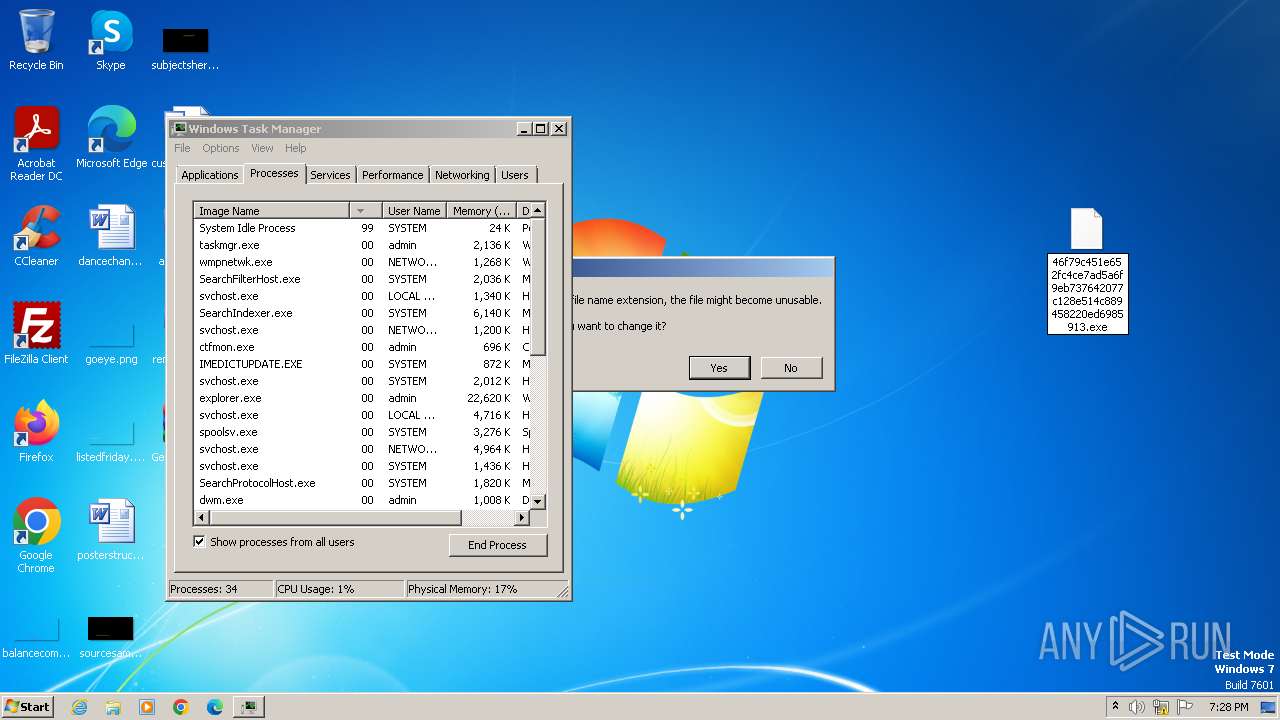
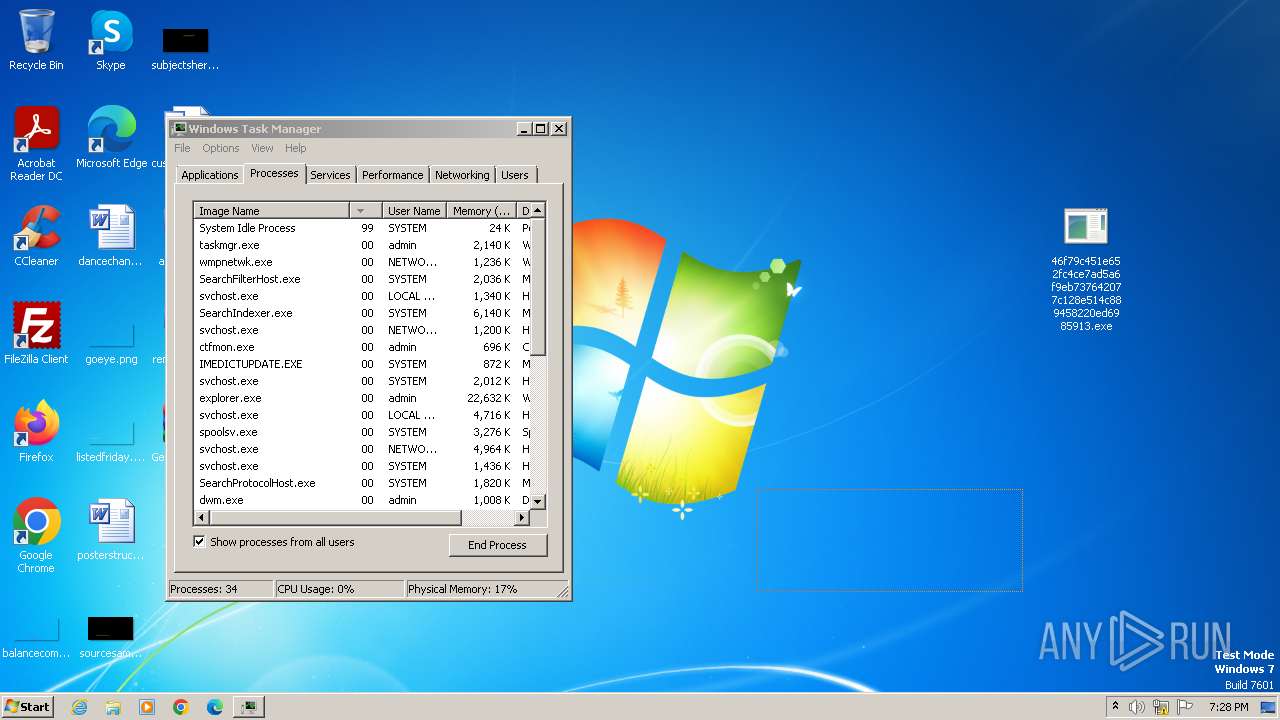
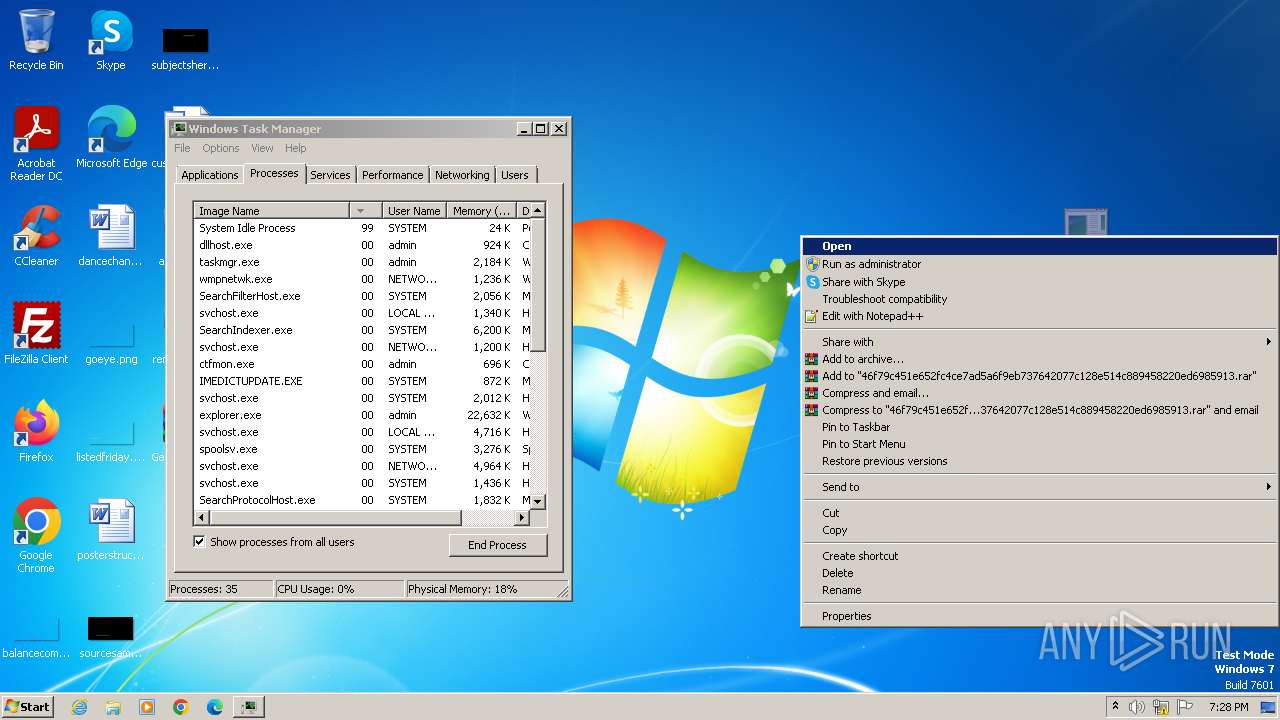
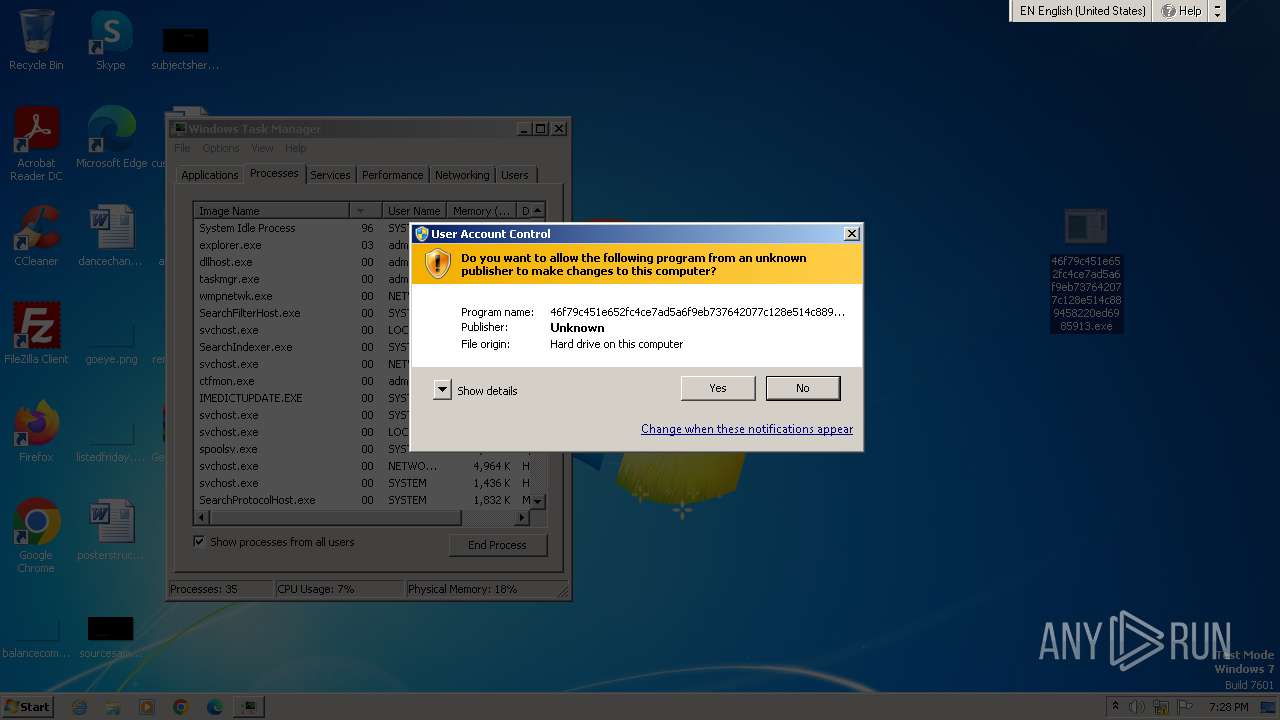
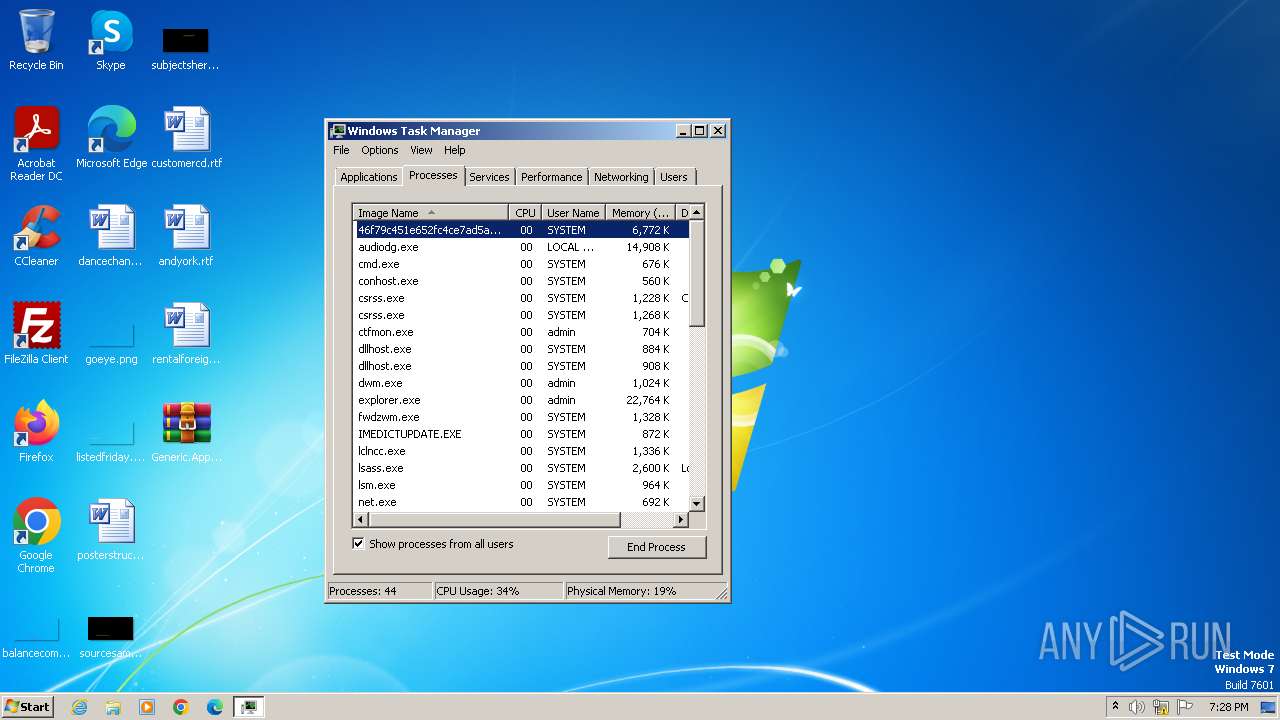
| File name: | Generic.Application.CoinMiner.1.3138E7A5.7z |
| Full analysis: | https://app.any.run/tasks/15939cbb-7c3a-41b5-bea6-582bd69185b0 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2023, 19:27:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | F8F17056031E377BA45A5BDF920C041F |
| SHA1: | AEDFEAA6711440168292CC54102051EB6354F147 |
| SHA256: | 31FF27A58BCE0B4378A3A21A8BFDEE61A480A7BD52F9766133E1B80D33C097C9 |
| SSDEEP: | 98304:aAVrxhrs8Bgm2JDzsavDSf8wcpzhyYP9TcMT4cxVz33SObXGf1iZ4t1wtDAJ1+8w:XYHZBaVM |
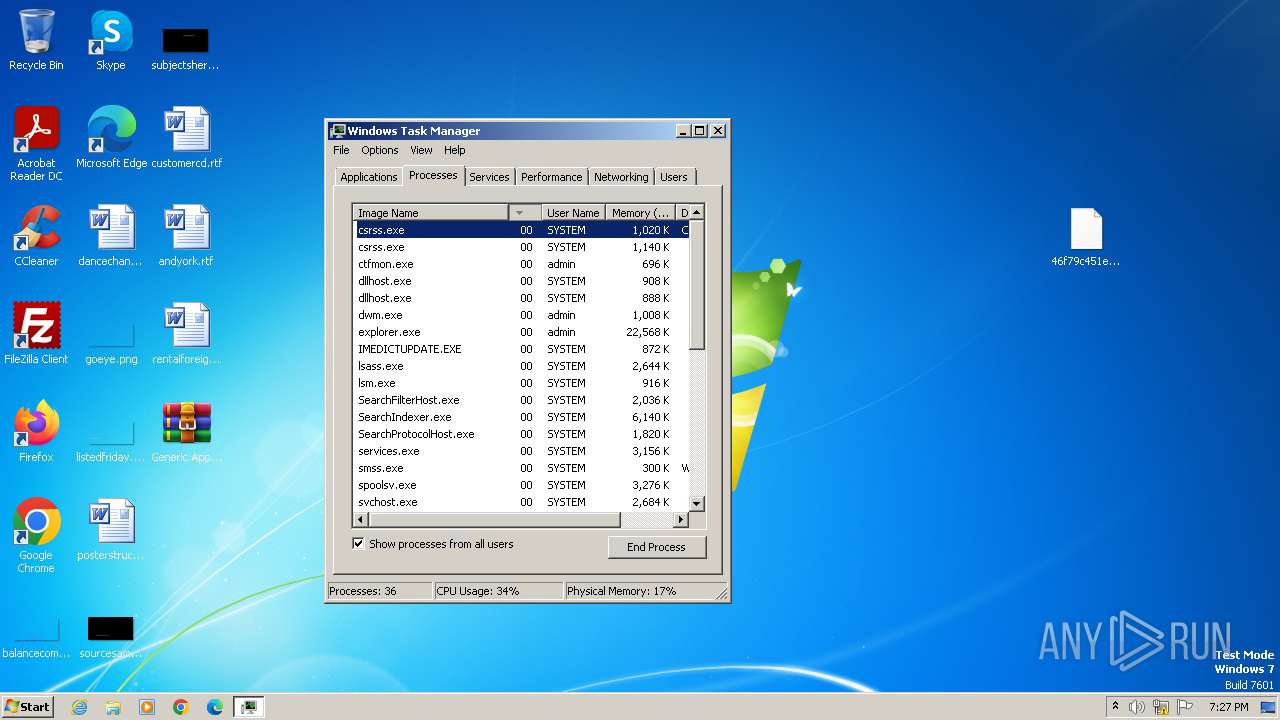
MALICIOUS
Drops the executable file immediately after the start
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3704)
- wimnat.exe (PID: 1832)
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
- opperce.exe (PID: 2096)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1600)
- cmd.exe (PID: 296)
- cmd.exe (PID: 1232)
- cmd.exe (PID: 148)
Starts NET.EXE for service management
- cmd.exe (PID: 1880)
- cmd.exe (PID: 2000)
- cmd.exe (PID: 2028)
- net.exe (PID: 1592)
- net.exe (PID: 1696)
- net.exe (PID: 328)
