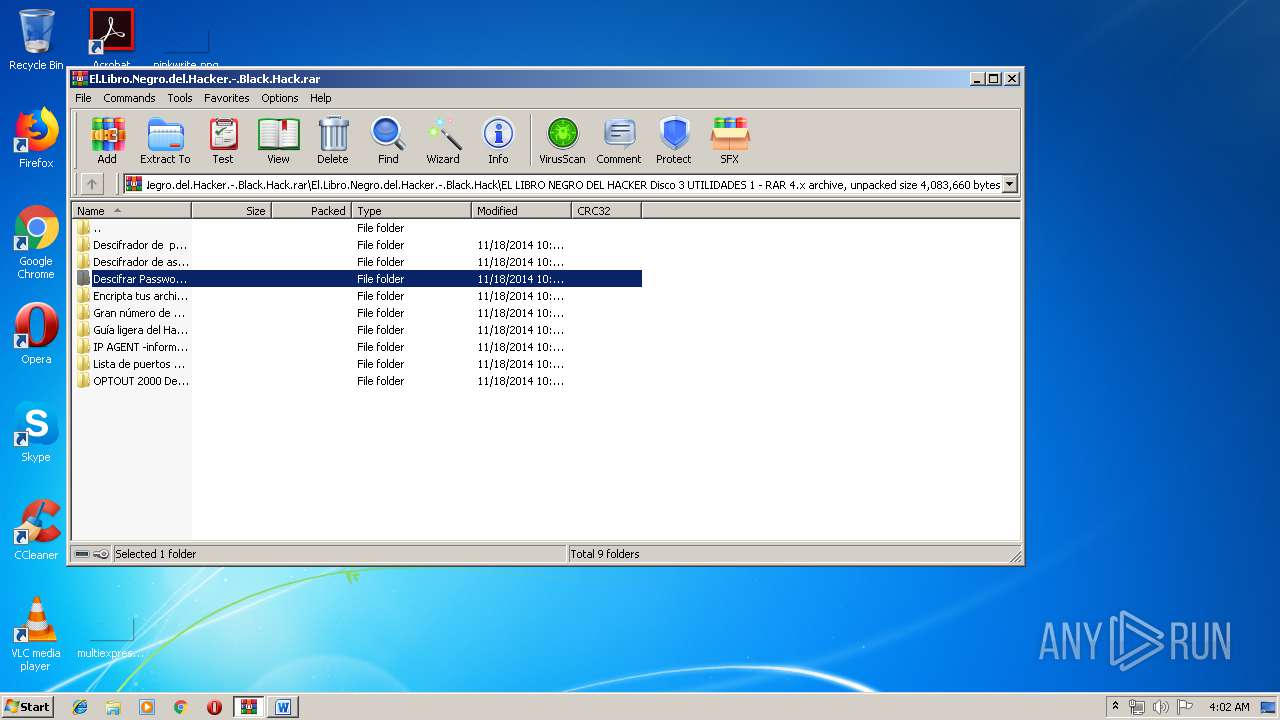
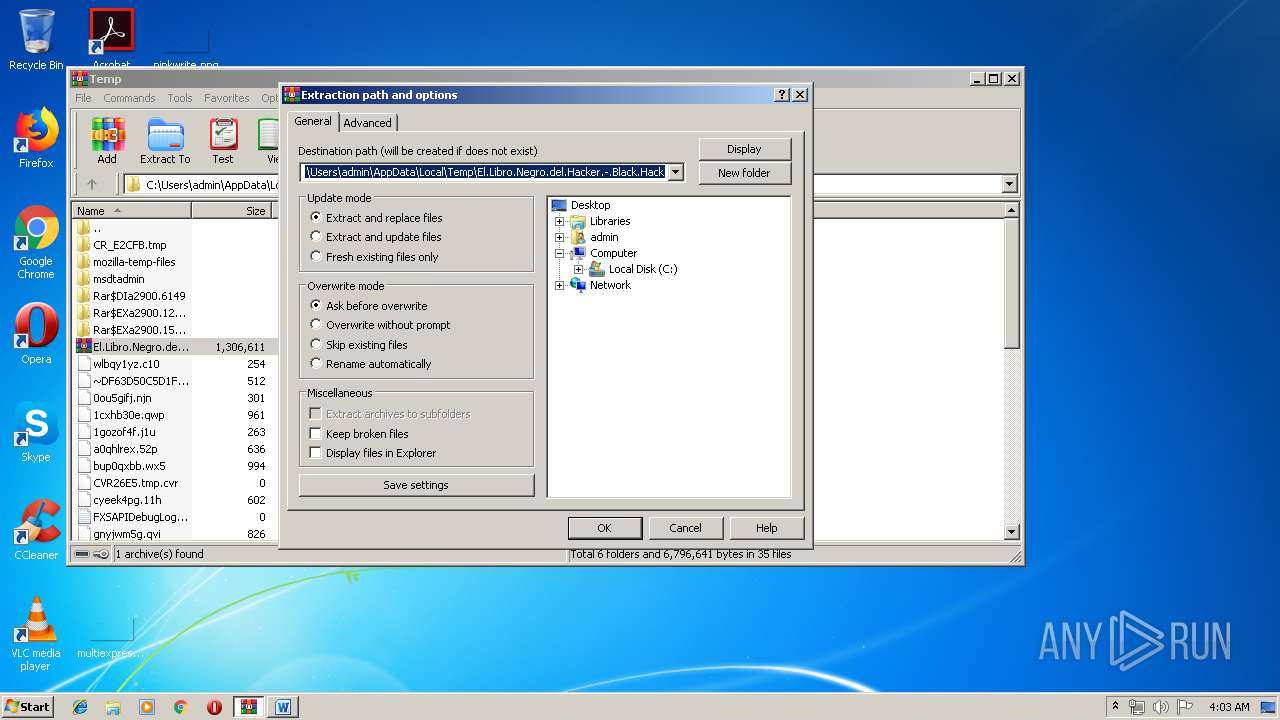
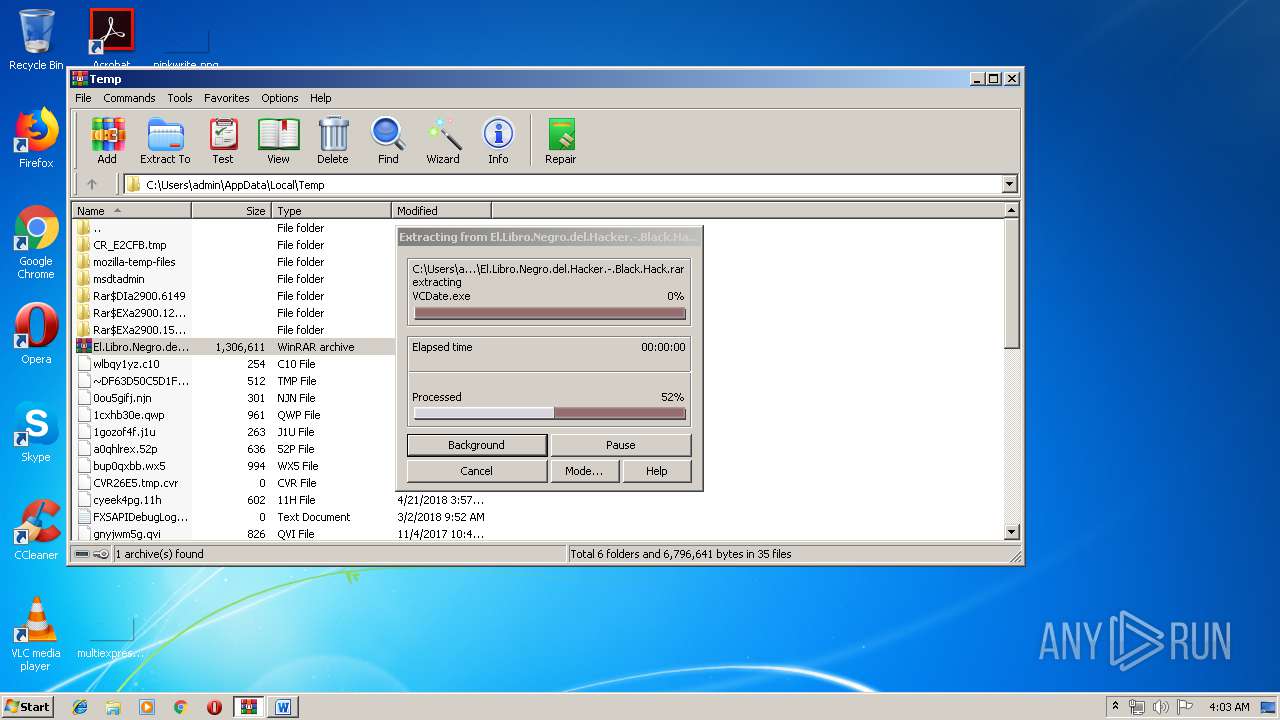
| File name: | El.Libro.Negro.del.Hacker.-.Black.Hack.rar |
| Full analysis: | https://app.any.run/tasks/1d39fb01-c21e-4a00-91a7-5d43d3a34ac7 |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2019, 03:00:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: RecoveryRecordPresent |
| MD5: | E7C56FCF5200A46F32DC98631110D908 |
| SHA1: | A8DA61393C8922F316C787197BEA9EB368B16388 |
| SHA256: | 3244E723F2C13684B7D1515F0A94A264C38D71A022E4EE801D3FFA66ABDF8E54 |
| SSDEEP: | 24576:O+c/bW4uHdVx0GDv1t0tDRMi353a+U9XqONF6Z3d8jOZvLP7CSxxTalae:qNu9H16dfG0QA3uqLPm4x+8e |
MALICIOUS
Application was dropped or rewritten from another process
- Setup.exe (PID: 1088)
- Setup.exe (PID: 1924)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2196)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 2900)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2900)
