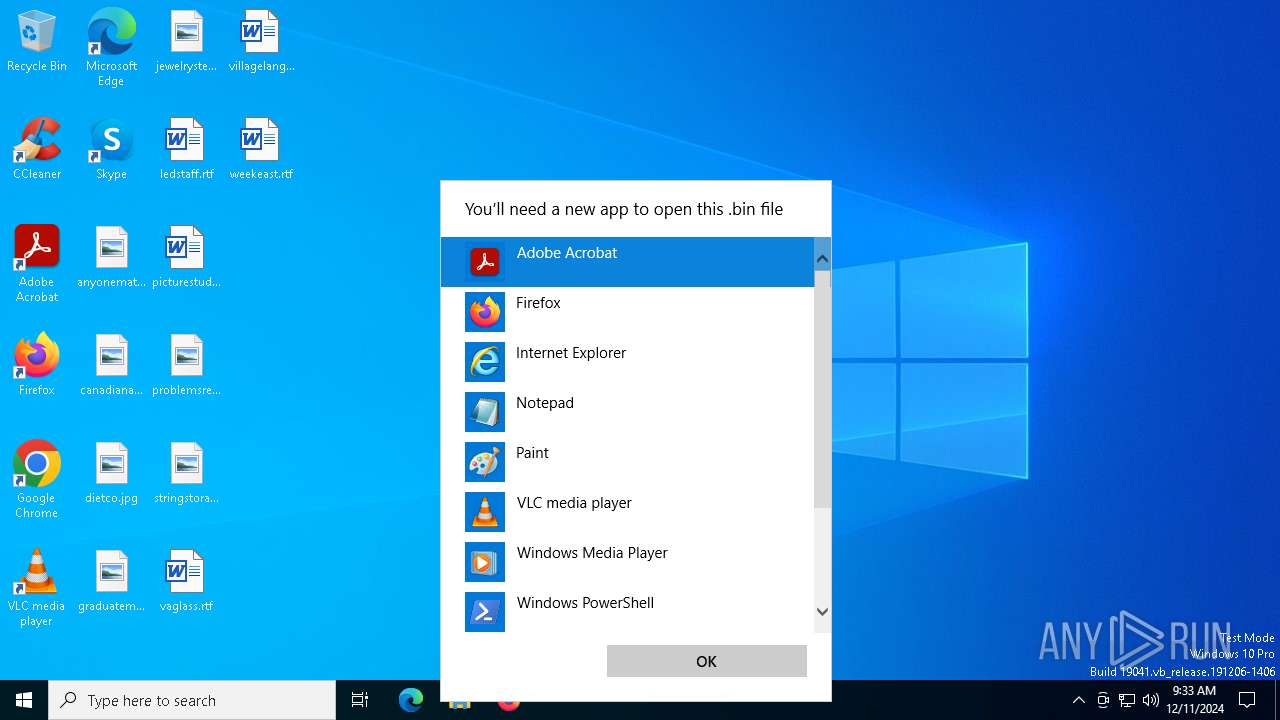
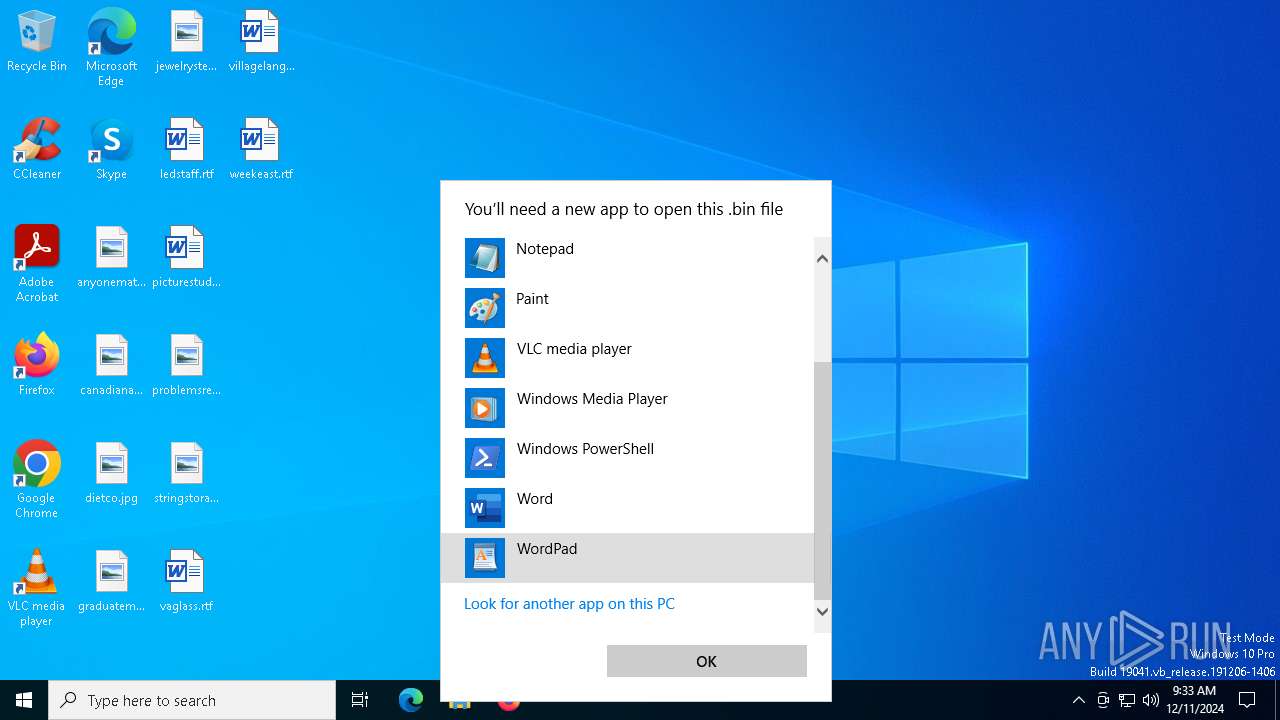
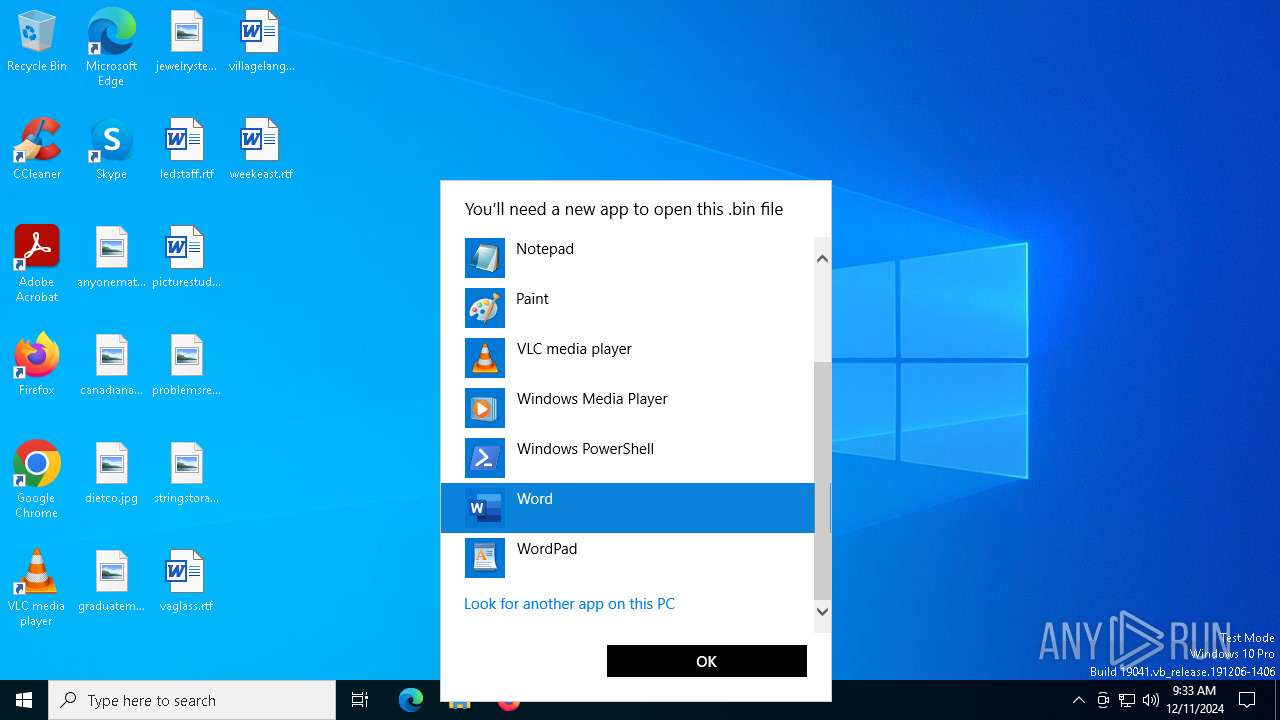
A deliberately damaged file exploiting the Office/Archive self-repair mechanism has been detected (suspicious first bytes)
- OpenWith.exe (PID: 6476)
SUSPICIOUS
No suspicious indicators.INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6476)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 6476)
Sends debugging messages
- WINWORD.EXE (PID: 1512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
133
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
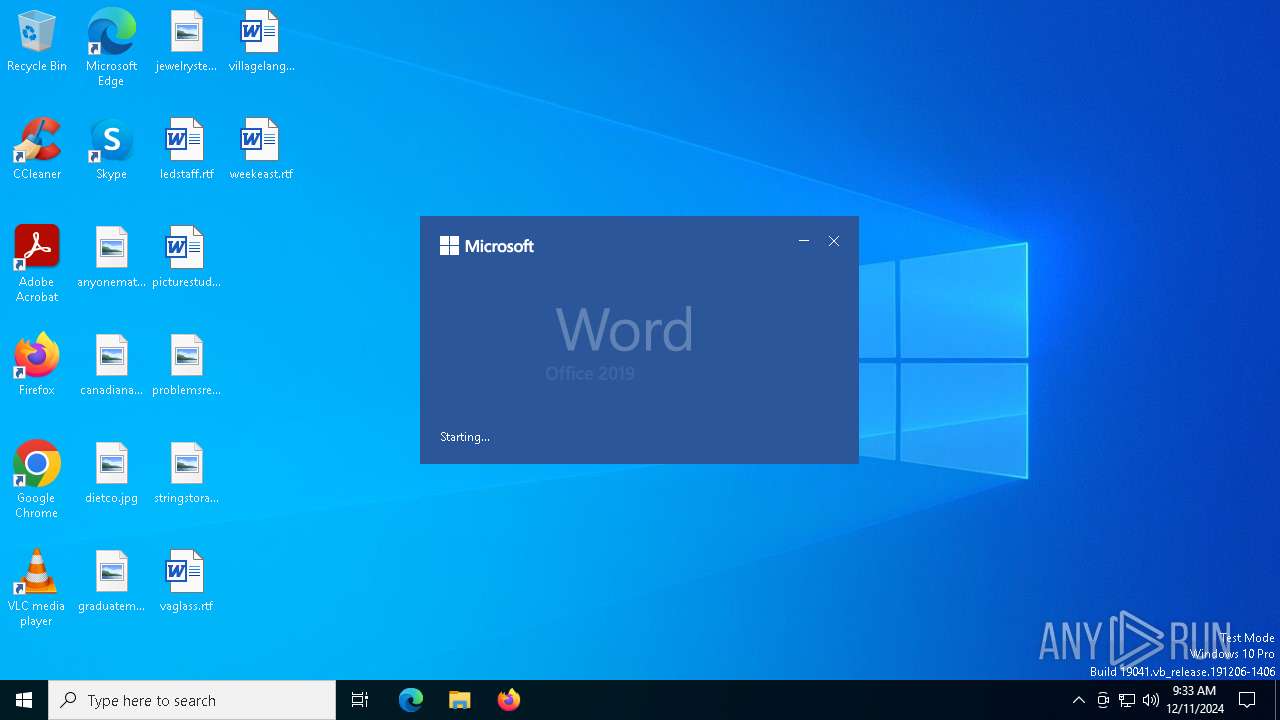
| 1512 | "C:\Program Files\Microsoft Office\root\Office16\Winword.exe" /n "C:\Users\admin\AppData\Local\Temp\broken_phishing1.docx.bin" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | OpenWith.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6476 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\AppData\Local\Temp\broken_phishing1.docx.bin | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7156 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "478101D1-2BDF-4593-87EC-0CA3AD2A68D5" "1518779E-2631-4B6F-9460-1F9A938F08E4" "1512" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
14 461
Read events
14 104
Write events
329
Delete events
28
Modification events
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\1512 |
| Operation: | write | Name: | 0 |
Value: 0B0E107ABFEB65E7B5344DB29EDFC8E23A671A230046C88A91B8FCF5D2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511E80BD2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (1512) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
6
Suspicious files
136
Text files
42
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:208708BFB45252D979AB5BA44053C609 | SHA256:936F238FE633EE6E5783B80325311FD09C63C0471B094D95B990FD52BA57FD2B | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\3694F7E6-B9E1-4A29-BAE4-F1DEDE5339DE | xml | |
MD5:72E7D4A4F4B6DD81E90A8F1966C5F304 | SHA256:028D9D61E9E6CF8A10B84DD805B600D45BF8D0FB871536D05D37AC006CAAA8DB | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:937C4372AA8F2D7A4E0CD693FE9C4280 | SHA256:DE042D141103D4B40C45F2D44A73D79776A22E6741101E4BB5752EDAA015DED6 | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:6C4FD3566D6954F2DB7FE114393FE38D | SHA256:0E3AA895FE37D0C29966A88FE14B71852B6B0571AFF6E789D69D92B74C5215AD | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRD0000.doc | binary | |
MD5:2FCFE7FD02C682BF9360DBC68105FAA1 | SHA256:AE893B242EC9361BC3E956E5537E2B664678A1831140B7C5EE57FF1FAFE010E0 | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:F95EBD31B77436D07942E1E9D9E40E6A | SHA256:B8DD2B3B3289E079B2FBDFF0A85786A73E7AE96855F1EB51A12C79A70A3F3CB9 | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:9FEB3A866A7AD8D492102151D53F85D2 | SHA256:5086AEF3A1C96E913B3A8DC570AE95BBDED4FC5C0B4ABAA6C634ECEA3C727F78 | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_40.ttf | binary | |
MD5:4296A064B917926682E7EED650D4A745 | SHA256:E04E41C74D6C78213BA1588BACEE64B42C0EDECE85224C474A714F39960D8083 | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRD0002.doc | binary | |
MD5:B210E9CDD7722A8D3575E5B76F0813D8 | SHA256:4AFBA1568004779D2B558229B107D8943E40BCA6D570FC45645C8F15AFFA82D7 | |||
| 1512 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRD0003.doc | binary | |
MD5:15954568C82298516E126506E6E5C590 | SHA256:79C6CECEC7EC44626C32AC4554F8606122B8F45BF72E9B9043771A82473945ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
76
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6708 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6204 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1512 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1512 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6204 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1512 | WINWORD.EXE | GET | 200 | 2.16.164.98:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|