Uses NET.EXE to stop Windows Defender service
- cmd.exe (PID: 1880)
- net.exe (PID: 1592)
Creates a writable file in the system directory
- wimnat.exe (PID: 1832)
- opperce.exe (PID: 2096)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3440)
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3704)
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
Reads the Internet Settings
- taskmgr.exe (PID: 3228)
- taskmgr.exe (PID: 1948)
Application launched itself
- taskmgr.exe (PID: 3228)
- taskmgr.exe (PID: 1948)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 2152)
Executes as Windows Service
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
- lclncc.exe (PID: 3780)
- fwdzwm.exe (PID: 2176)
Connects to unusual port
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
Starts CMD.EXE for commands execution
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 2812)
The process creates files with name similar to system file names
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
Starts SC.EXE for service management
- cmd.exe (PID: 2084)
Creates or modifies Windows services
- wimnat.exe (PID: 1832)
- opperce.exe (PID: 2096)
The process executes via Task Scheduler
- cmd.exe (PID: 2812)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 2912)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2152)
- cmd.exe (PID: 2812)
INFO
Manual execution by a user
- taskmgr.exe (PID: 3228)
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3704)
- taskmgr.exe (PID: 1948)
Checks supported languages
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3704)
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
- taskmgr.exe (PID: 1616)
- taskmgr.exe (PID: 1296)
- wimnat.exe (PID: 1832)
- taskmgr.exe (PID: 1816)
- taskmgr.exe (PID: 604)
- taskmgr.exe (PID: 2412)
- opperce.exe (PID: 2096)
- fwdzwm.exe (PID: 2176)
- taskmgr.exe (PID: 1992)
- lclncc.exe (PID: 3780)
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3484)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3440)
Reads the computer name
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3704)
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
- wimnat.exe (PID: 1832)
- lclncc.exe (PID: 3780)
- opperce.exe (PID: 2096)
- fwdzwm.exe (PID: 2176)
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3484)
Reads the machine GUID from the registry
- 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe (PID: 3808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
107
Monitored processes
44
Malicious processes
6