INFO
Manual execution by user
- WINWORD.EXE (PID: 2848)
- WINWORD.EXE (PID: 2940)
- WINWORD.EXE (PID: 2452)
Creates files in the user directory
- WINWORD.EXE (PID: 2060)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2848)
- WINWORD.EXE (PID: 2060)
- WINWORD.EXE (PID: 2940)
- WINWORD.EXE (PID: 2452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 7260 |
|---|---|
| UncompressedSize: | 29184 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2004:01:19 14:22:01 |
| PackingMethod: | Best Compression |
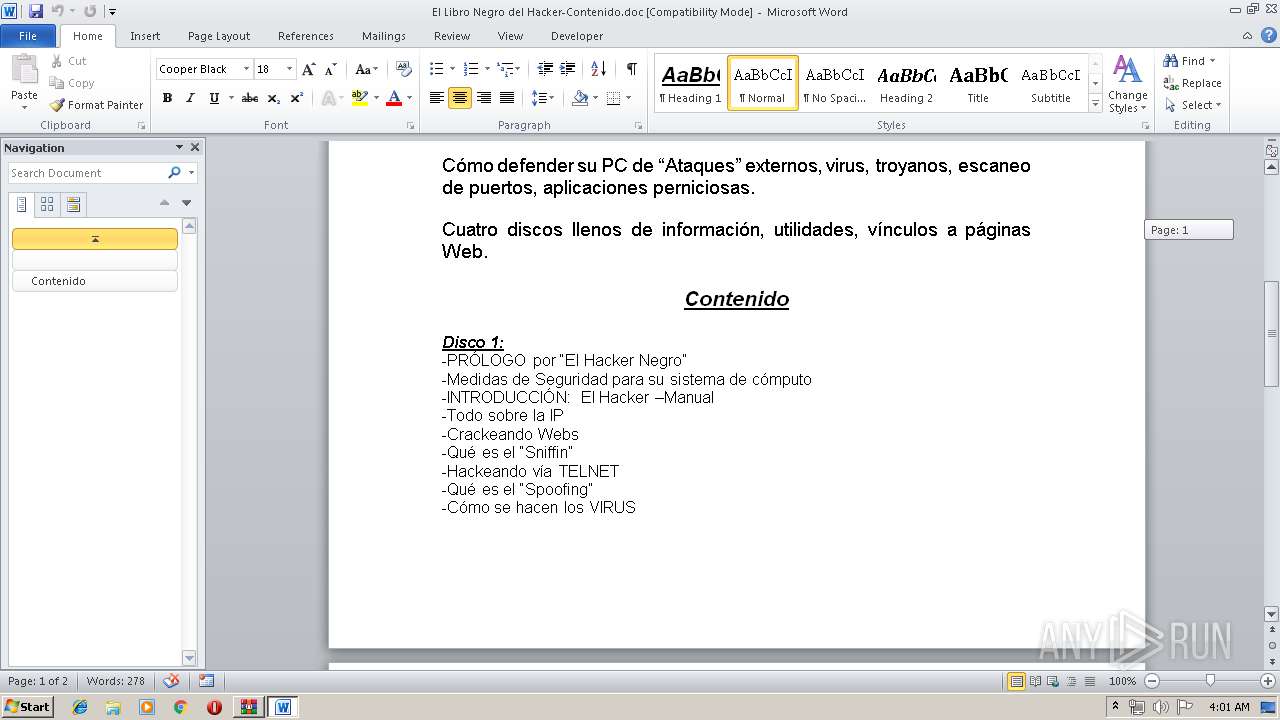
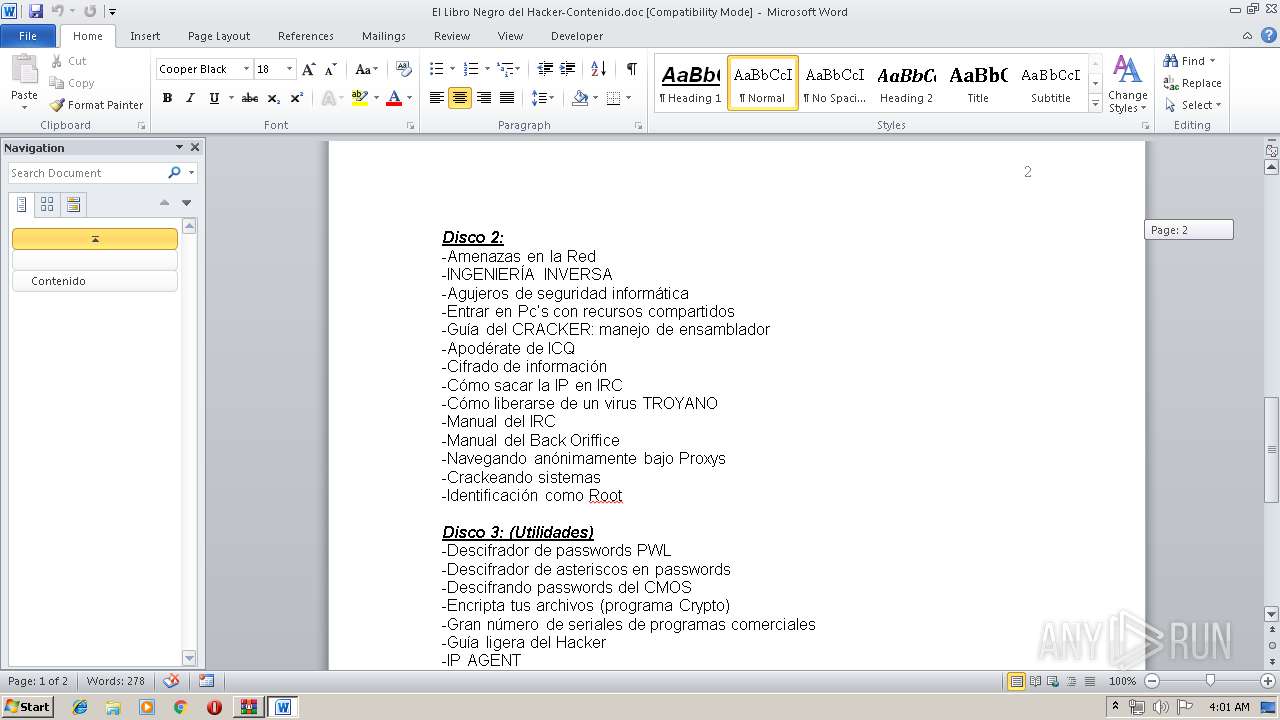
| ArchivedFileName: | El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 1\A. Pr?logo\El Libro Negro del Hacker-Contenido.doc |
Total processes
55
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
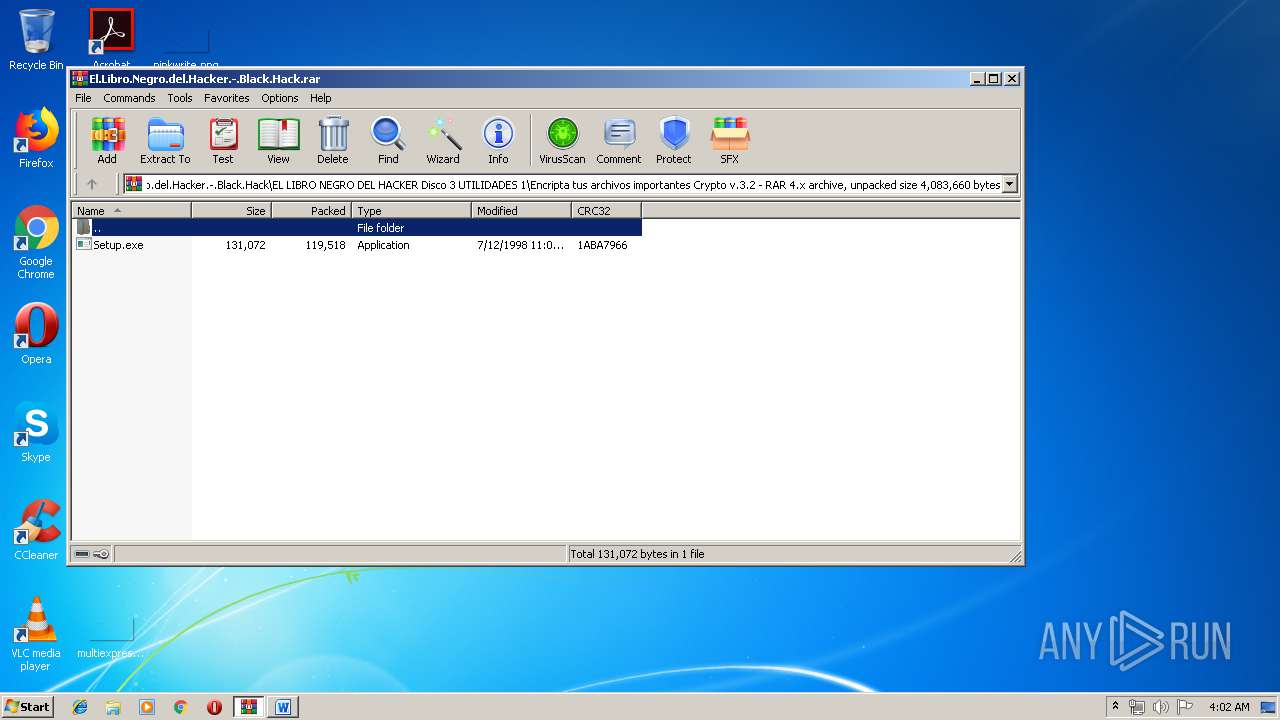
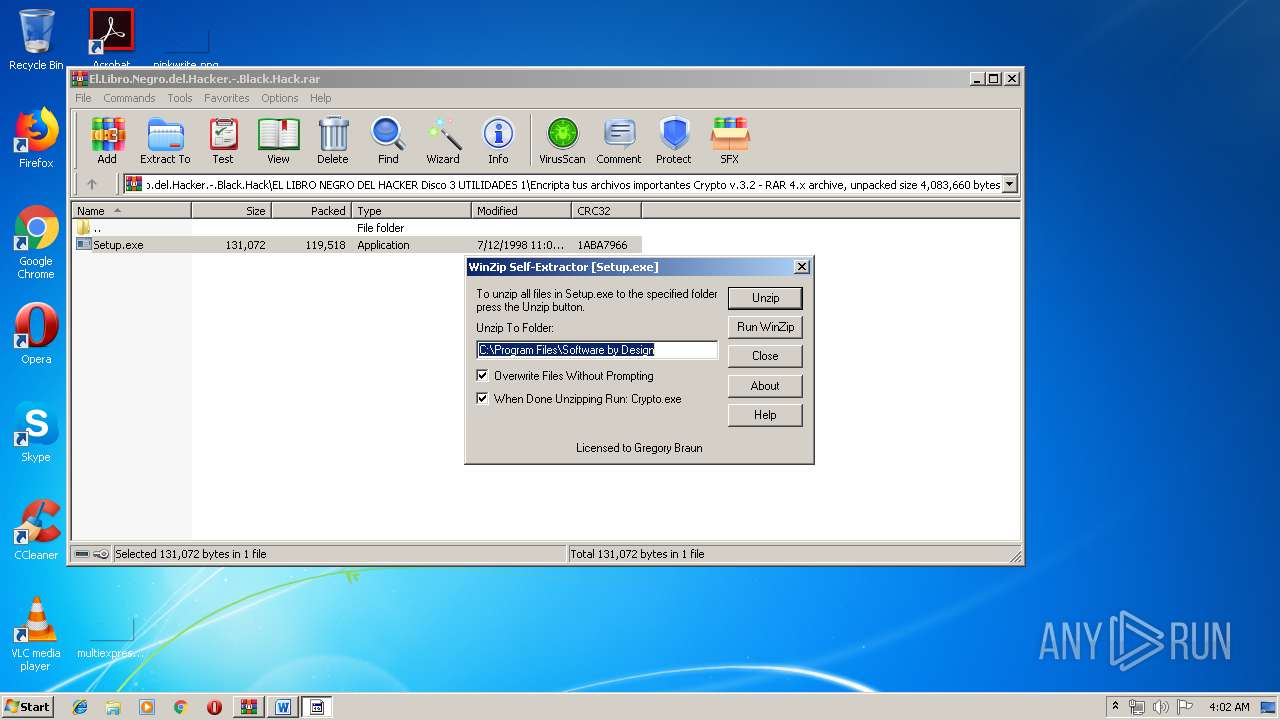