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | cmd /c schtasks /create /sc minute /mo 1 /tn "Netframework" /ru system /tr "cmd /c echo Y|cacls C:\Windows\46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe /p everyone:F" | C:\Windows\System32\cmd.exe | — | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 296 | cmd /c schtasks /create /sc minute /mo 1 /tn "Miscfost" /ru system /tr "cmd /c C:\Windows\ime\46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe" | C:\Windows\System32\cmd.exe | — | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 328 | net stop SharedAccess | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | C:\Windows\TEMP\Networks\taskmgr.exe | C:\Windows\Temp\Networks\taskmgr.exe | — | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Task Manager Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1036 | C:\Windows\system32\net1 stop LanmanServer | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1232 | cmd /c schtasks /create /sc minute /mo 1 /tn "Flash" /ru system /tr "cmd /c echo Y|cacls C:\Windows\TEMP\Networks\taskmgr.exe /p everyone:F" | C:\Windows\System32\cmd.exe | — | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1296 | C:\Windows\TEMP\Networks\taskmgr.exe | C:\Windows\Temp\Networks\taskmgr.exe | — | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Task Manager Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1508 | schtasks /delete /tn * /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1592 | net stop MpsSvc | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1600 | cmd /c schtasks /delete /tn * /f | C:\Windows\System32\cmd.exe | — | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 398
Read events
3 345
Write events
53
Delete events
0
Modification events
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
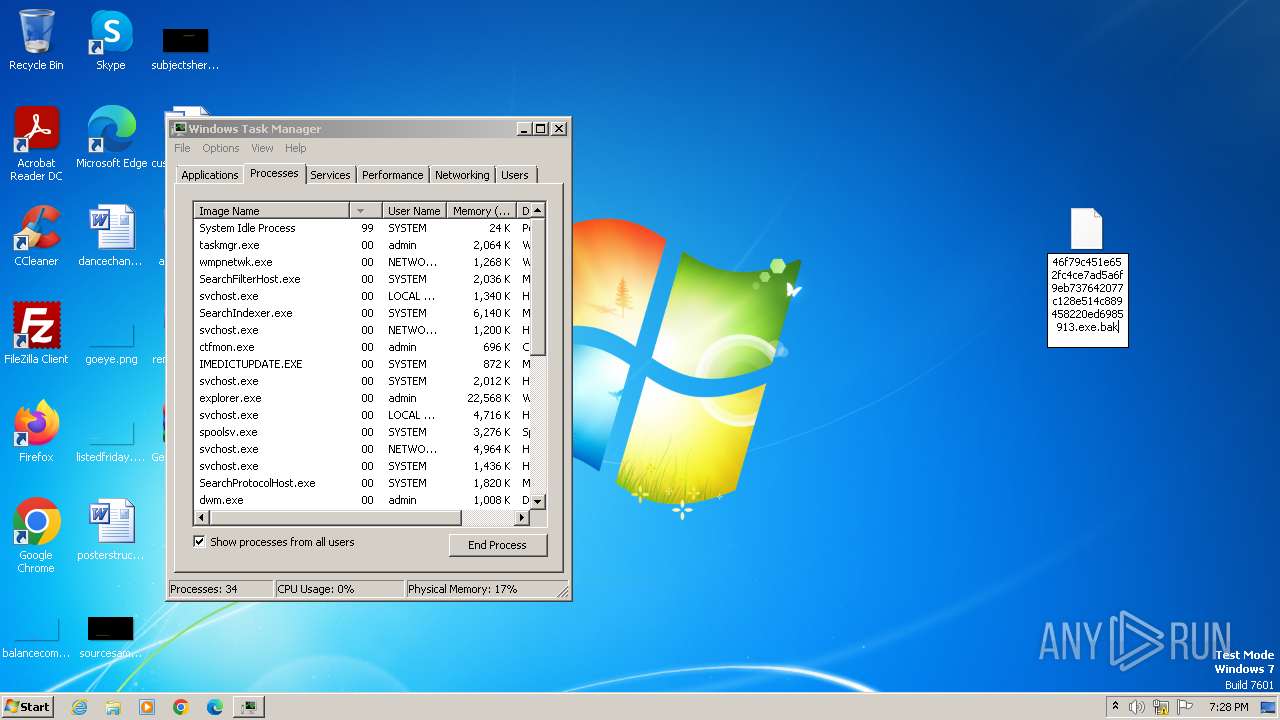
Executable files
52
Suspicious files
23
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3704 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | C:\Windows\46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | executable | |
MD5:C22908FE460312D76B50129AA3EF2CF2 | SHA256:46F79C451E652FC4CE7AD5A6F9EB737642077C128E514C889458220ED6985913 | |||
| 3704 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | C:\Users\admin\AppData\Local\Temp\1508859\....\TemporaryFile | executable | |
MD5:C22908FE460312D76B50129AA3EF2CF2 | SHA256:46F79C451E652FC4CE7AD5A6F9EB737642077C128E514C889458220ED6985913 | |||
| 3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | C:\Windows\TEMP\Networks\taskmgr.exe | executable | |
MD5:048D757EC1B33C9F08FB5C7B00CD2CBA | SHA256:6046E8CAA7B2D2ABF60986F3773B533EF3AFB4BF4AF5F62E234070D12F65BDE9 | |||