| 1088 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2900.15091\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 3 UTILIDADES 1\Encripta tus archivos importantes Crypto v.3.2\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2900.15091\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 3 UTILIDADES 1\Encripta tus archivos importantes Crypto v.3.2\Setup.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1924 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2900.15091\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 3 UTILIDADES 1\Encripta tus archivos importantes Crypto v.3.2\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2900.15091\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 3 UTILIDADES 1\Encripta tus archivos importantes Crypto v.3.2\Setup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIa2900.6149\El Libro Negro del Hacker-Contenido.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2196 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe14_ Global\UsGthrCtrlFltPipeMssGthrPipe14 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 2\T. Crackeando Sistemas\Sistema.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2848 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 1\D. Todo sobre la IP\IP.DOC" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2900 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\El.Libro.Negro.del.Hacker.-.Black.Hack.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2940 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 1\H. Spoofing\SPOOFING.DOC" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 554
Read events
2 080
Write events
428
Delete events
46
Modification events
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\El.Libro.Negro.del.Hacker.-.Black.Hack.rar | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | e&9 |
Value: 652639000C080000010000000000000000000000 | |||
| (PID) Process: | (2060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
Executable files
42
Suspicious files
70
Text files
115
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR26E5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2060 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIa2900.6149\~$ Libro Negro del Hacker-Contenido.doc | pgc | |
MD5:— | SHA256:— | |||
| 2060 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryES0c0a.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2900.6149\El Libro Negro del Hacker-Contenido.doc | document | |
MD5:0545FF945D3684E4D630C61AF3842AB4 | SHA256:1E4E7243E05588AF4B9D31BBC5FD8CF191143B6331CC0D2310BE5C4C9C6904D0 | |||
| 2900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2900.12729\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 1\A. Prólogo\El Libro Negro del Hacker-Contenido.doc | document | |
MD5:0545FF945D3684E4D630C61AF3842AB4 | SHA256:1E4E7243E05588AF4B9D31BBC5FD8CF191143B6331CC0D2310BE5C4C9C6904D0 | |||
| 2060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2CBB67F0.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2900.12729\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 1\B. MEDIDAS DE SEGURIDAD ¡peligro!\Medidas de Seguridad.doc | document | |
MD5:F9153F9643AEDB219E3CC002CD9BDDC7 | SHA256:6B2520281EED09A6942C83C3E3E63AFFF65DC491FE267375DF84BB713EEC5B73 | |||
| 2900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2900.12729\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 1\G. Hackear via Telnet\Guia1_5.htm | html | |
MD5:C3B7BC59177B53DE7488F6505AF020D4 | SHA256:85819A2B35966B7006F9C83CACCDC92CBB874E9E3988B9A2F4AB0847053C9172 | |||
| 2900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2900.12729\El.Libro.Negro.del.Hacker.-.Black.Hack\EL LIBRO NEGRO DEL HACKER Disco 1\F. Sniffing\SNIFFING.DOC | document | |
MD5:F87427E1CAB1B95ABE12E8CD6F7CDA6E | SHA256:F0E8E75089B725F31A526E3E3A42200207468D9BF31EE734F1742C4B408B6D61 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report