| 3440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3440.44512\Generic.Application.CoinMiner.1.3138E7A5\46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe.bak | executable | |
MD5:C22908FE460312D76B50129AA3EF2CF2 | SHA256:46F79C451E652FC4CE7AD5A6F9EB737642077C128E514C889458220ED6985913 | |||
| 3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | C:\Windows\Temp\1528015\....\TemporaryFile | text | |
MD5:44A3A500793BEE8452486B405735D7EF | SHA256:D0D4BC1A332E9080AC6545373EDE48F2D7029CFB720D8ECF7424A3AE011180B2 | |||
| 3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | C:\Windows\ime\46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | executable | |
MD5:C22908FE460312D76B50129AA3EF2CF2 | SHA256:46F79C451E652FC4CE7AD5A6F9EB737642077C128E514C889458220ED6985913 | |||
| 3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | C:\Windows\TEMP\Networks\config.json | text | |
MD5:44A3A500793BEE8452486B405735D7EF | SHA256:D0D4BC1A332E9080AC6545373EDE48F2D7029CFB720D8ECF7424A3AE011180B2 | |||
| 3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | C:\Windows\InfusedAppe\UnattendGC\AppCapture_x32.dll | executable | |
MD5:C64F0888AC169EF64EFC3494A903445F | SHA256:E88E82AB4503C1F9F06DB2F657B0D9966BB9A067A947FF4377EE967086F3DE08 | |||
| 2096 | opperce.exe | C:\Windows\System32\1531875.bak | executable | |
MD5:A7195BEAE808BA6CD4E4E373F4B540ED | SHA256:BC57AA3E6562468E09CC341CDEAAE364B13A33AAB9E75A7E11D1DABBA1788614 | |||
| 3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | C:\Windows\TEMP\wimnat.exe | executable | |
MD5:2334BB8BAF5E062683D8EC67B7AC531E | SHA256:6C310B9829FE5FAC50B0EA752242B456B3B86462DEE46624337715831DEB8B2E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | GET | — | 34.94.160.21:57890 | http://a88.bulehero.in:57890/Cfg.ini | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | 34.94.160.21:57890 | a88.bulehero.in | GOOGLE-CLOUD-PLATFORM | US | unknown |
3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | 110.81.155.138:80 | 2018.ip138.com | Chinanet | CN | unknown |
3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | 59.57.13.133:80 | 2018.ip138.com | Quanzhou | CN | unknown |
3808 | 46f79c451e652fc4ce7ad5a6f9eb737642077c128e514c889458220ed6985913.exe | 59.57.13.182:80 | 2018.ip138.com | Quanzhou | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
a88.bulehero.in |
| unknown |
a88.heroherohero.info |
| unknown |
a45.bulehero.in |
| unknown |
off.heroherohero.info |
| unknown |
2018.ip138.com |
| unknown |
dns.msftncsi.com |
| shared |